Student: Tapiwanashe Mlambo
Module: Threat Intelligence Tools
1. INTRODUCTION
I completed the “Threat Intelligence Tools” room on TryHackMe, available here (https://tryhackme.com/room/threatinteltools). We covered various concepts in Threat Intelligence as well as the open-source tools that are useful under this topic, including urlscan.io, abuse.ch, PhishTool, and Talos Intelligence (CISCO).
2. THREAT INTELLIGENCE
The room started by defining the concept of Threat Intelligence that is, the analysis of data and information using tools and techniques to generate meaningful patterns on how to mitigate against potential risks associated with existing or emerging threats targeting organizations, industries, sectors or governments.
To mitigate against risks, we can start by trying to answer a few simple questions:
- Who’s attacking you?
- What’s their motivation?
- What are their capabilities?
- What artefacts and indicators of compromise should you look out for?
Threat Intelligence is classified into:
- Strategic Intel: High-level intel that looks into the organization’s threat landscape and maps out the risk areas based on trends, patterns and emerging threats that may impact business decisions.
- Technical Intel: Looks into evidence and artefacts of attack used by an adversary. Incident Response teams can use this intel to create a baseline attack surface to analyze and develop defense mechanisms.
- Tactical Intel: Assesses adversaries’ tactics, techniques, and procedures (TTPs). This intel can strengthen security controls and address vulnerabilities through real-time investigations.
- Operational Intel: Looks into an adversary’s specific motives and intent to perform an attack. Security teams may use this intel to understand the critical assets available in the organization (people, processes, and technologies) that may be targeted.
3. URLSCAN.IO
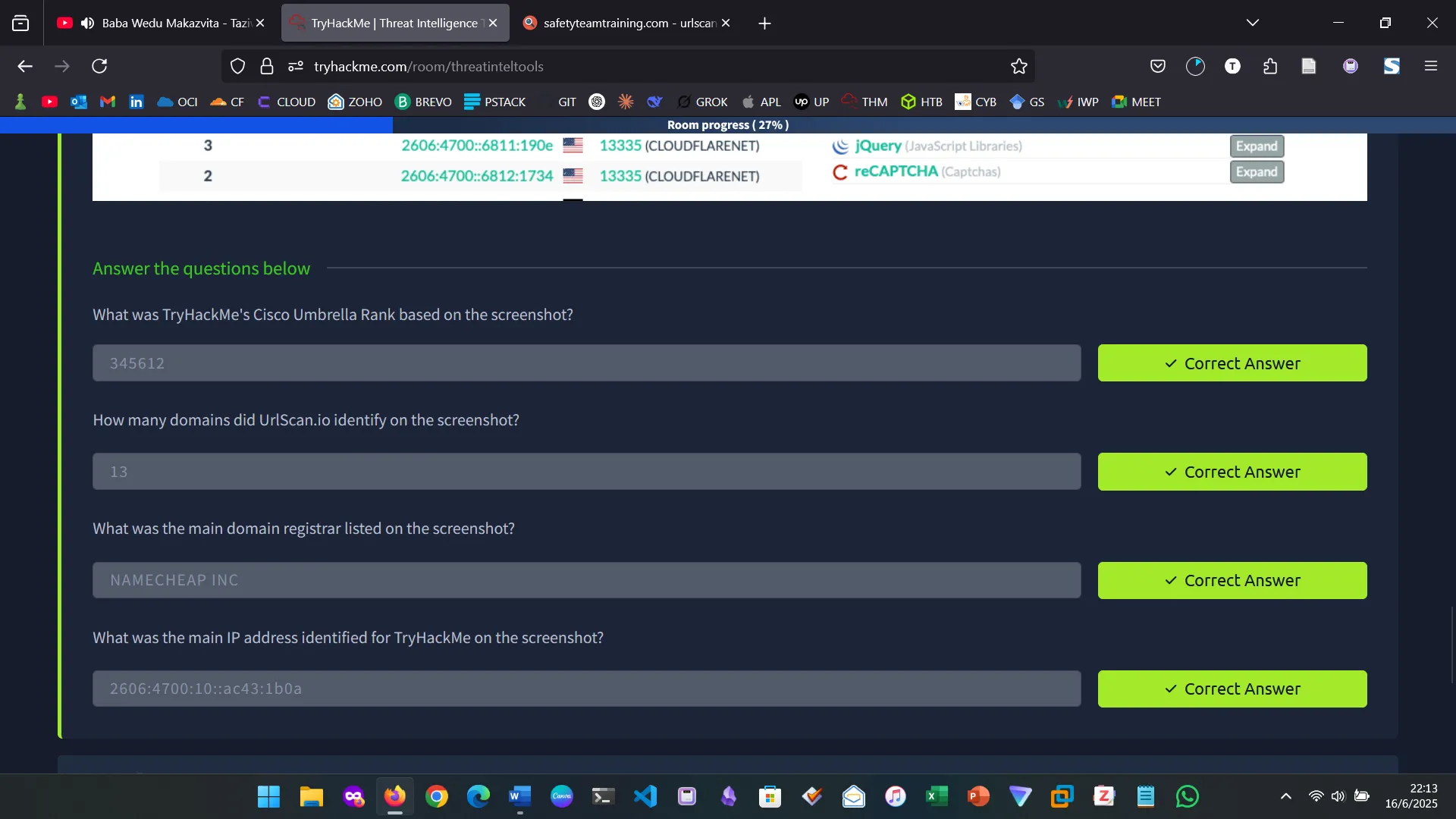
Urlscan.io is a free service developed to assist in scanning and analysing websites. It is used to automate the process of browsing and crawling through websites to record activities and interactions.
4. ABUSE.CH
Abuse.ch is a research project hosted by the Institue for Cybersecurity and Engineering at the Bern University of Applied Sciences in Switzerland. It was developed to identify and track malware and botnets through several operational platforms developed under the project. These platforms are:
- Malware Bazaar: A resource for sharing malware samples.
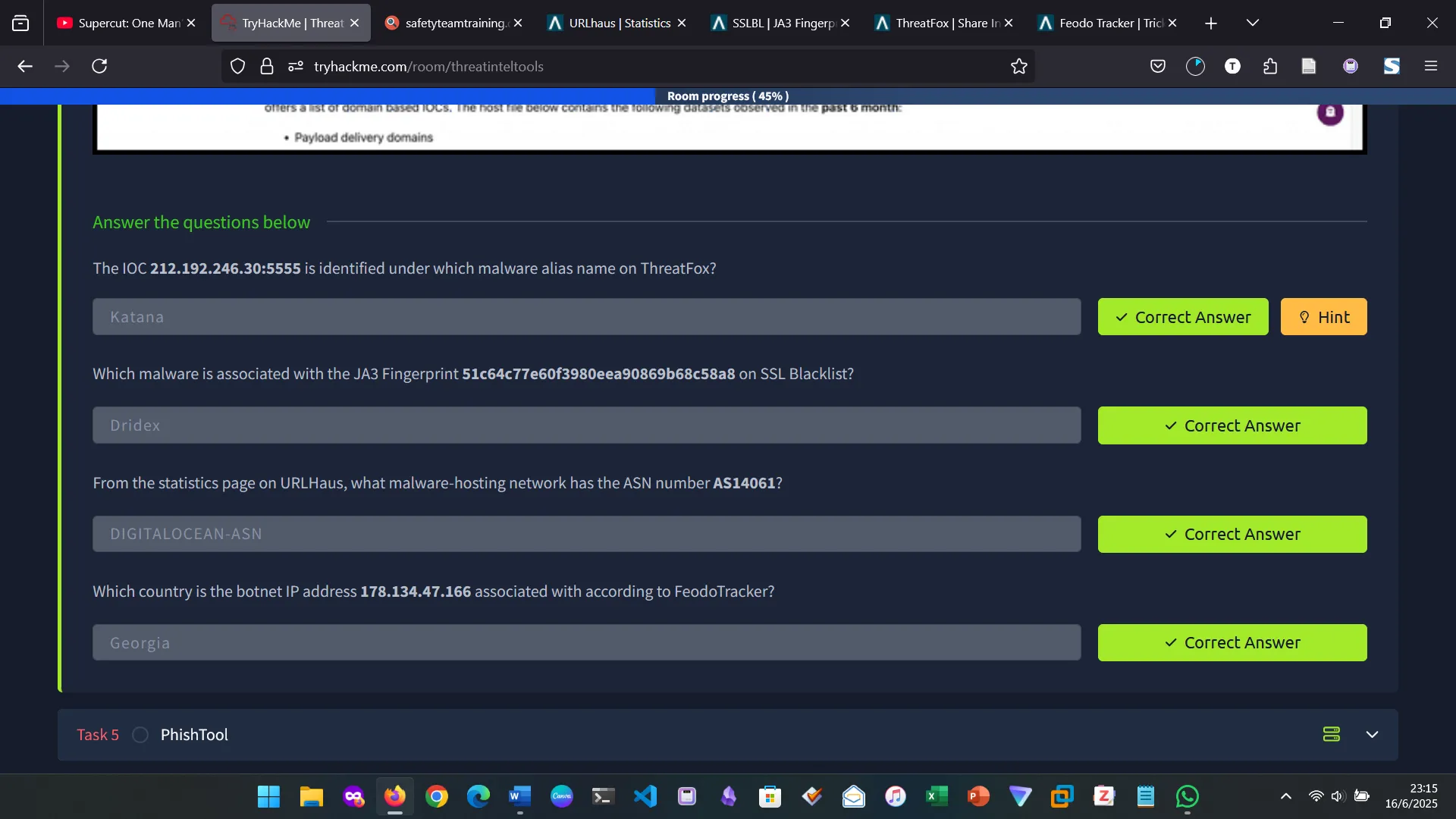
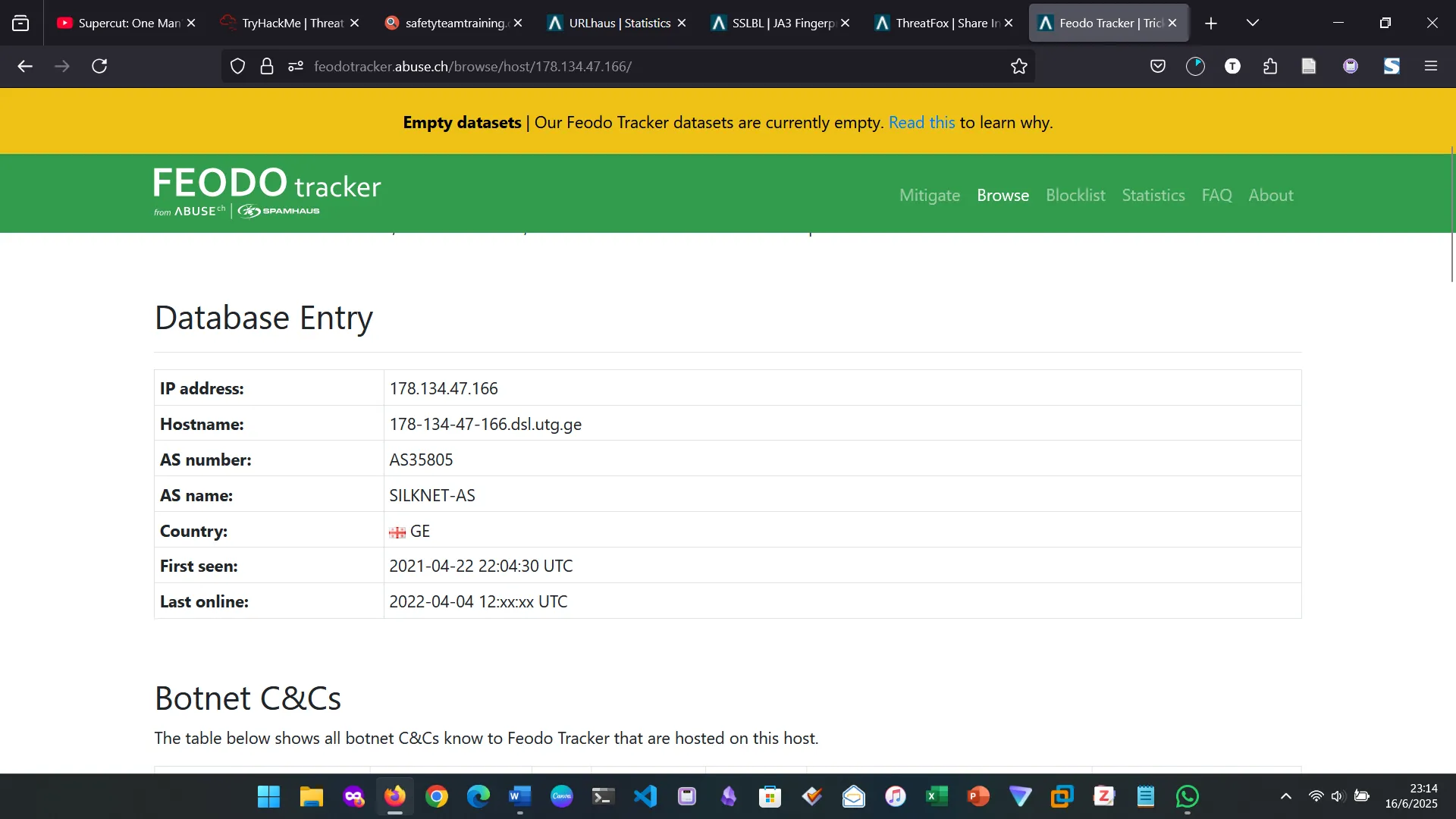
- Feodo Tracker: A resource used to track botnet command and control (C2) infrastructure linked with Emotet, Dridex and TrickBot.
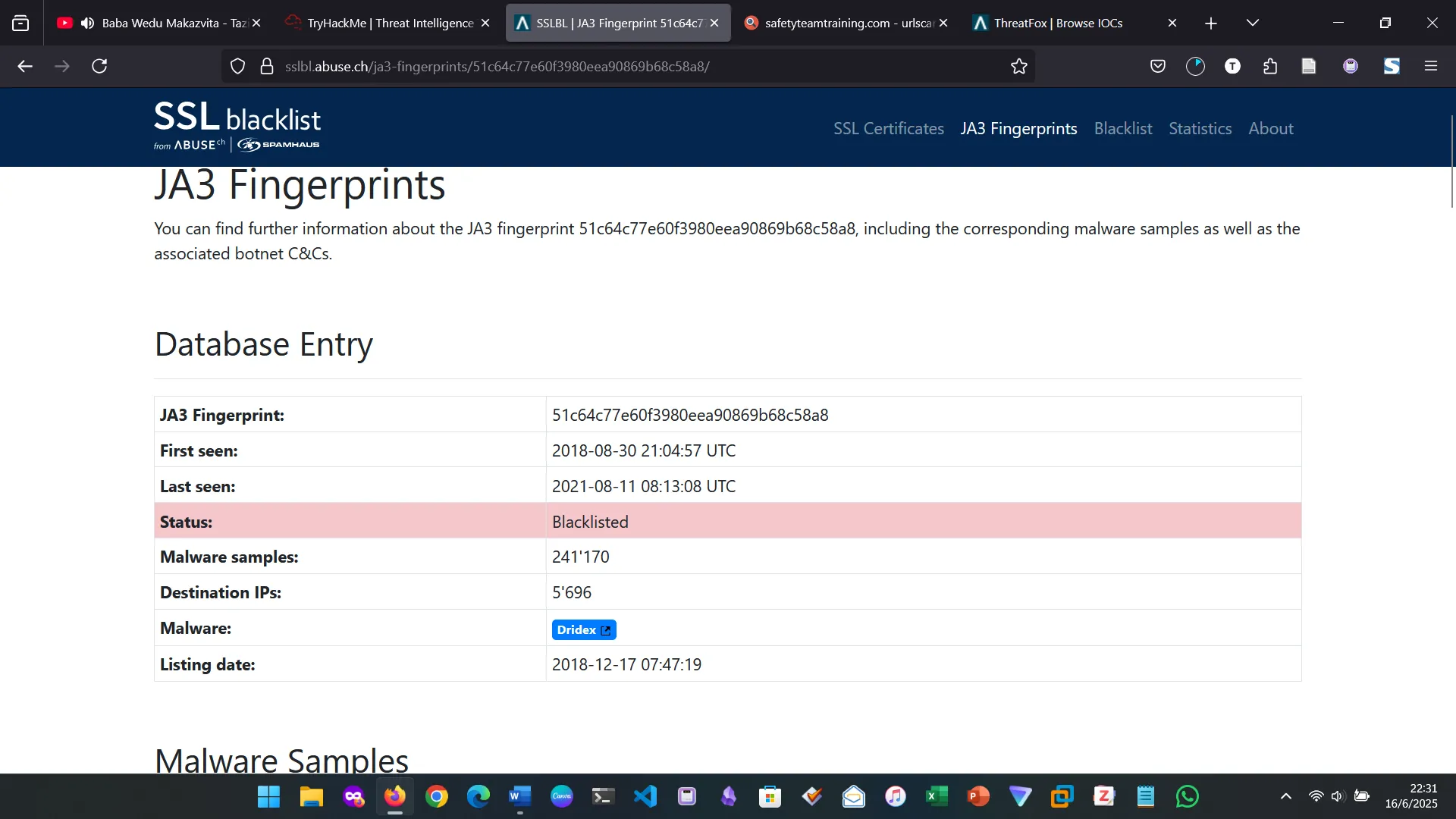
- SSL Blacklist: A resource for collecting and providing a blocklist for malicious SSL certificates and JA3/JA3s fingerprints.
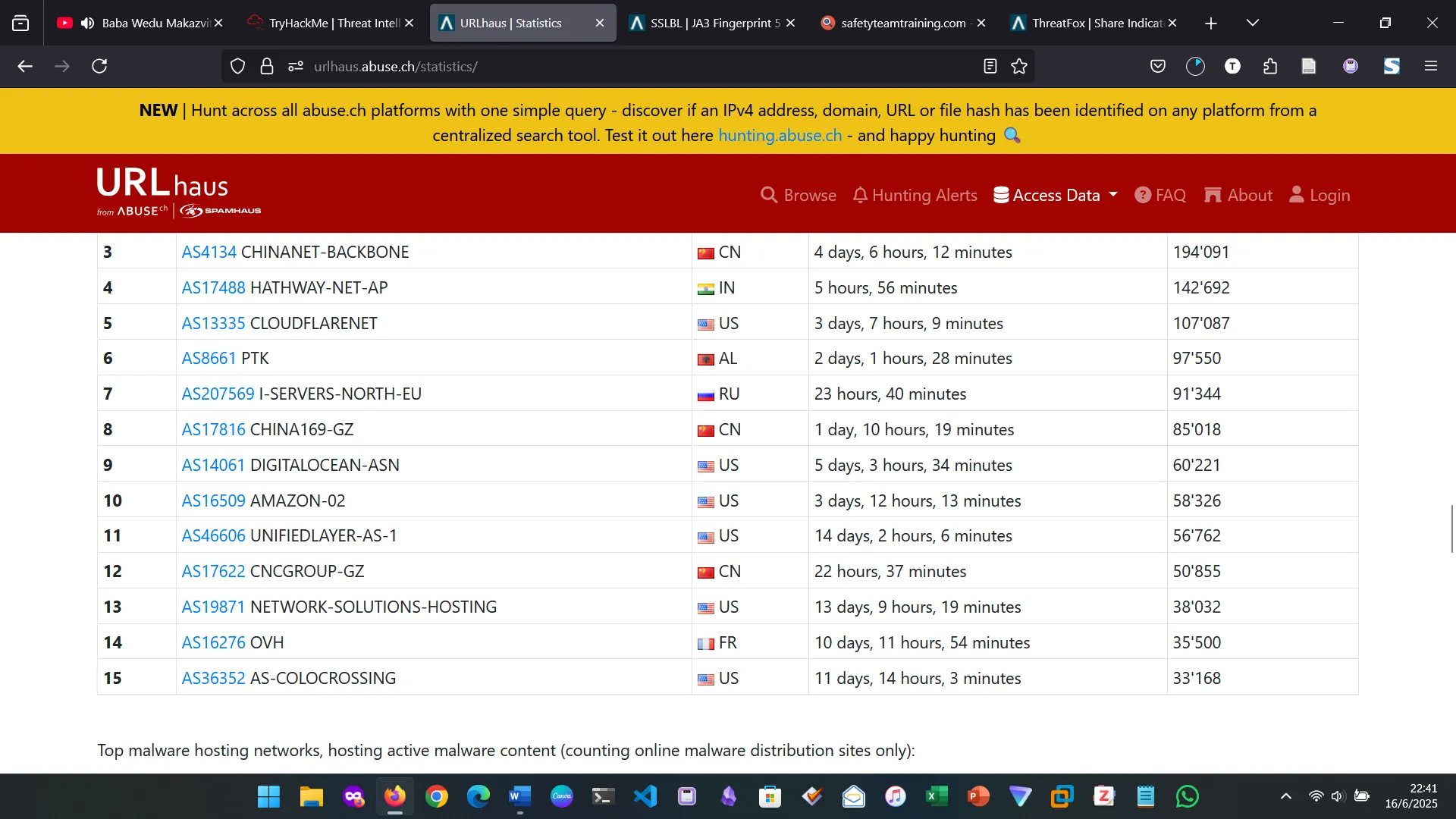
- URL Haus: A resource for sharing malware distribution sites.
