1. INTRODUCTION
I completed the WiFi Hacking 101 room on TryHackMe:
https://tryhackme.com/room/wifihacking101
2. KEY TERMS
The module introduced fundamental concepts around WPA2 network security:
- SSID – The name of the wireless network shown when connecting.
- ESSID – A logical SSID shared across multiple access points, e.g., in enterprise environments.
- BSSID – The MAC address of a specific access point.
- WPA2-PSK – Common WiFi security where users connect using a shared password.
- WPA2-EAP – Enterprise authentication using usernames/passwords validated via a RADIUS server.
- RADIUS – A backend authentication server used in enterprise networks.
3. AIRCRACK-NG
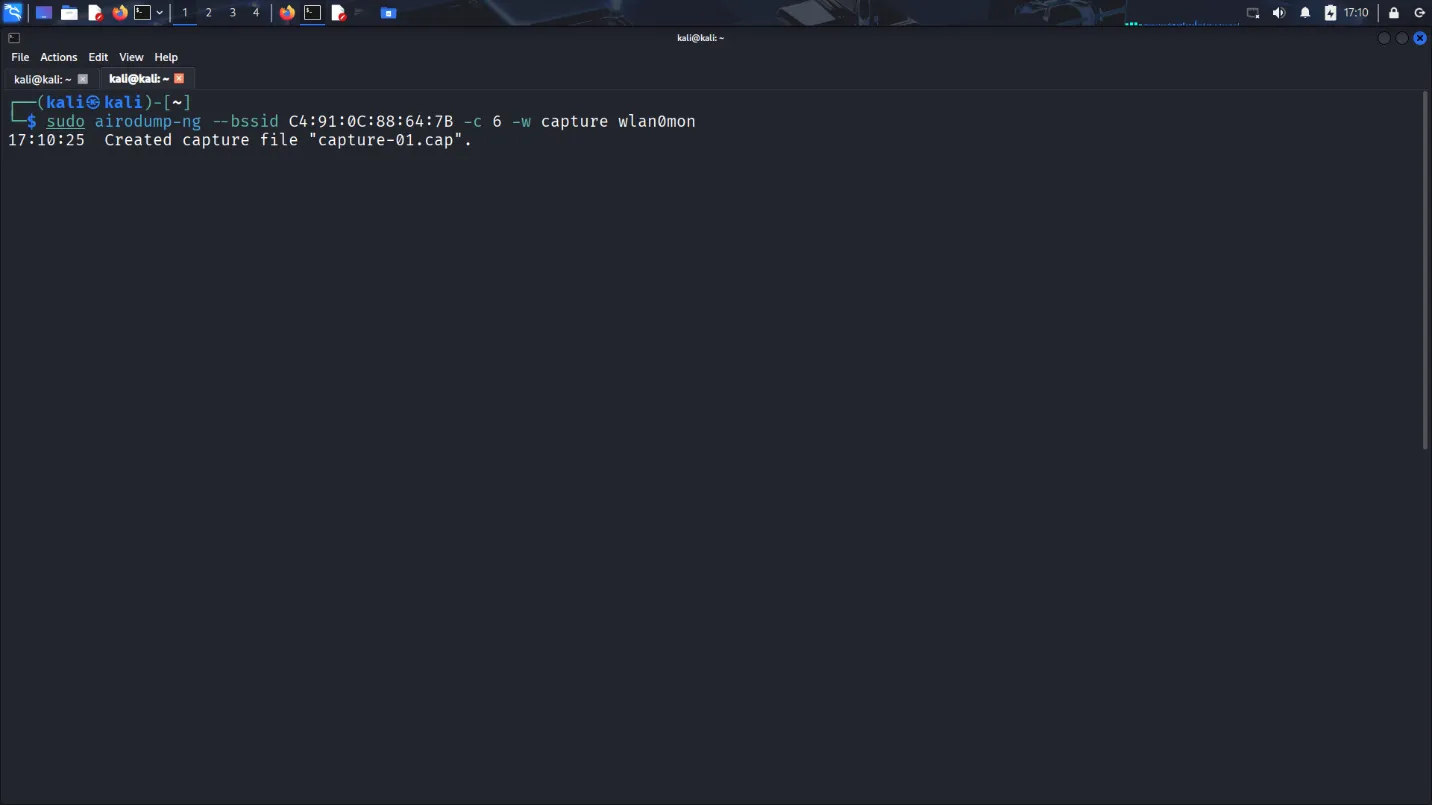
