INTRODUCTION
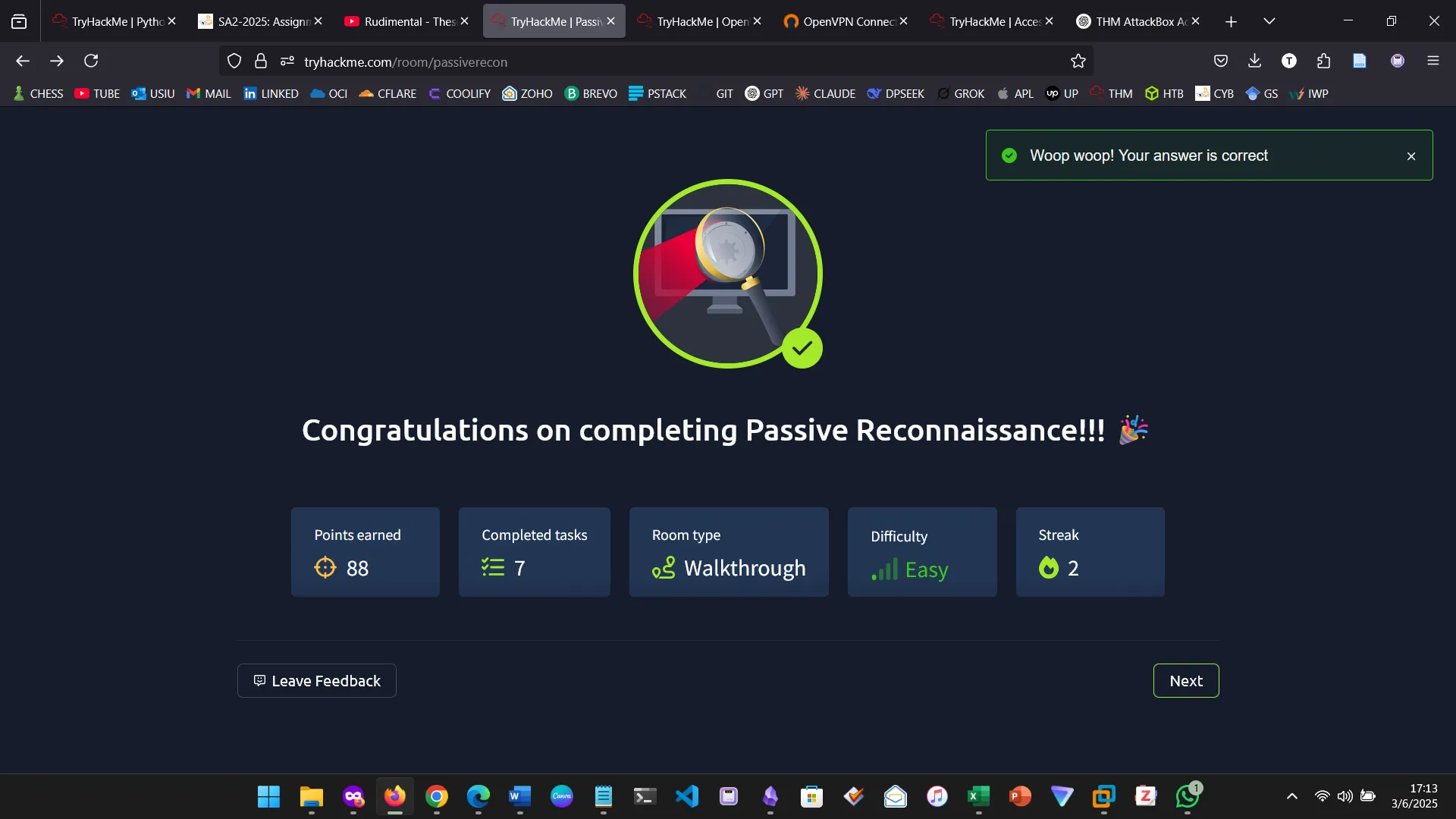
I completed the Passive Reconnaissance room on TryHackMe, available here (https://tryhackme.com/room/passiverecon). Reconnaissance is the process of gathering information about a target before launching an attack or securing a system. This module was about passive reconnaissance, which is the act of collecting publicly available information without directly engaging with the target. I learned about several essential tools used in passive reconnaissance, including whois, nslookup, and dig for querying DNS records, as well as online services like DNSDumpster and Shodan.io, which allow for extensive information gathering without direct interaction with the target.
