1. INTRODUCTION
I completed the Windows Forensics 1 room on TryHackMe:
https://tryhackme.com/room/windowsforensics1
This room introduces digital forensics fundamentals by analyzing Windows artifacts like registry hives, execution logs, and USB activity. Key tools included Registry Explorer, FTK Imager, and Eric Zimmerman’s EZtools suite.
2. WINDOWS REGISTRY
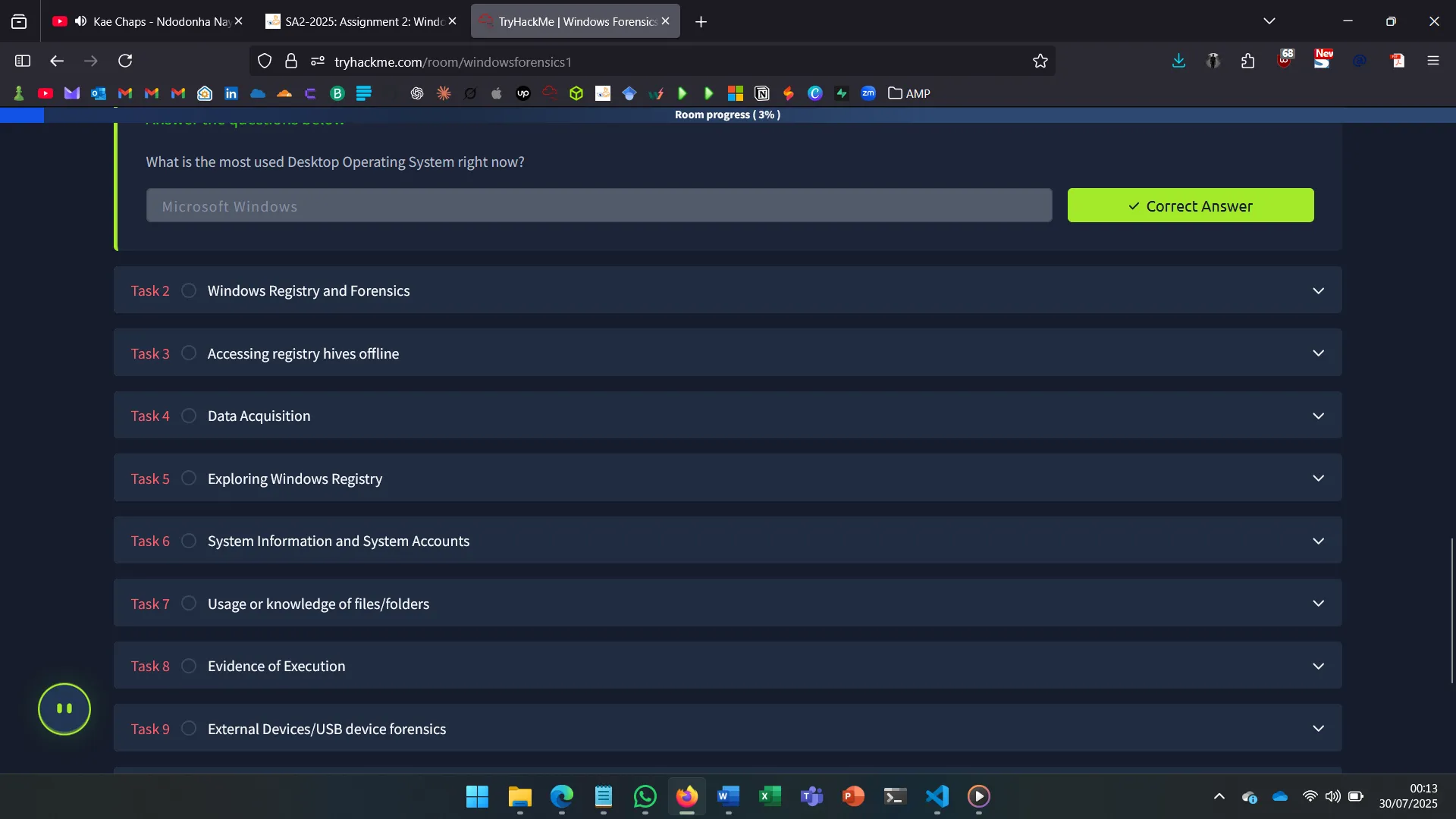
The Windows Registry is a hierarchical database storing OS and user configurations. It consists of five root keys:
- HKEY_CURRENT_USER
- HKEY_USERS
- HKEY_LOCAL_MACHINE
- HKEY_CLASSES_ROOT
- HKEY_CURRENT_CONFIG
Each plays a vital role in forensic investigations.
