1. INTRODUCTION
The Web Requests module on HackTheBox is a practical dive into how the client-server model works. It explores the HTTP protocol, different request/response methods, status codes, and how attackers may manipulate these. The module emphasizes both HTTP and its secure counterpart, HTTPS.
2. HTTP
HTTP communication consists of a client requesting a resource and the server responding with it. The default port is 80, but this may vary depending on configuration.
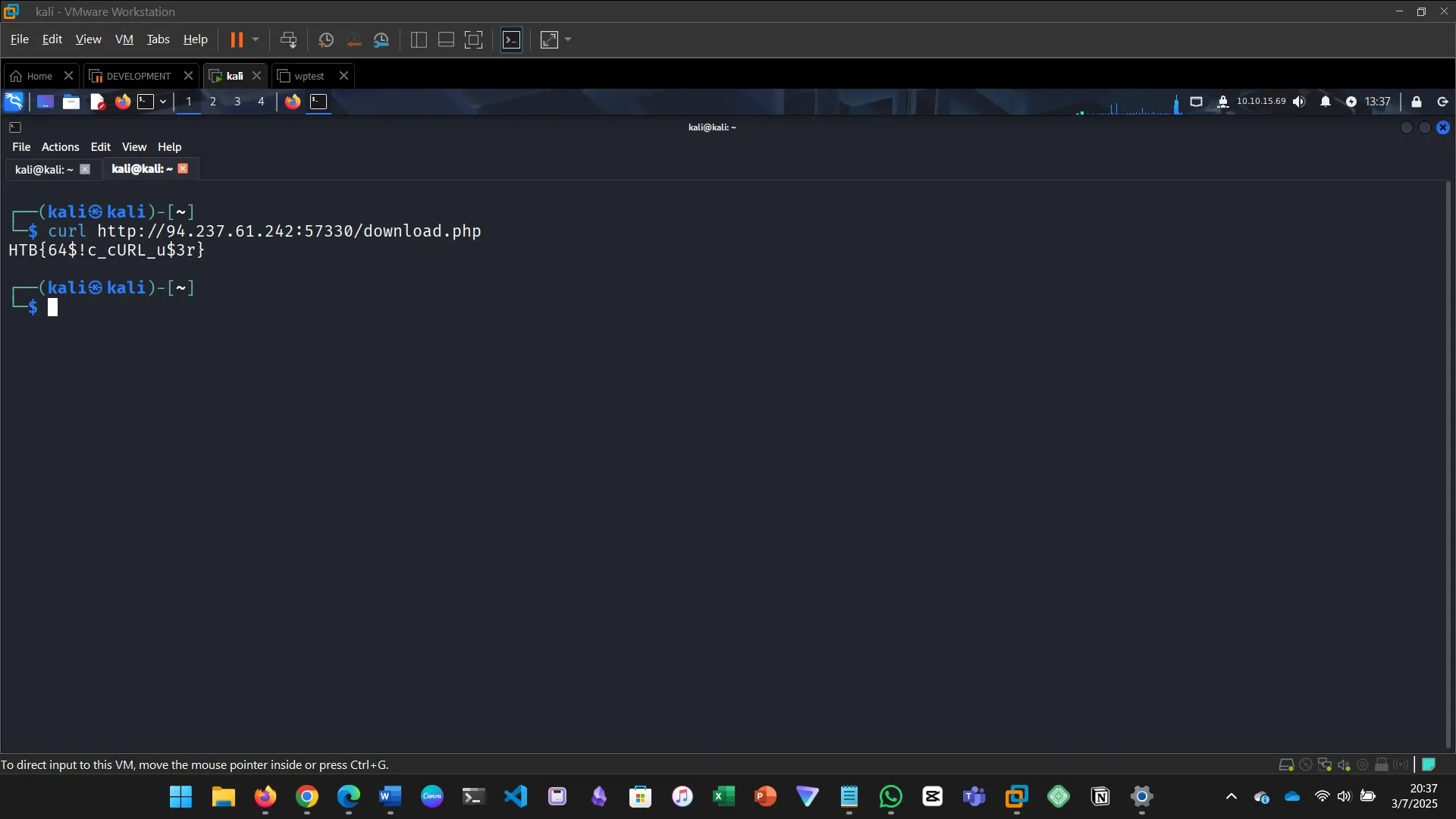
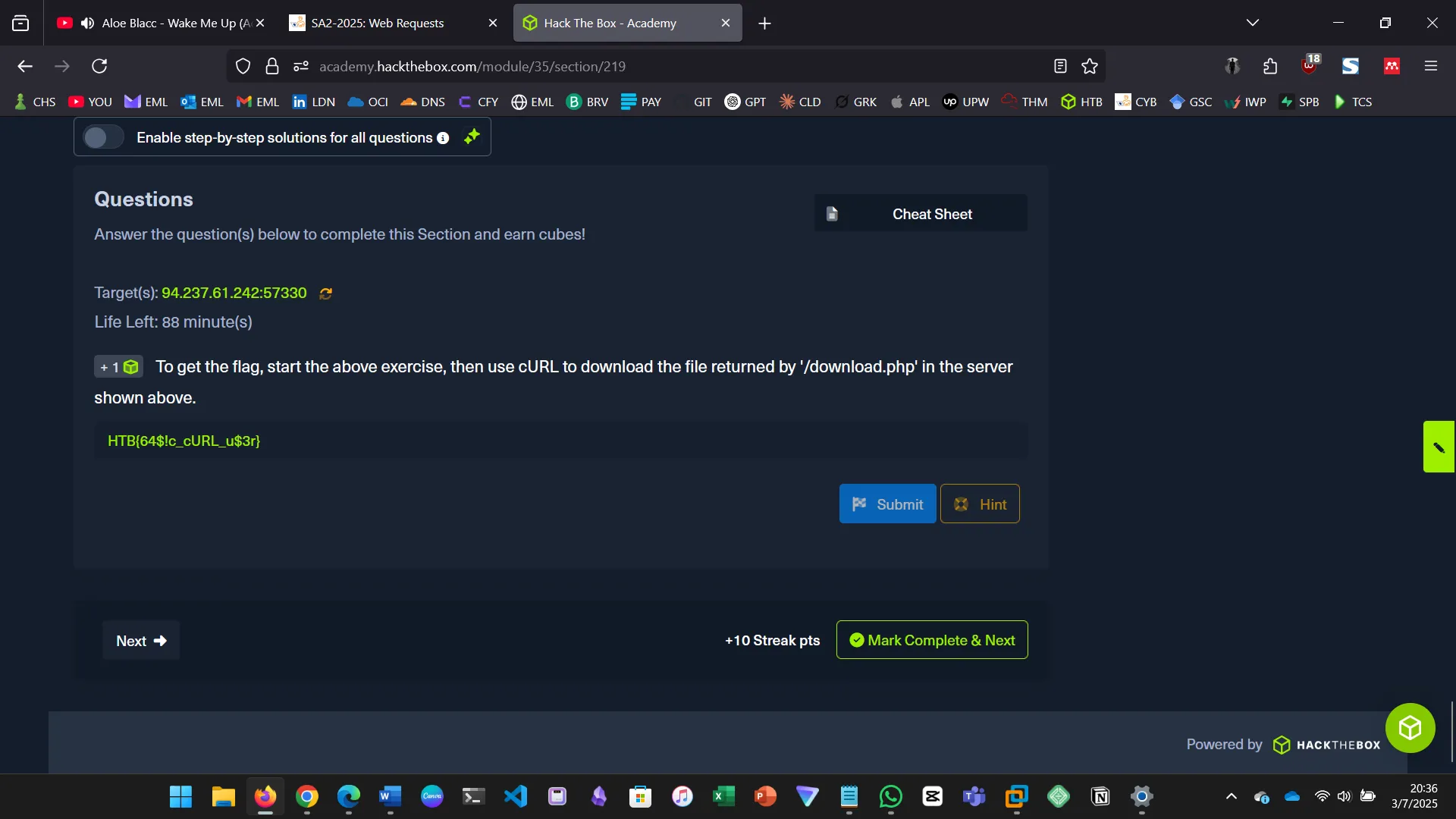
To get the flag, start the exercise and use cURL to download the file from /download.php.
