Module: Attacking Web Apps with Ffuf
1. INTRODUCTION
I completed the module on attacking web applications with ffuf on HackTheBox. Ffuf is a command line tool used for web fuzzing / bruteforcing. Fuzzing refers to a testing technique that sends various types of user input to a certain interface to study how it would react. This module was an intense dive into fuzzing and covered fuzzing for directories, files and extensions, hidden vhosts, PHP parameters as well as parameter values. Ffuf works with wordlists, of which the most commonly used are from the seclists repository. This is what I used.
2. DIRECTORY FUZZING
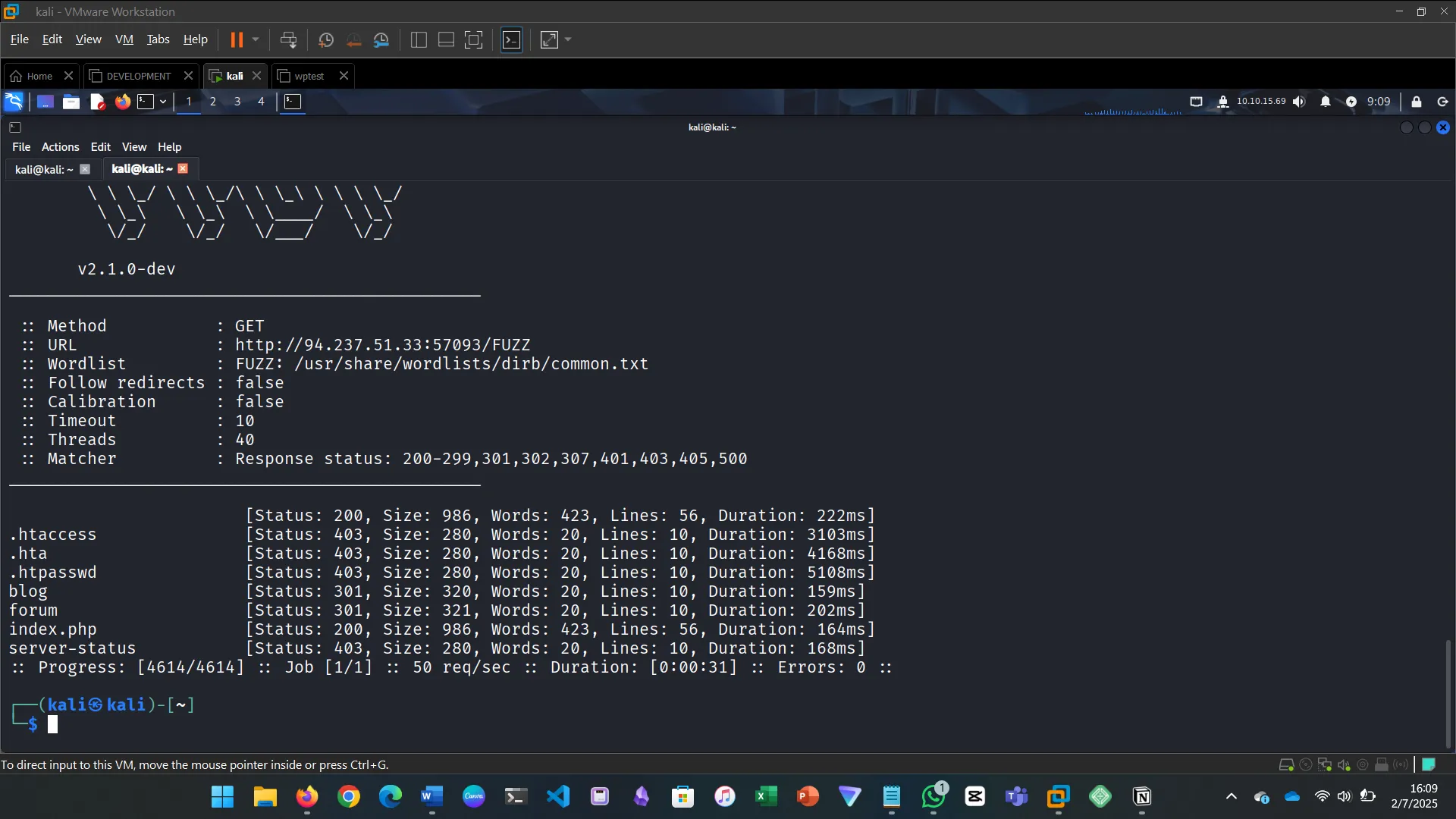
The walkthrough for this section explained and demonstrated how to use ffuf to fuzz for directories. The challenge was to do a similar fuzzing to find another directory that could be found on the server.
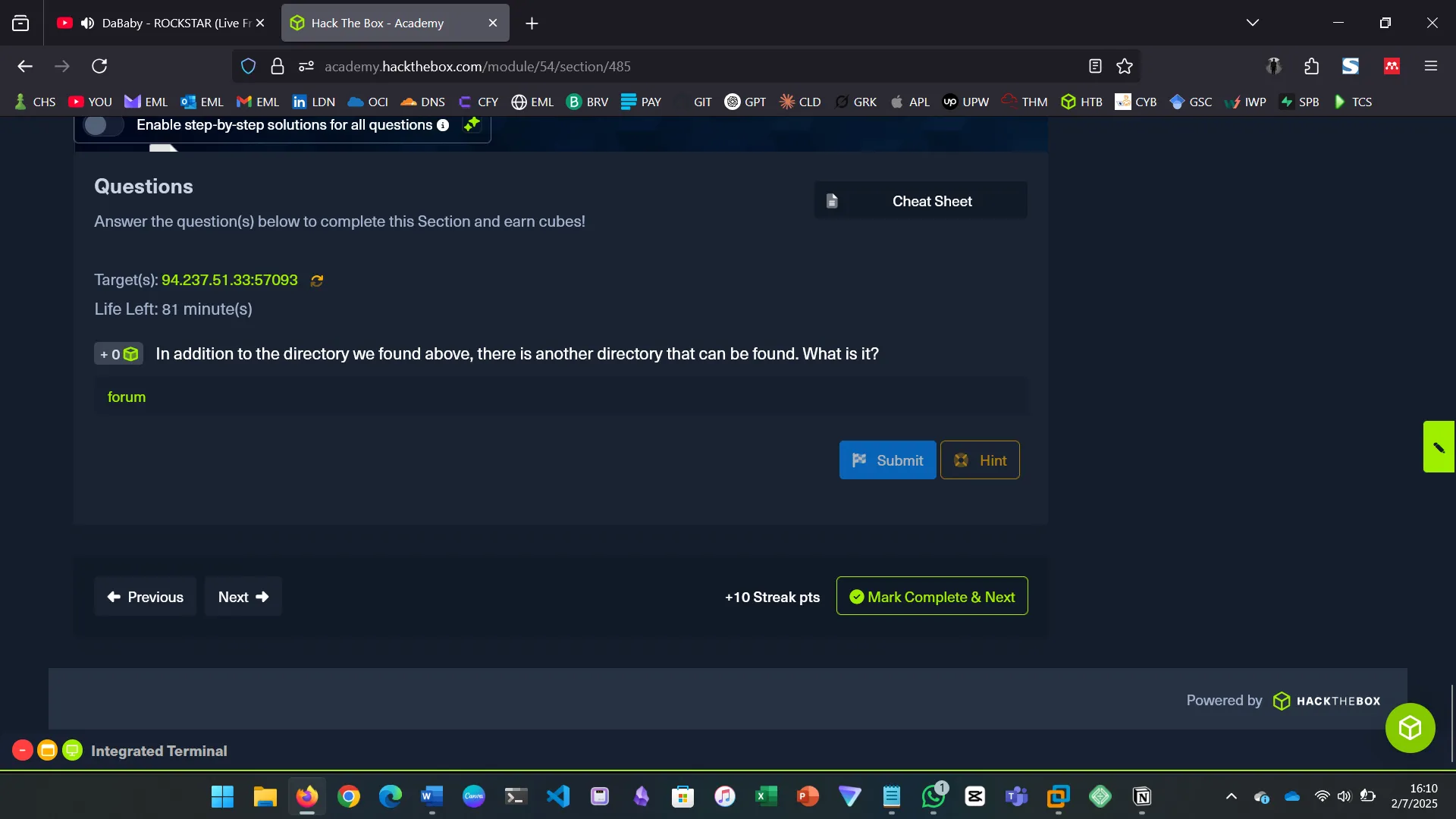
3. PAGE FUZZING
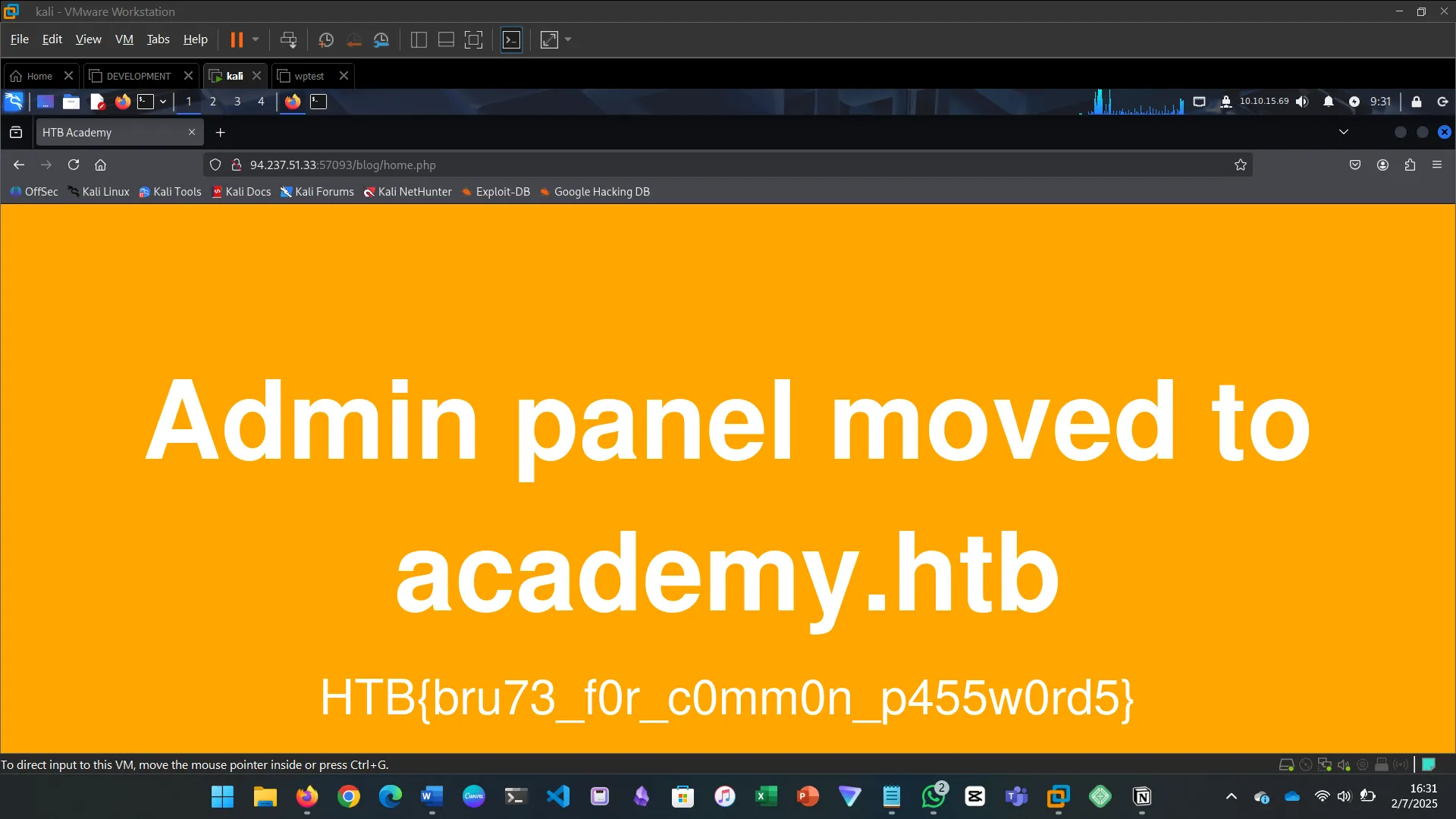
The challenge on page fuzzing was to fuzz the /blog directory and find all pages, one of which contained the flag.