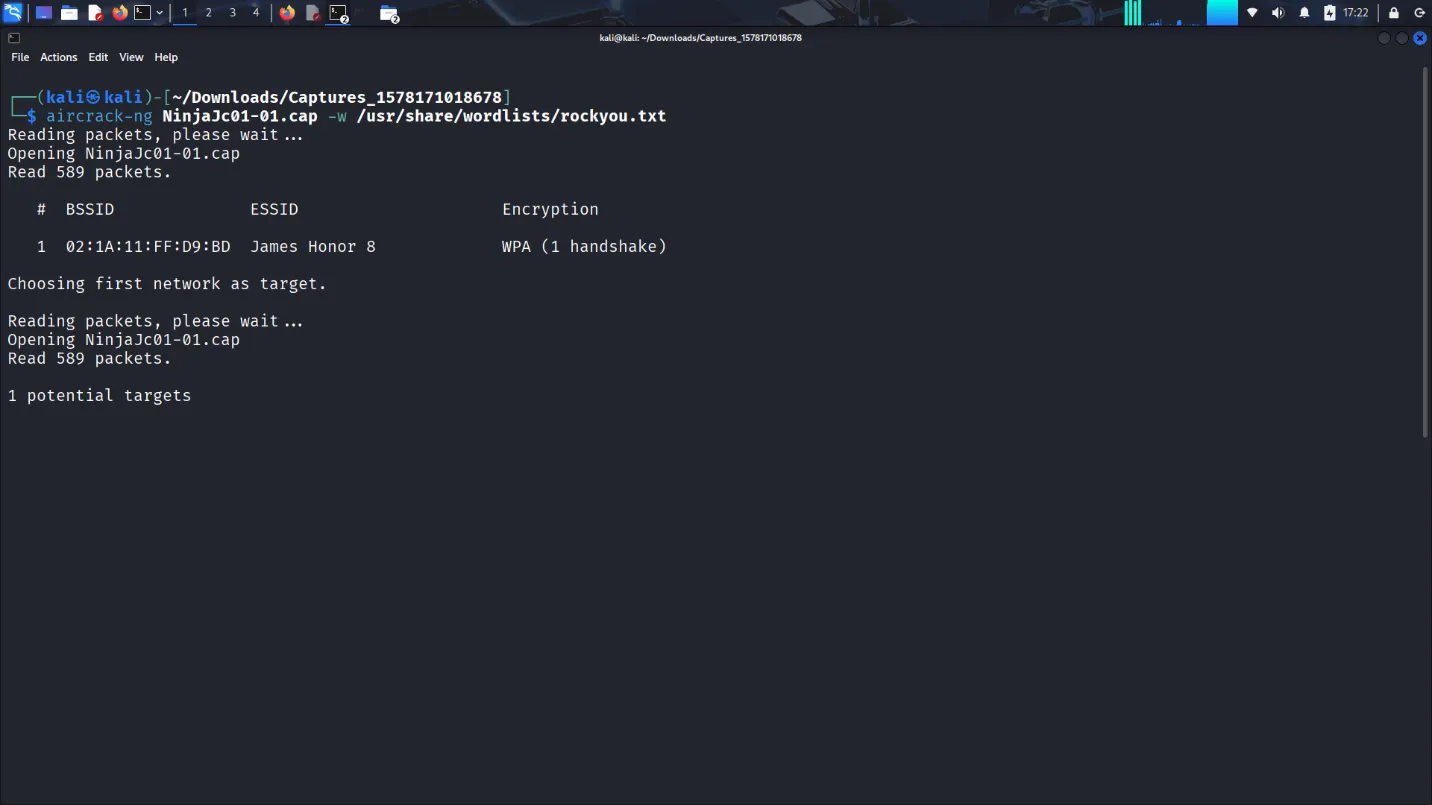
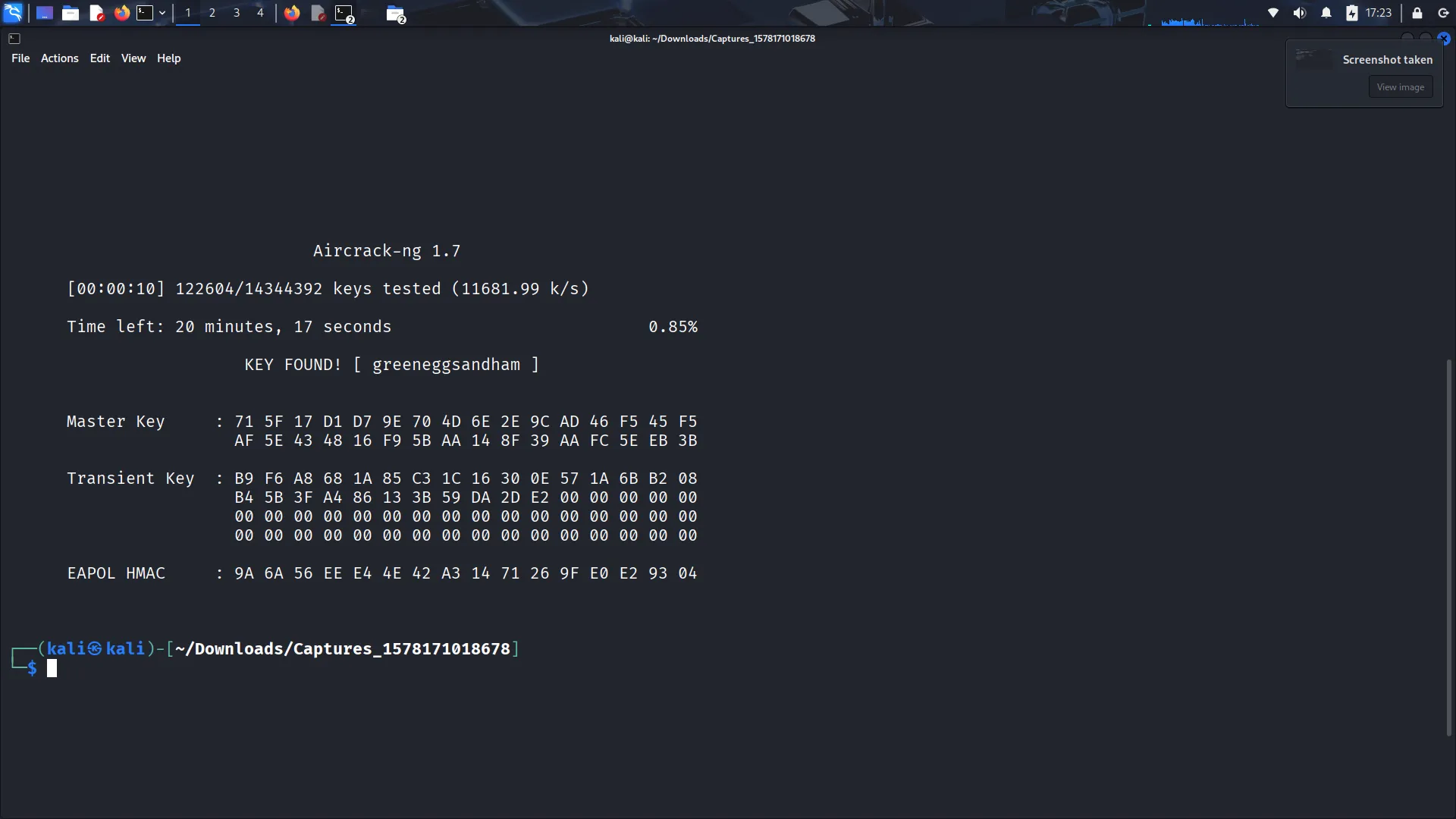
We used the Aircrack-ng suite to carry out a WPA2 cracking attack. Key tools included:
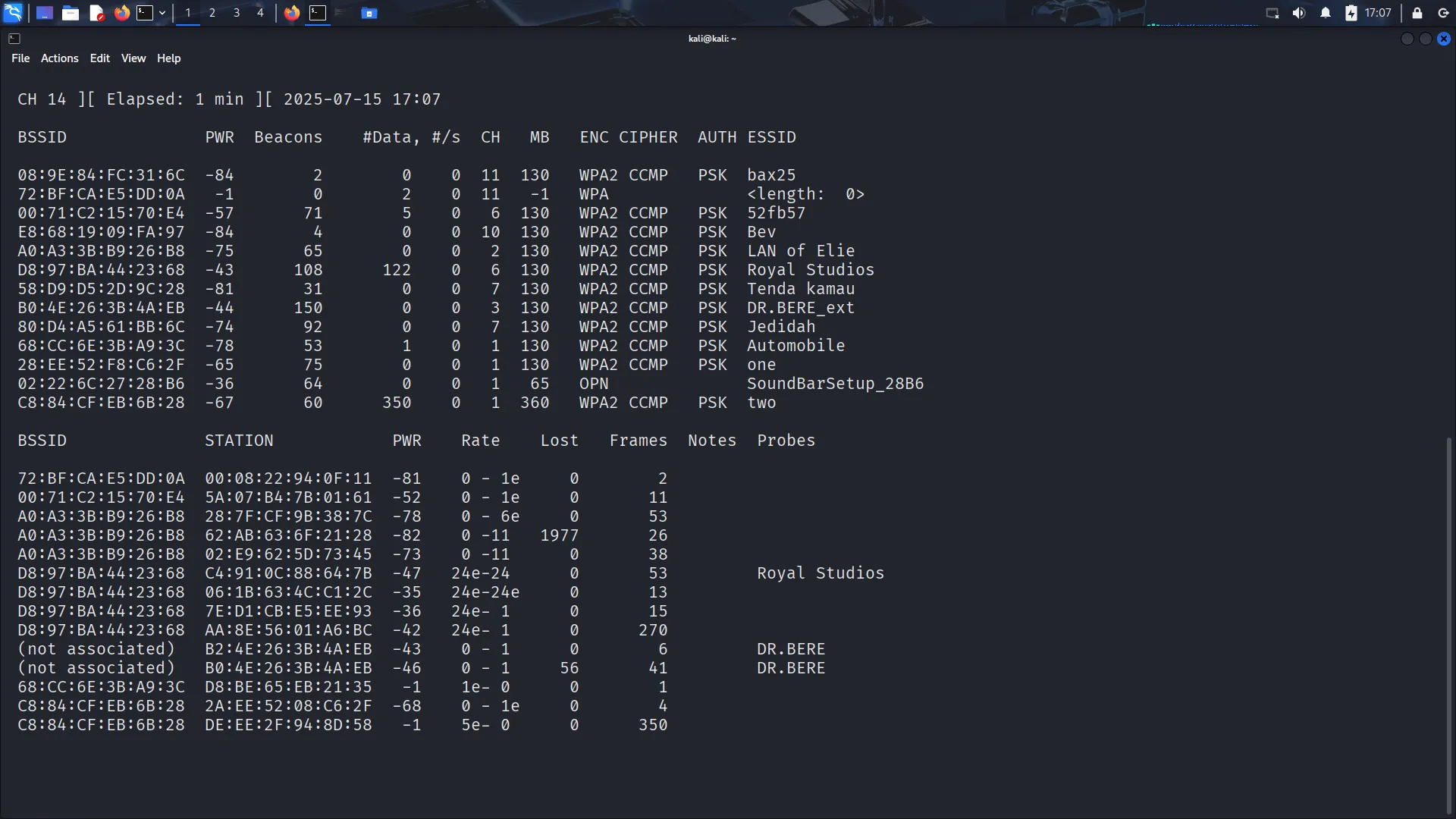
airmon-ng– enables monitor modeairodump-ng– captures