3. REQUESTS AND RESPONSES
HTTP requests come from the client (e.g., browser or cURL), while responses are served by the server. Requests include methods, URLs, parameters, headers, and optional data.
What is the HTTP method used while intercepting the request?
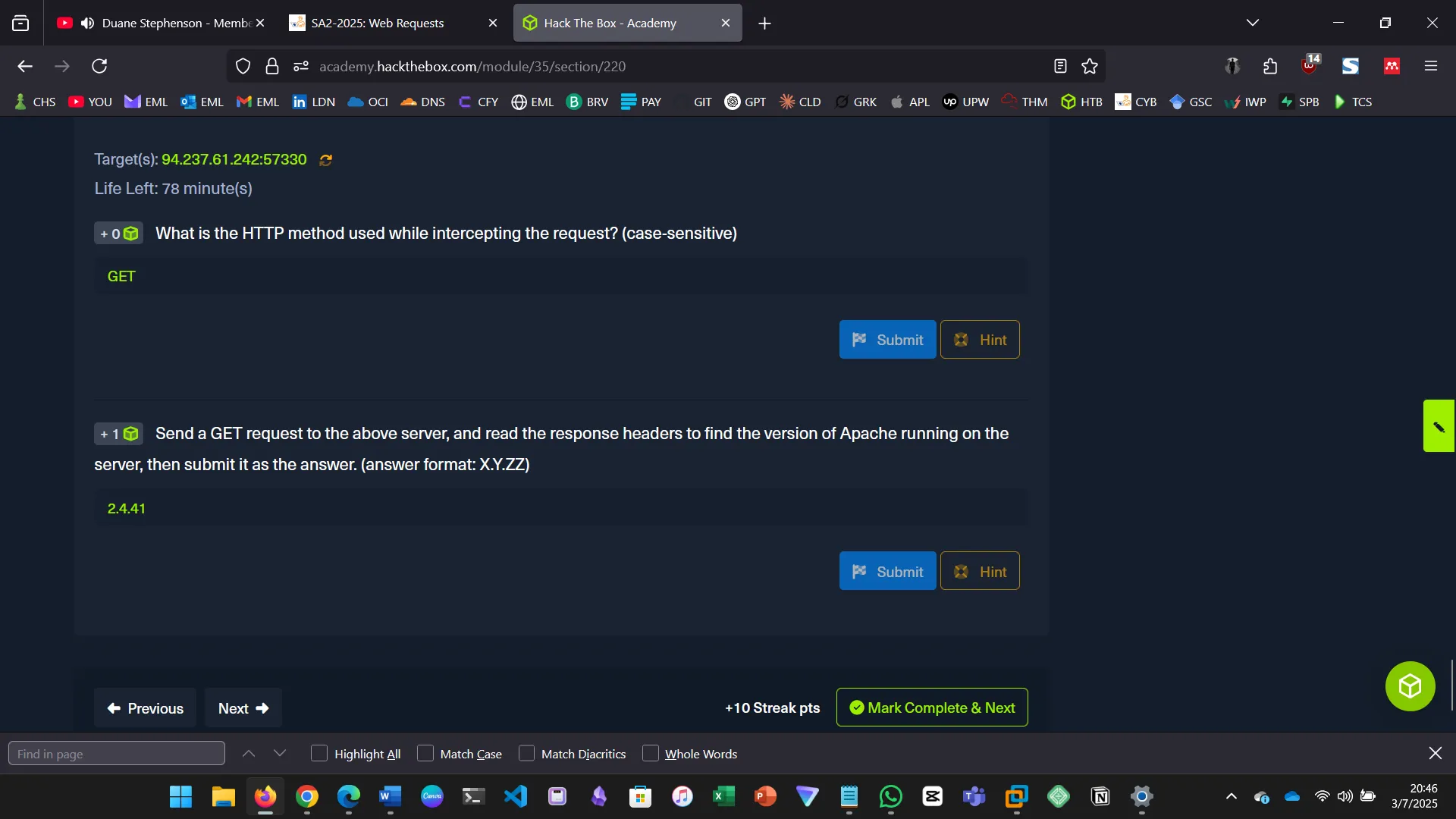
4. HTTP HEADERS