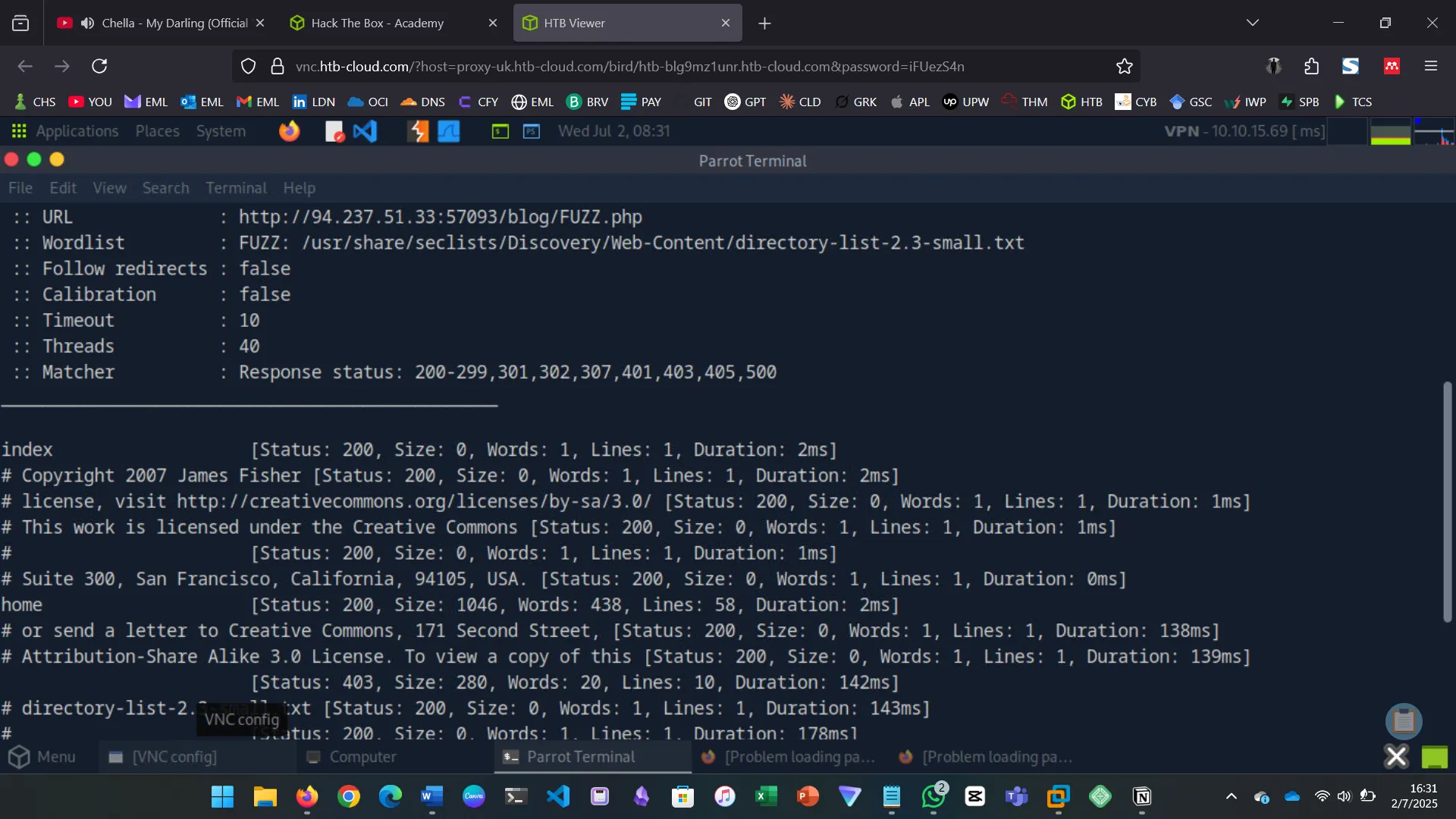
4. RECURSIVE FUZZING
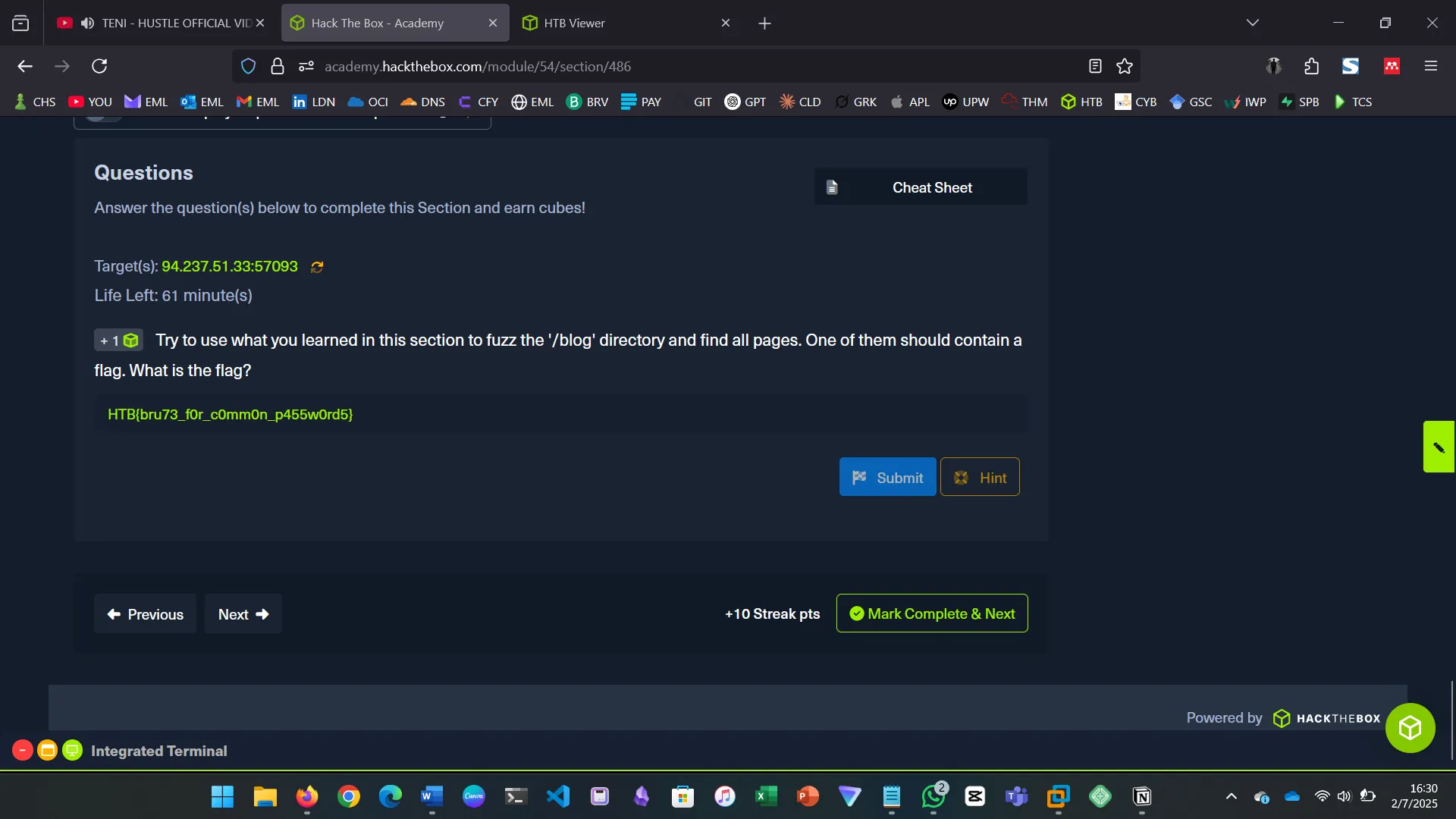
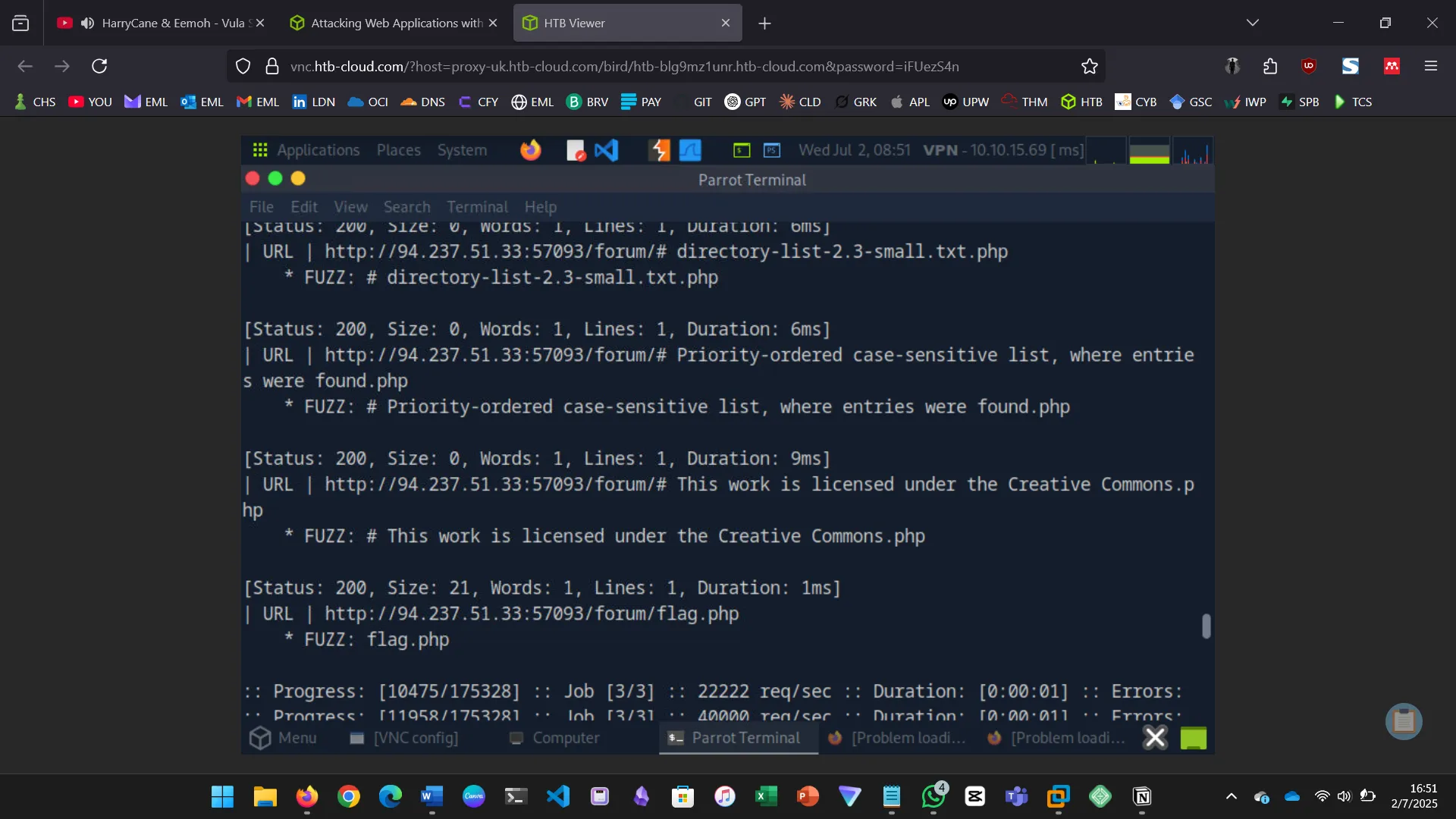
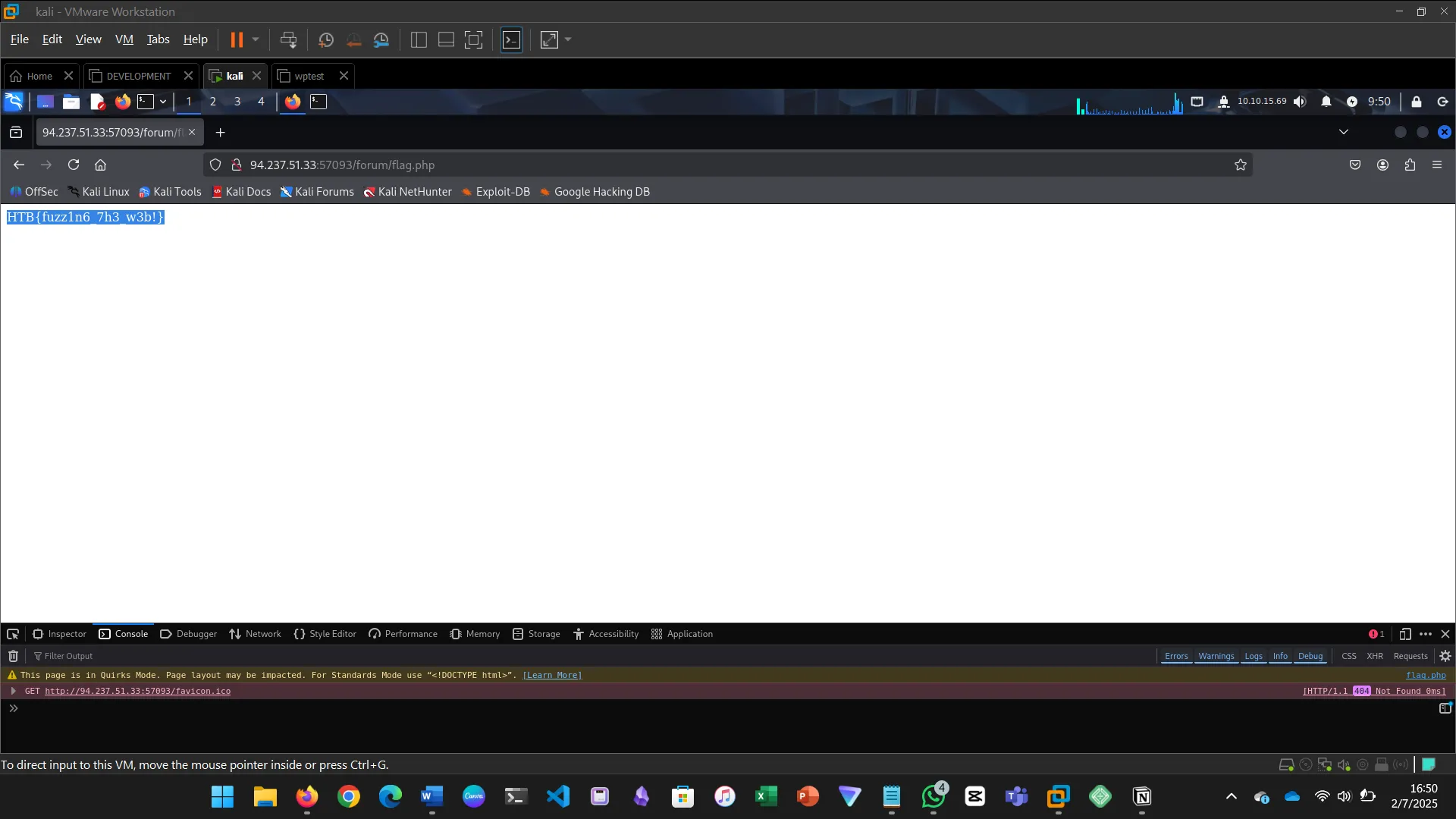
If we had dozens of directories, each with their own subdirectories and files, individual fuzzing techniques would take a very long time to complete. To be able to automate this, we utilize recursive fuzzing. The challenge for this section was to try and apply the learned content by practicing.
