INTRODUCTION
I completed the “Introduction to Networking” module on HackTheBox. As said in the module, it is important for security professionals to understand networking in order to be able to diagnose and be able to secure the network even if it fails and the error is silent. The module used real-life scenarios of how networking works, allowing an easy understanding of the content.
NETWORK TYPES
This section introduced both common and book terms regarding network types. It simplified the meanings of terms like WAN, LAN, and VPN which define the Internet, home or company networks, and secure remote access technologies, respectively. Some arguably repetitive and redundant terms like GAN and WLAN were also mentioned. My key takeaway regarding these was the fact that the Internet is not the only network that can be called a GAN, Global Area Network.
NETWORKING TOPOLOGIES
A network topology is the way devices are arranged and connected in a network, either physically or logically. Several topologies exist, including Point-to-Point, Bus, Star, Ring, Mesh, Tree, Hybrid, and Daisy Chain.
I learned about the differences between them and how they impact network structure, performance, and reliability.
In simple terms:
- Point-to-Point: A direct connection between two devices, like a phone call between two people.
- Bus: All devices share a single cable to communicate, like a group chat where everyone listens to the same message.
- Star: Devices connect to a central hub, like spokes on a bicycle wheel.
- Ring: Devices form a closed loop where data moves in one direction, similar to passing notes in a circle.
- Mesh: Devices are interconnected, ensuring multiple paths for communication, like roads in a busy city.
- Tree: A combination of star networks arranged in a hierarchy, similar to an organizational chart.
- Hybrid: A mix of two or more topologies tailored to specific needs.
- Daisy Chain: Devices are linked in a series, like stringing fairy lights together.
I also learned about various terms used in networking, including nodes (devices in a network), NICs (network interface controllers), routers, switches, firewalls, and different types of connections like wired and wireless.
My key takeaway was that network topology significantly impacts communication efficiency, reliability, and scalability in different environments. Understanding these structures helps in designing effective networks for various use cases.
PROXIES
This module explained what proxies are and the various misconceptions that exist about them. The correct definition of a proxy is when a device or service sits in the middle of a connection and acts as a mediator. A proxy is not simply a tool for hiding an IP address or bypassing geo-restrictions—this is a common misconception. Many people mistakenly equate proxies with VPNs, but while VPNs encrypt all traffic and change the user’s IP address, proxies primarily mediate and inspect traffic.
The module also explained the different types of proxies, including:
- Forward Proxy: Acts on behalf of clients, forwarding requests to the internet. Often used in corporate networks to filter web access.
- Reverse Proxy: Protects servers by filtering incoming requests, commonly used for security and load balancing.
- Transparent Proxy: Operates without the client knowing, often used in schools or workplaces for monitoring and filtering.
- Dedicated Proxy: A private proxy assigned to a single user for enhanced security and anonymity.
I also learned an interesting thing about Firefox: unlike browsers such as Chrome and Edge, Firefox does not use the system proxy settings by default. Instead, it relies on libcurl, making it less likely for malware to automatically detect and bypass proxy settings. This unique approach enhances security in environments where proxies are used for filtering and monitoring.