WiFi trafficaircrack-ng– attempts to crack WPA handshakes using a wordlist
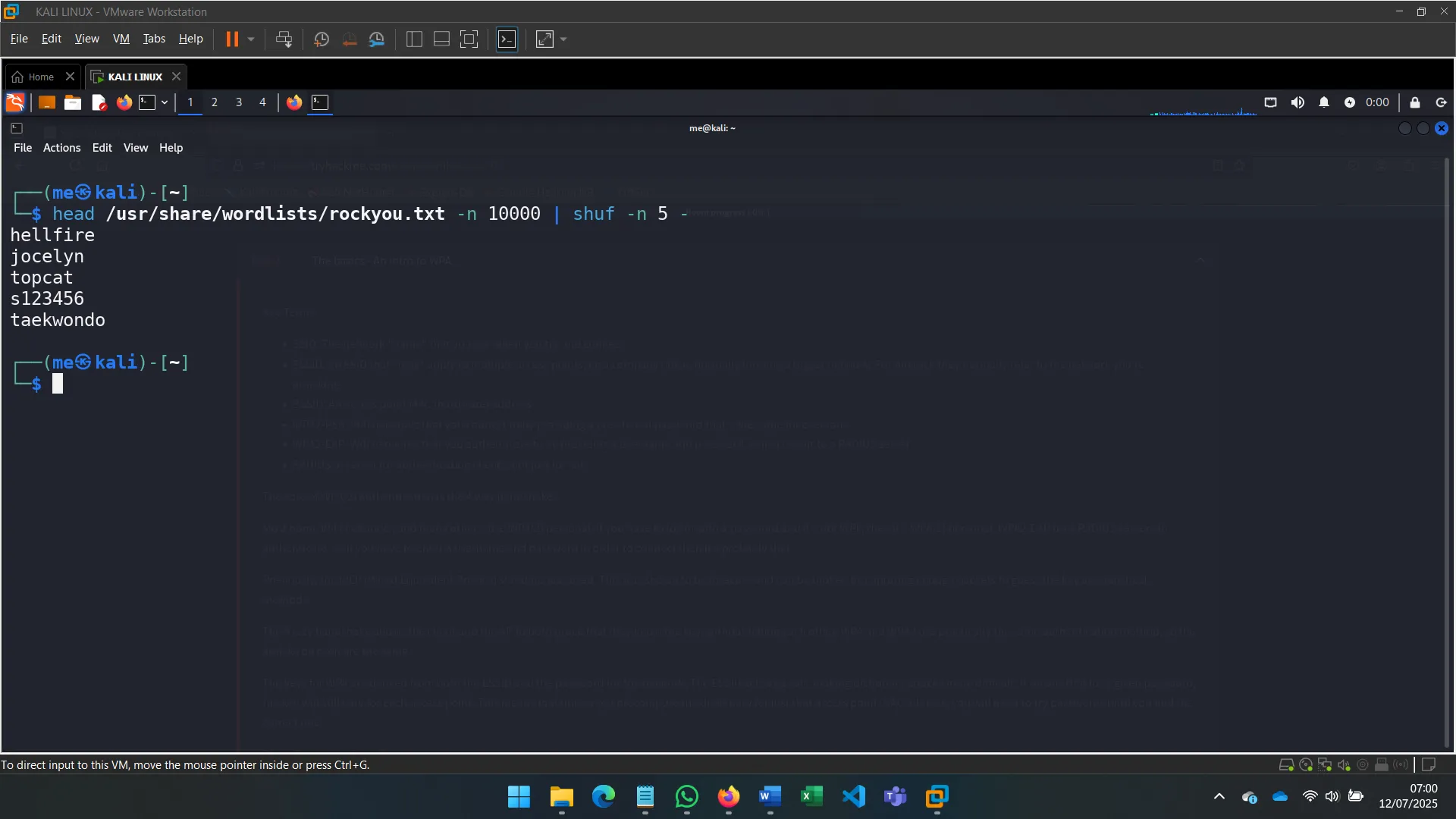
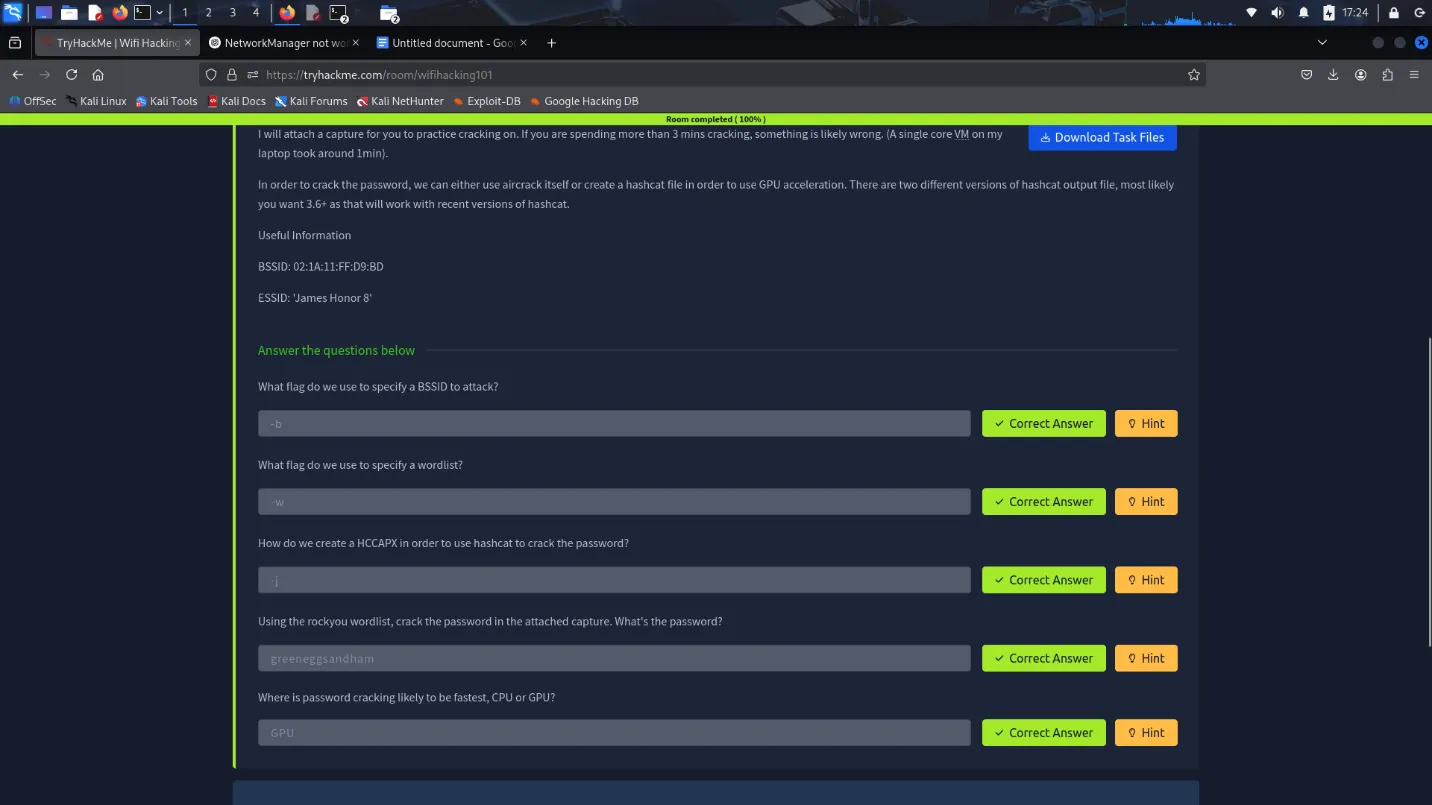
I started by generating a few random passwords from the rockyou.txt wordlist.