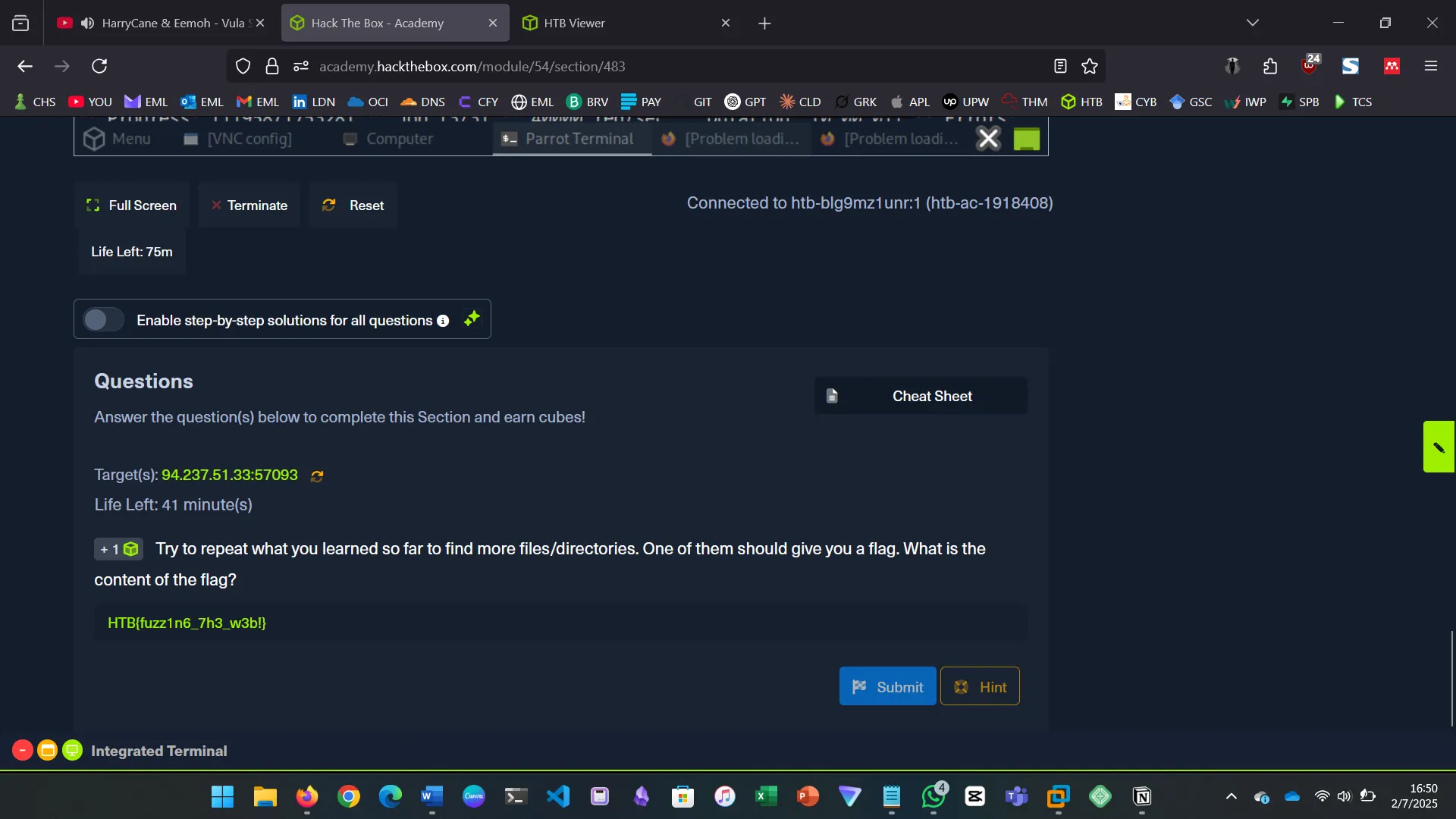
Try to repeat what you learned so far to find more files/directories. One of them should give you a flag. What is the content of the flag?
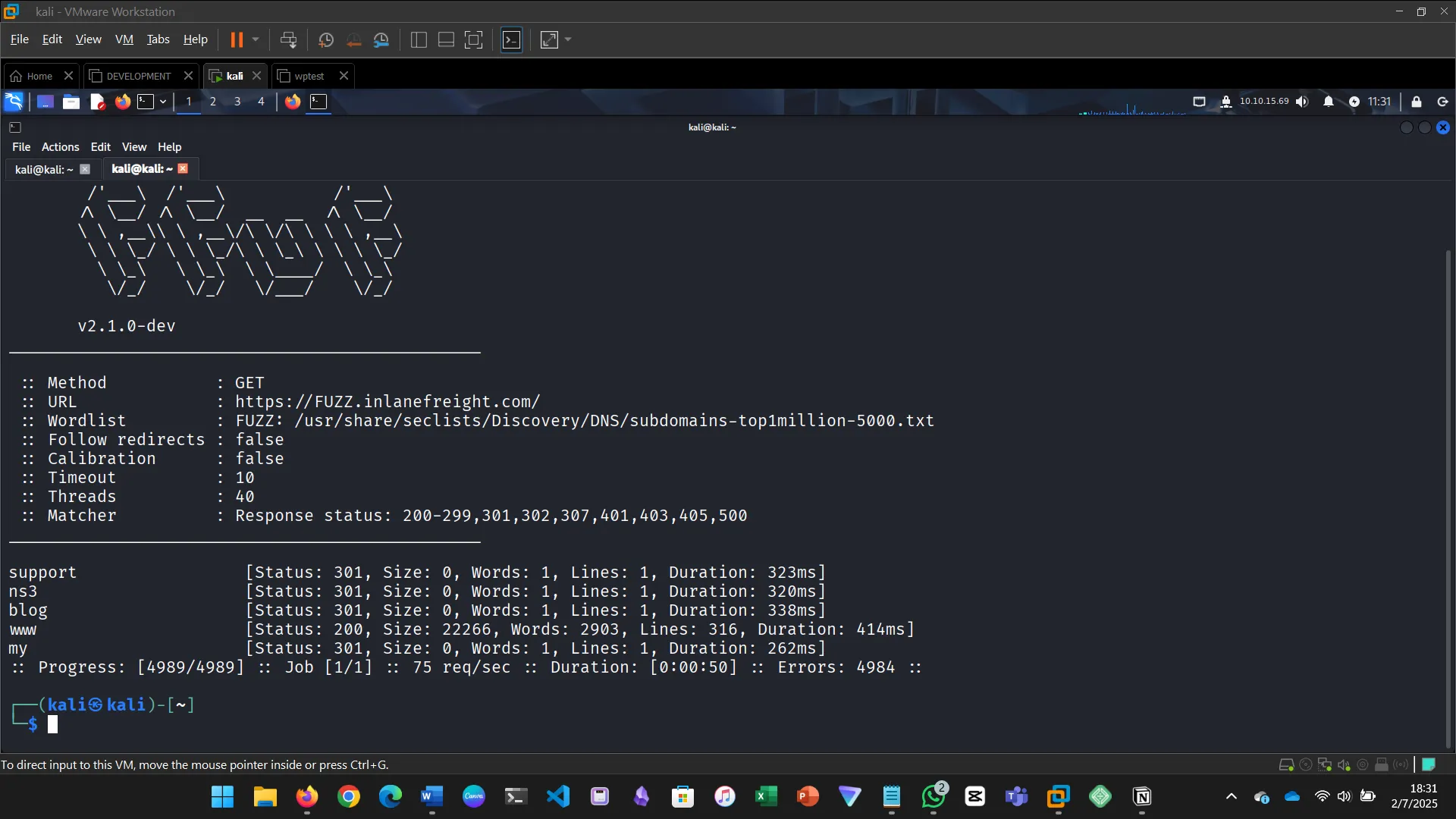
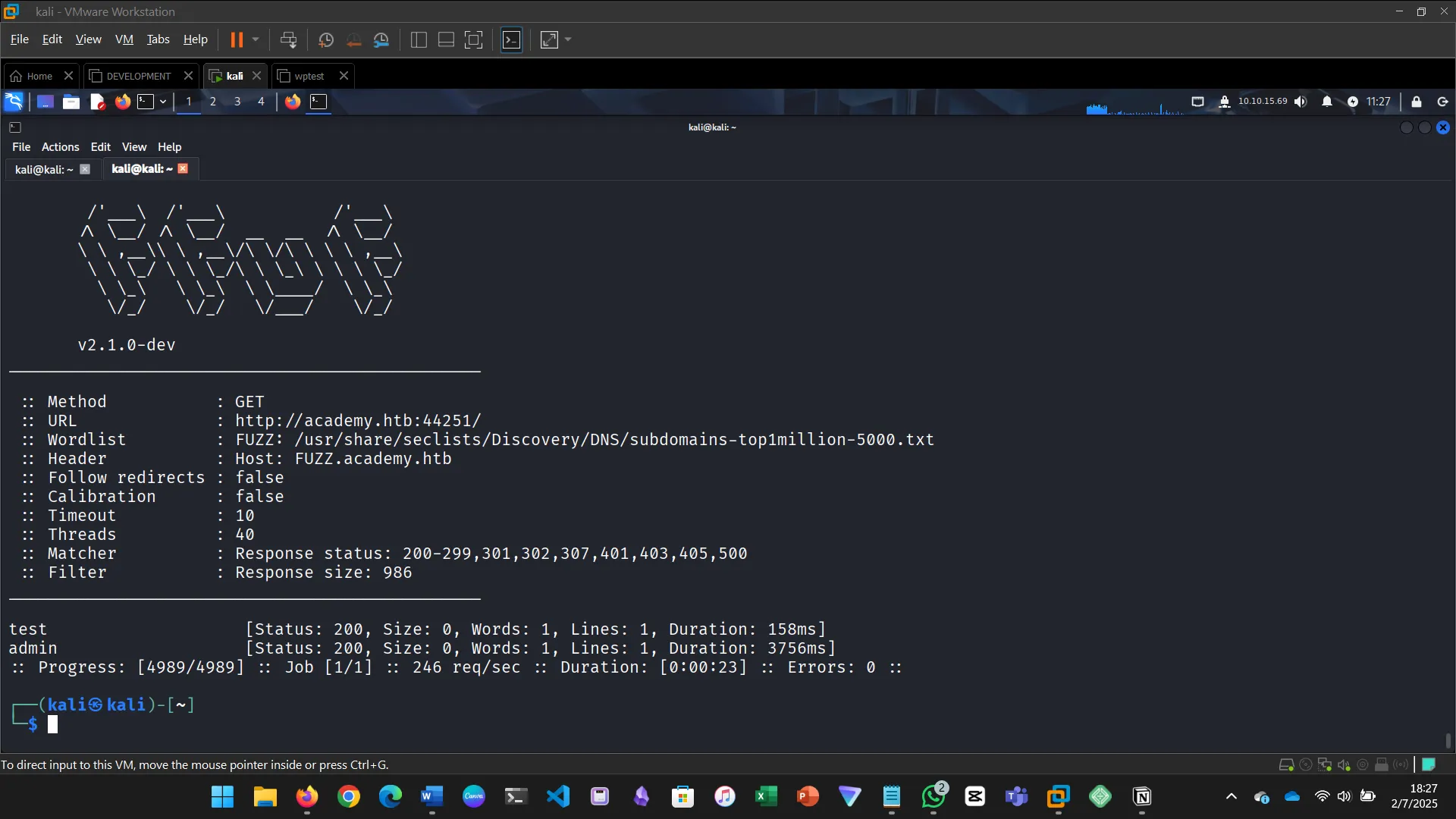
5. SUBDOMAIN FUZZING
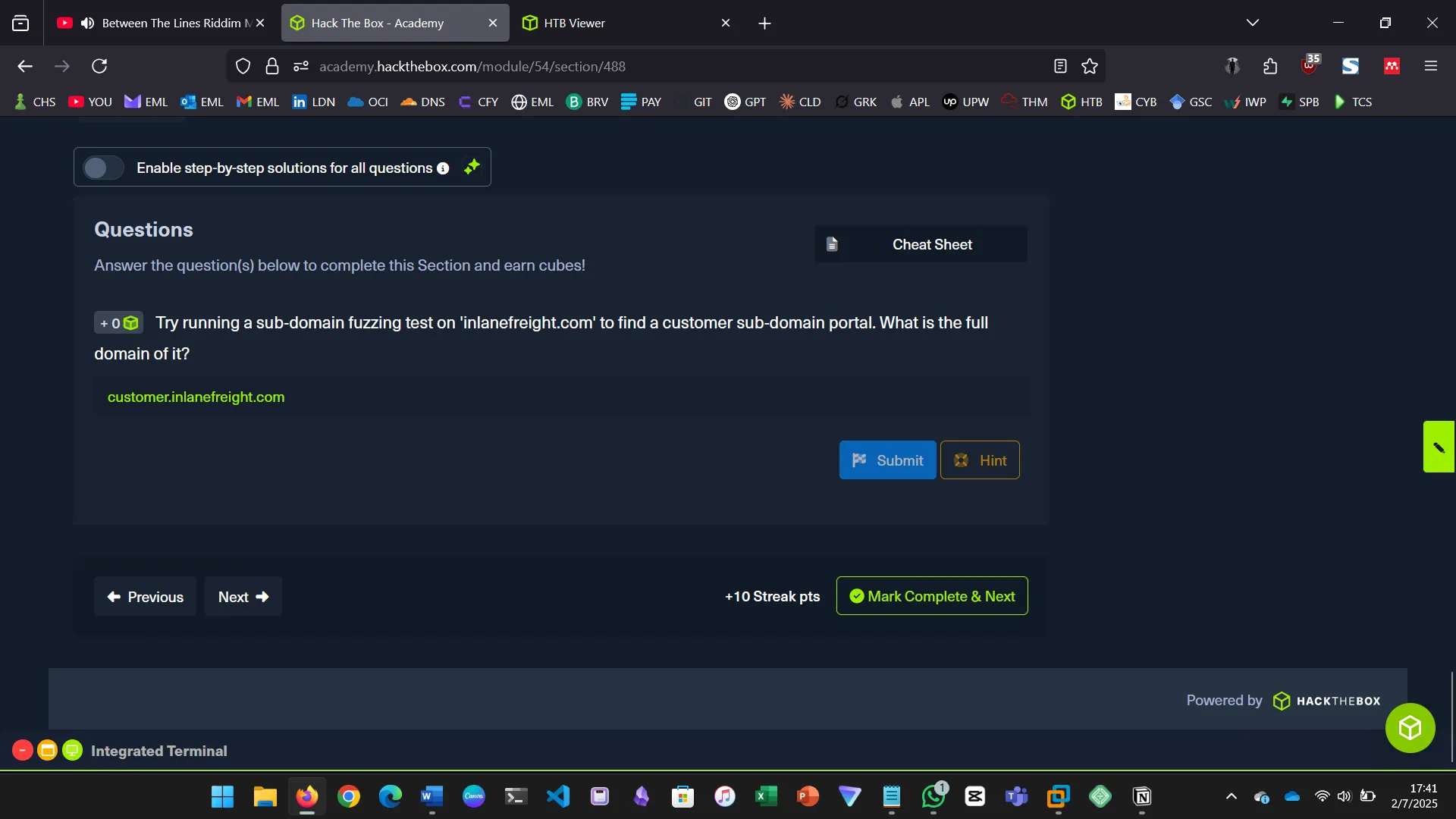
Try running a sub-domain fuzzing test on ‘inlanefreight.com’ to find a customer sub-domain portal. What is the full domain of it?