3. HIVES
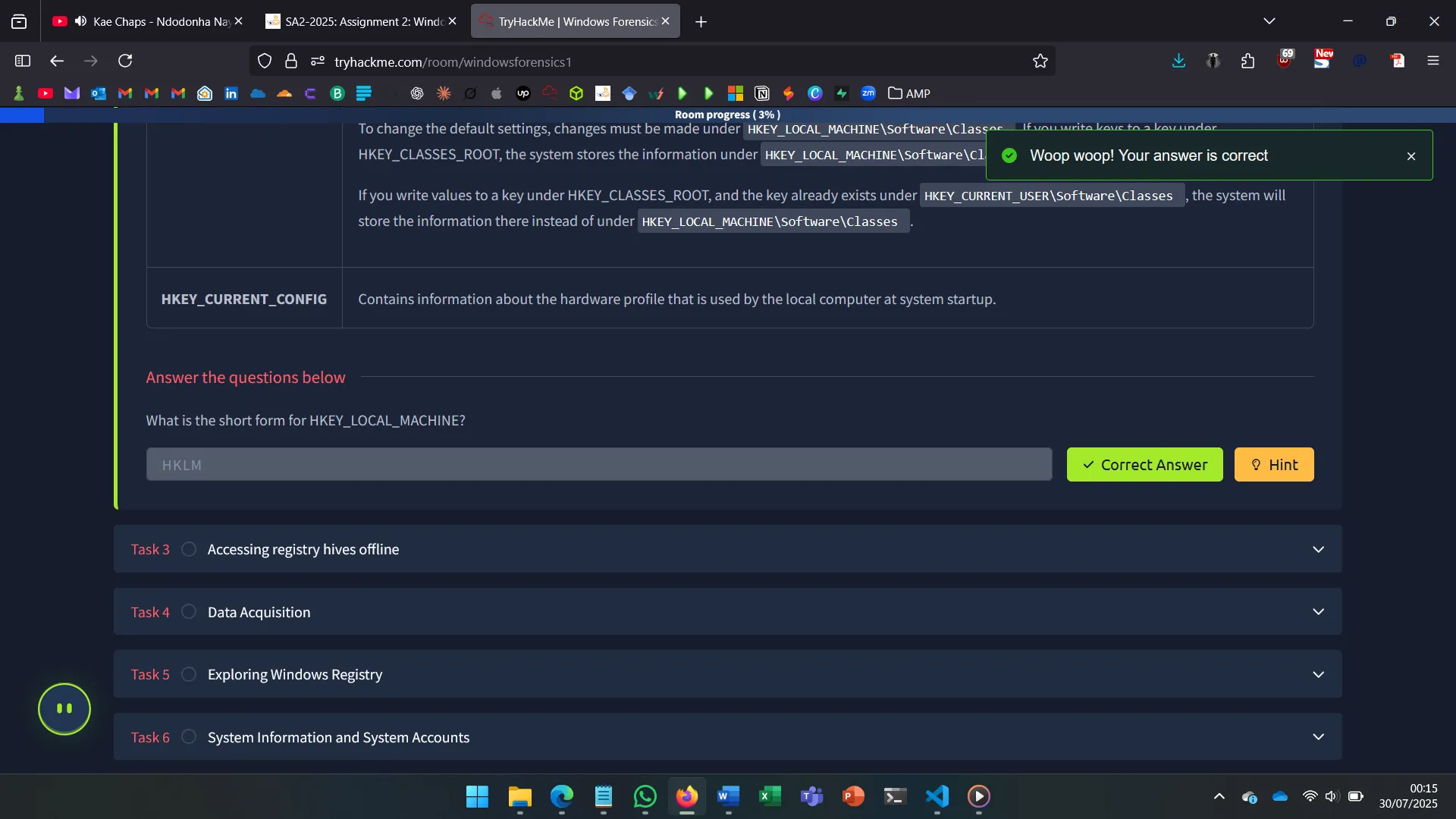
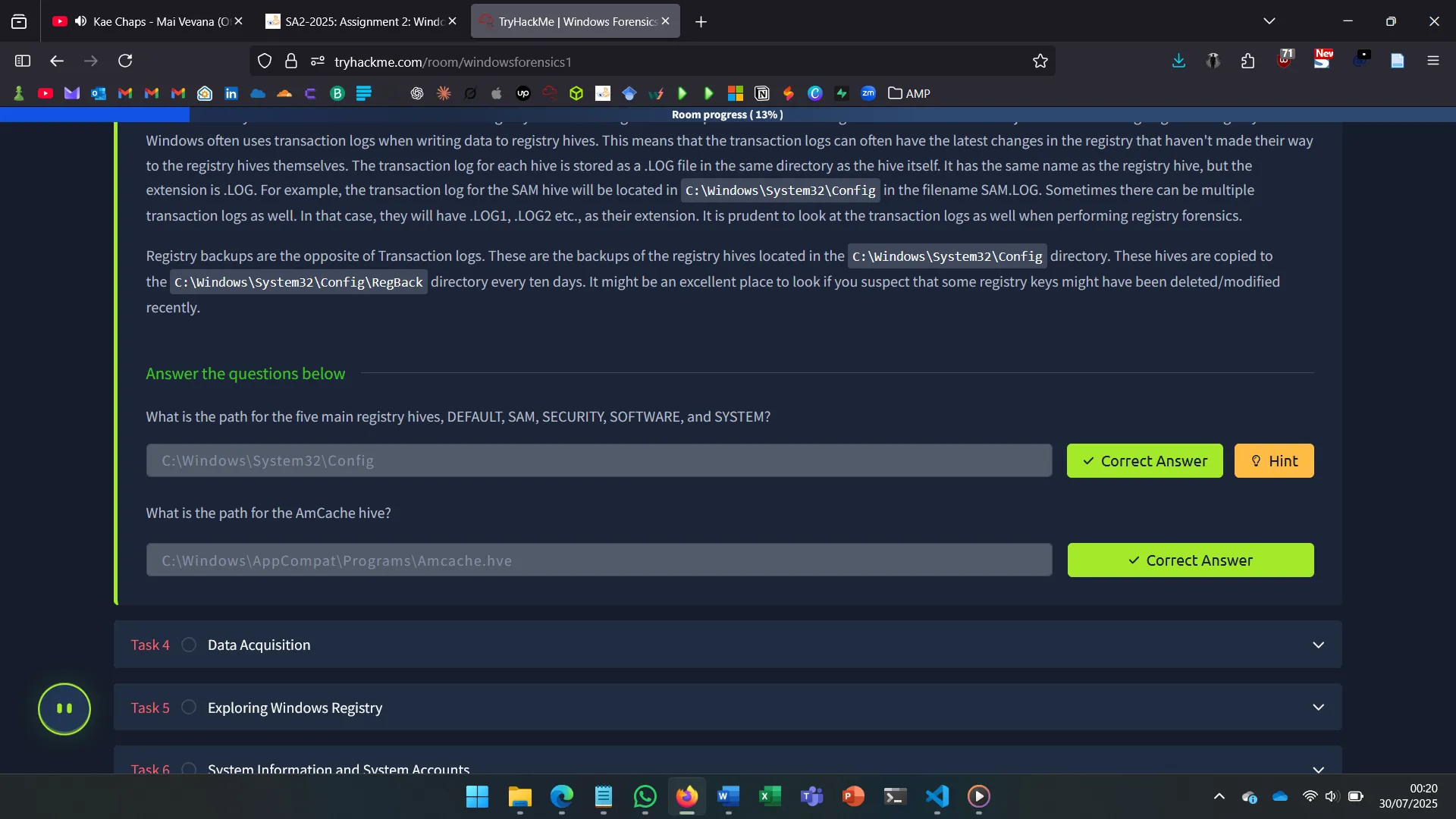
Important registry hives include:
- SYSTEM, SOFTWARE, SAM, SECURITY, DEFAULT → located at
C:\Windows\System32\Config - NTUSER.DAT, USRCLASS.DAT → user-specific hives in profile folders
- Amcache.hve → recent program execution data
- Transaction logs → capture changes not yet committed
4. DATA ACQUISITION
Live analysis risks data integrity. Forensic tools like:
- KAPE
- Autopsy
- FTK Imager
…are used to acquire registry hives securely. In this module, data was pre-captured in the VM.