- Threat Fox: A resource for sharing indicators of compromise (IOCs).
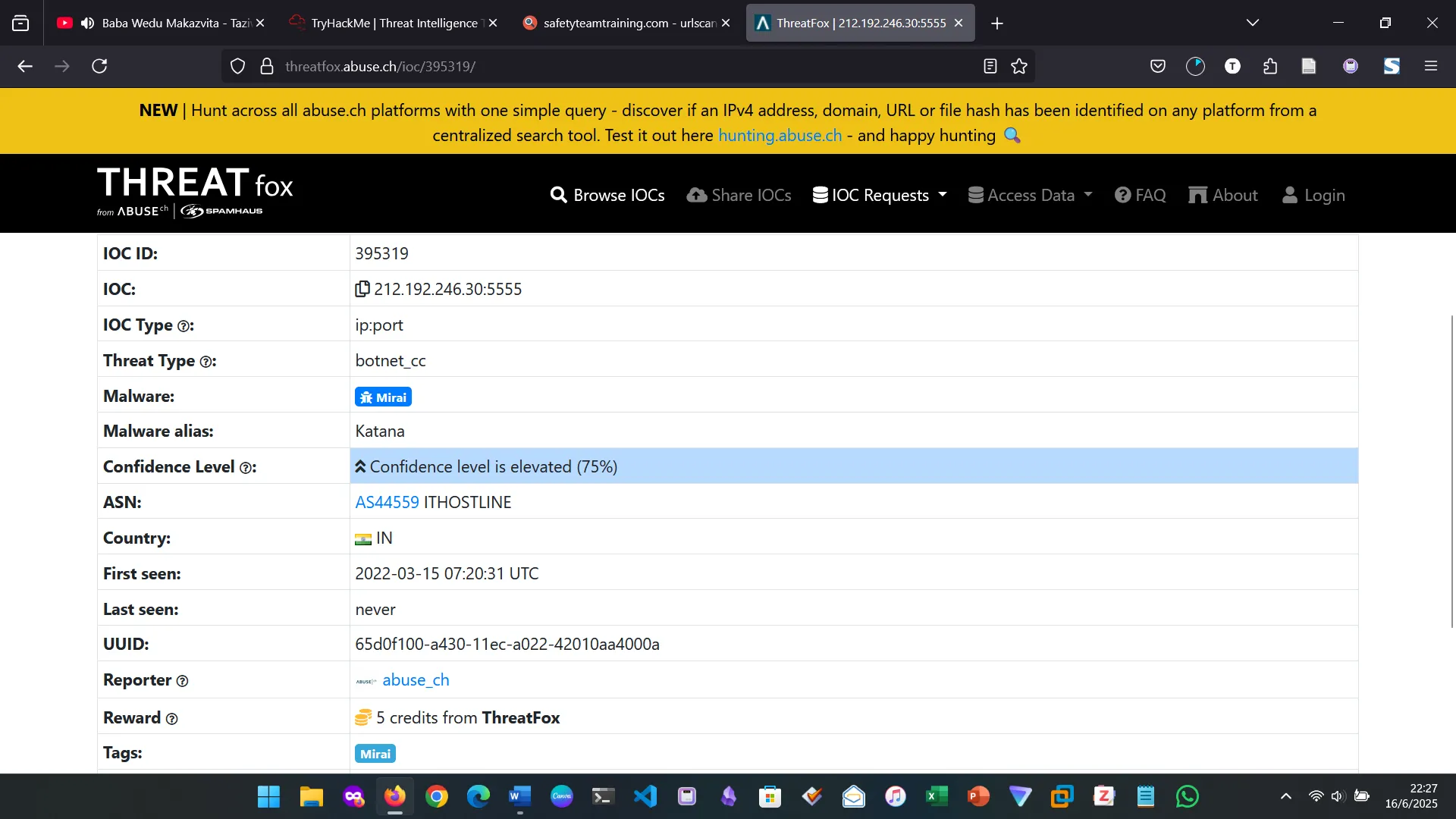
Analyzing IOC 212.192.246.30:5555 on Threatfox
Analyzing JA3 Fingerprint 51c64c77e60f3980eea90869b68c58a8 on SSLBlacklist