6. FILTERING RESULTS
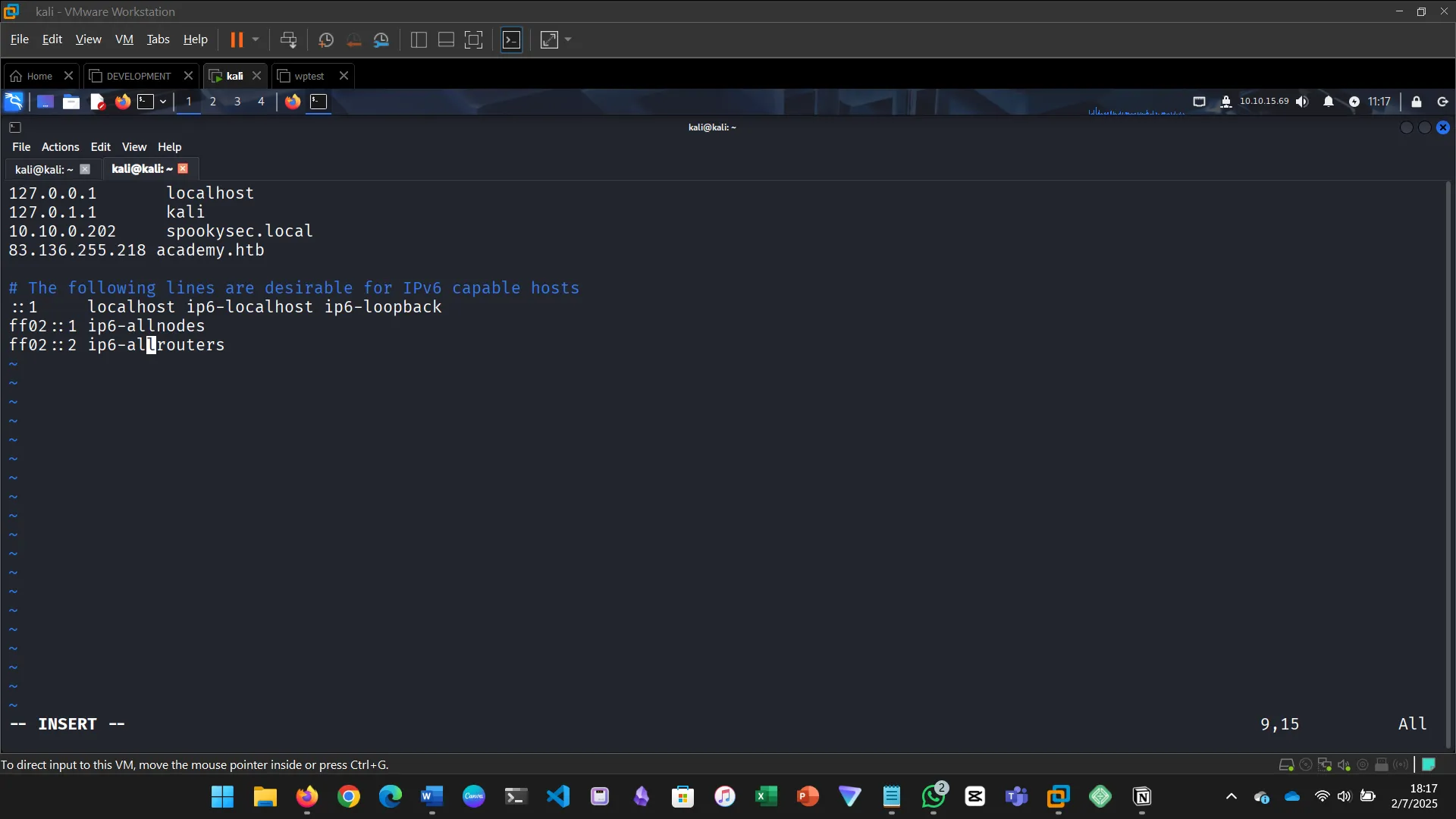
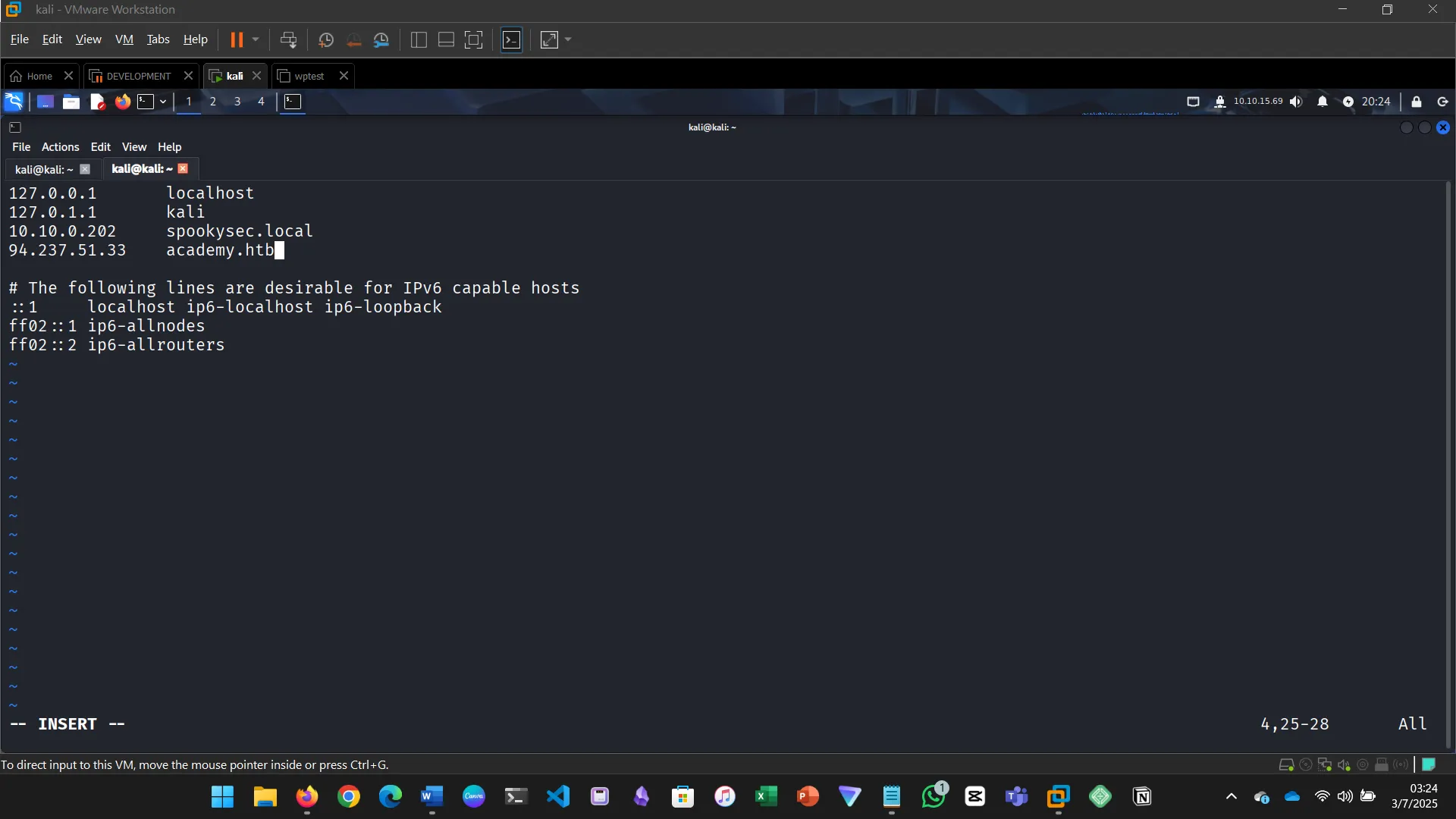
The challenge for this section required editing the hosts file because .htb is not a standard TLD. Task was to do VHost fuzzing on academy.htb and discover other VHosts.
Try running a VHost fuzzing scan on ‘academy.htb’, and see what other VHosts you get. What other VHosts did you get?
7. PARAMETER FUZZING — GET
Using what you learned in this section, run a parameter fuzzing scan on this page. What is the parameter accepted by this webpage?