5. EXPLORING WINDOWS REGISTRY
To analyze hives:
- Registry Explorer (Eric Zimmerman) – Supports logs, bookmarks, multiple hives
- Registry Viewer – Good UI, but limited to one hive
- RegRipper – Parses hives and outputs text reports (no transaction logs)
This module used Registry Explorer primarily.
6. SYSTEM INFORMATION AND SYSTEM ACCOUNTS
7. FILES/FOLDERS USAGE/KNOWLEDGE
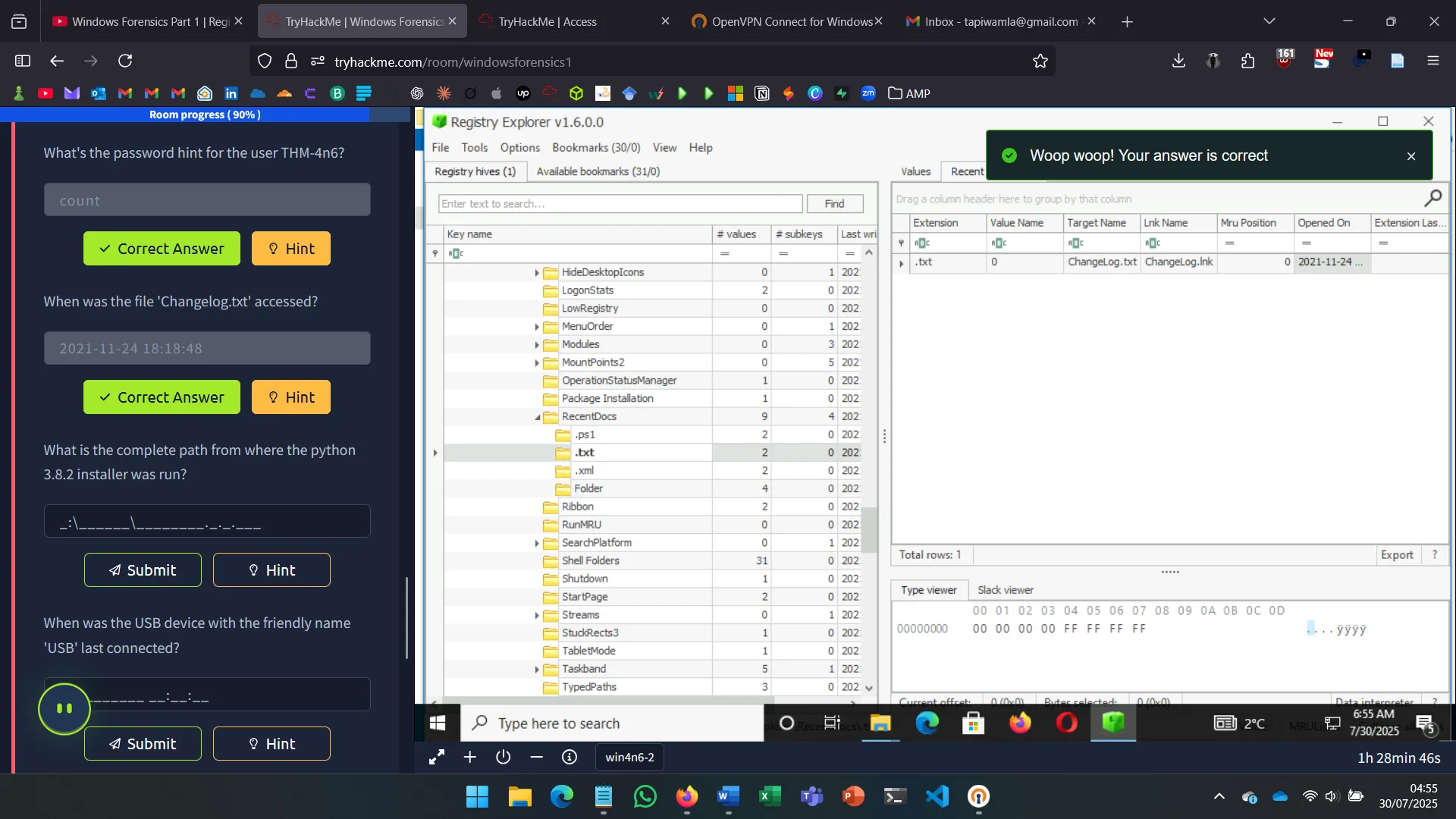
Artifacts from NTUSER.DAT and USRCLASS.DAT include:
- RecentDocs – Opened files
- ShellBags – Accessed folders
- OpenSavePidlMRU – Dialog-based file access
- TypedPaths, WordWheelQuery – Explorer bar/search input history
These provide strong insight into user activity.
