1. Introduction
I presumed the aim of this module was to provide foundational knowledge of the Windows Operating System relevant to cybersecurity. Although I’ve used Windows for years, this was a deep and structured dive into its internals—covering NTFS permissions, service management, system security, and administrative tools.
2. Windows Overview
The course began with a history and versioning of Windows OS. It also introduced remote access techniques and tools such as XFreeRDP, which I used for practical exercises.
3. Operating System Structure
We explored the standard Windows directory structure, from root folders to user-created paths, and how to navigate them using the command line.
4. File System
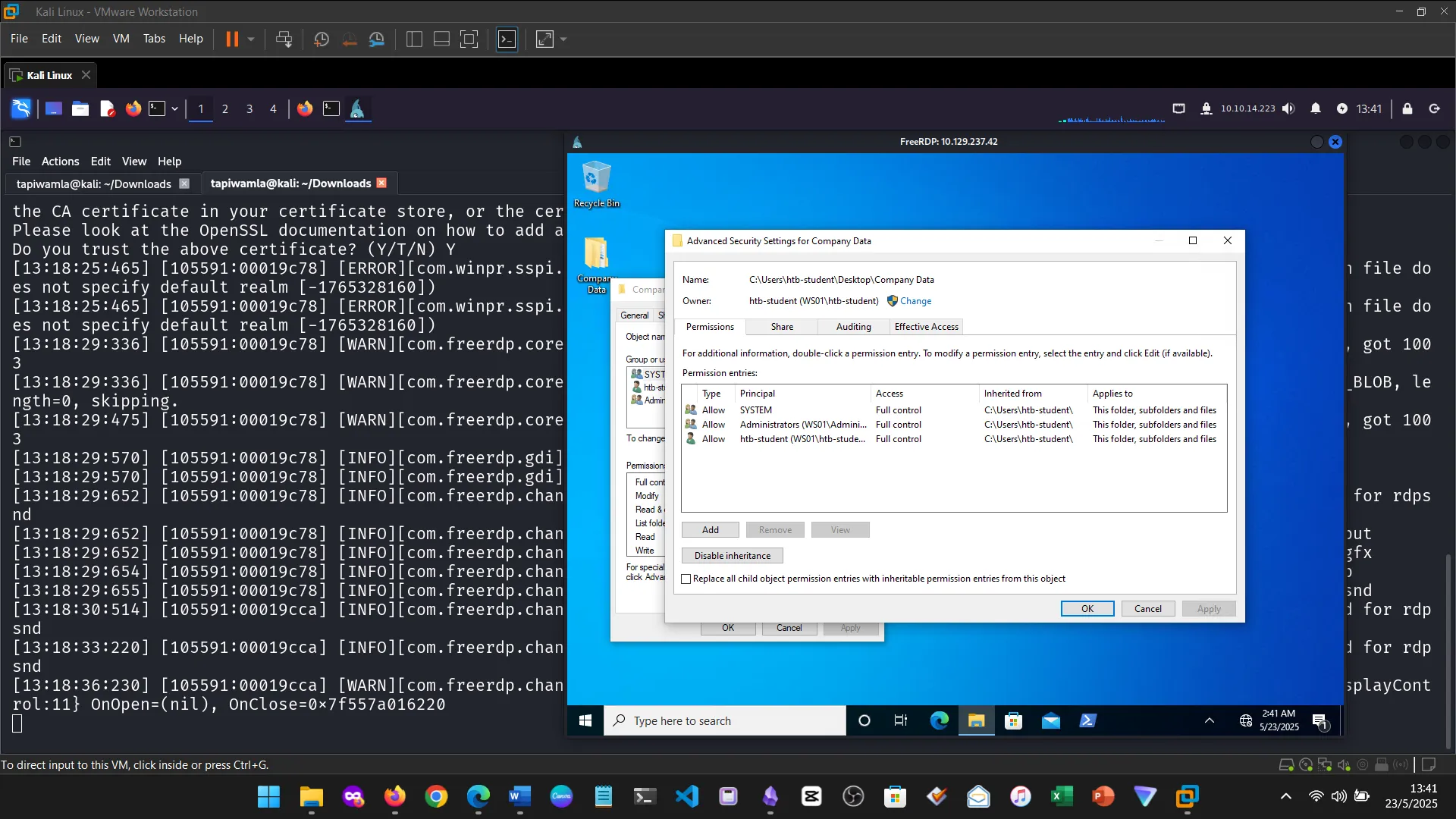
This section discussed FAT32, exFAT, and NTFS. I focused on how NTFS supports access control via ICACLS, ACLs, and permissions, which are vital in Windows security.
5. NTFS vs. Share Permissions
I learned the difference between NTFS permissions (local disk-level) and Share permissions (network-level), especially under SMB connections.
6. Windows Services and Processes