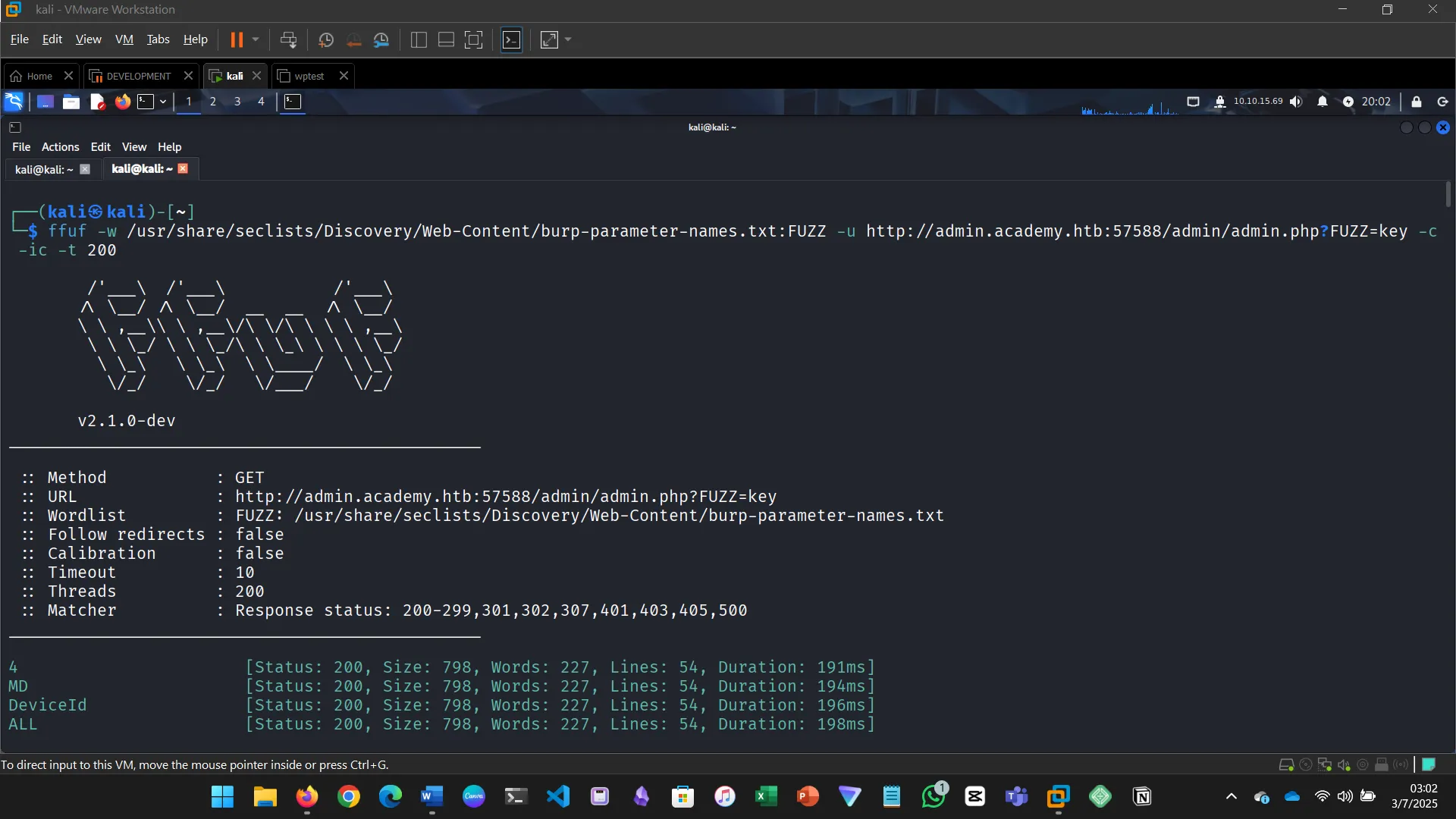
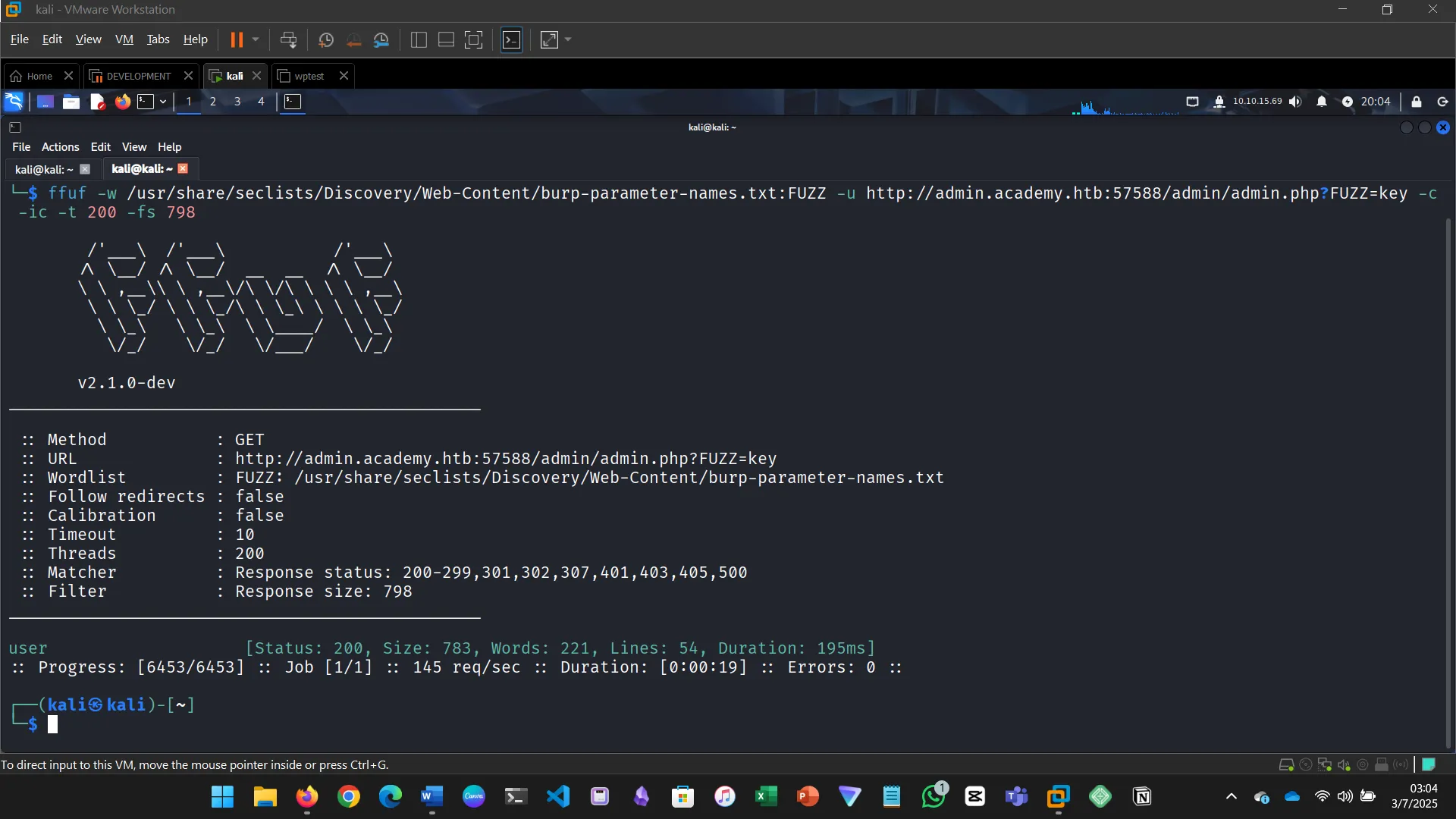
8. VALUE FUZZING
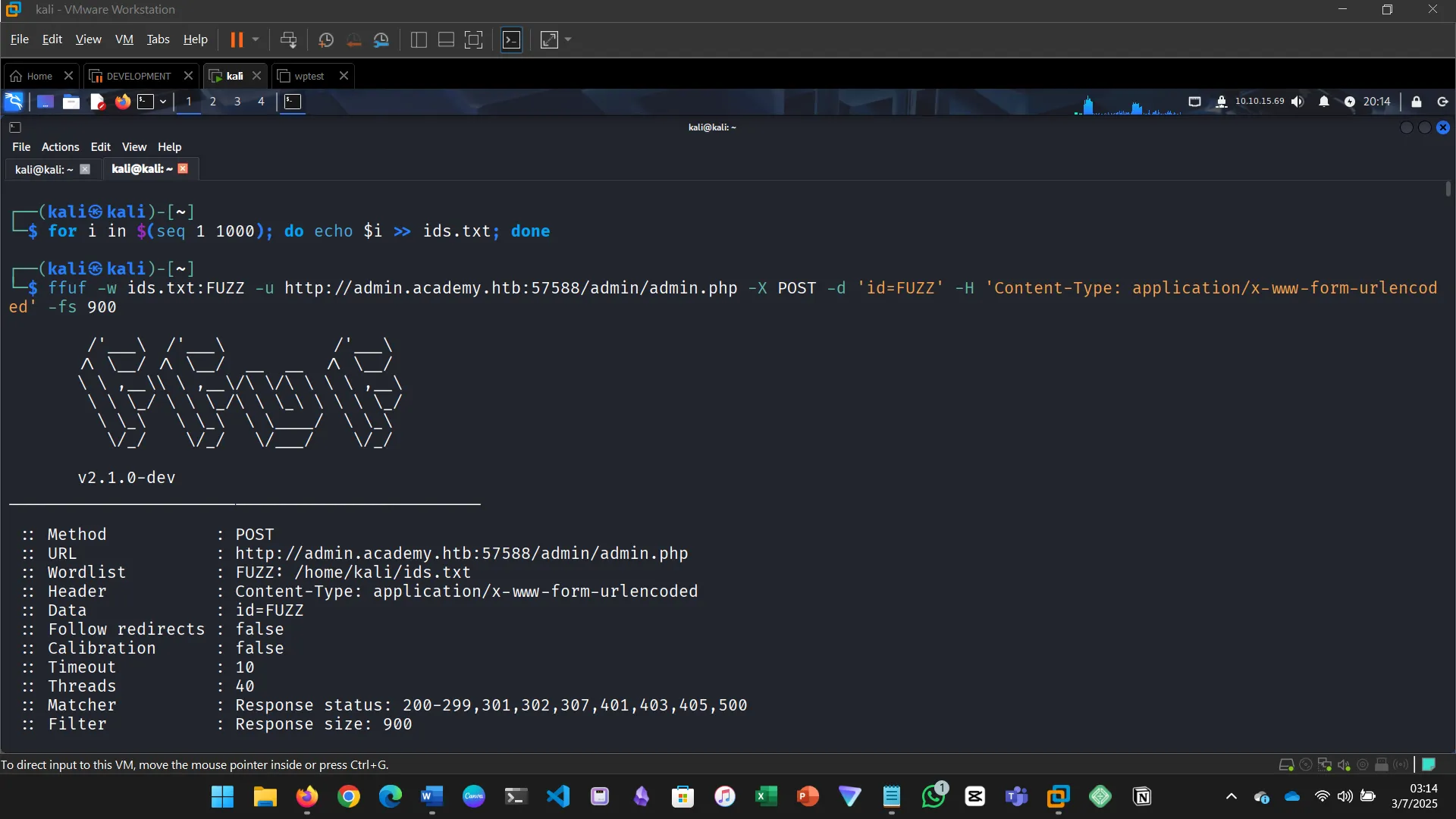
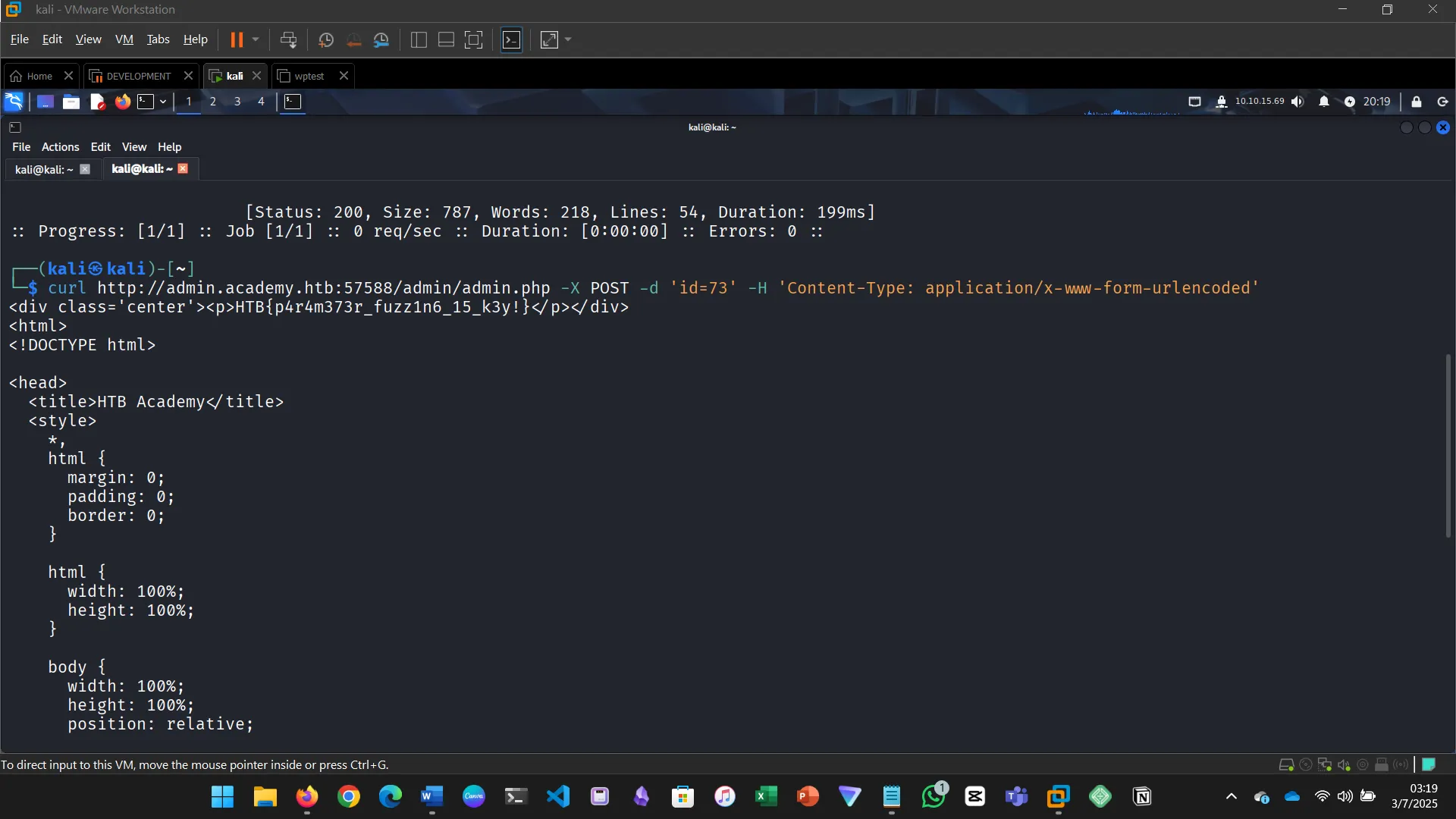
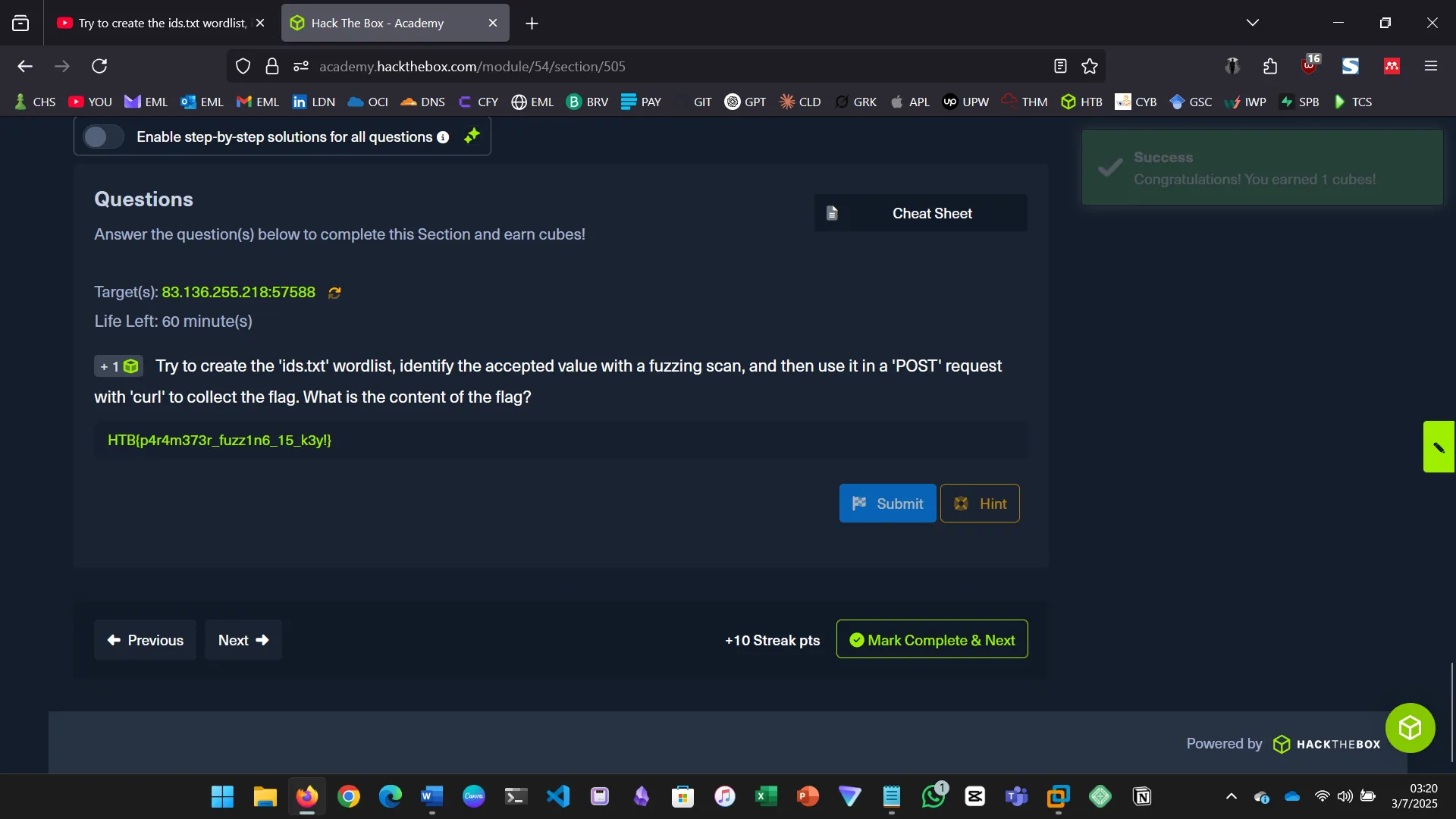
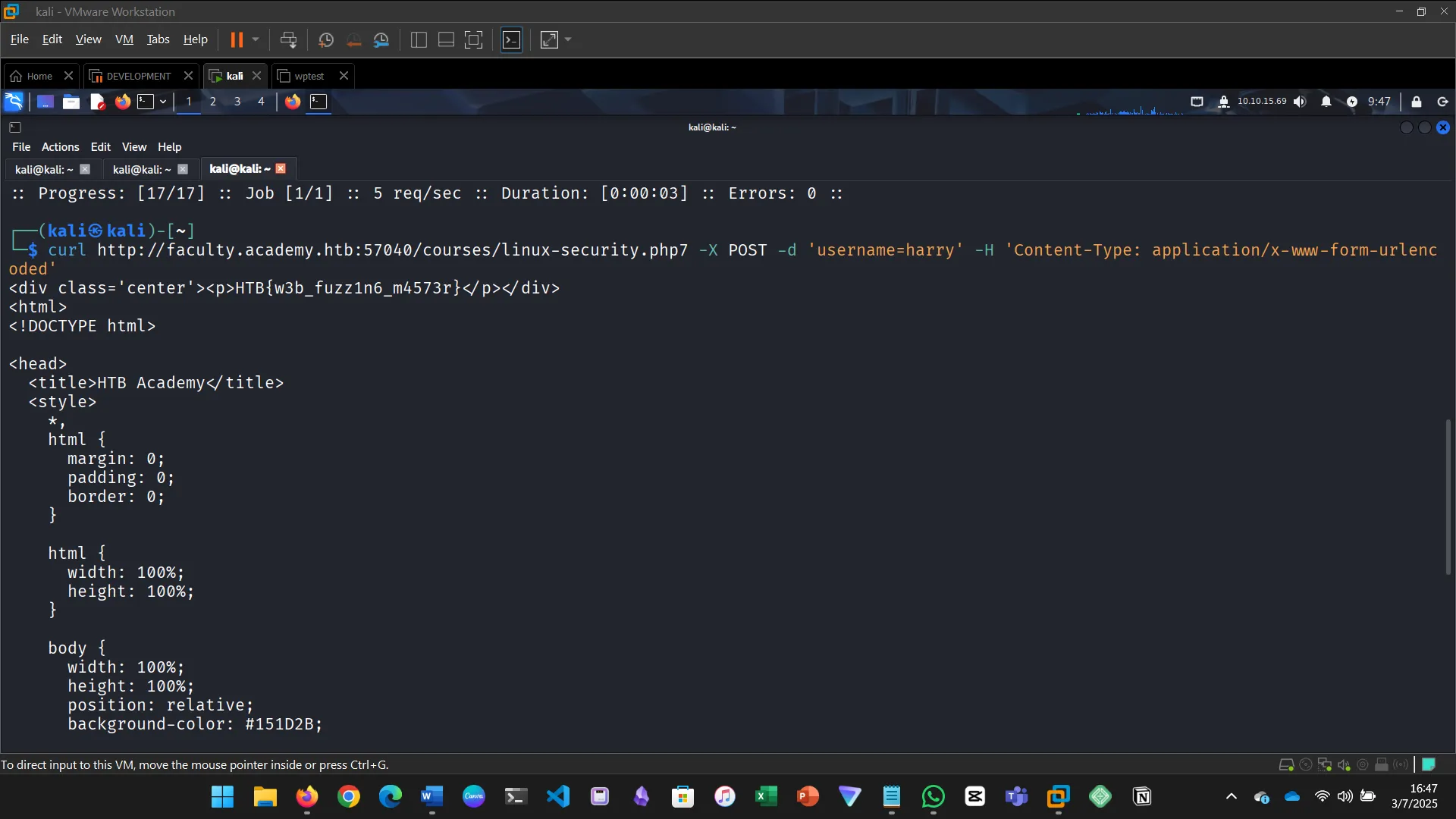
Try to create the ‘ids.txt’ wordlist, identify the accepted value with a fuzzing scan, and then use it in a ‘POST’ request with ‘curl’ to collect the flag. What is the content of the flag?
9. SKILLS ASSESSMENT — WEB FUZZING