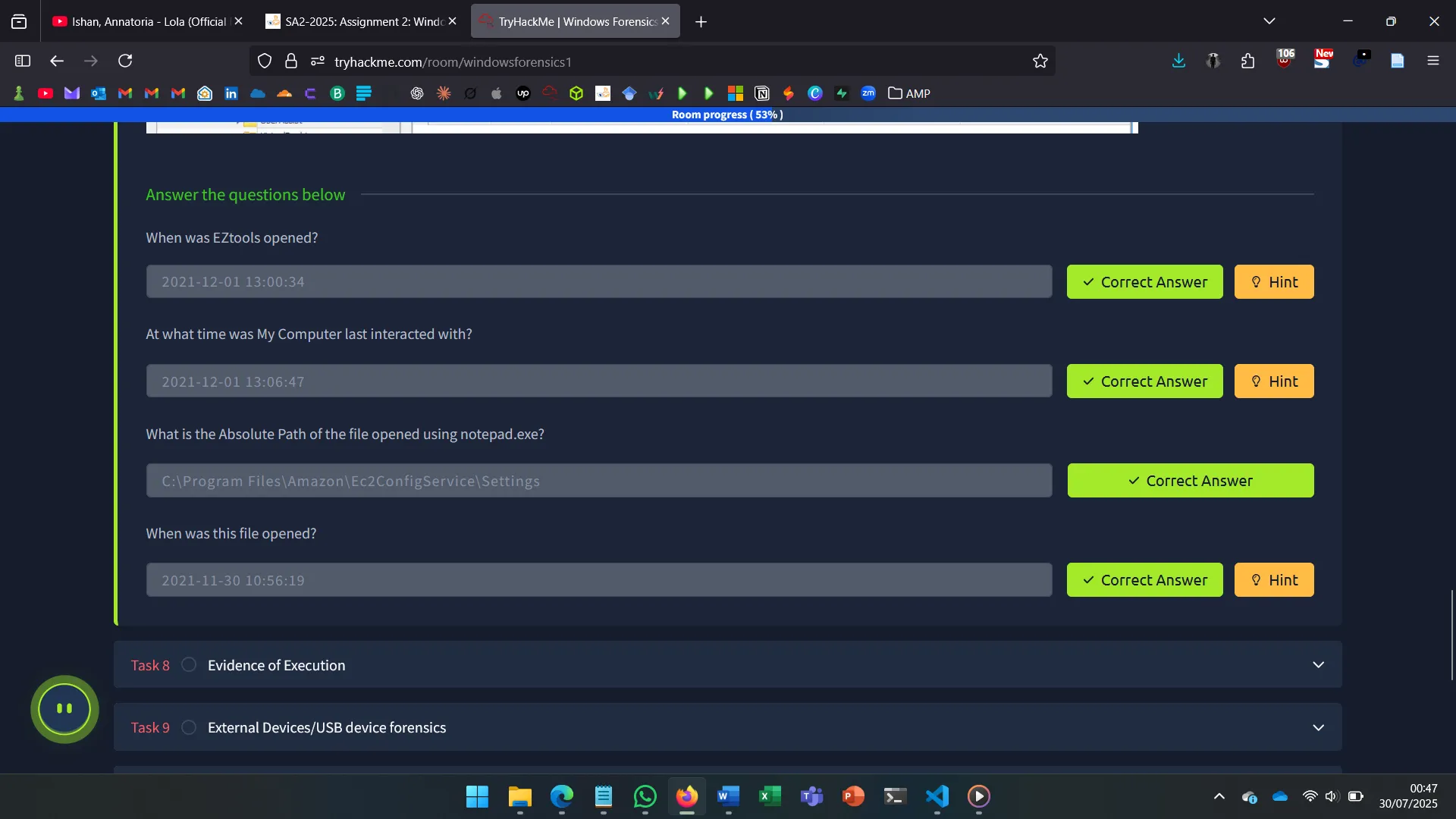
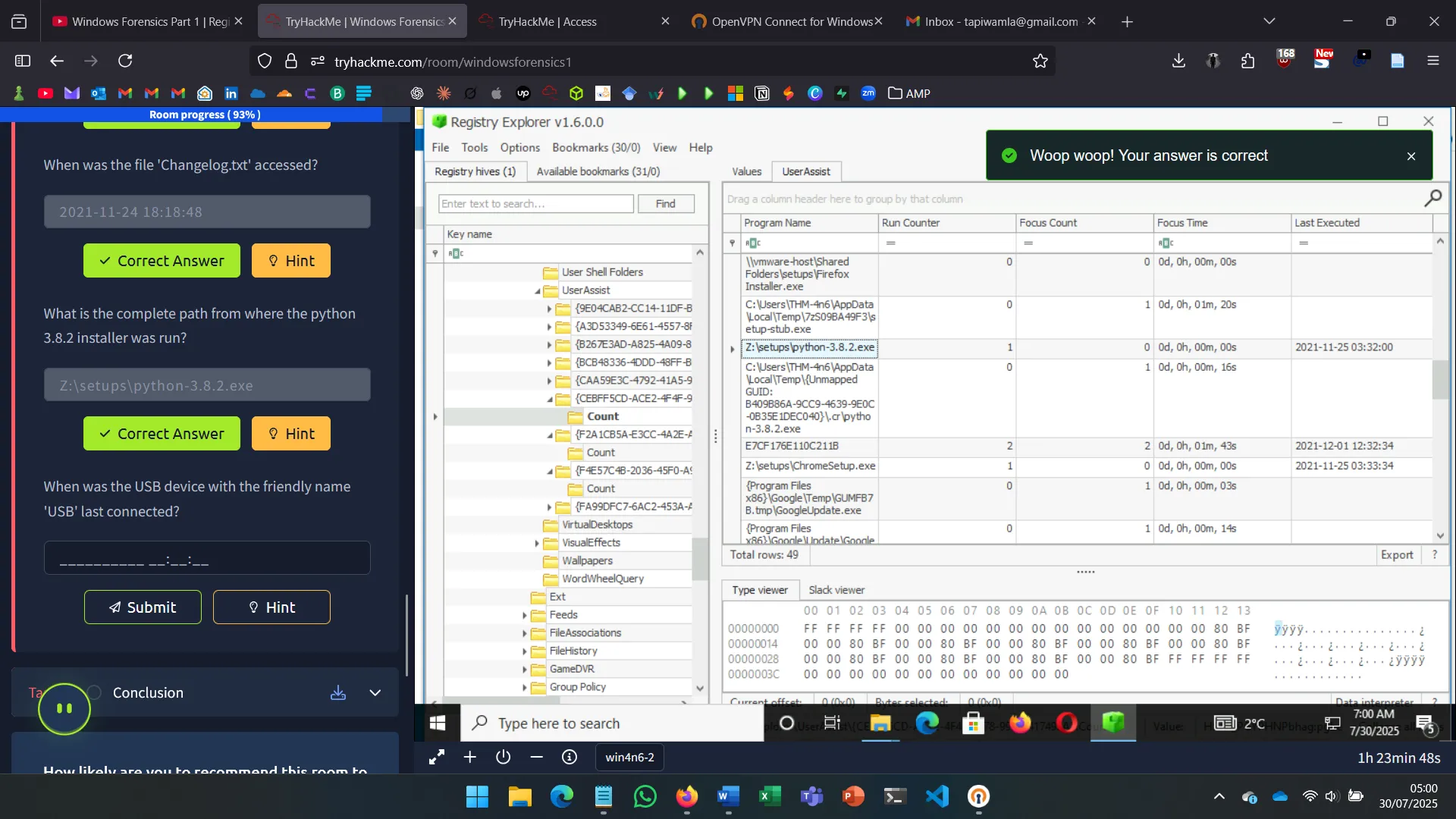
8. EVIDENCE OF EXECUTION
Artifacts indicating program execution:
- UserAssist – GUI-launched apps, execution count