Send a GET request and inspect the response headers to determine the version of Apache running.
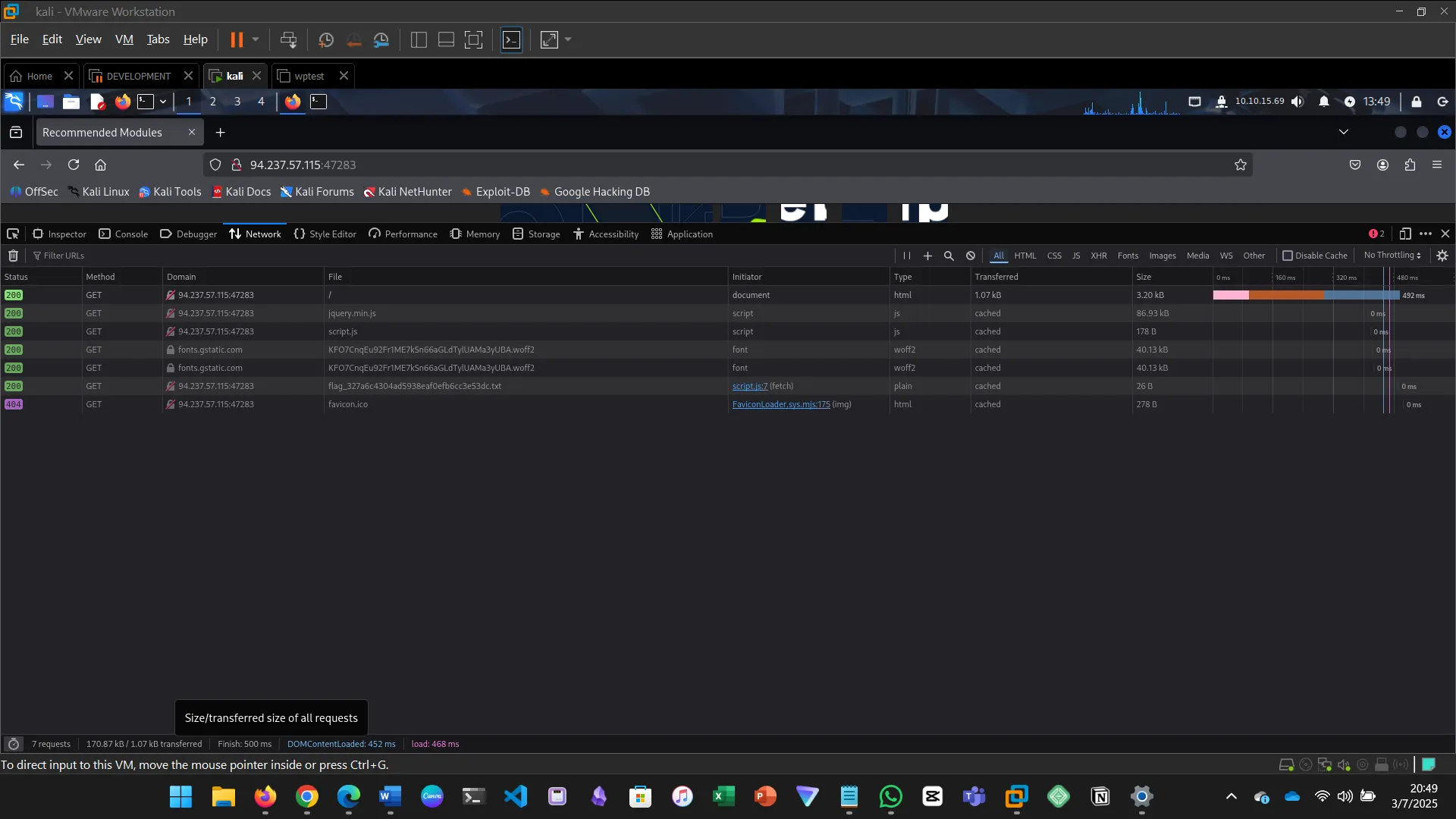
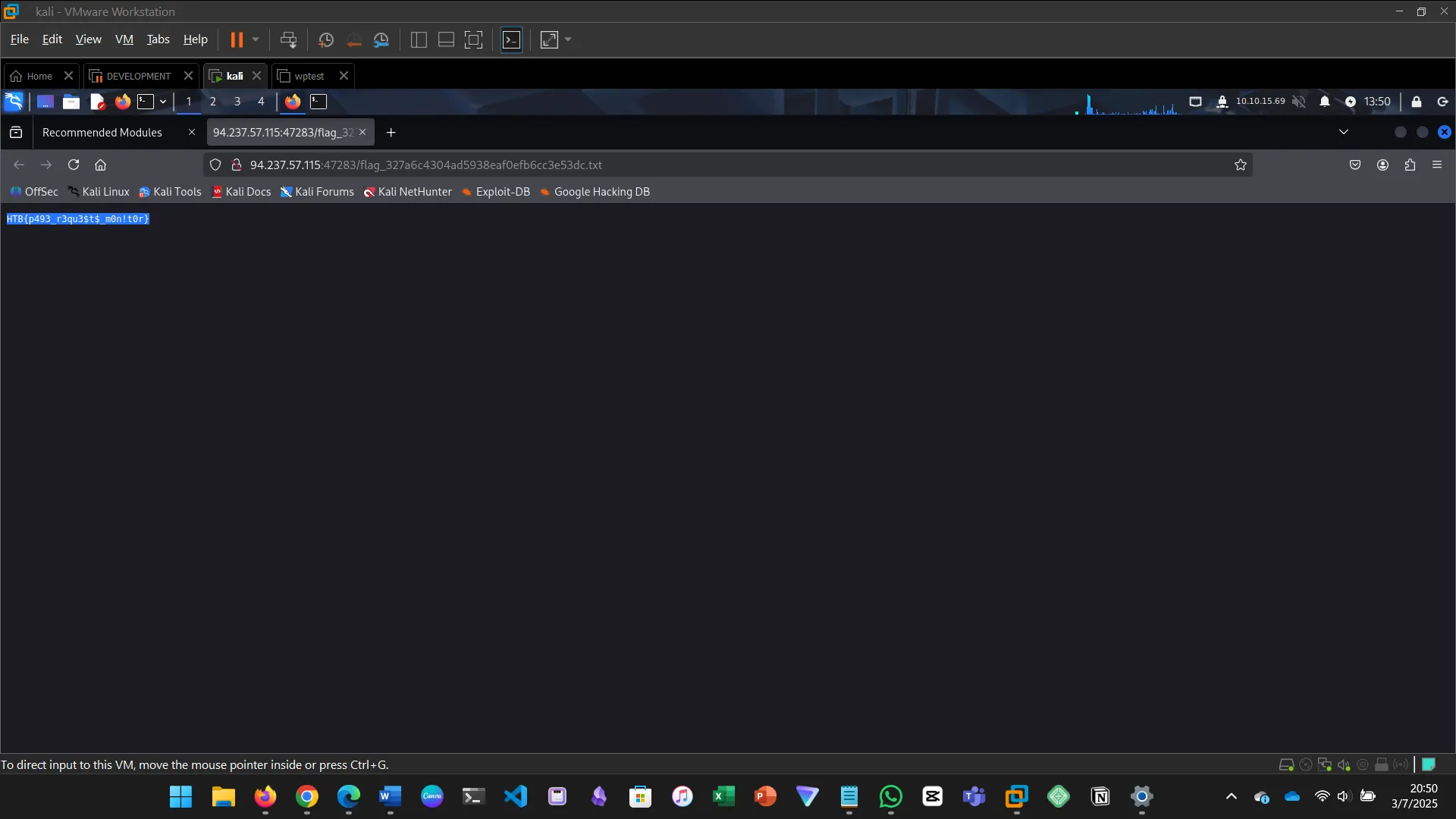
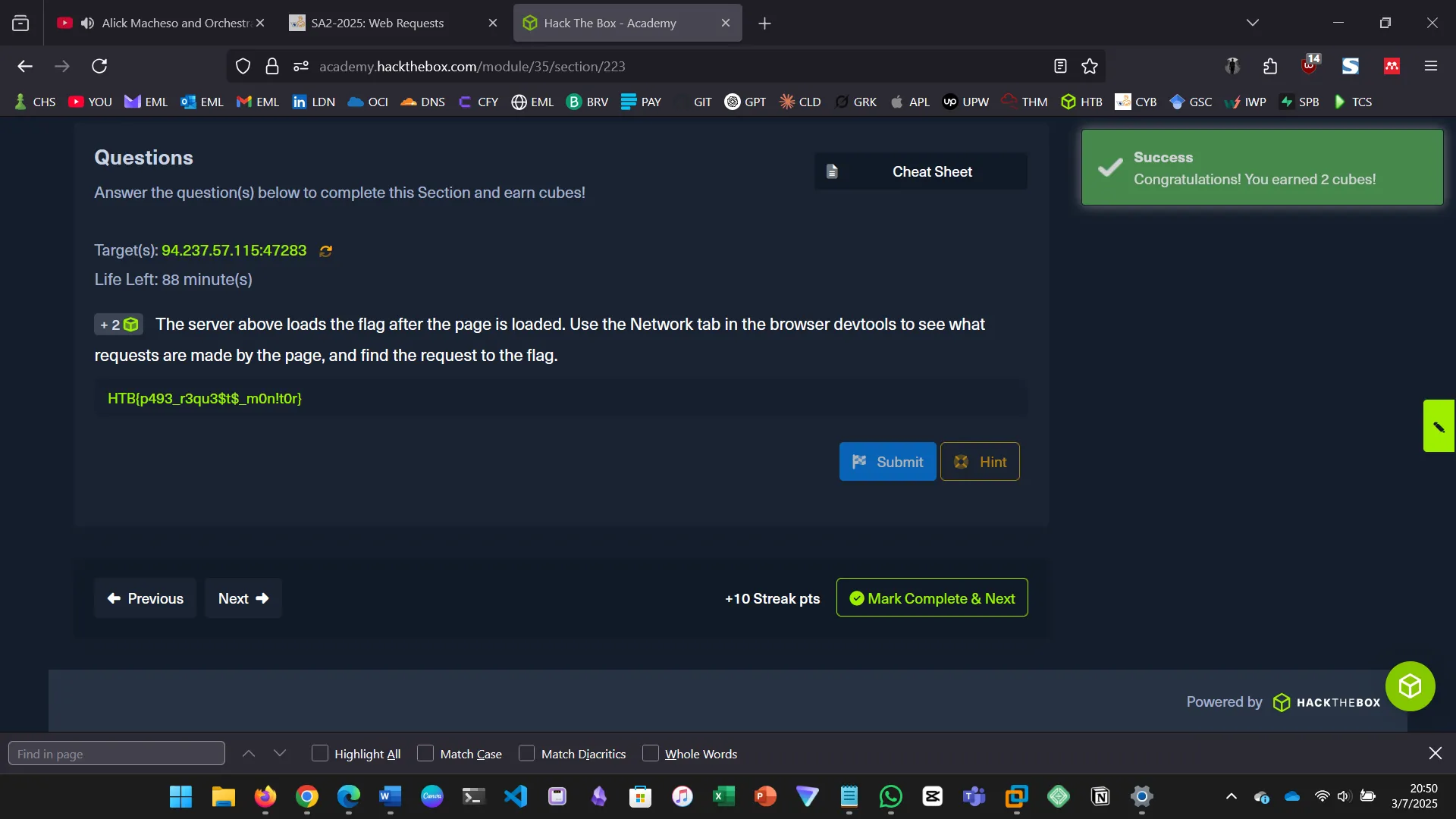
5. GET
Browsers use GET requests by default. The module shows how to inspect these requests using browser devtools.