The skills assessment was more of a recap on the whole module, now unguided.
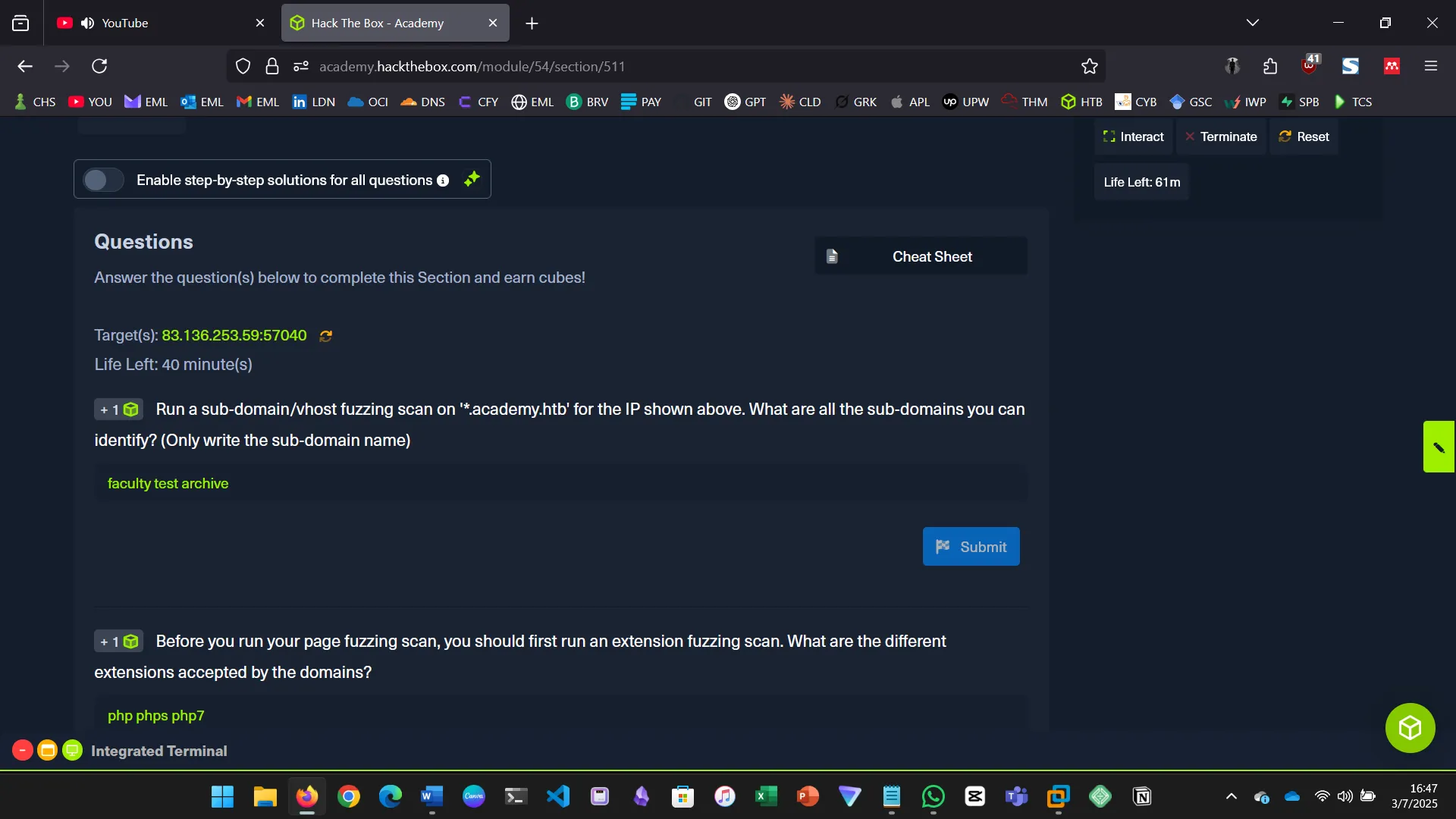
Run a sub-domain/vhost fuzzing scan on ‘.academy.htb’ for the IP shown above. What are all the sub-domains you can identify? (Only write the sub-domain name)*
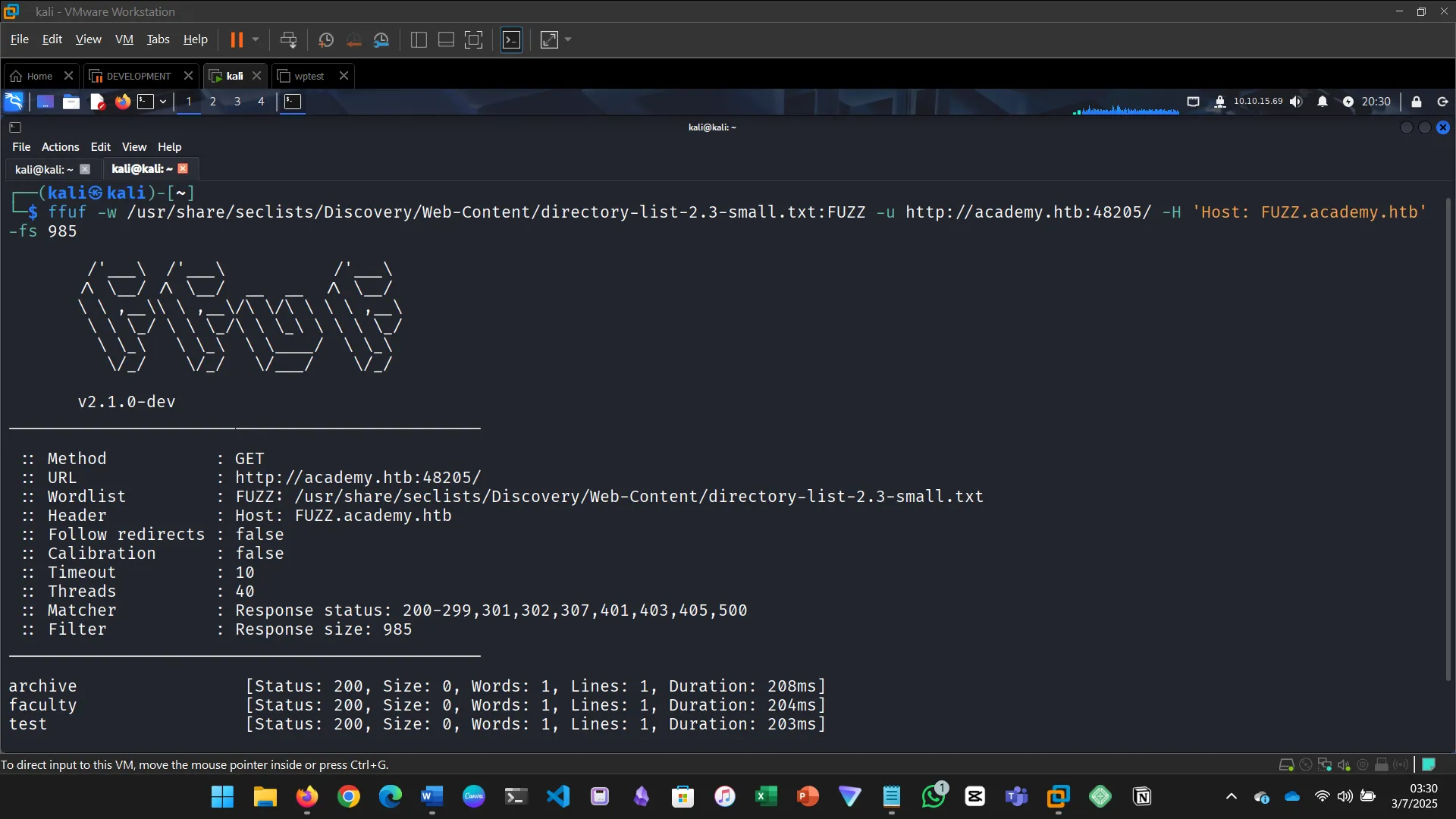
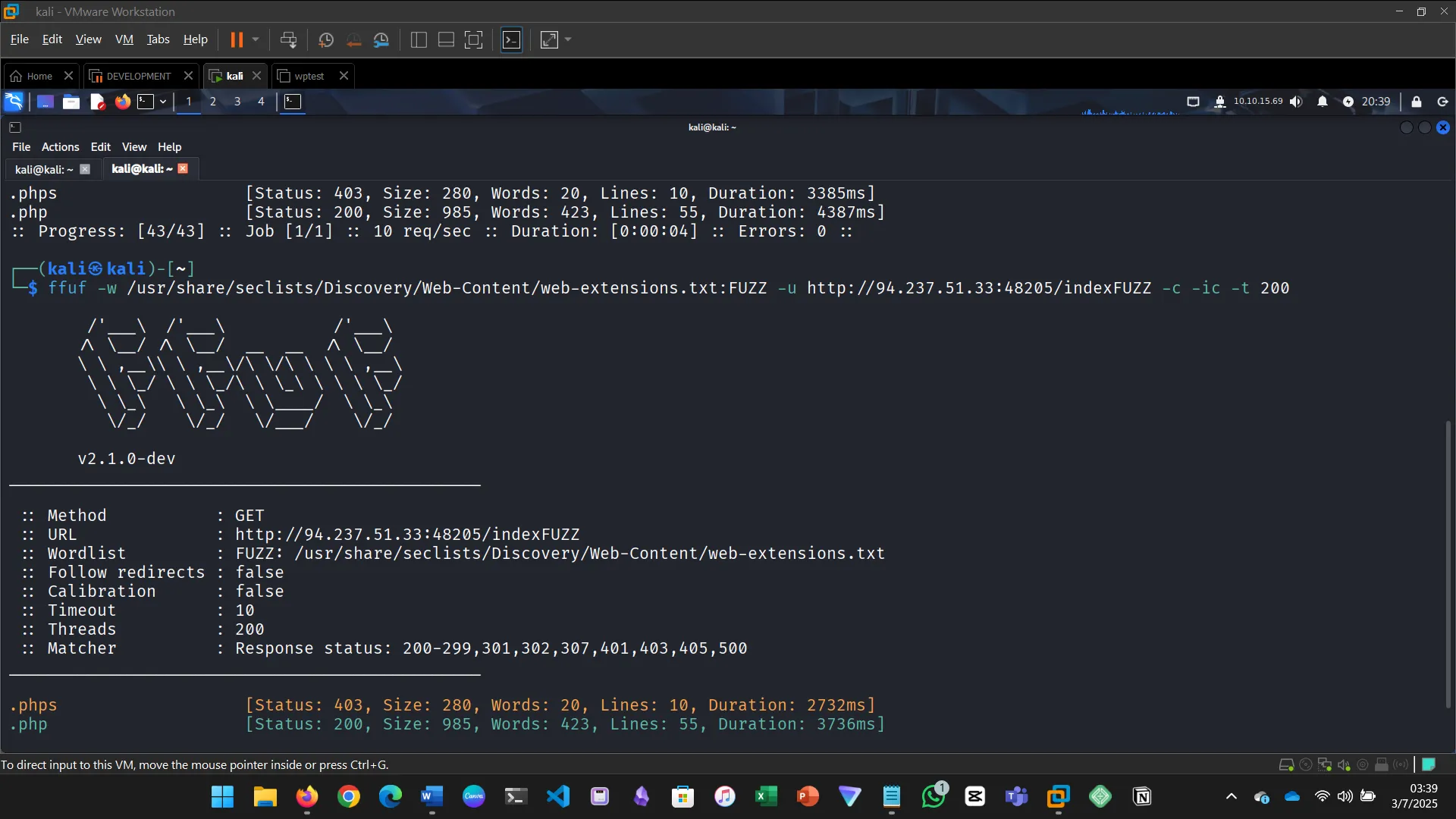
Before you run your page fuzzing scan, you should first run an extension fuzzing scan. What are the different extensions accepted by the domains?