URLHaus
Feodotracker
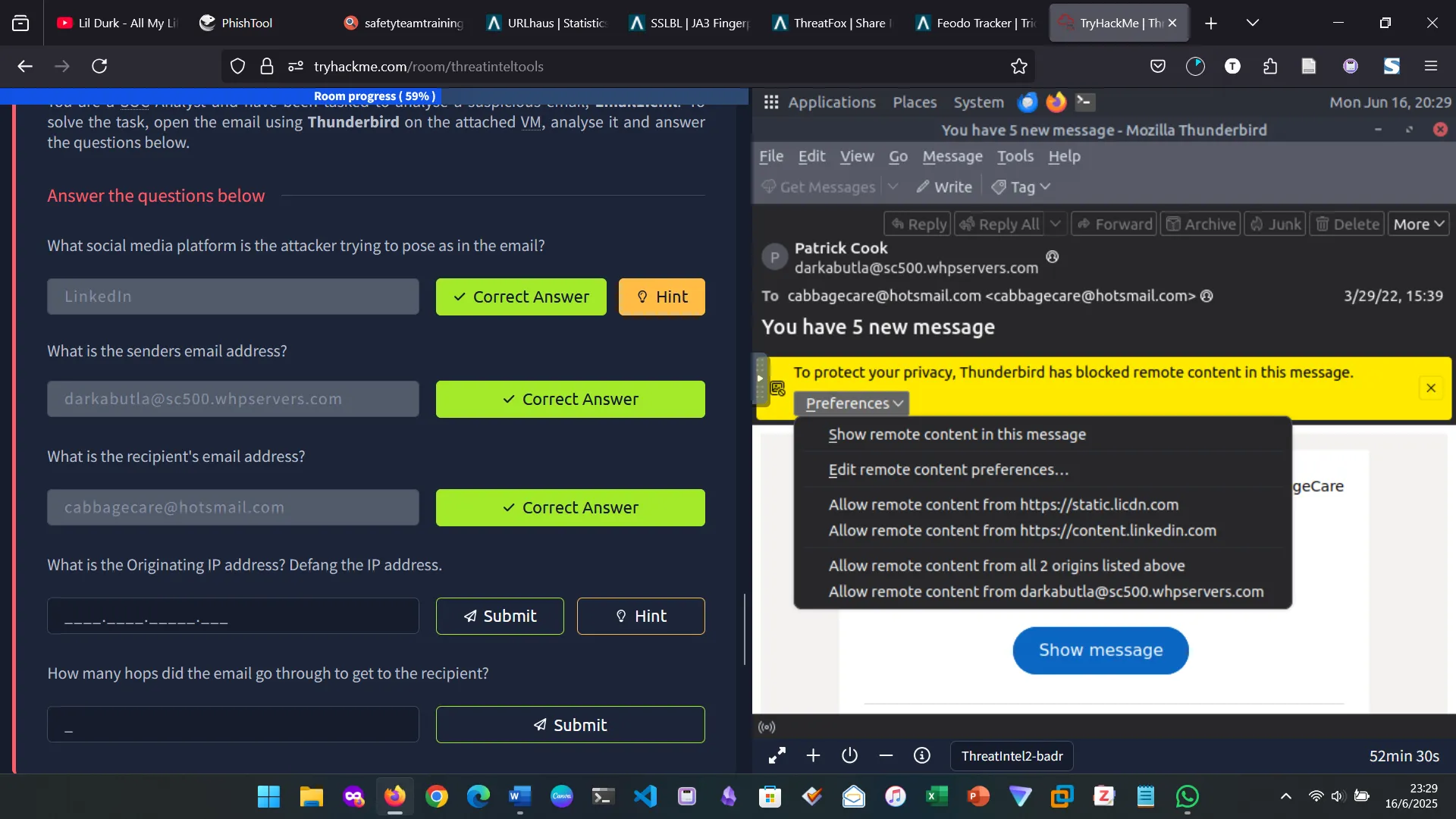
5. PHISHTOOL
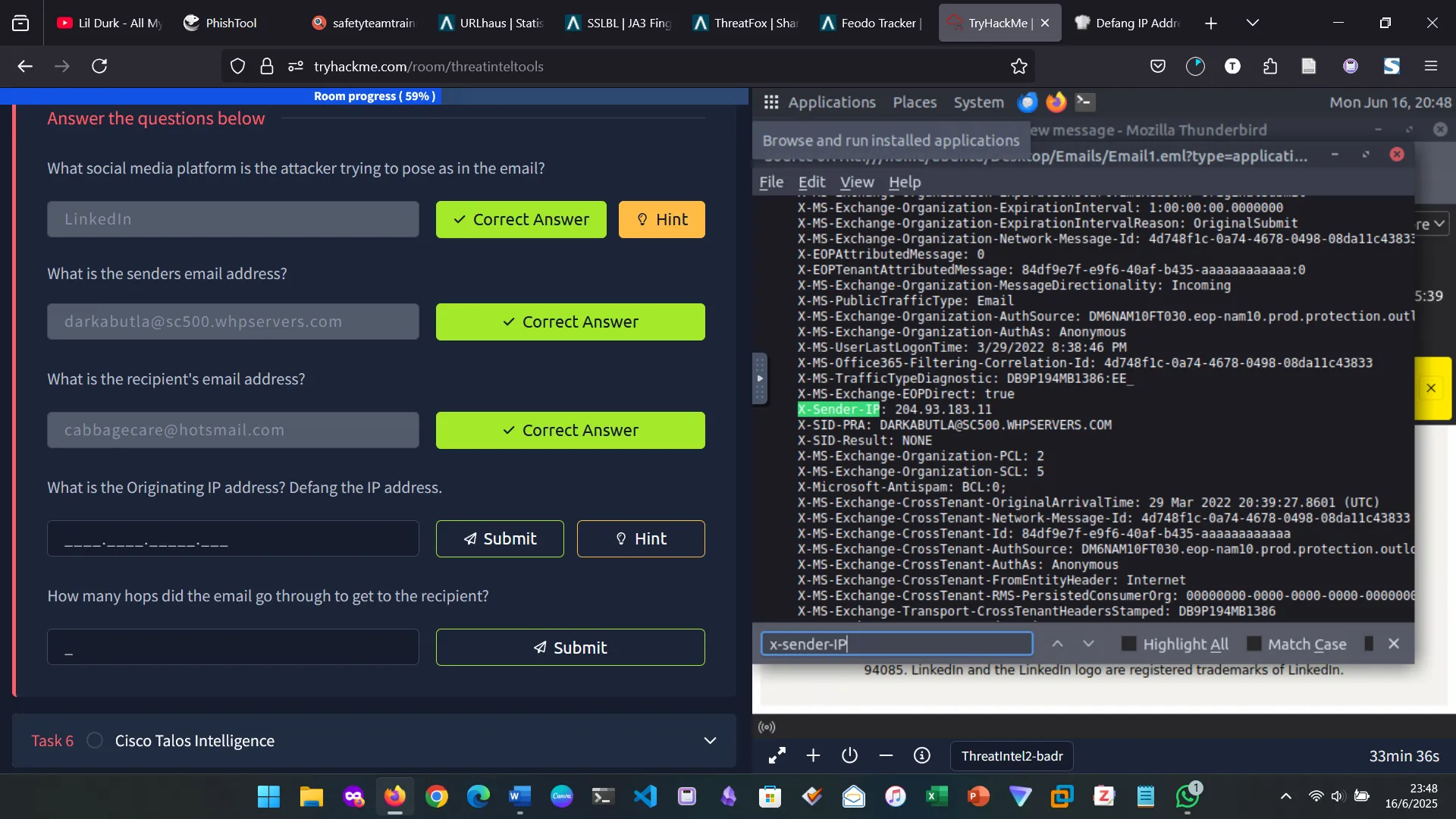
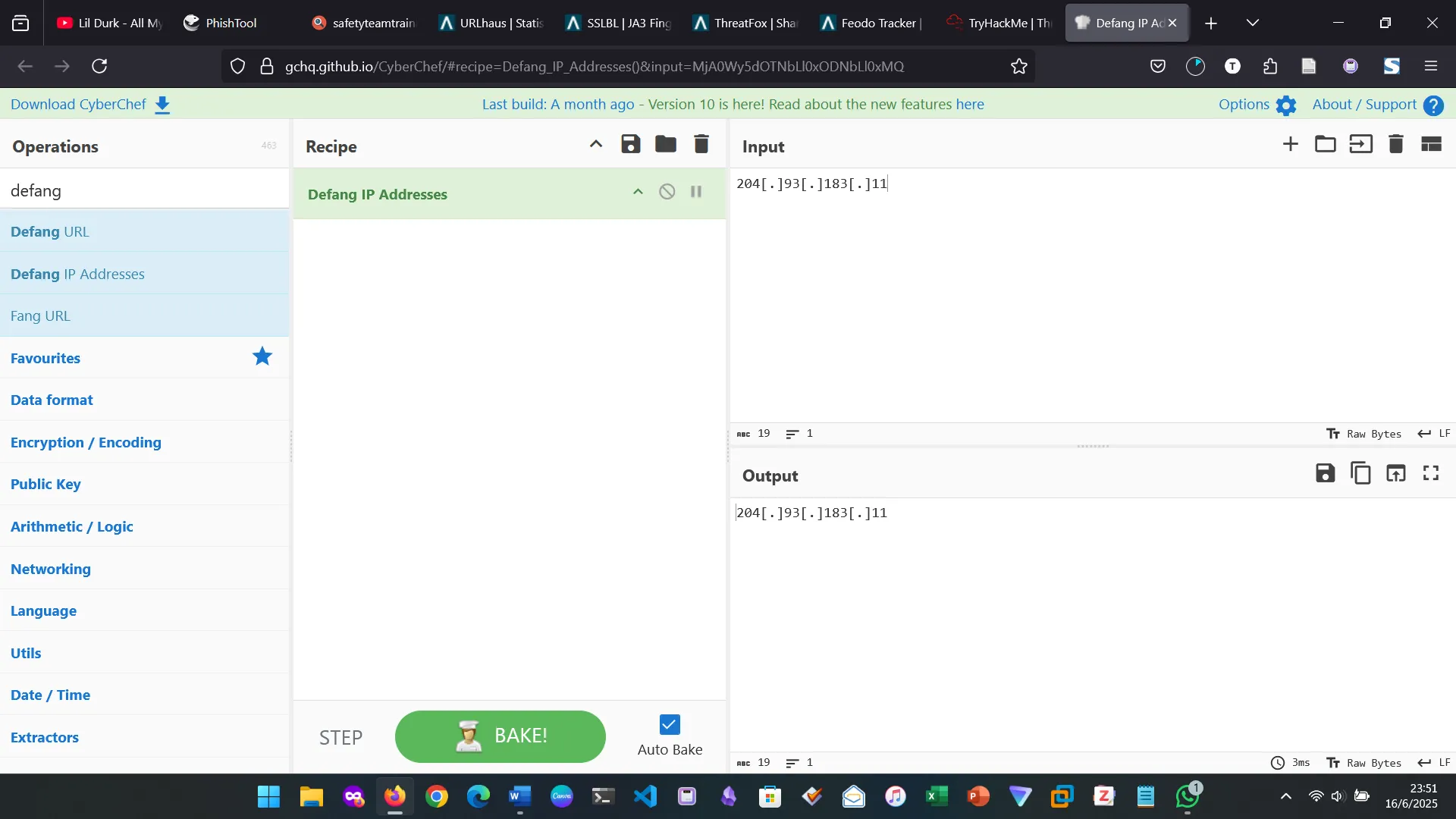
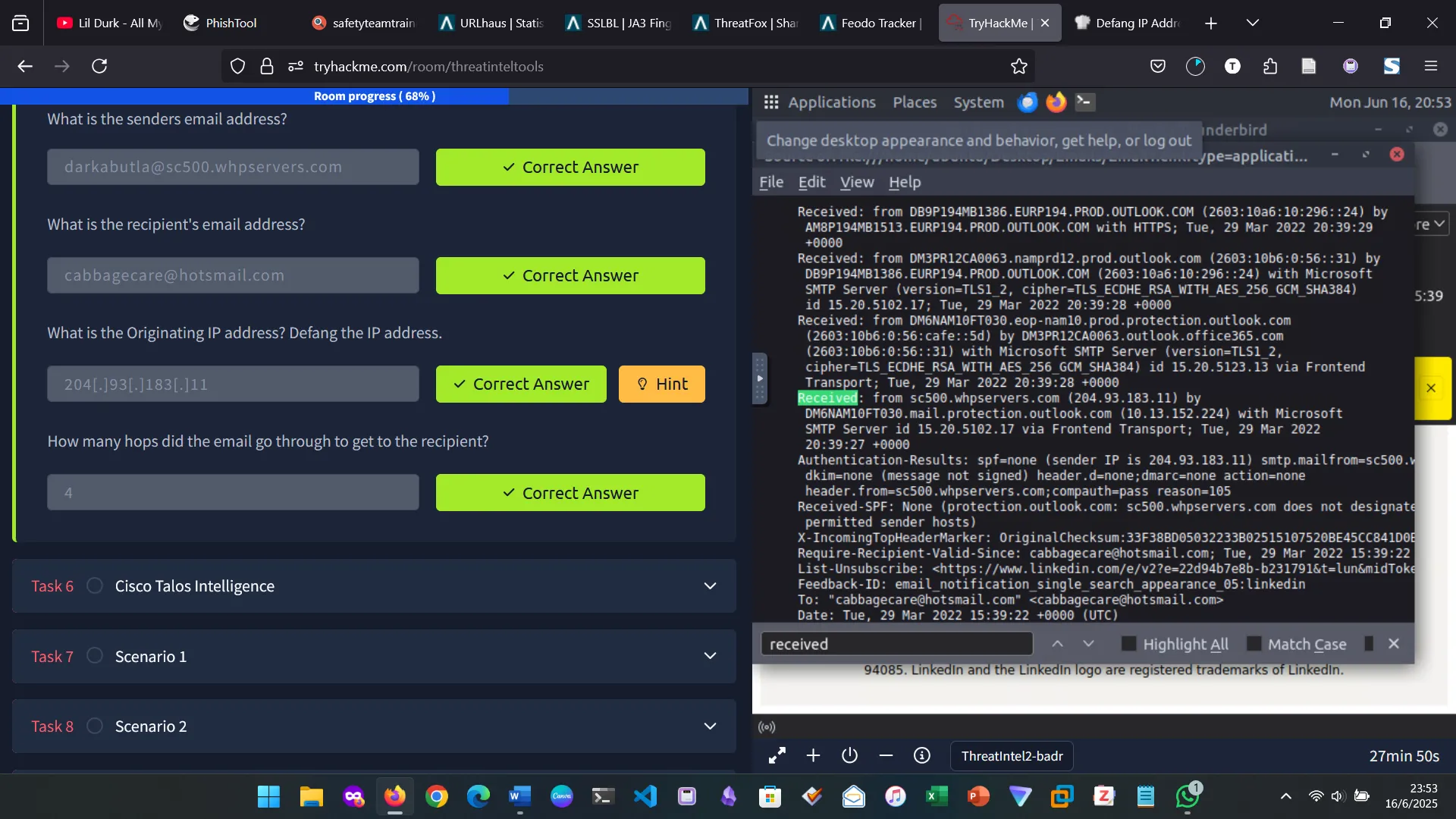
6. TALOS INTELLIGENCE