- ShimCache (AppCompatCache) – Metadata of past apps
- AmCache – Timestamps and hashes
- BAM/DAM – Background activity and recent runs
Tools like AppCompatCacheParser are needed to interpret some formats.
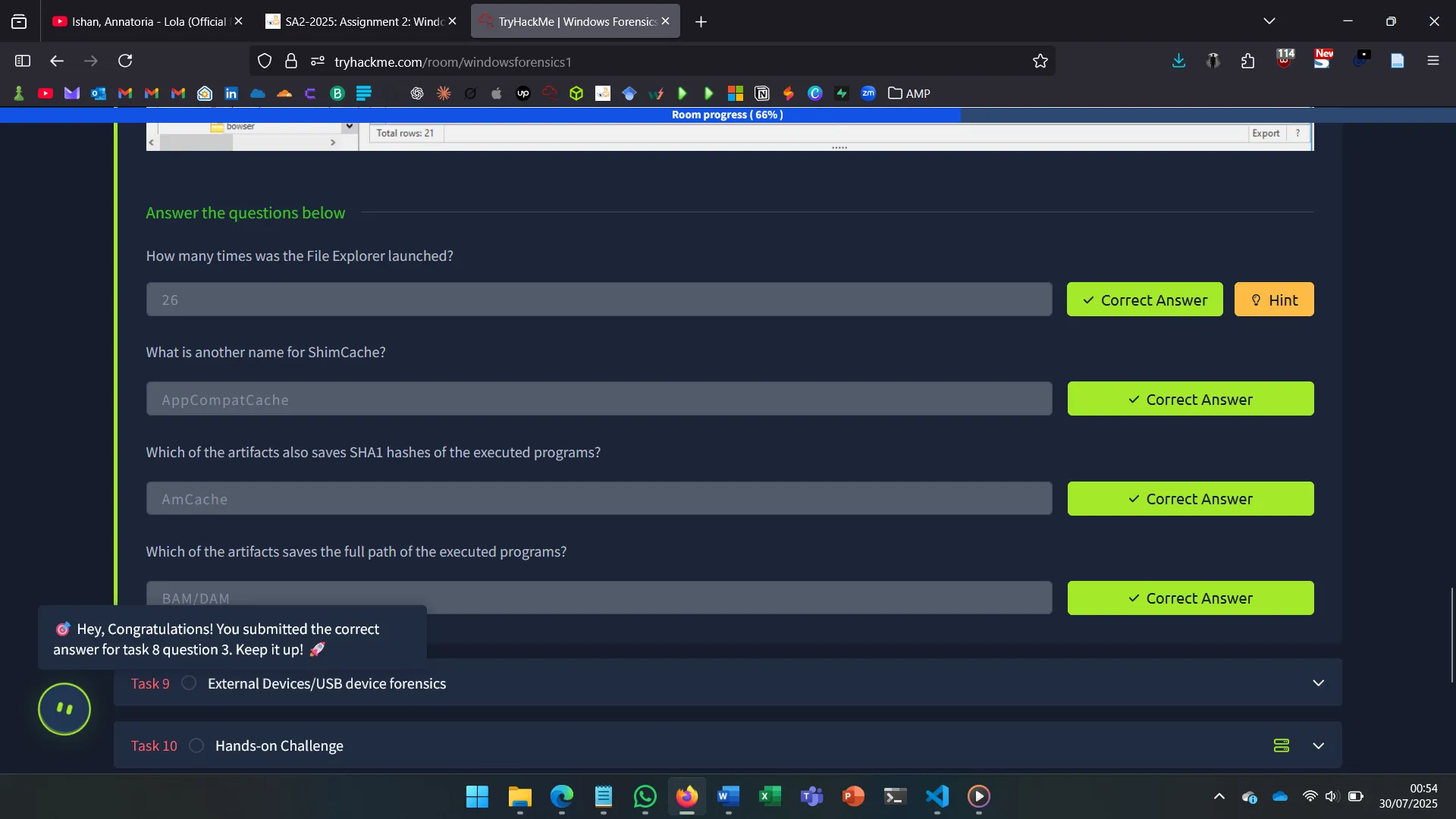
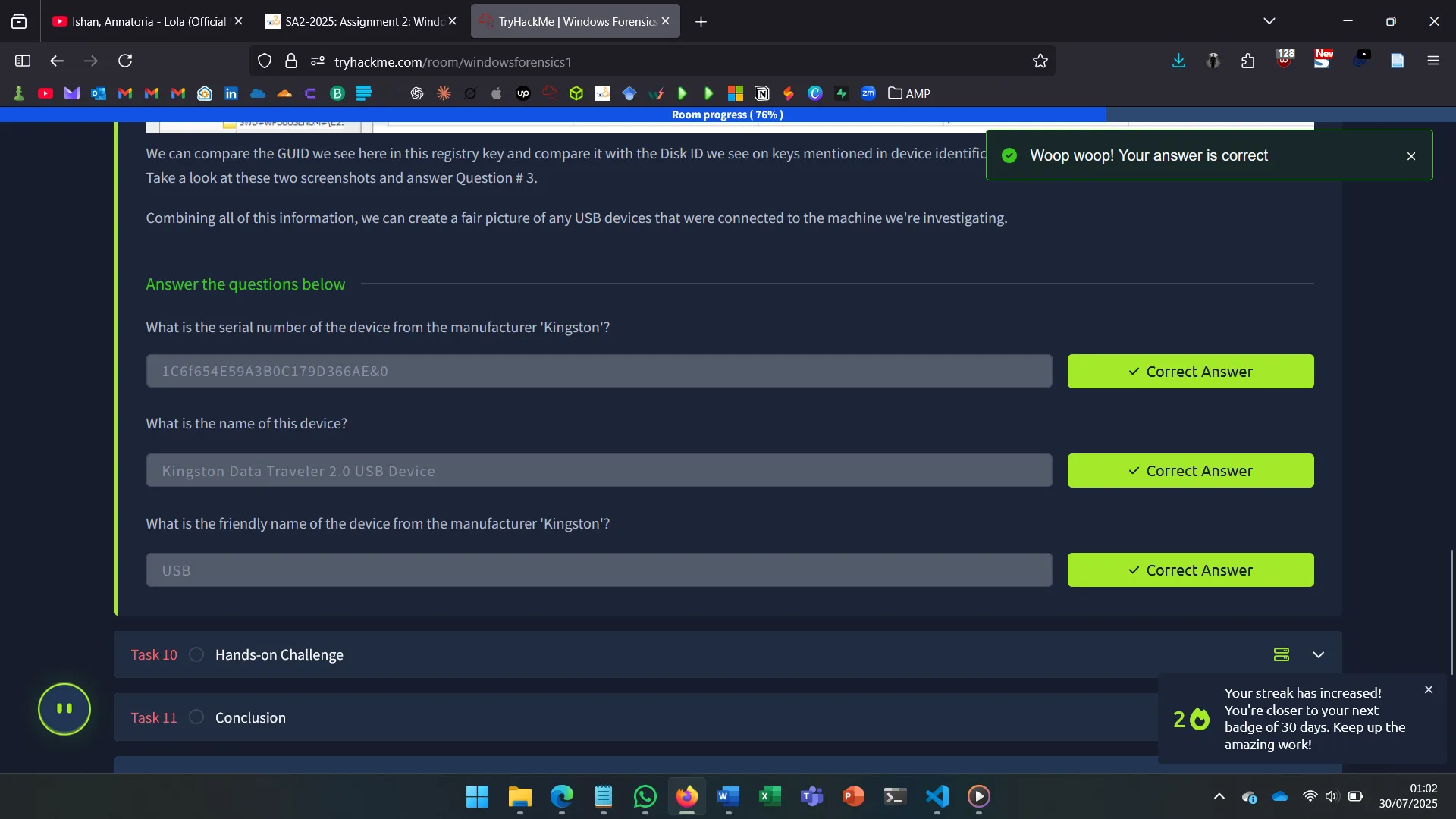
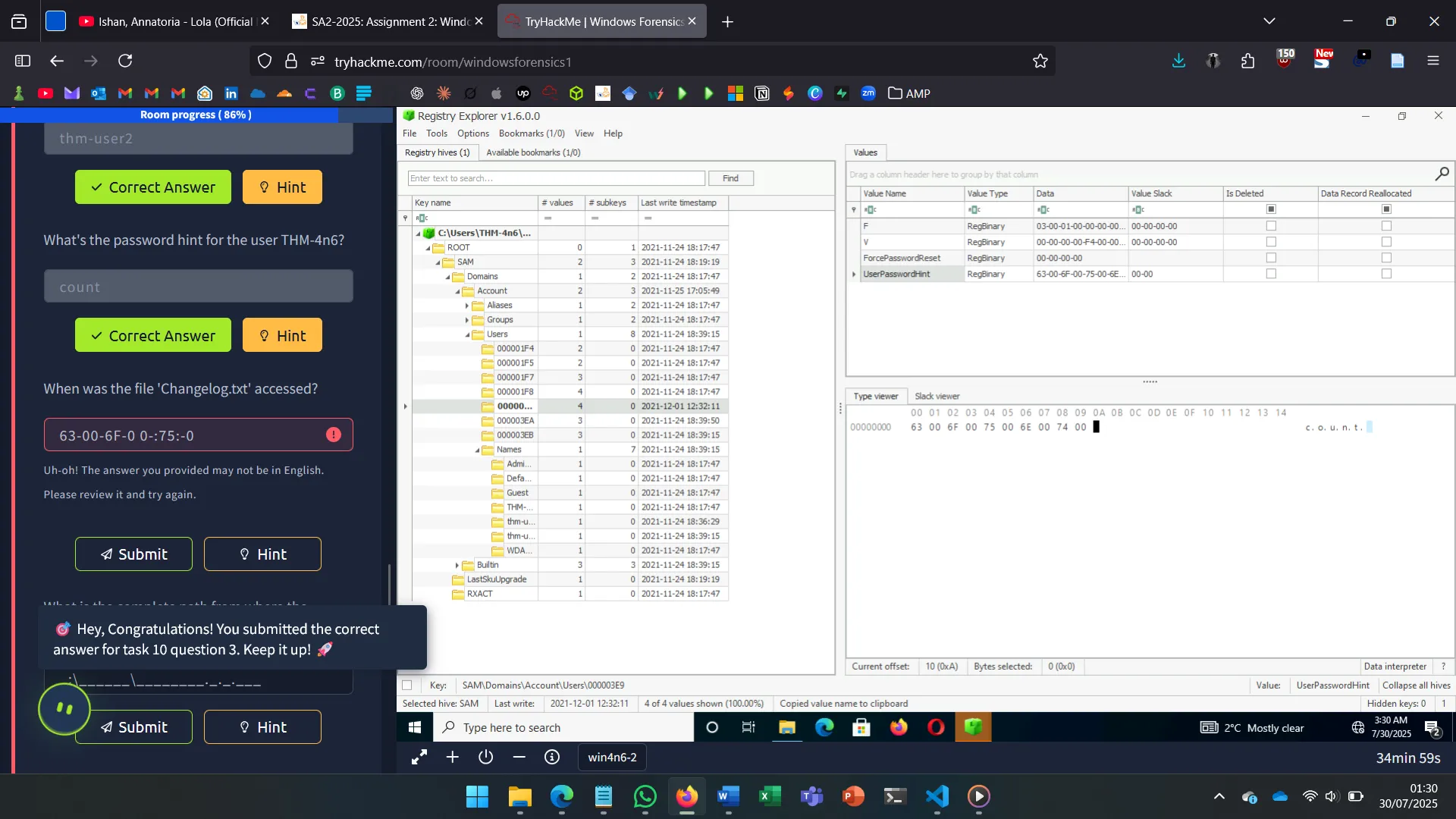
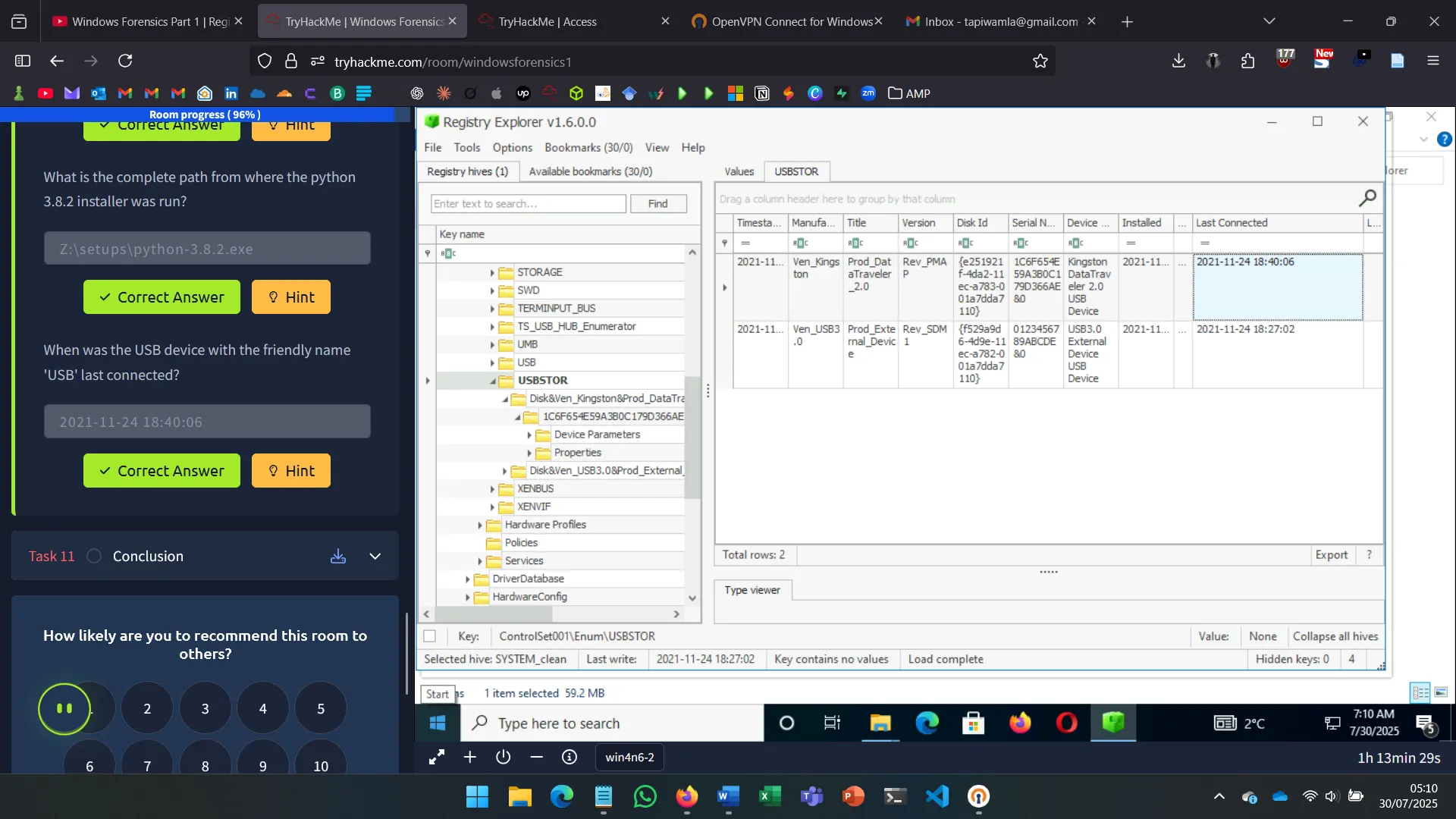
9. USB
USB analysis relies on:
SYSTEM\Enum\USBSTOR– Device vendor/product/version- Connection/removal timestamps (values: 0064, 0066, 0067)
- Volume name from
SOFTWARE\Microsoft\Windows Portable Devices\Devices
These entries can be correlated using Registry Explorer.