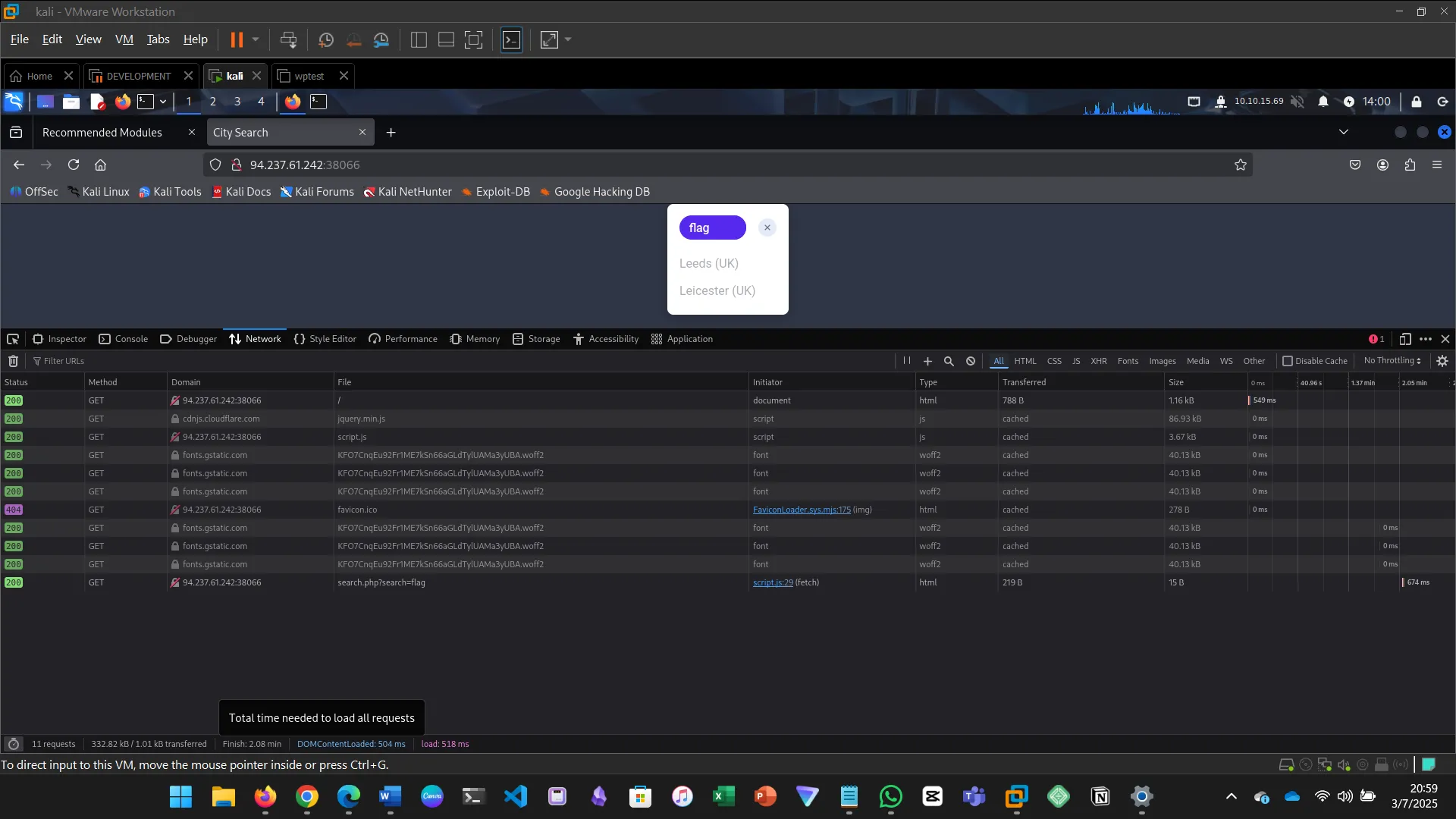
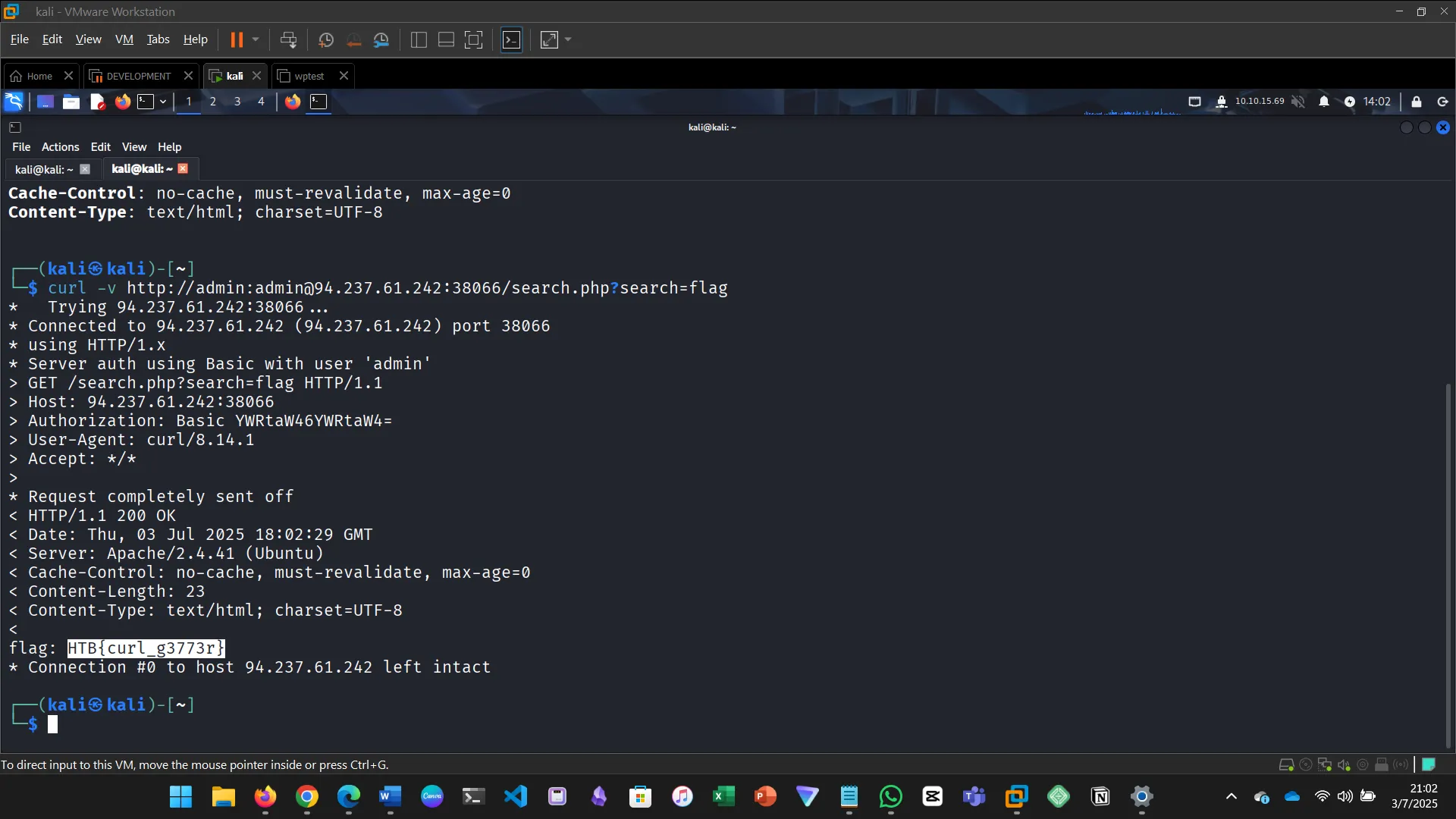
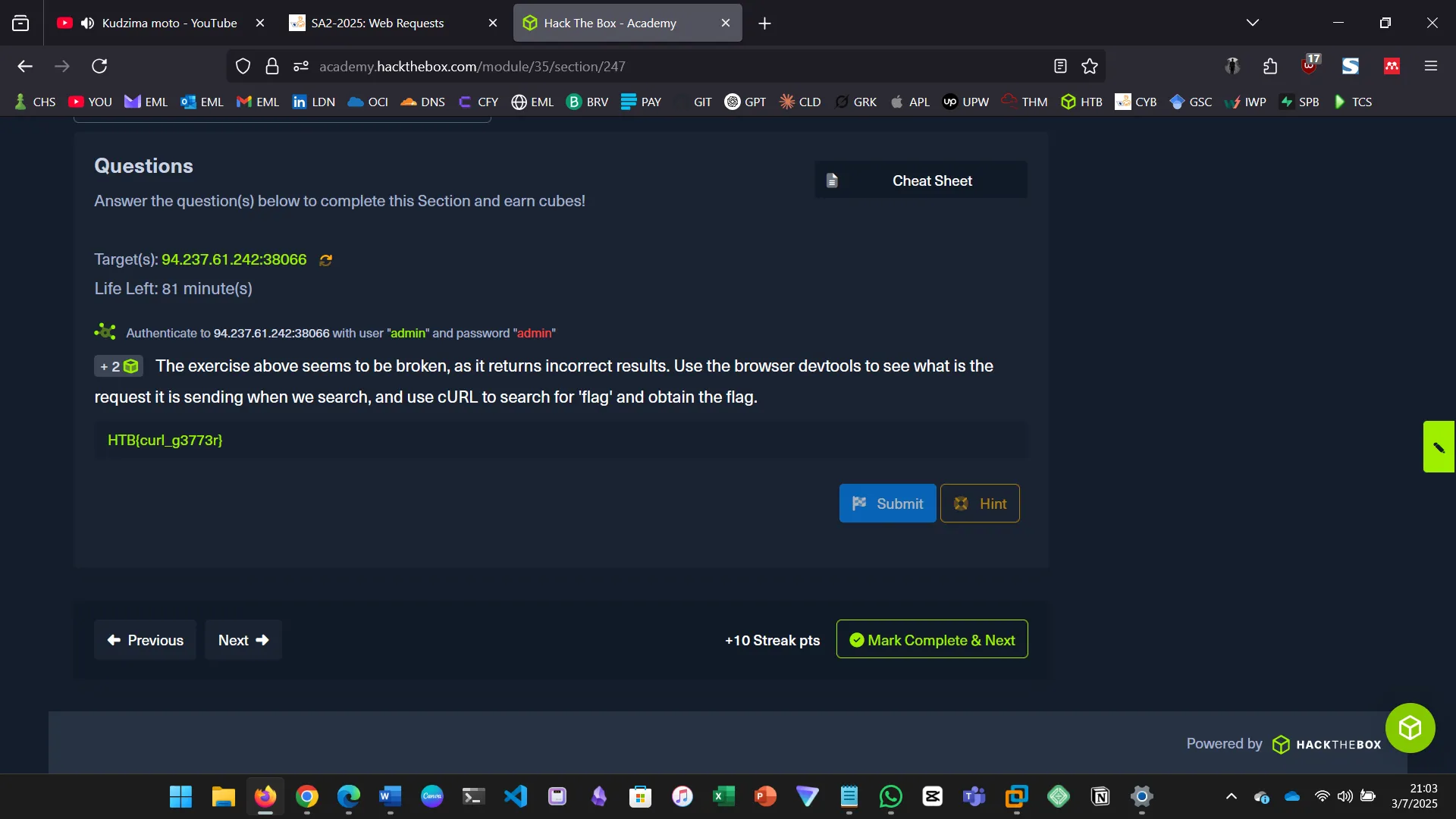
Use browser devtools to inspect the request being sent, then use cURL to search for flag.
6. POST
POST requests carry parameters in the request body, making them useful for login and data submission.