This section was particularly enlightening. I explored how services are essentially long-running processes, and how tools like SysInternals Suite offer powerful insights into system behavior without needing installation.
7. Service Permissions
I hadn’t considered how dangerous misconfigured service permissions could be. This section showed how such mistakes can allow privilege escalation or persistence by attackers.
8. Windows Sessions
Covered the differences between interactive and non-interactive sessions. Key takeaway: system accounts like NT AUTHORITY\SYSTEM, LocalService, and NetworkService run non-interactively.
9. Interacting with Windows
This was practical-heavy: interacting via CMD, PowerShell, RDP, and GUI. Each interface offers different levels of control. I became comfortable using CLI tools and managing the system remotely.
10. Windows Management Instrumentation (WMI)
WMI allows advanced control and monitoring of Windows machines. I practiced querying system info and controlling services using PowerShell and WMI commands.
11. Microsoft Management Console (MMC)
MMC allows administrators to create customizable management dashboards using snap-ins. It’s been around since Windows Server 2000 and remains useful today.
12. Windows Subsystem for Linux (WSL)
As a Linux CLI user, this section felt familiar. WSL lets you run Linux tools (like grep, awk, bash) directly on Windows, blending development and administration workflows.
13. Desktop Experience vs. Server Core
This section compared Windows Server Core (lightweight CLI) with Desktop Experience (GUI-based). Each has use cases based on resource needs and admin skills.
14. Windows Security
Covered key concepts:
- Security Identifiers (SIDs)
- Access Control Lists (ACLs)
- User Account Control (UAC)
The practical involved analyzing registry security and understanding how Windows implements layered security controls.