PASSIVE VS. ACTIVE RECON
In this task, I learned about the differences between active and passive reconnaissance. In simple terms, the difference is that while active reconnaissance requires direct engagement with the target, passive recon relies on publicly available information.
WHOIS
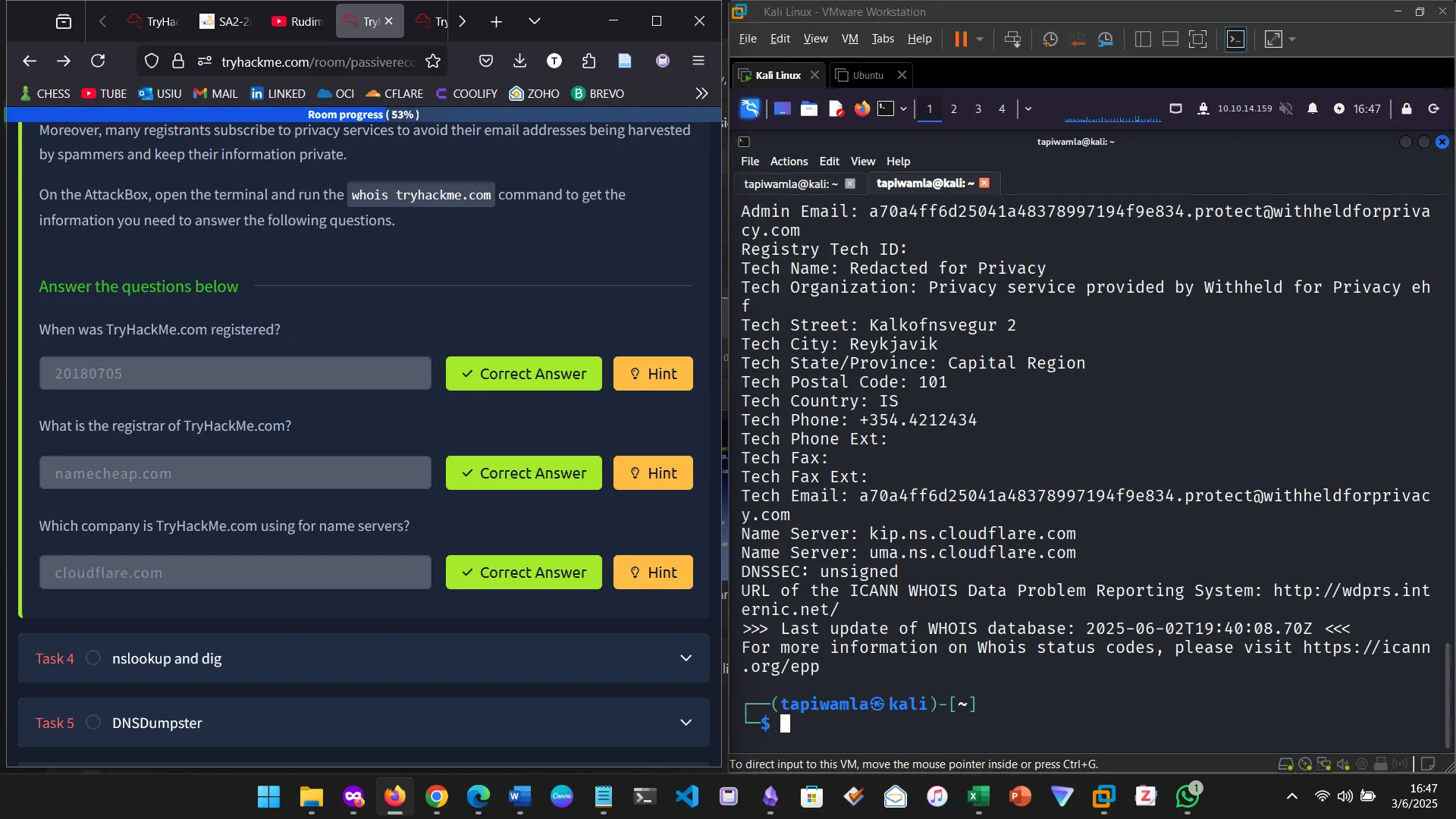
In this section, I learned about WHOIS, the request and response protocol that returns various information about a domain name, including name of registrar, DNS provider, registration dates, registrar contact information, etc.