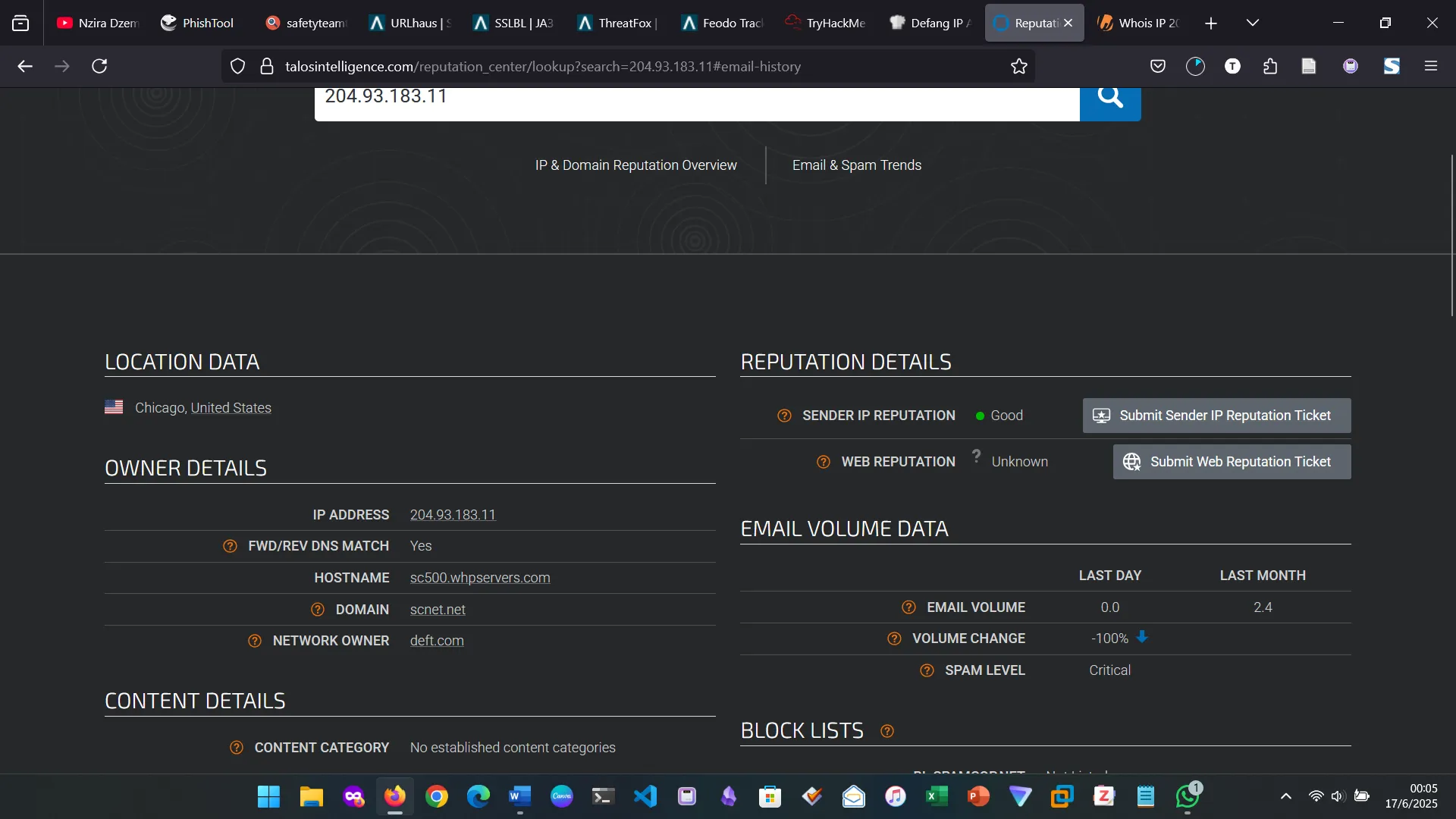
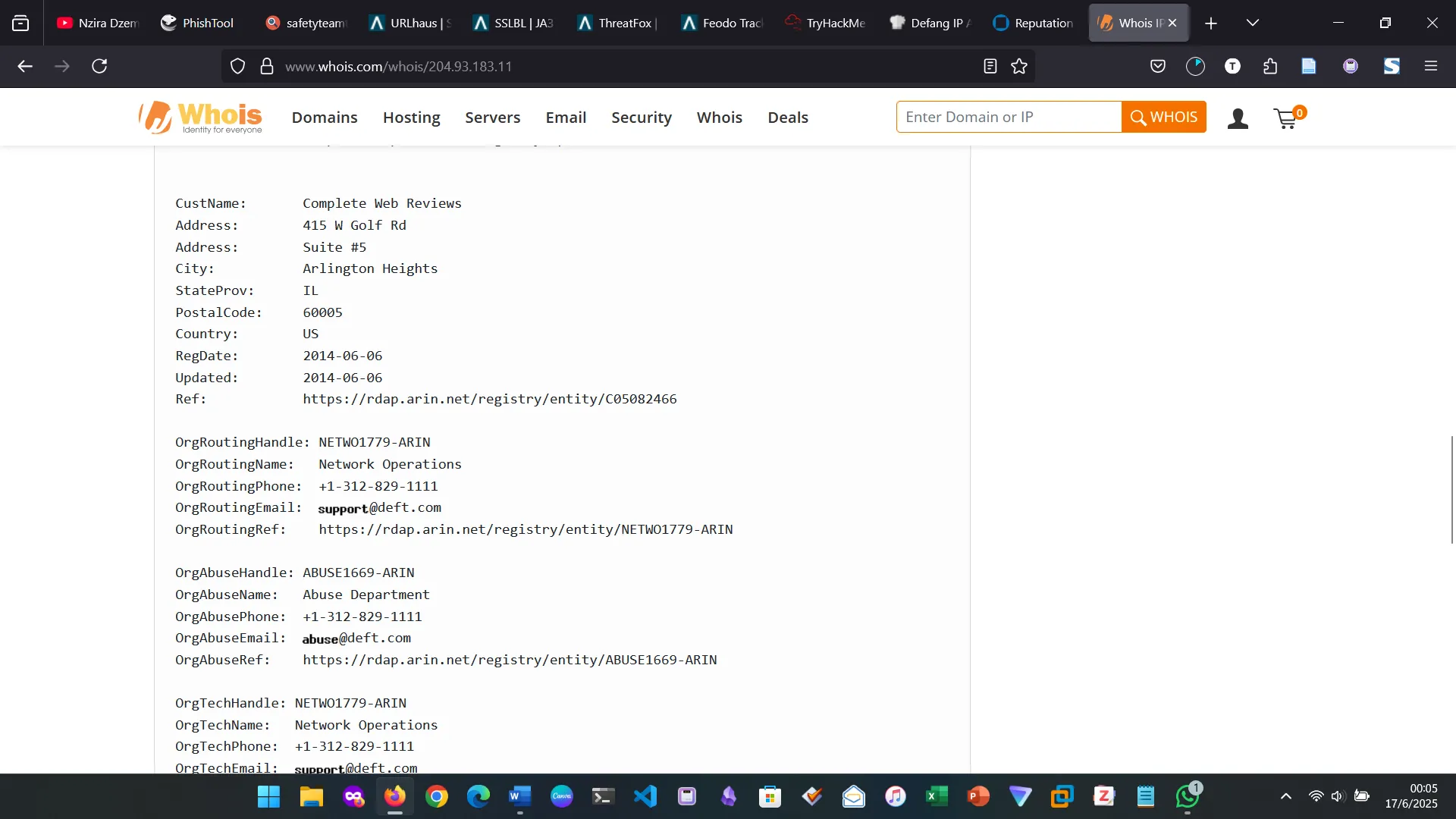
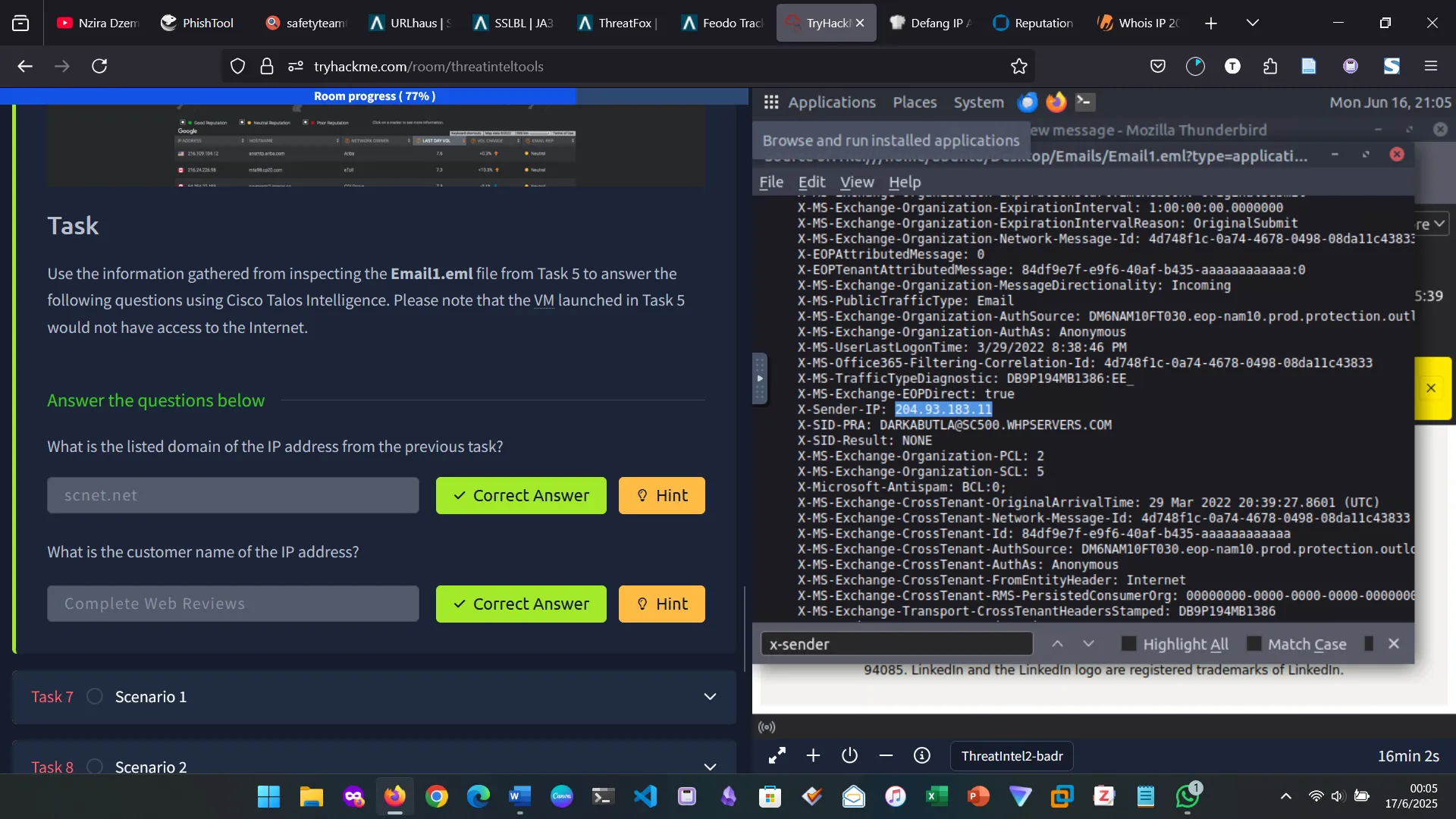
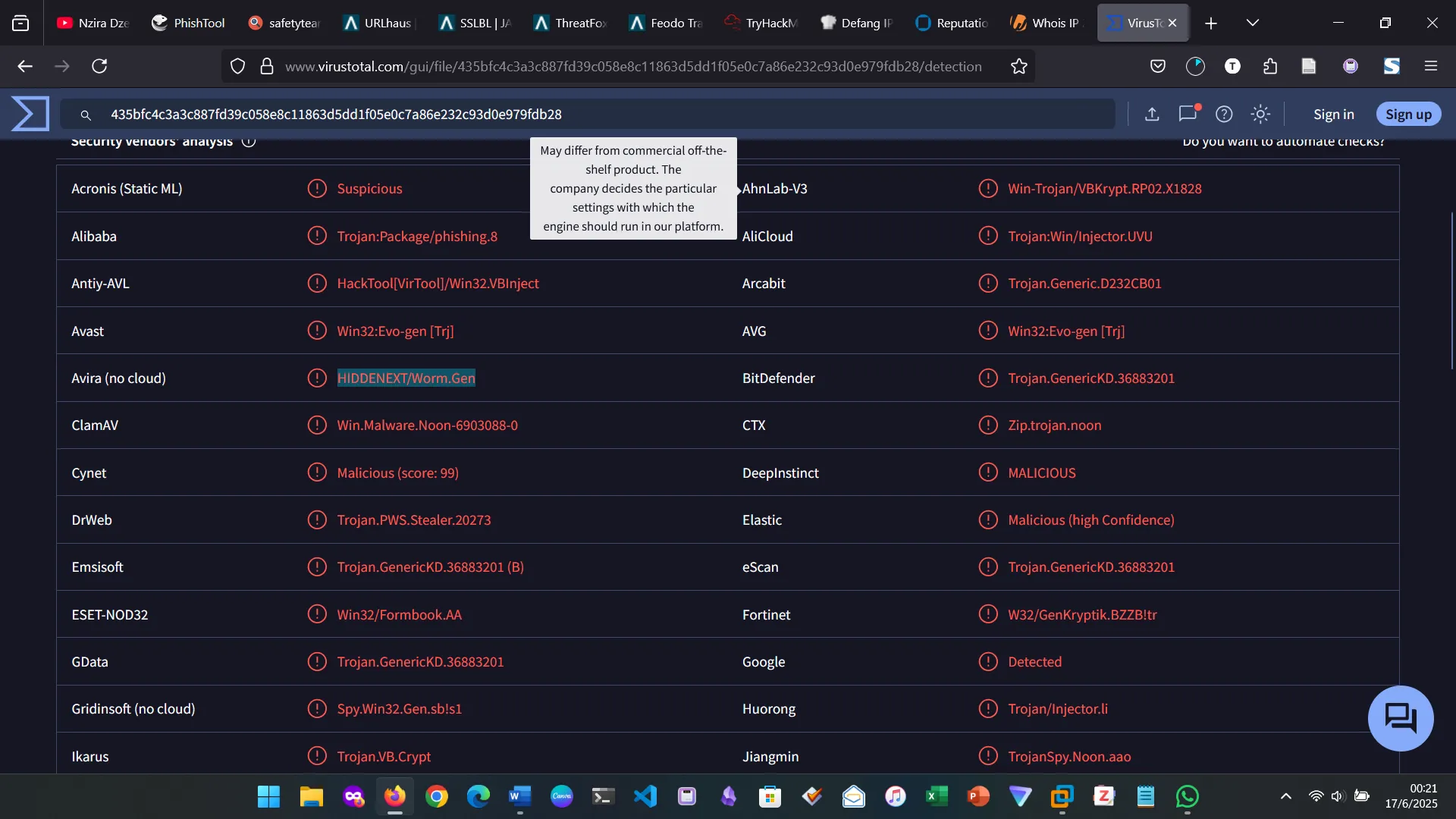
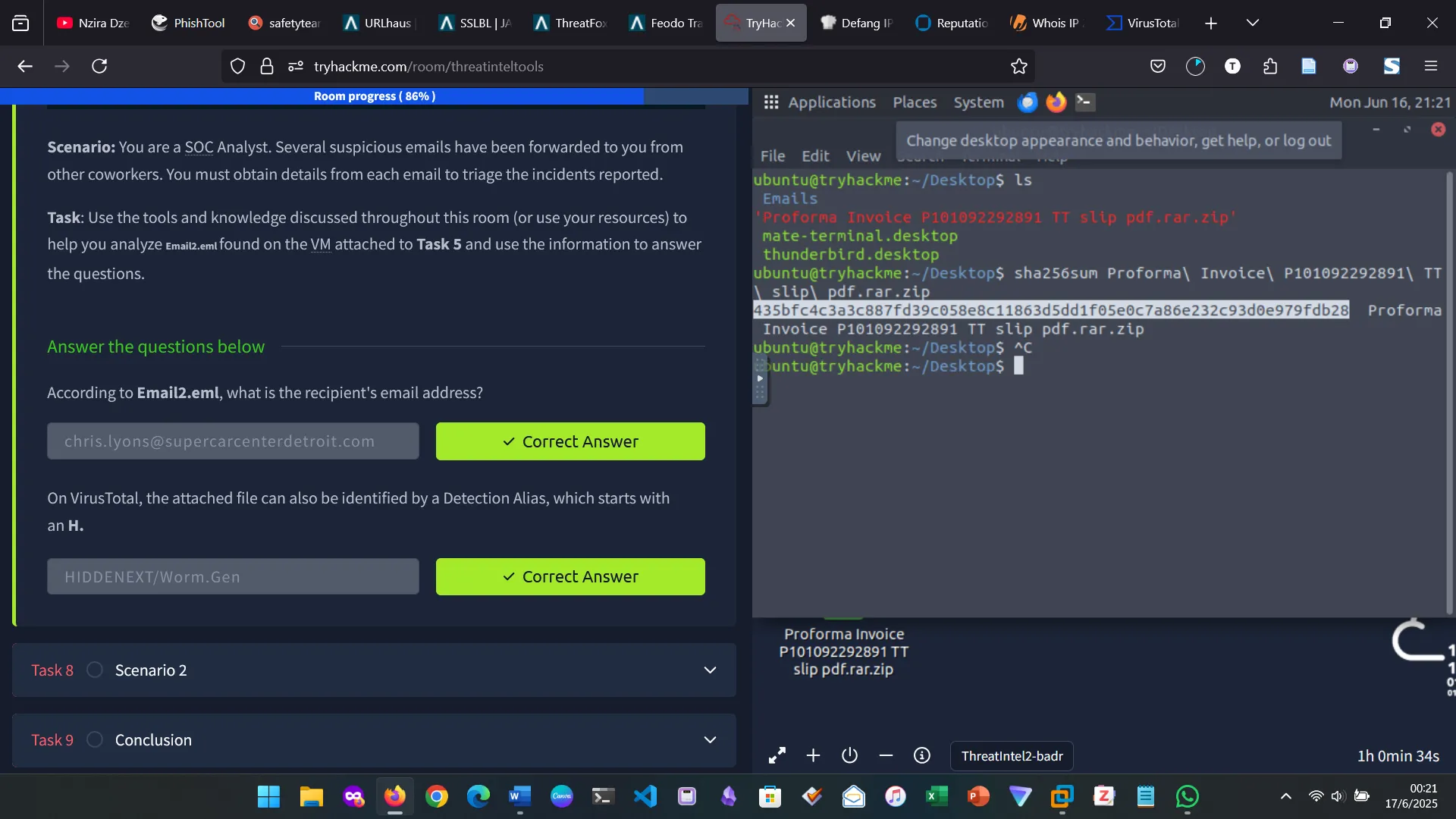
7. SCENARIO 1