One of the pages you will identify should say ‘You don’t have access!’. What is the full page URL?
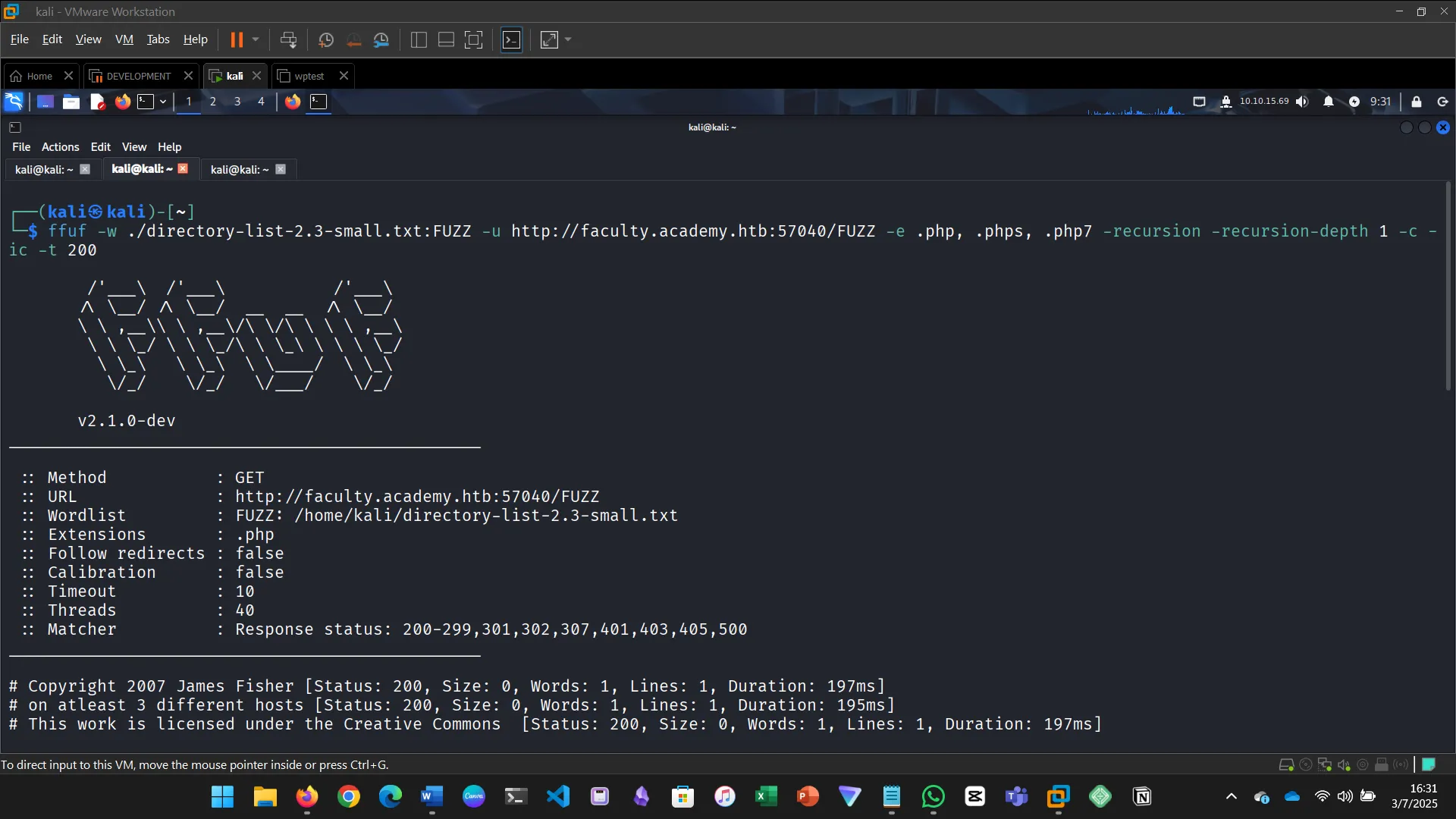
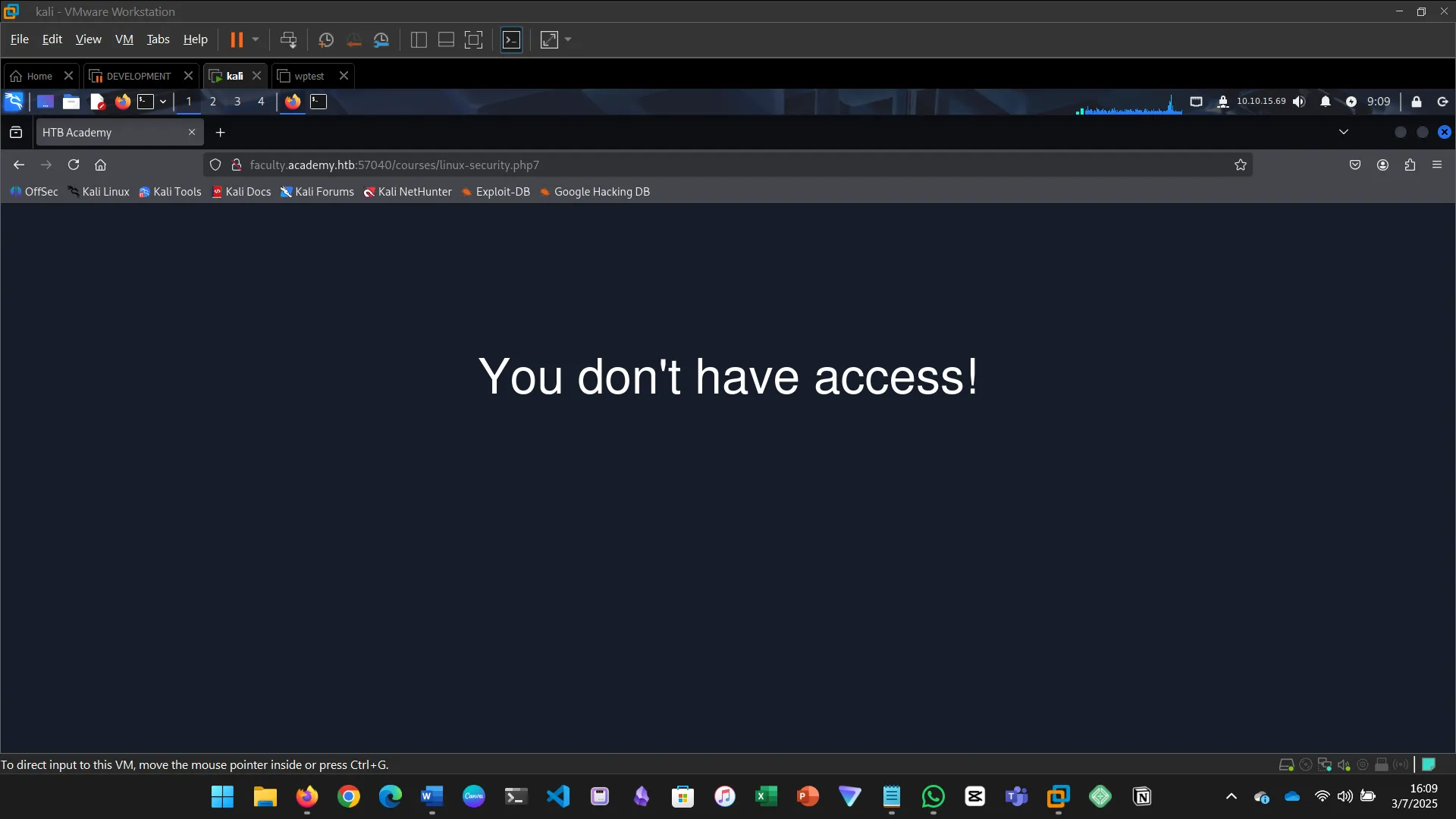
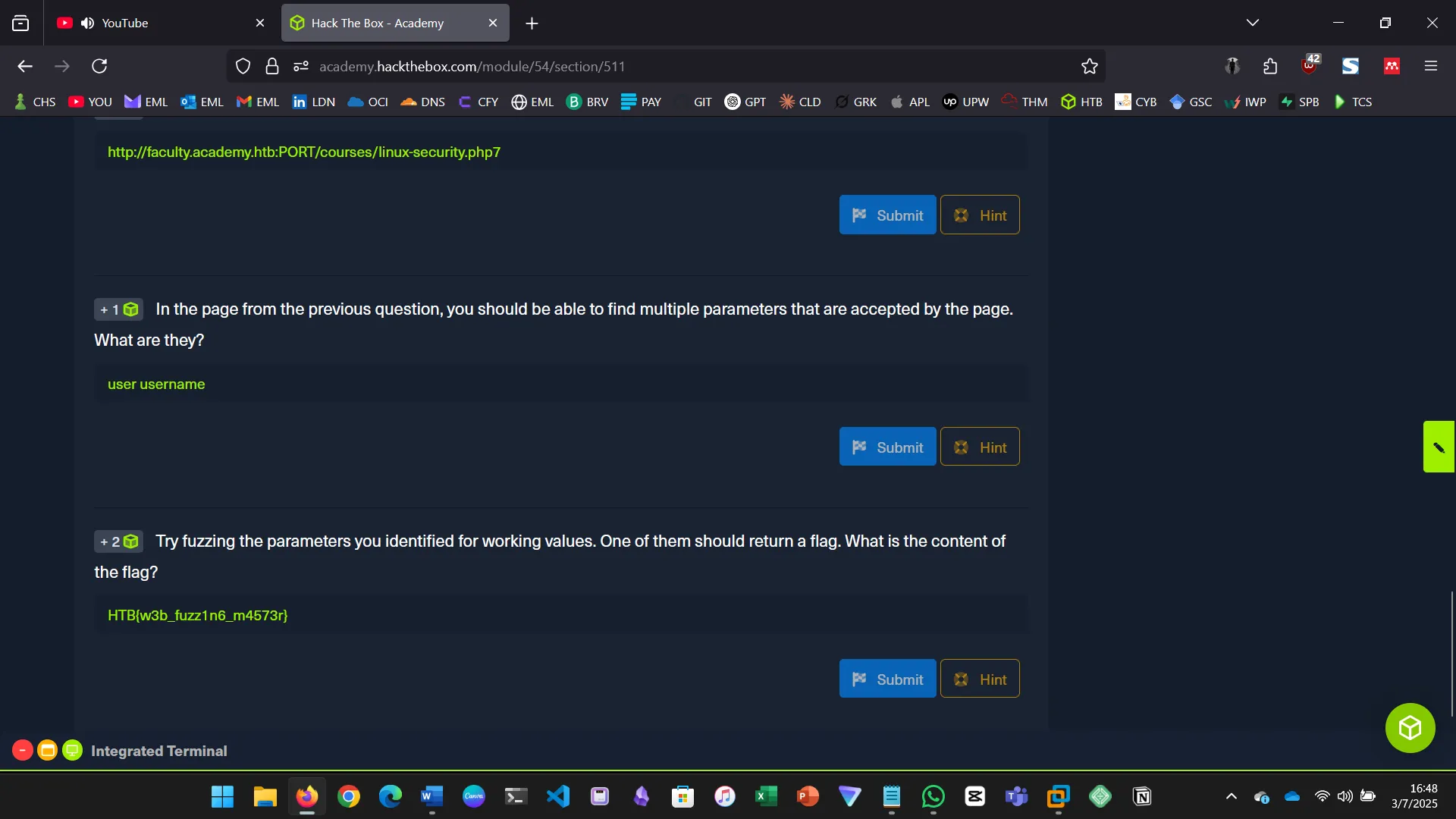
In the page from the previous question, you should be able to find multiple parameters that are accepted by the page. What are they?