NSLOOKUP AND DIG
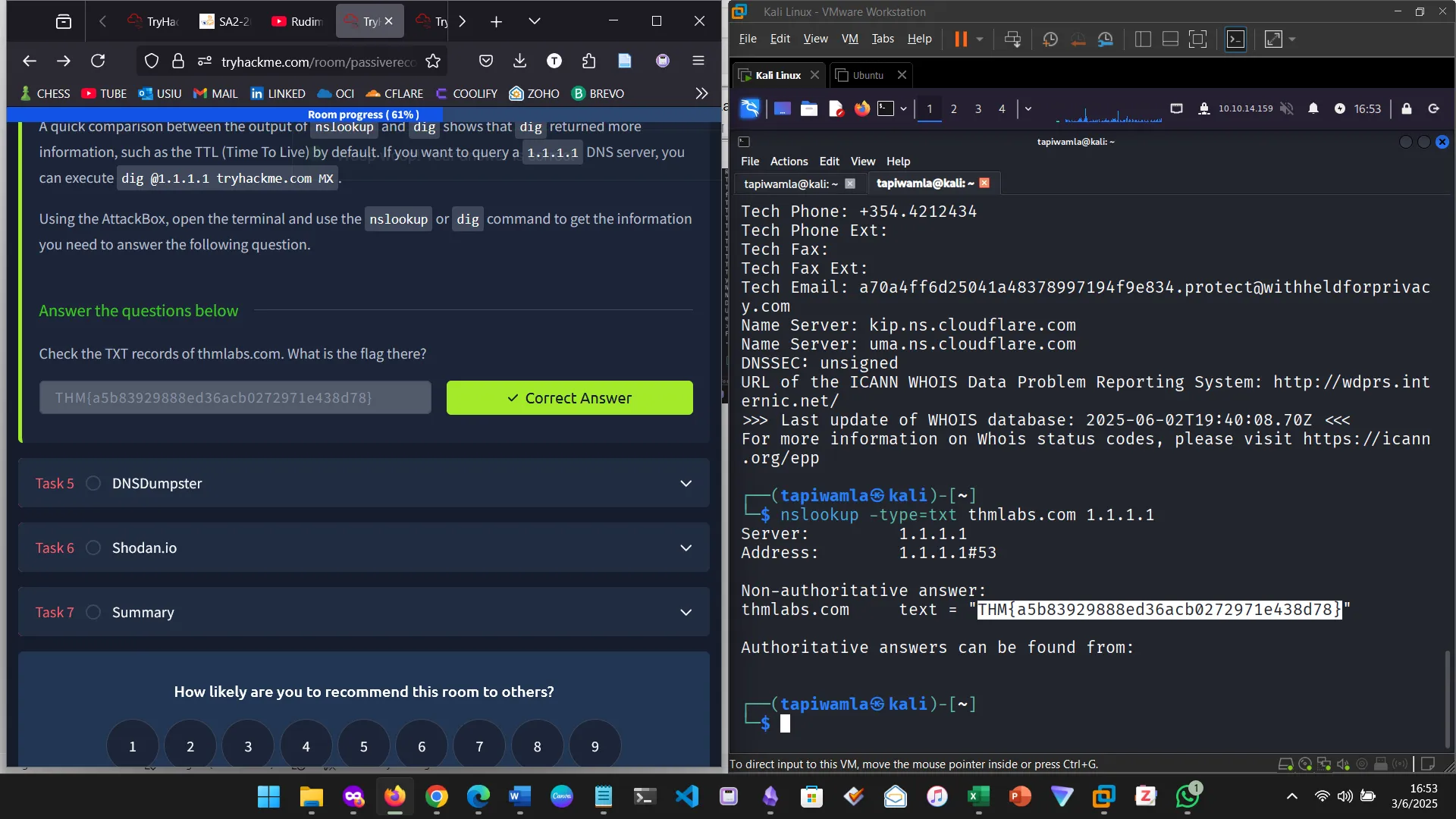
NSLookup is a command used to retrieve a domain’s DNS records, including A (IPv4), AAAA (IPv6), MX (Mail Exchange), CNAME (Canonical Name), TXT records, etc.