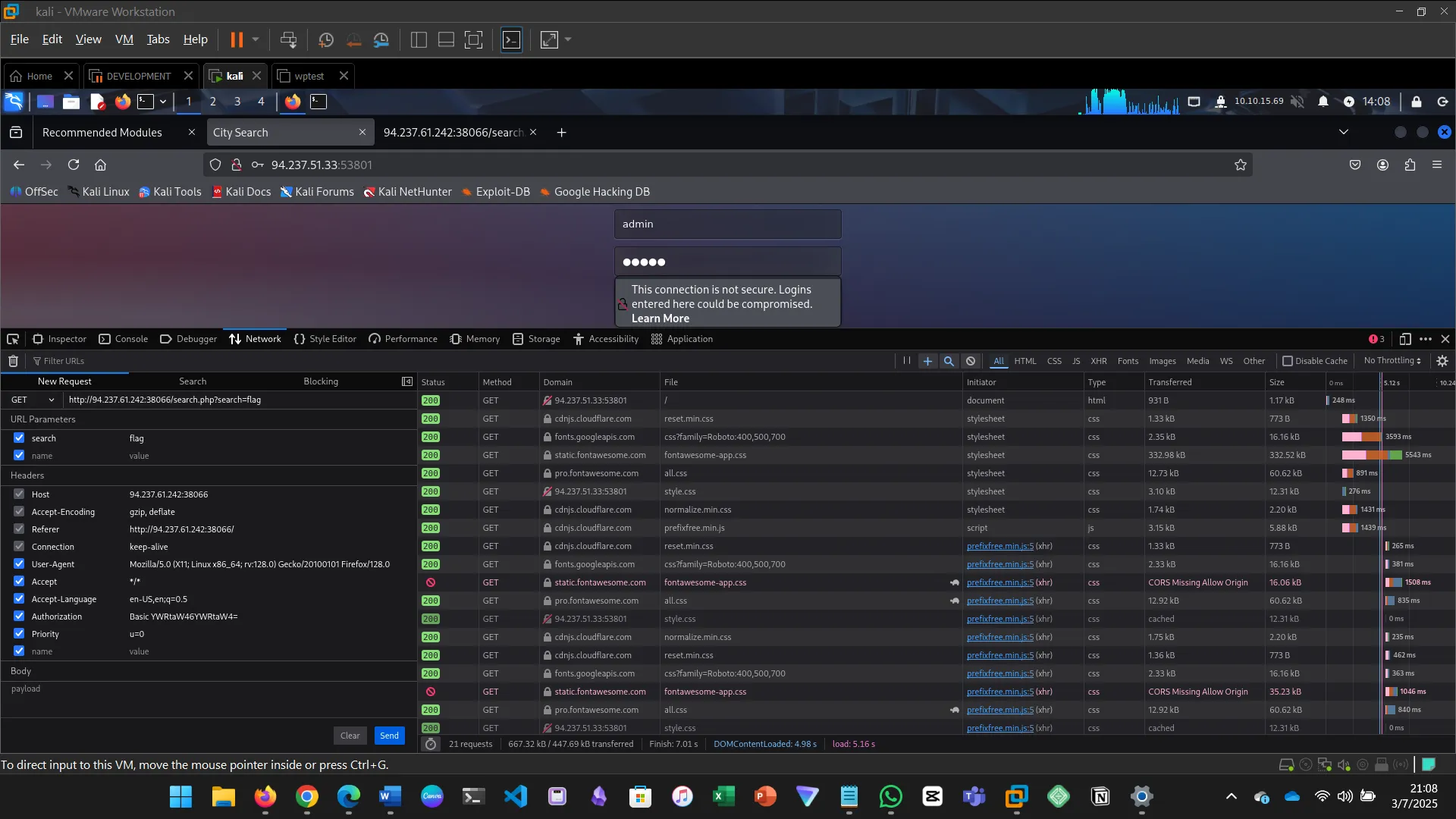
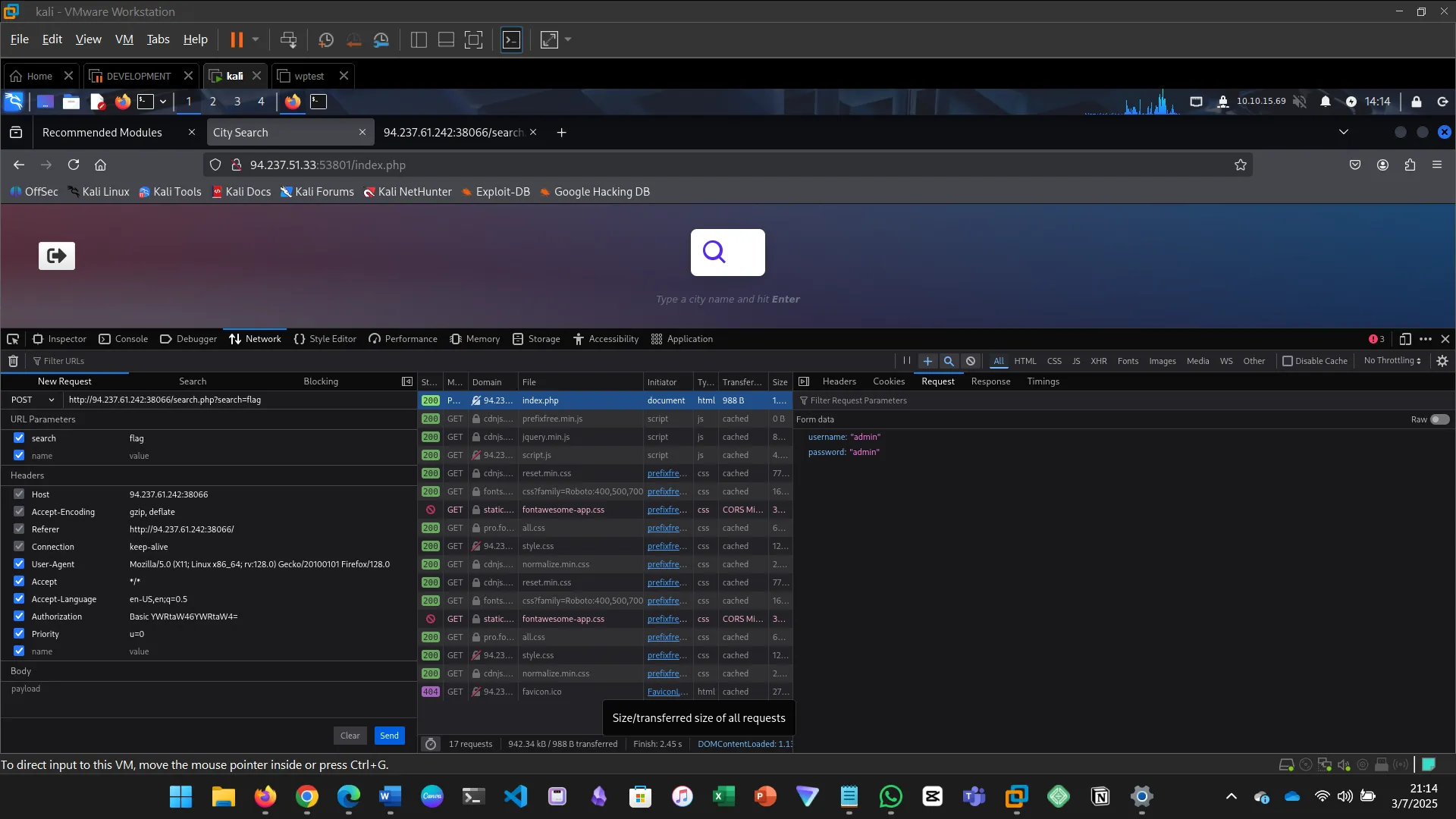
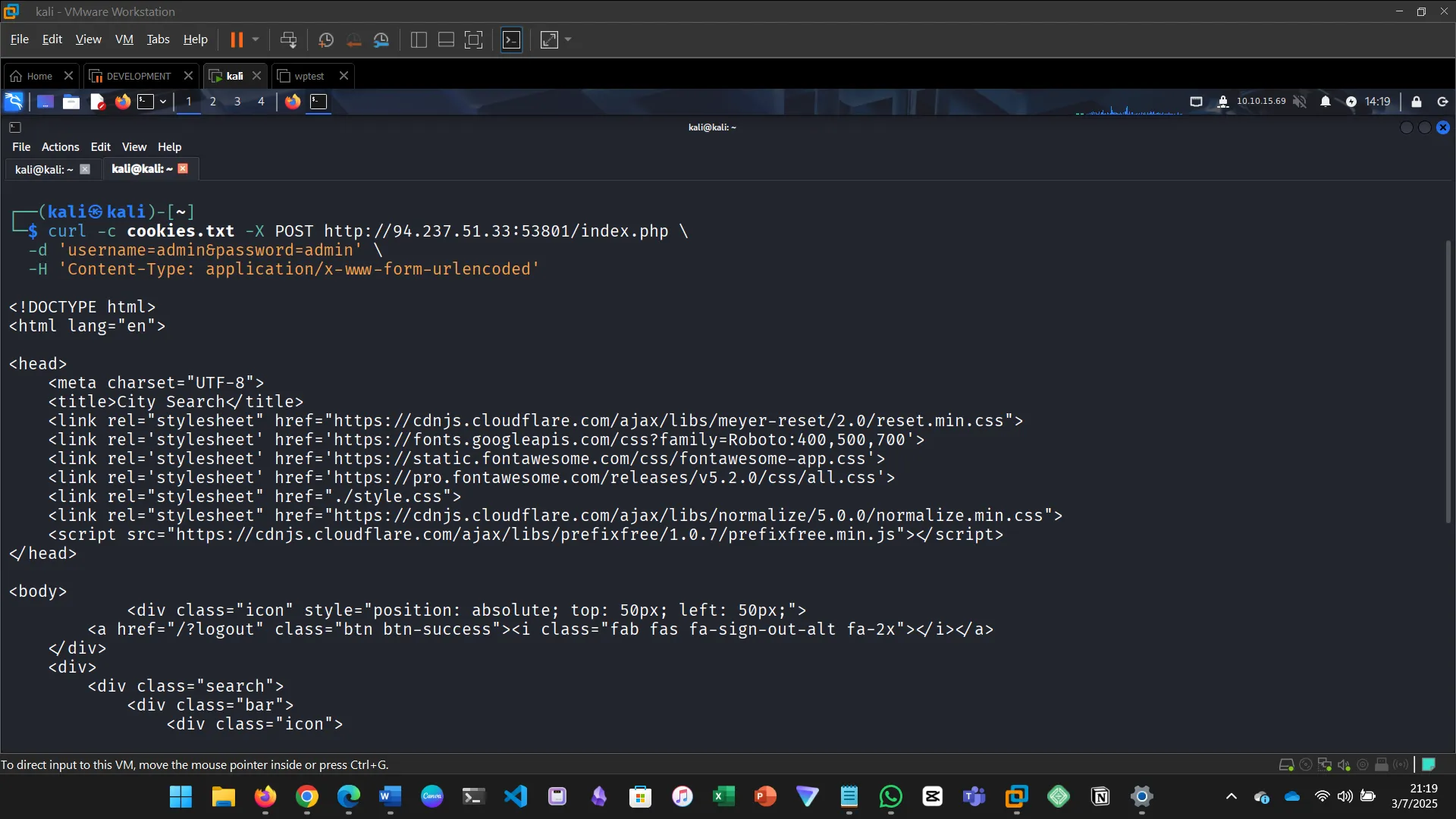