NETWORKING MODELS
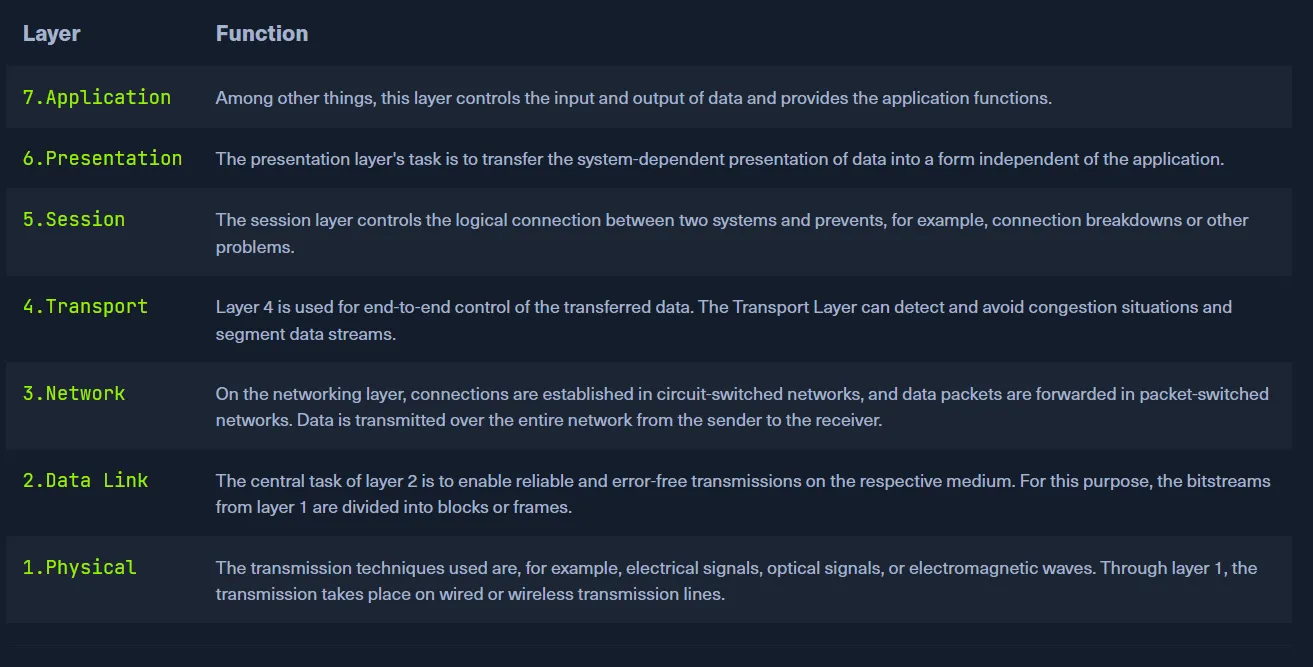
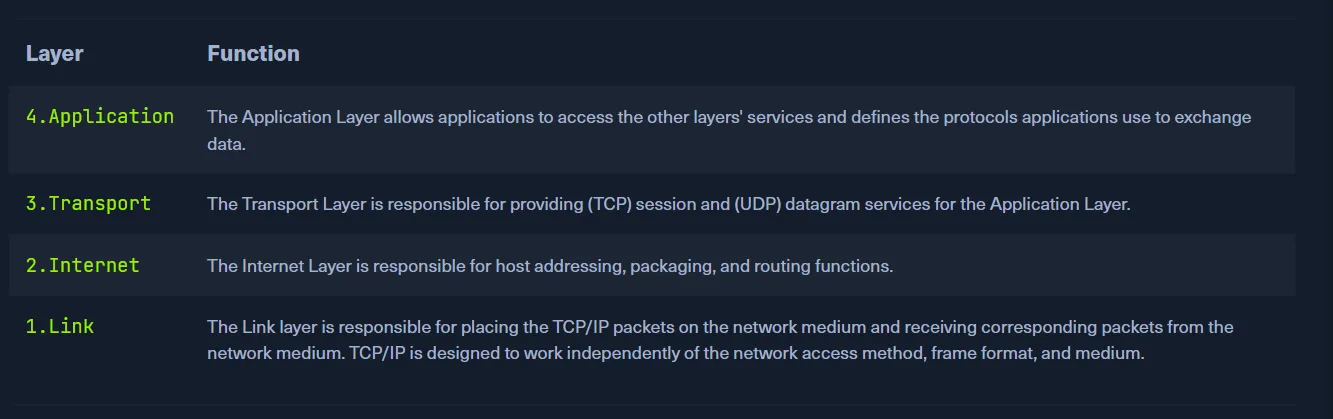
This section was a quick dive into networking models, particularly the OSI (Open Systems Interconnection) and TCP/IP models.