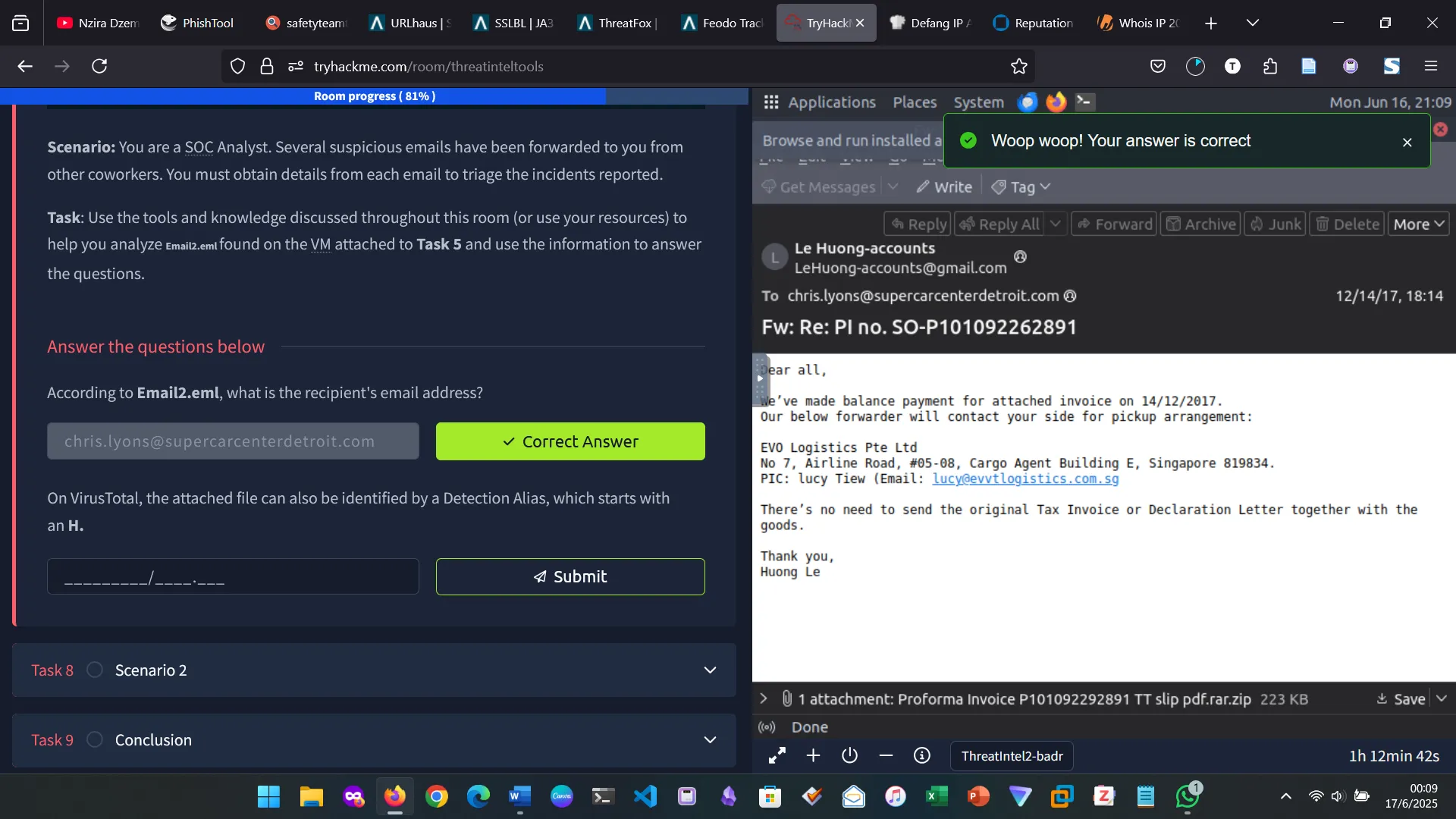
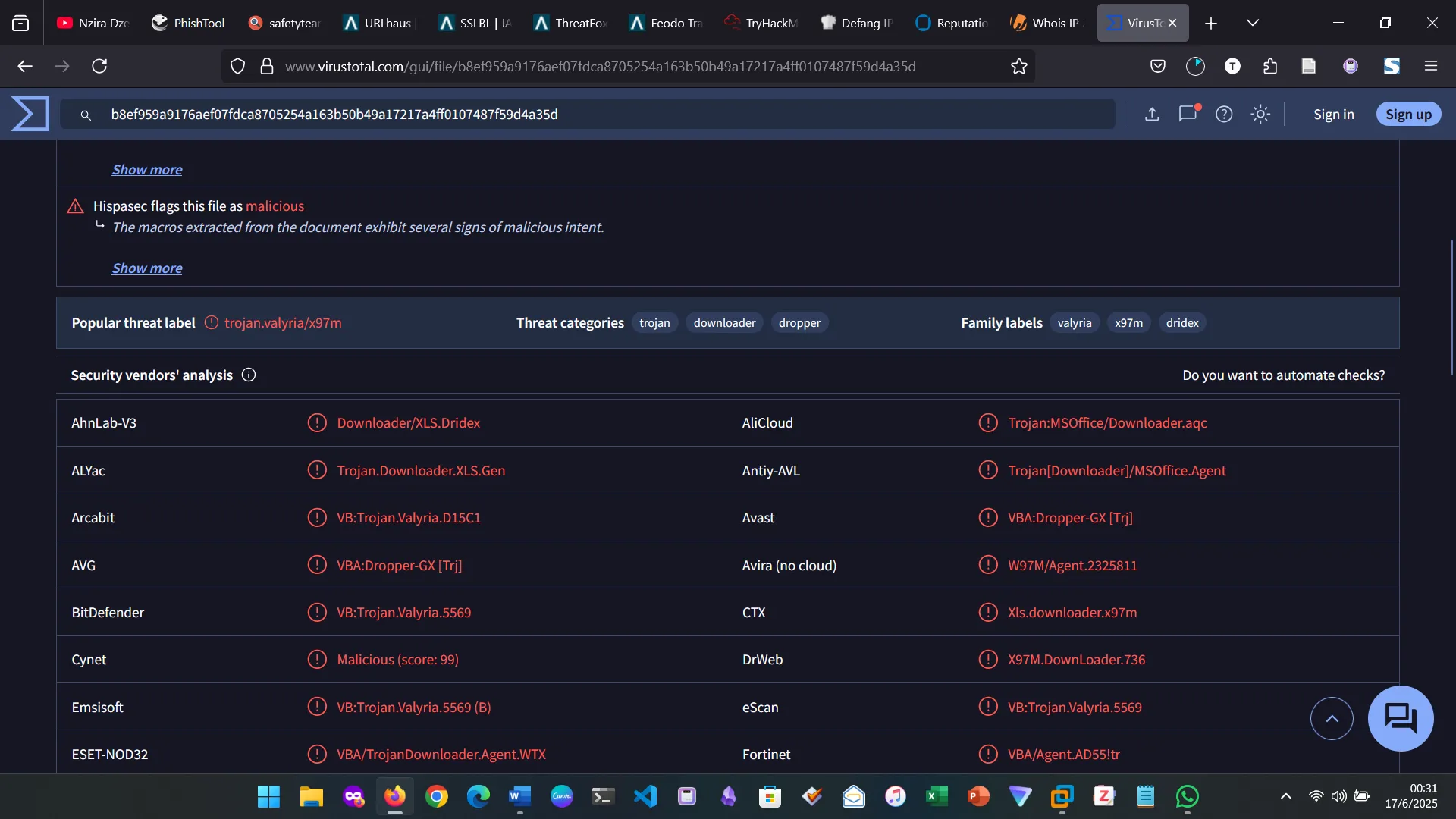
For the second question, first I found the file hash, then used it on virastotal.
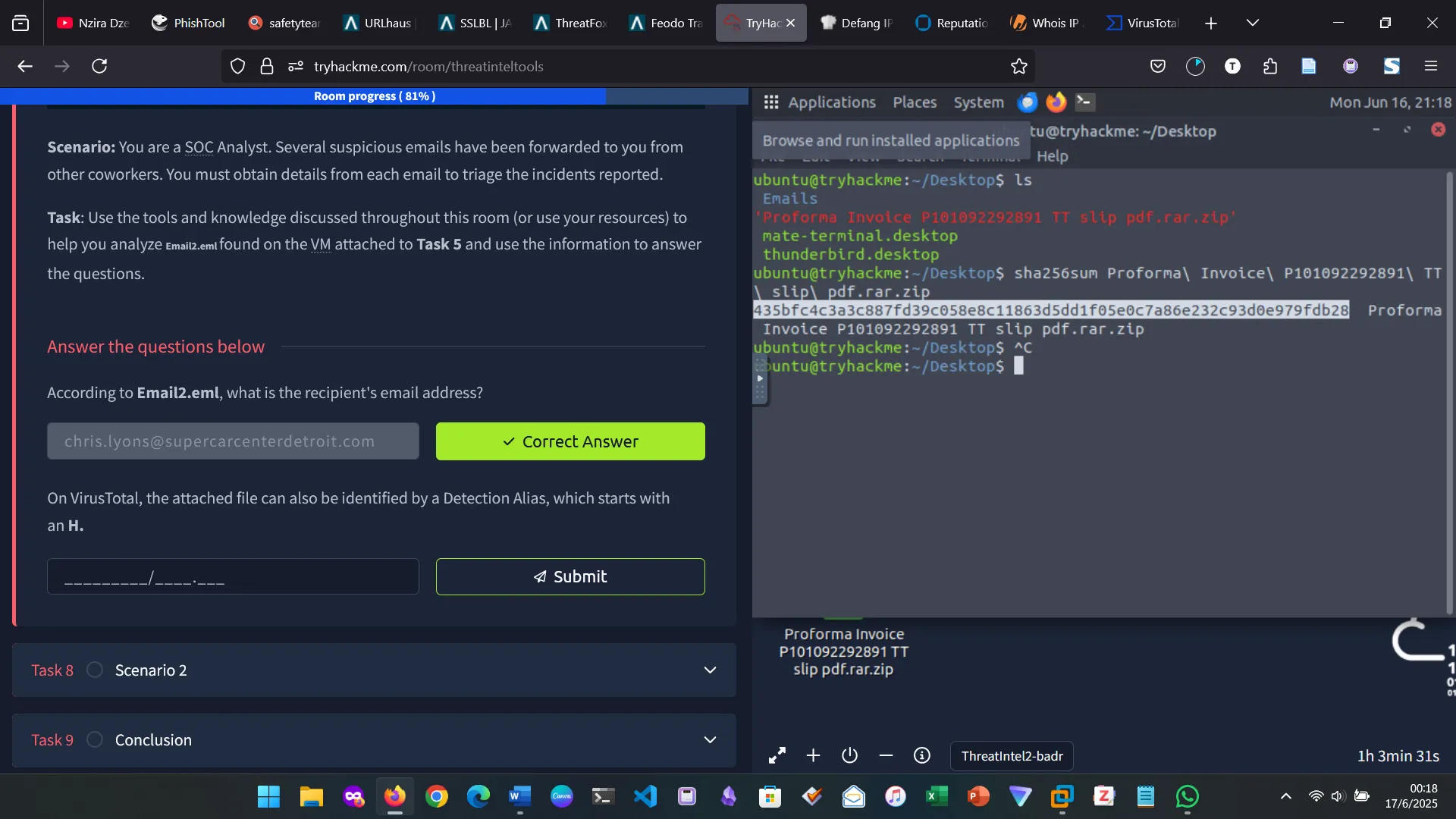