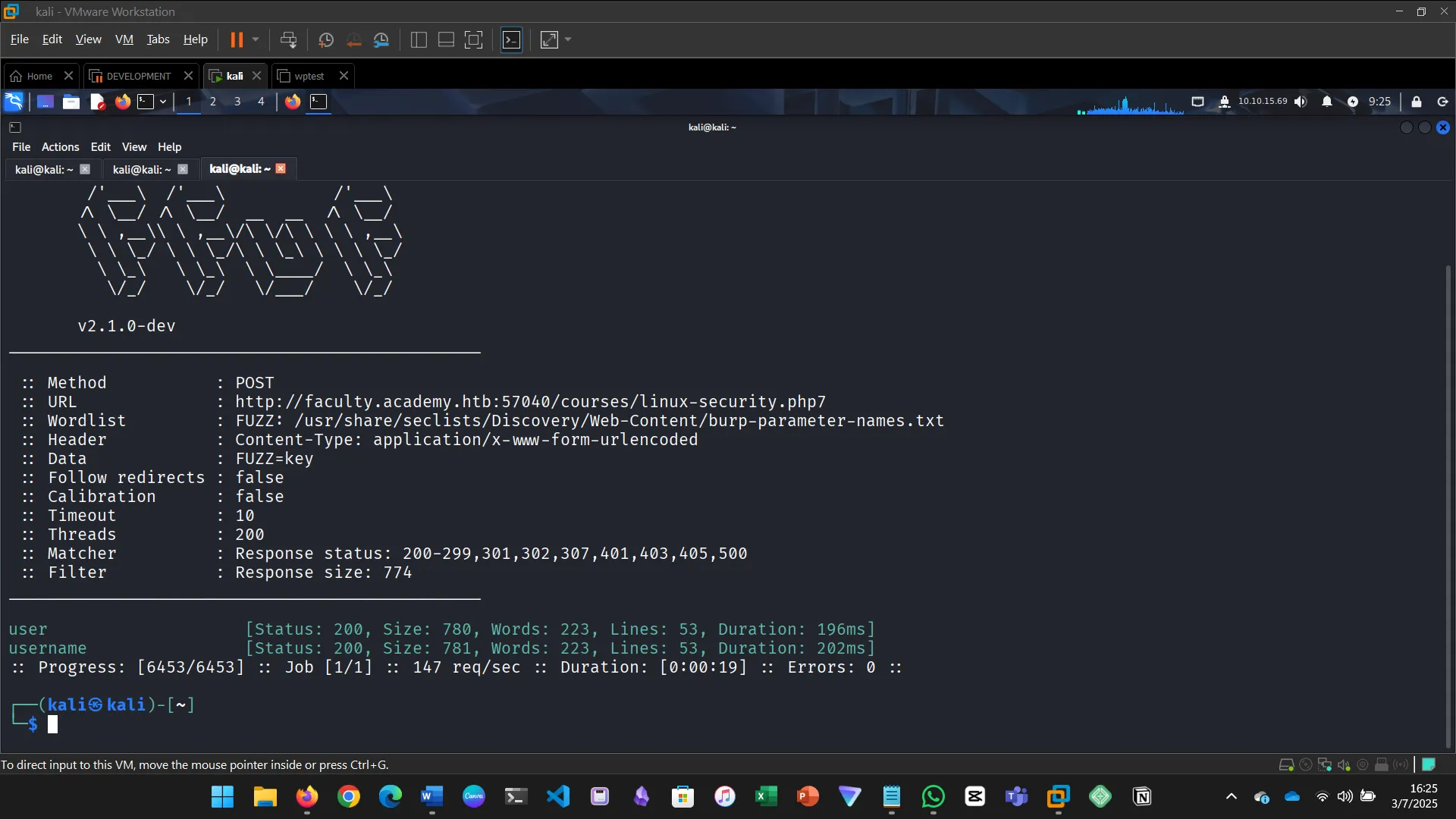
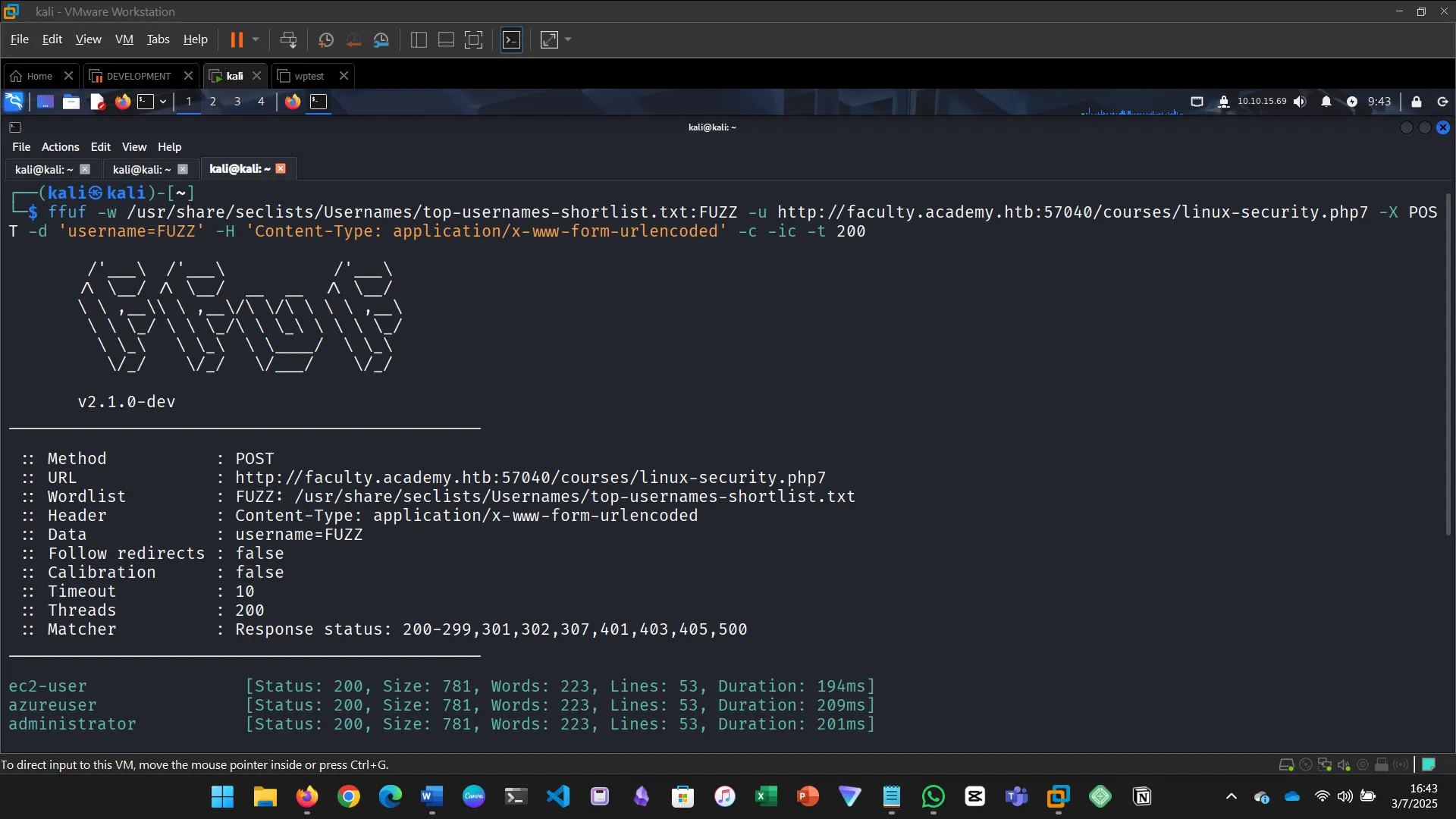
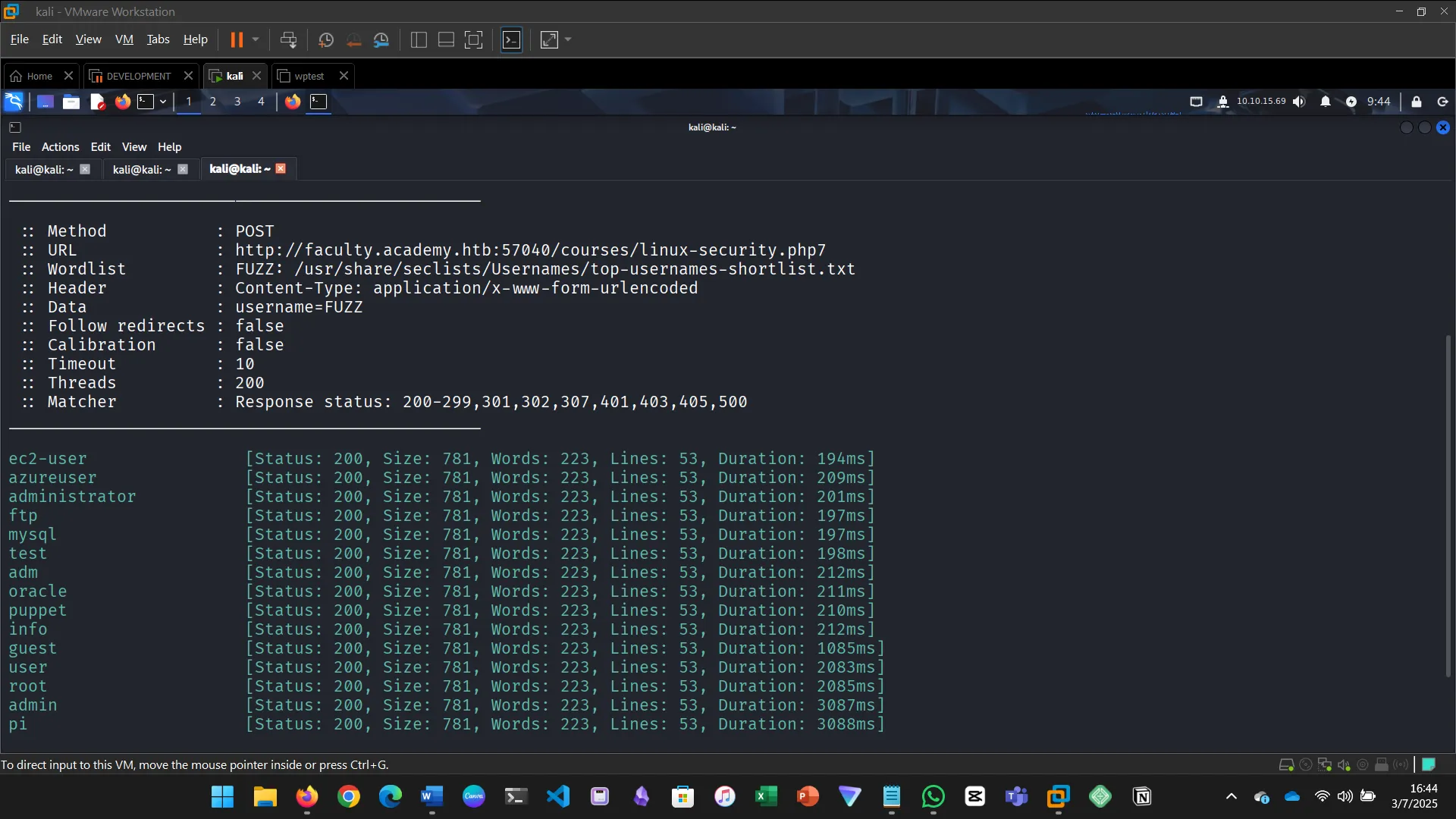
Try fuzzing the parameters you identified for working values. One of them should return a flag. What is the content of the flag?
10. CONCLUSION
The module was quite intensive, yet very enriching. The skills assessment was carefully crafted, it managed to fill all gaps that had been left by the guided walkthroughs. There was quite a number of eye openers into troubleshooting, solving problems, and critical thinking. Coupled with the fact that I underestimated the module, it was a wake-up call.