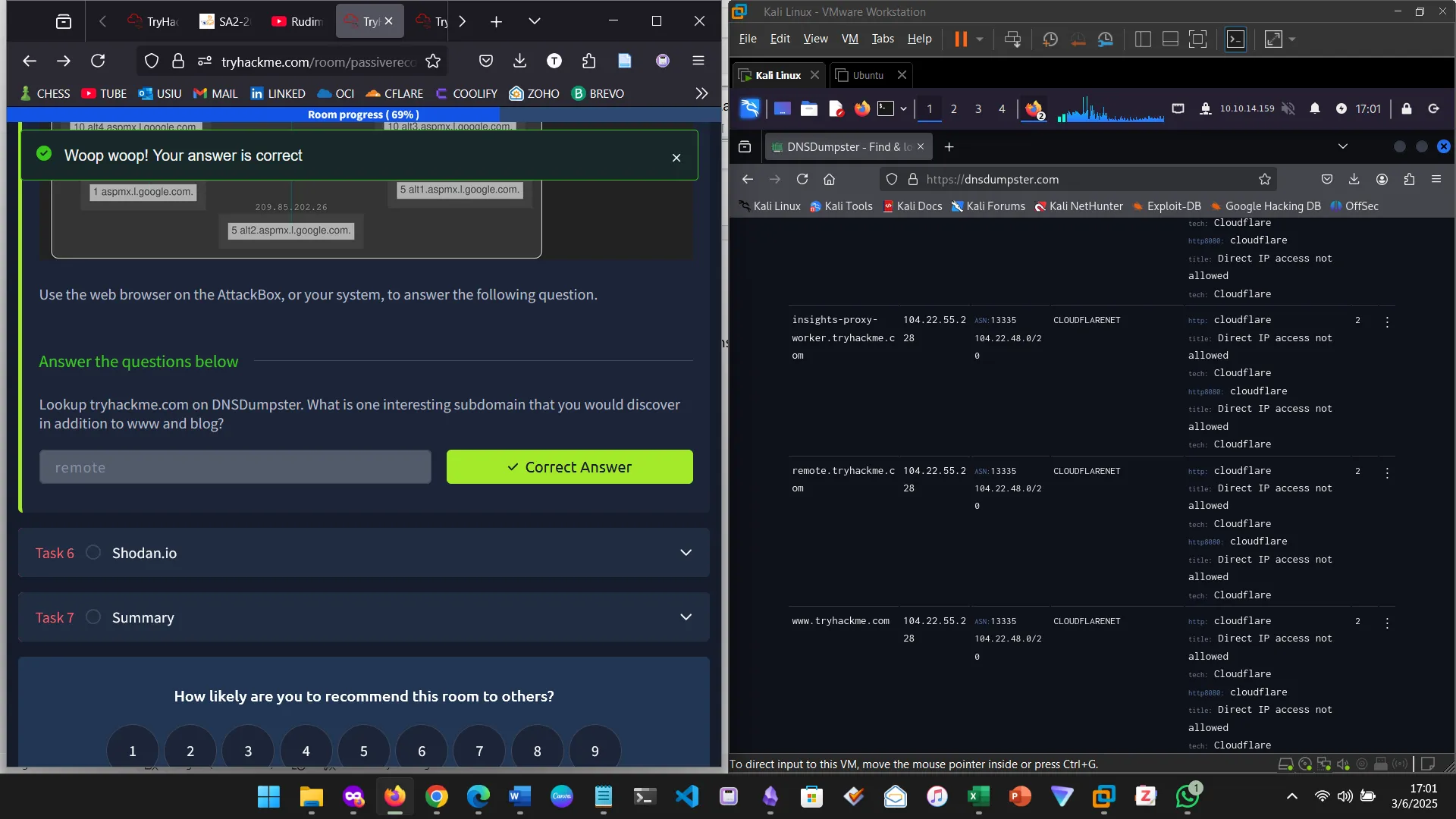
DNSDUMPSTER
DNSDumpster is an online service that returns more information about a domain name such as hidden subdomains.