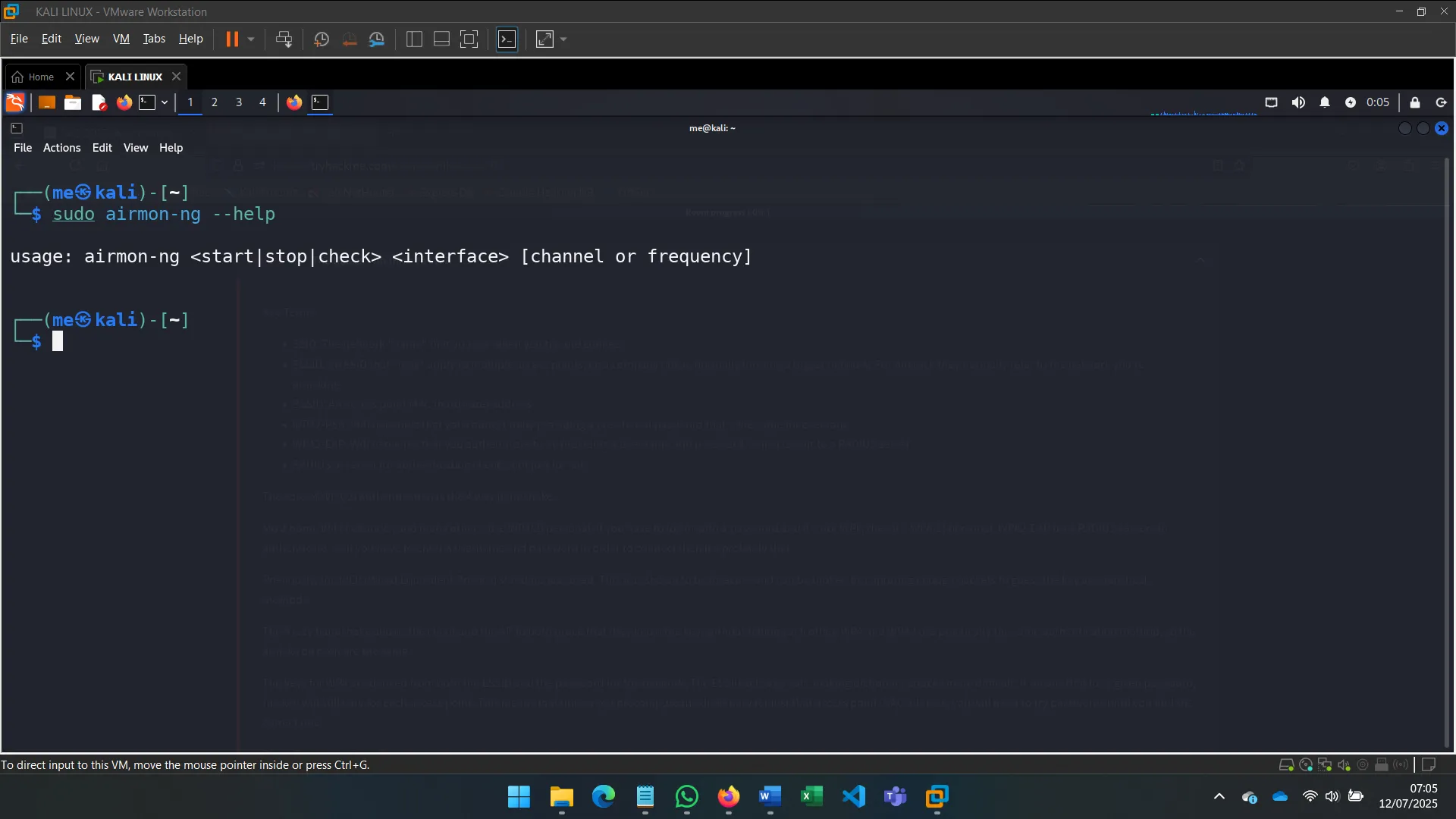
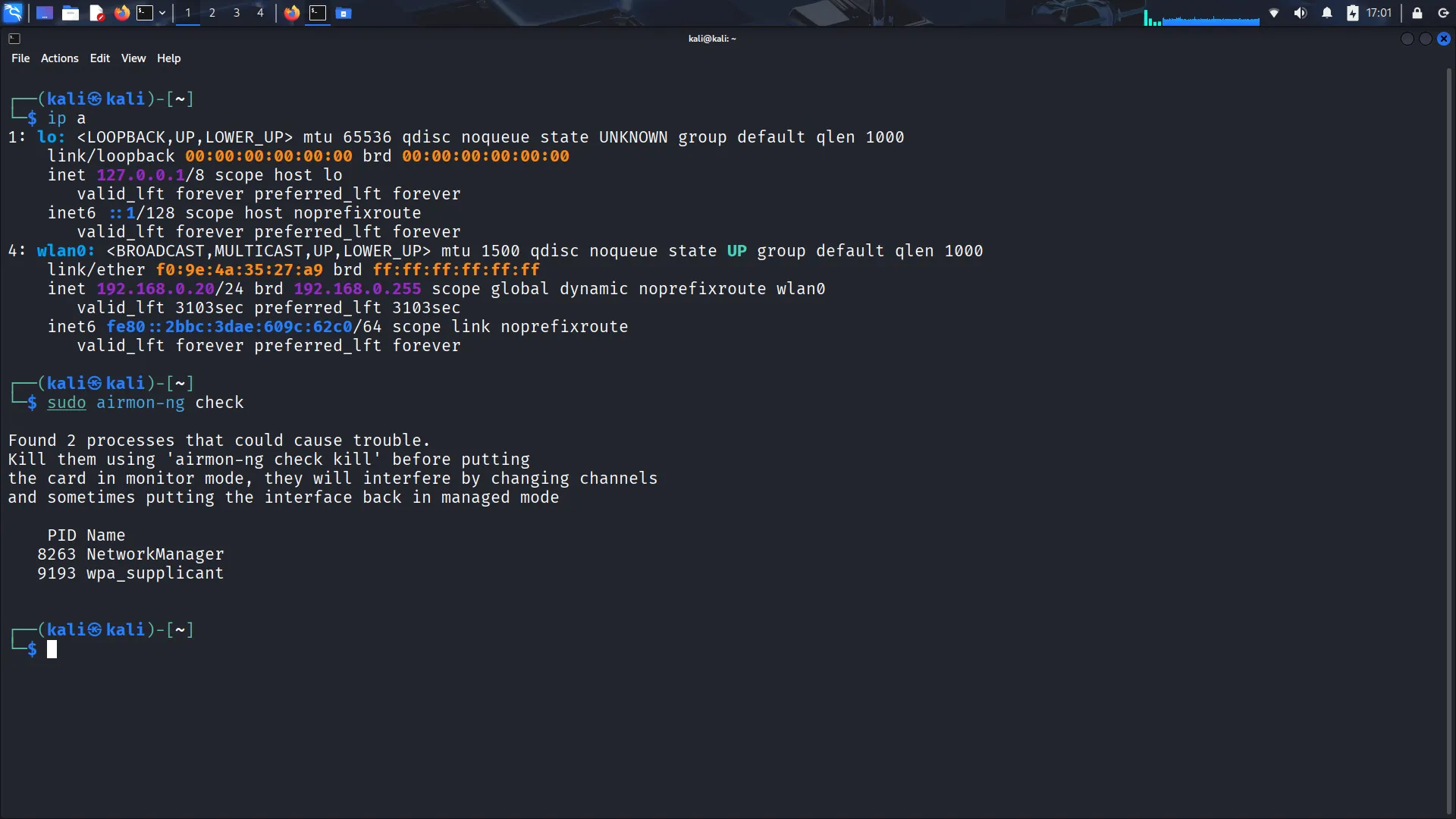