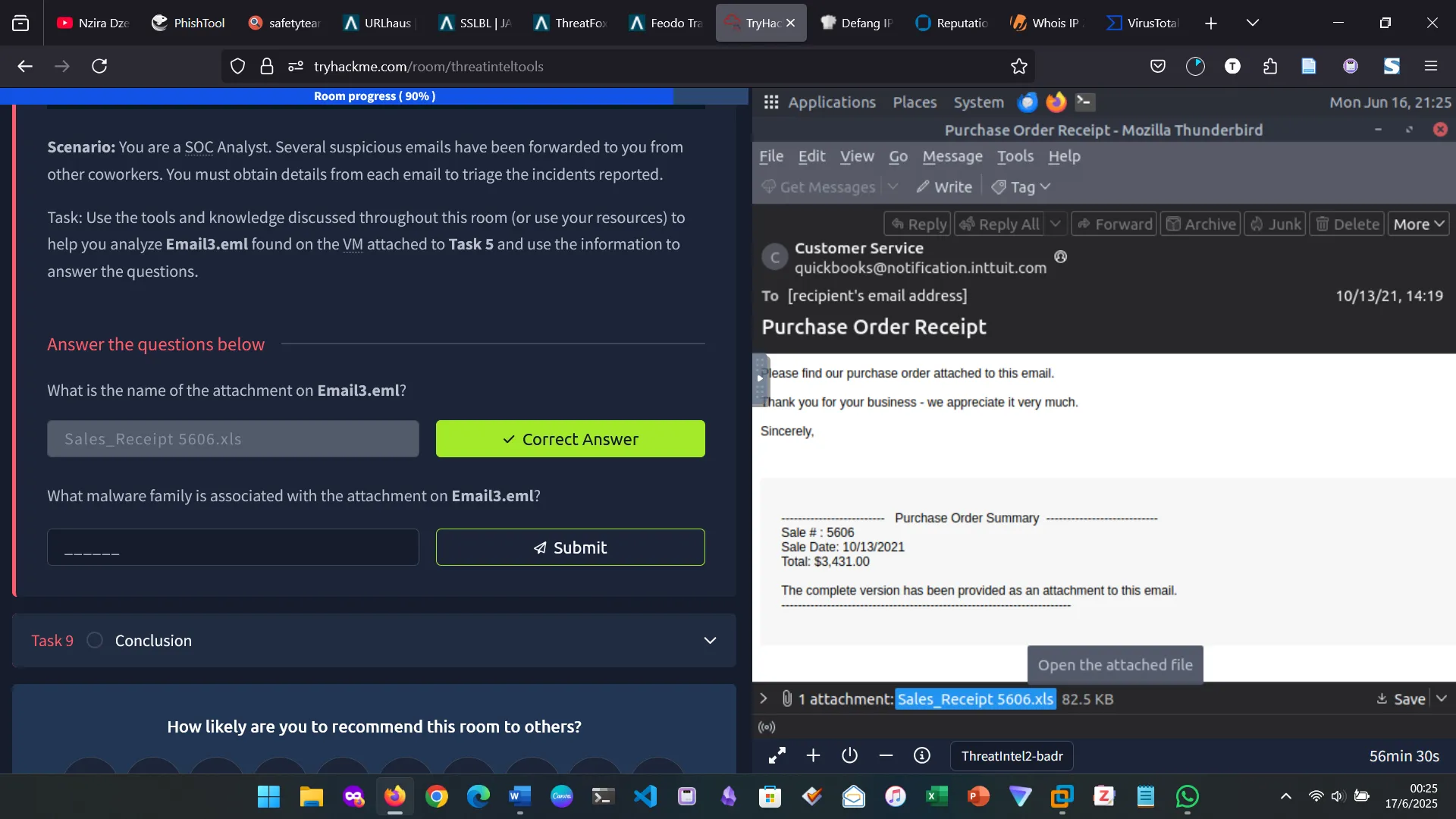
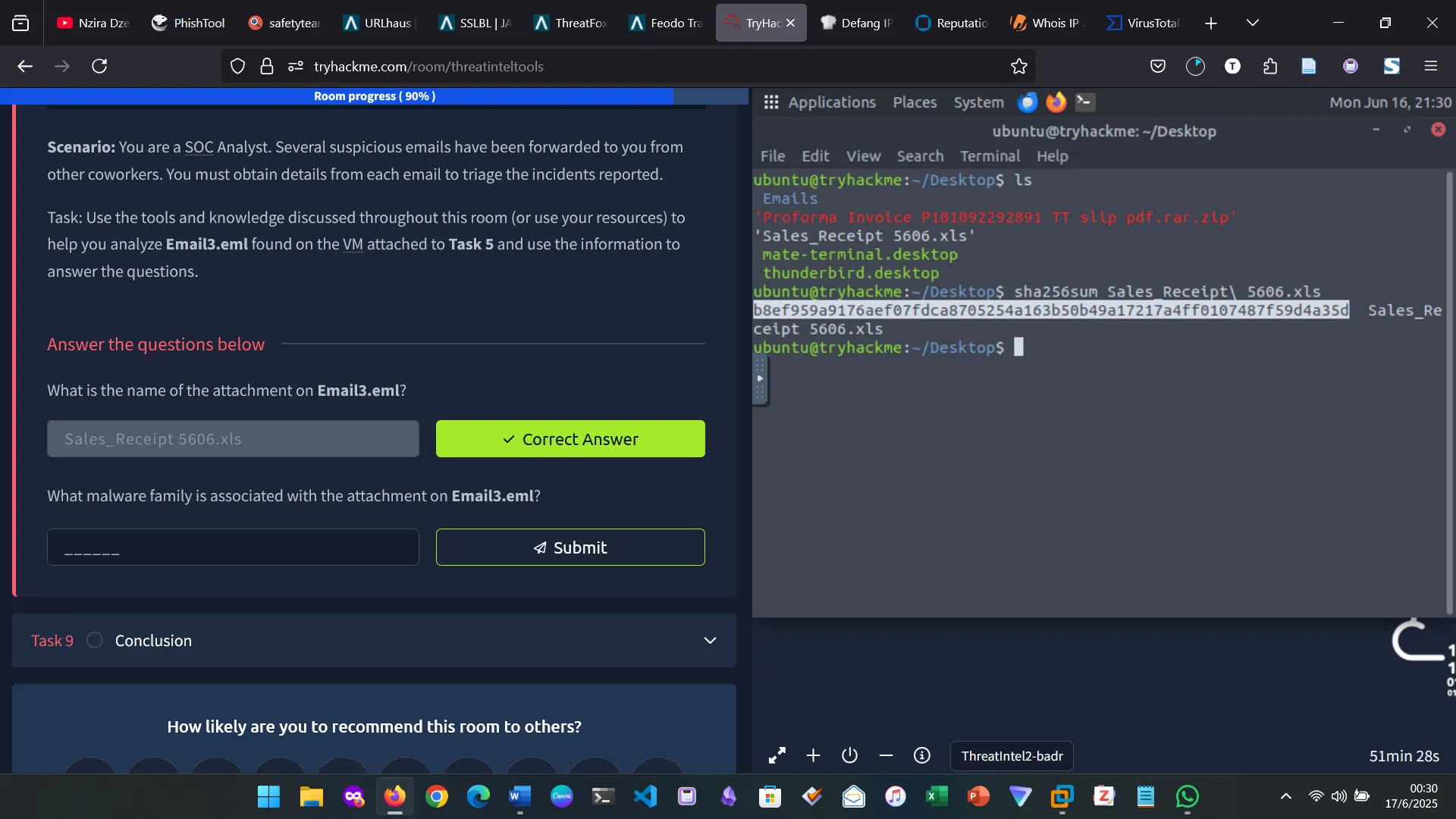
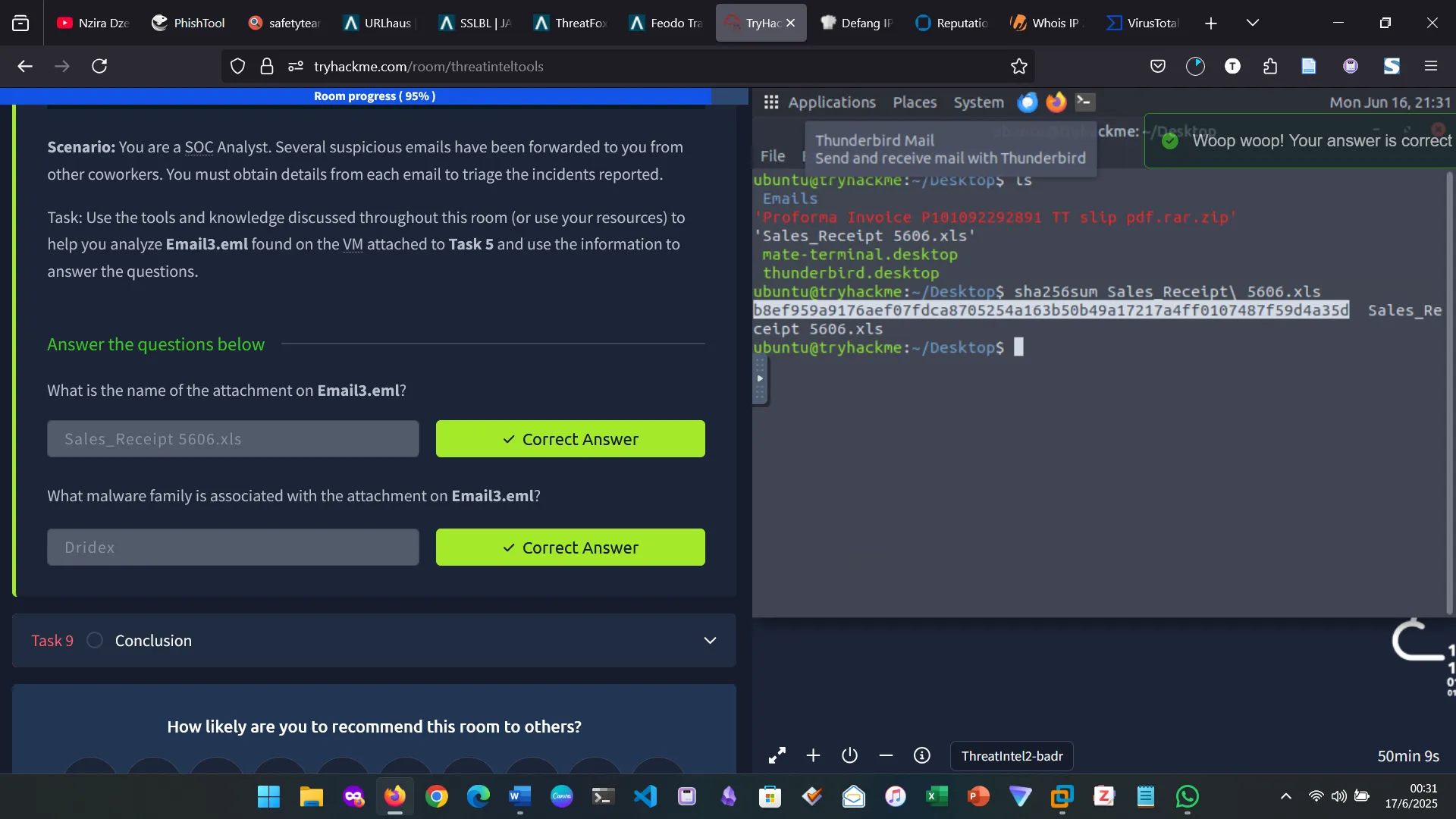
8. SCENARIO 2
9. CONCLUSION
This was an eventful room. I was glad to use a combination of new and existing tools to go through the tasks. The scenarios felt very practical as they were set on actual everyday tools that are used to spread malware. Email. Altogether, a fruitful experience. More knowledge added, and onto next chapters.