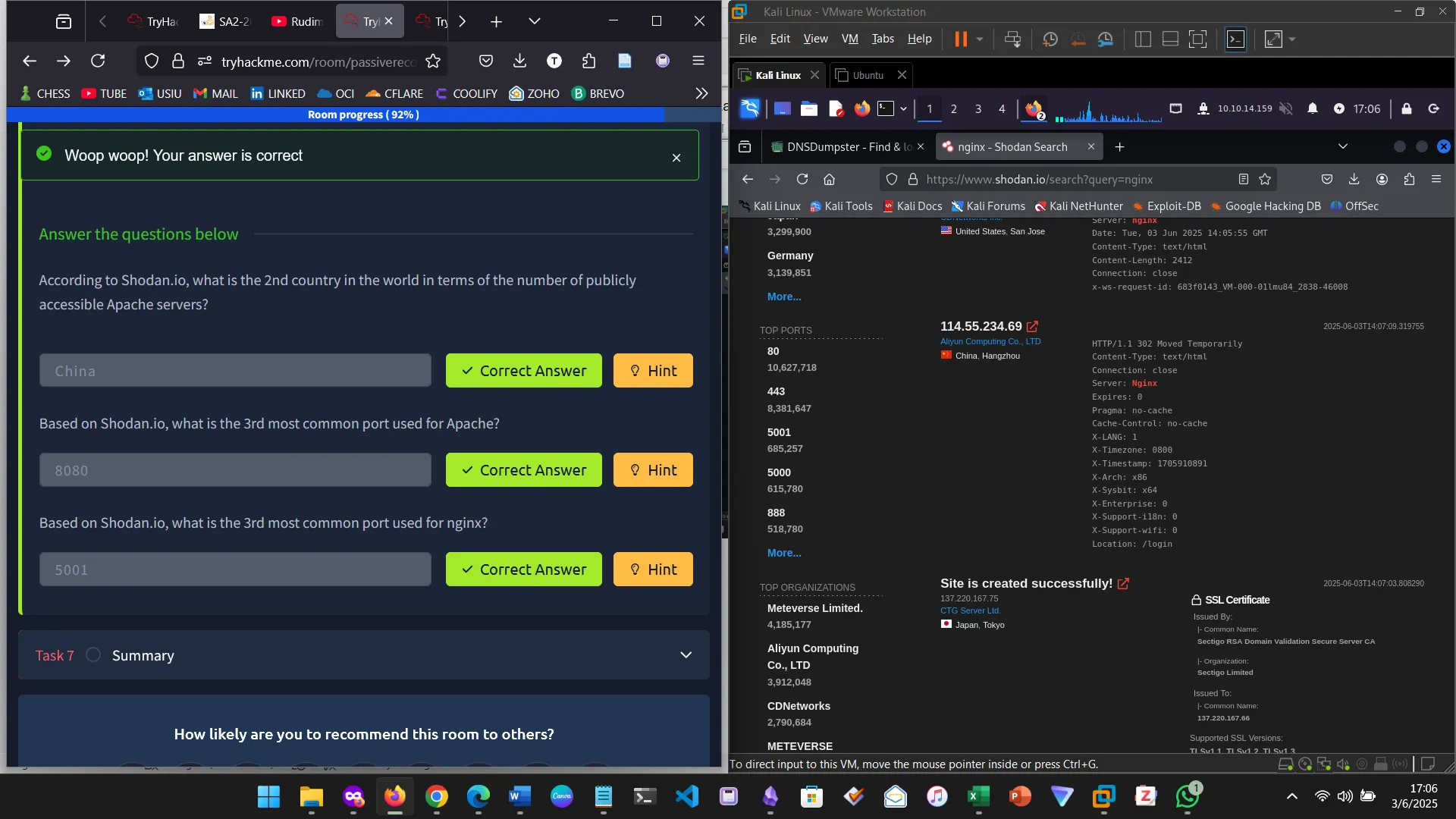
SHODAN.IO
Shodan.IO is a website that returns various information about a network without actively connecting to it. The service tries to connect to every device reachable online to build a search engine of connected “things” in contrast with a search engine for web pages. Once it gets a response, it collects all the information related to the service and saves it in the database to make it searchable on their site.
CONCLUSION
This was a great module. There’s a time when I used to have a wildcard DNS record on my domain and did not care about the subdomains that I created when setting up various services. I learned the risk about this and other activities regarding domain names and such. Great!