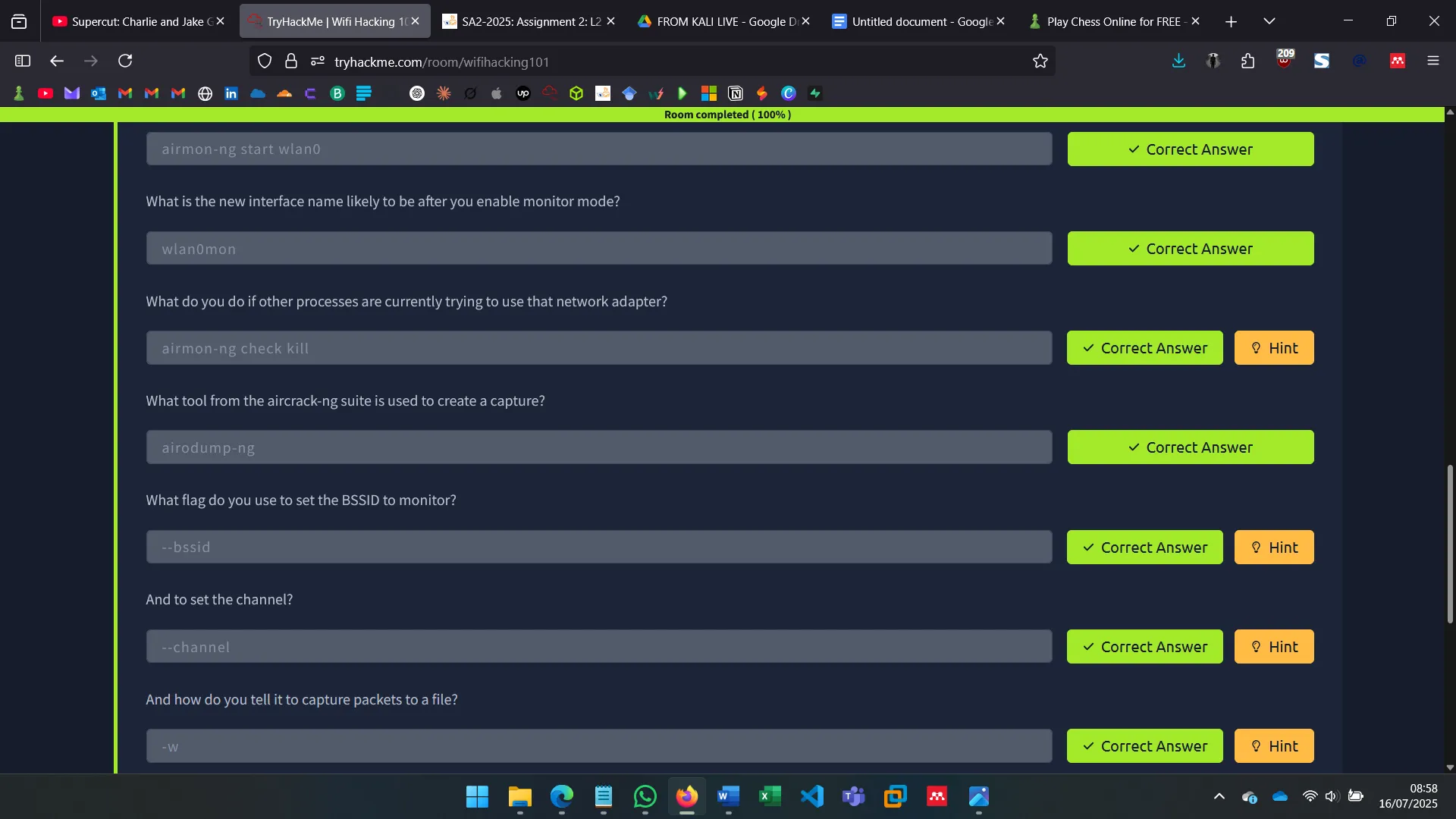
How do you put the interface “wlan0” into monitor mode with Aircrack tools?