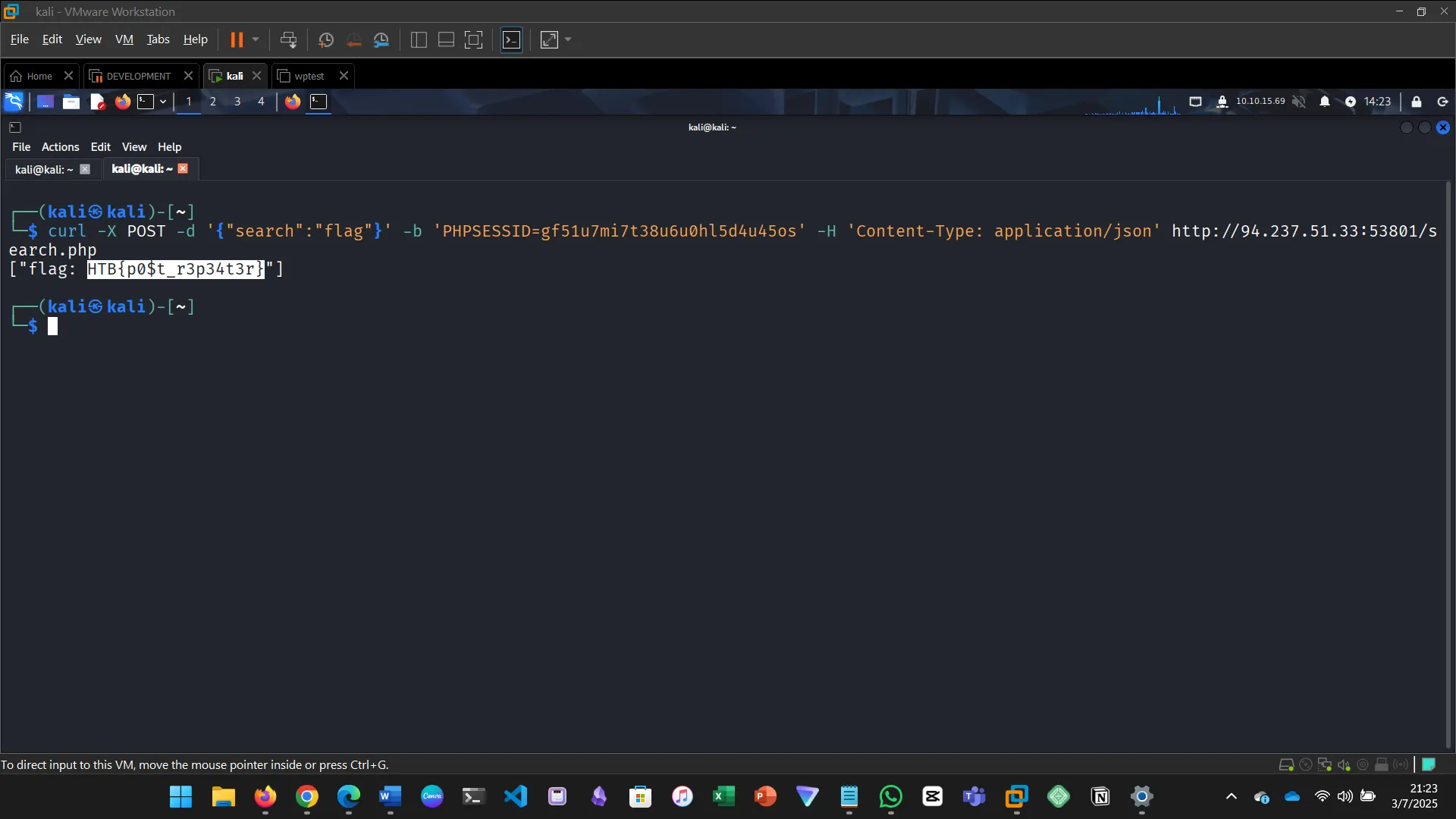
Obtain a session cookie through login, then use cURL to POST JSON data to /search.php and find the flag.