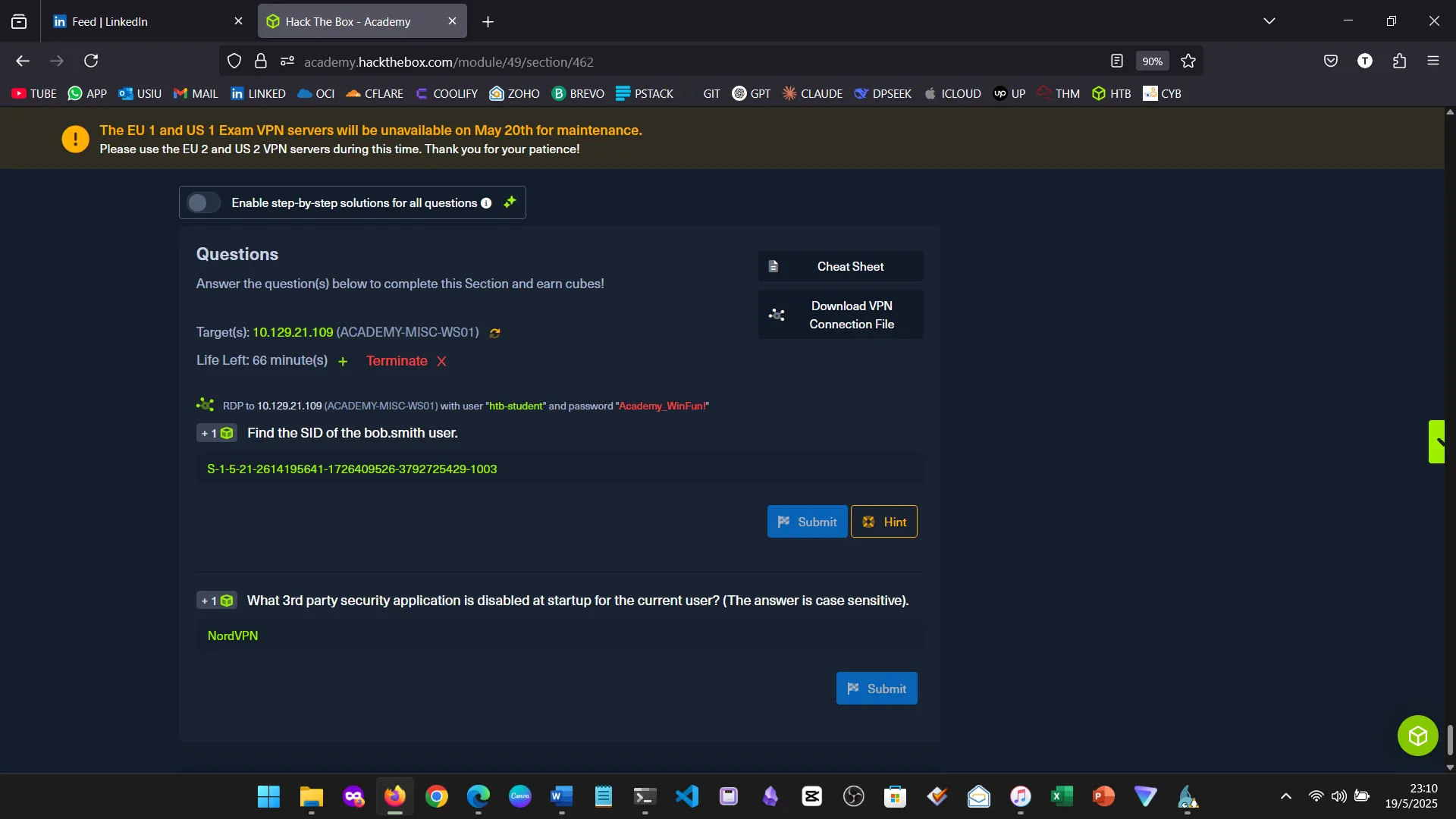
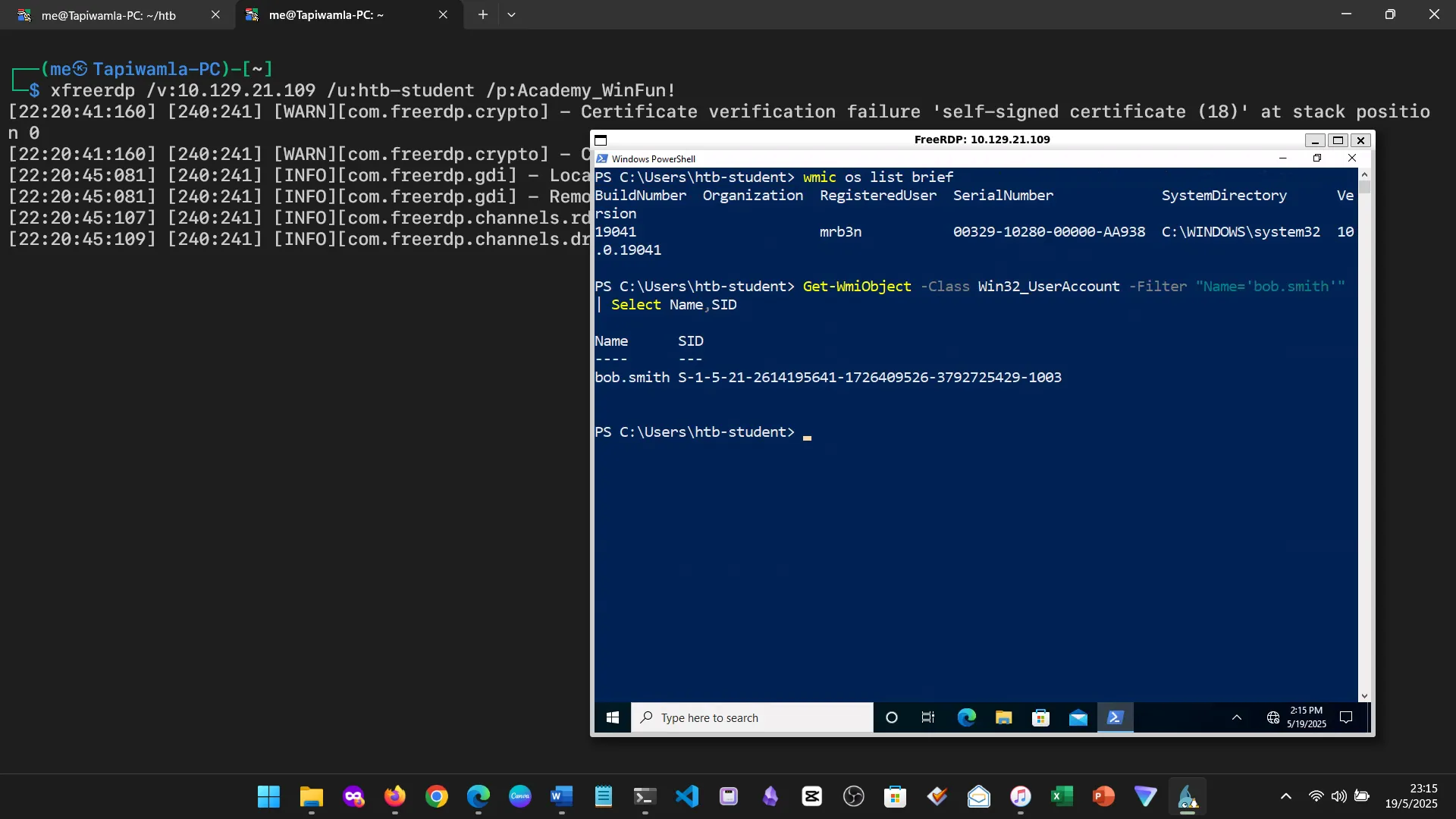
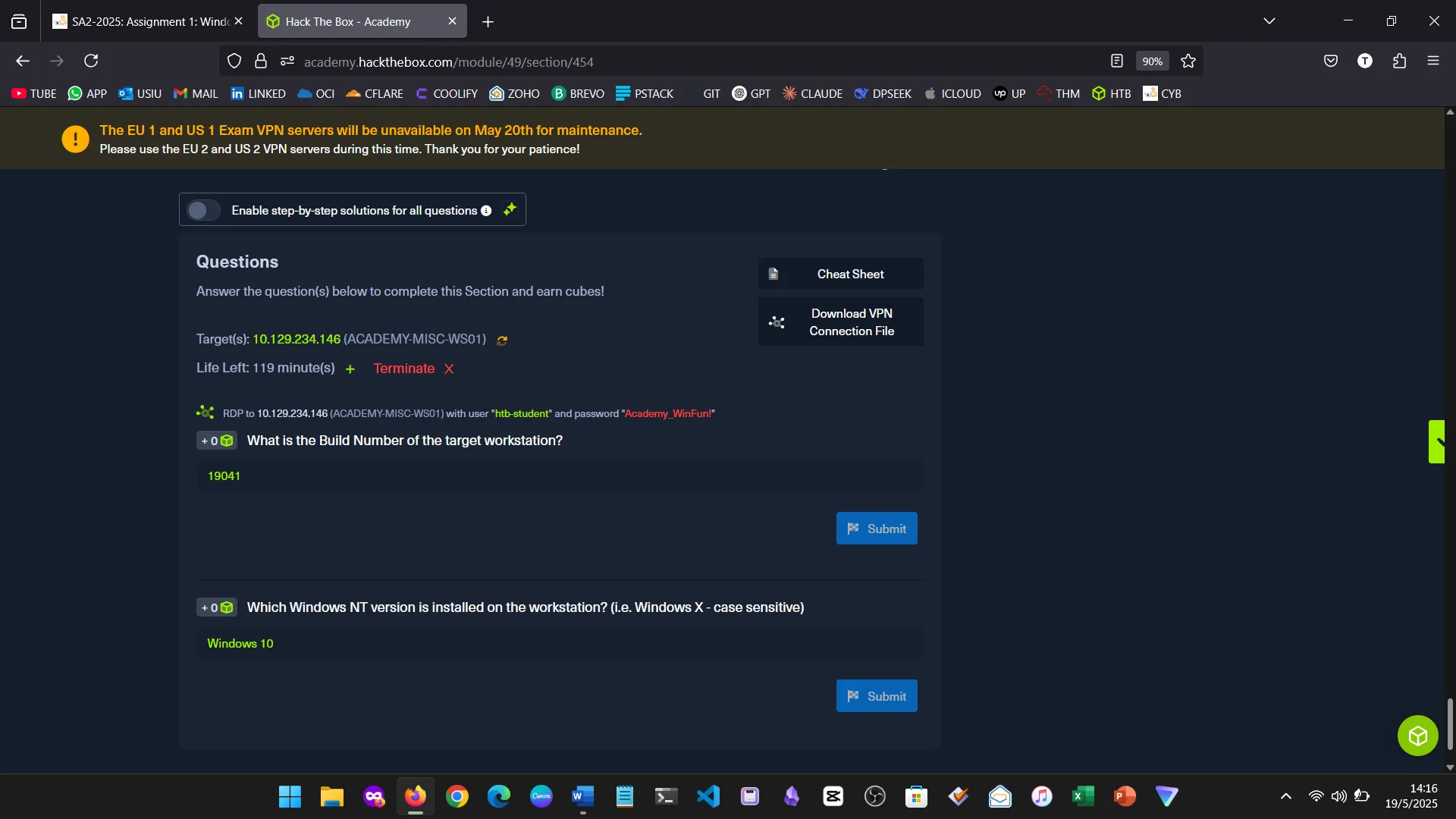
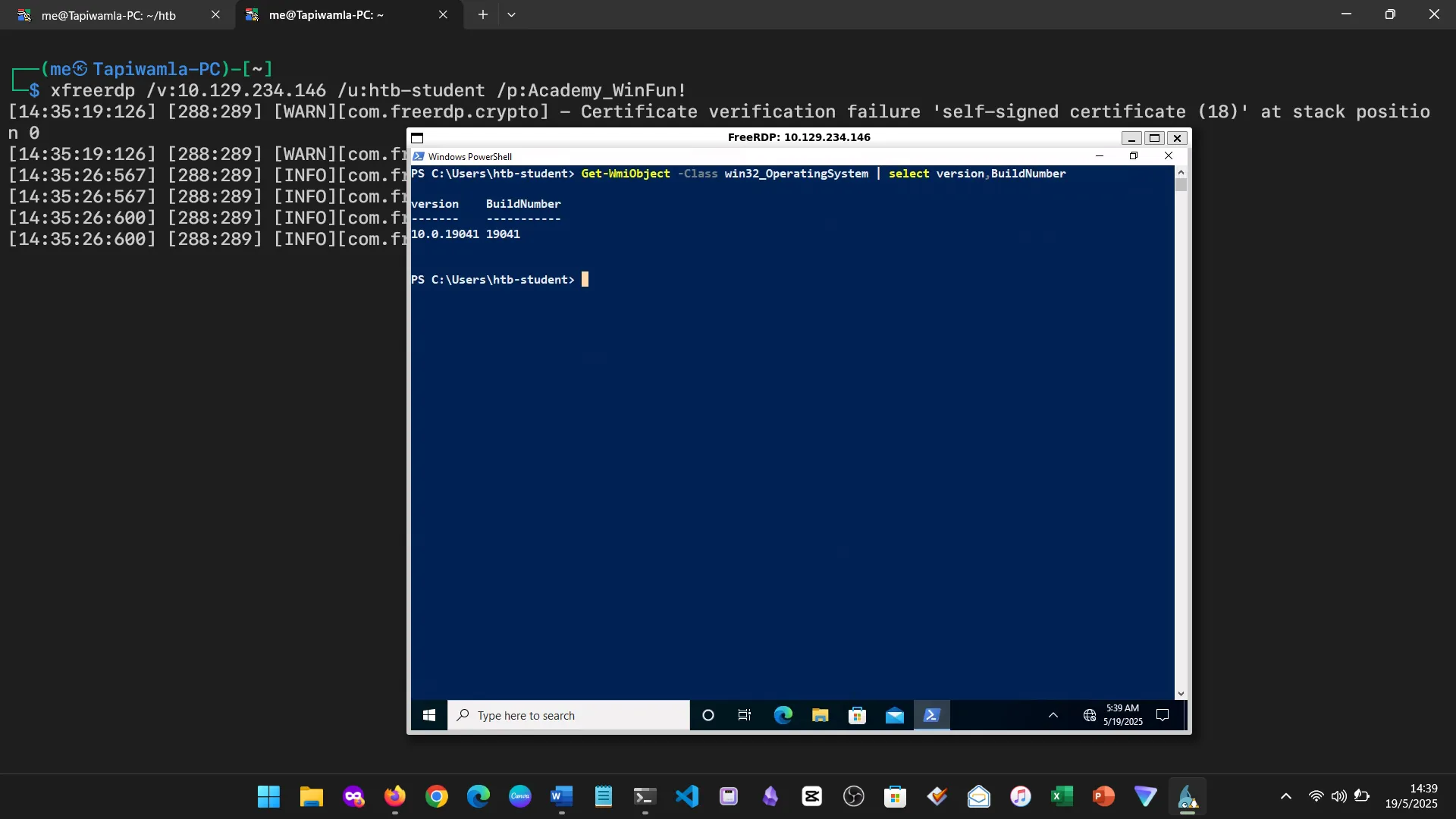
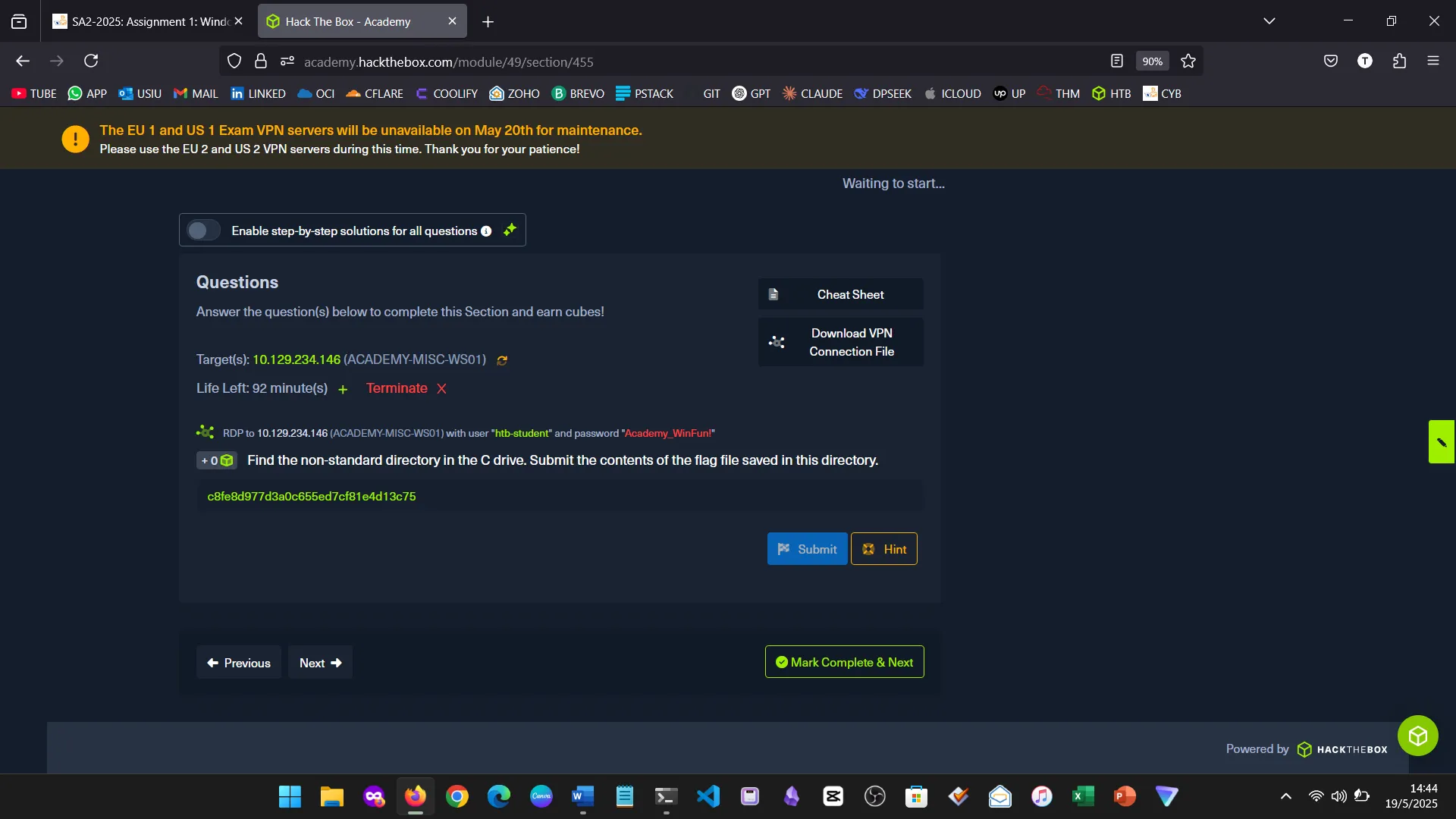
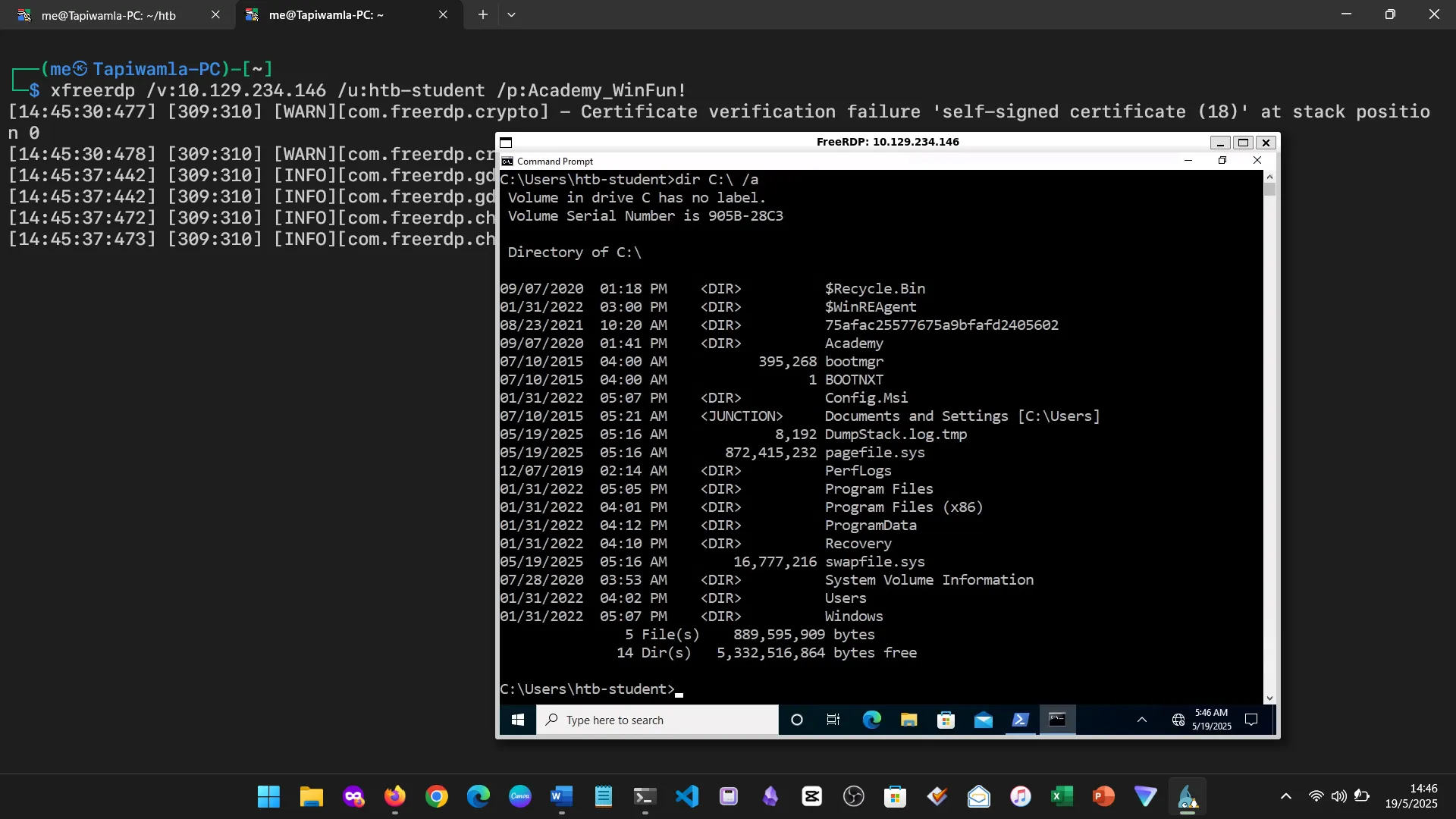
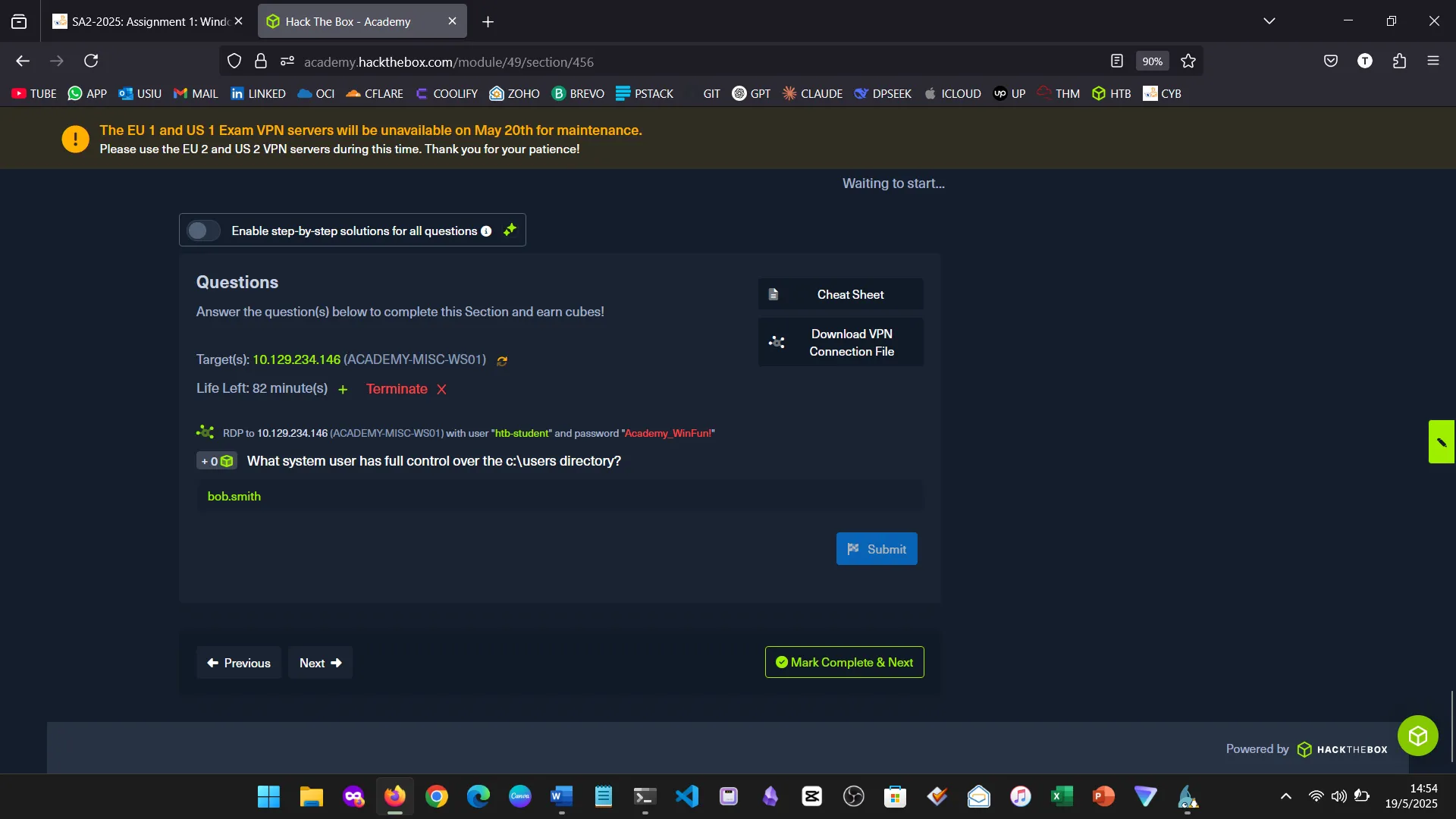
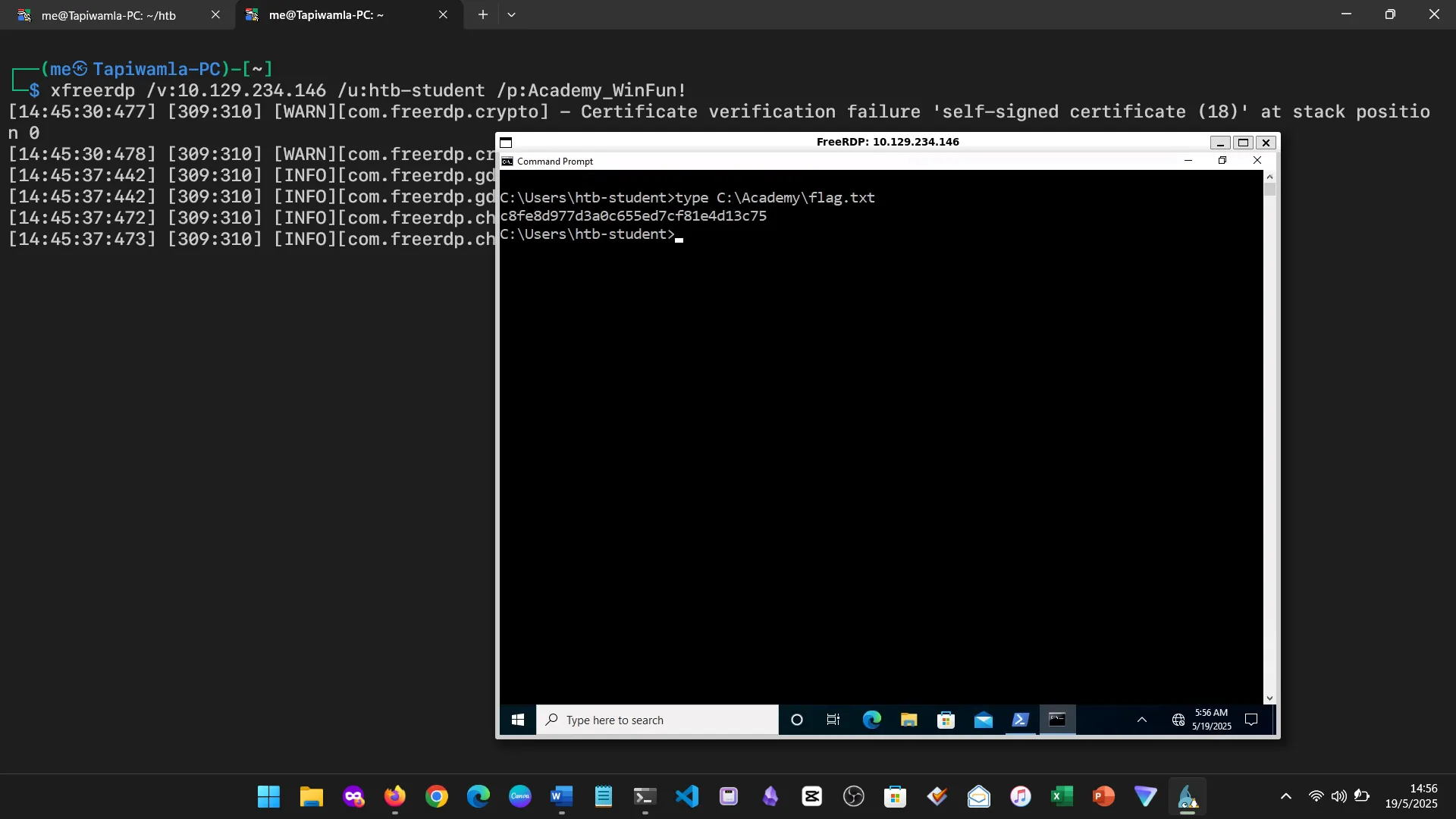
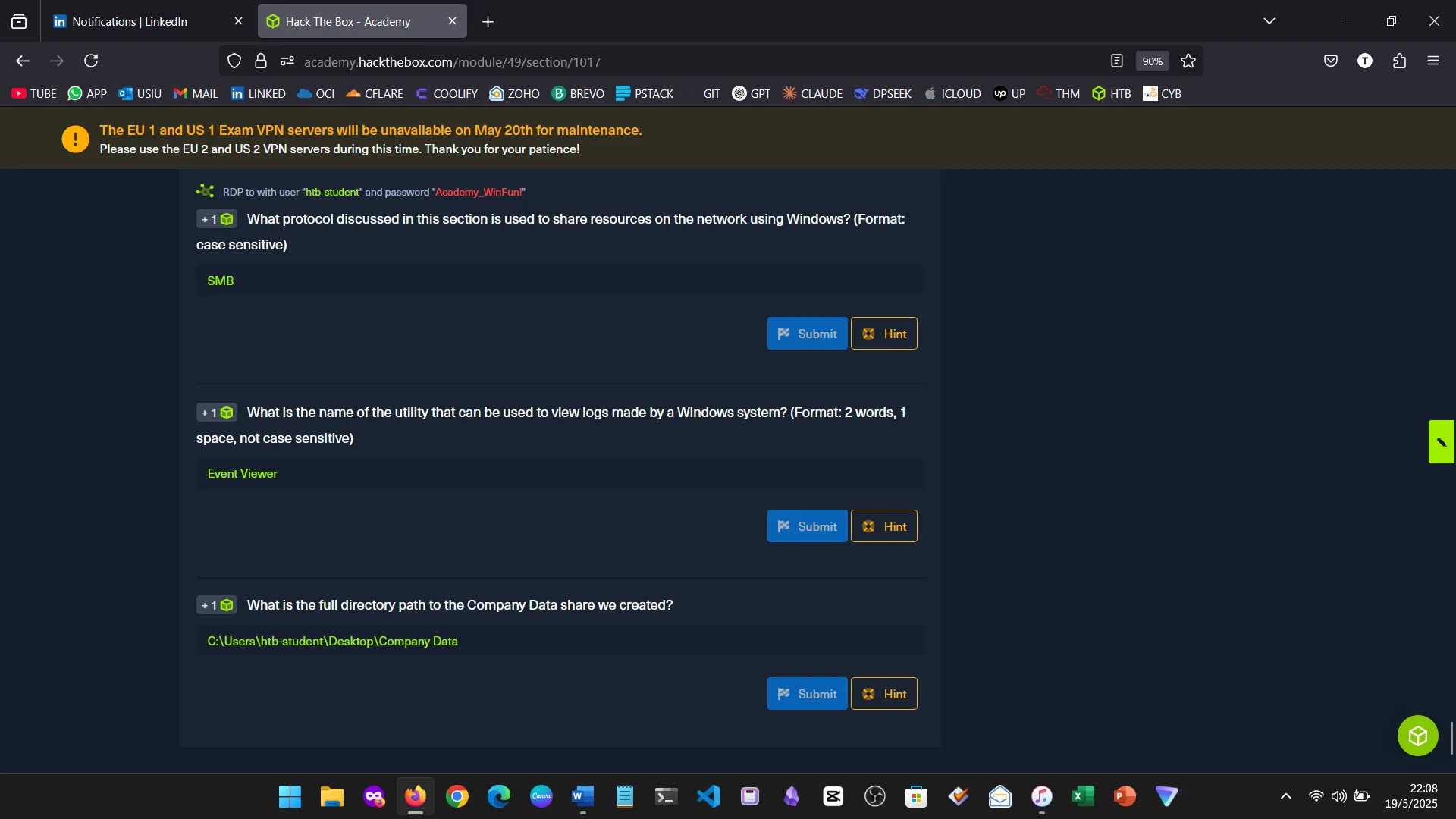
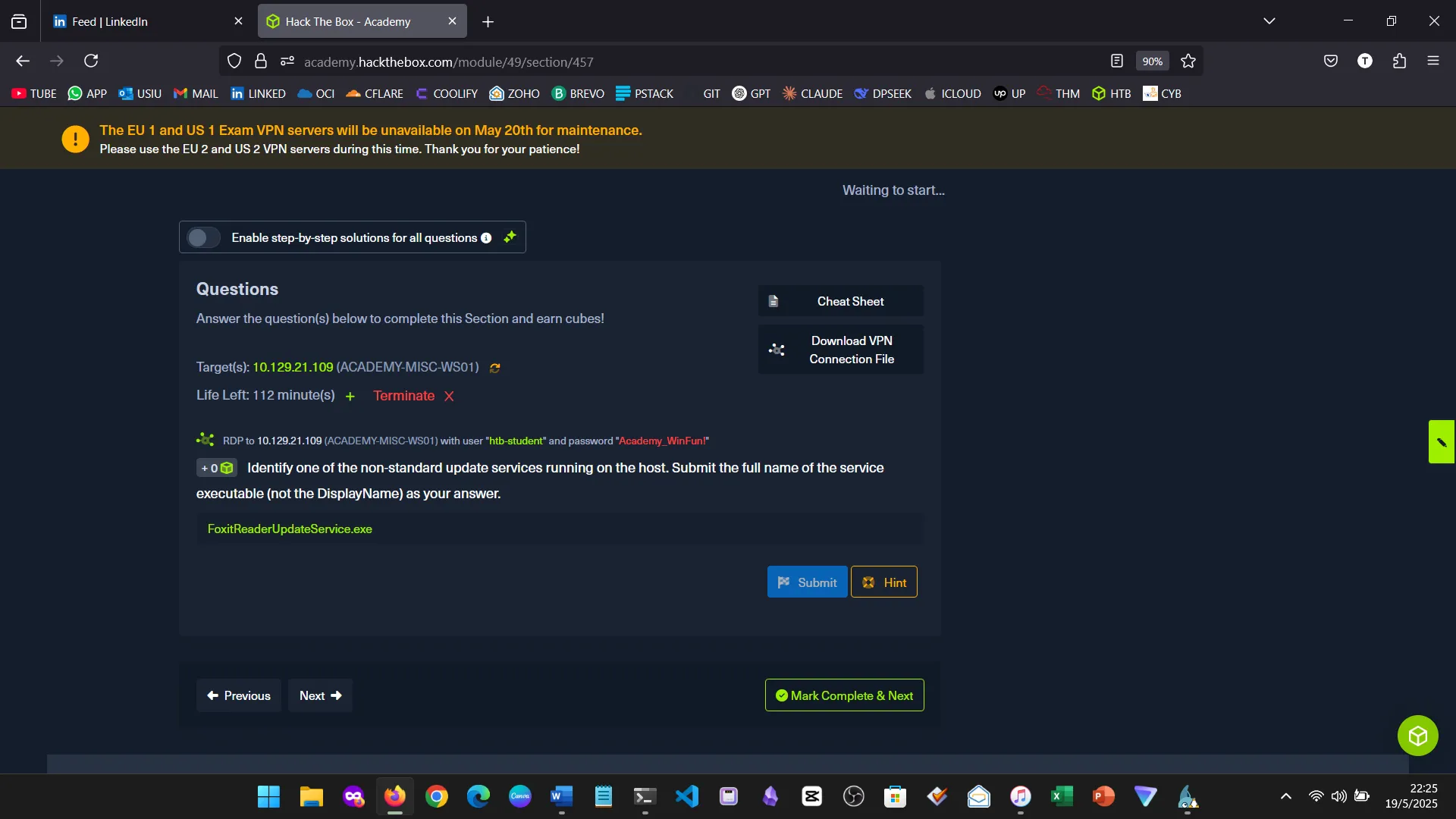
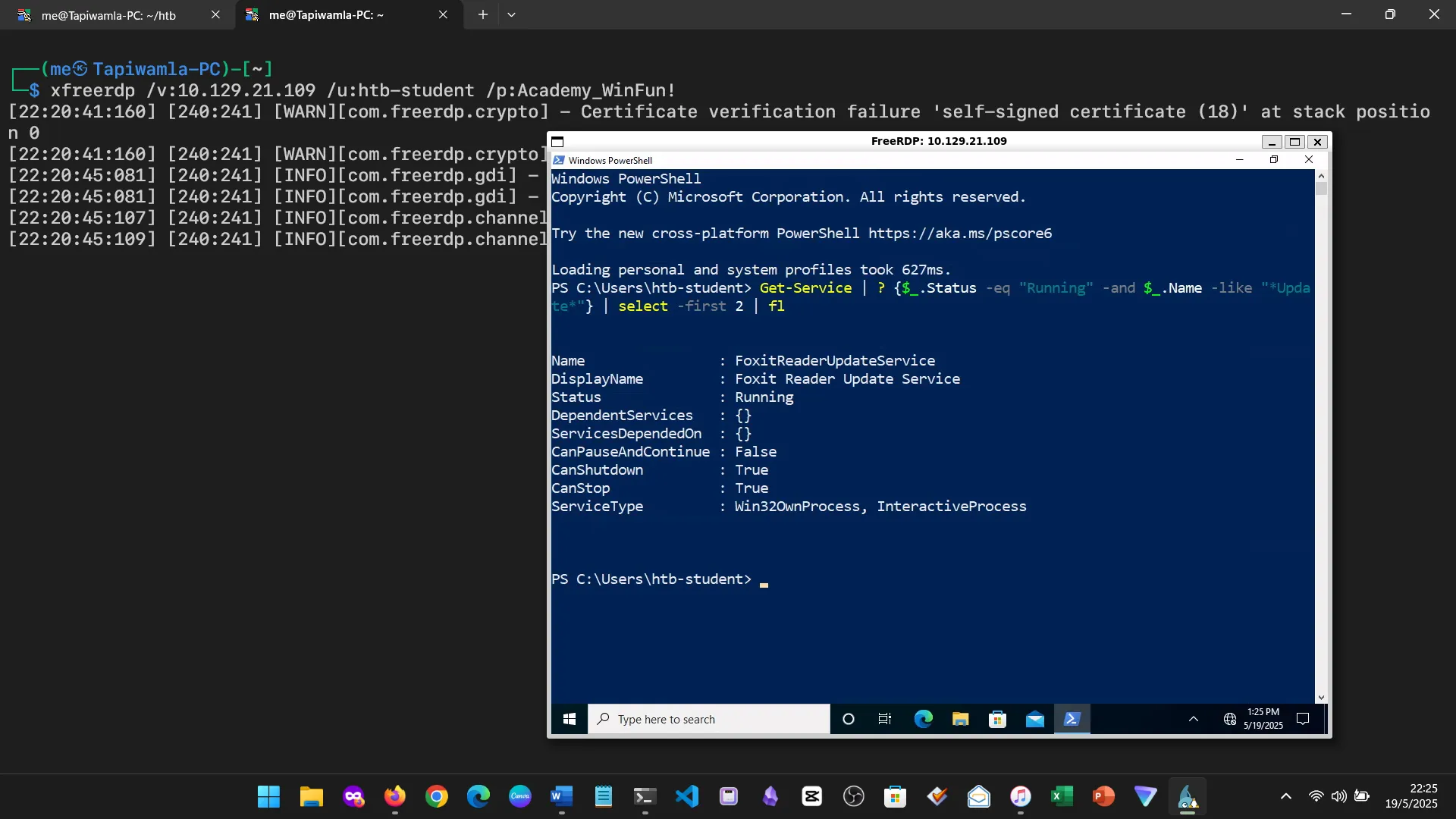
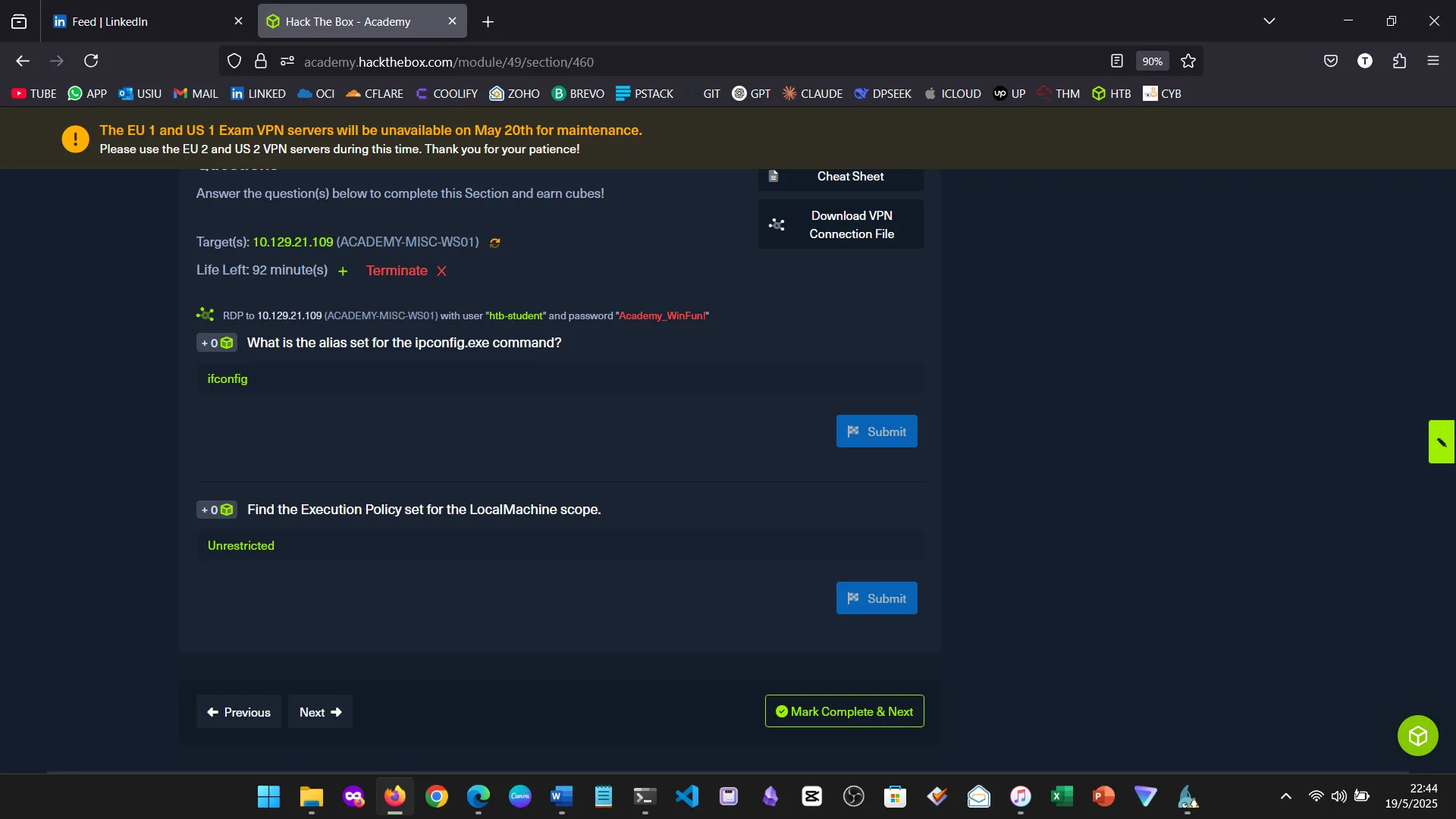
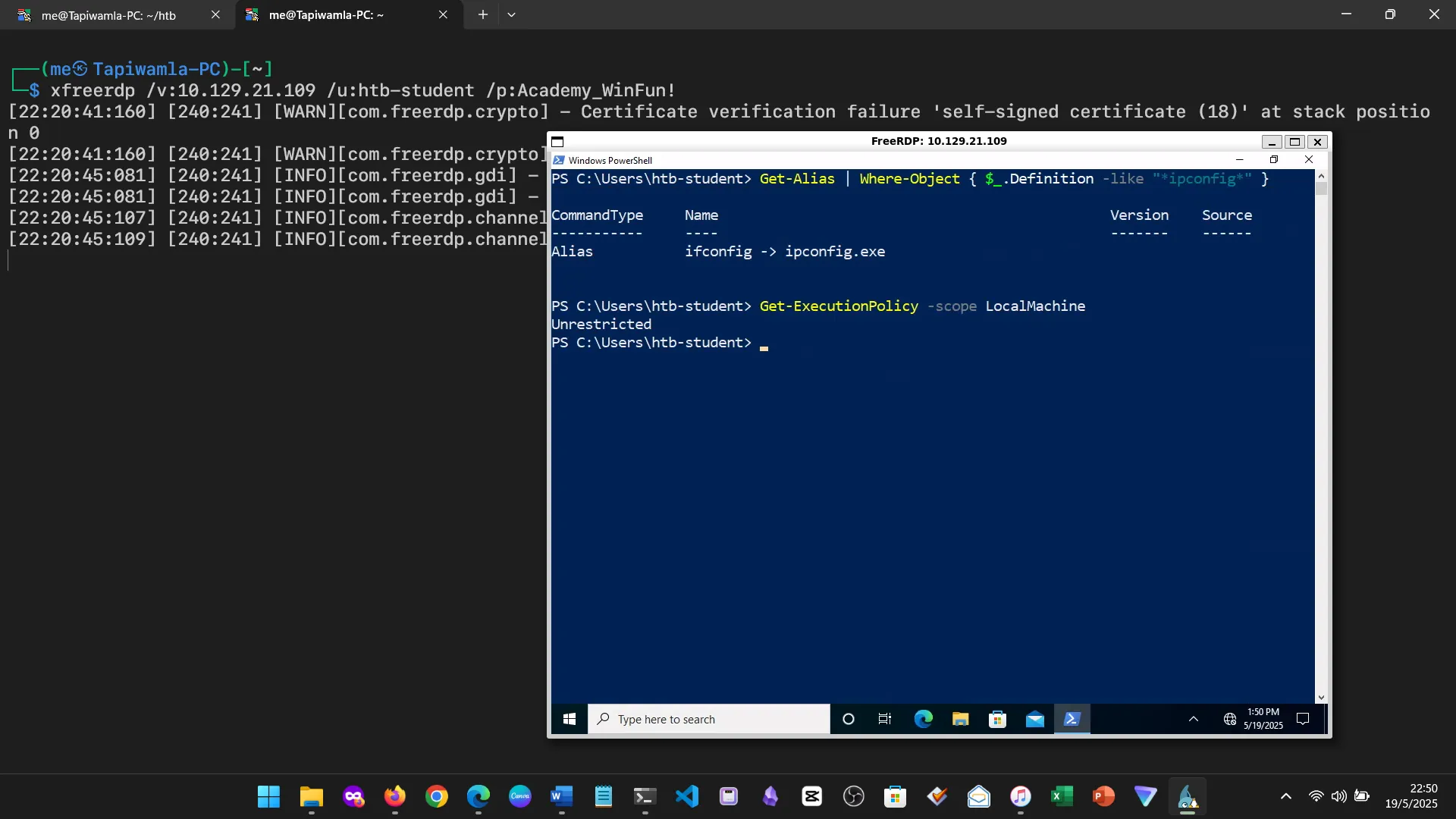
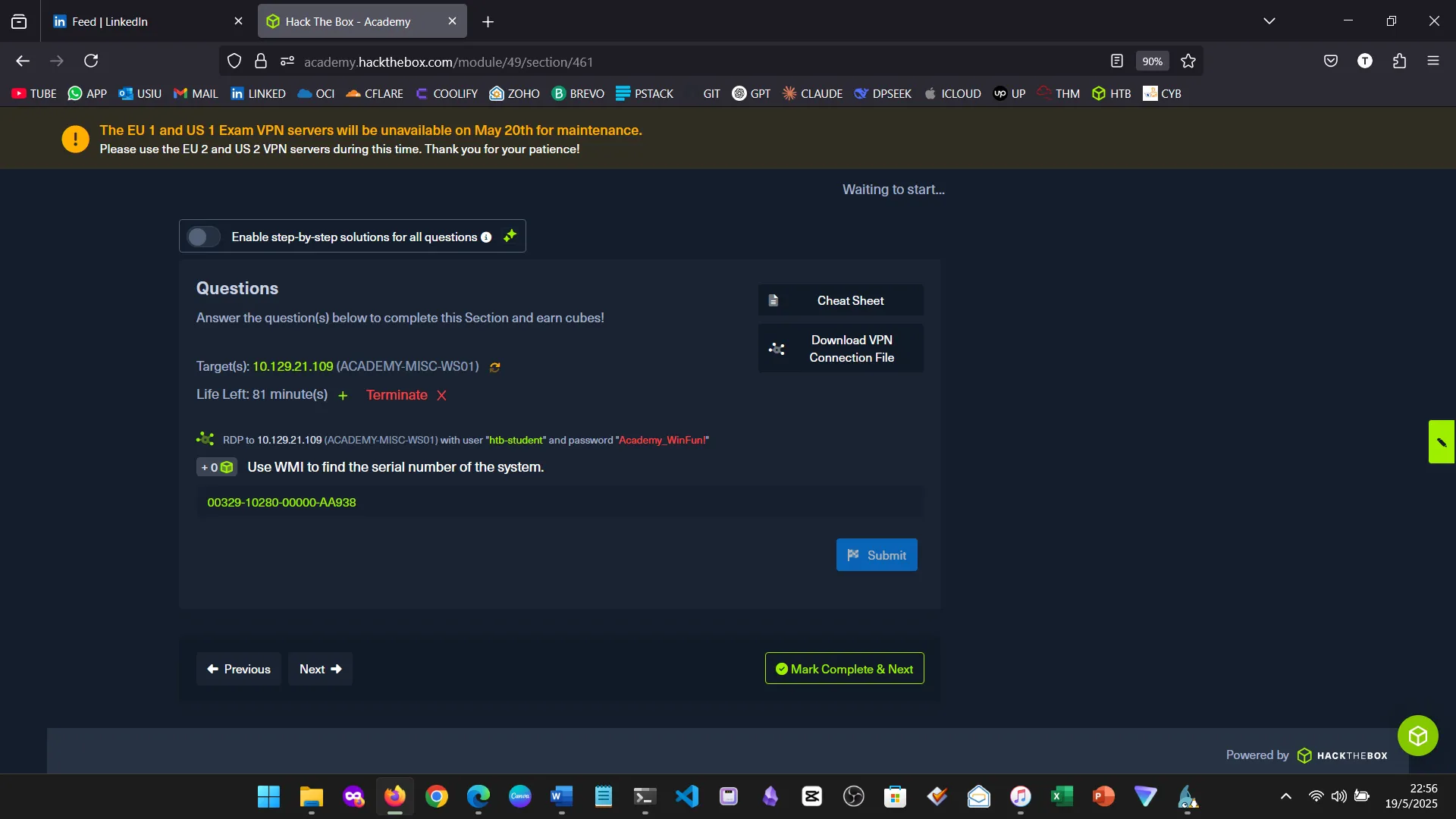
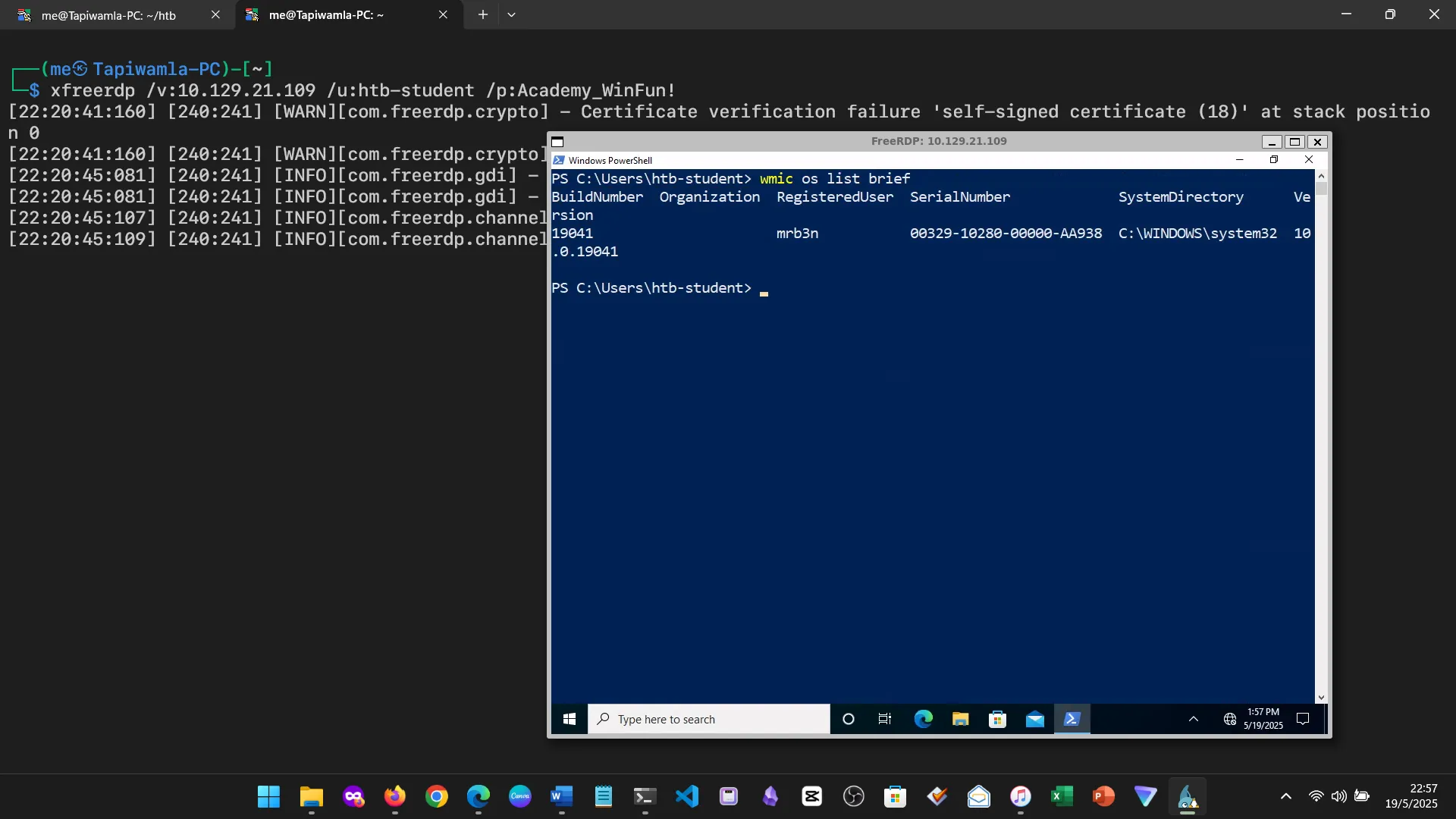