(Answer: airmon-ng start wlan0)
PRACTICAL
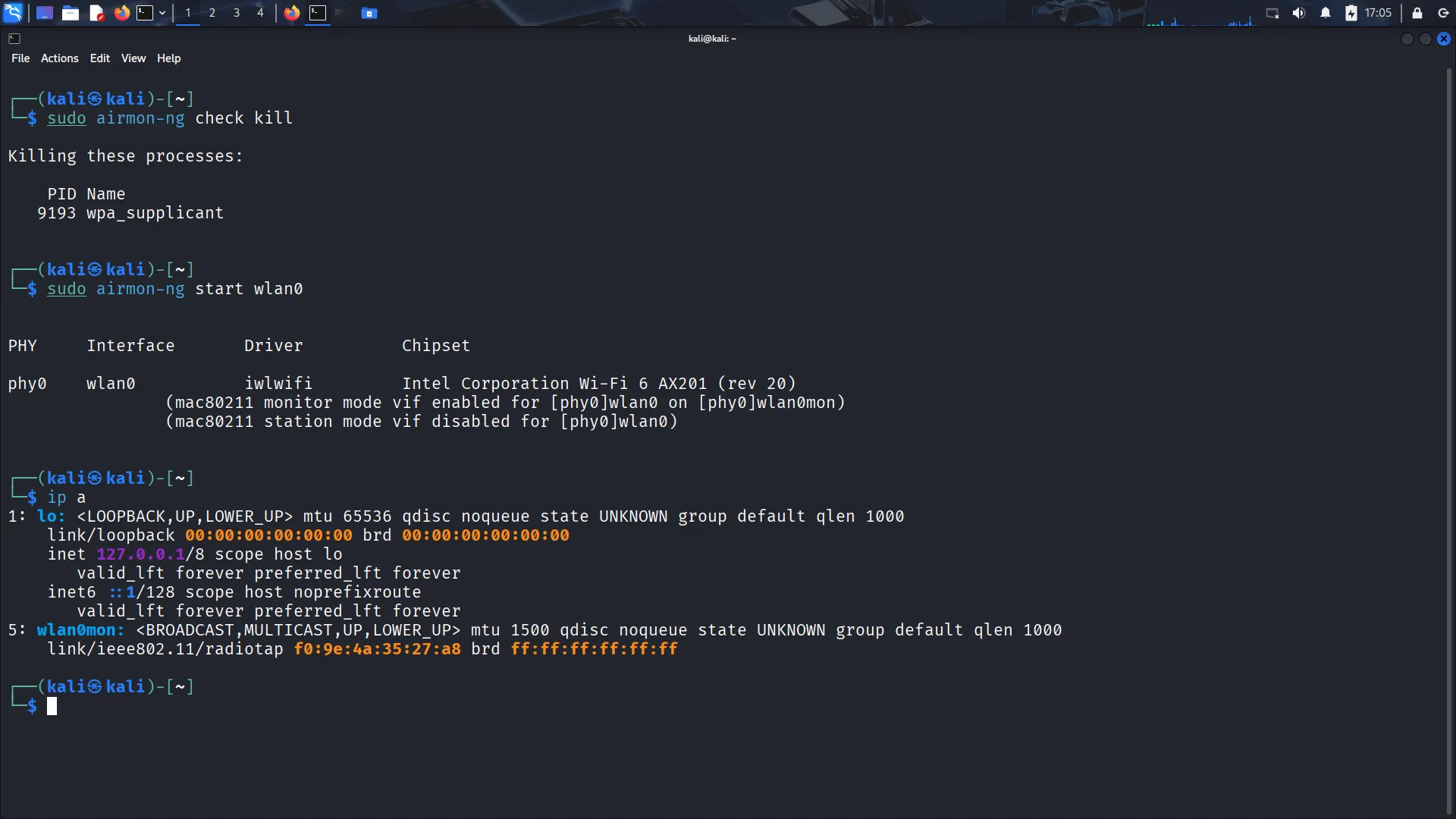
The cracking process required running tools on a system with a compatible wireless card in monitor mode, which wasn’t possible in a VM. I had to boot a Linux live USB to complete the tasks. The steps involved capturing a WPA handshake, then using a wordlist to crack it using aircrack-ng.
4. CONCLUSION
Security becomes more fascinating when you understand how common technologies can be exploited. We use WPA2 daily on phones and routers without ever thinking about the risks. This was an insightful introduction into wireless network vulnerability and ethical hacking.