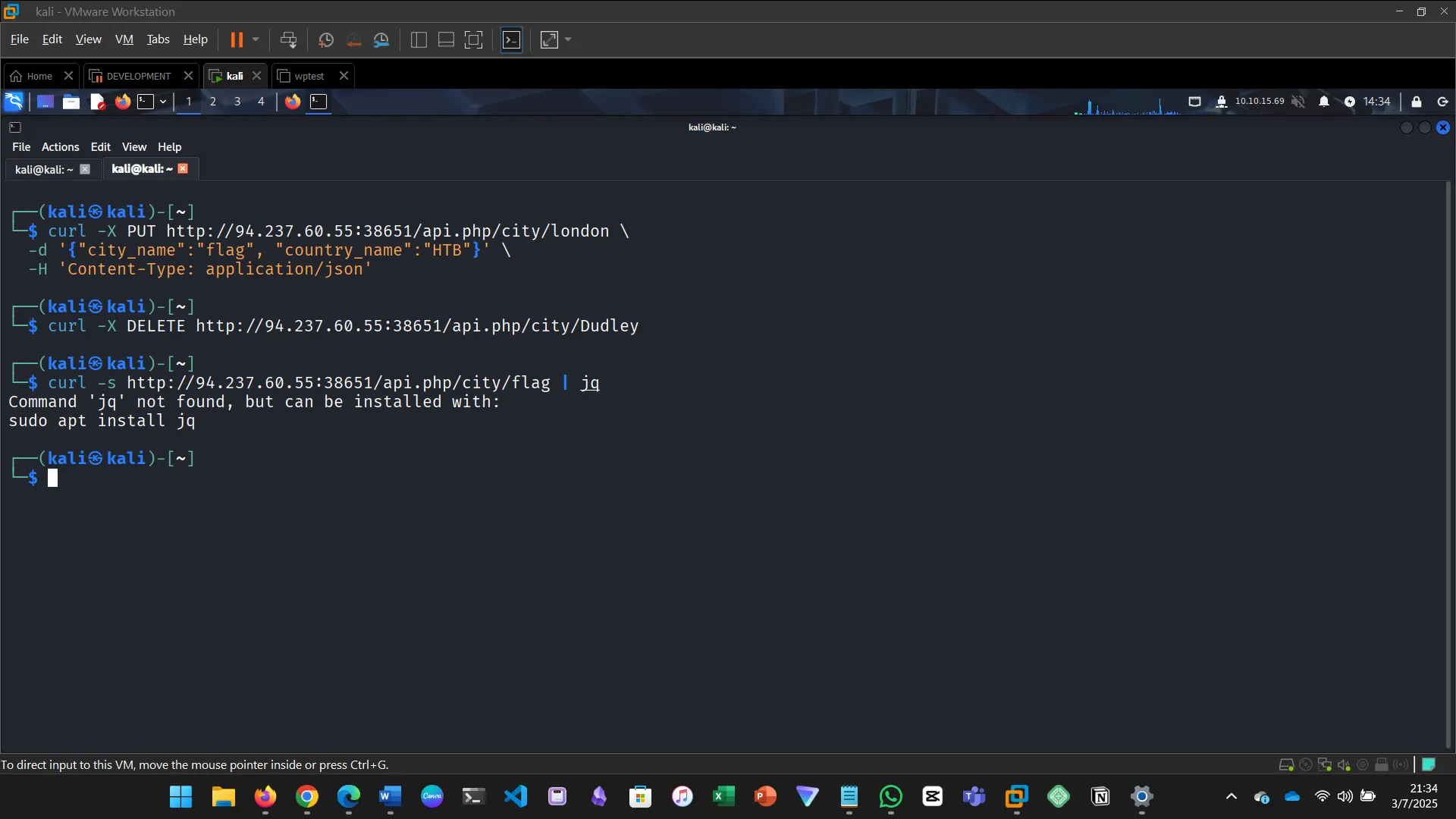
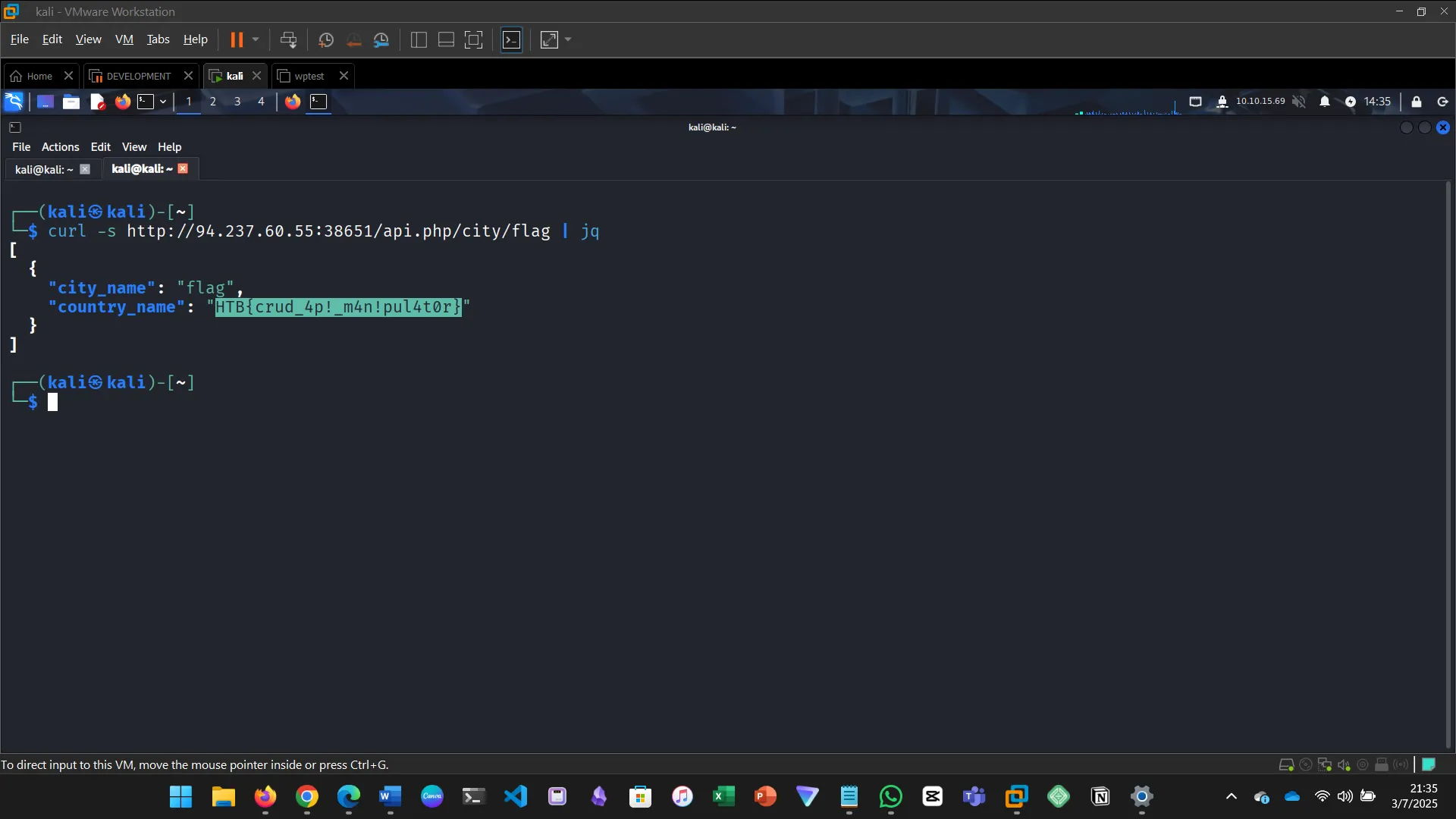
7. CRUD API
Update a city’s name to flag, delete a city, then search for the city named flag to get the flag.
8. CONCLUSION
This was another great learning experience. It’s a unique kind of insight when you investigate the tools and protocols you use daily. These discoveries stay with you long after the module ends.