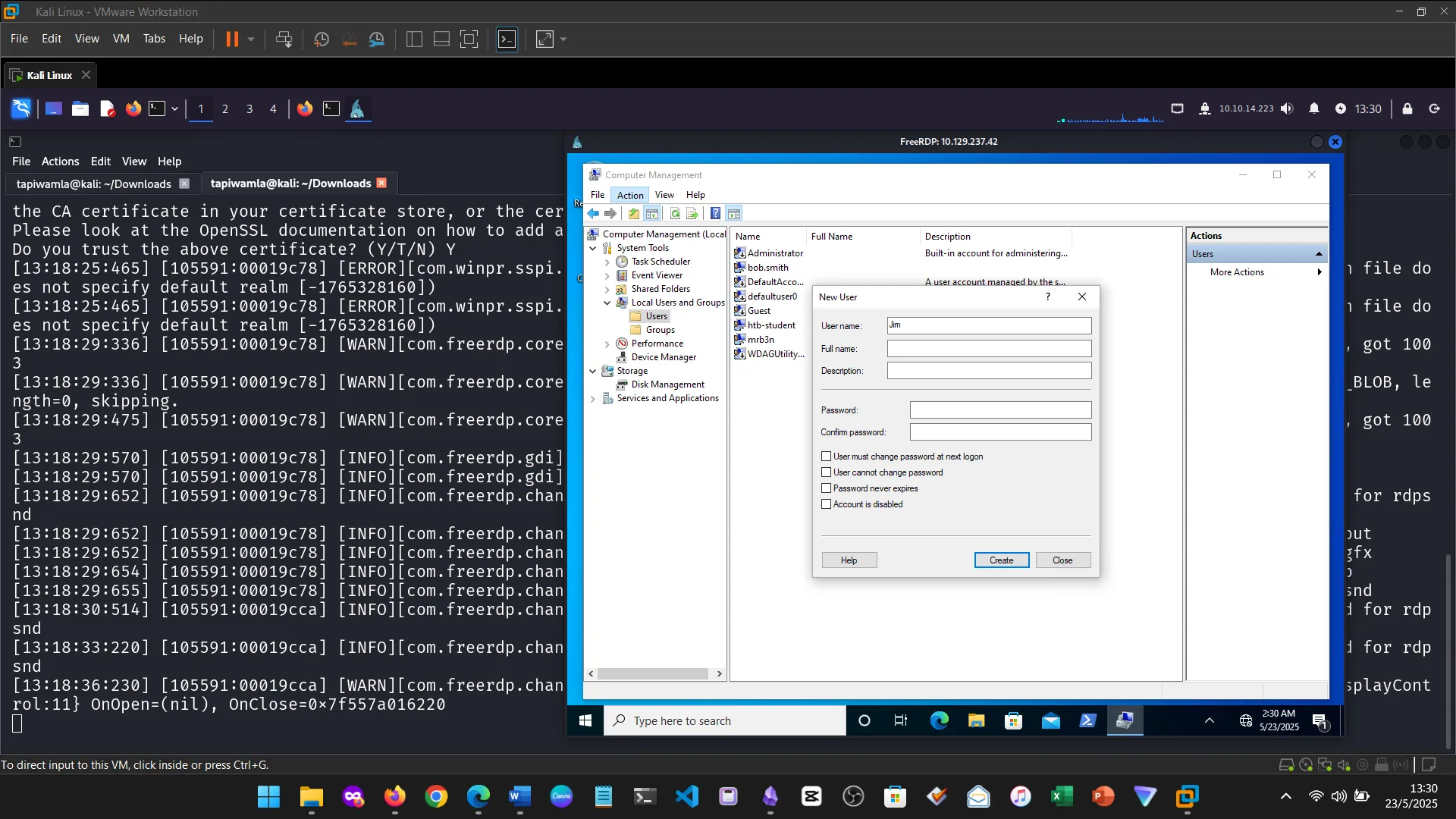
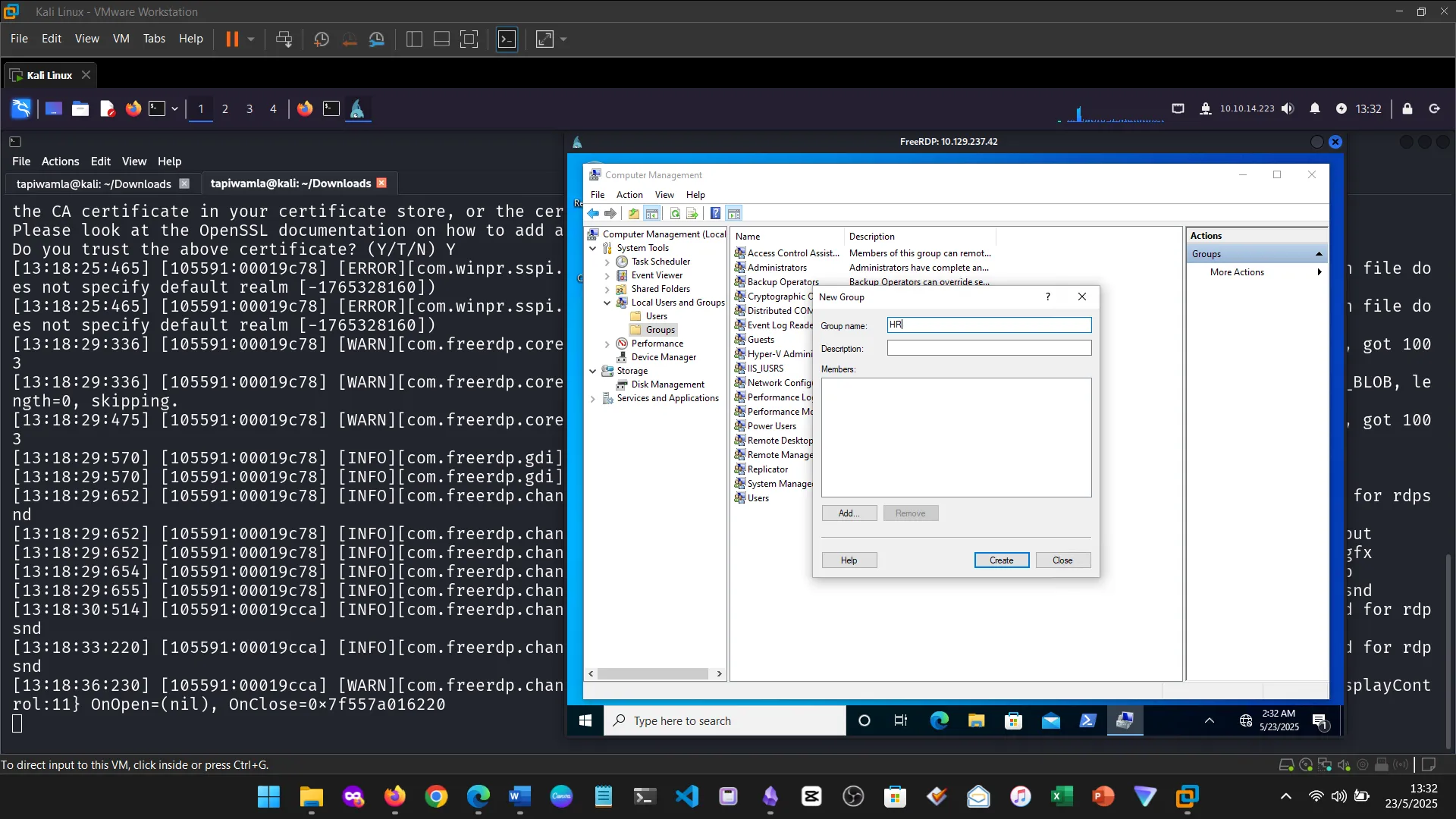
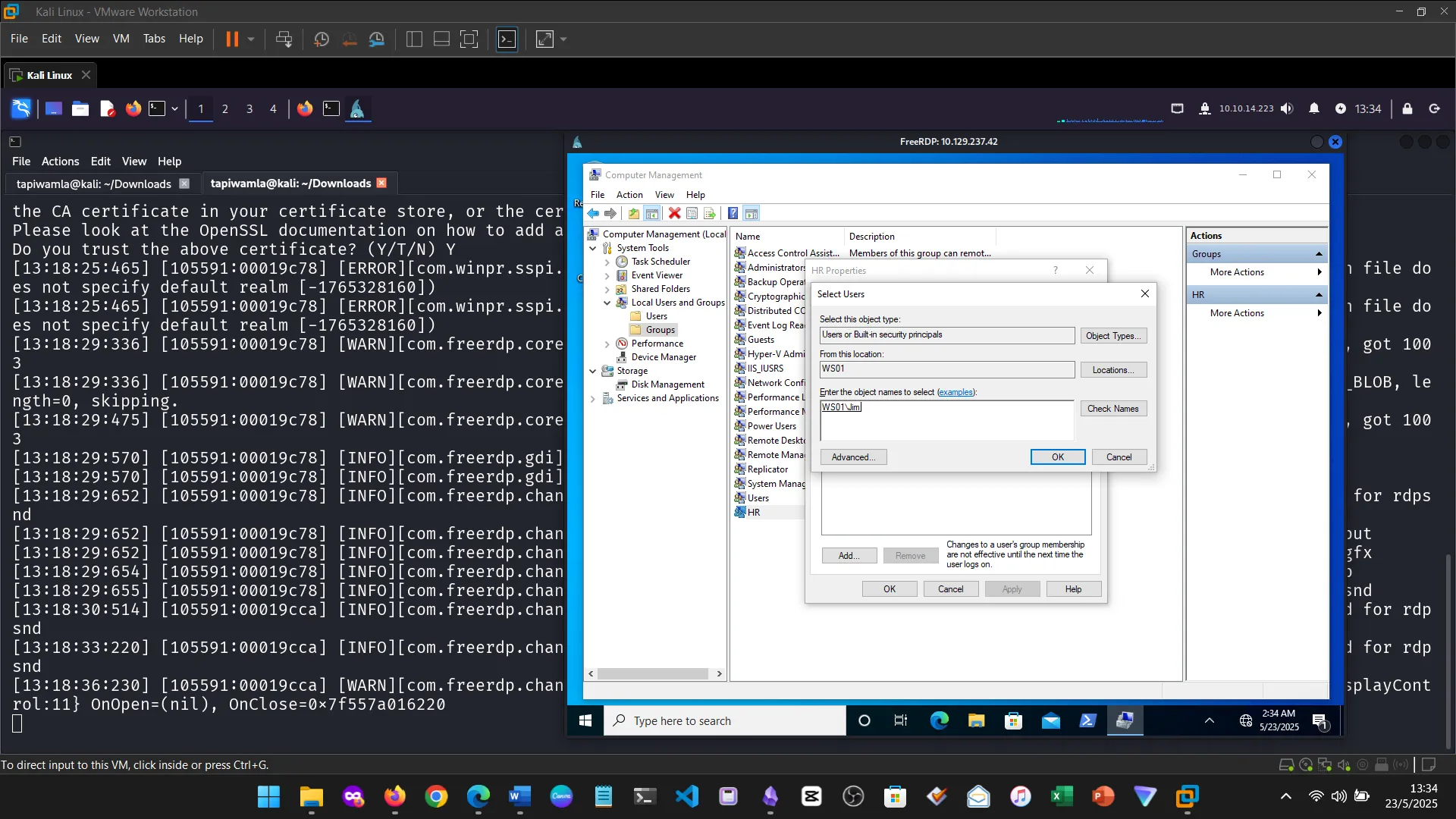
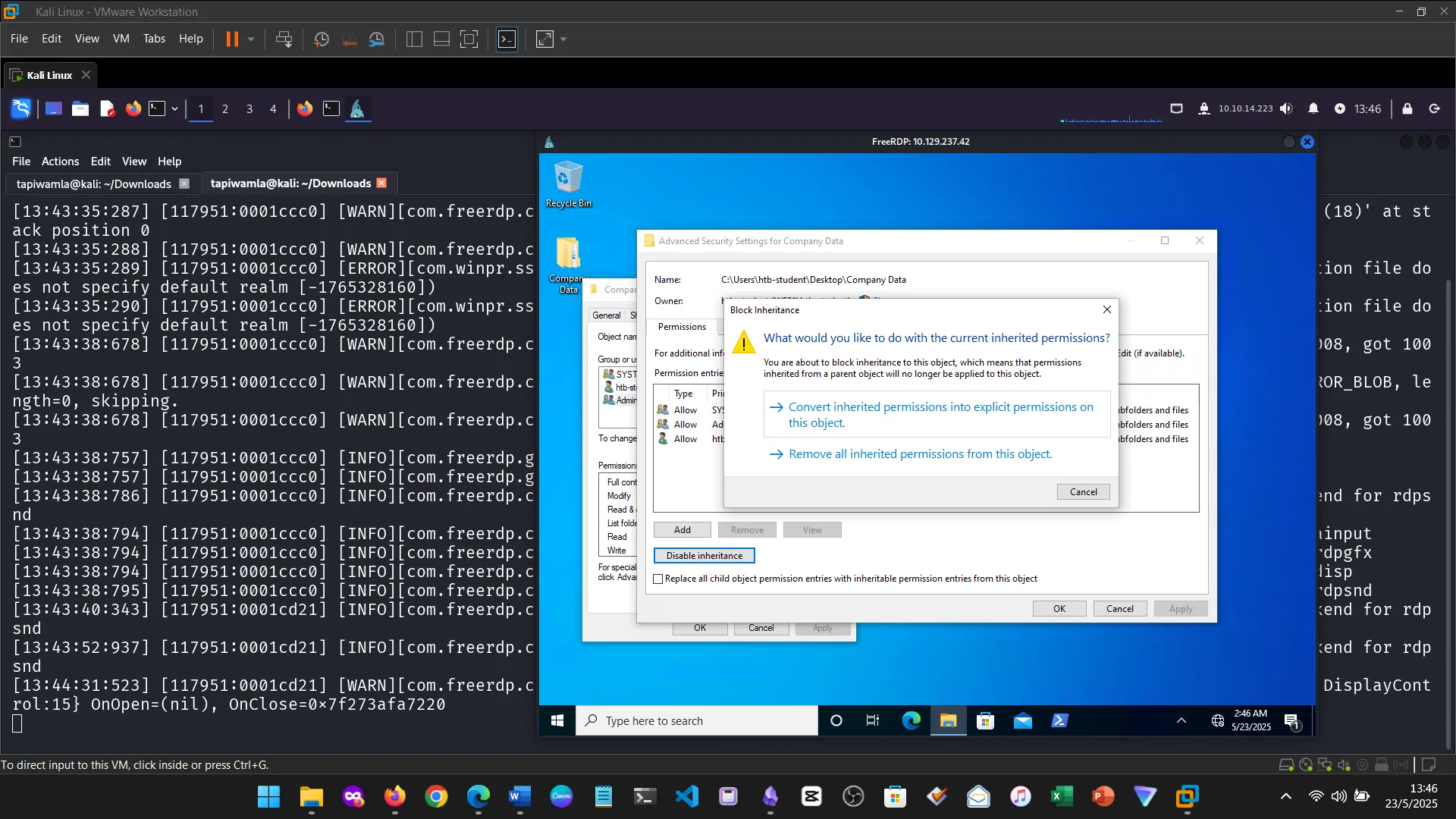
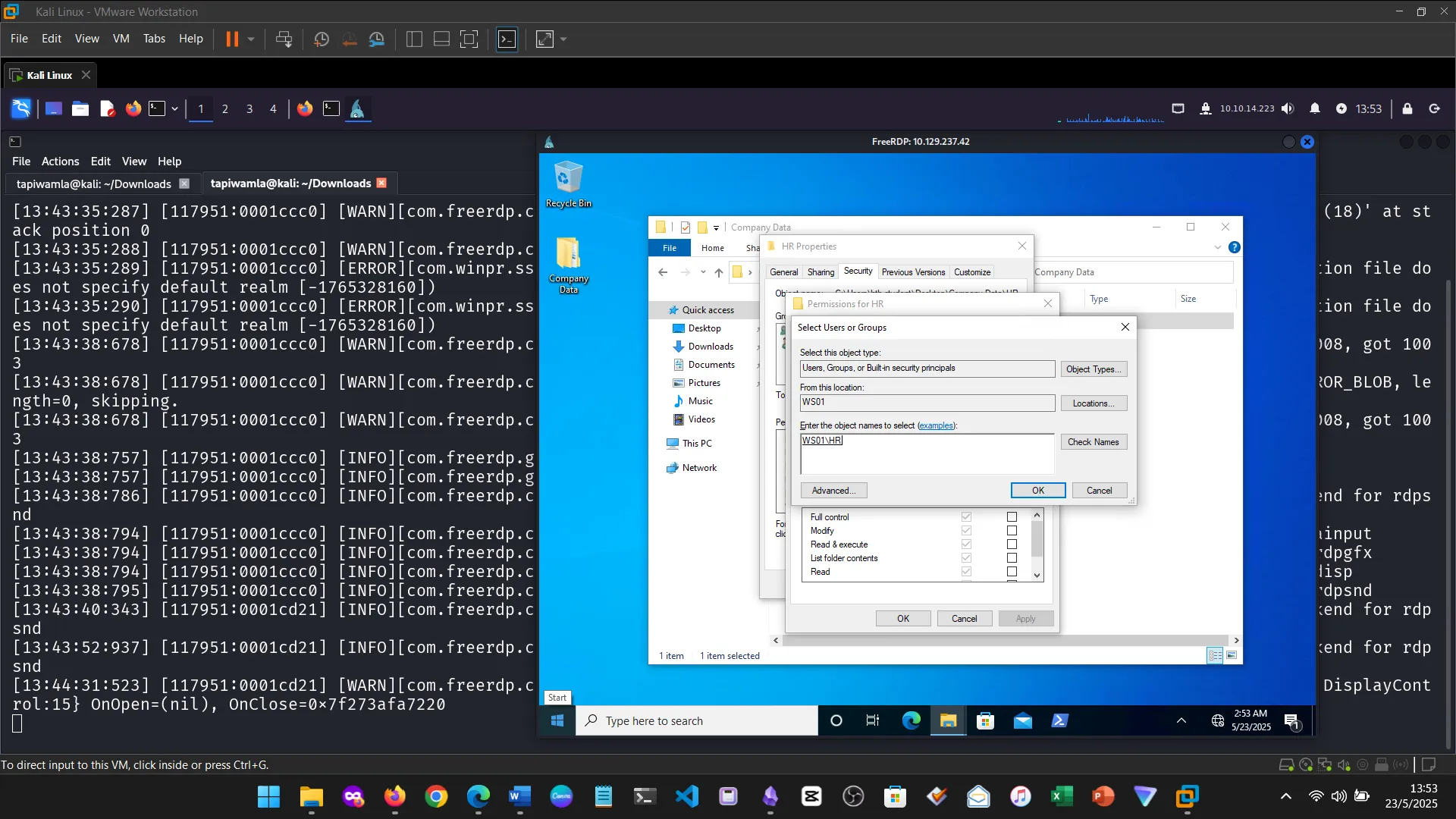
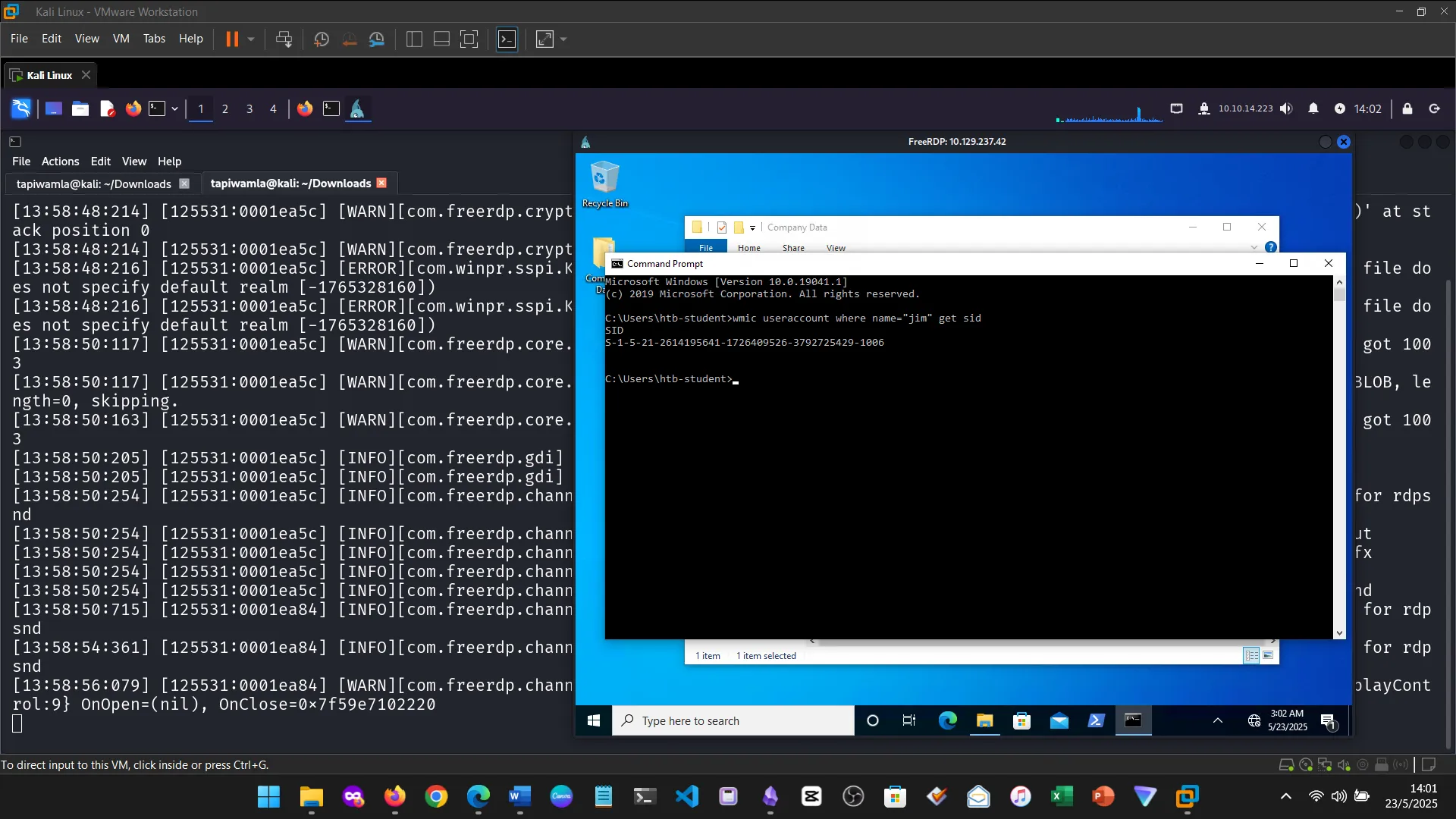
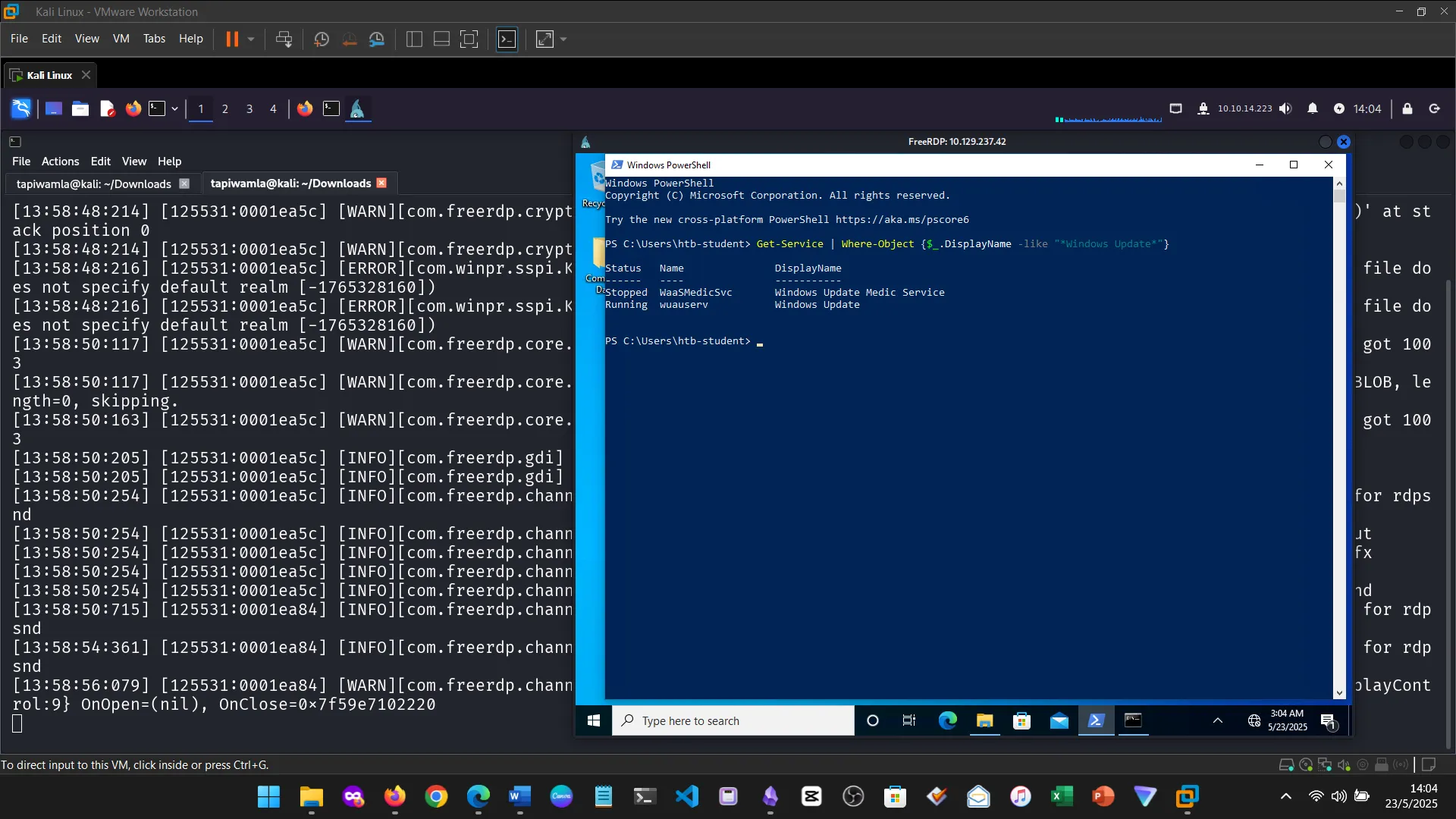
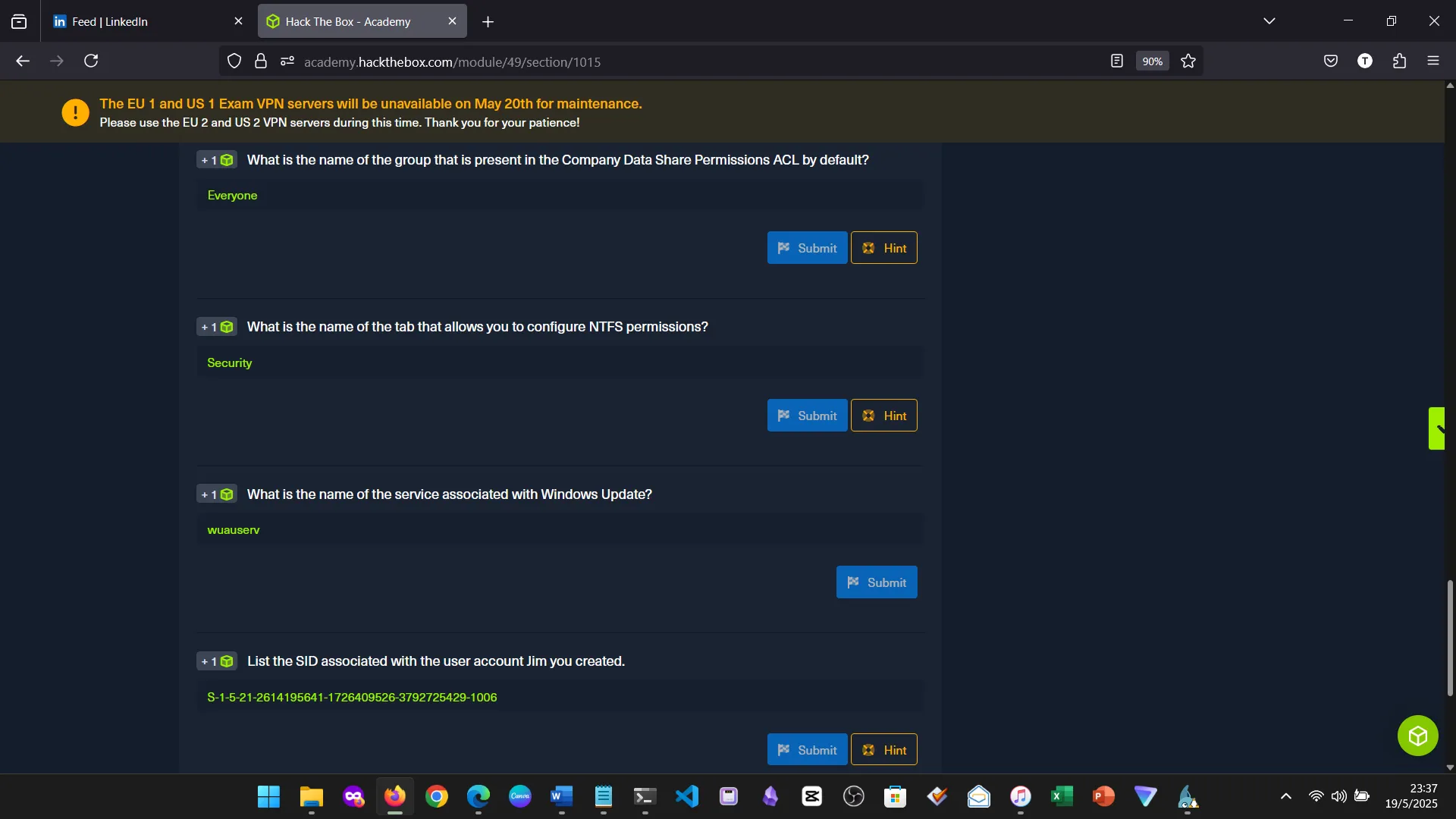
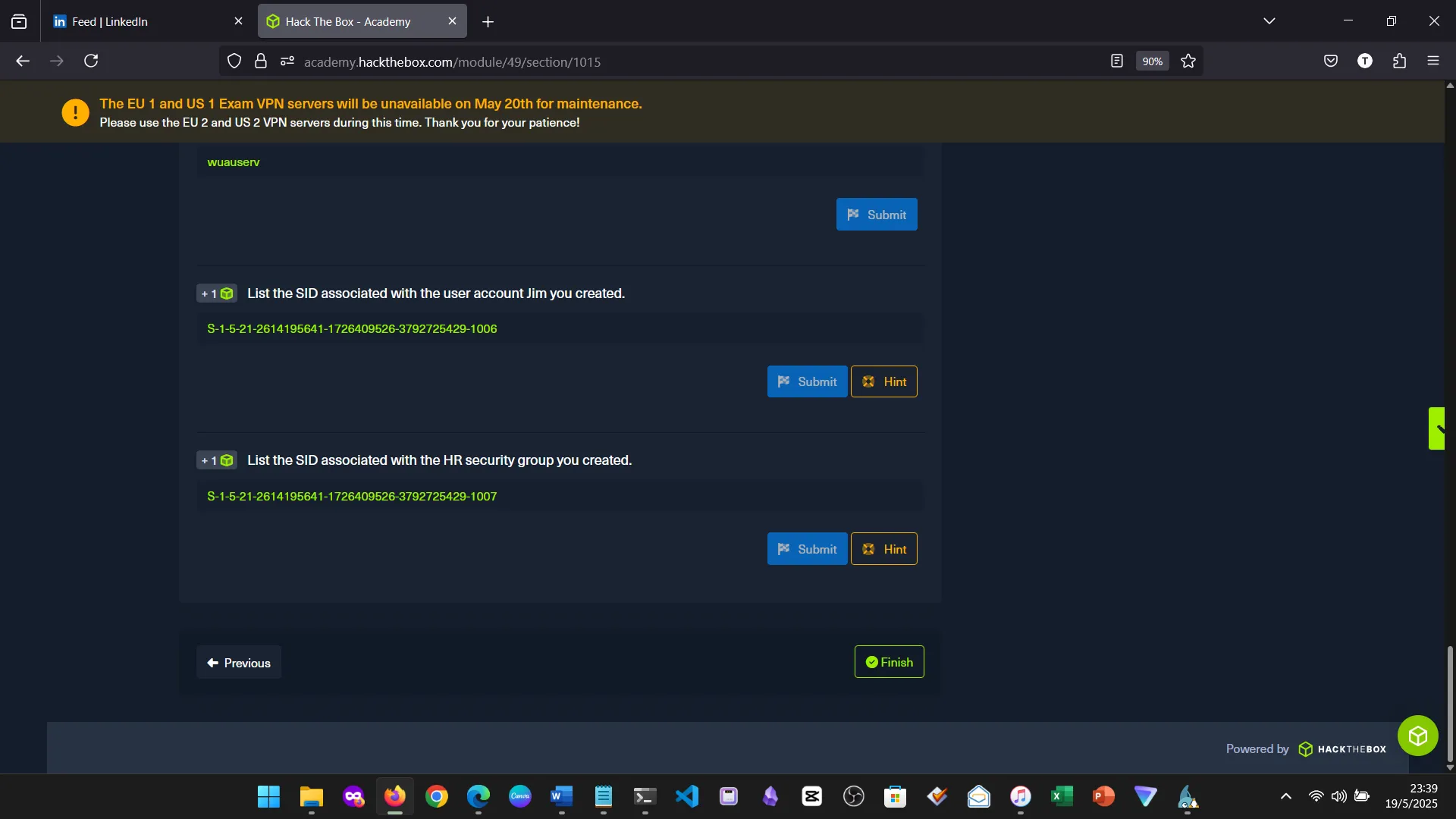
15. Skills Assessment
Below are screenshots from the hands-on demo I completed for the assessment, covering multiple key areas from the module.
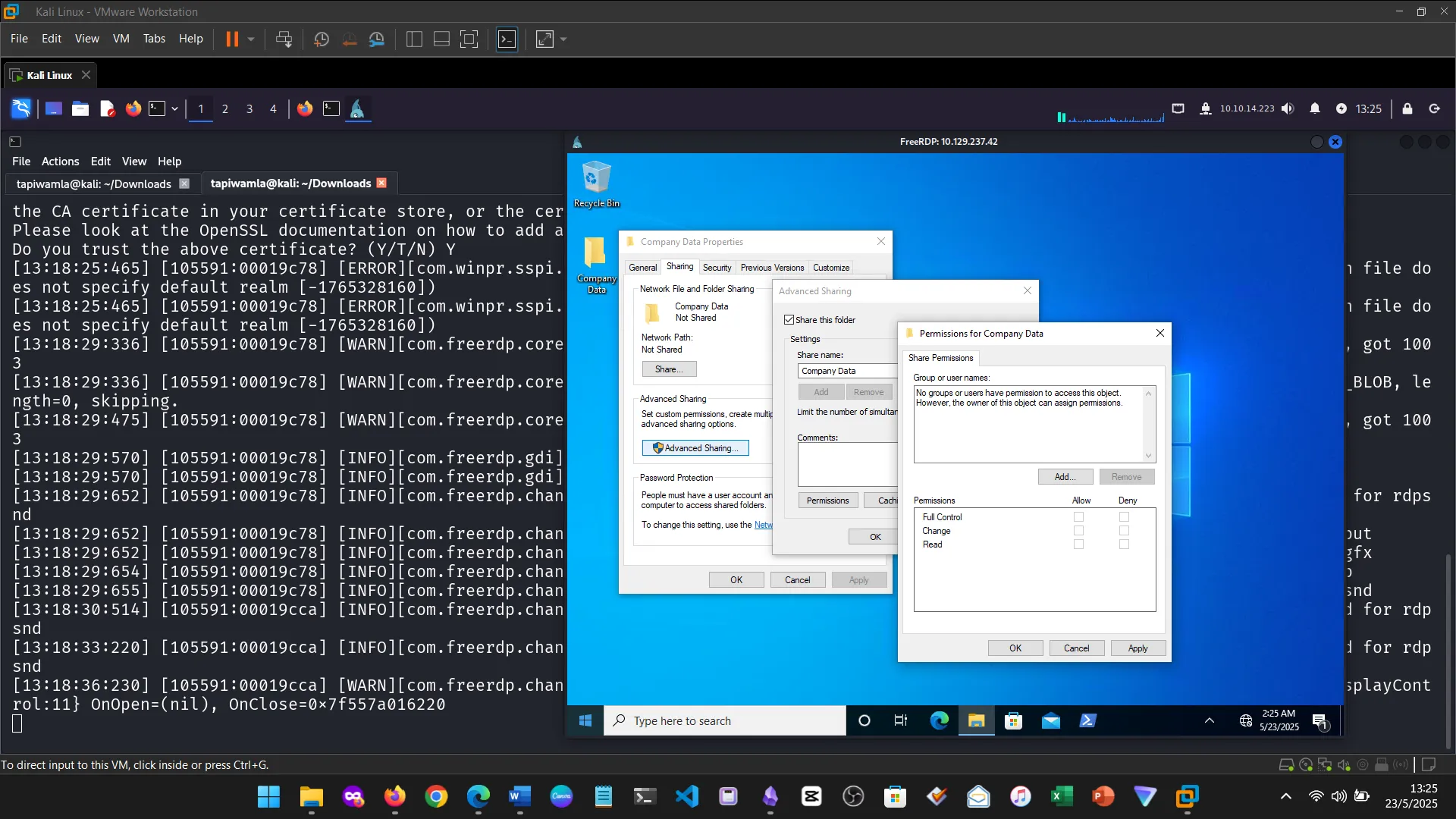
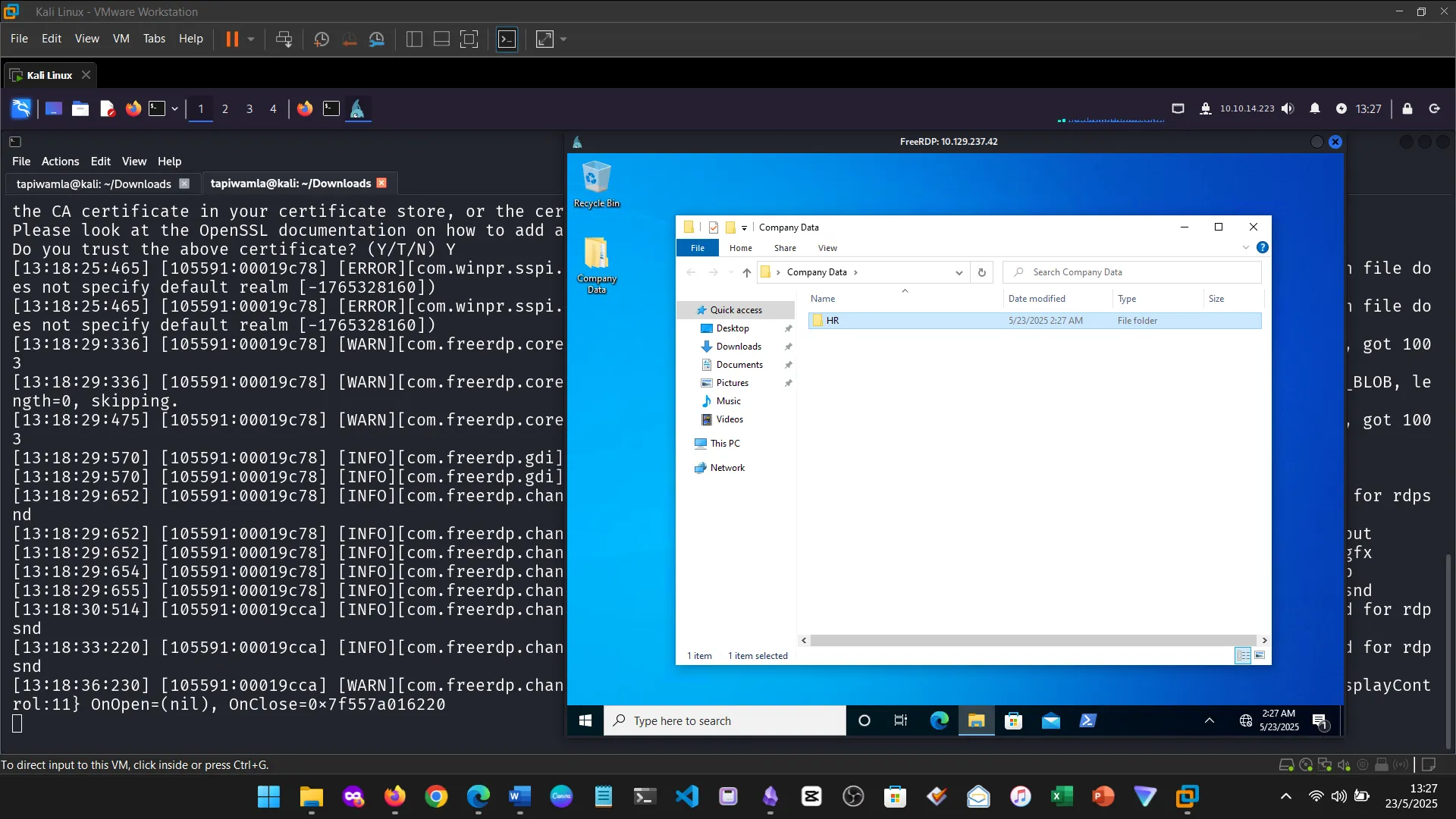
16. Conclusion
This module was a game changer for me. Despite years of using Windows, I realized how little I truly understood about its internals, especially from a cybersecurity perspective.
Even the differences between PowerShell and CMD—which commands are shared or not—were eye-opening. I learned that even subtle things like slash direction (\ vs /) can cause issues in scripting.
Windows has layers of tools, permissions, and controls I had not previously appreciated. The module pushed me to update my personal learning roadmap to include Windows system administration as a core cybersecurity skill.