The OSI model is a reference model composed of seven distinct layers that clearly separate tasks, offering a structured gateway between the network and end-users. It emphasizes strict protocols and detailed communication processes. Meanwhile, the TCP/IP model refers to a family of protocols, including TCP, IP, UDP, and ICMP, and serves as the foundation for how hosts communicate over the Internet. It focuses more on practical functionality than rigid structure, allowing flexibility as long as general guidelines are followed.
My moment of truth was on which model is newer. I previously thought that the TCP/IP model came after the OSI model due to its real-world application on the Internet, but it turns out the OSI model is actually newer and is more commonly used as a reference for understanding and analyzing communication systems.
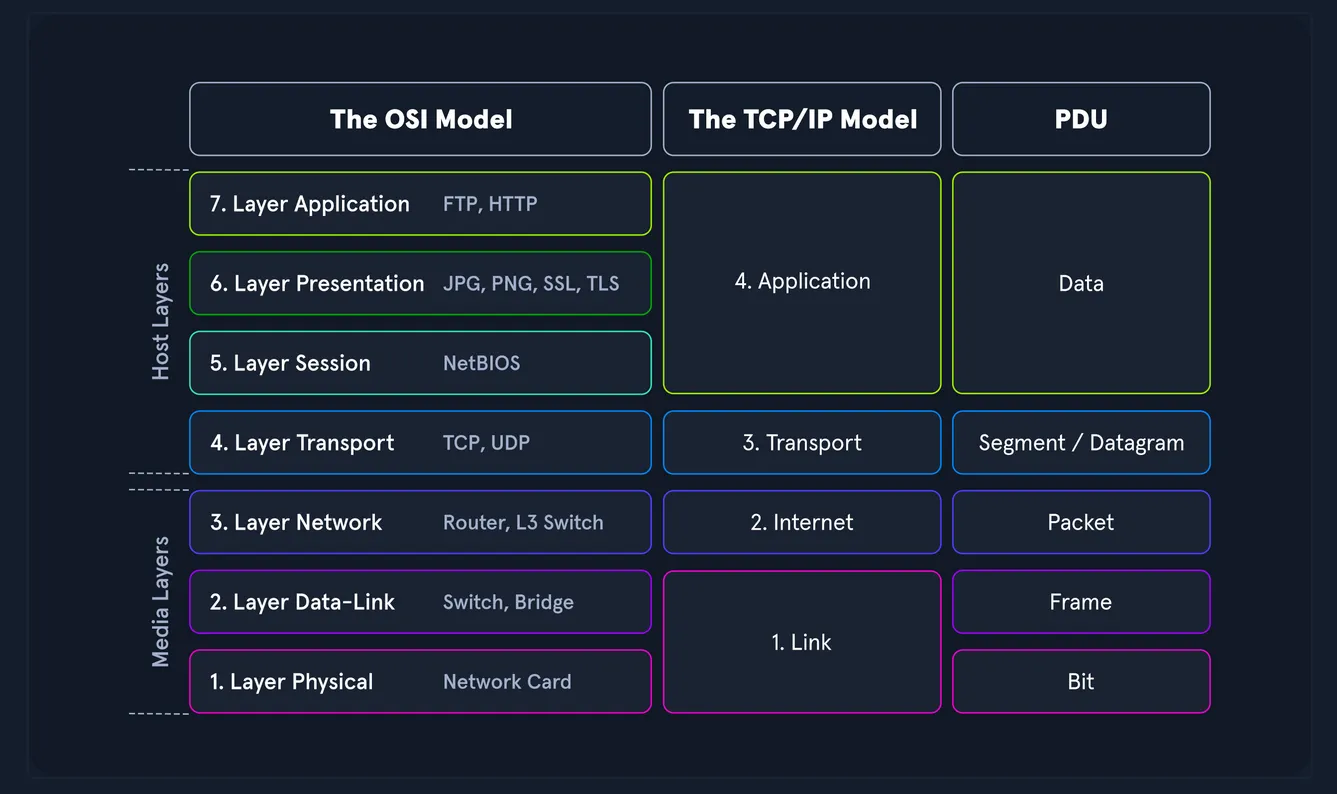
THE OSI MODEL
THE TCP/IP MODEL
NETWORK LAYER
This section looked at the Network Layer (Layer 3) of the OSI model and what it is responsible for—that is, enabling logical addressing and routing of data packets across different networks. Since data cannot always be directly delivered from sender to receiver, the Network Layer ensures packets are forwarded from node to node until they reach their destination. It handles address evaluation, routing path decisions, and the construction of routing tables. Importantly, it also manages communication between subnets with different or incompatible addressing schemes.