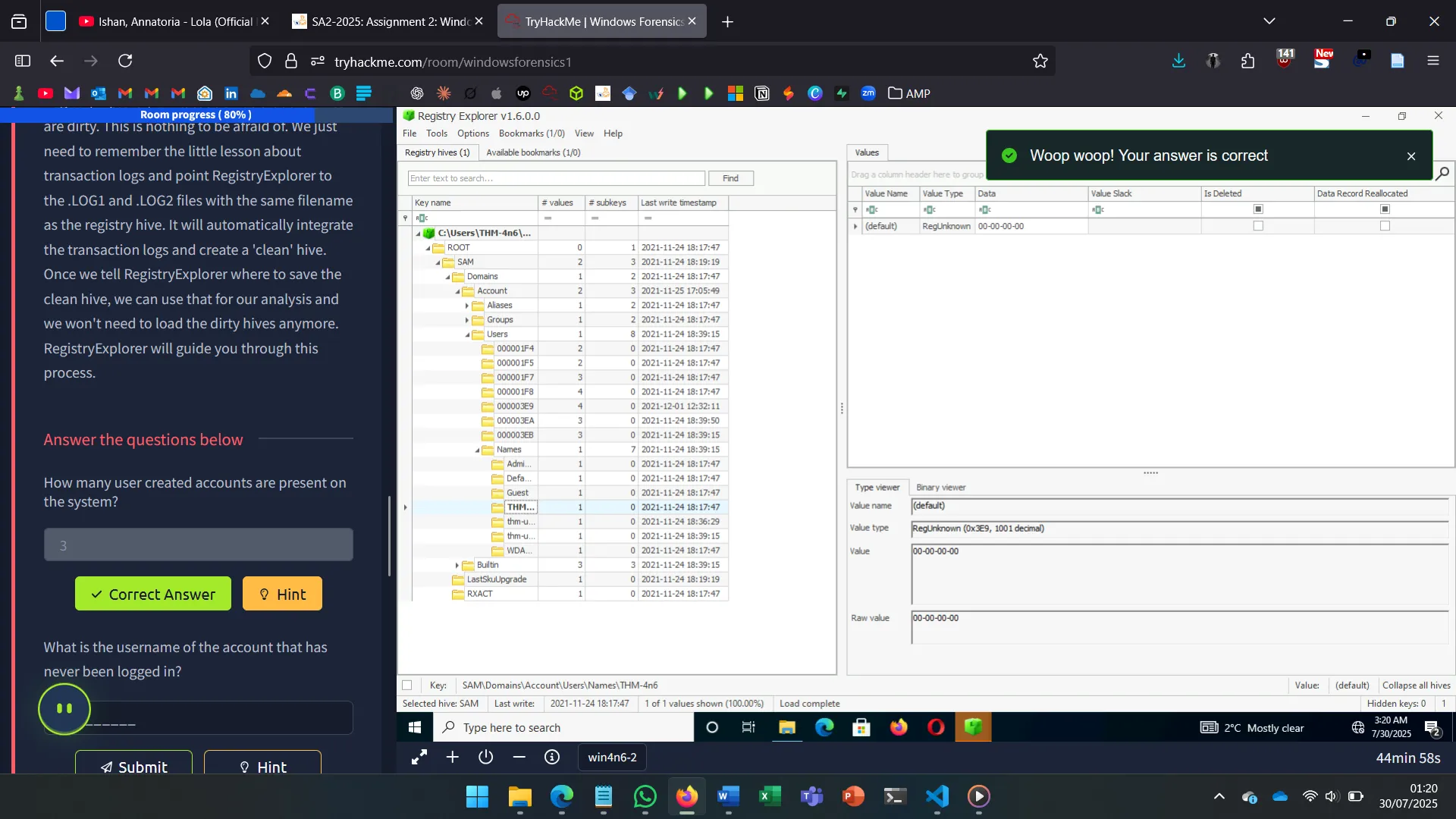
10. HANDSON CHALLENGE
The final task involved analyzing forensic triage data using Eric Zimmerman’s tools to:
- Identify user accounts and activity
- Trace USB history
- Spot accessed network locations
- Reconstruct usage timelines
Key skills were interpreting registry keys, timestamps, and mounted device logs.
11. CONCLUSION
This was a deep dive into real-world forensic techniques on Windows. I now better understand the importance and structure of the registry, and how to extract meaningful activity logs using specialized tools. A valuable and highly practical walkthrough.