It also explained the protocols applicable to this layer including:
- IPv4 / IPv6 – Provide logical addressing and packet forwarding across networks
- IPsec – Secures IP communication by authenticating and encrypting each IP packet
- ICMP – Used for diagnostic functions and error reporting (e.g., ping)
- IGMP – Manages membership of IP multicast groups
- RIP – A distance-vector routing protocol for determining the best route
- OSPF – A link-state routing protocol used within larger enterprise networks
IP ADDRESSES
Key points from this section:
- IP Addresses: Unique identifiers for devices in a network.
- IPv4: 32-bit addresses shown in dotted-decimal format (e.g., 192.168.0.1).
- Subnet Mask: Defines how much of the address identifies the network vs host.
- Gateway & Broadcast: Special roles for certain addresses in a range.
- Binary & CIDR: Understanding IP addressing in binary and using CIDR notation for flexibility.
SUBNETTING
Subnetting divides larger networks into smaller segments. Key concepts covered:
- Network vs. Host bits
- Network and Broadcast addresses
- CIDR and subnet masks
- Subnet size calculations
- Creating /28 subnets from a /27 range
- Fast mental shortcuts using binary logic
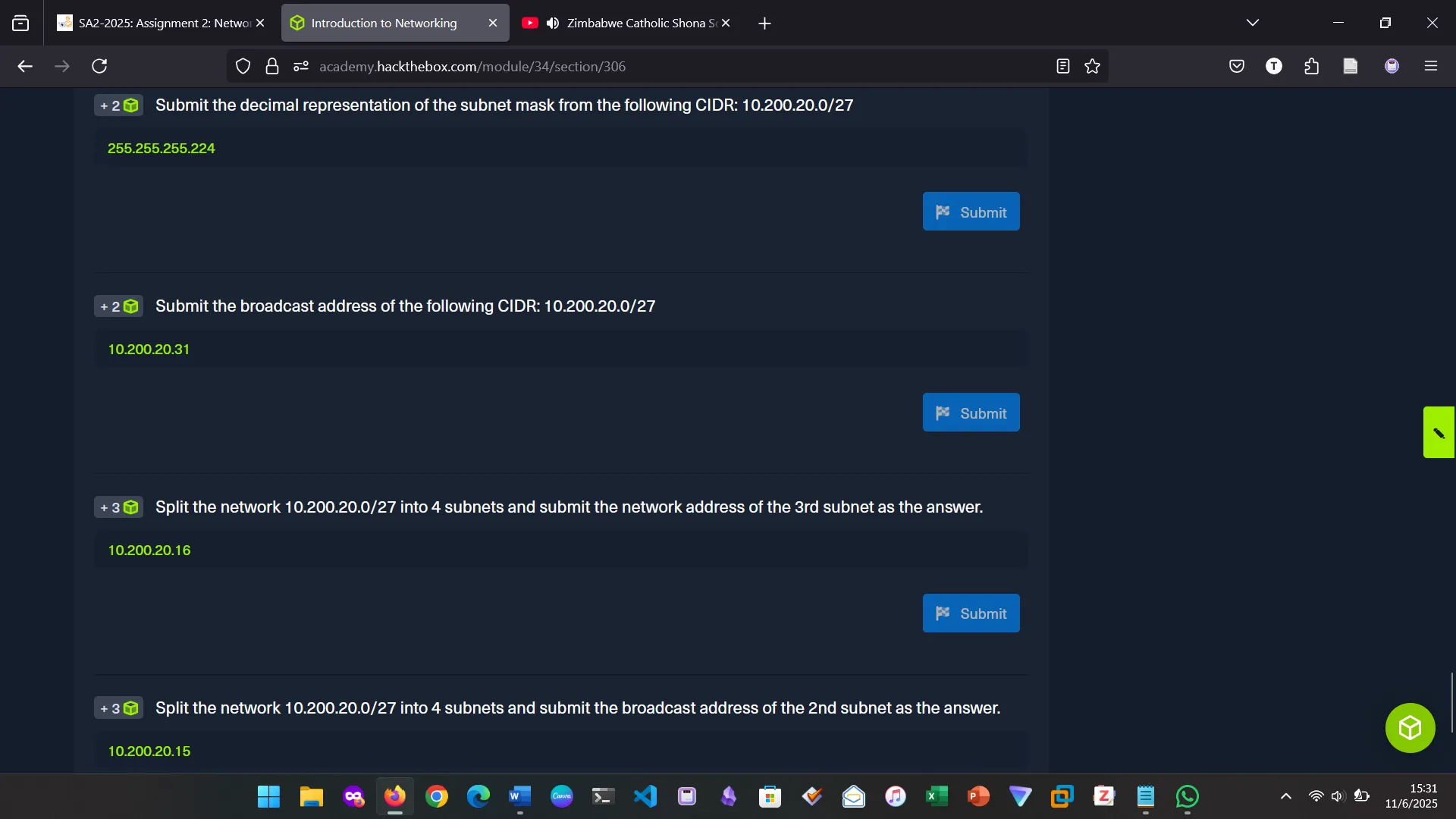
SUBNETTING PRACTICAL
-
Subnet mask for 10.200.20.0/27
→ 255.255.255.224 -
Broadcast address for 10.200.20.0/27
→ 10.200.20.31 -
3rd subnet from 10.200.20.0/27 split into 4
→ 10.200.20.16/30 -
Broadcast address of 2nd subnet
→ 10.200.20.15
MAC ADDRESSES
This section covered the 48-bit MAC address structure (OUI + NIC), used for Layer 2 identification. Important points:
- MACs are fixed per device but can be spoofed
- Represented in hex and binary
- Useful for local routing and network control
- Vulnerabilities include MAC spoofing, flooding, and ARP spoofing
IPv6 ADDRESSES
Covered:
- 128-bit structure and address space
- SLAAC for self-configuration
- Anycast addressing
- Prefix notation and address structure
- Integrated security through IPsec
PROTOCOLS AND TERMINOLOGY
Learned about:
- Common protocols (HTTP, FTP, DNS, DHCP, etc.)
- Wireless standards and security (WEP, WPA2, etc.)
- VPN types and tunneling concepts
- Vendor-specific protocols like Cisco’s
CONNECTION ESTABLISHMENT
Key topics:
- Key Exchange: DH, RSA, ECDH, ECDSA
- Authentication: Kerberos, SRP, TLS, OAuth, OpenID, SAML
- Transport Protocols: TCP (stateful, reliable) vs UDP (stateless, fast)
- Cryptography: Symmetric/asymmetric encryption, cipher modes, AES/RSA standards
CONCLUSION
This module felt like a deep dive into something I have always brushed through. Revisiting subnetting and cryptography were a gap-filling exercise into such areas where I had been lacking. The best thing of it all was going through content that you have a surety of its relevance in cybersecurity. It was a great learning experience altogether.